交换机作为STelnet客户端登录其他设备配置示例
1、组网需求
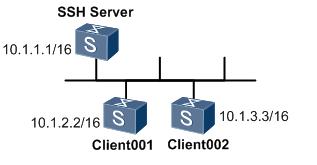
图1 设备通过STelnet登录其他设备组网图
如上图1所示,用户希望在服务器端和客户端进行安全的数据交互,配置两个登录用户为client001和client002,分别使用password认证方式和RSA认证方式登录SSH服务器,并且配置新的端口号,而不使用缺省端口号。
2、配置思路
1、在SSH服务器端生成本地密钥对,实现在服务器端和客户端进行安全的数据交互。
2、在SSH服务器端配置SSH用户client001和client002分别使用不同的认证方式。
3、在SSH服务器端开启STelnet服务功能。
4、在SSH服务器端配置SSH用户client001和client002的服务方式为STelnet。
5、在SSH服务器端配置SSH服务器的端口号,有效防止攻击者对SSH服务标准端口的访问,确保安全性。
6、用户client001和client002分别以STelnet方式实现登录SSH服务器。
3、操作步骤
3.1、在服务器端生成本地密钥对
system-view
[HUAWEI] sysname SSH Server
[SSH Server] rsa local-key-pair create
The key name will be: SSH Server_Host
The range of public key size is (512 ~ 2048).
NOTES: If the key modulus is greater than 512,
it will take a few minutes.
Input the bits in the modulus[default = 2048]:2048
Generating keys...
......................++++++++
........................................................++++++++
........+++++++++
.....+++++++++
3.2、在服务器端创建SSH用户
3.2.1、配置VTY用户界面。
[SSH Server] user-interface vty 0 4
[SSH Server-ui-vty0-4] authentication-mode aaa
[SSH Server-ui-vty0-4] protocol inbound ssh
[SSH Server-ui-vty0-4] quit
3.2.2、创建SSH用户client001。 新建用户名为client001的SSH用户,且认证方式为password。
[SSH Server] aaa
[SSH Server-aaa] local-user client001 password irreversible-cipher Huawei@123
[SSH Server-aaa] local-user client001 privilege level 3
[SSH Server-aaa] local-user client001 service-type ssh
[SSH Server-aaa] quit
[SSH Server] ssh user client001
[SSH Server] ssh user client001 authentication-type password
3.3.3、创建SSH用户client002。新建用户名为client002的SSH用户,且认证方式为RSA。
[SSH Server] ssh user client002
[SSH Server] ssh user client002 authentication-type rsa
3.4、在STelnet客户端Client002生成客户端的本地密钥对。
system-view
[HUAWEI] sysname client002
[client002] rsa local-key-pair create
The key name will be: client002_Host
The range of public key size is (512 ~ 2048).
NOTES: If the key modulus is greater than 512,
it will take a few minutes.
Input the bits in the modulus[default = 2048]:2048
Generating keys...
......................++++++++
........................................................++++++++
........+++++++++
.....+++++++++
3.5、查看客户端上生成的RSA密钥对的公钥部分。
[client002] display rsa local-key-pair public
=====================================================
Time of Key pair created: 2014-03-03 16:51:28-05:13
Key name: client002_Host
Key type: RSA encryption Key
=====================================================
Key code:
30820109
02820100
CA97BCDE 697CEDE9 D9AB9475 9E004D15 C8B95116
87B79B0C 5698C582 69A9F4D0 45ED0E53 AF2EDEC1
A09DF4BE 459E34B6 6697B85D 2191A00E 92F3A5E7
FB0E73E7 F0212432 E898D979 8EAA491E E2B69727
4B51A2BE CD86A144 16748D1E 4847A814 3FE50862
6EB1AD81 EB49A05E 64F6D186 C4E94CDB 04C53074
B839305A 7F7BCE2C 606F6C91 EA958B6D AC46C12B
8C2B1E03 98F1C09D 3AF2A69D 6867F930 DF992692
9A921682 916273FC 4DD875D4 44BC371E DDBB8F6A
C0A4CDB3 ADDAE853 DB86B9FA DB13CCA9 D8CF6EC1
530CC2F5 697C4707 90829982 4339507F F354FAF9
0F9CD2C2 F7D6FF3D 901D700F F0588104 856B9592
71D773E2 E76E8EEB 431FB60D 60ABC20B
0203
010001
Host public key for PEM format code:
---- BEGIN SSH2 PUBLIC KEY ----
AAAAB3NzaC1yc2EAAAADAQABAAABAQDKl7zeaXzt6dmrlHWeAE0VyLlRFoe3mwxW
mMWCaan00EXtDlOvLt7BoJ30vkWeNLZml7hdIZGgDpLzpef7DnPn8CEkMuiY2XmO
qkke4raXJ0tRor7NhqFEFnSNHkhHqBQ/5QhibrGtgetJoF5k9tGGxOlM2wTFMHS4
OTBaf3vOLGBvbJHqlYttrEbBK4wrHgOY8cCdOvKmnWhn+TDfmSaSmpIWgpFic/xN
2HXURLw3Ht27j2rApM2zrdroU9uGufrbE8yp2M9uwVMMwvVpfEcHkIKZgkM5UH/z
VPr5D5zSwvfW/z2QHXAP8FiBBIVrlZJx13Pi526O60Mftg1gq8IL
---- END SSH2 PUBLIC KEY ----
Public key code for pasting into OpenSSH authorized_keys file :
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDKl7zeaXzt6dmrlHWeAE0VyLlRFoe3mwxWmMWCaan00EXtDlOvLt7BoJ30vkWeNLZml7hdIZGgDpLzpef7DnPn8CEkMuiY2XmOqkke4raXJ0tRor7NhqFEFnSNHkhHqBQ/5QhibrGtgetJoF5k9tGGxOlM2wTFMHS4OTBaf3vOLGBvbJHqlYttrEbBK4wrHgOY8cCdOvKmnWhn+TDfmSaSmpIWgpFic/xN2HXURLw3Ht27j2rApM2zrdroU9uGufrbE8yp2M9uwVMMwvVpfEcHkIKZgkM5UH/zVPr5D5zSwvfW/z2QHXAP8FiBBIVrlZJx13Pi526O60Mftg1gq8IL rsa-key
=====================================================
Time of Key pair created: 2014-03-03 16:51:29-05:13
Key name: client002_Server
Key type: RSA encryption Key
=====================================================
Key code:
3081B8
0281B0
BCF579A1 063A03D7 595C1E4F D7252C49 CDB04F32
B9FFEB6F AC0CA862 5033B5BF B05442B4 684D0EB9
F3E2510C C9B55C59 671E6E9A 0E0D1C17 9EE621BD
766774DF AB6EFD70 21D405C9 BD181E53 7F643D82
CA5828DA C9C75455 E87400CB C06D3760 84B765CA
FA4FF828 D1B223BA 8BCB2F93 766D9835 0F011511
CE9041B5 12326069 61DD0352 6D9A80CC C4BB88EC
227C74A5 5AF14AFA 74FE7B98 C3EF723A AFF753F1
9ED3306A CDA857D8 0E90434F 5783A36B
0203
010001
3.6、将客户端上产生的RSA公钥配置到服务器端(上面display命令显示信息中黑体部分即为客户端产生的RSA公钥,将其拷贝粘贴至服务器端)。
[SSH Server] rsa peer-public-key rsakey001
[SSH Server-rsa-public-key] public-key-code begin
[SSH Server-rsa-key-code] 30820109
[SSH Server-rsa-key-code] 2820100
[SSH Server-rsa-key-code] CA97BCDE 697CEDE9 D9AB9475 9E004D15 C8B95116
[SSH Server-rsa-key-code] 87B79B0C 5698C582 69A9F4D0 45ED0E53 AF2EDEC1
[SSH Server-rsa-key-code] A09DF4BE 459E34B6 6697B85D 2191A00E 92F3A5E7
[SSH Server-rsa-key-code] FB0E73E7 F0212432 E898D979 8EAA491E E2B69727
[SSH Server-rsa-key-code] 4B51A2BE CD86A144 16748D1E 4847A814 3FE50862
[SSH Server-rsa-key-code] 6EB1AD81 EB49A05E 64F6D186 C4E94CDB 04C53074
[SSH Server-rsa-key-code] B839305A 7F7BCE2C 606F6C91 EA958B6D AC46C12B
[SSH Server-rsa-key-code] 8C2B1E03 98F1C09D 3AF2A69D 6867F930 DF992692
[SSH Server-rsa-key-code] 9A921682 916273FC 4DD875D4 44BC371E DDBB8F6A
[SSH Server-rsa-key-code] C0A4CDB3 ADDAE853 DB86B9FA DB13CCA9 D8CF6EC1
[SSH Server-rsa-key-code] 530CC2F5 697C4707 90829982 4339507F F354FAF9
[SSH Server-rsa-key-code] 0F9CD2C2 F7D6FF3D 901D700F F0588104 856B9592
[SSH Server-rsa-key-code] 71D773E2 E76E8EEB 431FB60D 60ABC20B
[SSH Server-rsa-key-code] 203
[SSH Server-rsa-key-code] 10001
[SSH Server-rsa-key-code] public-key-code end
[SSH Server-rsa-public-key] peer-public-key end
3.7、在SSH服务器端为SSH用户client002绑定STelnet客户端的RSA公钥。
[SSH Server] ssh user client002 assign rsa-key rsakey001
3.8、SSH服务器端开启STelnet服务功能
[SSH Server] stelnet server enable
3.9、配置SSH用户client001、client002的服务方式为STelnet
[SSH Server] ssh user client001 service-type stelnet
[SSH Server] ssh user client002 service-type stelnet
3.10、配置SSH服务器端新的端口号
[SSH Server] ssh server port 1025
3.11、STelnet客户端连接SSH服务器
3.11.1、 第一次登录,需要使能SSH客户端首次认证功能。使能客户端Client001首次认证功能。
system-view
[HUAWEI] sysname client001
[client001] ssh client first-time enable
使能客户端Client002首次认证功能。
[client002] ssh client first-time enable
3.11.2、STelnet客户端Client001用password认证方式连接SSH服务器,输入配置的用户名和密码。
[client001] stelnet 10.1.1.1 1025
Please input the username:client001
Trying 10.1.1.1 ...
Press CTRL+K to abort
Connected to 10.1.1.1 ...
The server is not authenticated. Continue to access it?[Y/N]:y
Save the server's public key?[Y/N]:y
The server's public key will be saved with the name 10.1.1.1. Please wait...
Enter password:
输入密码,显示登录成功信息如下:
Info: The max number of VTY users is 8, and the number
of current VTY users on line is 2.
The current login time is 2012-08-16 10:33:18+00:00.
3.11.3、STelnet客户端Clent002用RSA认证方式连接SSH服务器。
[client002] stelnet 10.1.1.1 1025
Please input the username: client002
Trying 10.1.1.1 ...
Press CTRL+K to abort
Connected to 10.1.1.1 ...
The server is not authenticated. Continue to access it?[Y/N]:y
Save the server's public key?[Y/N]:y
The server's public key will be saved with the name 10.1.1.1. Please wait...
Info: The max number of VTY users is 8, and the number
of current VTY users on line is 3.
The current login time is 2012-08-16 11:48:42+00:00.
如果登录成功,用户将进入用户视图。如果登录失败,用户将收到Session is disconnected的信息。
3.12、验证配置结果
3.12.1、攻击者使用原端口号22登录SSH服务器,不能成功。
[client002] stelnet 10.1.1.1
Please input the username:client002
Trying 10.1.1.1 ...
Press CTRL+K to abort
Error: Failed to connect to the remote host.
在SSH服务器端执行display ssh server status命令可以查看到STelnet服务已经使能。执行display ssh user-information命令可以查看服务器端SSH用户信息。
3.12.2、查看SSH状态信息。
[SSH Server] display ssh server status
SSH version :1.99
SSH connection timeout :60 seconds
SSH server key generating interval :0 hours
SSH authentication retries :3 times
SFTP server :Disable
Stelnet server :Enable
Scp server :Disable
SSH server port :1025
SSH server source :0.0.0.0
ACL4 number :0
ACL6 number
:0
3.12.3、查看SSH用户信息。
[SSH Server] display ssh user-information
User 1:
User Name : client001
Authentication-type : password
User-public-key-name : -
User-public-key-type : -
Sftp-directory : -
Service-type : stelnet
Authorization-cmd : No
User 2:
User Name : client002
Authentication-type : rsa
User-public-key-name : rsaKey001
User-public-key-type : rsa
Sftp-directory : -
Service-type : stelnet
Authorization-cmd : No
4、配置文件
4.1、SSH服务器的配置文件
#
sysname SSH Server
#
rsa peer-public-key rsakey001
public-key-code begin
30820109
02820100
CA97BCDE 697CEDE9 D9AB9475 9E004D15 C8B95116 87B79B0C 5698C582 69A9F4D0
45ED0E53 AF2EDEC1 A09DF4BE 459E34B6 6697B85D 2191A00E 92F3A5E7 FB0E73E7
F0212432 E898D979 8EAA491E E2B69727 4B51A2BE CD86A144 16748D1E 4847A814
3FE50862 6EB1AD81 EB49A05E 64F6D186 C4E94CDB 04C53074 B839305A 7F7BCE2C
606F6C91 EA958B6D AC46C12B 8C2B1E03 98F1C09D 3AF2A69D 6867F930 DF992692
9A921682 916273FC 4DD875D4 44BC371E DDBB8F6A C0A4CDB3 ADDAE853 DB86B9FA
DB13CCA9 D8CF6EC1 530CC2F5 697C4707 90829982 4339507F F354FAF9 0F9CD2C2
F7D6FF3D 901D700F F0588104 856B9592 71D773E2 E76E8EEB 431FB60D 60ABC20B
0203
010001
public-key-code end
peer-public-key end
#
aaa
local-user client001 password irreversible-cipher %@%@HW=5%Mr;:2)/RX$FnU1HLO%-TBMp4wn%;~#%iAut}_~O%0L%@%@
local-user client001 privilege level 3
local-user client001 service-type ssh
#
stelnet server enable
ssh server port 1025
ssh user client001
ssh user client001 authentication-type password
ssh user client001 service-type stelnet
ssh user client002
ssh user client002 authentication-type rsa
ssh user client002 assign rsa-key rsakey001
ssh user client002 service-type stelnet
#
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
#
return
4.2、SSH客户端Client001的配置文件
#
sysname client001
#
ssh client first-time enable
#
return
4.3、SSH客户端Client002的配置文件
#
sysname client002
#
ssh client first-time enable
#
return




















 1731
1731











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








