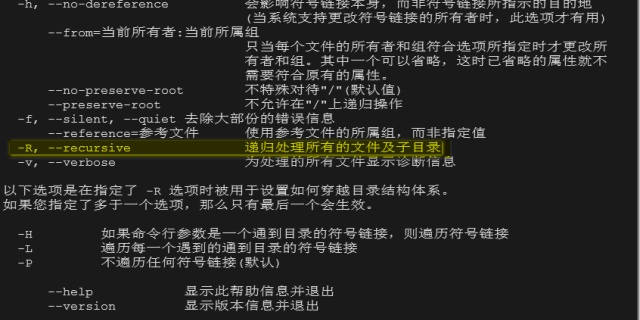
第一步,切换为root
su第二步,配置/etc/ssh/sshd_config
vi /etc/ssh/sshd_config输入G,直达配置文件底部寻找是否有
Subsystem sftp /usr/libexec/openssh/sftp-server有则注释掉
# Subsystem sftp /usr/libexec/openssh/sftp-server输入
Subsystem sftp internal-sftp
Match Group grouptest
ForceCommand internal-sftp
ChrootDirectory /var/report/grouptest/jack
PermitTunnel no
AllowAgentForwarding no
AllowTcpForwarding no
X11Forwarding no这里可以输入变量%u和%h。%u可以自动获得用户名/var/report/grouptest/%u,适合跳转用户比较多时使用,%h则为直接跳转到home该用户目录下。这里务必注意ChrootDiectory
ChrootDirectory
Specifies the pathname of a directory to chroot(2) to after authentication. All components of the pathname must be root-owned directories that are not writable by any other user or group. After the chroot, sshd(8) changes the working directory to the user's home directory.
根据官方文档说明可知,该跳转目录必须为root作为owner,如果不是,用FileZilla以sftp登录会弹出出Network error Software caused connection abort的错误。可以用如下命令更改
chown root:grouptest /var/report/grouptest/jack Match 可以组Group,也可以是用户User,取决于具体需求。
第三步,设置目录,分配用户名,为用户设置密码
name="jack"
groupname="grouptest"
groupadd $groupname
useradd -g $groupname -s /sbin/nologin $name
mkdir -p /var/report/$groupname
chmod g+rx /var/report/$groupname
mkdir -p /var/report/$groupname/$name
chgrp -R $groupname /var/report/$groupname
chmod g+rwx /var/report/$groupname/$name
chown root:$groupname /var/report/$groupname/$name
chmod 755 /var/report/$groupname/$name
service sshd restart这里useradd -s 、sbin/nologin是禁止用户ssh登录,可以把以上代码保存为useradd.sh,直接执行bash useradd.sh即可
第四部,绑定数据文件夹
mkdir -p /var/report/grouptest/jack/data
mount --bind /home/anotherusename/data /var/report/grouptest/jack/data这里共享数据我们不能用symbolic link和hard link,因为我们用Chroot限制了jack的根目录为/var/report/grouptest/jack, 用上面的link会访问不了,Jack的根由/ 变为了/var/report/grouptest/jack。因此只能用mount --bind
原文解释如下
root@server:/home/username# ln -s /var/www www
root@server:/home/username# cd www
root@server:/home/username/www# chown username:username *Now, with filezilla, I can see www folder like this:
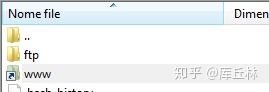
But when I try to open it, I get this:
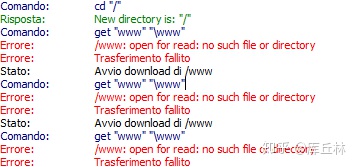
It's likely the SFTP is being chrooted, so that the directory /var/www is not available to the user in the chroot jail.
Look in /etc/ssh/sshd_config and examine the sftp directives. Do you see something like:
Match group sftp ChrootDirectory /home/%u AllowTcpForwarding no ForceCommand internal-sftp
The sshd_config man page is here.
Basically, once the user is in /home/username in SFTP, that directory becomes / and references outside of /home/username are not available. In fact, a symlink like ln -s /var/www /home/username/www will look like you're trying to reach /home/username/var/www (i.e., /home/username is now / so any link that references /var/www must also be a subdirectory of /home/username in the context of the chroot).
As a solution, you can turn off the chroot (but this will have other security implications, mainly with SFTP users having full rein over your filesystem). You can do a loop mount of /var/www into /home/username/www (something like mount --bind /var/www /home/username/www (check your documentation for mount) which should work as you'd expect under chroot). You can also muck with the sshd_config file to exclude that one particular user from chroot (though, again, with security implications).
I would try the bind mount first.
第五步,用FileZilla登录查看
附:
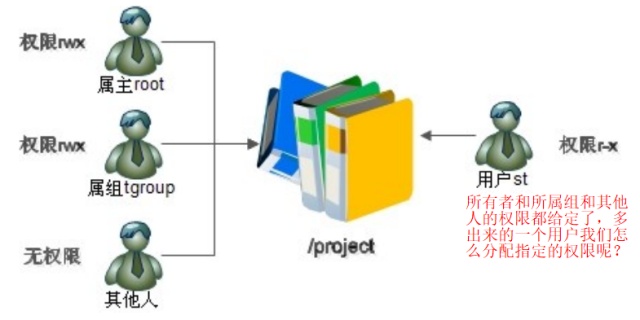
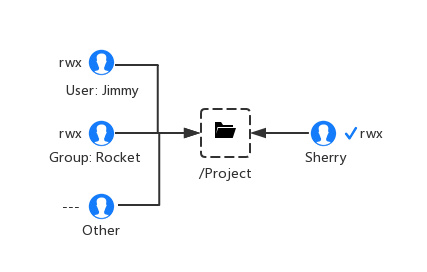
-rwxrw-r‐-1 root root 1213 Feb 2 09:39 abc
- 第一个字符代表文件(-)、目录(d),链接(l)
- 其余字符每3个一组(rwx),读(r)、写(w)、执行(x)
- 第一组rwx:文件所有者的权限是读、写和执行
- 第二组rw-:与文件所有者同一组的用户的权限是读、写但不能执行
- 第三组r--:不与文件所有者同组的其他用户的权限是读不能写和执行
也可用数字表示为:r=4,w=2,x=1 因此rwx=4+2+1=7
Reference:
centos 安装sftp服务 - Jack Deng - 博客园www.cnblogs.com groupdel: cannot remove user's primary groupask.apelearn.com





























 371
371











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








