事情起因是震惊全国大学生的1013事件!!!
刚好看到社团群里在讨论这个,于是就发挥专业特长分析一下

拿到apk ,第一步肯定先放到虚拟机里跑一下看下效果
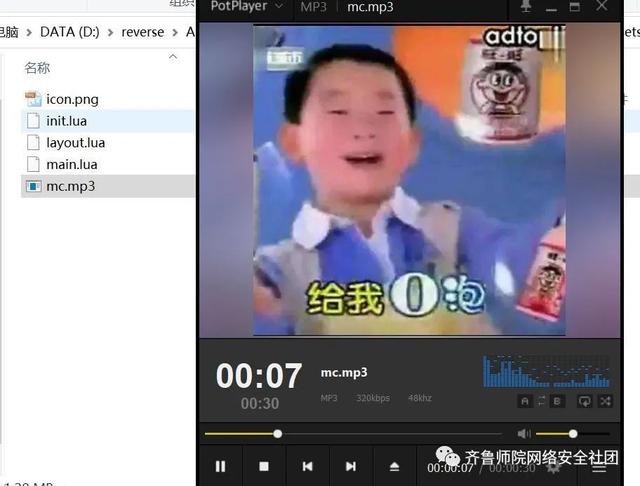
emmm这似曾相识的页面,这熟悉的音量,唯一变化的就是音乐变成了O泡果奶的魔性洗脑广告。
懂了,这不就是 "送给最好的ta.apk" 吗?

使用Android killer或apk改之理分析一下,这里使用Android Killer:
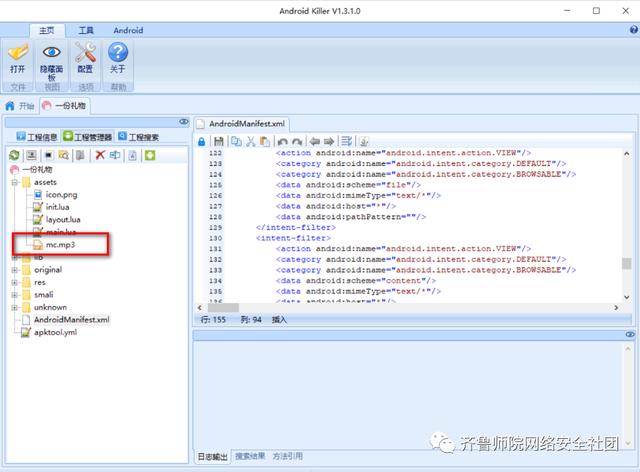
通过对比送给最好的ta.apk发现:
多了一个layout.lua文件,不过从名字上看这就是个布局文件,影响不大,再就是mp3文件名字从原来的0.mp3改为了mc.mp3,其他的都没变,甚至软件图标都没变。这个mc.mp3就是播放的广告音频了。

剩下的就简单了,虽然lua文件是加密过的,通过分析java代码,发现加密方式也没变,依旧使用/lib/armeabli-v7a/libluajava.so加密,因此使用ida7.0(x32)对这个文件逆向分析:
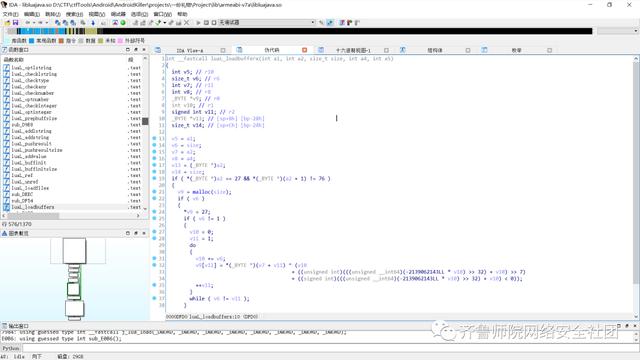
查找到在luaL.loadbufferx里面有对文件解密的过程
这里直接拿pcat大佬写的解密脚本:
from ctypes import *import sysdef decrypt(filename): s = open(filename, 'rb').read() outfile = 'out.lua' if s[0] == chr(0x1b) and s[1] != chr(0x4c): rst = chr(0x1b) size = len(s) v10 = 0 for i in range(1, size): v10 += size v = (c_ulonglong(-2139062143 * v10).value >> 32) + v10 v1 = c_uint(v).value >> 7 v2 = c_int(v).value < 0 rst += chr(ord(s[i]) ^ (v10 + v1 + v2) & 0xff) with open(outfile, 'wb') as f: f.write(rst) else: passdef foo(): print len(sys.argv) if len(sys.argv) == 2: filename = sys.argv[1] else: filename = 'main.lua' decrypt(filename)if __name__ == '__main__': foo()将得到的文件使用unluac.jar进行还原,最终得到三个lua文件分别为:init.lua:local L0, L1appname = "2301431462281871829.0"appver = "9.0"packagename = "com.ta.cnm"appcode = "9"appsdk = "15"theme = "Theme_DeviceDefault_Light_NoActionBar"L0 = {}L1 = "WRITE_EXTERNAL_STORAGE"L0[1] = L1user_permission = L0main.lua:
local L0, L1, L2, L3L0 = requireL1 = "import"L0(L1)L0 = importL1 = "android.app.*"L0(L1)L0 = importL1 = "android.os.*"L0(L1)L0 = importL1 = "android.widget.*"L0(L1)L0 = importL1 = "android.view.*"L0(L1)L0 = importL1 = "android.view.View"L0(L1)L0 = importL1 = "android.content.Context"L0(L1)L0 = importL1 = "android.media.MediaPlayer"L0(L1)L0 = importL1 = "android.media.AudioManager"L0(L1)L0 = importL1 = "com.androlua.Ticker"L0(L1)L0 = activityL0 = L0.getSystemServiceL1 = ContextL1 = L1.AUDIO_SERVICEL0 = L0(L1)L0 = L0.setStreamVolumeL1 = AudioManagerL1 = L1.STREAM_MUSICL2 = 15L3 = AudioManagerL3 = L3.FLAG_SHOW_UIL0(L1, L2, L3)L0 = activityL0 = L0.getDecorViewL0 = L0()L0 = L0.setSystemUiVisibilityL1 = ViewL1 = L1.SYSTEM_UI_FLAG_HIDE_NAVIGATIONL2 = ViewL2 = L2.SYSTEM_UI_FLAG_IMMERSIVEL1 = L1 | L2L0(L1)L0 = MediaPlayerL0 = L0()m = L0L0 = mL0 = L0.resetL0()L0 = mL0 = L0.setDataSourceL1 = activityL1 = L1.getLuaDirL1 = L1()L2 = "/mc.mp3"L1 = L1 .. L2L0(L1)L0 = mL0 = L0.prepareL0()L0 = mL0 = L0.startL0()L0 = mL0 = L0.setLoopingL1 = trueL0(L1)L0 = TickerL0 = L0()ti = L0L0 = tiL0.Period = 10L0 = tifunction L1() local L0, L1, L2, L3 L0 = activity L0 = L0.getSystemService L1 = Context L1 = L1.AUDIO_SERVICE L0 = L0(L1) L0 = L0.setStreamVolume L1 = AudioManager L1 = L1.STREAM_MUSIC L2 = 15 L3 = AudioManager L3 = L3.FLAG_SHOW_UI L0(L1, L2, L3) L0 = activity L0 = L0.getDecorView L0 = L0() L0 = L0.setSystemUiVisibility L1 = View L1 = L1.SYSTEM_UI_FLAG_HIDE_NAVIGATION L2 = View L2 = L2.SYSTEM_UI_FLAG_IMMERSIVE L1 = L1 | L2 L0(L1)endL0.onTick = L1L0 = tiL0 = L0.startL0()function L0(A0, A1) local L2, L3, L4, L5 L2 = string L2 = L2.find L3 = tostring L4 = A1 L3 = L3(L4) L4 = "KEYCODE_BACK" L2 = L2(L3, L4) if L2 ~= nil then L2 = activity L2 = L2.getSystemService L3 = Context L3 = L3.AUDIO_SERVICE L2 = L2(L3) L2 = L2.setStreamVolume L3 = AudioManager L3 = L3.STREAM_MUSIC L4 = 15 L5 = AudioManager L5 = L5.FLAG_SHOW_UI L2(L3, L4, L5) end L2 = true return L2endonKeyDown = L0layout.lua:
local L0, L1, L2, L3L0 = {}L1 = LinearLayoutL0.layout_width = "fill"L0.layout_height = "fill"L2 = {}L3 = ButtonL2.textColor = "#D50000"L2.text = "230131138228184141230131138229150156 230132143228184141230132143229164150"L2.layout_height = "match_parent"L2.layout_width = "match_parent"L2.background = "#88888888"L2[1] = L3L0[1] = L1L0[2] = L2return L0分析这三个文件:
init.lua: 定义了app的名字,版本(已经是9.0了吗),包名(有点暴躁啊这位老哥),sdk版本,使用的主题,需要的权限等数据
main.lua: 具体逻辑都在这里面,大概就是读取mc.mp3 播放 并一直把音量调整到15(最大),监听禁用返回按钮。
layout.lua: 设置页面布局

恶搞一时爽,但是也要有度。
万一下一次是个带病毒的文件呢?
对了 解决方案-----------关掉进程或关机

文章来源:齐鲁师院网络安全社团






 本文分析了一款名为“送给最好的ta”的恶搞APP,揭示其工作原理及潜在风险。通过逆向工程发现该APP播放特定音频并屏蔽返回键,提醒用户警惕类似恶意软件。
本文分析了一款名为“送给最好的ta”的恶搞APP,揭示其工作原理及潜在风险。通过逆向工程发现该APP播放特定音频并屏蔽返回键,提醒用户警惕类似恶意软件。
















 2万+
2万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








