环境准备
:::info
实验目标:ServerA通过用户ServerB(已发送密钥和指定端口)
:::
| 主机 | IP | 身份 |
|---|
| ServerA | 192.168.10.201 | SSH客户端 |
| ServerB | 192.168.10.202 | SSH目标主机 |
在使用SSH登录远程主机时,指定的用户名是指远程主机上的用户。命令格式如下:
这里的 username 是指您打算用来登录远程目标主机的用户名,这个用户必须存在于远程目标主机的系统中,并且具有相应的访问权限。remote_host 则代表您想要连接的远程服务器的IP地址或域名。
举例来说,如果您要使用名为 myuser 的用户账户登录IP地址为 192.168.0.100 的远程服务器,命令应写作:
在这个命令中:
myuser 是您指定的用户名,对应的是远程服务器上已经存在的用户账户。
192.168.0.100 是远程主机的IP地址
执行此命令后,SSH客户端会尝试使用您本机当前用户的公钥(如果有已配置的密钥对认证)或提示您输入 myuser 账户在远程主机上的密码来进行身份验证。一旦身份验证成功,您将获得 myuser 用户在远程服务器上的 shell 终端会话。
总结来说,通过SSH登录远程主机时指定的用户名是指远程主机上的用户,而不是本机用户。本机用户的信息仅用于确定本地的SSH客户端配置(如私钥位置)以及可能的代理转发设置等,但实际登录远程服务器时的身份是由您提供的远程用户名决定的。
禁止root登录
root登录测试
|
| [root@ServerA ~] |
|
| Activate the web console with: systemctl enable --now cockpit.socket |
|
| |
|
| This system is not registered to Red Hat Insights. See https://cloud.redhat.com/ |
|
| To register this system, run: insights-client --register |
|
| |
|
| Last failed login: Thu Apr 18 03:59:14 EDT 2024 from 192.168.10.201 on ssh:notty |
|
| There was 1 failed login attempt since the last successful login. |
|
| Last login: Thu Apr 18 03:56:51 2024 from 192.168.10.201 |
|
| [root@ServerB ~] |
取消注释改为no
(如果不注销配置则无法生效)

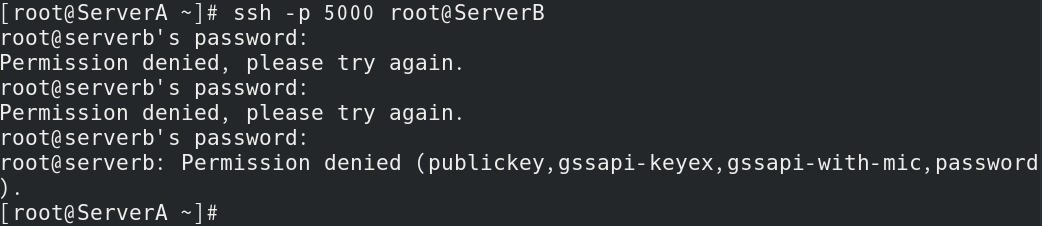
root用户测试
|
| [root@ServerA ~] |
|
| root@serverb's password: |
|
| Permission denied, please try again. |
|
| root@serverb's password: |
|
| Permission denied, please try again. |
|
| root@serverb's password: |
|
| root@serverb: Permission denied (publickey,gssapi-keyex,gssapi-with-mic,password). |
|
| |
允许禁止某用户登录
远程主机创建用户
|
| [root@Serverb ~] |
|
| [root@Serverb ~] |
|
| 更改用户 zhangsan 的密码 。 |
|
| 新的 密码: |
|
| 无效的密码: 密码是一个回文 |
|
| 重新输入新的 密码: |
|
| passwd:所有的身份验证令牌已经成功更新。 |
|
| [root@Serverb ~] |
|
| [root@Serverb ~] |
|
| 更改用户 lisi 的密码 。 |
|
| 新的 密码: |
|
| 无效的密码: 密码是一个回文 |
|
| 重新输入新的 密码: |
|
| passwd:所有的身份验证令牌已经成功更新。 |
两个用户都可以远程登录
|
| [root@servera ~] |
|
| zhangsan@serverb's password: |
|
| Last login: Fri Jul 12 14:33:34 2024 from servera |
|
| [zhangsan@serverb ~]$ exit |
|
| logout |
|
| Connection to serverb closed. |
|
| [root@servera ~]# ssh lisi@ServerB -p 5000 |
|
| lisi@serverb's password: |
|
| Last login: Fri Jul 12 11:24:26 2024 from servera |
|
| [lisi@serverb ~]$ exit |
|
| logout |
|
| Connection to serverb closed. |
|
| [root@servera ~] |
底部添加参数允许zhangsan拒绝lisi
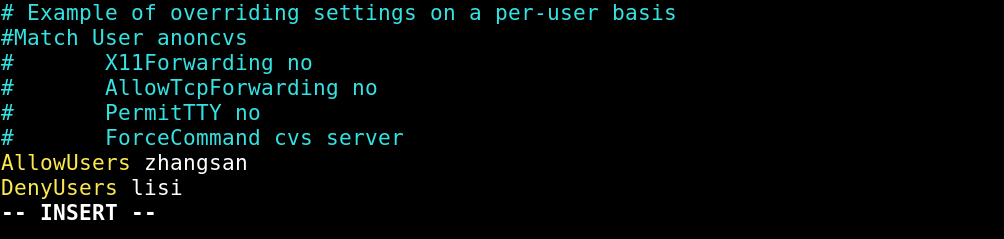
|
| [root@Serverb ~] |
|
| [root@Serverb ~] |
|
| [root@Serverb ~] |
|
| |
|
| AllowUsers zhangsan |
|
| DenyUsers lisi |
|
| [root@Serverb ~] |
测试登录
张三允许登录
|
| [root@servera ~] |
|
| zhangsan@serverb's password: |
|
| Last login: Fri Jul 12 14:42:10 2024 from servera |
|
| [zhangsan@serverb ~]$ exit |
|
| logout |
|
| Connection to serverb closed. |
|
| |
李四禁止登录
|
| [root@servera ~] |
|
| lisi@serverb's password: |
|
| Permission denied, please try again. |
|
| lisi@serverb's password: |
|
| Permission denied, please try again. |
|
| lisi@serverb's password: |
|
| |
Pam模块禁止用户
ServerB
只允许李四登录
|
| [root@serverb ~]# echo "lisi" | sudo tee /etc/ssh/allowed_users |
|
| lisi |
|
| [root@serverb ~]# cat /etc/ssh/allowed_users |
|
| lisirverB ~]# chmod 644 /etc/ssh/allowed_users |
|
| [root@Serverb ~]# systemctl restart sshd.service |
|
| [root@Serverb ~]# tail -n 1 /etc/ssh/sshd_config |
|
| # ForceCommand cvs server |
|
| [root@Serverb ~]# tail -n 1 /etc/pam.d/sshd |
|
| auth required pam_listfile.so item=user sense=allow onerr=fail file=/etc/ssh/allowed_users |
张三禁止登录
|
| [root@servera ~]# ssh zhangsan@ServerB -p 5000 |
|
| zhangsan@serverb's password: |
|
| Permission denied, please try again. |
|
| zhangsan@serverb's password: |
|
| Permission denied, please try again. |
|
| zhangsan@serverb's password: |
|
| Permission denied (publickey,gssapi-keyex,gssapi-with-mic,password). |
|
| |
李四可登录
|
| [root@servera ~]# ssh lisi@ServerB -p 5000 |
|
| lisi@serverb's password: |
|
| Last login: Fri Jul 12 14:50:03 2024 from servera |
Match User模块
ServerB
使用模块禁止李四
|
| [root@ServerB ~]# vim /etc/ssh/sshd_config |
|
| [root@ServerB ~]# tail -n 6 /etc/ssh/sshd_config |
|
| # AllowTcpForwarding no |
|
| # PermitTTY no |
|
| # ForceCommand cvs server |
|
| Match User lisi |
|
| PermitTTY no |
|
| ForceCommand /bin/false |
|
| [root@ServerB ~]# systemctl restart sshd.service |
这里,PermitTTY no禁止分配伪终端,ForceCommand /bin/false设置了一个无效的命令,确保用户无法成功登录。
ServerA
张三用户可登录
|
| [root@servera ~]# ssh zhangsan@ServerB -p 5000 |
|
| zhangsan@serverb's password: |
|
| Last login: Fri Jul 12 15:01:09 2024 from servera |
|
| [zhangsan@serverb ~]$ exit |
|
| logout |
|
| Connection to serverb closed. |
李四用户不可登录
|
| [root@servera ~]# ssh lisi@ServerB -p 5000 |
|
| lisi@serverb's password: |
|
| PTY allocation request failed on channel 0 |
|
| Connection to serverb closed. |
指定其他用户免密登录
ServerA
Server通过指定端口将密钥发送到对应用户文件夹下
|
| [root@servera ~]# ssh-copy-id -i .ssh/id_rsa.pub -p 5000 zhangsan@ServerB |
|
| /usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: ".ssh/id_rsa.pub" |
|
| /usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed |
|
| /usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys |
|
| zhangsan@serverb's password: |
|
| |
|
| Number of key(s) added: 1 |
|
| |
|
| Now try logging into the machine, with: "ssh -p '5000' 'zhangsan@ServerB'" |
|
| and check to make sure that only the key(s) you wanted were added. |
|
| |
ServerB
|
| [root@ServerB ~]# systemctl restart sshd.service |
|
| [root@ServerB ~]# ll /home/zhangsan/.ssh/ |
|
| 总用量 4 |
|
| -rw-------. 1 zhangsan zhangsan 580 4月 18 04:35 authorized_keys |
|
| [root@ServerB ~]# |
ServerA登录
|
| [root@servera ~]# ssh zhangsan@ServerB -p 5000 |
|
| Last login: Fri Jul 12 15:05:21 2024 from servera |
|
| [zhangsan@serverb ~]$ exit |
|
| logout |
|
| Connection to serverb closed. |
禁止密码登录
|
| PasswordAuthentication no |
密码登录测试与免密测试
|
| [root@servera ~]# ssh lisi@ServerB -p 5000 |
|
| Permission denied (publickey,gssapi-keyex,gssapi-with-mic). |
|
| [root@servera ~]# ssh zhangsan@ServerB -p 5000 |
|
| Last login: Fri Jul 12 15:06:25 2024 from servera |
|
| [zhangsan@serverb ~]$ exit |
|
| logout |
|
| Connection to serverb closed. |
|
| |
指定用户和IP登录
|
| AllowUsers zhangsan@192.168.10.201 |
拒绝登录
|
| [root@localhost ~]# ifconfig ens160 |
|
| ens160: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 |
|
| inet 192.168.10.128 netmask 255.255.255.0 broadcast 192.168.10.255 |
|
| inet6 fe80::3429:206b:def4:69f2 prefixlen 64 scopeid 0x20<link> |
|
| ether 00:0c:29:be:62:ce txqueuelen 1000 (Ethernet) |
|
| RX packets 1453 bytes 1745198 (1.6 MiB) |
|
| RX errors 0 dropped 0 overruns 0 frame 0 |
|
| TX packets 859 bytes 68106 (66.5 KiB) |
|
| TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 |
|
| |
|
| [root@localhost ~]# ssh zhangsan@192.168.10.202 -p 5000 |
|
| zhangsan@192.168.10.202's password: |
|
| Permission denied, please try again. |
|
| zhangsan@192.168.10.202's password: |
|
| Permission denied, please try again. |
|
| zhangsan@192.168.10.202's password: |
允许地址登录
|
| [root@servera ~]# ifconfig ens33 |
|
| ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 |
|
| inet 192.168.10.201 netmask 255.255.255.0 broadcast 192.168.10.255 |
|
| inet6 fe80::c086:7d71:44a8:c234 prefixlen 64 scopeid 0x20<link> |
|
| ether 00:0c:29:9f:70:a6 txqueuelen 1000 (Ethernet) |
|
| RX packets 811 bytes 153103 (149.5 KiB) |
|
| RX errors 0 dropped 0 overruns 0 frame 0 |
|
| TX packets 993 bytes 212878 (207.8 KiB) |
|
| TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 |
|
| |
|
| [root@servera ~]# ssh zhangsan@ServerB -p 5000 |
|
| Last failed login: Fri Jul 12 15:58:09 CST 2024 from 192.168.10.128 on ssh:notty |
|
| There were 3 failed login attempts since the last successful login. |
|
| Last login: Fri Jul 12 15:24:32 2024 from servera |
|
| [zhangsan@serverb ~]$ |
原创作者: yuanqing09 转载于: https://www.cnblogs.com/yuanqing09/p/18308856
























 2638
2638

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








