目录
1. 前提概要
本项目通过采用目前较流行的四种框架进行整合,实现基于数据库的动态权限分配及用户认证项目,可拓展性好,开箱即用,任何涉及权限分配及角色认证的业务均可在该项目基础上直接进行业务开发!此文仅对项目的核心模块进行介绍及如何使用,其它模块类似于异常处理模块将不做介绍。
项目已上传到github:https://github.com/SmallPineApp1e/SpringBoot-Security
POM导入相关依赖
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<parent>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-parent</artifactId>
<version>2.2.4.RELEASE</version>
<relativePath/> <!-- lookup parent from repository -->
</parent>
<groupId>org.smallpineapple</groupId>
<artifactId>springboot-security</artifactId>
<version>0.0.1-SNAPSHOT</version>
<name>springboot-security</name>
<description>Demo project for Spring Boot</description>
<properties>
<java.version>1.8</java.version>
</properties>
<dependencies>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-security</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.mybatis.spring.boot</groupId>
<artifactId>mybatis-spring-boot-starter</artifactId>
<version>2.1.1</version>
</dependency>
<dependency>
<groupId>com.alibaba</groupId>
<artifactId>druid-spring-boot-starter</artifactId>
<version>1.1.21</version>
</dependency>
<dependency>
<groupId>mysql</groupId>
<artifactId>mysql-connector-java</artifactId>
<scope>runtime</scope>
<version>8.0.19</version>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
<exclusions>
<exclusion>
<groupId>org.junit.vintage</groupId>
<artifactId>junit-vintage-engine</artifactId>
</exclusion>
</exclusions>
</dependency>
<dependency>
<groupId>org.springframework.security</groupId>
<artifactId>spring-security-test</artifactId>
<scope>test</scope>
</dependency>
<dependency>
<groupId>io.jsonwebtoken</groupId>
<artifactId>jjwt</artifactId>
<version>0.9.1</version>
</dependency>
</dependencies>
<build>
<resources>
<resource>
<directory>src/main/java</directory>
<includes>
<include>**/*.xml</include>
</includes>
</resource>
<resource>
<directory>src/main/resources</directory>
</resource>
</resources>
<plugins>
<plugin>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-maven-plugin</artifactId>
</plugin>
</plugins>
</build>
</project>
2. 数据库表结构
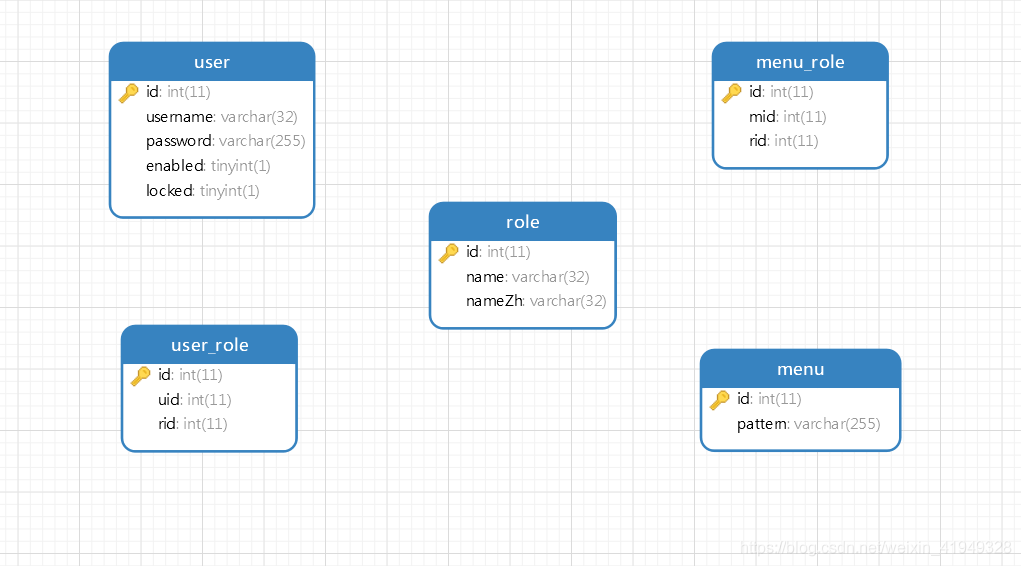
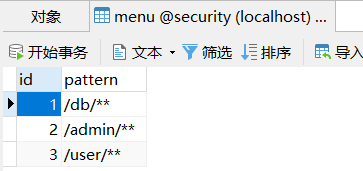
menu是请求路径规则,例如/admin/**,代表拥有admin角色的用户可以访问这一种路径规则的所有接口
/*
Navicat Premium Data Transfer
Source Server : localhost
Source Server Type : MySQL
Source Server Version : 80018
Source Host : localhost:3306
Source Schema : security
Target Server Type : MySQL
Target Server Version : 80018
File Encoding : 65001
Date: 26/02/2020 23:29:25
*/
SET NAMES utf8mb4;
SET FOREIGN_KEY_CHECKS = 0;
-- ----------------------------
-- Table structure for menu
-- ----------------------------
DROP TABLE IF EXISTS `menu`;
CREATE TABLE `menu` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`pattern` varchar(255) CHARACTER SET utf8mb4 COLLATE utf8mb4_0900_ai_ci NOT NULL COMMENT '请求路径匹配规则',
PRIMARY KEY (`id`) USING BTREE
) ENGINE = InnoDB AUTO_INCREMENT = 4 CHARACTER SET = utf8mb4 COLLATE = utf8mb4_0900_ai_ci ROW_FORMAT = Dynamic;
-- ----------------------------
-- Records of menu
-- ----------------------------
INSERT INTO `menu` VALUES (1, '/db/**');
INSERT INTO `menu` VALUES (2, '/admin/**');
INSERT INTO `menu` VALUES (3, '/user/**');
-- ----------------------------
-- Table structure for menu_role
-- ----------------------------
DROP TABLE IF EXISTS `menu_role`;
CREATE TABLE `menu_role` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`mid` int(11) NOT NULL COMMENT 'menu表外键',
`rid` int(11) NOT NULL COMMENT 'role表外键',
PRIMARY KEY (`id`) USING BTREE
) ENGINE = InnoDB AUTO_INCREMENT = 4 CHARACTER SET = utf8mb4 COLLATE = utf8mb4_0900_ai_ci ROW_FORMAT = Dynamic;
-- ----------------------------
-- Records of menu_role
-- ----------------------------
INSERT INTO `menu_role` VALUES (1, 1, 1);
INSERT INTO `menu_role` VALUES (2, 2, 2);
INSERT INTO `menu_role` VALUES (3, 3, 3);
-- ----------------------------
-- Table structure for role
-- ----------------------------
DROP TABLE IF EXISTS `role`;
CREATE TABLE `role` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`name` varchar(32) CHARACTER SET utf8 COLLATE utf8_general_ci NULL DEFAULT NULL,
`nameZh` varchar(32) CHARACTER SET utf8 COLLATE utf8_general_ci NULL DEFAULT NULL,
PRIMARY KEY (`id`) USING BTREE
) ENGINE = InnoDB AUTO_INCREMENT = 4 CHARACTER SET = utf8 COLLATE = utf8_general_ci ROW_FORMAT = Dynamic;
-- ----------------------------
-- Records of role
-- ----------------------------
INSERT INTO `role` VALUES (1, 'dba', '数据库管理员');
INSERT INTO `role` VALUES (2, 'admin', '系统管理员');
INSERT INTO `role` VALUES (3, 'user', '用户');
-- ----------------------------
-- Table structure for user
-- ----------------------------
DROP TABLE IF EXISTS `user`;
CREATE TABLE `user` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`username` varchar(32) CHARACTER SET utf8 COLLATE utf8_general_ci NULL DEFAULT NULL,
`password` varchar(255) CHARACTER SET utf8 COLLATE utf8_general_ci NULL DEFAULT NULL,
`enabled` tinyint(1) NULL DEFAULT NULL,
`locked` tinyint(1) NULL DEFAULT NULL,
PRIMARY KEY (`id`) USING BTREE
) ENGINE = InnoDB AUTO_INCREMENT = 4 CHARACTER SET = utf8 COLLATE = utf8_general_ci ROW_FORMAT = Dynamic;
-- ----------------------------
-- Records of user
-- ----------------------------
INSERT INTO `user` VALUES (1, 'root', '$2a$10$RMuFXGQ5AtH4wOvkUqyvuecpqUSeoxZYqilXzbz50dceRsga.WYiq', 1, 0);
INSERT INTO `user` VALUES (2, 'admin', '$2a$10$RMuFXGQ5AtH4wOvkUqyvuecpqUSeoxZYqilXzbz50dceRsga.WYiq', 1, 0);
INSERT INTO `user` VALUES (3, 'sang', '$2a$10$RMuFXGQ5AtH4wOvkUqyvuecpqUSeoxZYqilXzbz50dceRsga.WYiq', 1, 0);
-- ----------------------------
-- Table structure for user_role
-- ----------------------------
DROP TABLE IF EXISTS `user_role`;
CREATE TABLE `user_role` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`uid` int(11) NULL DEFAULT NULL,
`rid` int(11) NULL DEFAULT NULL,
PRIMARY KEY (`id`) USING BTREE
) ENGINE = InnoDB AUTO_INCREMENT = 5 CHARACTER SET = utf8 COLLATE = utf8_general_ci ROW_FORMAT = Dynamic;
-- ----------------------------
-- Records of user_role
-- ----------------------------
INSERT INTO `user_role` VALUES (1, 1, 1);
INSERT INTO `user_role` VALUES (2, 1, 2);
INSERT INTO `user_role` VALUES (3, 2, 2);
INSERT INTO `user_role` VALUES (4, 3, 3);
SET FOREIGN_KEY_CHECKS = 1;
3. 项目结构
4. 编写实体类
User类:
需要实现UserDetails接口,用于SpringSecurity的用户状态认证(登录用户名密码、用户是否锁定、用户账号是否可用.....)
/**
* @author Zeng
* @date 2020/2/24 22:27
*/
public class User implements UserDetails {
private Integer id;
private String username;
private String password;
private Boolean enabled;
private Boolean locked;
//用户具备的角色
private List<Role> roles;
//登录后返回的token
private String token;
public String getToken() {
return token;
}
public void setToken(String token) {
this.token = token;
}
public List<Role> getRoles() {
return roles;
}
public void setRoles(List<Role> roles) {
this.roles = roles;
}
public Integer getId() {
return id;
}
public void setId(Integer id) {
this.id = id;
}
@Override
public String getUsername() {
return username;
}
//账户是否未过期
@Override
public boolean isAccountNonExpired() {
return true;
}
//账户是否未锁定
@Override
public boolean isAccountNonLocked() {
return !locked;
}
//账户密码是否未过期
@Override
public boolean isCredentialsNonExpired() {
return true;
}
public void setUsername(String username) {
this.username = username;
}
//获取用户的角色
@Override
public Collection<? extends GrantedAuthority> getAuthorities() {
List<SimpleGrantedAuthority> list = new ArrayList<>(roles.size());
roles.forEach(role -> {
list.add(new SimpleGrantedAuthority(role.getName()));
});
return list;
}
@Override
public String getPassword() {
return password;
}
public void setPassword(String password) {
this.password = password;
}
@Override
public boolean isEnabled() {
return enabled;
}
public void setEnabled(Boolean enabled) {
this.enabled = enabled;
}
public Boolean getLocked() {
return locked;
}
public void setLocked(Boolean locked) {
this.locked = locked;
}
}Role类:
package org.smallpineapple.springbootsecurity.bean;
/**
* @author Zeng
* @date 2020/2/24 22:32
*/
public class Role {
private Integer id;
private String name;
private String nameZh;
public Integer getId() {
return id;
}
public void setId(Integer id) {
this.id = id;
}
public String getName() {
return name;
}
public void setName(String name) {
this.name = name;
}
public String getNameZh() {
return nameZh;
}
public void setNameZh(String nameZh) {
this.nameZh = nameZh;
}
}
Menu类:
/**
* @author Zeng
* @date 2020/2/24 22:32
*/
public class Menu {
private Integer id;
private String pattern;
//当前路径需要具备的角色
private List<Role> roles;
public List<Role> getRoles() {
return roles;
}
public void setRoles(List<Role> roles) {
this.roles = roles;
}
public Integer getId() {
return id;
}
public void setId(Integer id) {
this.id = id;
}
public String getPattern() {
return pattern;
}
public void setPattern(String pattern) {
this.pattern = pattern;
}
}
4. 核心配置类SecurityConfig
该类负责注册有关权限控制和用户登录校验的类
/**
* @author Zeng
* @date 2020/2/24 22:52
*/
@Configuration
public class SecurityConfig extends WebSecurityConfigurerAdapter {
@Autowired
UserService userService;
@Autowired
MyFilter myFilter;
@Autowired
CustomAccessDecisionManager customAccessDecisionManager;
//使用的密码加密方式
@Bean
PasswordEncoder passwordEncoder() {
return new BCryptPasswordEncoder();
}
//注册登录认证方法
@Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception {
auth.userDetailsService(userService);
}
//配置登录及注销及权限配置
@Override
protected void configure(HttpSecurity http) throws Exception {
http.authorizeRequests()
//注册MyFilter和customAccessDecisionManager进行权限管理
.withObjectPostProcessor(new ObjectPostProcessor<FilterSecurityInterceptor>() {
@Override
public <O extends FilterSecurityInterceptor> O postProcess(O o) {
o.setAccessDecisionManager(customAccessDecisionManager);
o.setSecurityMetadataSource(myFilter);
return o;
}
})
//路径为“/doLogin”的POST请求自动放行
.antMatchers(HttpMethod.POST, "/doLogin")
.permitAll()
//其它请求都需要认证
.anyRequest().authenticated()
.and()
//添加登录的过滤器,当请求路径为"/doLogin"时该过滤器截取请求
.addFilterBefore(new JwtLoginFilter("/doLogin",
authenticationManager()), UsernamePasswordAuthenticationFilter.class)
//添加token校验的过滤器,每次发起请求都被该过滤器截取判断是否登录
.addFilterBefore(new JwtFilter(), UsernamePasswordAuthenticationFilter.class)
.csrf().disable();
}
}
5. 登录认证
定义JwtLoginFilter类,用户登录时会被该过滤器截取下来,defaultFilterProcessesUrl代表登录的请求路径,如果定义为“/doLogin”时,用户请求登录"/doLogin"将会来到该过滤器的attemptAuthentication()方法进行用户名和密码的校验,如果校验成功则会生成token返回给客户端
/**
* @author Zeng
* @date 2020/2/25 11:16
*/
public class JwtLoginFilter extends AbstractAuthenticationProcessingFilter {
public JwtLoginFilter(String defaultFilterProcessesUrl, AuthenticationManager authenticationManager) {
super(new AntPathRequestMatcher(defaultFilterProcessesUrl));
setAuthenticationManager(authenticationManager);
}
/**
* 从登录参数中提取出用户名密码, 然后调用 AuthenticationManager.authenticate() 方法去进行自动校验
* @param req
* @param resp
* @return
* @throws AuthenticationException
* @throws IOException
* @throws ServletException
*/
@Override
public Authentication attemptAuthentication(HttpServletRequest req, HttpServletResponse resp) throws AuthenticationException, IOException, ServletException {
String username = req.getParameter("username");
String password = req.getParameter("password");
UsernamePasswordAuthenticationToken token = new UsernamePasswordAuthenticationToken(username, password);
return getAuthenticationManager().authenticate(token);
}
/**
* 校验成功的回调函数,生成jwt的token
* @param req
* @param resp
* @param chain
* @param authResult
* @throws IOException
* @throws ServletException
*/
@Override
protected void successfulAuthentication(HttpServletRequest req, HttpServletResponse resp, FilterChain chain, Authentication authResult) throws IOException, ServletException {
Collection<? extends GrantedAuthority> authorities = authResult.getAuthorities();
StringBuffer roles = new StringBuffer();
//遍历用户角色,将其写入jwt中,注意角色之间以逗号分隔,是一种规范
for (GrantedAuthority authority : authorities) {
roles.append(authority.getAuthority())
.append(",");
}
String jwt = Jwts.builder()
.claim("authorities", roles)//配置用户角色
.setSubject(authResult.getName())//设置jwt的主题为用户的用户名
.setExpiration(new Date(System.currentTimeMillis() + 10 * 60 * 1000))//设置过期时间为10分钟
.signWith(SignatureAlgorithm.HS512,"turing-team") //使用密钥对头部和载荷进行签名
.compact();//生成jwt
//返回给前端
resp.setContentType("application/json;charset=utf-8");
PrintWriter out = resp.getWriter();
User user = (User) authResult.getPrincipal();
user.setToken(jwt);
JsonResultUtil jsonResultUtil = JsonResultUtil.success("登录成功", user);
System.out.println(jsonResultUtil.toString());
out.write(new ObjectMapper().writeValueAsString(jsonResultUtil));
out.flush();
out.close();
}
/**
* 校验失败的回调函数
* @param req
* @param resp
* @param failed
* @throws IOException
* @throws ServletException
*/
@Override
protected void unsuccessfulAuthentication(HttpServletRequest req, HttpServletResponse resp, AuthenticationException failed) throws IOException, ServletException {
resp.setContentType("application/json;charset=utf-8");
PrintWriter out = resp.getWriter();
JsonResultUtil failure = JsonResultUtil.failure("用户名或密码错误,请重新登录!", null);
out.write(new ObjectMapper().writeValueAsString(failure));
out.flush();
out.close();
}
}6. 验证token过滤器
/**
* @author Zeng
* @date 2020/2/25 11:43
* 用户携带的token是否有效
*/
public class JwtFilter extends GenericFilterBean {
@Override
public void doFilter(ServletRequest servletRequest, ServletResponse servletResponse, FilterChain filterChain) throws IOException, ServletException {
HttpServletRequest req = (HttpServletRequest) servletRequest;
HttpServletResponse resp = (HttpServletResponse) servletResponse;
//获取token
String cliToken = req.getHeader("token");
PrintWriter pw;
if("".equals(cliToken) || cliToken == null){
pw = resp.getWriter();
resp.setContentType("application/json;charset=utf-8");
JsonResultUtil jsonResult = JsonResultUtil.failure("必须传递用户的认证信息", null);
pw.write(new ObjectMapper().writeValueAsString(jsonResult));
pw.flush();
pw.close();
return ;
}
//解析token
Jws<Claims> jws;
try {
jws = Jwts.parser()
.setSigningKey("turing-team") //设置生成jwt时使用的密钥
.parseClaimsJws(cliToken);
}catch (JwtException ex){
pw = resp.getWriter();
resp.setContentType("application/json;charset=utf-8");
JsonResultUtil jsonResult = JsonResultUtil.failure("登录已过期,请重新登陆", null);
pw.write(new ObjectMapper().writeValueAsString(jsonResult));
pw.flush();
pw.close();
return ;
}
Claims claims = jws.getBody();
//获取用户的用户名,在生成token时指定了主题为用户名
String username = claims.getSubject();
//获取用户的所有角色,以逗号分割的字符串
String authoritiesStr = (String) claims.get("authorities");
//转成用户的所有角色对象,如果是以逗号分隔则可以自动转换为GrantedAuthority对象
List<GrantedAuthority> authorities = AuthorityUtils.commaSeparatedStringToAuthorityList(authoritiesStr);
//对用户进行校验
UsernamePasswordAuthenticationToken token = new UsernamePasswordAuthenticationToken(username, null, authorities);
SecurityContextHolder.getContext().setAuthentication(token);
//放行
filterChain.doFilter(servletRequest, servletResponse);
}
}7. 获取请求路径所需角色过滤器
/**
* @author Zeng
* @date 2020/2/24 23:05
* 定义过滤器,分析出用户的请求地址匹配逻辑并分析出需要哪些角色
*/
@Component
public class MyPermissionFilter implements FilterInvocationSecurityMetadataSource {
//路径匹配类,用于检查用户的请求路径是否与数据库中某个路径规则匹配
AntPathMatcher antPathMatcher = new AntPathMatcher();
@Autowired
MenuService menuService;
//每次用户发出请求都会先进入该方法,分析出该请求地址需要哪些角色
@Override
public Collection<ConfigAttribute> getAttributes(Object o) throws IllegalArgumentException {
//强转对象
FilterInvocation filterInvocation = (FilterInvocation) o;
//获取用户请求地址
String requestUrl = filterInvocation.getRequestUrl();
//获取所有路径规则
List<Menu> menus = menuService.findAllMenusWithRoles();
//遍历路径规则
for (Menu menu : menus) {
//判断与哪一条路由规则匹配
if(antPathMatcher.match(menu.getPattern(), requestUrl)){
//获取访问该路径所需要的所有角色
List<Role> roles = menu.getRoles();
//转化为返回值类型
String[] rolesStr = new String[roles.size()];
for (int i = 0; i < rolesStr.length; i++) {
rolesStr[i] = roles.get(i).getName();
}
return SecurityConfig.createList(rolesStr);
}
}
//全部都匹配不上,则返回一个默认的标识符,表示该路径是登录后就可以访问的路径
return SecurityConfig.createList("ROLE_login");
}
@Override
public Collection<ConfigAttribute> getAllConfigAttributes() {
return null;
}
//是否支持该方式,返回true
@Override
public boolean supports(Class<?> aClass) {
return true;
}
}8. 用户权限验证
/**
* @author Zeng
* @date 2020/2/24 23:33
* 判断请求当前用户具有哪些角色,如果用户具备访问路径须具备的角色则允许访问,否则判为非法请求
*/
@Component
public class CustomAccessDecisionManager implements AccessDecisionManager {
/**
* 核心方法,判断用户是否可以有权限访问该路径
* @param authentication 可以获取登录的用户信息
* @param o 实际是FilterInvocation对象,可以获取请求路径
* @param collection 访问该路径所需要的角色,是MyFilter中的返回值
* @throws AccessDeniedException 非法请求,权限不够
* @throws InsufficientAuthenticationException
*/
@Override
public void decide(Authentication authentication, Object o, Collection<ConfigAttribute> collection) throws AccessDeniedException, InsufficientAuthenticationException {
//遍历访问该路径所需要的所有角色名字
for (ConfigAttribute configAttribute : collection) {
//如果返回是登录后可访问,则判断用户是否登录
if("ROLE_login".equals(configAttribute.getAttribute())){
//AnonymousAuthenticationToken为匿名访问,则不允许访问
if(authentication instanceof AnonymousAuthenticationToken){
throw new AccessDeniedException("尚未登录,请前往登录!");
}
return ;
}
//获取当前用户所具有的所有角色
Collection<? extends GrantedAuthority> authorities = authentication.getAuthorities();
//遍历该用户的所有角色并判断是否具有必须具备的角色
for (GrantedAuthority authority : authorities) {
if(authority.getAuthority().equals(configAttribute.getAttribute())){
return ;
}
}
}
throw new AccessDeniedException("权限不足,请联系管理员!");
}
@Override
public boolean supports(ConfigAttribute configAttribute) {
return true;
}
@Override
public boolean supports(Class<?> aClass) {
return true;
}
}9. UserService
/**
* @author Zeng
* @date 2020/2/24 22:42
*/
@Service
public class UserService implements UserDetailsService {
@Autowired
UserMapper userMapper;
@Override
public UserDetails loadUserByUsername(String s) throws UsernameNotFoundException {
User user = userMapper.loadUserByUsername(s);
if(user == null){
throw new UsernameNotFoundException("用户不存在!");
}
user.setRoles(userMapper.findRolesByUserId(user.getId()));
return user;
}
}10. HelloController
/**
* @author Zeng
* @date 2020/2/24 22:55
*/
@RestController
public class HelloController {
@GetMapping("/hello")
public JsonResultUtil hello(){
return JsonResultUtil.success("成功访问公共接口", null);
}
@GetMapping("/db/hello")
public JsonResultUtil db(){
return JsonResultUtil.success("成功访问dba角色的接口", null);
}
@GetMapping("/admin/hello")
public JsonResultUtil admin(){
return JsonResultUtil.success("成功访问admin角色的接口", null);
}
@GetMapping("/user/hello")
public JsonResultUtil user(){
return JsonResultUtil.success("成功访问user角色的接口", null);
}
}9. 流程解析
当用户发起非登录请求时,首先会被JwtFilter截取请求进行token有效性校验,判断用户是否处于已登录状态;若已登录接下来被MyPermissionFilter截取请求,判断该请求需要用户具备哪些角色才可以访问,然后把需要的角色封装起来传递到请求访问管理类CustomAccessDecsionManager判断用户是否具有任意一个相应的角色,如果具有则此次访问是正常地访问,否则说明该访问是非法的,不允许访问,抛出异常。
10. 接口测试
| 用户 | root | admin | sang |
|---|---|---|---|
| 角色 | admin, db | admin | user |
| 可访问接口规则 | /admin/**,/db/** | /admin/** | /user/** |
10.1 登录测试
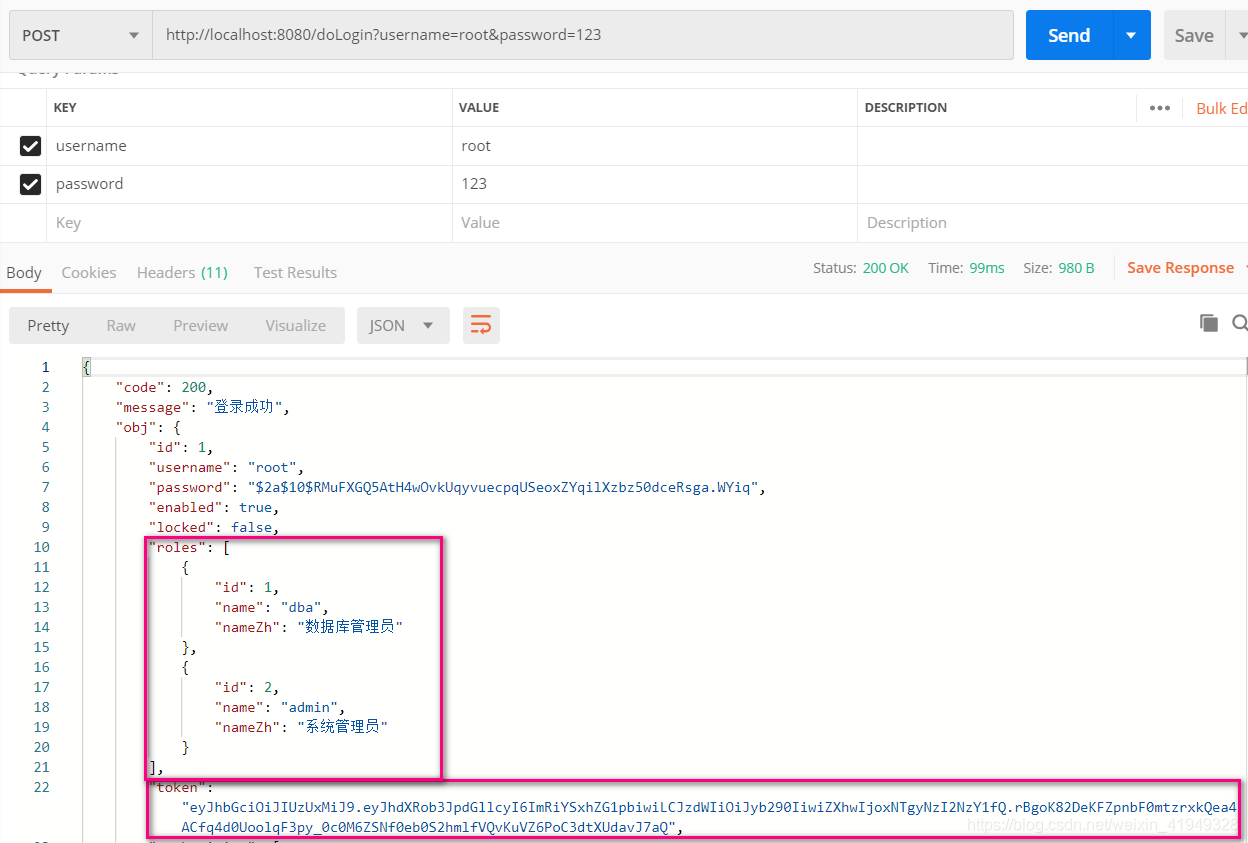
10.2 访问有权限的接口
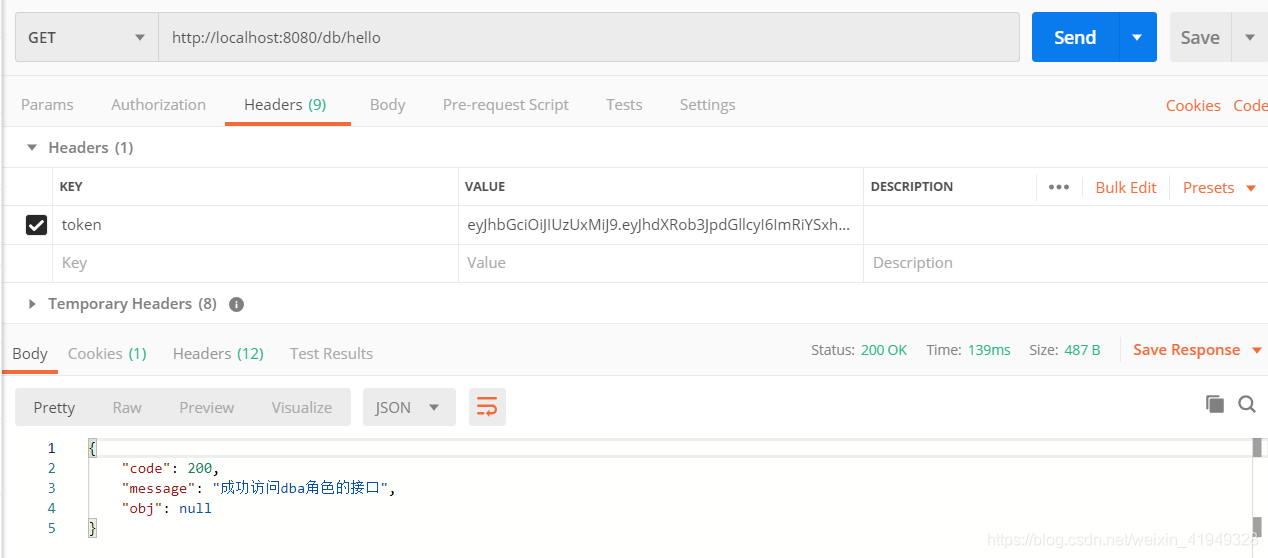
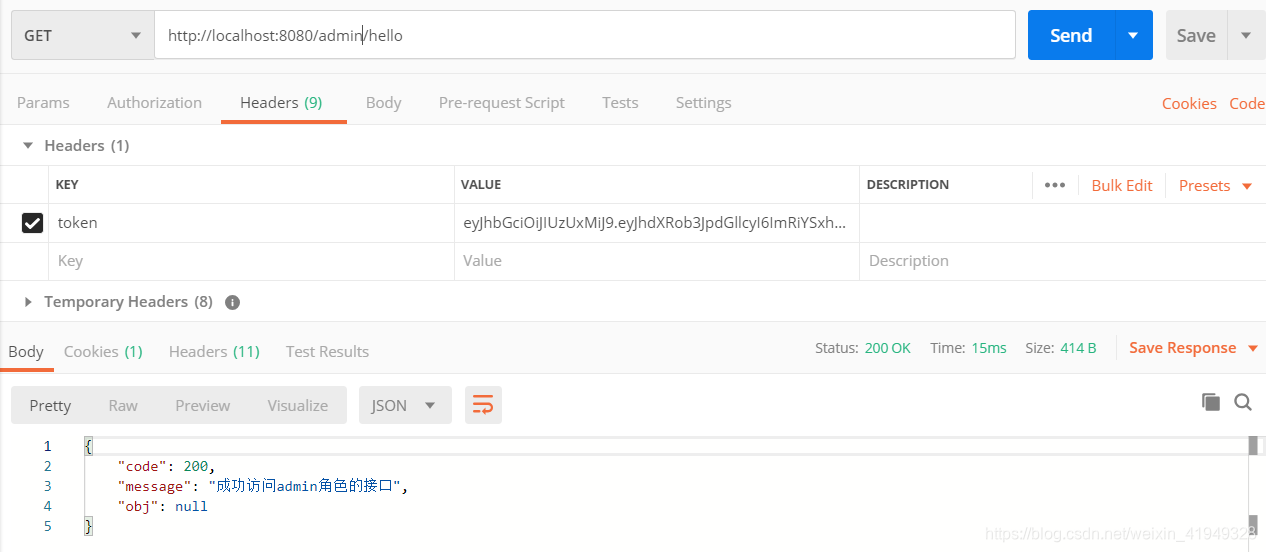
10.3 访问无权限的接口
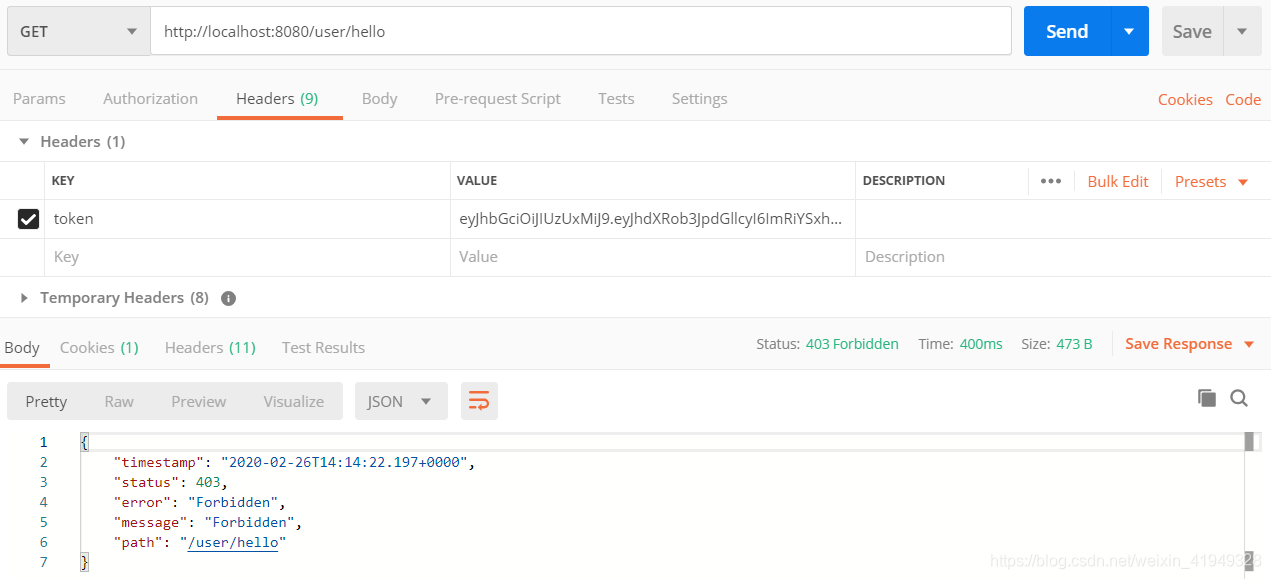
这里的异常没有处理好,可以采用统一异常处理返回友好的JSON信息给前端,可参考我的另一篇博客:SpringBoot统一异常处理
10.4 访问权限表以外的接口(登录即可访问)
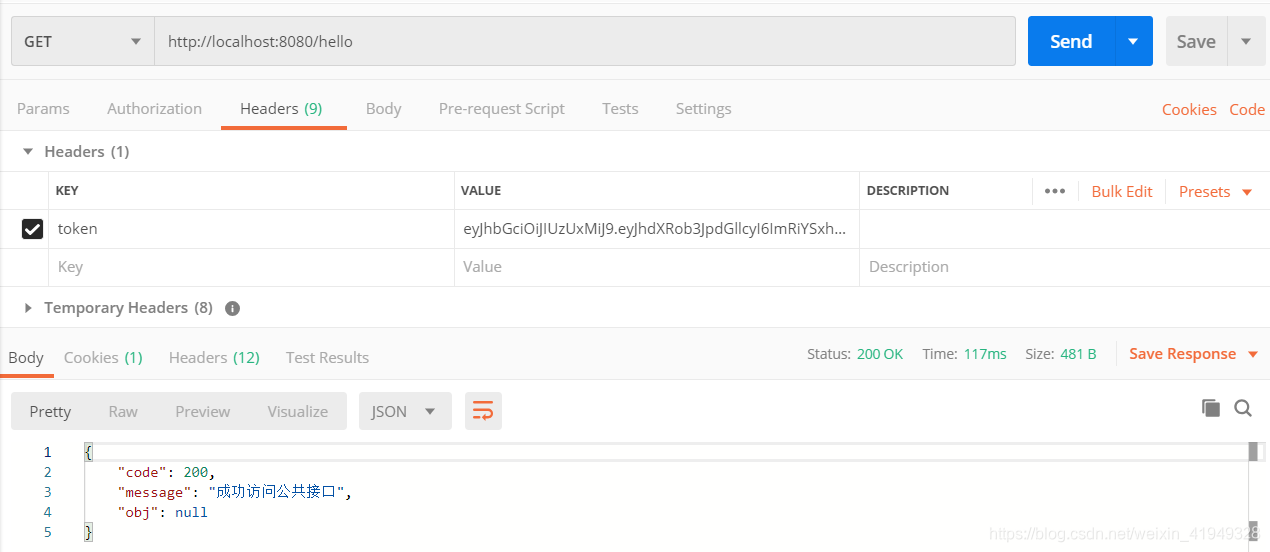
至此,整个环境已经搭建起来了,可以往上继续添加其它业务,登录模块和权限控制模块已经搭建好了,时间有限,能力有限,如果有什么错误欢迎大家指出,乐意与你们交流!






















 1068
1068











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








