声明:文章内容仅供学习参考,严禁用于商业用途,否则由此产生一切后果与作者无关,如有侵权请联系作者进行删除。

2022.04.20
前言:frida, jadx,ida,unidbg,apk版本22.03.02,由于该款软件为海外软件,故需要采用一些科学的方法才能访问和采集,但抓包工具本身也是一层代理,这不是冲突了吗,还好fiddler和charles有对应功能给我们解决这个问题,这里以fiddler为例,先打开科学上网工具,确定我们可以科学上网后,win+s寻找下internet选项中可以看到对应端口,然后回到fiddler中,设置网关,这样就能成功抓包了,解决完这些前提,正式抓包,本次分析的是登录页。



1.逻辑分析
1.1 抓包
输入要登录的账号和密码后,可抓到包如下
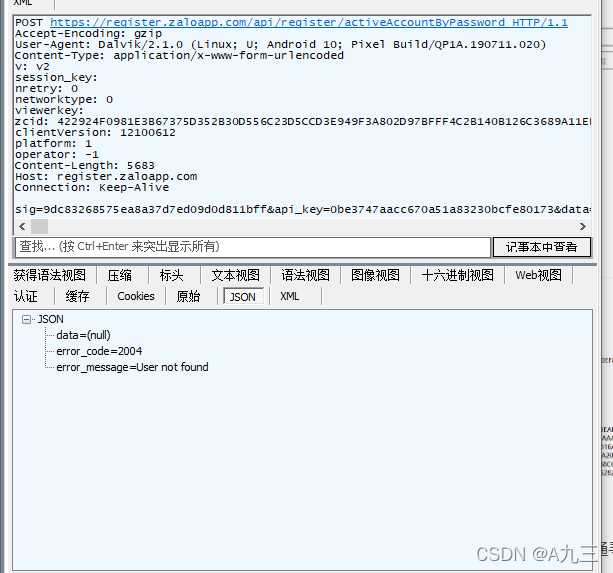

好家伙,全给加密了一点东西都看不到,上jadx直接反编译一波,一通寻找后马上可以找到,好家伙在so层;
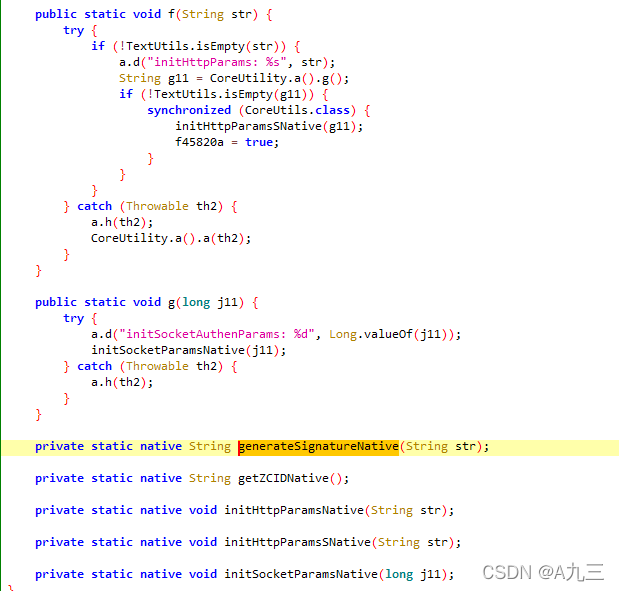
作为爬虫工程师,对这些init函数需要非常敏感,跟so层的callJniinit一般,一般会让人摸不着头脑为什么报错,这里通过对三个init函数进行hook,可以发现,当打开apk后,会走initHttpParamsSNative函数传入字段"0,unknown,Pixel,1650432878472,90c13502-db34-4166-8557-588509328e5f", 返回就是请求头中的zcid,,看起来就很像aes,这里我们保持怀疑, 这些字段其实就代表了设备信息,一台设备肯定就接受不了太多请求的狂轰滥炸;
1.2 so层定位
那是动态注册还是静态注册呢,在哪个so呢,比起System.loadLibrary,这时候我想到了前辈们造的轮子
yang神的:hook_RegisterNatives.js
上frida运行一波

找不到,那就极大可能是静态注册,接着利用一个骚操作,就是 frida-trace -FU -i “Java_com_*”

可以看到当我们操作后,点击手机后,会生成一个临时文件,这时候就可以惊喜的发现,简简单单,libnative_utils就是我们定位到的so文件,舒服。

2. so层分析
2.1 initHttpParamsSNative
我们通过firda hook java层 generateSignatureNative的入参和结果
initHttpParamsSNative arg1: 0,unknown,Pixel,1650432878472,90c13502-db34-4166-8557-588509328e5f

这里能看到这个软件还是很友好哈,进到sub_13324中,对可疑的函数下断点

对于so层的分析,往往需要去分析某些函数的入参和结果,有好几种方式,这里上unidbg;
首先先使用frida或objection去截取入参,然后在unidbg种跑起来
package com.zalo;
import com.github.unidbg.AndroidEmulator;
import com.github.unidbg.Emulator;
import com.github.unidbg.Module;
import com.github.unidbg.file.FileResult;
import com.github.unidbg.file.IOResolver;
import com.github.unidbg.linux.android.AndroidEmulatorBuilder;
import com.github.unidbg.linux.android.AndroidResolver;
import com.github.unidbg.linux.android.dvm.*;
import com.github.unidbg.memory.Memory;
import java.io.File;
public class zalo extends AbstractJni implements IOResolver{
private final AndroidEmulator emulator;
private final Module module;
private final VM vm;
private final DvmClass NativeClass;
public zalo() {
emulator = AndroidEmulatorBuilder.for64Bit().setProcessName("com.zing.zalo").build(); // 创建模拟器实例,要模拟32位或者64位,在这里区分
final Memory memory = emulator.getMemory(); // 模拟器的内存操作接口
memory.setLibraryResolver(new AndroidResolver(23)); // 设置系统类库解析
emulator.getSyscallHandler().addIOResolver(this); //注册绑定IO重定向
vm = emulator.createDalvikVM(new File("unidbg-android/src/test/java/com/zalo/zalo.apk"));
vm.setJni(this); //设置JNI
vm.setVerbose(true); // 打印日志
DalvikModule dm = vm.loadLibrary("native_utils", true);
module = dm.getModule(); // 加载好的so对应为一个模块DAB0
emulator.attach().addBreakPoint(module.base + 0x133FC);
emulator.attach().addBreakPoint(module.base + 0x106AC);
dm.callJNI_OnLoad(emulator); // 调用JNI Onload
NativeClass = vm.resolveClass("com/zing/zalocore/utils/cryptology/CoreUtils");
}
public static void main(String[] args) {
zalo zalo = new zalo();
zalo.initHttpParamsSNative();
}
@Override
public FileResult resolve(Emulator emulator, String pathname, int oflags) {
System.out.println("访问:"+pathname);
return null;
}
public void initHttpParamsSNative(){
String arg1 = "0,unknown,Pixel,1650359262073,90c13502-db34-4166-8557-588509328e5f";
String methodSig = "initHttpParamsSNative(Ljava/lang/String;)V";
NativeClass.newObject(null).callJniMethod(emulator, methodSig, arg1);
}
@Override
public DvmObject<?> callStaticObjectMethodV(BaseVM vm, DvmClass dvmClass, String signature, VaList vaList) {
switch (signature){
case "com/zing/zalocore/CoreUtility->getAppContext()Landroid/content/Context;": {
return vm.resolveClass("android/content/Context").newObject(signature);
}
}
return super.callStaticObjectMethodV(vm, dvmClass, signature, vaList);
}
}

在0x106AC上断了下来,入参来自sub_122C4,进去一看

还有sub_F8E8, 像极了aes的密钥编排算法,马上试试,且是写死在so中的,

那么加密完的数据用来干什么呢,我们接着往下看;

大概额逻辑就是
zcid_input = '0,unknown,Pixel,1649665149902,90c13502-db34-4166-8557-588509328e5f'
zcid = '422924f0981e3b67375d352b30d556c2b1cf3643d97cf076d0e99555cf2615caf3913456d239e418a462315c83e7f8bfe8f6b2612e1b7fec42992611002c8dbca9bd41cc13508dde64217a693111b0fc'
aes_key = ''
for index in range(0, 16):
aes_key += zcid[2 * index]
v24 = (len(zcid_input) & 4294967280) + 16
v17 = 2 * v24
v18 = zcid[v17 - 1]
v19 = v17 - 3
aes_key += v18
for i in range(17, 32):
v21 = zcid[v19]
v19 -= 2
aes_key += v21
return aes_key
可以很明显看出,把加密出来的zcid的取不同的位数组成一个新32字段的值放在固定的地址中,为什么这么做呢,有经验的人已经猜出来了,至此,initHttpParamsSNative函数我们就分析完了。
2.2 generateSignatureNative
为加密参数sig的加密

果然友好,硕大的MD5Update;
我们通过firda hook java层 generateSignatureNative的入参和结果
generateSignatureNative arg1: api_key=0be3747aacc670a51a83230bcfe80173data=0874802BBFDAF1526FCEEA1875D7BCC14971103443E613EAB63AA893F1838FB44D3BFC477ACAEE03CB0A3807E23DBDEBC05CE17634AA6933E2A37FFF50160C1A4EC120FC71F32A08A6D94200B5BCDDE8B1E62CD123C2D3CE26EBC930A1D6F40E4819FD81DCCFCB0A527A907FCDDB17FBCEC941963656FCA2F50AE95050FE0624F334C597D7EE151E7F62390CEBFC1DDDF9EAC7707D8D663B67C05A9352C691C9BB4C33B050D1372FBD18B1C86BCEAA478DE2018B4159C09B1B83A5BF4FD12A2EF4B39766517E2D6A358BDEDA33FB719692EBE3F1DD57C829C1E072127D614851B3604A1FA32CAD86D23CCE042CAABE834E3D0A7BD6666B818E12DA033527480854BF6DF0FA2957BC57A0C3E31D79177990B25A28C43BC573084ACE48D7596CD5461C686363A1F842B8A174697026D9D42654C7E46F41FE352A5EBDB0F22CD0A558BAB4CAB1030F8926558B73D20BD9DE8FF4B777E4A446A2E7CE8A2C342F9E1802AC3F2C4C087615B5B71B419B08030F6E2D82C1869240D5DD8356A5FA20AEB2BA2CDC400E5069E59E516481BD66CCCC2C9F857642861E4CE1EEB452AD84C589B324F90F3BC6869C264EC25C754FCD9A3063BEFD917D40B2023224975F33B897664A2C75E3AB7D51B599270F4288BA37B9CE40E699A937F1B9628DDF39C0F7260B0F97C6231E3C6827AFAFE16675E4F5AE62C4A5C6203C2D29FE908B4D435A689F875AC451C07AF16E070A6F7DFFAF49FD0C99AFFAAAEA82163E856ED03BAEF021C2F34954363DD748916934F2507F478A796FB52B4A822D6F409ADD5140EF9ADBFE2F7328F1F3E12D77D29AFC7831394D0392A881B183A2F63D3B0926E54855A44E9E693098477BDC22468C43190F22D80E3AC3E889087D522173164178990183BBD13E978457B38D63335B85C4137952F21F24CABC35D16B3D390154BB428D56F65BEAA9DD787E1BCAC4A5078AB6EA9954E2A1D060A20A14065590A97BA7513394EB6D1C8DE23D5AE9AC2B75529274BD8833491355398C40CE445F2A6A460AEA17A58859E20D36FD4EB0A9C31DFAC0636080793828D8D838A19550EAEA6AF82F10A4F57D2C181563C93AF828A1D912310407EB6998739694C9A79A292658AE7B7F2F48BFB6AF6617BA76C4F291C799FAB44EE292C5763A565BE03031FD0603325A979E5ED846BFEBFFE00C8590E0FD02E73716ACBFE8A18F85B7D063C44F98060433BBC1B44492ED30B6DD09A8746E4A2478AB56C8CEC6256DC1BFD7827BD6EC58E67A7E49BC1A92D063744B964A2312ADF8DA8387B0803119C25DC1E33A10CFB4AB5012E5CDCBA5D25A99412C05C60F0253DC09C2A796755A82F23827530111595E29F408B2A39F54C45026B4B0033B2D9BCA98E7770D0FFCBE4AFBCA6F71F26E7C607753724FC7512DCD255DDC28110962D57084C14138D3EF0FFDA66954A1B02462C914AA33B527215378B2100BFE6D4496D16A0BA238D6FA197B3F948E3D977AFE374787A9218376A9BC8724F005FEBA7A64FC195E5E3761FE41A95B7049FD80DCC7B504122C7FBB41740DF4880CB5EAB28B5FF1787FE30C0C59DFA4F828D6B6CD7E0B89715550D4FA8E799715BB4FDD534080A968BFC1623B9DD2180257AF8863A171C6FAB58F609FA1D80A325E3D698CE3773D62A6EC1F1922BF037D9907ECD05AB9BF84DCA78D864B76923617CDC226AB821ABE5D98979F776DF0FC3671AD6D90366B05D9B828721D6AE27F4D760150C5A0EB34C334B6F82331B2F7F5F94CCDD13CD186F79EB9C2B70EC838C7AB3F7B58CE00FBCE4E74F5A6D3AF5664635AB60F0CD0A3643755D74EF459890B746037D1EF2B4C346BC19570D038D7CC3CB81C31DC39C887F08518572990824407FF36730F297A348F59182258EC342C9D5223611BF035E891FD27D1DEA8C2DC485BB30C54FFBD57C7C385AA7442C6B053671988BC5091C0014B1F7C3CF278EFBABEC261A811EE3A53A89A1FD52F5A933517AB11807494AEA5115CA0BDBF881C7959E66319212619BE5DA681BB858E48C9A03465D0D0805CDCC68AB1ABB4D9D244C901F616A3827102ECC366DB787450BC1DB0B72AF82C4B452A8DCC6A6F9621AC029F2A01698C752852249FA5790030858B7023AC017D06436E2937950FC54CEC1C4019F75EFED04C262A19D0E7F39B65FACE55EB4DC1AF33CBA1ECAAB7BCD2DA6B24A201434EFBB7C12AB913DCAE6A86826CB90856E4297EC39CD5913D458E5D44D55FC99C9C468D1B7CF5D3CFBEB5936A7E19EA856B81433FAB8A10AD63BF93B8E345DD8B9415C0963F8040100533A369A42F13EDD2D052FFC2728971A97034C896BC0E707E3631E0E030B8BAF21865A3CFA6292A04686427854DC9A29E1D0C35C0B3E5EADF0C2D6196C79D6ABD862BCA698ACCE23724887EF934855F30101028346B0754920FDE5EF0A573FBCBE1A7E3BC3C31E2CB780B169EC0EFF600BB04E4270BCF00A01237A7D8B1812CA7FF73076C937449E4EE8AF4989946845B019214AA89836916B3C7033C24A517D9C75183E7E5655E47195B232178C6B17A2CC70278BDB2DD0CEBCBDF8B2777527C2B0A2E0684102F668ABEE61B6F73F003BB587A13F58583D90268087BF8AF6945E976A3DAFEE8BA2B66A80B1806585A024CE4D97671210BF1D86FB838E9950619EFE0333AB4D48D04991F2158E33147399E4EE4A9A5BBADDBB786B70D956A0AF116F110E7EA6E747E313A12D22AB9DE356D67D98D6F7C03EC693633BE69CB6CEB95FC02E82F83C284FB5401641EB96BAA7B211D4812202BEA93A59D2D9EC4B7FE3FAED93D995DE8F4D10D9F0877B67CABB262C5F829966B202972E8B7701E6FB8BF5E8050A3E2C0C893C49D907A9C4B14FA3C5AAF9FD72D67BC6AD1904344DCE38B3F11E466DA3A4FDC6E1188A201AEC83DA879888C61C022BE28950DF680A69BAC819E8C39FE1AC48C61621CF93B38D4ACDC4F1FFF2F3B24DC3827242A51398F07082F66962F079DD117659816B7216A461C8BC5B4DC297A00499A2CC1D4F5D81607A75067C354A255BFF99744CF553E11F8A7EF14268C8E8C44D650BBC667DF84F3682C6C1463A1901CDA6D0AC6769DC40B6833D2B3D37BE26ECCB76FB0A018E1962F2494290CFDD82B1E48218F76C857733E5FB5E5EE5B6C8DB8A8410F004E66D11A7715F551ACF0A778CDEA4299BF5921194BC1702ED540E25809C8F95271745321789F1FBAADFA05AAFF15EF8BC539DFB171486430890101626132166C5E8AA885967884D1BA03F10EB3E4356AE4B191962DF65F541E9D8DCB76A1FFDAACC641603850D5DF8F2E795301F12CED5F0E45243B16A9709D349604D9BBAABF86120453F549C6759130B3E8C40C2199FDEC33E55705EDA78539DA646E9A4DA03B0A1718A0C2F42823BFDFAB565F3903D750B3B0C9E55E796251F01F422599F8FC59C8D52BE9465532FDFFBE8D93CB2B9BAAFE7323AA06D3CCB880D8A56B7BC3C21B36D6E1B80E0056F0A575959F4FD3D830E844EB037A40E20CB0B6EA70EBFE003A28C6AB1B948B57A656BCFD3C280E1A40E057CC69066891C0FCD5AAA92BB663B1ABAE7D00D3179B505A04B87DD462438BC6D33307246626C51BC533860907085786430325042B7E0237D70FD583D4D17B0C23005282F287FA598F3C3D1A9657D1546C3CDB802C257427B3ACEE8BABAA835DAE07855B2EEE7C9038CB03423747C5FC7CEA5F765F5E09F8519612DDA31D0F455DCF62E01137ACB0F8D49B919C9574B7DAC0CEA5ADBB7E42CEEB32D24CD82AC6A948047DDDDF95947934C0C219BB13C31456B44656EEB94413DB836865AC1DE66C19F0E48C65736258398D28411AC208CD72E4B1D43689CCC007CF3E036B23D1118D9DFAE3B5904D00C97602A407E1AA0FA73D64F2BF96DB54BC2153F837B04A9B2BAA520774B3600646CDC9E6DF09AB62562146A721645E0B61C9B77F03
generateSignatureNative result: 9dc83268575ea8a37d7ed09d0d811bff
通过阅读伪代码,可以看到进行了两次MD5Update, 通过对MD5的了解,多次Update相当于字段拼接;

没错就是加盐,在MD5Update 0x11648 处下断点可发现值为

验证通过,至此,generateSignatureNative为加盐md5加密,分析完成;
2.3 encodeHttpParamsNative
为加密参数data的加密
我们通过firda hook java层 encodeHttpParamsNative的入参和结果
encodeHttpParamsNative arg1: {"ckeyset":"AAAHYfE0FG4","width":"1080","captcha_value":"","height":"1794","error_code_fallback":"1","model":"Google_Pixel_10","distributor_mobile_tracking":"","clientVersion":"12100612","heap":"512","avatarSize":"160","client_version":"12100612","advertising_id":"90c13502-db34-4166-8557-588509328e5f","phone_num":"+8613888888888","build_info":"{\"APK_LANGUAGE\":\"0\",\"APPLICATION_ID\":\"com.zing.zalo\",\"BUILDER\":\"khanhtm\",\"BUILD_ID\":\"4d5c1b84-cd3d-41b3-834a-4a45d6a576d6\",\"BUILD_LITE_MODE\":\"false\",\"BUILD_MEDIUM_MODE\":\"false\",\"BUILD_PLAY_STORE\":\"true\",\"BUILD_TIME\":\"2022\\\/03\\\/30 11:52:57\",\"BUILD_TYPE\":\"release\",\"CI\":\"true\",\"DEBUG\":\"false\",\"DISABLE_MULTIDEX\":\"false\",\"DISTRIBUTOR\":\"GOO\",\"ENABLE_BITMAP_POOL\":\"true\",\"ENABLE_DEBUG_BRIDGE_STETHO\":\"false\",\"ENABLE_DEBUG_LEAK_CANARY\":\"false\",\"ENABLE_FINGERPRINT\":\"true\",\"ENABLE_FIREBASE_CRASHLYTICS\":\"true\",\"ENABLE_NETWORK_CONTROL\":\"true\",\"GIT_BRANCH\":\"release_220302\",\"GIT_COMMIT\":\"31613a0\",\"PRELOAD_BUILD\":\"false\",\"USE_FILE_LOGGING\":\"true\",\"USE_QUICK_STICKER_POPUP_MSG\":\"true\",\"USE_SMS_FEATURE\":\"false\",\"VERSION_CODE\":\"12100612\",\"VERSION_NAME\":\"22.03.02\"}","mac_address":"AC:37:43:E0:5F:83","device_identifier":"2002.SSZ-wu8DGTLrXQddcmj2d26MfkpQKrwCUe7jfzTNMOftXw2drLKLZtA0gAhKNXk7.1","local_time":"1650432907013","sign":"","zcid":"1_422924F0981E3B67375D352B30D556C23D5CCD3E949F3A802D97BFFF4C2B140B126C3689A11EF5D02134F7B0459E241F416C570FB604A00618764E0BB0EF80E723A516E36A7B5B4544CC4449968D36AB","network":"0","time_zone":"+08:00","protover":"1","distributor":"GOO","source_type":"1","language":"en","android_id":"16edebed9b04ce88","imei":"000000","cs":"7ad1cddec8101b35cc2fa47c46b8c84f","checkActiveCode":"1","deviceInfo":"{\"CPU_Processor\":\"aarch64\",\"CPU_Hardware\":\"\",\"CPU_Architecture\":\"8\",\"CPU_MAXFreq\":\"1593\",\"CPU_MINFreq\":\"307\",\"CPU_NumCore\":\"4\",\"Model\":\"Pixel\",\"Battery_Technology\":\"Li-ion\",\"Temperature\":\"34.5\",\"Voltage\":\"3922\",\"SimCardSlot\":\"1\",\"SimCardNumber\":\"\",\"SensorStepCount\":\"1\",\"SensorAccelerator\":\"1\",\"NonMarketAllowed\":\"1\"}","source_action":"0","captcha_token":"","preload_info":"unknown","source_switch":"0","answer_type":"","user_language":"en","password":"9af91d5ff305b68a8b9401db6e2544ba","iso_country_code":"CN","hcm_token":"","api_key":"0be3747aacc670a51a83230bcfe80173","certificatedKey":"9487ba76b32e9e36785fb4c3540021f85af8d7b7","inc_p":"1","fcm_token":"ckRFcMIoQoezS_de-njfBl:APA91bGZcU6eCpbZlSpHZzHGWikBy8kiMV__omQeKzH4RFw629XKbl2qzjyzLxretQjV4HNGNAncGRU7K6hVQsy94YDZQtA5t0wFBuXFiinGFbj_U4Fb0Wnq-eTmz_iKYcH-uIQ-iklh","operator":"-1","answer_value":"","question_type":"","clientType":"1","ts":"0","switch_account":"","session_key":"","type":"1"}
encodeHttpParamsNative result: 0874802BBFDAF1526FCEEA1875D7BCC14971103443E613EAB63AA893F1838FB44D3BFC477ACAEE03CB0A3807E23DBDEBC05CE17634AA6933E2A37FFF50160C1A4EC120FC71F32A08A6D94200B5BCDDE8B1E62CD123C2D3CE26EBC930A1D6F40E4819FD81DCCFCB0A527A907FCDDB17FBCEC941963656FCA2F50AE95050FE0624F334C597D7EE151E7F62390CEBFC1DDDF9EAC7707D8D663B67C05A9352C691C9BB4C33B050D1372FBD18B1C86BCEAA478DE2018B4159C09B1B83A5BF4FD12A2EF4B39766517E2D6A358BDEDA33FB719692EBE3F1DD57C829C1E072127D614851B3604A1FA32CAD86D23CCE042CAABE834E3D0A7BD6666B818E12DA033527480854BF6DF0FA2957BC57A0C3E31D79177990B25A28C43BC573084ACE48D7596CD5461C686363A1F842B8A174697026D9D42654C7E46F41FE352A5EBDB0F22CD0A558BAB4CAB1030F8926558B73D20BD9DE8FF4B777E4A446A2E7CE8A2C342F9E1802AC3F2C4C087615B5B71B419B08030F6E2D82C1869240D5DD8356A5FA20AEB2BA2CDC400E5069E59E516481BD66CCCC2C9F857642861E4CE1EEB452AD84C589B324F90F3BC6869C264EC25C754FCD9A3063BEFD917D40B2023224975F33B897664A2C75E3AB7D51B599270F4288BA37B9CE40E699A937F1B9628DDF39C0F7260B0F97C6231E3C6827AFAFE16675E4F5AE62C4A5C6203C2D29FE908B4D435A689F875AC451C07AF16E070A6F7DFFAF49FD0C99AFFAAAEA82163E856ED03BAEF021C2F34954363DD748916934F2507F478A796FB52B4A822D6F409ADD5140EF9ADBFE2F7328F1F3E12D77D29AFC7831394D0392A881B183A2F63D3B0926E54855A44E9E693098477BDC22468C43190F22D80E3AC3E889087D522173164178990183BBD13E978457B38D63335B85C4137952F21F24CABC35D16B3D390154BB428D56F65BEAA9DD787E1BCAC4A5078AB6EA9954E2A1D060A20A14065590A97BA7513394EB6D1C8DE23D5AE9AC2B75529274BD8833491355398C40CE445F2A6A460AEA17A58859E20D36FD4EB0A9C31DFAC0636080793828D8D838A19550EAEA6AF82F10A4F57D2C181563C93AF828A1D912310407EB6998739694C9A79A292658AE7B7F2F48BFB6AF6617BA76C4F291C799FAB44EE292C5763A565BE03031FD0603325A979E5ED846BFEBFFE00C8590E0FD02E73716ACBFE8A18F85B7D063C44F98060433BBC1B44492ED30B6DD09A8746E4A2478AB56C8CEC6256DC1BFD7827BD6EC58E67A7E49BC1A92D063744B964A2312ADF8DA8387B0803119C25DC1E33A10CFB4AB5012E5CDCBA5D25A99412C05C60F0253DC09C2A796755A82F23827530111595E29F408B2A39F54C45026B4B0033B2D9BCA98E7770D0FFCBE4AFBCA6F71F26E7C607753724FC7512DCD255DDC28110962D57084C14138D3EF0FFDA66954A1B02462C914AA33B527215378B2100BFE6D4496D16A0BA238D6FA197B3F948E3D977AFE374787A9218376A9BC8724F005FEBA7A64FC195E5E3761FE41A95B7049FD80DCC7B504122C7FBB41740DF4880CB5EAB28B5FF1787FE30C0C59DFA4F828D6B6CD7E0B89715550D4FA8E799715BB4FDD534080A968BFC1623B9DD2180257AF8863A171C6FAB58F609FA1D80A325E3D698CE3773D62A6EC1F1922BF037D9907ECD05AB9BF84DCA78D864B76923617CDC226AB821ABE5D98979F776DF0FC3671AD6D90366B05D9B828721D6AE27F4D760150C5A0EB34C334B6F82331B2F7F5F94CCDD13CD186F79EB9C2B70EC838C7AB3F7B58CE00FBCE4E74F5A6D3AF5664635AB60F0CD0A3643755D74EF459890B746037D1EF2B4C346BC19570D038D7CC3CB81C31DC39C887F08518572990824407FF36730F297A348F59182258EC342C9D5223611BF035E891FD27D1DEA8C2DC485BB30C54FFBD57C7C385AA7442C6B053671988BC5091C0014B1F7C3CF278EFBABEC261A811EE3A53A89A1FD52F5A933517AB11807494AEA5115CA0BDBF881C7959E66319212619BE5DA681BB858E48C9A03465D0D0805CDCC68AB1ABB4D9D244C901F616A3827102ECC366DB787450BC1DB0B72AF82C4B452A8DCC6A6F9621AC029F2A01698C752852249FA5790030858B7023AC017D06436E2937950FC54CEC1C4019F75EFED04C262A19D0E7F39B65FACE55EB4DC1AF33CBA1ECAAB7BCD2DA6B24A201434EFBB7C12AB913DCAE6A86826CB90856E4297EC39CD5913D458E5D44D55FC99C9C468D1B7CF5D3CFBEB5936A7E19EA856B81433FAB8A10AD63BF93B8E345DD8B9415C0963F8040100533A369A42F13EDD2D052FFC2728971A97034C896BC0E707E3631E0E030B8BAF21865A3CFA6292A04686427854DC9A29E1D0C35C0B3E5EADF0C2D6196C79D6ABD862BCA698ACCE23724887EF934855F30101028346B0754920FDE5EF0A573FBCBE1A7E3BC3C31E2CB780B169EC0EFF600BB04E4270BCF00A01237A7D8B1812CA7FF73076C937449E4EE8AF4989946845B019214AA89836916B3C7033C24A517D9C75183E7E5655E47195B232178C6B17A2CC70278BDB2DD0CEBCBDF8B2777527C2B0A2E0684102F668ABEE61B6F73F003BB587A13F58583D90268087BF8AF6945E976A3DAFEE8BA2B66A80B1806585A024CE4D97671210BF1D86FB838E9950619EFE0333AB4D48D04991F2158E33147399E4EE4A9A5BBADDBB786B70D956A0AF116F110E7EA6E747E313A12D22AB9DE356D67D98D6F7C03EC693633BE69CB6CEB95FC02E82F83C284FB5401641EB96BAA7B211D4812202BEA93A59D2D9EC4B7FE3FAED93D995DE8F4D10D9F0877B67CABB262C5F829966B202972E8B7701E6FB8BF5E8050A3E2C0C893C49D907A9C4B14FA3C5AAF9FD72D67BC6AD1904344DCE38B3F11E466DA3A4FDC6E1188A201AEC83DA879888C61C022BE28950DF680A69BAC819E8C39FE1AC48C61621CF93B38D4ACDC4F1FFF2F3B24DC3827242A51398F07082F66962F079DD117659816B7216A461C8BC5B4DC297A00499A2CC1D4F5D81607A75067C354A255BFF99744CF553E11F8A7EF14268C8E8C44D650BBC667DF84F3682C6C1463A1901CDA6D0AC6769DC40B6833D2B3D37BE26ECCB76FB0A018E1962F2494290CFDD82B1E48218F76C857733E5FB5E5EE5B6C8DB8A8410F004E66D11A7715F551ACF0A778CDEA4299BF5921194BC1702ED540E25809C8F95271745321789F1FBAADFA05AAFF15EF8BC539DFB171486430890101626132166C5E8AA885967884D1BA03F10EB3E4356AE4B191962DF65F541E9D8DCB76A1FFDAACC641603850D5DF8F2E795301F12CED5F0E45243B16A9709D349604D9BBAABF86120453F549C6759130B3E8C40C2199FDEC33E55705EDA78539DA646E9A4DA03B0A1718A0C2F42823BFDFAB565F3903D750B3B0C9E55E796251F01F422599F8FC59C8D52BE9465532FDFFBE8D93CB2B9BAAFE7323AA06D3CCB880D8A56B7BC3C21B36D6E1B80E0056F0A575959F4FD3D830E844EB037A40E20CB0B6EA70EBFE003A28C6AB1B948B57A656BCFD3C280E1A40E057CC69066891C0FCD5AAA92BB663B1ABAE7D00D3179B505A04B87DD462438BC6D33307246626C51BC533860907085786430325042B7E0237D70FD583D4D17B0C23005282F287FA598F3C3D1A9657D1546C3CDB802C257427B3ACEE8BABAA835DAE07855B2EEE7C9038CB03423747C5FC7CEA5F765F5E09F8519612DDA31D0F455DCF62E01137ACB0F8D49B919C9574B7DAC0CEA5ADBB7E42CEEB32D24CD82AC6A948047DDDDF95947934C0C219BB13C31456B44656EEB94413DB836865AC1DE66C19F0E48C65736258398D28411AC208CD72E4B1D43689CCC007CF3E036B23D1118D9DFAE3B5904D00C97602A407E1AA0FA73D64F2BF96DB54BC2153F837B04A9B2BAA520774B3600646CDC9E6DF09AB62562146A721645E0B61C9B77F03

可以看到,这里跟init函数一般一样用了aes加密,同样通过对sub_106AC下断点可发现key为

那么这个key是如何产生,往上翻,不就是我们前面initHttpParamsSNative的存放地址吗。

验证通过。
3. 风控分析
通过对data数据的解析可以发现, encodeHttpParamsNative的入参涉及的信息比较多,其中对设备的信息也会很敏感,通过重放攻击可以得,短时间内的大量请求会导致设备被风控;
通过新设备的重装,发现aes的key会随之改变,会重新走一个链接
可以抓到一个包,链接为:
https://ztevents.zaloapp.com/id/mobile/android
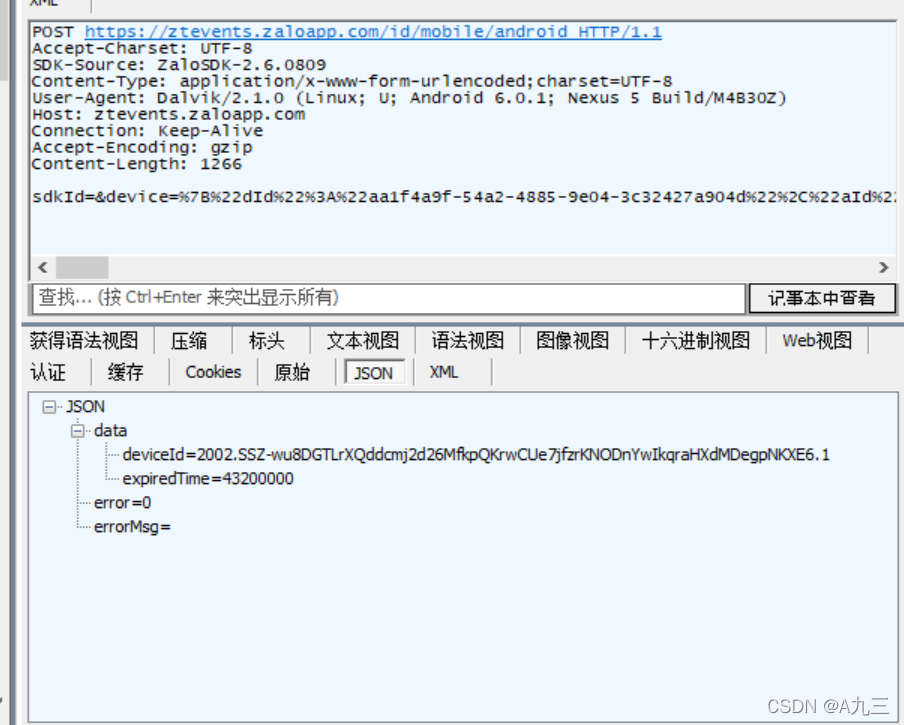
会发送设备信息去注册返回一个deviceID,也是data参数中的device_identifier,发送的数据我们可以通过模拟随机模拟,加密好sig

成功下发伪造的设备信息,然后根据伪造的设备和下发的设备id构造encodeHttpParamsNative的入参,

成功反回登录接口信息,至此,这个app的风控就分析完成了;
结束语
最后说一下,能看到这篇文章的,都是对爬虫感兴趣,又有兴趣去做采集的,相对来说,本文所说到的样本是比较适合新手的,之所以这么说,等到你安安静静去分析时你就会恍然大悟,原来只是这样;但一些坑点也是常规逆向过程中会遇到的,动手==会了~ 源码放在下面的链接,之所以设置这个价格是希望各位看官能自己下手去提升,避免伸手党。

当然 要下载也乐意至极,里面放了本次分析的文件。
下载链接可搜索公众号: jqiu爬虫分析日记,如有问题可私聊或留言;
























 1万+
1万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










