1、背景
因为本地持续集成需要,需要下载kubeconfig文件用于远程连接集群,通过web下载的kubeconfig文件内容为
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUMwakNDQWJxZ0F3SUJBZ0lKQU8rMjR3ZWlJWUhITUEwR0NTcUdTSWIzRFFFQkN3VUFNQlV4RXpBUkJnTlYKQkFNTUNtdDFZbVZ5Ym1WMFpYTXdJQmNOTWpJd016TXhNVEl3T1RJeldoZ1BNakV5TWpBek1EY3hNakE1TWpOYQpNQlV4RXpBUkJnTlZCQU1NQ210MVltVnlibVYwWlhNd2dnRWlNQTBHQ1NxR1NJYjNEUUVCQVFVQUE0SUJEd0F3CmdnRUtBb0lCQVFEbDdwbytjdzViYUpjT0RaOGJkdW5jcWc3QTRycmJSYzlzckI4R053dlF0QzJOZGN4emFrSUoKTnN6VGlNaVhWaGdiWkc1U3BUeU1MQ0dmWHB1dDhrUVFVK1QzUVBDK20vYi9RNWd2RW5udldrOWtMV081SHUxMwpHdnJYSTBYZGtuMXIwSXQ1SVFsNEl1aFBkbzAwamZHUXNOekxLYm5TZlcybjUxVHNyNndGbEJiS2JxeW8zRkRzCnRjdlJFOGFrQlpKQkpjVEMwUnl2OHJ6cjFBR0xKZUhmVWdHYjdRZklQeGRMeVZvZmE4YlpQSklEQjFxdjNZZkYKN3BpSEdUOTd5aGVvcWRpM0JiQjFDWUI2OHJnaGpMTDdZN2FSUVJFbnNDZXBpV3R2SXR3VTg5WFpEbWoyMHk3bgpSSkJlNk5yNWRNNHVQMGJrV2Z1TnN5R1czbys5QVRTakFnTUJBQUdqSXpBaE1BOEdBMVVkRXdFQi93UUZNQU1CCkFmOHdEZ1lEVlIwUEFRSC9CQVFEQWdLa01BMEdDU3FHU0liM0RRRUJDd1VBQTRJQkFRQS8zaFdlcEovd2J6d3cKTjExZkE3eE9sSE1SMVMwaGFaUXlJTG1ZYUU4TmwwVGRoMTFpaW0rMk5jSXlOQmY5SVJFbDh4blRydlpPaysyZgorWm51eHhkRVd0V2wrdFV2a3FGdE82Y0Juc0R6a2lNZ1JuUXd5RGdqY3JZWTZoeEhWSlBDYzY4cFR6R2szYkl5CjJqWDh3bk5GcTJUNXE2LzBEOURSckNxMXVoczFwR3F0dThmdlFHYVFjQ05xUjlvWm9tVGpNSHA4bXZuZkE1Y0MKZGpCYUJna0hSS3lhTFpVbUdkdVFTcS9Gc3FDUWRHMllxaEw0Q05wRnd1SHRpWklkOEh3Yk1YdklUTlFTa2hXbgpuakJ3V2M2aUFXbDdzTnRMdEp1b0lIeHdLMGx5djF4VWttSWVDL1liMjlRSnNqVi85bE13dW5DZUtlSTNkSjRNCnpnZm1jV2ZXCi0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K
server: https://10.10.1.51:8443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURBRENDQWVpZ0F3SUJBZ0lKQUtXK2pZUW9UVGxjTUEwR0NTcUdTSWIzRFFFQkN3VUFNQlV4RXpBUkJnTlYKQkFNTUNtdDFZbVZ5Ym1WMFpYTXdJQmNOTWpJd016TXhNVEl5TmpNNFdoZ1BNakV5TWpBek1EY3hNakkyTXpoYQpNRFF4R1RBWEJnTlZCQU1NRUd0MVltVnlibVYwWlhNdFlXUnRhVzR4RnpBVkJnTlZCQW9NRG5ONWMzUmxiVHB0CllYTjBaWEp6TUlJQklqQU5CZ2txaGtpRzl3MEJBUUVGQUFPQ0FROEFNSUlCQ2dLQ0FRRUE0L1RtSVg5NmcrY1EKMXN4aXp0MDF2cmo4VVFnWUY1TFlvZlVyVCt2N3I2VDZSbVhVVlJOWDNjNkhGSVQ1cWI2UmhzWkdWeENQcUN5VApYTW4rNXZnNjE2bFk1K0ZlS3EwVXVnU1A2TXN2TTllbnVEcDVNcEZwNWlPYlFBdGJWenlvVGtKNzlrQkFrMjRwCldMMnVZRkgveWFFdXdzRTF6YVczZlo0T3YyMUFQRi9xOGp3Z1B5NVZPcGp2Z3VWcituS2VXYmVqTytGbWdUQUcKMVBHczk3b0FXWVpRUExtazVTUDJnVitwdnpkM2Q2c0pCR0x6K2RLYW5USUdrZ1daVFRKalNYRThzL2xlYmVDbApVN3VKUXlYTmJpMUxYQTRMTDU4UXlVc09hbERnY2NERUM3a0gyZ0NmaW8vQ0NuTEhiMFRvbHkzaDAzN3lweWt1CnhwQ3VzOGVzWlFJREFRQUJvekl3TURBSkJnTlZIUk1FQWpBQU1BNEdBMVVkRHdFQi93UUVBd0lGb0RBVEJnTlYKSFNVRUREQUtCZ2dyQmdFRkJRY0RBakFOQmdrcWhraUc5dzBCQVFzRkFBT0NBUUVBMy83RlZpblJ0KzU4elJWcQpUZ0xONWJ0U3R3RXJ0b0NvYW5zT2dIYVJLYWgrcklyaXYwU1kxdVVKY2dtVTNNd3NLZFFEUWM5SjVnWGtqYTZyCk94SXdvaitwZ2QxQzZ4UndCeEozd3lmbHpKb2pKOGRqWm5wMWFHYkFZdnhQMmRKc0o0eGxjQ3g4M29sRTMzMU4KTmp3TTNlRXh5ZWsyYXl2T3ptSDRLVkxpQU1OaFV2b1VQNmVZSTBmd2RaSGsyTWhrSkRPd1lWNTNUdVRqQ0pURwo1UEdKWjFRdTJPV0RrWDdoZ1NTdEo0czg5T0VDSkVlSUladjI1MHh5YitDWmFocjZjckpNSzNydHBWdHJWNzBmCjh5dVIwck1SZ1k5dG5yMTNZekRiUEVtR05nd0JaRXNtQ1g3YS80bWZlcTlwU3dBcXhSbmlZSjFhd3hyZStLS1IKc216Nnl3PT0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=
client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcFFJQkFBS0NBUUVBNC9UbUlYOTZnK2NRMXN4aXp0MDF2cmo4VVFnWUY1TFlvZlVyVCt2N3I2VDZSbVhVClZSTlgzYzZIRklUNXFiNlJoc1pHVnhDUHFDeVRYTW4rNXZnNjE2bFk1K0ZlS3EwVXVnU1A2TXN2TTllbnVEcDUKTXBGcDVpT2JRQXRiVnp5b1RrSjc5a0JBazI0cFdMMnVZRkgveWFFdXdzRTF6YVczZlo0T3YyMUFQRi9xOGp3ZwpQeTVWT3Bqdmd1VnIrbktlV2Jlak8rRm1nVEFHMVBHczk3b0FXWVpRUExtazVTUDJnVitwdnpkM2Q2c0pCR0x6CitkS2FuVElHa2dXWlRUSmpTWEU4cy9sZWJlQ2xVN3VKUXlYTmJpMUxYQTRMTDU4UXlVc09hbERnY2NERUM3a0gKMmdDZmlvL0NDbkxIYjBUb2x5M2gwMzd5cHlrdXhwQ3VzOGVzWlFJREFRQUJBb0lCQVFDV0gzcFBKVHp5RVFJdAo4M3crNzcrdFV2WVlCMVNXY2NicElpVGNCWFZEUDByemdheE1PdWpxMGxCeld2OXdvbWdFY2g5d3h4OVVpY2FpCm5RU1o1M0FaQnhYZDM3VzhOVEFwTVVmMDc1cXVjWitxM0JkbERnN0gyVHNzK2syMUxlVkpaTTl1WlBJaUpiSmwKRnNYMytRaVRLT3M2cHpOZnMzc2I1ek9mTGJ2WUJiVGRVSTRheXBocFdhdC9JMXdZdnFVTGo0ZE5DdzBvam1MQwptNXB4dnUyUTdSZFNZZFFWWitsWHRGTkRnZGMzQTY5TzN0d1d5VDU0Z0tXMzlhcWVaU2tUc3FPMWJ4Ly9vcldOCmFRNGRGQ2VZVUI4dlFmTkJ4bjBEMXpEcWlqb2pteHdSNTBrRDNzK3B0L0VPUC9wZWZDL1puUnVKSEhYdjc4b00KT0VIQzBXRWhBb0dCQVBaNjM2bFRCRVlySjBISmZMOEU3bUhMV2ovQ2ZYOG1nOVg1K0ZkR0hJdm4xZVpqTHQ0bQpDVUE0Rzg4Q3JpMUU1MnJQcXNsdUp5ZkxLdmlVQlBMQmkvSnNYM1IyUXdvbVJzMjZnZnhock51UnZnM3JjMHZkClVuY2t4UGwxV1pwOHV6VjFINGtBRkpDUU5NbUtrazdYeUM3emxBeXBuM3Q3T3I4RkZRMnBrTnEvQW9HQkFPekMKM3lBUkU4ai9yWWlRcDZ2OFZWSDl0THJCN2UwM2ZYcWk1V3d6azM2Qk1LQWpJZDdiT0NPcDcvRmZLMUh0Zy9LLwp3MENUdEc3ZklSMng2djlacjJtTkMyRTVTRTRHQWRNakxKTkFFN1FOakdETGQ1SXNVK296aEdTUjZwTjFRR1lJCi9DRXA0TzhXWnNVR2lhR2xja3UxRkwraGw3bUhxeGRncXlQTUxUWGJBb0dBQzJGdEJsSnc5aFIwQVpPZUVPdlgKWGVpWHlDM2d3WWd6dWlPS2xlMEUwR2pwOVhOSzdMTHc1bWd3MElRZEtyWHR3WDdKTWZmR0V3NU1jNkhTQUt0egpITVJvTytaaC9ndjZaUEZob3hlWGRhUHJGSlYwZzJJNnRvbWFGcktXYW8ycnp6SVRQSzRtUk82RG9YS21nc0Z2CjJzc2dZTjFNSWRWMHh2RWpJYmhjbWQwQ2dZRUFzV2JxN1FvZXV4THBJbFRSYmdycW16N3d0cWNzOGZ3TUoySDcKYWZIVGFJekF0SnplZWkva2hzU0VwMlZaL2s5citPNDdEUjRmcXB2Q0lvLzN0MUdxSC9xeE5pNUh3VDY3QzB0bAowUWZJTzdlVEljd1RVaEdvNXVtbkgvdzl1ak8zQnoxZ1BqRTArN0RiWEhJam1sMXZvTTZVTjJxTFYxY1NtYmV6ClJHVnUwdFVDZ1lFQXhFZ0RTYm4wN2NaNWxkeFNIZi9PVHJuRGhFbDVYeHBybWcxTWV5S0huNmlueGdsdXlPRVYKUFZuUDIzR0szOElVUHpOMDZFV2VZeEd3NWdrcUs0UW90ZW9LTnFqUVhzemZvbUZGYmJzcTE5U0J0c0gvZko0VQpvQ2YvSXVTeUt1ODRCUUhVeWtpNlFFZy9LK1FBMWwzV3pKMXQ0bG5YdXZoWDVkZUZtRkF5V0lRPQotLS0tLUVORCBSU0EgUFJJVkFURSBLRVktLS0tLQo=通过映射的方式将server的地址映射到外网:10.10.1.51:8443---->115.236.96.34:22544,然后再修改kubeconfig文件server地址以为可以这样连接。
2、问题
但修改后的文件本地kubectl连接后报错:
[kube-test@8-106 .kube]$ kubectl get ns
Unable to connect to the server: x509: certificate is valid for 127.0.0.1, ::1, 10.0.0.1, 10.10.1.51, 10.10.1.51, not 115.236.96.34原因:生成的apiserver证书中不包含这个地址的认证,需要重新生成一个证书
#删除老的证书
[root@kube-test-master-1 pki]# rm /etc/kubernetes/pki/apiserver.*
#重新初始化一个证书,并添加外网地址相关参数--apiserver-cert-extra-sans 115.236.96.34
[root@kube-test-master-1 pki]# kubeadm init phase certs apiserver --apiserver-advertise-address 10.10.1.51 --apiserver-cert-extra-sans 115.236.96.34
I0401 22:24:17.377881 11145 version.go:251] remote version is much newer: v1.23.5; falling back to: stable-1.20
[certs] Generating "apiserver" certificate and key
[certs] apiserver serving cert is signed for DNS names [kube-test-master-1 kubernetes kubernetes.default kubernetes.default.svc kubernetes.default.svc.cluster.local] and IPs [10.96.0.1 10.10.1.51 115.236.96.34]
#更新admin.conf文件即kubeconfig文件
[root@kube-test-master-1 pki]# kubeadm certs renew admin.conf
[renew] Reading configuration from the cluster...
[renew] FYI: You can look at this config file with 'kubectl -n kube-system get cm kubeadm-config -o yaml'
certificate embedded in the kubeconfig file for the admin to use and for kubeadm itself renewed
#同时需要重启kube-apiserver
[root@kube-test-master-1 pki]# kubectl -n kube-system get pod | grep api
kube-apiserver-kube-test-master-1 1/1 Running 0 3h57m
[root@kube-test-master-1 pki]# kubectl -n kube-system delete pod kube-apiserver-kube-test-master-1
pod "kube-apiserver-kube-test-master-1" deleted注:重新生成的证书,过期时间为1年,因为kubeadm内置的证书生成语法过期时间就为一年
[root@kube-test-master-1 pki_bak]# openssl x509 -in /etc/kubernetes/pki_bak/apiserver.crt -noout -text |grep ' Not '
Not Before: Mar 31 12:09:23 2022 GMT
Not After : Apr 1 10:29:37 2023 GMT参考以下两篇文章的思路,下载源码同时临时更换kubeadm二进制文件后去生成的证书过期时间可为100年
https://www.cnblogs.com/lixinliang/p/12217328.html
https://sysin.cn/blog/kubernetes-kubeadmin-cert-100y/#5-%E4%B8%8B%E8%BD%BD
[root@kube-test-master-1 pki]# kubeadm certs check-expiration
[check-expiration] Reading configuration from the cluster...
[check-expiration] FYI: You can look at this config file with 'kubectl -n kube-system get cm kubeadm-config -o yaml'
CERTIFICATE EXPIRES RESIDUAL TIME CERTIFICATE AUTHORITY EXTERNALLY MANAGED
admin.conf Mar 08, 2122 14:24 UTC 99y no
apiserver Mar 08, 2122 14:24 UTC 99y ca no
apiserver-kubelet-client Mar 07, 2122 12:26 UTC 99y ca no
controller-manager.conf Mar 07, 2122 12:26 UTC 99y no
front-proxy-client Mar 07, 2122 12:26 UTC 99y front-proxy-ca no
scheduler.conf Mar 07, 2122 12:26 UTC 99y no
CERTIFICATE AUTHORITY EXPIRES RESIDUAL TIME EXTERNALLY MANAGED
ca Mar 07, 2122 12:09 UTC 99y no
front-proxy-ca Mar 07, 2122 12:09 UTC 99y no一次到位,先把kubeadm更换掉,再重新初始化证书,再重启kube-apiserver
3、解决问题验证
在web页面上重新下载一个kubeconfig文件或者在master路径/etc/kubernetes下下载admin.conf文件到本地终端的$home/.kube目录下并重命名为config文件
注意config文件中的server地址需要手动修改成外网地址:
#这里的server地址必须手动更换,重新生成不会添加地址
[kube-test@jenkins-8-119 .kube]$ cat config
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUMwakNDQWJxZ0F3SUJBZ0lKQU8rMjR3ZWlJWUhITUEwR0NTcUdTSWIzRFFFQkN3VUFNQlV4RXpBUkJnTlYKQkFNTUNtdDFZbVZ5Ym1WMFpYTXdJQmNOTWpJd016TXhNVEl3T1RJeldoZ1BNakV5TWpBek1EY3hNakE1TWpOYQpNQlV4RXpBUkJnTlZCQU1NQ210MVltVnlibVYwWlhNd2dnRWlNQTBHQ1NxR1NJYjNEUUVCQVFVQUE0SUJEd0F3CmdnRUtBb0lCQVFEbDdwbytjdzViYUpjT0RaOGJkdW5jcWc3QTRycmJSYzlzckI4R053dlF0QzJOZGN4emFrSUoKTnN6VGlNaVhWaGdiWkc1U3BUeU1MQ0dmWHB1dDhrUVFVK1QzUVBDK20vYi9RNWd2RW5udldrOWtMV081SHUxMwpHdnJYSTBYZGtuMXIwSXQ1SVFsNEl1aFBkbzAwamZHUXNOekxLYm5TZlcybjUxVHNyNndGbEJiS2JxeW8zRkRzCnRjdlJFOGFrQlpKQkpjVEMwUnl2OHJ6cjFBR0xKZUhmVWdHYjdRZklQeGRMeVZvZmE4YlpQSklEQjFxdjNZZkYKN3BpSEdUOTd5aGVvcWRpM0JiQjFDWUI2OHJnaGpMTDdZN2FSUVJFbnNDZXBpV3R2SXR3VTg5WFpEbWoyMHk3bgpSSkJlNk5yNWRNNHVQMGJrV2Z1TnN5R1czbys5QVRTakFnTUJBQUdqSXpBaE1BOEdBMVVkRXdFQi93UUZNQU1CCkFmOHdEZ1lEVlIwUEFRSC9CQVFEQWdLa01BMEdDU3FHU0liM0RRRUJDd1VBQTRJQkFRQS8zaFdlcEovd2J6d3cKTjExZkE3eE9sSE1SMVMwaGFaUXlJTG1ZYUU4TmwwVGRoMTFpaW0rMk5jSXlOQmY5SVJFbDh4blRydlpPaysyZgorWm51eHhkRVd0V2wrdFV2a3FGdE82Y0Juc0R6a2lNZ1JuUXd5RGdqY3JZWTZoeEhWSlBDYzY4cFR6R2szYkl5CjJqWDh3bk5GcTJUNXE2LzBEOURSckNxMXVoczFwR3F0dThmdlFHYVFjQ05xUjlvWm9tVGpNSHA4bXZuZkE1Y0MKZGpCYUJna0hSS3lhTFpVbUdkdVFTcS9Gc3FDUWRHMllxaEw0Q05wRnd1SHRpWklkOEh3Yk1YdklUTlFTa2hXbgpuakJ3V2M2aUFXbDdzTnRMdEp1b0lIeHdLMGx5djF4VWttSWVDL1liMjlRSnNqVi85bE13dW5DZUtlSTNkSjRNCnpnZm1jV2ZXCi0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K
server: https://115.236.96.34:22544
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURBRENDQWVpZ0F3SUJBZ0lKQUtXK2pZUW9UVGxjTUEwR0NTcUdTSWIzRFFFQkN3VUFNQlV4RXpBUkJnTlYKQkFNTUNtdDFZbVZ5Ym1WMFpYTXdJQmNOTWpJd016TXhNVEl5TmpNNFdoZ1BNakV5TWpBek1EY3hNakkyTXpoYQpNRFF4R1RBWEJnTlZCQU1NRUd0MVltVnlibVYwWlhNdFlXUnRhVzR4RnpBVkJnTlZCQW9NRG5ONWMzUmxiVHB0CllYTjBaWEp6TUlJQklqQU5CZ2txaGtpRzl3MEJBUUVGQUFPQ0FROEFNSUlCQ2dLQ0FRRUE0L1RtSVg5NmcrY1EKMXN4aXp0MDF2cmo4VVFnWUY1TFlvZlVyVCt2N3I2VDZSbVhVVlJOWDNjNkhGSVQ1cWI2UmhzWkdWeENQcUN5VApYTW4rNXZnNjE2bFk1K0ZlS3EwVXVnU1A2TXN2TTllbnVEcDVNcEZwNWlPYlFBdGJWenlvVGtKNzlrQkFrMjRwCldMMnVZRkgveWFFdXdzRTF6YVczZlo0T3YyMUFQRi9xOGp3Z1B5NVZPcGp2Z3VWcituS2VXYmVqTytGbWdUQUcKMVBHczk3b0FXWVpRUExtazVTUDJnVitwdnpkM2Q2c0pCR0x6K2RLYW5USUdrZ1daVFRKalNYRThzL2xlYmVDbApVN3VKUXlYTmJpMUxYQTRMTDU4UXlVc09hbERnY2NERUM3a0gyZ0NmaW8vQ0NuTEhiMFRvbHkzaDAzN3lweWt1CnhwQ3VzOGVzWlFJREFRQUJvekl3TURBSkJnTlZIUk1FQWpBQU1BNEdBMVVkRHdFQi93UUVBd0lGb0RBVEJnTlYKSFNVRUREQUtCZ2dyQmdFRkJRY0RBakFOQmdrcWhraUc5dzBCQVFzRkFBT0NBUUVBMy83RlZpblJ0KzU4elJWcQpUZ0xONWJ0U3R3RXJ0b0NvYW5zT2dIYVJLYWgrcklyaXYwU1kxdVVKY2dtVTNNd3NLZFFEUWM5SjVnWGtqYTZyCk94SXdvaitwZ2QxQzZ4UndCeEozd3lmbHpKb2pKOGRqWm5wMWFHYkFZdnhQMmRKc0o0eGxjQ3g4M29sRTMzMU4KTmp3TTNlRXh5ZWsyYXl2T3ptSDRLVkxpQU1OaFV2b1VQNmVZSTBmd2RaSGsyTWhrSkRPd1lWNTNUdVRqQ0pURwo1UEdKWjFRdTJPV0RrWDdoZ1NTdEo0czg5T0VDSkVlSUladjI1MHh5YitDWmFocjZjckpNSzNydHBWdHJWNzBmCjh5dVIwck1SZ1k5dG5yMTNZekRiUEVtR05nd0JaRXNtQ1g3YS80bWZlcTlwU3dBcXhSbmlZSjFhd3hyZStLS1IKc216Nnl3PT0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=
client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcFFJQkFBS0NBUUVBNC9UbUlYOTZnK2NRMXN4aXp0MDF2cmo4VVFnWUY1TFlvZlVyVCt2N3I2VDZSbVhVClZSTlgzYzZIRklUNXFiNlJoc1pHVnhDUHFDeVRYTW4rNXZnNjE2bFk1K0ZlS3EwVXVnU1A2TXN2TTllbnVEcDUKTXBGcDVpT2JRQXRiVnp5b1RrSjc5a0JBazI0cFdMMnVZRkgveWFFdXdzRTF6YVczZlo0T3YyMUFQRi9xOGp3ZwpQeTVWT3Bqdmd1VnIrbktlV2Jlak8rRm1nVEFHMVBHczk3b0FXWVpRUExtazVTUDJnVitwdnpkM2Q2c0pCR0x6CitkS2FuVElHa2dXWlRUSmpTWEU4cy9sZWJlQ2xVN3VKUXlYTmJpMUxYQTRMTDU4UXlVc09hbERnY2NERUM3a0gKMmdDZmlvL0NDbkxIYjBUb2x5M2gwMzd5cHlrdXhwQ3VzOGVzWlFJREFRQUJBb0lCQVFDV0gzcFBKVHp5RVFJdAo4M3crNzcrdFV2WVlCMVNXY2NicElpVGNCWFZEUDByemdheE1PdWpxMGxCeld2OXdvbWdFY2g5d3h4OVVpY2FpCm5RU1o1M0FaQnhYZDM3VzhOVEFwTVVmMDc1cXVjWitxM0JkbERnN0gyVHNzK2syMUxlVkpaTTl1WlBJaUpiSmwKRnNYMytRaVRLT3M2cHpOZnMzc2I1ek9mTGJ2WUJiVGRVSTRheXBocFdhdC9JMXdZdnFVTGo0ZE5DdzBvam1MQwptNXB4dnUyUTdSZFNZZFFWWitsWHRGTkRnZGMzQTY5TzN0d1d5VDU0Z0tXMzlhcWVaU2tUc3FPMWJ4Ly9vcldOCmFRNGRGQ2VZVUI4dlFmTkJ4bjBEMXpEcWlqb2pteHdSNTBrRDNzK3B0L0VPUC9wZWZDL1puUnVKSEhYdjc4b00KT0VIQzBXRWhBb0dCQVBaNjM2bFRCRVlySjBISmZMOEU3bUhMV2ovQ2ZYOG1nOVg1K0ZkR0hJdm4xZVpqTHQ0bQpDVUE0Rzg4Q3JpMUU1MnJQcXNsdUp5ZkxLdmlVQlBMQmkvSnNYM1IyUXdvbVJzMjZnZnhock51UnZnM3JjMHZkClVuY2t4UGwxV1pwOHV6VjFINGtBRkpDUU5NbUtrazdYeUM3emxBeXBuM3Q3T3I4RkZRMnBrTnEvQW9HQkFPekMKM3lBUkU4ai9yWWlRcDZ2OFZWSDl0THJCN2UwM2ZYcWk1V3d6azM2Qk1LQWpJZDdiT0NPcDcvRmZLMUh0Zy9LLwp3MENUdEc3ZklSMng2djlacjJtTkMyRTVTRTRHQWRNakxKTkFFN1FOakdETGQ1SXNVK296aEdTUjZwTjFRR1lJCi9DRXA0TzhXWnNVR2lhR2xja3UxRkwraGw3bUhxeGRncXlQTUxUWGJBb0dBQzJGdEJsSnc5aFIwQVpPZUVPdlgKWGVpWHlDM2d3WWd6dWlPS2xlMEUwR2pwOVhOSzdMTHc1bWd3MElRZEtyWHR3WDdKTWZmR0V3NU1jNkhTQUt0egpITVJvTytaaC9ndjZaUEZob3hlWGRhUHJGSlYwZzJJNnRvbWFGcktXYW8ycnp6SVRQSzRtUk82RG9YS21nc0Z2CjJzc2dZTjFNSWRWMHh2RWpJYmhjbWQwQ2dZRUFzV2JxN1FvZXV4THBJbFRSYmdycW16N3d0cWNzOGZ3TUoySDcKYWZIVGFJekF0SnplZWkva2hzU0VwMlZaL2s5citPNDdEUjRmcXB2Q0lvLzN0MUdxSC9xeE5pNUh3VDY3QzB0bAowUWZJTzdlVEljd1RVaEdvNXVtbkgvdzl1ak8zQnoxZ1BqRTArN0RiWEhJam1sMXZvTTZVTjJxTFYxY1NtYmV6ClJHVnUwdFVDZ1lFQXhFZ0RTYm4wN2NaNWxkeFNIZi9PVHJuRGhFbDVYeHBybWcxTWV5S0huNmlueGdsdXlPRVYKUFZuUDIzR0szOElVUHpOMDZFV2VZeEd3NWdrcUs0UW90ZW9LTnFqUVhzemZvbUZGYmJzcTE5U0J0c0gvZko0VQpvQ2YvSXVTeUt1ODRCUUhVeWtpNlFFZy9LK1FBMWwzV3pKMXQ0bG5YdXZoWDVkZUZtRkF5V0lRPQotLS0tLUVORCBSU0EgUFJJVkFURSBLRVktLS0tLQo=
##可以正确获取集群信息
[kube-test@jenkins-8-119 .kube]$ kubectl get ns
NAME STATUS AGE
default Active 26h
kube-node-lease Active 26h
kube-operator Active 26h
kube-public Active 26h
kube-system Active 26h
wanghaibo-test Active 26h注意:
因为新生成了apiserver的证书,但是只认证了两个IP--apiserver-advertise-address 10.10.1.51 --apiserver-cert-extra-sans 115.236.96.34
未带默认的IP:10.0.0.1,后创建pod时报错如下
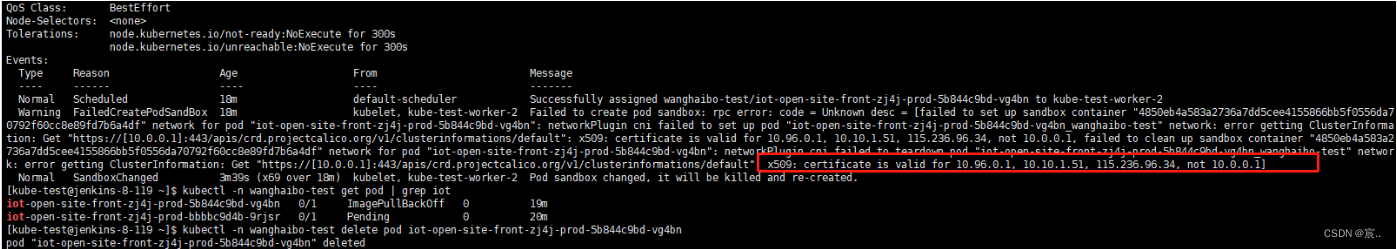
所以重新生成证书的命令应该修改成:
[root@kube-test-master-1 pki]# kubeadm init phase certs apiserver --apiserver-advertise-address 10.10.1.51 --apiserver-cert-extra-sans 115.236.96.34 --apiserver-cert-extra-sans 10.0.0.1一、远程连接集群版的解决方案
按照上面的方法,操作比较麻烦,且不知道原来的cert-extra-sans有没有少加,证书更新了,会不会像上面一样后续出现少认证IP的坑,在用kubeadm自己安装过一遍集群之后,找到了更好的解决方案。注意3个master都要执行
当有三个master使用Haproxy+keepalived做虚拟IP后,可以把虚拟IP映射出去
1、编辑kubeadm的配置文件
/etc/kubernetes/kubeadm-config.yaml
##编辑apiserver-certSANs相关段落
apiServer:
extraArgs:
allow-privileged: "true"
apiserver-count: "3"
feature-gates: "RemoveSelfLink=false"
enable-admission-plugins: NodeRestriction
encryption-provider-config: /etc/kubernetes/pki/secrets-encryption.yaml
kubelet-certificate-authority: /etc/kubernetes/pki/ca.crt
kubelet-client-certificate: /etc/kubernetes/pki/apiserver-kubelet-client.crt
kubelet-client-key: /etc/kubernetes/pki/apiserver-kubelet-client.key
profiling: "false"
service-node-port-range: 30000-32767
extraVolumes:
- hostPath: /etc/localtime
mountPath: /etc/localtime
pathType: File
readOnly: true
name: localtime
certSANs:
- localhost
- kubernetes
- kubernetes.default
- kubernetes.default.svc
- kubernetes.default.svc.cluster
- kubernetes.default.svc.cluster.local
- kube-master1-31
- kube-master2-32
- kube-master3-33
- 127.0.0.1
- 0:0:0:0:0:0:0:1
- 10.0.0.1
- 10.10.1.45
- 10.10.1.31
- 10.10.1.32
- 10.10.1.33
- 115.236.96.34
##把外网IP添加上,可以看到之前还有很多IP以及域名2、重新生成api-server证书
注意要提前改造kubeadm,换成改过代码自编译可使有效期变成100年的kubeadm
[root@kube-master2-32 pki]# pwd
/etc/kubernetes/pki
##把原来的证书删掉
[root@kube-master2-32 pki]# rm -f apiserver.*
##应用/etc/kubernetes/kubeadm-config.yaml文件重新生成证书
[root@kube-master2-32 pki]# kubeadm init phase certs apiserver --config /etc/kubernetes/kubeadm-config.yaml
[config] WARNING: Ignored YAML document with GroupVersionKind kubeadm.k8s.io/v1beta2, Kind=JoinConfiguration
[certs] Generating "apiserver" certificate and key
[certs] apiserver serving cert is signed for DNS names [kube-master1-31 kube-master2-32 kube-master3-33 kubernetes kubernetes.default kubernetes.default.svc kubernetes.default.svc.cluster kubernetes.default.svc.cluster.local localhost] and IPs [10.0.0.1 10.10.1.32 10.10.1.45 127.0.0.1 ::1 10.10.1.31 10.10.1.33 115.236.96.34]
###可以看到证书已经更新
[root@kube-master1-32 kubernetes]# kubeadm certs check-expiration
[check-expiration] Reading configuration from the cluster...
[check-expiration] FYI: You can look at this config file with 'kubectl -n kube-system get cm kubeadm-config -o yaml'
CERTIFICATE EXPIRES RESIDUAL TIME CERTIFICATE AUTHORITY EXTERNALLY MANAGED
admin.conf Mar 26, 2122 14:22 UTC 99y no
apiserver Mar 27, 2122 08:01 UTC 99y ca no
apiserver-kubelet-client Mar 26, 2122 14:22 UTC 99y ca no
controller-manager.conf Mar 26, 2122 14:22 UTC 99y no
front-proxy-client Mar 26, 2122 14:22 UTC 99y front-proxy-ca no
scheduler.conf Mar 26, 2122 14:22 UTC 99y no
CERTIFICATE AUTHORITY EXPIRES RESIDUAL TIME EXTERNALLY MANAGED
ca Mar 26, 2122 14:22 UTC 99y no
front-proxy-ca Mar 26, 2122 14:22 UTC 99y no实测,不需要重新把admin.conf也更新
3、重启kube-apiserver
[root@kube-master1-31 ~]# kubectl -n kube-system get pod | grep api
kube-apiserver-kube-master1-31 1/1 Running 2 (17h ago) 18h
kube-apiserver-kube-master2-32 1/1 Running 2 (17h ago) 18h
kube-apiserver-kube-master3-33 1/1 Running 1 (18h ago) 18h
[root@kube-master1-31 ~]# kubectl -n kube-system delete pod kube-apiserver-kube-master1-31 kube-apiserver-kube-master2-32 kube-apiserver-kube-master3-33
pod "kube-apiserver-kube-master1-31" deleted
pod "kube-apiserver-kube-master2-32" deleted
pod "kube-apiserver-kube-master3-33" deleted重启apiserver,然后使用原来改好外网IP和端口的kubeconfig文件即可正常获取到集群信息
##原来不可以
[kube-test@jenkins-8-119 .kube]$ kubectl get ns
Unable to connect to the server: x509: certificate is valid for 127.0.0.1, ::1, 10.0.0.1, 10.10.1.31, 10.10.1.32, 10.10.1.33, 10.10.1.45, not 115.236.96.34
##现在可以了
[kube-test@jenkins-8-119 .kube]$ kubectl get ns
NAME STATUS AGE
default Active 18h
kube-node-lease Active 18h
kube-operator Active 18h
kube-public Active 18h
kube-system Active 18h二、安装相关的坑
1、不要先装docker
由于脚本判断问题,如果安装docker但是未安装docker-compose的话,重新安装docker会报错。
如果安装了docker,docker-compose一并安装后即可解决
脚本逻辑如下:
....
....
# 检测 docker 是否存在
function install_docker() {
if which docker docker-compose ;then
log "... docker 已经安装,跳过安装步骤"
config_docker
if systemctl status docker|grep running;then
log "... docker 运行正常"
else
log "... docker 已经安装,跳过安装步骤"
fi
else
if [[ -d docker ]]; then
log "... 离线安装 docker"
cp docker/bin/* /usr/bin/
cp docker/service/docker.service /etc/systemd/system/
sudo chmod +x /usr/bin/docker*
sudo chmod 754 /etc/systemd/system/docker.service
log "... 配置 docker"
config_docker
....
.... 2、服务器时区要对
注意操作系统安装的时区要选对,否则使用自动安装的chronyd服务后,所有服务器都会同步错误的时区,设置方法:
##设置时区为亚洲/上海
timedatectl set-timezone Asia/Shanghai3、组件不健康状态
master为单点或者master为集群时都出现了scheduler组件不健康的状态,如下:
##如下,为Unhealthy状态
[root@kube-master2-32 pki]# kubectl get cs
Warning: v1 ComponentStatus is deprecated in v1.19+
NAME STATUS MESSAGE ERROR
scheduler Unhealthy Get "http://127.0.0.1:10251/healthz": dial tcp 127.0.0.1:10251: connect: connection refused
controller-manager Healthy ok
etcd-1 Healthy {"health":"true","reason":""}
etcd-2 Healthy {"health":"true","reason":""}
etcd-0 Healthy {"health":"true","reason":""}处理方式,修改/etc/kubernetes/manifests/kube-scheduler.yaml,删除port=0那一行
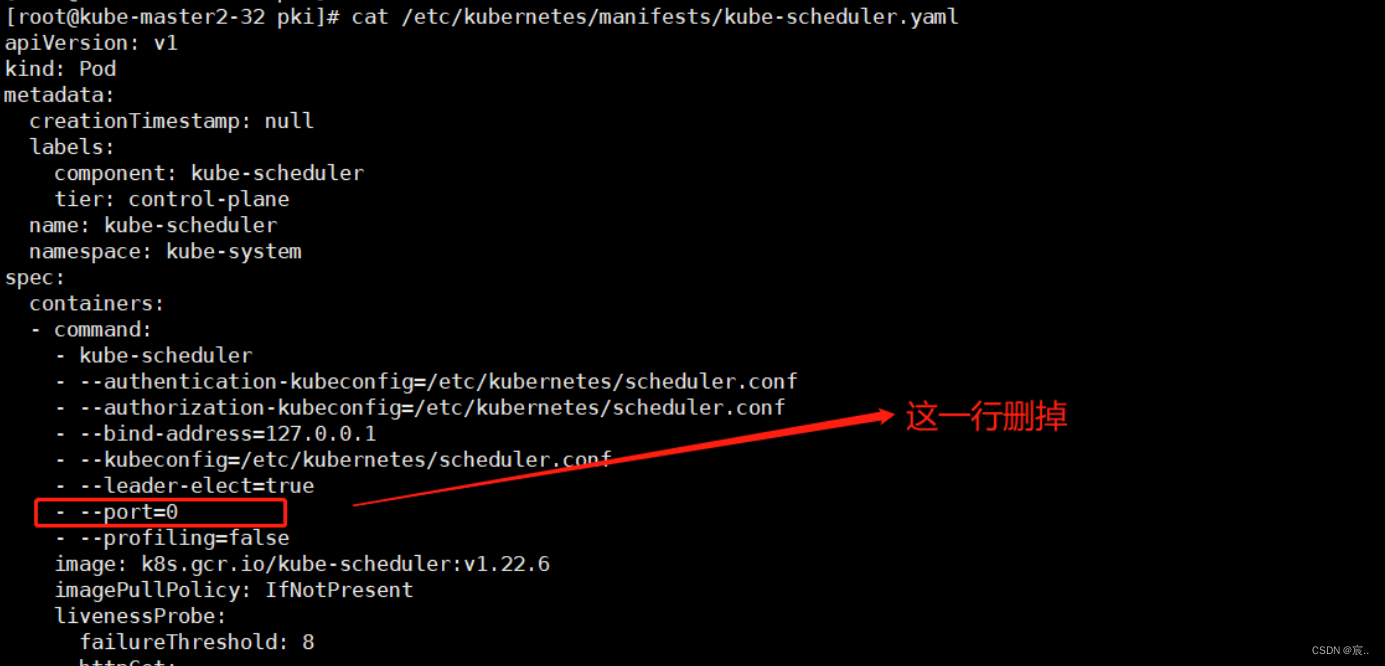
然后重启节点的kubelet,注意如果是三个节点的master,则三个节点都要这么操作:
##把port=0那一行删掉 [root@kube-master2-32 pki]# vi /etc/kubernetes/manifests/kube-scheduler.yaml [root@kube-master2-32 pki]# systemctl restart kubelet ##如下,已恢复正常 [root@kube-master2-32 pki]# kubectl get cs Warning: v1 ComponentStatus is deprecated in v1.19+ NAME STATUS MESSAGE ERROR scheduler Healthy ok controller-manager Healthy ok etcd-2 Healthy {"health":"true","reason":""} etcd-0 Healthy {"health":"true","reason":""} etcd-1 Healthy {"health":"true","reason":""}





















 1647
1647











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








