希望能帮助到对源码感兴趣的同学
架构

图片来自 docker 官网文档
源码
dockerd https://github.com/moby/moby
docker https://github.com/docker/cli
相关目录
api
cmd
daemon
libnetwork
调用关系
源码版本 master commit 6834304,时间 2023年1月7日。
cmd/dockerd/docker.go main
cmd/dockerd/daemon.go start
重要的
daemon.NewDaemon 后面有讲,先略过
initRouter
主要关心 container 相关接口
container.NewRouter
api/server/router/container/container.go NewRouter
注意参数 backend 即 daemon 指针
重要函数 initRoutes
api/server/router/container/backend.go Backend interface
感兴趣的 docker start 调用
daemon/start.go ContainerStart
重要的
daemon.conditionalMountOnStart
daemon.initializeNetworking
libcontainerd.ReplaceContainer
网络
daemon/container_operations.go initializeNetworking
daemon/container_operations.go allocateNetwork
重要的
daemon.netController.NewSandbox
daemon.connectToNetwork
daemon/container_operations.go connectToNetwork
ep, err := n.CreateEndpoint(endpointName, createOptions...)
err := ep.Join(sb, joinOptions...)
err = d.ProgramExternalConnectivity(n.ID(), ep.ID(), sb.Labels())
netController 是什么 回到前面的 daemon.NewDaemon
daemon/daemon.go NewDaemon
daemon/daemon.go restore
关注的
daemon.initNetworkController
daemon\daemon_unix.go initNetworkController
daemon.netController, err = libnetwork.New(netOptions...)
err := configureNetworking(daemon.netController, daemon.configStore)
initBridgeDriver
Initialize default network on "bridge" with the same name
controller.NewNetwork
网络 CNM
Design

Sandbox
容器网络栈包含路由表、dns、loopback 等。
Endpoint
实现 sandbox 与 network 的连接,如 veth。
Network
类似交换机实现多个 endpoint 互相通信,如 bridge docker0。
源码
bridge
libnetwork\controller.go New
drvRegistry.AddDriver(i.ntype, i.fn, dcfg)
libnetwork\drvregistry\drvregistry.go AddDriver
fn(r, config) 即 bridge.Init
libnetwork\drivers\bridge\bridge.go Init
initIPAMDrivers 备注 ipam 指 IP Address Management
libnetwork\controller.go NewNetwork
err = c.addNetwork(nw)
err := d.CreateNetwork(n.id, n.generic, n, n.getIPData(4), n.getIPData(6))
libnetwork\drivers\bridge\bridge.go CreateNetwork
bridgeIface, err := newInterface(d.nlh, config)
创建 bridge
libnetwork\drivers\bridge\setup_ipv4.go setupBridgeIPv4
配置 IP 等
libnetwork\drivers\bridge\setup_ip_tables.go setupIP4Tables
配置 iptables
loopback
libnetwork\controller.go NewSandbox
libnetwork\osl\namespace_linux.go NewSandbox
命令行调 netns-create 创建 network namespace
github.com/vishvananda/netns
sboxNs, err := netns.GetFromPath(n.path) 获取 network namespace
github.com/vishvananda/netlink
n.nlHandle, err = netlink.NewHandleAt(sboxNs, syscall.NETLINK_ROUTE)
创建 NETLINK_ROUTE socket 操作 network device
libnetwork\osl\namespace_linux.go loopbackUp
iface, err := n.nlHandle.LinkByName("lo") 创建 loopback
dns
libnetwork\network.go CreateEndpoint
err = n.addEndpoint(ep)
调用相关 driver 的 CreateEndpoint
err = d.CreateEndpoint(n.id, ep.id, ep.Interface(), ep.generic)
libnetwork\endpoint.go Join
libnetwork\sandbox.go populateNetworkResources
libnetwork\sandbox_dns_unix.go startResolver
重要
resolverIPSandbox = "127.0.0.11"
err = sb.osSbox.InvokeFunc(sb.resolver.SetupFunc(0))
err = sb.resolver.Start()
libnetwork\resolver.go SetupFunc
参数 0 随机端口
r.conn, err = net.ListenUDP("udp", addr)
r.tcpListen, err = net.ListenTCP("tcp", tcpaddr)
libnetwork\resolver.go Start
err := r.setupIPTable()
libnetwork\resolver_unix.go setupIPTable
命令行调用参数 setup-resolver
libnetwork\resolver_unix.go reexecSetupResolver
github.com/miekg/dns
docker-proxy
libnetwork\drivers\bridge\bridge.go ProgramExternalConnectivity
network.allocatePorts(endpoint, network.config.DefaultBindingIP, d.config.EnableUserlandProxy)
libnetwork\portmapper\mapper.go MapRange
m.userlandProxy, err = newProxy(proto, hostIP, allocatedHostPort, t.IP, t.Port, pm.proxyPath)
libnetwork\portmapper\proxy_linux.go newProxyCommand
命令行启动 docker-proxy
实际环境观测
loopback
[root@computer02 /home/user_00]# docker ps | grep nginx
164b577c53df nginx-test:a35b0f87 "/docker-entrypoint.…" 2 days ago Up 2 days 0.0.0.0:80->80/tcp, 0.0.0.0:443->443/tcp nginx-test
[root@computer02 /home/user_00]# docker inspect --format '{{ .State.Pid }}' 164b577c53df
11297
[root@computer02 /home/user_00]# nsenter -t 11297 -n ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
279249: eth0@if279250: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 02:42:c0:a8:60:2c brd ff:ff:ff:ff:ff:ff link-netnsid 0
inet 192.168.96.44/20 brd 192.168.111.255 scope global eth0
valid_lft forever preferred_lft forever
dns
[root@computer02 /home/user_00]# nsenter -t 11297 -n netstat -lnp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 11297/nginx: master
tcp 0 0 127.0.0.11:34738 0.0.0.0:* LISTEN 1693/dockerd
udp 0 0 127.0.0.11:33184 0.0.0.0:* 1693/dockerd
[root@computer02 /home/user_00]# nsenter -t 11297 -n iptables -t nat -L
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
DOCKER_OUTPUT all -- anywhere 127.0.0.11
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
DOCKER_POSTROUTING all -- anywhere 127.0.0.11
Chain DOCKER_OUTPUT (1 references)
target prot opt source destination
DNAT tcp -- anywhere 127.0.0.11 tcp dpt:domain to:127.0.0.11:34738
DNAT udp -- anywhere 127.0.0.11 udp dpt:domain to:127.0.0.11:33184
Chain DOCKER_POSTROUTING (1 references)
target prot opt source destination
SNAT tcp -- 127.0.0.11 anywhere tcp spt:34738 to::53
SNAT udp -- 127.0.0.11 anywhere udp spt:33184 to::53
docker-proxy
相关 iptables 就不列了
[root@computer02 /home/user_00]# ps -aux | grep 192.168.96.44
root 10749 0.0 0.0 217044 3236 ? Sl Jan05 0:00 /usr/bin/docker-proxy -proto tcp -host-ip 0.0.0.0 -host-port 443 -container-ip 192.168.96.44 -container-port 443
root 10966 0.0 0.0 364508 3236 ? Sl Jan05 0:00 /usr/bin/docker-proxy -proto tcp -host-ip 0.0.0.0 -host-port 80 -container-ip 192.168.96.44 -container-port 80网络架构
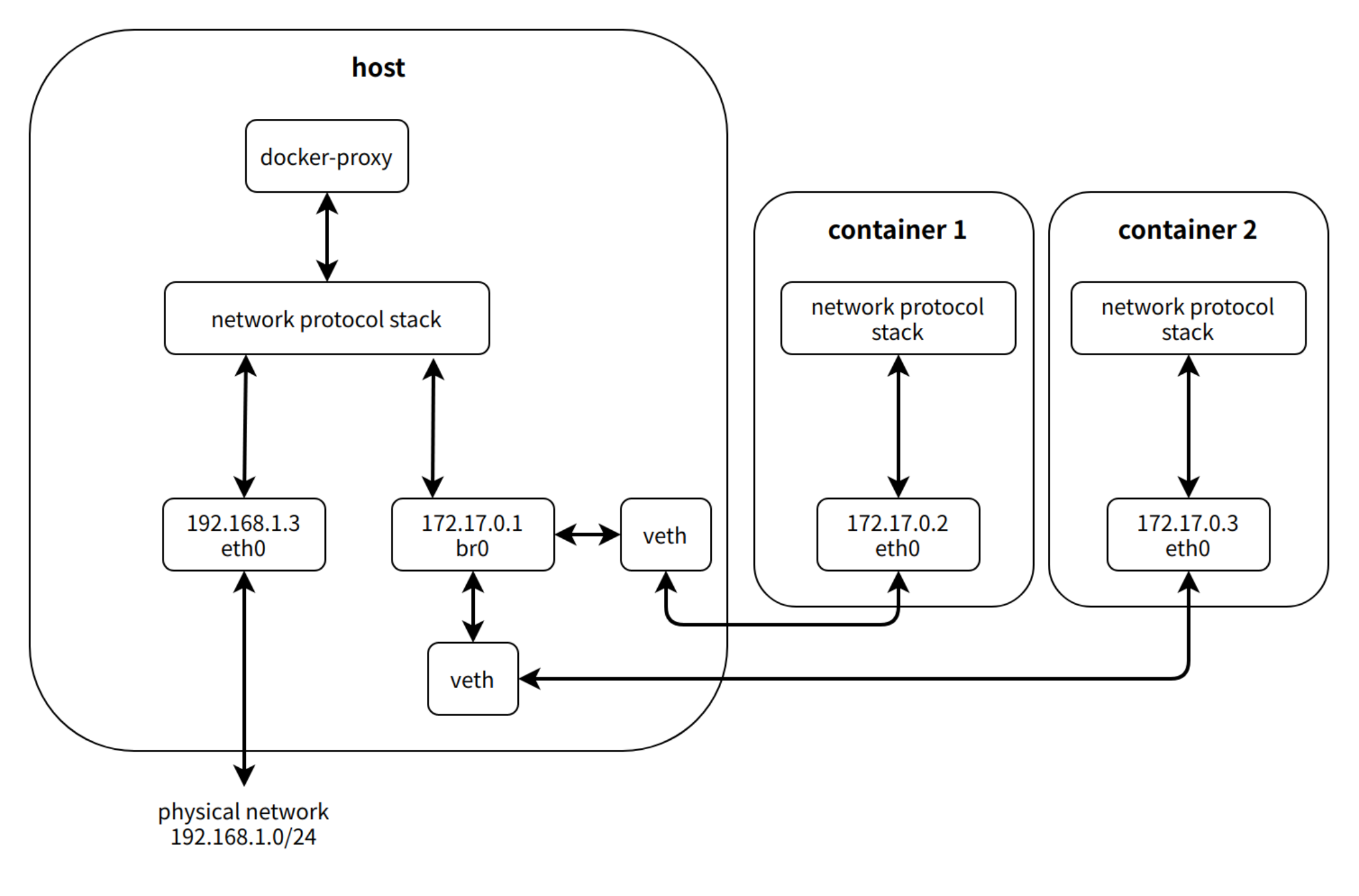
Linux 组件
bridge

veth






















 1475
1475

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








