0x01概况
为期4周的比赛,ak了密码部分
0x02题解
WEEK1
baBAbaseSEse
拿随波逐流解了几次就卡了,然后用bugku的工具箱解的
https://ctf.bugku.com/tool/base32
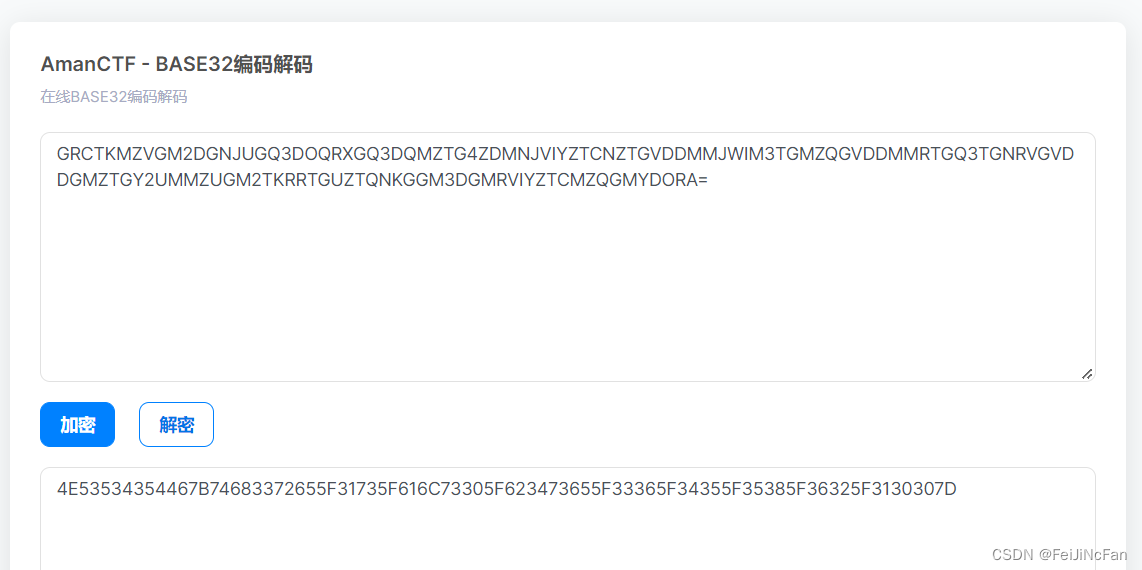
16进制转字符即可
A dictator
附件如下:
from random import randint
from secret import flag
offset = randint(1,100) % 26
# print(offset)
assert flag.startswith('NSSCTF{')
assert all([ord(c) not in range(ord('A'),ord('Z')) for c in flag[7:-1]])
for char in flag[7:-1]:
if ord('a') <= ord(char) <= ord('z'):
index = ord(char)-ord('a')
new_char = chr((index+offset)%26 + ord('a'))
print(new_char,end='')
else:
print(char,end='')
# lzw_uswksj_uahzwj_ak_gfw_gx_lzw_egkl_tskau_udskkausd_uahzwjk
new_char = chr((index+offset)%26 + ord(‘a’))
枚举下
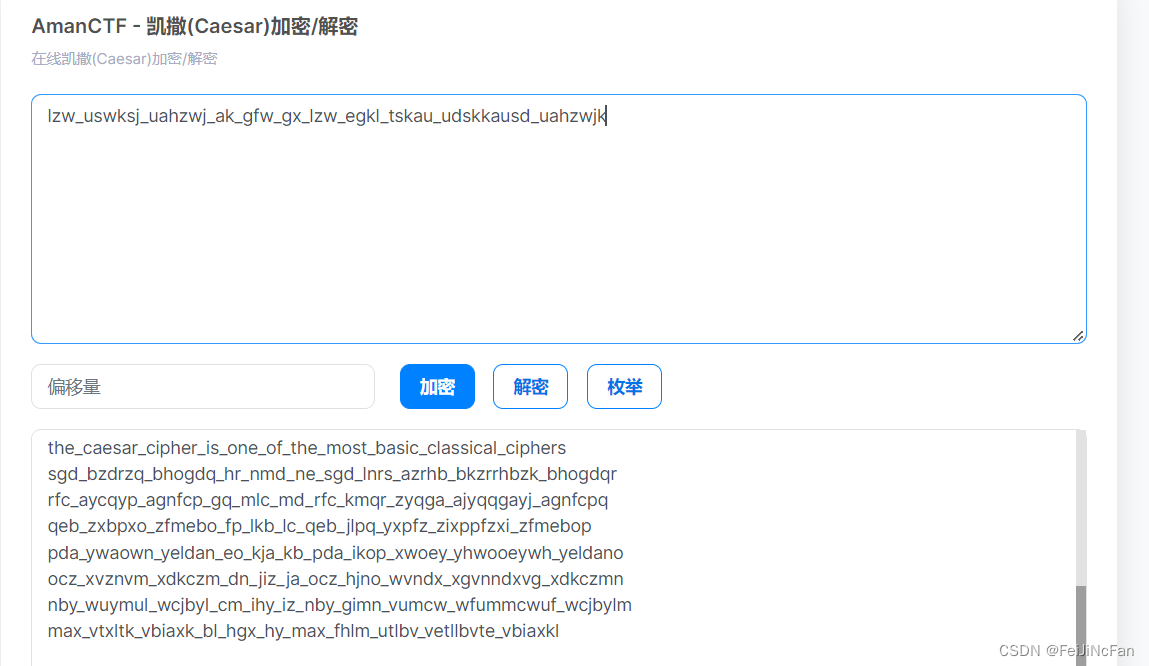
littleprince
task.py
from secret import flag
from Crypto.Util.number import *
from random import randint
def enc(a,b,c):
return a>>b|(a&((1<<b)-1))<<(c-b)
def outp(x,h):
p=randint(1<<h,1<<h+1)
q=randint(1<<h,1<<h+1)
c1,c2=x%p,x%q
print(p,q,c1,c2)
m=bytes_to_long(flag)
m_len=m.bit_length()
d,h,st=32,16,32
r=m_len%d
assert(r>h)
while st<=m_len:
x=enc(m,st,m_len)
x>>=(m_len-d)
outp(x,h)
st+=d
m>>=(m_len-r)
outp(m,h)
output.txt
58831 56263 46164 34042
55579 48157 2944 35950
35507 38933 1938 2559
63419 51803 24116 33843
40423 47237 20923 43307
33599 43441 4324 37076
43541 40771 42833 32799
54869 40031 21847 16617
48953 34841 36031 3788
34403 58271 12464 55665
33457 61463 3512 47396
53047 57283 185 38171
52583 59281 45851 38603
60727 58043 36261 37164
给了hint
hint:When we generate two numbers, there may be a coincidence that they are coprime.
求一下公约数,没有。中国剩余定理求一下
求出来的不对。之后改了下脚本,exp.py如下
from functools import reduce
from Crypto.Util.number import *
import gmpy2
def CRT(cipher, n):
N = reduce(lambda x, y: x * y, (i for i in n))
result = 0
data = zip(cipher, n)
for ci, ni in data:
Ni = N // ni
di = gmpy2.invert(Ni, ni)
result += ci * Ni * di
return result % N, N
with open("output.txt",'r') as f:
data = f.readlines()[::-1]
flag = b''
flag_bin=''
for t in data:
c_list = []
n_list = []
tmp = t.strip("\n").split(" ")
c_list.append(int(tmp[2]))
c_list.append(int(tmp[3]))
n_list.append(int(tmp[0]))
n_list.append(int(tmp[1]))
x, N = CRT(c_list, n_list)
print(int(x),long_to_bytes(int(x)))
if int(x) <618357700:
flag += long_to_bytes(int(x) + int(tmp[0])*int(tmp[1]))
else:
flag += long_to_bytes(int(x))
print(flag)
baby_rsa
task.py
from Crypto.Util.number import bytes_to_long, getPrime
from gmpy2 import *
from secret import flag
m = bytes_to_long(flag)
p = getPrime(128)
q = getPrime(128)
n = p * q
e = 65537
c = pow(m,e,n)
print(n,c)
# 62193160459999883112594854240161159254035770172137079047232757011759606702281
# 17331436837911040930486942133359735652484926528331507431552667656734821231501
n可以直接分解
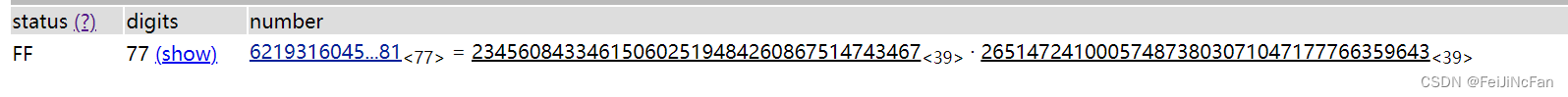
这里给一下网址
http://factordb.com/
你想学密码吗?
下载完,按附件的运行一下就行。
XXXOOORRR
task.py
from flag import flag
from Crypto.Util.number import *
import os
randBytes = [bytes_to_long(os.urandom(64)) for _ in range(3)]
m = bytes_to_long(flag)
print(f'a = {randBytes[0]}')
print(f'b = {randBytes[0] ^ randBytes[1]}')
print(f'c = {randBytes[1] ^ randBytes[2]}')
print(f'd = {m ^ randBytes[0] ^ randBytes[1] ^ randBytes[2]}')
'''
a = 1215421974111272707828609697064234072332368362928440865251897449605952163161176359366553487776268706107760670434157083936287598207881176904763353849369234
b = 10533604054267448009117468094542127075826310122733511023911022436253583775790861879410728001403728088545946257902341417532648419689212361977221573357292618
c = 6401236597601556248960570084212025183497657335932789785351897915858852832577623776212842429736547820800219382515052263929074210010546149322465536545021479
d = 5711309307698496426409561761492698639489294806611133698231840146911562848869711567477706456972659368849642409039245400981517493100724067475248620536111560
'''
按异或的特性,异或出m
from Crypto.Util.number import *
a = 1215421974111272707828609697064234072332368362928440865251897449605952163161176359366553487776268706107760670434157083936287598207881176904763353849369234
b = 10533604054267448009117468094542127075826310122733511023911022436253583775790861879410728001403728088545946257902341417532648419689212361977221573357292618
c = 6401236597601556248960570084212025183497657335932789785351897915858852832577623776212842429736547820800219382515052263929074210010546149322465536545021479
d = 5711309307698496426409561761492698639489294806611133698231840146911562848869711567477706456972659368849642409039245400981517493100724067475248620536111560
tmp = (d^a)^(a^b)^(a^b^c)
print(long_to_bytes(tmp))
爱妃
affine fx = ax + b
hint:a,m互质
这里没用hint,直接爆破出a,b
task.py
from secret import flag
from random import getrandbits
from string import *
def encrypt(message,a,b,m):
return bytes([(i*a+b)%m for i in message])
a,b = getrandbits(4),getrandbits(8)
print(f'c = {encrypt(flag,a,b,1<<8)}')
# c = b'y\xba\xba\xea\xc7\x11\xc2\xc7\xcb\xd8ZV\xd8ZVp\xb1\xb1\xd8\x19\xa4V\xa4\x19\x8aM\xa83g\xd8&\x19\xdc'
from random import getrandbits
def encrypt(message,a,b,m):
return bytes([(i*a+b)%m for i in message])
flag = b"NSSCTF{"
for a in range(0,1<<4):
for b in range(0,1<<8):
print(f'c = {encrypt(flag, a, b, 1 << 8)}',a,b)
c = b'y\xba\xba\xea\xc7\x11\xc2' 13 131
# get a,b
exp.py
import string
table = string.printable
a = 13
b = 131
c = b'y\xba\xba\xea\xc7\x11\xc2\xc7\xcb\xd8ZV\xd8ZVp\xb1\xb1\xd8\x19\xa4V\xa4\x19\x8aM\xa83g\xd8&\x19\xdc'
flag = ""
for t in c:
for f in table:
if (a*ord(f) + b) % 0x100 == t:
flag += f
# print(a,b)
print(flag)
WEEK2
littleLattice
Lattice入门题
task.py
from Crypto.Util.number import *
from hashlib import *
p = getPrime(2048)
f = getPrime(1024)
g = getPrime(768)
h = pow(f,-1,p)*g%p# h = (f**-1 * g)%p
verify = sha256(bytes.fromhex(hex(f+g)[2:])).hexdigest()
print(f'verify = {verify}')
print(f'p = {p}')
print(f'h = {h}')
print('NSSCTF{' + md5(bytes.fromhex(hex(f+g)[2:])).hexdigest() + '}')
'''
verify = 24425b693dbcace08a32572d499a5cbeb36e30db9278704195c67c3d32a81bdf
p = 29908110980126088961686288727545150169450107297750996656924523214377817308111189721234667959695817050736874247951762130190209278324144437406652857446810518839546701950883392761869656586963587376306050382973323860395932741791372333809871487575268245618618143456971257992301722141464238875859134379745122404533776003095129169004284619647906206323263396219776072091827094295366090100037898314156271404760715453914459484087562963158208356228410105170495322276351631637885450926240143055767142216931354736779666836018983658010126520397012025067407223630891975504746697630878807952266767406899527721170062789607980517722293
h = 26523576589113781532769165293024254940419790396713708680496148398686334583553504180195363282085884580924842673123375450894537445679687851322807762432476357713740302064160599132450619363411158141423252170448770929403179895813409897048848337375715079396639330537231353596884530617911351334318435031007342479134081403319324838464987064025256038807217697133175585927493402963025439540077915248356077623612217525231722274634984400273765262532561558296870531741633238736650375250957780701118781183335729715295271752736307479795186963108377228330313771245434127095507278278768792281414702334956407755841000748255424212840137
'''
=========================================================
s.sage
p = 29908110980126088961686288727545150169450107297750996656924523214377817308111189721234667959695817050736874247951762130190209278324144437406652857446810518839546701950883392761869656586963587376306050382973323860395932741791372333809871487575268245618618143456971257992301722141464238875859134379745122404533776003095129169004284619647906206323263396219776072091827094295366090100037898314156271404760715453914459484087562963158208356228410105170495322276351631637885450926240143055767142216931354736779666836018983658010126520397012025067407223630891975504746697630878807952266767406899527721170062789607980517722293
h = 26523576589113781532769165293024254940419790396713708680496148398686334583553504180195363282085884580924842673123375450894537445679687851322807762432476357713740302064160599132450619363411158141423252170448770929403179895813409897048848337375715079396639330537231353596884530617911351334318435031007342479134081403319324838464987064025256038807217697133175585927493402963025439540077915248356077623612217525231722274634984400273765262532561558296870531741633238736650375250957780701118781183335729715295271752736307479795186963108377228330313771245434127095507278278768792281414702334956407755841000748255424212840137
L = matrix(ZZ, [[1, h],[0, p]])
v = L.LLL()[0]
f, g = map(abs, v)
print(f,g)
print('NSSCTF{' + md5(bytes.fromhex(hex(f+g)[2:])).hexdigest() + '}')
Chaos
这题推了好长时间,最后拿了个二血
mix = lambda msg,k:''.join(reduce(lambda a,b:a+b,[[msg[j] for j in range(i[1],len(msg),len(k))] for i in [_ for _ in sorted(zip(k, range(len(k))))]]))
这个匿名函数研究一下,就可以模拟过程了
根据c 求出 时间t 注意zfill(20) 得到rnd 进一步得到经过128次排序后的flag 接下来就是根据mix函数得到flag 爆破即可
给一下脚本:
求出乱序flag
import random
from functools import reduce
with open("output",'rb') as f:
c = f.read()
print(c,len(c))
a = [0x66]*20
tm = c[33:]
print(len(tm))
res = [chr(a[0]^tm[i]) for i in range(20)]
print("".join(res))
print(len("001664636257.1991372"))
rnd =[67, 92, 185, 141, 226, 120, 177, 162, 89, 186, 84, 43, 126, 92, 182, 12, 49, 137, 155, 169, 164, 96, 137, 215, 60, 154, 99, 200, 38, 205, 169, 105, 6]
for i in range(len(rnd)):
print(chr(c[i] ^ rnd[i]),end="")
爆破出正确的flag
# !/usr/bin/env python
# -*- coding: utf-8 -*-
# @author: yjp
# @software: PyCharm
# @file: last_part.py
# @time: 2022-10-06 16:57
from functools import reduce
def mix(msg,k):
tmp = reduce(lambda a,b:a+b,[[msg[j] for j in range(i[1],len(msg),len(k))] for i in [_ for _ in sorted(zip(k, range(len(k))))]])
return ''.join(tmp)
from functools import reduce
def add(x, y) :
return x + y
sum2 = reduce(lambda x, y: x+y, [1,2,3,4,5])
from itertools import permutations
items = [1,2,3,4,5,6,7,8,9]
for p in permutations(items):
k = list(p)
# print(k)
msg = "NcnSmPiltSetTniFJw}akhtaC{_s_iu__"
res = []
for i in [_ for _ in sorted(zip(k, range(len(k))))]:
for j in range(i[1], len(msg), len(k)):
res.append(msg[j])
sum2 = reduce(lambda x, y: x + y, res)
enc = sum2
for i in range(128):
if "NSSCTF{" in enc:
print(enc)
enc = mix(enc,k)
RSA again
e1 = 3,直接开根
exp.py
n1 = 19920284552214772740140135352548541831031690920425912140961436065508824546041514076016684238261995522677433833330399269923572993489681770913908642529489382472548548664350078176417366141695108301338793624641102311886122714705781923892243561473766978666116035403145672686443197319003393949350402512739343998236331447680561106899174404316265329944969786438022711742891334905159259854026408058542492105569778656883811323759583727586331462200020945101286801110840081277963013591342157754264111051785385892113635682519079401538045775697382691195557344630571694510115674941400112478156619785019370731073096018975390492287333
n2 = 16329690193309629244191723145720681753145067517963214005637012320130767690248475184382159868590994476900972592910808281306311987027465355492106975220876976952805197358639881107619560544543352300924359258546945240852850094015390140482140815264345348655887196971643211396274684514779113163628885090661524523232327450873503097327714815509514869056066300689707819915660849896274673178482085029145101175879255721581466301617903290840675945809027289325795423671263820619585424051649443606301277124322653881307702397752575258862656767834175467463999624688529625582031941402015943516022965802189663157681884162493551612612033
e1 = 3
e2 = 65537
c1 = 1752041777918702842605810950957832076618830231626916748933875881505173164404519153781007066742915517004902508987841695668088780745675304779496841107726530280651344357647334690721873124324358539328142005709830859468027528835981960873390785515876157664035579935532043154959183555353553164481674735512873428044452976229459806219115571797514157279125
c2 = 13118485959563304540673377439664643422000629435115361166348221705991314239675693340024813013156594762061646798463551395329521013651893257141697813554253378348002502855822191264845788826850528723400519059095869424931054523865083127809240502348046515579012160733570975234405522250330692499687684922633627550243811524972452606330768418753137605045204137872122584136368073471612976975360656501198000053578279110813009137808852376287556012668702182416374333935081007133880603708035832346742292444210108820267460698390600228183548619401334969739679892562475501201965275739796687679445529050630235296740377171065357995433586
print(long_to_bytes(gmpy2.iroot(c1,3)[0]))
strange RSA
task.py
from Crypto.Util.number import *
from secret import flag
pad = lambda x:x + bytes([16 - len(x)%16] * (16 - len(x)%16))
m = bytes_to_long(pad(flag))
p = getPrime(100)
q = getPrime(100)
n = p*p*q*q
e = 0x10001
c = pow(m,e,n)
print(f'n = {n}')
print(f'c = {c}')
print(f'e = {e}')
'''
n = 564070152909085514893862673848191100242629745476416876533996976389897932324860687952230733393080567203972999049426141761
c = 269509453821913281608300827585653465889617103481995203776655691658799441157871331220899710463748827149644657719450056013
e = 65537
'''
p,q较小可直接分解
exp.py
from Crypto.Util.number import *
import gmpy2
n = 564070152909085514893862673848191100242629745476416876533996976389897932324860687952230733393080567203972999049426141761
c = 269509453821913281608300827585653465889617103481995203776655691658799441157871331220899710463748827149644657719450056013
e = 65537
p = 709662686105519282917793669093
q = 1058314117179226194777612760717
phin = p*q*(p-1)*(q-1)
d = gmpy2.invert(e,phin)
m = gmpy2.powmod(c,d,n)
print(long_to_bytes(m))
solve_the_equation
z3轻轻松松
task.py
from Crypto.Util.number import bytes_to_long, getPrime
from gmpy2 import *
from flag import flag
m = bytes_to_long(flag)
p = getPrime(2048)
q = getPrime(2048)
n = p * q
e = 65537
gift = 2022 * p + 9 * q + 28 * e
c = pow(m,e,n)
print(n,c,gift)
# 559013759419746202691240598235115105126834606071307611491891982898293133657843987454339580258031532272691584368719342942404675509580909313170933925796189789232538297110756754383546447669571766593521267667716779348776308179675709803388978100416839504625045239819627379469827980589668625084314985969634985583431058156810528172627873121320455715399011186280324236548934145366222271636328254497851289112650375015433741699898290781472376090171361276557886637892800404830030548291487615566596504234212554381817510798554015481259307992175226543595948798873846335558746933940683482819439715578130806800536423771482474206047548549237879025655562739463111822524633757040958223066367993671472508367287181357997804485542311011003871312708995599690715923692968372474814753669031805664070760705148563294700043336457334028810890271434599241312612447640877347296648737167576464851763570272180801042067934843953206083053874624644994067168364645748243999074053494066054657595233970985982095621265309066132852511490426399921749091156312387594448586826952283581592003247165562367202134878625798756167825941929996806801073247649667626854029875184014003650020610359836971629737204456239324237077361643697429780638179887750984791035339697744210904151734797
# 73407318923483936681380982096598838839602514018601041044571793373013418096970487001956204920233481604663088115926046001478564679328045899017826536373925483312496867862798918521256833686293905627264784839084309695013473729502056597198558911052248943918139429481528120149662544426266704140382476129564563832751550189116712164319522536680400998100426969878312141399338984622535922004572374724499994480294086487511972287034778386491943792466926044305651852709046949243652756946391206931252732067537917128777152678266816232179411054474713462051435447023851233892017069674808619784767176865947753180156093197684363218543237706358137237603822953178987601908200096630034921280599733190041134038060644827637374731999991143342404380959195318030935855850625849684867326087432054830971960076859722417639414733054394674533018860606074648324450983897579183842853010968597034663149214229791831193351337193195298921766564073265470525286769595835642479920483047959570057149110246705969802722576770273329236163660486942433423522588321736639231667766680582482974393228214947178327111783901303686854030864244720750585928819691608599558058859371899416709995780300197269497143959726959313506292966639680257096421491364629690813416340577056873916752193925
# 63829120016023768052886024054478552450378183173692549289836790500844466624984770449526584263524969873611417764466777251459739549064993441916734929304056657281688756040121378172997367361118927461471925755841160032723693319039128805185488328610549652307644061769088611063117016010827595409949224043526660999362737741312450095192593608666286680915796697255817583078927076945852260612453896867746751729217633935143780193497702898684210698859292191506586139420497299988065973759272644964857853100511651254633164029275099534568064491202987945733565755982565356202756330311841048849063747767451397616638500281324618902190280761
exp.py
from z3 import *
e = 65537
n = 559013759419746202691240598235115105126834606071307611491891982898293133657843987454339580258031532272691584368719342942404675509580909313170933925796189789232538297110756754383546447669571766593521267667716779348776308179675709803388978100416839504625045239819627379469827980589668625084314985969634985583431058156810528172627873121320455715399011186280324236548934145366222271636328254497851289112650375015433741699898290781472376090171361276557886637892800404830030548291487615566596504234212554381817510798554015481259307992175226543595948798873846335558746933940683482819439715578130806800536423771482474206047548549237879025655562739463111822524633757040958223066367993671472508367287181357997804485542311011003871312708995599690715923692968372474814753669031805664070760705148563294700043336457334028810890271434599241312612447640877347296648737167576464851763570272180801042067934843953206083053874624644994067168364645748243999074053494066054657595233970985982095621265309066132852511490426399921749091156312387594448586826952283581592003247165562367202134878625798756167825941929996806801073247649667626854029875184014003650020610359836971629737204456239324237077361643697429780638179887750984791035339697744210904151734797
gift = 63829120016023768052886024054478552450378183173692549289836790500844466624984770449526584263524969873611417764466777251459739549064993441916734929304056657281688756040121378172997367361118927461471925755841160032723693319039128805185488328610549652307644061769088611063117016010827595409949224043526660999362737741312450095192593608666286680915796697255817583078927076945852260612453896867746751729217633935143780193497702898684210698859292191506586139420497299988065973759272644964857853100511651254633164029275099534568064491202987945733565755982565356202756330311841048849063747767451397616638500281324618902190280761
# from z3 import *
# p = Int('p')
# q = Int('q')
# solver = Solver()
# solver.add(gift == 2022 * p + 9 * q + 28 * e )
# solver.add(n == p*q)
# if solver.check() == sat:
# m = solver.model()
# print(m) # 一元二次方程属于是
from Crypto.Util.number import *
import gmpy2
p = 31488299927163782375594305784598354985055343576902151378139638110290196067918972709864013036909993584566357500427488971564319756822589646977081872239028723217808372250207143372686512583814138881980368846428364451724191019810210583450208745323418623199057207740178726519465136933610452840086315545766227500114368026151391214297362847972215483754128409704386255997220347329566039222555930464490406419002226257326118774942404683970363544788642504594073256844610344691049585870560973659315882902006631997716334351866723219577903275769313404136367236735062099234386473703566068495328080598914833401280780692803508570349879
q = 17753062588733343270481973113408741177364273466266578137604693537521130628067514464616655876995871735360322066932727884076111196635241747675042626304508770586691927800281585936137657405193182456402216484778567926375452998098111716574027285177466244350043079827469560084278792340806640810521556665260999347942843603815228875925103340718552529438783648172063716949726071718858811605089496505238883332792493647818670062684514188459512366295227468596668231188353669195967903222039580635681985850471261694526218866731687175727118621937360285536800367141087950091875609247828705723374310716178275472084635608436063660110043
c = 73407318923483936681380982096598838839602514018601041044571793373013418096970487001956204920233481604663088115926046001478564679328045899017826536373925483312496867862798918521256833686293905627264784839084309695013473729502056597198558911052248943918139429481528120149662544426266704140382476129564563832751550189116712164319522536680400998100426969878312141399338984622535922004572374724499994480294086487511972287034778386491943792466926044305651852709046949243652756946391206931252732067537917128777152678266816232179411054474713462051435447023851233892017069674808619784767176865947753180156093197684363218543237706358137237603822953178987601908200096630034921280599733190041134038060644827637374731999991143342404380959195318030935855850625849684867326087432054830971960076859722417639414733054394674533018860606074648324450983897579183842853010968597034663149214229791831193351337193195298921766564073265470525286769595835642479920483047959570057149110246705969802722576770273329236163660486942433423522588321736639231667766680582482974393228214947178327111783901303686854030864244720750585928819691608599558058859371899416709995780300197269497143959726959313506292966639680257096421491364629690813416340577056873916752193925
phin = (p-1)*(q-1)
d = gmpy2.invert(e,phin)
m = gmpy2.powmod(c,d,n)
print(long_to_bytes(m))
hash
套题,4个for循环,拼接后的字符md5
# !/usr/bin/env python
# -*- coding: utf-8 -*-
# @author: yjp
# @software: PyCharm
# @file: exp.py
# @time: 2022-10-07 23:53
# nc 1.14.71.254 28575
import hashlib
import string
table = string.ascii_letters + string.digits
tmp = "fJTICilMLRzRFoMf"
# 1、待加密的字符串
for a in table:
for b in table:
for c in table:
for d in table:
str = a + b + c + d + tmp
# 2、实例化一个sha256对象
sha256 = hashlib.sha256()
# 3、调用update方法进行加密
sha256.update(str.encode('utf-8'))
# 4、调用hexdigest方法,获取加密结果
if sha256.hexdigest() == "512406195151b0b4aa44d1cbcf64db6615555b78f598d91ec7497a41e60862c2":
print(str)
break
# 结果为:
# 936a185caaa266bb9cbe981e9e05cb78cd732b0b3280eb944412bb6f8f8f07af
# nc 1.14.71.254 28826
S1mple_ECB
拿到的数据分成2组给服务器即可
a_big_water_problem
不止一个解
solve.sage
from Crypto.Util.number import *
from gmpy2 import *
# p = 1909085838901160004148366390307428971507303404468754423228343787769448200442038361348125740523088751663337211595662597150812621519152229037912543068209
# c = 1722797706292328891382841146705672635973386450156658022578860976717568774388136853606026526614826060041480340908970565567375361451272929245900841087253
#
# e = 2
# R.<x> = Zmod(p)[]
# f = x^e-c
# r1 = [int(i[0]) for i in f.roots()]
# print(r1)
m = [1909085838901160004148366390307428971507303404468754423225790958338228561363281269134920126915908258675394336152584408495192768869366046640978717105844, 2552829431219639078757092213205613607180492987942875443078188655619852649786182396933825962365]
for i in m:
# a = iroot(int(i),2)[0]
# print(long_to_bytes(a>>300))
print(long_to_bytes(i))
md5太残暴了
还是碰撞
直接给exp吧
import hashlib
import string
plaintext = "}{}{}_P4ssw0rd_N3v3r_F0rg3t_63{}{}{}{}{}"
res = "ac7f4d52c3924925aa9c8a7a1f522451"
t1 = string.ascii_uppercase
t2 = string.ascii_lowercase
t3 = string.digits
for a in t1:
for b in t2:
for c in t3:
for d in t3:
for e in t3:
for f in t3:
str = "flag{" + a+"00" + b + "_P4ssw0rd_N3v3r_F0rg3t_63" + c + d + e + f + "}"
if hashlib.md5(str.encode()).hexdigest() == res:
print(str)
break
mathRSA
task.py
from Crypto.Util.number import getPrime, bytes_to_long
from flag import flag
m = bytes_to_long(flag)
p = getPrime(512)
q = getPrime(512)
n = p*q
e = 0x10001
c = pow(m, e, n)
hint = p**5 - q**4
print(f"n = {n}")
print(f"e = {e}")
print(f"c = {c}")
print(f"h = {hint}")
print(f"f = {flag}")
"""
n = 76236418318712173274495941060488893810931309177217802334230599201457092723011685048556311576262486371987147895332408646920500226769161418792142565209634495797142268681403865426056588605013602625268553194169434049817172340173907696496945054049859221379092764811535206778031226535614731731322630330166833765943
e = 65537
c = 7207616060389865156270906240837846478541820008527247539698331406253371238674590766101711421196342768182325013873320402422918804780590951789425587131632422554819735000106070325708057225062376701298825910565526713270553888227235612227223162695870584803109353377288421750982913226189395526612487664144379690552
h = 130285072635228037239175162118613869214302695058325046962039091162567931492116336918638092534964417960274466351834311039222269165021532950982276262717322395682559639859781516047319178212473103057947426886870612637975024605166325017663998263834789814181250953051730859433354534450232382414565421858172075431133498326501045697132640582932453817599366612200146802110424409285814189125929844293789544163802323048780585398714263586547670912817768592459281775837372982750626103047573532664320692775783627129463700810934670066747044799514243631607384814191188276380589420289084574680852618867732847029105400406874790675559126905078326495799755425006555539699119063191489852930421412630857588890593040420277938268954008973405431053073576987401154763326417551463323055736754390446
"""
化简不了,直接z3
exp.py
# !/usr/bin/env python
# -*- coding: utf-8 -*-
# @author: yjp
# @software: PyCharm
# @file: exp.py
# @time: 2022-10-11 0:03
# hint = p**5 - q**4
from z3 import *
from Crypto.Util.number import *
import gmpy2
# p,q = Ints("p q")
# solver = Solver()
hint = 130285072635228037239175162118613869214302695058325046962039091162567931492116336918638092534964417960274466351834311039222269165021532950982276262717322395682559639859781516047319178212473103057947426886870612637975024605166325017663998263834789814181250953051730859433354534450232382414565421858172075431133498326501045697132640582932453817599366612200146802110424409285814189125929844293789544163802323048780585398714263586547670912817768592459281775837372982750626103047573532664320692775783627129463700810934670066747044799514243631607384814191188276380589420289084574680852618867732847029105400406874790675559126905078326495799755425006555539699119063191489852930421412630857588890593040420277938268954008973405431053073576987401154763326417551463323055736754390446
n = 76236418318712173274495941060488893810931309177217802334230599201457092723011685048556311576262486371987147895332408646920500226769161418792142565209634495797142268681403865426056588605013602625268553194169434049817172340173907696496945054049859221379092764811535206778031226535614731731322630330166833765943
# solver.add(hint == p**5 - q**4)
# solver.add(n == p*q)
# if solver.check() == sat:
# print(solver.model())
q = 7230753434414569972828808651891325142186523078619542872286840414394373161212272545789342965212718184298307353595004152854764254216044770456139231711296409
p = 10543357481374908938696626650832667304979816176891429562773232136754485382413647547320866232418359800743787286242710171986152592431595912519025867918658127
d = gmpy2.invert(65537,(p-1)*(q-1))
c = 7207616060389865156270906240837846478541820008527247539698331406253371238674590766101711421196342768182325013873320402422918804780590951789425587131632422554819735000106070325708057225062376701298825910565526713270553888227235612227223162695870584803109353377288421750982913226189395526612487664144379690552
print(long_to_bytes(gmpy2.powmod(c,d,n)))
WEEK3
后面难度增加了些
Binomials
考察多项式定理
task.py
from Crypto.Util.number import *
# from flag import flag
pad = lambda x:x + bytes([16 - len(x)%16] * (16 - len(x)%16))
flag = b''
p = getPrime(1024)
q = getPrime(1024)
N = p*q
m = bytes_to_long(pad(flag))
m1 = p+3*q
m2 = 3*p + 2*q
e1 = 0x10001
e2 = 0x65537
c = pow(m,e1,N)
c1 = pow(m1,e1,N)
c2 = pow(m2,e2,N)
print(f"N = {hex(N)}")
print(f"e1,e2 = {hex(e1)},{hex(e2)}")
print(f"c1,c2 = {hex(c1)},{hex(c2)}")
print(f"c = {hex(c)}")
'''
N = 0xa65149a38fe4784da050db9390c5cc5d4b9ef376b40e6919b487aadec0bd4c6e683205f3bf1d6bb51fceb9e14965305183229184ec69b4e22b467ad2c08337e81a54219dd40160c9d84a4abdf95e05121a11737570b0924ed8941390a3e1fae259f745b76f4a0a23ece5cbcbda5269d7312329b105cd255d2a2ffaf905d32b6b42e64f1bd67039f526789e9065b41a9426a1e9a6e65746af7c4ca343ddbf1392073b566a37c2e66edeef47ecc4629dee6fa4f5dc839ffa6b2647eb0b6dced42bff46653e7205bf37e89d4c417fd41cf8d315448e593f08e2d1e8d7c4b299ce35f59bf45830f9efdaaf51f726e4466ef0fb583d8c6285b6a04477eba429a7fb81
e1,e2 = 0x10001,0x65537
c1,c2 = 0xa371721c01ab221a30fcf761b3a22cff4cb3401eb76db69743cba2d24225fe3edf05053674039928cf3a2e1ddc58f03cc90c3837cd43281b228952d5c28c5798092550176362fe6474b2f7e8c3af328999688161322d218e39a168dea95c1581ad0c367ce969f1f6531fe12240417350d0b1c7c9b257d261c91548dff2a4f15678585745e0adf9215997dc590999feb03bd32889e92688d2d30ff73edcb67791726f9e0eac9480d48e4e37bfd268fd22200534ece8e3eb59504c8bb4aa6e7153c8476655ee01d5a624f77a6c5149eacd6783ce894798467b2ecefa4199ce40d009817053f6816d36c2dcf985092ef56f2589571fead26e15640add0bc1a885a6,0x2ce039abd666a05b18f2831caca34a6800c495e439553ef40ceed62e881bc23b69b8f7526b57fef2b5fe7299173e5c271e934cb9240b1b5b5a18590be50b6359f5cd08d08607aaa039a37eabebb722dcc85449e335f96d580f936ec9e406b0be5298f8b5244155534a15db5cc8f24abad4acb6bbb83095bd151ef9dd2102a81865e2bb7e705d7f1a8a39f51c3990e20740ff3724bd6c5d52098200a445bf604e477dc3f6e849d1e0021252c52755c8402601020041cdc6f2ffa4cc901ef5ef21e00417a2e586c7d66c65927b67c86f239abe6ee6456a122ef557812dafad26e00ef22069381b3a2755824a1e6e3eb3c5af62316adea1d9ecd64e4f06bbd8926d
c = 0x99b0b0a6a427ed9e3b757ed516f396e4f2f88712a6ff38b954d189aa46642e55fcf550f9e5b378523f98f969ba6a3e70baa13f71ca92b7d0bfc248b22b91ac586f48d930d5c8180acb466a438d4abe338d1fdb6e3521a1ffab07908882e6e245466de85b2469ba6d273a46672c151430a9d5cc0521bf6b648727d5f188662ee130315e92ded631b366de1302b7617b5d132d3732ff7f76c95e7bbbf8f6aca7b15c427b1814778cb5ab7d60b250a4ed718d9d72666220df76205d537fc2672bbf15ffe2c03bb92b2b6bec6ad1cd46862c6bdfa4b2d2c3ff09b5b2d68268078578d2404fdc61c71d7f3fc678530ebcd283ef5594c6ebe44ecd19ba70f517efe69b
'''
推导过程后面补上
exp.py
N = 0xa65149a38fe4784da050db9390c5cc5d4b9ef376b40e6919b487aadec0bd4c6e683205f3bf1d6bb51fceb9e14965305183229184ec69b4e22b467ad2c08337e81a54219dd40160c9d84a4abdf95e05121a11737570b0924ed8941390a3e1fae259f745b76f4a0a23ece5cbcbda5269d7312329b105cd255d2a2ffaf905d32b6b42e64f1bd67039f526789e9065b41a9426a1e9a6e65746af7c4ca343ddbf1392073b566a37c2e66edeef47ecc4629dee6fa4f5dc839ffa6b2647eb0b6dced42bff46653e7205bf37e89d4c417fd41cf8d315448e593f08e2d1e8d7c4b299ce35f59bf45830f9efdaaf51f726e4466ef0fb583d8c6285b6a04477eba429a7fb81
e1,e2 = 0x10001,0x65537
c1,c2 = 0xa371721c01ab221a30fcf761b3a22cff4cb3401eb76db69743cba2d24225fe3edf05053674039928cf3a2e1ddc58f03cc90c3837cd43281b228952d5c28c5798092550176362fe6474b2f7e8c3af328999688161322d218e39a168dea95c1581ad0c367ce969f1f6531fe12240417350d0b1c7c9b257d261c91548dff2a4f15678585745e0adf9215997dc590999feb03bd32889e92688d2d30ff73edcb67791726f9e0eac9480d48e4e37bfd268fd22200534ece8e3eb59504c8bb4aa6e7153c8476655ee01d5a624f77a6c5149eacd6783ce894798467b2ecefa4199ce40d009817053f6816d36c2dcf985092ef56f2589571fead26e15640add0bc1a885a6,0x2ce039abd666a05b18f2831caca34a6800c495e439553ef40ceed62e881bc23b69b8f7526b57fef2b5fe7299173e5c271e934cb9240b1b5b5a18590be50b6359f5cd08d08607aaa039a37eabebb722dcc85449e335f96d580f936ec9e406b0be5298f8b5244155534a15db5cc8f24abad4acb6bbb83095bd151ef9dd2102a81865e2bb7e705d7f1a8a39f51c3990e20740ff3724bd6c5d52098200a445bf604e477dc3f6e849d1e0021252c52755c8402601020041cdc6f2ffa4cc901ef5ef21e00417a2e586c7d66c65927b67c86f239abe6ee6456a122ef557812dafad26e00ef22069381b3a2755824a1e6e3eb3c5af62316adea1d9ecd64e4f06bbd8926d
c = 0x99b0b0a6a427ed9e3b757ed516f396e4f2f88712a6ff38b954d189aa46642e55fcf550f9e5b378523f98f969ba6a3e70baa13f71ca92b7d0bfc248b22b91ac586f48d930d5c8180acb466a438d4abe338d1fdb6e3521a1ffab07908882e6e245466de85b2469ba6d273a46672c151430a9d5cc0521bf6b648727d5f188662ee130315e92ded631b366de1302b7617b5d132d3732ff7f76c95e7bbbf8f6aca7b15c427b1814778cb5ab7d60b250a4ed718d9d72666220df76205d537fc2672bbf15ffe2c03bb92b2b6bec6ad1cd46862c6bdfa4b2d2c3ff09b5b2d68268078578d2404fdc61c71d7f3fc678530ebcd283ef5594c6ebe44ecd19ba70f517efe69b
from gmpy2 import *
print(gcd((pow(3,e1*e2,N)*pow(c1,e2,N)-pow(c2,e1,N))%N,N))
from Crypto.Util.number import *
q=152107131208559962666081321012383244988602947630529176450722212303209912807003109204173673723351078518713808877441201241521885258163159577205450770010453288581208278208476521790193971987154307237939354656019457830825620835974101871935531710721675893839674455533943096811136186649408275053809709682147892399347
p=N//q
phi=(p-1)*(q-1)
d=invert(e1,phi)
m=pow(c,d,N)
print(long_to_bytes(m))
Shift
伪造假的flag来模拟下shift过程
# 54683 3496092809 input
# 54621 3514344512 res
# 54683 3514344512
# 54745 3496092809
# 57287 4112227317 input
# 57225 4237651889 res 62
# 57287 4237651889
# 57349 4112227317
最后可以发现 input出现在res的前62个地方
# !/usr/bin/env python
# -*- coding: utf-8 -*-
# @author: yjp
# @software: PyCharm
# @file: test.py
# @time: 2022-10-14 19:34
flag = b'nssctf{4514aaaaaaaaaaaaaaaaaaaaaaaaaaaaazzzzzzzzzzzzzzz12345678}' # 64byte = 512 bits
m = []
# flag = int.from_bytes(flag,'big')
# while flag:
# m.append(flag & 0xffffffff)
# flag >>= 32
# print(m)
# encflag=[54944101, 2631583238, 3136570822, 4270135104, 4270135104, 4270135104, 2826876565, 2826876565, 2826876565, 2826876565, 2826876565, 2826876565, 2826876565, 1579526594, 3430236210, 90571546] 16
from Crypto.Util.number import *
def Shift(y):
y = y ^ y >> 11
y = y ^ y << 4 & 2636928640
y = y ^ y << 5 & 4022730752
y = y ^ y >> 14
return y&0xffffffff
def Encode(msg):
enc = msg
for i in range(0,114514):
enc = Shift(enc)
print(i,enc)
return enc
def Decode(msg):
res_dict = {}
enc = msg
for i in range(0,114514):
enc = Shift(enc)
res_dict[i] = enc
index = check(res_dict,msg)
return res_dict[index + 62]
def check(res_dict,msg):
for i in range(0, 114514):
if res_dict[i] == msg:
break
return i
if __name__ == '__main__':
res = []
data = [3496092809, 3496092809, 3496092809, 4112227317, 230793617, 17662838, 2170352847, 2484065947, 3309324691,
3435226108, 1990056851, 2743015085, 2738150252, 3050712017, 3787180668, 2621989131][::-1]
flag = b""
for t in data:
tmp = Decode(t)
# print(long_to_bytes(tmp))
flag += long_to_bytes(tmp)
res.append(tmp)
print(flag)
# 54683 3496092809 input
# 54621 3514344512 res
# 54683 3514344512
# 54745 3496092809
# 57287 4112227317 input
# 57225 4237651889 res 62
# 57287 4237651889
# 57349 4112227317
AnyoneIsOk
开始一直解不出来
给了hint
hint:from Crypto.Cipher import PKCS1_OAEP
原来一直做的是无padding的
下面给出读取文件和解出flag的脚本
import Crypto.PublicKey.RSA as rsa
import gmpy2
from Crypto.Util.number import *
from Crypto.Cipher import PKCS1_OAEP
e = 65537
n_list = [0]*100
c_list = [0]*100
for i in range(0,100):
with open("./attachment/{}.pem".format(i+1), 'rb') as x:
public_key = rsa.importKey(x.read())
n_list[i] = public_key.n
# print(public_key.e)
with open("./attachment/msg{}".format(i+1),"rb") as f:
c = f.read()
c_list[i] = bytes_to_long(c)
for i in range(0,99):
for j in range(i+1,100):
if(gmpy2.gcd(n_list[i],n_list[j]))!=1:
common_f = gmpy2.gcd(n_list[i],n_list[j])
n = n_list[j]
q = n // common_f
d = gmpy2.invert(e,(q-1)*(common_f-1))
c = long_to_bytes(c_list[j])
privkey = rsa.construct((int(n), int(e), int(d), int(q), int(common_f)))
key = PKCS1_OAEP.new(privkey)
flag = key.decrypt(c)
print(flag)
s1mple_block
交互题
task.py
import socketserver
import os, sys, signal
import string, random
from hashlib import sha256, md5
from secret import flag
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad,unpad
KEY = md5(os.urandom(2)).digest()
def decrypt(ciphertext:str,key):
try:
ciphertext = bytes.fromhex(ciphertext)
key = bytes.fromhex(key)
cipher = AES.new(key, AES.MODE_ECB)
decrypted = cipher.decrypt(ciphertext)
except ValueError as e:
return str(e)
return decrypted.hex()
def encrypt(plaintext:str):
try:
if len(plaintext) % 32 != 0:
plaintext = pad(bytes.fromhex(plaintext),16)
else:
plaintext = bytes.fromhex(plaintext)
cipher = AES.new(KEY, AES.MODE_ECB)
encrypted = cipher.encrypt(plaintext)
except ValueError as e:
return str(e)
return encrypted.hex()
class Task(socketserver.BaseRequestHandler):
def _recvall(self):
BUFF_SIZE = 2048
data = b''
while True:
part = self.request.recv(BUFF_SIZE)
data += part
if len(part) < BUFF_SIZE:
break
return data.strip()
def send(self, msg, newline=True):
if type(msg) is str:
msg = msg.encode()
try:
if newline:
msg += b'\n'
self.request.sendall(msg)
except:
pass
def recv(self, prompt=b'> '):
self.send(prompt, newline=False)
return self._recvall()
def close(self):
self.send(b"Bye~")
self.request.close()
def proof_of_work(self):
random.seed(os.urandom(8))
proof = ''.join([random.choice(string.ascii_letters+string.digits) for _ in range(20)])
_hexdigest = sha256(proof.encode()).hexdigest()
self.send(f"sha256(XXXX+{proof[4:]}) == {_hexdigest}".encode())
x = self.recv(prompt=b'Give me XXXX: ')
if len(x) != 4 or sha256(x+proof[4:].encode()).hexdigest() != _hexdigest:
return False
return True
def handle(self):
if not self.proof_of_work():
return
self.send("Encrypt_FLAG: " + encrypt(flag.hex()))
while 1:
data,key = self.recv(prompt=b'Data to decrypt:').strip().split(b'||')
self.send(decrypt(data.decode(),key.decode()))
self.close()
class ThreadedServer(socketserver.ThreadingMixIn, socketserver.TCPServer):
pass
class ForkedServer(socketserver.ThreadingMixIn, socketserver.TCPServer):
pass
if __name__ == "__main__":
HOST, PORT = '0.0.0.0', 10000
server = ForkedServer((HOST, PORT), Task)
server.allow_reuse_address = True
server.serve_forever()
# nc 1.14.71.254 28209
直接爆破
exp.py
# !/usr/bin/env python
# -*- coding: utf-8 -*-
# @author: yjp
# @software: PyCharm
# @file: exp.py
# @time: 2022-10-14 20:46
from pwn import *
import hashlib
import string
import re
table = string.printable
from Crypto.Util.number import *
def prof_work(tmp,prof):
table = string.ascii_letters + string.digits
# 1、待加密的字符串
for a in table:
for b in table:
for c in table:
for d in table:
Str = a + b + c + d + str(tmp)[2:-1]
# 2、实例化一个sha256对象
sha256 = hashlib.sha256()
# 3、调用update方法进行加密
sha256.update(Str.encode('utf-8'))
# 4、调用hexdigest方法,获取加密结果
if sha256.hexdigest() == str(prof)[2:-1]:
return a + b + c + d
def get_key(i,j):
res = table[i] + table[j]
return res
context.log_level = "debug"
p = remote("1.14.71.254",28437)
data = p.recvline()
flag_part = data[12:28]
prof = data[-65:-1]
payload1 = prof_work(flag_part,prof)
p.sendlineafter("XXXX: ",payload1)
data = p.recvline()
# print(data)
i,j = 77,48
enc_data = str(data[-65:-1])[2:-1]+"||"
# print(enc_data)
key = hashlib.md5(get_key(i,j).encode()).hexdigest()
payload2 = enc_data + key
p.sendlineafter("Data to decrypt:",payload2)
flag_str = p.recvline()
# flag_str -> hex
if long_to_bytes(int(flag_str,16)) in b'flag{' or long_to_bytes(int(flag_str,16)) in b'nssctf{' or long_to_bytes(int(flag_str,16)) in b'NSSCTF{':
print(long_to_bytes(int(flag_str,16)))
i, j = 77, 49
while 1:
key = hashlib.md5(get_key(i, j).encode()).hexdigest()
j += 1
if j ==len(table):
i += 1
j = 0
print(i,j)
payload2 = enc_data + key
p.sendlineafter("Data to decrypt:",payload2)
flag_str = p.recvline()
print(long_to_bytes(int(flag_str, 16)))
if long_to_bytes(int(flag_str, 16)) in b'flag{' or long_to_bytes(int(flag_str, 16)) in b'nssctf{' or long_to_bytes(int(flag_str, 16)) in b'NSSCTF{':
print(long_to_bytes(int(flag_str, 16)))
break
Base42?
肯定不是base。需要看懂他的加密过程
btl = lambda a:sum((v*256**i)for i,v in enumerate(a[::-1]))
while len(flag) > 0:
val = btl(flag[:21])
# print("val=>",bin(val))
flag = flag[21:]
chunk = ''
while len(chunk)<32:
chunk += alphabet[val%len(alphabet)]
val //= len(alphabet)
out += chunk[::-1]
btl 从二进制的形式来看就是累加一个数然后把结果向高位移8位,也就是说flag的每一位可以对应val二进制形式的8位。
while len(chunk)<32:
chunk += alphabet[val%len(alphabet)]
val //= len(alphabet)
按照这个过程逆一下即可
s.py
alphabet = "0123456789aAbBcCdDeEfFgGhHiIjJkKlLmMnNoOpP"
out = ""
btl = lambda a:sum((v*256**i)for i,v in enumerate(a[::-1])) #abc => cba abc
def so_btl(a):
sum = 0
for i, v in enumerate(a[::-1]):
print(i,bin(v))
sum += v*256**i
print(bin(sum))
return sum
if __name__ == '__main__':
alphabet = "0123456789aAbBcCdDeEfFgGhHiIjJkKlLmMnNoOpP"
alphabet_dict = {}
for a, b in enumerate(alphabet):
alphabet_dict[b] = a
val = 0
flag_all = "0gpnO5ffI310EEjF3LeHCf7LC7HnfhIN0LMK1E79Gdf1dFCN93nBL35eJfKMhkAM000000000000000008fb46HFH4pA4GKI"
flag = b""
for i in range(3):
for f in flag_all[i*32:i*32+32]:
val = val * 42 + alphabet_dict[f]
flag += long_to_bytes(val)
val = 0
print(flag)
many_factors
task.py
from Crypto.Util.number import *
from flag import flag
n = 1
for i in range(60):
f = getPrime(10)
n *= f
e = 65537
c = pow(bytes_to_long(flag.encode()), e, n)
# print(f"flag = {flag}")
print(f"e = {e}")
print(f"n = {n}")
print(f"c = {c}")
"""
e = 65537
n = 36618139579386063246087882054063631367923586826293230665209915187491823328978276724908066032487515386697740611819366867179565337532194305783987450587518624526250530134446397
c = 3053043969587277731075013823380664207370991627277672374256662715889363487017560381573682876563907215099359894935326265406537547932246927604121814198201993671878573628633125
"""
拿到网站上分解一下,然后手改。sage应该有直接求欧拉函数的函数
exp.py
from Crypto.Util.number import *
import gmpy2
n = 521**3 * 541 * 547 * 557**2 * 577 * 587 * 593 * 601 * 607 * 631**4 * 641 * 643 * 683 * 701**2 * 719 * 727**3 * 733 * 739**2 * 743 *757 * 761 * 769 * 773 * 787*2 * 809 * 821**3 * 863 * 877**2 * 881 * 907**5 * 919**2 * 929 * 937 * 953**2 * 967**2 * 991 * 997**2 * 1019
c = 3053043969587277731075013823380664207370991627277672374256662715889363487017560381573682876563907215099359894935326265406537547932246927604121814198201993671878573628633125
e = 65537
phin = 521**2*520*540*546*557*556*576*586*592*600*606*630*631**3*640*642*682*700*701*718*727**2*726*732*739*738*742*756*760*768*772*787*786*808*821**2*820*862*877*876*880*907**4*906*919*918*928*953*952*966*967*990*997*996*1018
d = gmpy2.invert(e,phin)
m = gmpy2.powmod(c,d,n)
print(long_to_bytes(m))
babyCBC
字节反转攻击
hint:https://ctf-wiki.org/crypto/blockcipher/mode/cbc/#_8
查看源码后可知要使解密后的明文有Admin
下面是修改Guest的脚本
part1.py
import json
import time
import binascii
from Crypto.Util.Padding import pad,unpad
from Crypto.Cipher import AES
key = b'tb\x01\xb7\xe4Vry\xa9+\xeaA\xc9k\x98\x96\xd0\x05%\xc0>m\xa6\xb9B\x93$\x065\xa6\x12\x82'
iv = b'U\x14$\xe8A1\xf56\x15\xd9%3J\xc9\xeci'
plaintext = 'flag{1114514111111111111111111111111111111111111111111}'
payload = {'permission':'Guest','Time':f'{time.time()}','data':plaintext}
payload = pad(json.dumps(payload).encode(),16)
print(payload)
cipher = AES.new(key, AES.MODE_CBC, iv)
encrypted = cipher.encrypt(payload)
print()
data = encrypted.hex()
data = binascii.unhexlify(data)
cipher = list(data)
idx = 0
cipher[idx + 0] = cipher[idx + 0] ^ ord('G') ^ ord('A')
cipher[idx + 1] = cipher[idx + 1] ^ ord('u') ^ ord('d')
cipher[idx + 2] = cipher[idx + 2] ^ ord('e') ^ ord('m')
cipher[idx + 3] = cipher[idx + 3] ^ ord('s') ^ ord('i')
cipher[idx + 4] = cipher[idx + 4] ^ ord('t') ^ ord('n')
encrypted = bytes(cipher).hex()
print(encrypted)
ciphertext = bytes.fromhex(encrypted)
cipher = AES.new(key, AES.MODE_CBC, iv)
decrypted = unpad(cipher.decrypt(ciphertext),16)
print(decrypted)
# nc 43.143.7.97 28337
# a = {'permission':' len(a) == 16
之后发送回去decrypted
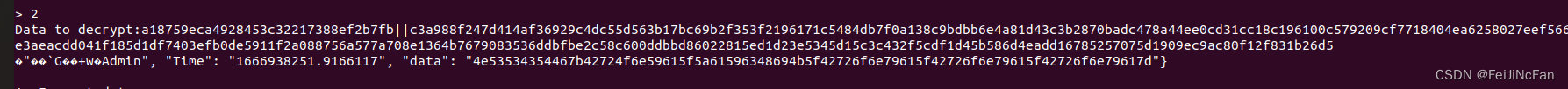
将16进制转为字符即可
partialP
这个的话coppersmith简单使用
已知p高位
task.py
from Crypto.Util.number import *
import uuid
p = getPrime(512)
q = getPrime(512)
n = p*q
e=65537
flag = "flag{"+str(uuid.uuid4())[:20]+"}"
m = bytes_to_long(flag.encode())
assert(m<n)
c=pow(m,e,n)
print(f"h = {((p>>128)<<128)}")
print(f"e = 65537")
print(f"c = {c}")
print(f"n = {n}")
"""
h = 9605964225476901441398365225327926616880072280289780777971846998748464126891804587377933727304510424852546683782576240573278202121547956666293242671661056
e = 65537
c = 2226099021169425534206121605501718994593261953280046899345810118356590881389142531649792348146129153474985003929407172972982275439970723778495455838452638879586163957468972518078320159354264971816842073874550773309020013613432004074760802192607651584906352686468143648939740004838208640531785439362344039075
n = 96928253979490973984593903132811649229014718994486532280648145898877952846656019305217095845257550421730063527538581223570539203247068060192535543753763017716750817560470547219370972835770943358384150269303529653434434525449357699107332781898776312692702549420939758722366794431784782973884379040574148608179
"""
s.sage
# !/usr/bin/env python
# -*- coding: utf-8 -*-
# @author: yjp
# @software: PyCharm
# @file: exp.py
# @time: 2022-10-17 19:52
from Crypto.Util.number import *
import gmpy2
# p = 9605964225476901441398365225327926616880072280289780777971846998748464126891804587377933727304510424852546683782576240573278202121547956666293242671661056
n = 96928253979490973984593903132811649229014718994486532280648145898877952846656019305217095845257550421730063527538581223570539203247068060192535543753763017716750817560470547219370972835770943358384150269303529653434434525449357699107332781898776312692702549420939758722366794431784782973884379040574148608179
e = 65537
c = 2226099021169425534206121605501718994593261953280046899345810118356590881389142531649792348146129153474985003929407172972982275439970723778495455838452638879586163957468972518078320159354264971816842073874550773309020013613432004074760802192607651584906352686468143648939740004838208640531785439362344039075
# kbits = 128
# PR.<x> = PolynomialRing(Zmod(n))
# f = x + p
# x0 = f.small_roots(X=2^kbits, beta=0.4)[0]
# print("x: %s" %hex(int(x0)))
# p = p+x0
# print("p: ", hex(int(p)))
# assert n % p == 0
# q = n/int(p)
# print("q: ", hex(int(q)))
p= 0xb768f99e33a5d8e8a3e1d4b605638b7a5f447e35d232c6b237b8ae4ec9bb417e36a09906d064cd8af7505f50d716460fc4e96336e8ca5b2fb9dfe9078c4c34ab
q= 0xc0a8f755654474cfba542d5568477f452d4a95ed1e646004b1dc91fdb17b5fbd3e77f84d4a25f73d0e0ef72e295743e90cea7e5e128638529b031e6c12681419
d=gmpy2.invert(e,(p-1)*(q-1))
print(long_to_bytes(gmpy2.powmod(c,d,n)))
pnearq
注意到get_nextprime() p,q接近 直接拿yafu分解
exp.py
from Crypto.Util.number import *
import gmpy2
p = 139362494120072096065216081618966249746574239262460284744468865719850996551067753709694109554061693572089871188264746799340636786772313403025084938651609422567995344046775583983367311974802321610889005077947700976481552283896499334735377828779462799614319016720722734724022186712293418763283488943785244226387
q = 139362494120072096065216081618966249746574239262460284744468865719850996551067753709694109554061693572089871188264746799340636786772313403025084938651609422567995344046775583983367311974802321610889005077947700976481552283896499334735377828779462799614319016720722734724022186712293418763283488943785244226299
n = 19421904767367129549329507820147867763064747101931314714173717122035977491291441314433180813343755107381230481007143328156292096871675328839756035726106037229325380698967544660649710464634698425387682458721466040894830503881966355435442651493212040443436714597490121865537266815247879839020846287255634123530517095030752832857842819836940083915495464712363169428825344678729929317207583197980607919720642725221740680718976635305544368542563503440076036727388062097647374046378854873864505267644315352602271587283702733779081805129429479541906613334092422428543951370065910195162721686773383508480268145903016615151713
c = 16430654037742749931837577925393394466626615745270895225352757745284038922799868617243616416116392338428121605256850230862894296244375242336599929497221079420665154174930054597666915358687410522457846003186806053368237783147731665147575913322026626738697036282908055611350347494310666532700194563684837580022875526378181343082801716942536163583090541294011987732281942148455345223347021675781368596340860151253774597168954881987520338304516390785094435356412111780768446904948045448510663589654475221029009283144829902553888829840193614048967712676048740814622290029846433107762872806981599110271586325156855299974310
print(long_to_bytes(gmpy2.powmod(c,gmpy2.invert(65537,(p-1)*(q-1)),n)))
smallRSA
p = getPrime(100)
q = getPrime(100)
直接分解
exp.py
# !/usr/bin/env python
# -*- coding: utf-8 -*-
# @author: yjp
# @software: PyCharm
# @file: exp.py
# @time: 2022-10-17 20:01
from Crypto.Util.number import *
import gmpy2
p = 768780063730500942699787302253
q = 813910604866037851538498611597
n = 625718246679843150194146350359795658237410693353450690028041
c = 118795719073790634455854187484104547013000179946116068066473
e = 65537
print(long_to_bytes(gmpy2.powmod(c,gmpy2.invert(e,(p-1)*(q-1)),n)))
AES
ECB模式
可以用前一个分组的密文当作key来解下一个分组的密文,这样得到的明文是部分flag,拼接即可
exp.py
from Crypto.Cipher import AES
ct = b'\x179\xb8l\x97\xbew\xc2\xd5f~\x8e\xdc\xf2\x9b\xabR\xa9a\xd2\xf4\xde\xd6|\xd1\x9f\xe9q\x1d\xfcm\xfbj\xe9\x9e\xab\xf5fL\xb3\xb5_\xa5\x16\x8e\x7f\x9fV`\x8b\x16\xa1\xa6)\x08\x97\x91\xbd3\x1d\xeb\\\x86\xa2\xd6\x94>\xf3\xfdt\xd9\x14\xf3\xfc\xe2\x02\xd6\xc4\xcfq"\x1a\x14~2]4\x9f\xc9\x88\xf8\x12\xb6\xa2\xd7\xec\x0b\x7f\xd4d\xdc\xc6\xb4]\x10u\xc6f\x97m\xccA\x82\x02\xa5gh\x85\x85Wz\xd9.\xff\x9bx\x99J\x0e\x86\x16\x90\xad\x1e\x17\x86\x95\xb8S\x17\xea\x93v\xd0'
out = []
for i in range(len(ct)//16):
key = ct[16*i:16*i+16]
cipher = AES.new(key, AES.MODE_ECB)
next = cipher.decrypt(ct[16*i+16:16*i+32])
out.append(next)
key = next
print(out)
[b'45e4-11ed-bba0-2', b'8d0eab06969}NSSC', b'TF{07104f28-45e4', b'-11ed-bba0-28d0e', b'ab06969}NSSCTF{0', b'7104f28-45e4-11e', b'd-bba0-28d0eab06', b'969}\x0c\x0c\x0c\x0c\x0c\x0c\x0c\x0c\x0c\x0c\x0c\x0c', b'']
WEEK4
终于要结束了,感觉学到不少东西。
random
伪随机数预测。
这里贴一下学习链接
https://blog.csdn.net/m0_62506844/article/details/124278580
用到rankcrack 但是我github上没搜到这个仓库,直接pip也能装上
exp.py
from randcrack import RandCrack
rc = RandCrack()
with open("output.txt",'r') as f:
data = f.readlines()
for i in range(624):
rc.submit(int(data[i]))
for i in range(666-624):
this_num = rc.predict_randrange(0, 4294967295)
print(this_num)
this_num = rc.predict_randrange(0, 4294967295)
print(this_num)
c = '91fd1824ddc0a35e845e87f59e53a103334df418e6a65a7d7769699c3ca2119019361cd23a46a61d4e7f6cdff5f5200f586f90b66eabfd8ecff4ddf11ee444d37f80ada0bbe8af09e4fc32c1a51e3f29e2771b51c71d2ba4acb84fda61904b96'
iv = bytes.fromhex(c[:32])
r = this_num
key = bytes.fromhex(hex(r)[2:])
key = md5(key).digest()
cipher = AES.new(key,AES.MODE_CBC,iv)
print(cipher.decrypt(bytes.fromhex(c[32:])))
square
e = 16
直接求出所有可能的根,然后解密成明文即可
from Crypto.Util.number import *
from gmpy2 import *
# n = 0xcaea4e2db0dc68029999cdad792fa1f9142117163af28f3230f7500ef748841554141ef35555ba23b95dc87f4c83f75dad14b6204dd4907fb75650fa7799def911f077b945f359e345bb9350c4a8268906c547e95e5819ef44ff124566a88fa2174ddfe3e895016df0036b59a50c6efb78724bde5d16a8a5cae45c918f329e462d10abe56ecdfae95bd13665260d0e8b648540d11f2447eef9aef3ea370faaecaab4c82ec1fe2bc83f2ce1b2793d95187eb2637e75700ba9745c253e928a4a603139dbf6b8bbf8111900a58be21a269992a9744c0284cf8f3ad7a3b95106d17af6baceac1acf543e425dc6317ab7f799a8ce19633b22e709eacb5d74ce4b56f9
# c = 0x2700a92e463d1c5da073b38d075a2da57c89ff9d658066c0bd38391cc60259a4fc992f1a6f1c5756d6e5934831fc0fbf7bfd85607f0d18781d30a4ab485e119af4f08b5fe7bf927aeaf7572b05dfec764d6ddda2b247b9f6b731300ece4209606d94c5708388d6e8efc1fa6e9c0cdda41cee95eb4a6b053b862fc43e55648973863f9874ee79ce4408277c9dc38fb26b44880e58f054b957c64fcf0d39c1fd496ad2fc5f5e5e70ba41422a4d945da299b5a695a4b7013a1f9ae1b629e395ffb0942d783d6e6be1f0888dfcb02d0aa1e9b7076e952a339bdc60f044f598afa2da28a4d7f094b959c8a8fefd5a11d10971cd681722f6868cf15a200cb910c591e1
#
# c= 0x2700a92e463d1c5da073b38d075a2da57c89ff9d658066c0bd38391cc60259a4fc992f1a6f1c5756d6e5934831fc0fbf7bfd85607f0d18781d30a4ab485e119af4f08b5fe7bf927aeaf7572b05dfec764d6ddda2b247b9f6b731300ece4209606d94c5708388d6e8efc1fa6e9c0cdda41cee95eb4a6b053b862fc43e55648973863f9874ee79ce4408277c9dc38fb26b44880e58f054b957c64fcf0d39c1fd496ad2fc5f5e5e70ba41422a4d945da299b5a695a4b7013a1f9ae1b629e395ffb0942d783d6e6be1f0888dfcb02d0aa1e9b7076e952a339bdc60f044f598afa2da28a4d7f094b959c8a8fefd5a11d10971cd681722f6868cf15a200cb910c591e1
# e = 16
# R.<x> = Zmod(n)[]
# f = x^e-c
# r1 = [int(i[0]) for i in f.roots()]
# print(r1)
m_list = [25615677894578755047156343445844436265410029831929516816331615976442311723531561327119120421902137698702653352454485089340848821437391616202141872920071595012903043917129450415132281907851460389644978646684609345443875666422198491448869630433730250869349508030370580903892239207884756374806258109492943540694025256336359221536523445463701649424494112650847740223587312753305758484739299091282445005021428673424732397006712358416313791876278338631941370485282183820941394817190803527812730459595063525543676864011831621261546685501816080758863765608285760956408604370742317675113279260023090820056964546946448729327594, 24072367155045049121538350559452436123760625674850036887400917611963001043425277658590765669098038279032511209656766731851112555056082333560946068560958136635450354184400845466823159542498565735578284414677938847565345435268619941467830506642234170223615472540060479482250736366661339782825842222750498295373524349825492103059453842032165892523230350122381720065998495626851241149502139264262580869523661467741485311344845519374629180329037981137465862020038414285296394747359446242328488668743848790524262574489753290227188557314524093509983688354857005768464595599040661333002861275422817830930045336538934525600036, 22410284915869332915517353475405301781361874997511620014765307716896609134768752598582584704665037725485578318861190319579404022449775594129425860979978888272443446324093514666314685424695000601786686561006052411264877076748054463659902146625722029484456473027960815036305882742747518983542532772826030995019547403388699014520255435093536041121723793417289085198882108642039061716629900663673185654638085326455126099981185733763692003629409489559712215078372884665625160603972308815617077592138575143204160714378785745066118022886827674355196815158593721675680283188298853358878159695139190175292207533127255034143712, 19073979249275923038893403197873802702942330898221412935002649745044628810289760160906684289522634756719764289365141953863154441618860322921339033977398137618850126299000852728420859130729324165431279514548481361259733142809124530477420924010397665965873357195354849848588229804376977984636683366863855736325383167291647351033039353473600211555662607490573852684908975665488806129740839801624701017800394009286759153911158126133388953551250607486734408238163212404235716911901582709861984044176063401493384378563087390984887945676907220888380393998115118953005740848277298983697518540266717111840324178318373259180622, 6541698645302832008262940247970633562467698933708103881328966231397682913241801166212436132379502941982889063089343135477694379818531293280802838942673457394052917618128597686711422777122136224213699132136127984184142523613073960971448706423332584903476150835015731055304009403507778390169574742629087804368703460732998669837597738720119482937031238843681810088915673826941865000058898348157163412745731930147221176216054781442545666046969521342926260834211384338749444032842775055037996717706324772768300639435331444465728608728138351824860891626691575771833819130630414042360017020843812450263396637265856188996779, 3205392978709422131638989970439134484048154834417896801566308259545702588762808728536535717237099973217075033593294769761444798987616022072716011940092706740459597593035935748817596483156459787858292085678556934178998589674144027788967483808008221384893035002409765867586356465137237391263725336666912545674539224635947006350381657100183653370970052916966577574942540850391609413169837486108678775908040612978854230146027173812242615968810639269948453994001712077360000340772048949282903169743813031057524303619633090384498531518217898358044470466212973049159276790608859667179375865971339386811513282456974414033689, 1543310739533705925617992886392000141649404157079479928930698364479310680106283668528354752804099419670142142797718357489736266381309282641195804359113458377452689732728604948309122365352894654066694232006670497878530231153578549981039123791496080645734035490310101421641502841223416591980415886742445245320562278199153917811183250161553801969463496211873942707826153865579429980297598885519283561022464471692495018782367388201305439269182147692194807052336182457688766197384911522571492093138539383737422443508665545223427997090521479203257597269949688956374964379867051693054674285687711731173675479045294922577365, 61371688286799334113646730018045068199733683407922550237336739124912645060439058499419425524697266009247933120500549159620827721941790197719298587092412922043766127553554237087250302287324648718008153986587214189069868903229491954377520016520933768430955608165395350944256301087438742046756268637780718849807]
for t in m_list:
print(long_to_bytes(t))
0x03总结
不知不觉一个月过去了,好多东西觉得还是要记录一下容易遗忘。
最后凑个整






















 1663
1663











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








