iptables
防火墙 - - - firewall
作用:防止别人进入自己的电脑,攻击自己的电脑,不能杀病毒
攻击的方式:
dos
ddos
cc
syn flooding等
软件防火墙
linux系统的防火墙功能是由内核实现的
防火墙:数据过滤机制
数据包过滤机制是netfilter ,管理工具是iptables
netfilter是linux防火墙的“内核态”
iptables是 linux防火墙的“用户态”
规则链
默认的五种规则链:
INPUT:处理入站数据包
OUTPUT:处理出站数据包
FORWARD:处理转发数据包
POSTROUTING链:在进行路由选择后处理数据包
PREROUTING链:在进行路由选择前处理数据包
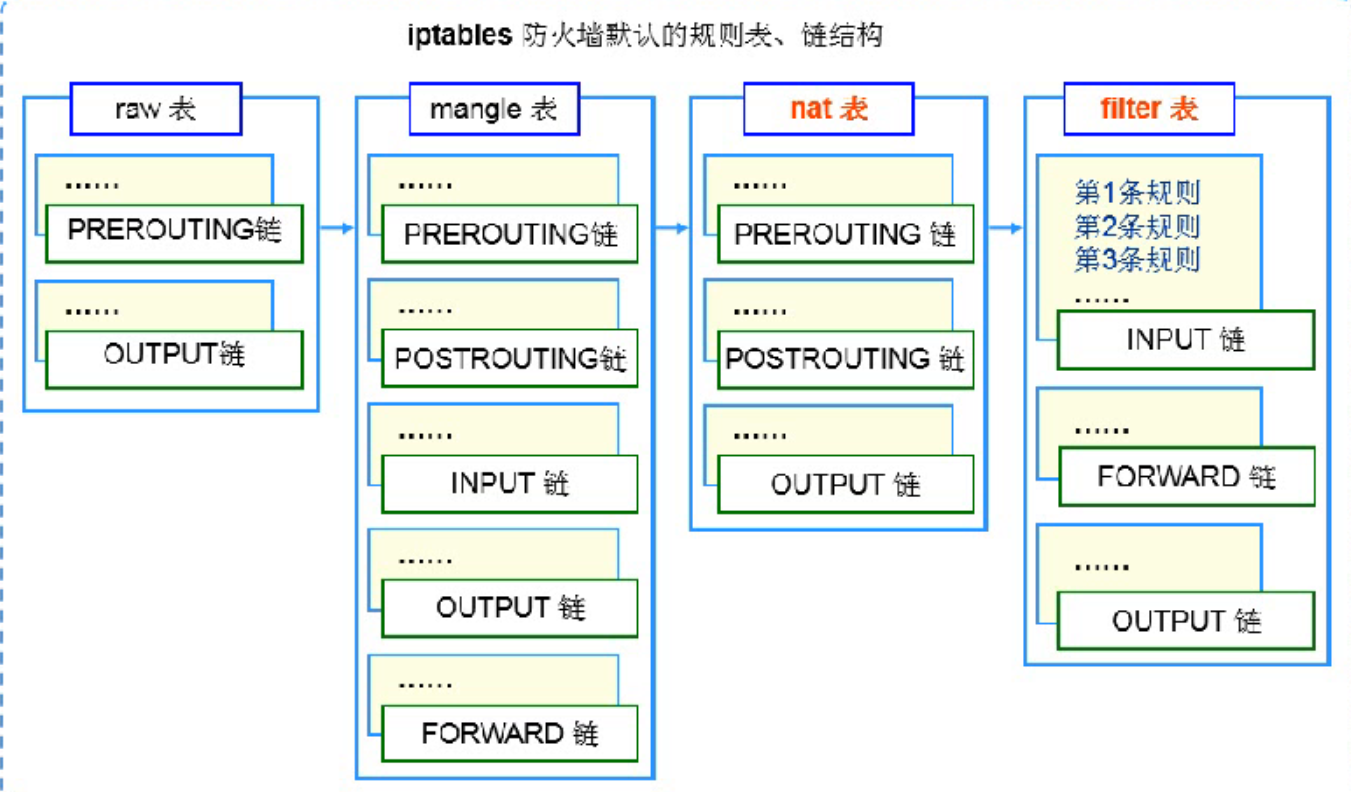
规则表:表里有很多的规则链
默认的四个规则表:
raw表:确定是否对该数据包进行状态跟踪
mangle表:为数据包设置标记
nat表:修改数据包中的源、目标IP地址或端口
filter表: 确定是否放行该数据包(过滤)- - - 保护应用程序数据、路由数据
[root@peipei ~]# iptables -L -t filter
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
默认的规则表、链结构
raw
[root@peipei ~]# iptables -L -t raw
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
mangle
[root@peipei ~]# iptables -L -t mangle
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
nat
[root@peipei ~]# iptables -L -t nat
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
filter
[root@peipei ~]# iptables -L -t filter
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
iptables -L 默认不接表名,查看的是filter
[root@peipei ~]# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
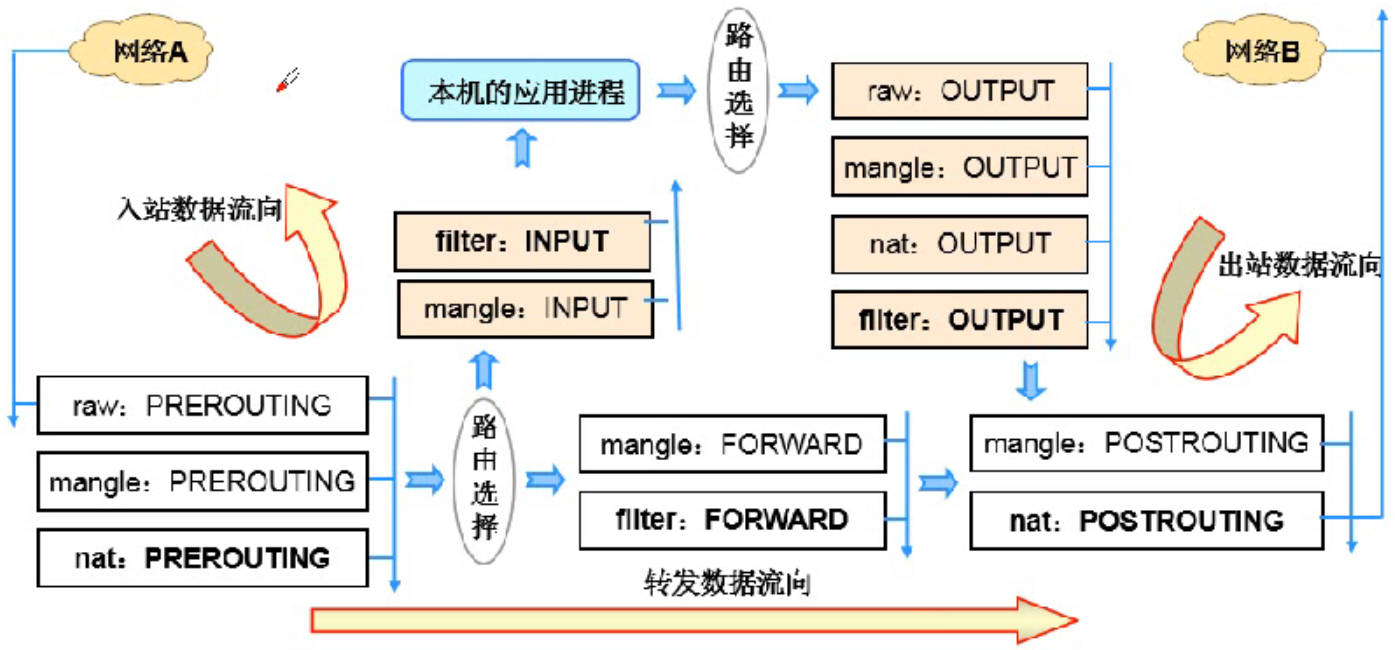
规则表间的优先顺序
raw、mangle、nat、filter
规则链间的匹配顺序
入站数据:PREROUTING 、INPUT
出战数据:OUPUT、POSTROUTING
转发数据:PREROUTING 、FPRWARD、POSTROUTING
规则链内的匹配顺序
按顺序依次进行检查,找到相匹配的规则即停止(LOG策略会有例外)
若在该链内找不到相匹配的规则,则按该链的默认策略处理
#清除filter的规则
iptables -F
#设置默认策略
iptables -P INPUT DROP
#禁用web
iptables -A INPUT -s 192.168.186.135 -p tcp --dport 80 -j DROP
#禁用MYSQL
iptables -A INPUT -s 192.168.186.135 -p tcp --dport 3306 -j DROP
#禁用别人PING本机
iptables -A INPUT -p icmp --icmp-type 8 -j DROP
#允许本机ping其他主机
iptables -A INPUT -p icmp --icmp-type 0 -j ACCEPT
#允许ssh
iptables -A INPUT -s 192.168.186.135 -p tcp --dport 22 -j ACCEPT
设置默认策略
iptables -P INPUT DROP
此命令会导致未开放本机连接ssh的服务,导致不能远程连接服务器。
最好设置计划任务清除iptables的规则
查看链的顺序
[root@peipei ~]# iptables -L -n --line-num -v
Chain INPUT (policy ACCEPT 511 packets, 69681 bytes)
num pkts bytes target prot opt in out source destination
1 3 228 DROP icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8
2 2 168 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 0
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 497 packets, 88995 bytes)
num pkts bytes target prot opt in out source destination
-n 以数字形式显示
-
- line-num 显示规则的编号
-v 显示匹配到的数据包的个数和字节数
数据过滤流程图
iptables命令的语法格式
iptables -t 表名 链名 条件匹配 -j 目标动作或跳转
注意事项
- 不指定表名时,默认表示filter表
- 不指定链名时,默认表示该表内所有链
- 除非设置规则链的缺省策略,否则需要指定匹配条件
设置规则内容:
-A :在链尾追加一条新的规则
-I:在指定位置(或链首)插入一条新的规则
默认插入到链首
[root@peipei ~]# iptables -I INPUT -s 192.168.186.135 -p tcp --dport 80 -j DROP
[root@peipei ~]# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP tcp -- 192.168.186.135 anywhere tcp dpt:http
DROP icmp -- anywhere anywhere icmp echo-request
ACCEPT icmp -- anywhere anywhere icmp echo-reply
DROP tcp -- 192.168.186.135 anywhere tcp dpt:mysql
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
指定位置插入
[root@peipei ~]# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP tcp -- 192.168.186.135 anywhere tcp dpt:http
ACCEPT tcp -- 192.168.186.135 anywhere tcp dpt:ssh
DROP icmp -- anywhere anywhere icmp echo-request
ACCEPT icmp -- anywhere anywhere icmp echo-reply
DROP tcp -- 192.168.186.135 anywhere tcp dpt:mysql
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
-R:修改、替换指定位置或内容的规则
-P:设置指定链的默认策略
列表查看规则
-L:列表查看各条规则信息
- -line-numbers:查看规则信息时显示规则的行号
-n:以数字形式显示IP地址、端口等信息
-v:显示数据包个数、字节数等详细信息
清除规则
-D:删除指定位置或内容的规则
[root@peipei ~]# iptables -D INPUT 5
[root@peipei ~]# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP tcp -- 192.168.186.135 anywhere tcp dpt:http
ACCEPT tcp -- 192.168.186.135 anywhere tcp dpt:ssh
DROP icmp -- anywhere anywhere icmp echo-request
ACCEPT icmp -- anywhere anywhere icmp echo-reply
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
-F:清空规则链内的所有规则
自定义规则链
-N:创建一条新的规则链
用户自定义链名:传递给自定义链内的规则进行处理
1.新建自定义链
[root@peipei ~]# iptables -N WEB
[root@peipei ~]# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain WEB (0 references)
target prot opt source destination
2.往自定义链里添加规则
[root@peipei ~]# iptables -I WEB -p tcp --dport 80 -s 192.168.186.140 -j REJECT
[root@peipei ~]# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain WEB (0 references)
target prot opt source destination
REJECT tcp -- 192.168.186.140 anywhere tcp dpt:http reject-with icmp-port-unreachable
-X:删除自定义的规则链
其他
-h:查看iptables命令的使用帮助
常见数据包处理方式
ACCEPT:放行数据包
DROP:丢弃数据包
REJECT:拒绝数据包
LOG:记录日志信息,并传递给下一条规则处理
设置匹配数据包的条件

协议匹配
-p 协议名
地址匹配
-s 源地址
-d 目的地址
接口匹配
-i 网络接口名 (接收)
-o 网络接口名 (发送)
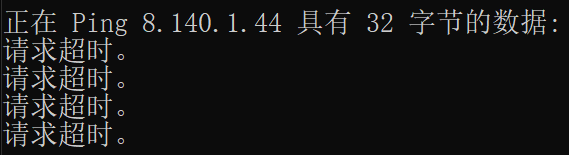
REJECT
会给回复
[root@peipei ~]# iptables -A INPUT -p icmp -j REJECT
端口匹配
-
-sport 源端口
-
-dport 目标端口
20:80表示一个范围的端口
TCP标记匹配
-
- tcp-flags SYN,RST,ACK SYN
表示检查SYN、RST、ACK这三个标记,只有SYN为1时满足条件 - - - 三次握手
ICMP类型匹配
- -icmp-type icmp类型
echo-request 8 echo-reply 0
MAC地址匹配
-m mac - -mac-source MAC地址
多端口匹配
-m multiport - -sport 源端口列表 / - -dports 目标端口列表
多个端口用,隔开 连续的端口用:表示
数据包状态匹配
-m state - - state 状态类型
常见的数据包状态包括:
NEW(第一次连接)、ESTABLISHED(已经建立连接)、RELATED(有关联的- - 根据一个连接,建立另外一个连接)
多种状态用,分割开
[root@peipei ~]# iptables -A INPUT -p tcp -m state --state ESTABLISHED,RELATED -j ACCEPT
[root@peipei ~]# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP tcp -- 192.168.186.135 anywhere tcp dpt:http
ACCEPT tcp -- 192.168.186.135 anywhere tcp dpt:ssh
DROP icmp -- anywhere anywhere icmp echo-request
ACCEPT icmp -- anywhere anywhere icmp echo-reply
REJECT icmp -- anywhere anywhere reject-with icmp-port-unreachable
ACCEPT tcp -- anywhere anywhere state RELATED,ESTABLISHED
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
ftp - - - File Transfer Protocol 文件传输协议
主动模式:TCP/IP协议中,FTP标准命令TCP端口号为21,Port方式数据端口为20。
打开被动模式 - - - passive
iptables -A INPUT -p tcp --dport 21 -j ACCEPT
iptables -A INPUT -m state --state ESTABLIED,RELATED -j ACCEPT
加载支持ftp状态跟踪的模块
modprobe ip_conntrack_ftp
lsmod
lsmod是一个命令行实用程序,用于显示有关已加载的Linux内核模块的信息。
[root@peipei ~]# lsmod
Module Size Used by
iptable_raw 12678 0
iptable_mangle 12695 0
iptable_nat 12875 0
nf_nat_ipv4 14115 1 iptable_nat
nf_nat 26583 1 nf_nat_ipv4
nf_conntrack_ipv4 15053 2
nf_defrag_ipv4 12729 1 nf_conntrack_ipv4
xt_conntrack 12760 1
nf_conntrack 137239 4 nf_nat,nf_nat_ipv4,xt_conntrack,nf_conntrack_ipv4
libcrc32c 12644 2 nf_nat,nf_conntrack
AliSecGuard 22180 2
ipt_REJECT 12541 1
nf_reject_ipv4 13373 1 ipt_REJECT
iptable_filter 12810 1
modprobe
可载入指定的个别模块,或是载入一组相依的模块
[root@peipei ~]# modprobe ip_conntrack_ftp
[root@peipei ~]# lsmod|grep ftp
nf_conntrack_ftp 18638 0
nf_conntrack 137239 5 nf_nat,nf_nat_ipv4,xt_conntrack,nf_conntrack_ftp,nf_conntrack_ipv4
模块存放目录
[root@peipei netfilter]# pwd
/lib/modules/3.10.0-957.el7.x86_64/kernel/net/netfilter
防火墙脚本的一般结构
1.设置网段、网卡、IP地址等变量
2.加载包过滤相关的内核模块
ETP相关,ip_nat_ftp、 ip_conntrack_ftp
Mail相关: ip_nat_irc、ip_ conntrack_irc
3.确认开启路由转发功能
方法1: /sbin/sysctl -W net .ipv4.ip_ forward=1
[root@peipei yum.repos.d]# /sbin/sysctl -w net.ipv4.ip_forward=1
net.ipv4.ip_forward = 1
方法2: echo 1 > /proc/sys/netipv4/ip_ forward
[root@peipei yum.repos.d]# cat /proc/sys/net/ipv4/ip_forward
0
方法3:修改/etc/sysctl. conf,设置net.ipv4.ip_ forward = 1
[root@peipei yum.repos.d]# cat /etc/sysctl.conf
vm.swappiness = 0
net.ipv4.neigh.default.gc_stale_time = 120
# see details in https://help.aliyun.com/knowledge_detail/39428.html
net.ipv4.conf.all.rp_filter = 0
net.ipv4.conf.default.rp_filter = 0
net.ipv4.conf.default.arp_announce = 2
net.ipv4.conf.lo.arp_announce = 2
net.ipv4.conf.all.arp_announce = 2
# see details in https://help.aliyun.com/knowledge_detail/41334.html
net.ipv4.tcp_max_tw_buckets = 5000
net.ipv4.tcp_syncookies = 1
net.ipv4.tcp_max_syn_backlog = 1024
net.ipv4.tcp_synack_retries = 2
net.ipv6.conf.all.disable_ipv6 = 1
net.ipv6.conf.default.disable_ipv6 = 1
net.ipv6.conf.lo.disable_ipv6 = 1
kernel.sysrq = 1
4.用于添加的具体防火墙规则内容
清空原有规则,建立新的规则
导入、导出防火墙规则
导出规则
iptables -save
[root@peipei yum.repos.d]# iptables-save
# Generated by iptables-save v1.4.21 on Fri May 14 16:44:28 2021
*raw
:PREROUTING ACCEPT [1299:345978]
:OUTPUT ACCEPT [976:173880]
COMMIT
# Completed on Fri May 14 16:44:28 2021
# Generated by iptables-save v1.4.21 on Fri May 14 16:44:28 2021
*mangle
:PREROUTING ACCEPT [1330:347704]
:INPUT ACCEPT [1330:347704]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [997:179210]
:POSTROUTING ACCEPT [997:179210]
COMMIT
# Completed on Fri May 14 16:44:28 2021
# Generated by iptables-save v1.4.21 on Fri May 14 16:44:28 2021
*nat
:PREROUTING ACCEPT [60:5596]
:INPUT ACCEPT [13:672]
:OUTPUT ACCEPT [120:8310]
:POSTROUTING ACCEPT [120:8310]
COMMIT
# Completed on Fri May 14 16:44:28 2021
# Generated by iptables-save v1.4.21 on Fri May 14 16:44:28 2021
*filter
:INPUT ACCEPT [124:12580]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [1367:252554]
-A INPUT -s 192.168.186.135/32 -p tcp -m tcp --dport 80 -j DROP
-A INPUT -s 192.168.186.135/32 -p tcp -m tcp --dport 22 -j ACCEPT
-A INPUT -p icmp -m icmp --icmp-type 8 -j DROP
-A INPUT -p icmp -m icmp --icmp-type 0 -j ACCEPT
-A INPUT -p icmp -j REJECT --reject-with icmp-port-unreachable
-A INPUT -p tcp -m state --state RELATED,ESTABLISHED -j ACCEPT
COMMIT
# Completed on Fri May 14 16:44:28 2021
结合重定向保存规则信息
[root@peipei /]# iptables-save >/lianxi/all_iptables.txt
[root@peipei /]# cd /lianxi
[root@peipei lianxi]# ls
all_iptables.txt
[root@peipei lianxi]# cat all_iptables.txt
# Generated by iptables-save v1.4.21 on Fri May 14 16:46:26 2021
*raw
:PREROUTING ACCEPT [1591:370606]
:OUTPUT ACCEPT [1170:204910]
COMMIT
# Completed on Fri May 14 16:46:26 2021
# Generated by iptables-save v1.4.21 on Fri May 14 16:46:26 2021
*mangle
:PREROUTING ACCEPT [1622:372332]
:INPUT ACCEPT [1622:372332]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [1191:210240]
:POSTROUTING ACCEPT [1191:210240]
COMMIT
# Completed on Fri May 14 16:46:26 2021
# Generated by iptables-save v1.4.21 on Fri May 14 16:46:26 2021
*nat
:PREROUTING ACCEPT [61:5656]
:INPUT ACCEPT [14:732]
:OUTPUT ACCEPT [129:8942]
:POSTROUTING ACCEPT [129:8942]
COMMIT
# Completed on Fri May 14 16:46:26 2021
# Generated by iptables-save v1.4.21 on Fri May 14 16:46:26 2021
*filter
:INPUT ACCEPT [132:13330]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [1561:283584]
-A INPUT -s 192.168.186.135/32 -p tcp -m tcp --dport 80 -j DROP
-A INPUT -s 192.168.186.135/32 -p tcp -m tcp --dport 22 -j ACCEPT
-A INPUT -p icmp -m icmp --icmp-type 8 -j DROP
-A INPUT -p icmp -m icmp --icmp-type 0 -j ACCEPT
-A INPUT -p icmp -j REJECT --reject-with icmp-port-unreachable
-A INPUT -p tcp -m state --state RELATED,ESTABLISHED -j ACCEPT
COMMIT
# Completed on Fri May 14 16:46:26 2021
导入规则
iptables-restore
[root@peipei lianxi]# iptables-restore </lianxi/all_iptables.txt
开机自动加载脚本
/etc/rc.local
vim /etc/rc.local
#!/bin/bash
# THIS FILE IS ADDED FOR COMPATIBILITY PURPOSES
#
# It is highly advisable to create own systemd services or udev rules
# to run scripts during boot instead of using this file.
#
# In contrast to previous versions due to parallel execution during boot
# this script will NOT be run after all other services.
#
# Please note that you must run 'chmod +x /etc/rc.d/rc.local' to ensure
# that this script will be executed during boot.
touch /var/lock/subsys/local
需要加权限
[root@peipei lianxi]# ll /etc/rc.d/rc.local
-rw-r--r-- 1 root root 473 Jul 3 2019 /etc/rc.d/rc.local
[root@peipei lianxi]# chmod +x /etc/rc.d/rc.local
[root@peipei lianxi]# ll /etc/rc.d/rc.local
-rwxr-xr-x 1 root root 473 Jul 3 2019 /etc/rc.d/rc.local
/root/.bashrc
[root@peipei lianxi]# vim /root/.bashrc
# .bashrc
# User specific aliases and functions
alias rm='rm -i'
alias cp='cp -i'
alias mv='mv -i'
# Source global definitions
if [ -f /etc/bashrc ]; then
. /etc/bashrc
fi
~






















 3万+
3万+











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








