拓扑图如下:

其中有Internet、AR1、AR2三台路由器,Internet路由器为公网路由器;AR1路由器连接PC端PC1与客户端Client http与Client ftp,AR2路由器连接PC端PC2与服务器Server dns、Server http和Server ftp。
IPSec VPN通道建立在AR1路由器的GE0/0/1接口与AR2路由器的GE0/0/1接口上。
配置过程如下:
先是AR1,创建好AR1连接的PC1、Client http与Client ftp并设置好各自的ip地址等信息后,进行AR1的配置:
sys
sysname AR1 //路由器命名AR1
int g0/0/0
ip add 192.168.10.254 24 //配置端口地址
quit
int g0/0/1
ip add 100.1.1.1 30
quit
vlan 11 //创建vlan
quit
vlan 12
quit
int e0/0/0
port link-type access
port default vlan 11
quit
int e0/0/1
port link-type access
port default vlan 12
quit
int vlan 11
ip add 192.168.11.254 24 //配置vlan地址
quit
int vlan 12
ip add 192.168.12.254 24
quit
ip route-static 200.1.1.0 30 100.1.1.2 //设置静态路由
ip route-static 192.168.20.0 24 200.1.1.0
ip route-static 192.168.21.0 24 200.1.1.0
ip route-static 192.168.22.0 24 200.1.1.0
ip route-static 192.168.23.0 24 200.1.1.0
在AR2连接PC2、Server dns与Server http、Server ftp后,先创建好ftp与http需要的文件夹,配置文件根目录,并配置好dns的主机域名、地址等相关信息以及三个服务器的ip地址等信息,先进入AR2进行ftp相关配置:
FTP配置:(AR2)
ftp 192.168.21.1
配置用户名为:xxx 密码为:12345
sys
sysname AR2
ftp server enable //启用ftp
aaa
local-user ftp password cipher 12345
local-user ftp ftp-directory flash:
local-user ftp service-type ftp
local-user ftp privilege level 15
quit
后续为与AR1一样的步骤:
int g0/0/0
ip add 192.168.20.254 24
quit
int g0/0/1
ip add 200.1.1.1 30
quit
vlan 21
quit
vlan 22
quit
vlan 23
quit
int e0/0/0
port link-type access
port default vlan 21
quit
int e0/0/1
port link-type access
port default vlan 22
quit
int e0/0/2
port link-type access
port default vlan 23
quit
int vlan 21
ip add 192.168.21.254 24
quit
int vlan 22
ip add 192.168.22.254 24
quit
int vlan 23
ip add 192.168.23.254 24
quit
ip route-static 100.1.1.0 30 200.1.1.2
ip route-static 192.168.10.0 24 100.1.1.0
ip route-static 192.168.11.0 24 100.1.1.0
ip route-static 192.168.12.0 24 100.1.1.0
配置Internet路由器,同样是设置端口地址与配置静态路由:
sys
sysname Internet
int g0/0/0
ip add 100.1.1.2 30
quit
int g0/0/1
ip add 200.1.1.2 30
quit
ip route-static 192.168.10.0 24 100.1.1.1
ip route-static 192.168.11.0 24 100.1.1.1
ip route-static 192.168.12.0 24 100.1.1.1
ip route-static 192.168.20.0 24 200.1.1.1
ip route-static 192.168.21.0 24 200.1.1.1
ip route-static 192.168.22.0 24 200.1.1.1
ip route-static 192.168.23.0 24 200.1.1.1
完成以上后试着运行一次是否有报错或没有配通,配通后再进行下面的VPN配置,此时在端口上抓包均为原始的流量类别
进行IPSec配置:
先是AR1:
acl 3000 //创建acl
rule 10 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
rule 11 permit ip source 192.168.11.0 0.0.0.255 destination 192.168.21.0 0.0.0.255
rule 12 permit ip source 192.168.12.0 0.0.0.255 destination 192.168.22.0 0.0.0.255
rule 13 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.23.0 0.0.0.255 //允许访问网段
ipsec proposal gd //设置ipsec安全协议为gd
encapsulation-mode tunnel //报文封装形式采用隧道模式
transform esp //传输协议为esp
esp encryption-algorithm des //加密算法为des
esp authentication-algorithm md5 //认证算法为md5
ipsec policy gdut 10 manual //设置名为gdut的IPSec策略,序号为10,手动方式
security acl 3000 //匹配acl
proposal gd //使用安全协议gd
tunnel local 100.1.1.1 //设置本地隧道端口
tunnel remote 200.1.1.1 //设置对端隧道端口
sa spi inbound esp 54321 //设置sa入方向的密钥为54321
sa string-key inbound esp cipher kiki //入方向为加密的密钥kiki
sa spi outbound esp 12345 //设置sa入方向的密钥为12345
sa string-key outbound esp cipher kiki //出方向为加密的密钥kiki
int g0/0/1
ipsec policy gdut //在端口上启用IPSec
acl 3001
rule 20 deny ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
rule 21 deny ip source 192.168.11.0 0.0.0.255 destination 192.168.21.0 0.0.0.255
rule 22 deny ip source 192.168.12.0 0.0.0.255 destination 192.168.22.0 0.0.0.255
rule 23 deny ip source 192.168.10.0 0.0.0.255 destination 192.168.23.0 0.0.0.255
rule 25 permit ip
quit
int g0/0/1
nat outbound 3001
AR2是一样的方式:
acl 3000
rule 10 permit ip source 192.168.20.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
rule 11 permit ip source 192.168.21.0 0.0.0.255 destination 192.168.11.0 0.0.0.255
rule 12 permit ip source 192.168.22.0 0.0.0.255 destination 192.168.12.0 0.0.0.255
rule 13 permit ip source 192.168.23.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
ipsec proposal ho
encapsulation-mode tunnel
transform esp
esp encryption-algorithm des
esp authentication-algorithm md5
ipsec policy home 10 manual
security acl 3000
proposal ho
tunnel local 200.1.1.1
tunnel remote 100.1.1.1
sa spi inbound esp 12345
sa string-key inbound esp cipher kiki
sa spi outbound esp 54321
sa string-key outbound esp cipher kiki
int g0/0/1
ipsec policy home
acl 3001
rule 20 deny ip source 192.168.20.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
rule 21 deny ip source 192.168.21.0 0.0.0.255 destination 192.168.11.0 0.0.0.255
rule 22 deny ip source 192.168.22.0 0.0.0.255 destination 192.168.12.0 0.0.0.255
rule 23 deny ip source 192.168.23.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
rule 25 permit ip
quit
int g0/0/1
nat outbound 3001
要注意,一端路由器的入/出方向密钥要与另一端路由器的出/入方向密钥要一致。
在AR1的GE0/0/1接口上进行抓包,以ftp为例,在未进行加密时,抓包结果如下,数据包中有多种协议的流量数据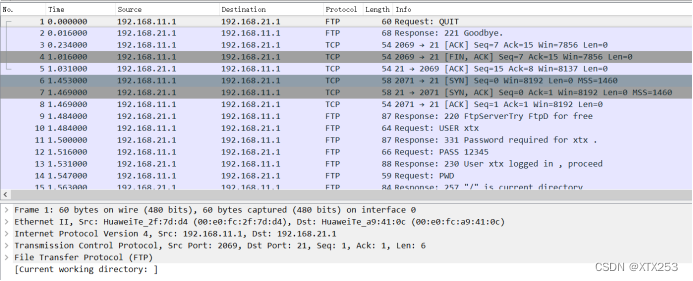
加密后,抓包结果如下,当流量加密后,数据包的源IP、目的IP、协议均发生改变,IP地址变为IPSec VPN隧道两端的地址,协议变为IPSec的ESP协议:
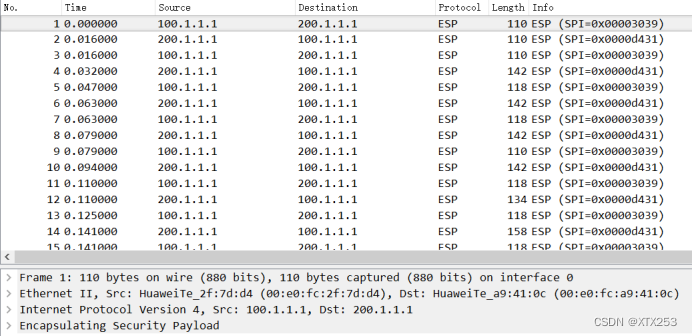
注意,若进行IPSec VPN配置后,经过试验后已经配通,但是抓包后发现流量并没有经过IPSec加密,表明仍没有配置成功,需要找出是否有错漏的地方。
若只进行IPSec vpn配置,无需传输多种流量,如下图,则无需配置vlan

配置过程如下:
AR1:
sys
sysname AR1
int g0/0/0
ip add 192.168.10.254 24
quit
int g0/0/1
ip add 100.1.1.1 30
quit
ip route-static 0.0.0.0 0.0.0.0 100.1.1.2
AR2:
sys
sysname AR2
int g0/0/0
ip add 192.168.20.254 24
quit
int g0/0/1
ip add 200.1.1.1 30
quit
ip route-static 0.0.0.0 0.0.0.0 200.1.1.2
Internet
sys
sysname Internet
int g0/0/0
ip add 100.1.1.2 30
quit
int g0/0/1
ip add 200.1.1.2 30
quit
ip route-static 192.168.10.0 24 100.1.1.1
ip route-static 192.168.20.0 24 200.1.1.1
IPSec配置:
AR1:
acl 3000
rule 10 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
ipsec proposal gd
encapsulation-mode tunnel
transform esp
esp encryption-algorithm des
esp authentication-algorithm md5
ipsec policy gdut 10 manual
security acl 3000
proposal gd
tunnel local 100.1.1.1
tunnel remote 200.1.1.1
sa spi inbound esp 54321
sa string-key inbound esp cipher kiki
sa spi outbound esp 12345
sa string-key outbound esp cipher kiki
int g0/0/1
ipsec policy gdut
acl 3001
rule 20 deny ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
rule 25 permit ip
quit
int g0/0/1
nat outbound 3001
AR2:
acl 3000
rule 10 permit ip source 192.168.20.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
ipsec proposal ho
encapsulation-mode tunnel
transform esp
esp encryption-algorithm des
esp authentication-algorithm md5
ipsec policy home 10 manual
security acl 3000
proposal ho
tunnel local 200.1.1.1
tunnel remote 100.1.1.1
sa spi inbound esp 12345
sa string-key inbound esp cipher kiki
sa spi outbound esp 54321
sa string-key outbound esp cipher kiki
int g0/0/1
ipsec policy home
acl 3001
rule 20 deny ip source 192.168.20.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
rule 25 permit ip
quit
int g0/0/1
nat outbound 3001





















 2万+
2万+











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








