目录
(2)将一个IP地址转换为另一个IP地址(增加内部网络设备的安全性)
一.ACL访问控制
1.ACL功能和特点
(1)功能
对感兴趣的路由 (控制层面)进行设置策略
对感兴趣的流量 (数据层面)进行设置策略
(2)特点
(1)自上而下匹配(编号由小到大执行),一旦匹配,立即执行
(2)ACL 列表的调用分为in(进入路由器的方向) ,先匹配ACL再查看路由。out ,离开路由器的方向,先查看路由,再匹配ACL。
(3)ACL 分为 标准 ACL 和 扩展 ACL
(4)在华为设备中若没有匹配到ACL 则假装认为没有这个ACL,需要明确写清策略为拒绝或允许
2.ACL种类
(1)基础ACL:
关注源IP地址 ,只要源IP在ACL条目内,就执行相应的ACL规则,在配置时尽量靠近目标路由器,避免误伤其他路径
(2)增强ACL:
关注源IP地址 、目标IP地址 、协议种类,在使用时尽量靠近源(ACL不能过滤自身产生的流量,所以不能位于源之上 )
3.配置演示
(1)基础ACL:
实现AR1环回0ping不通AR4环回,但环回1和AR1出接口G0/0/0可以ping通
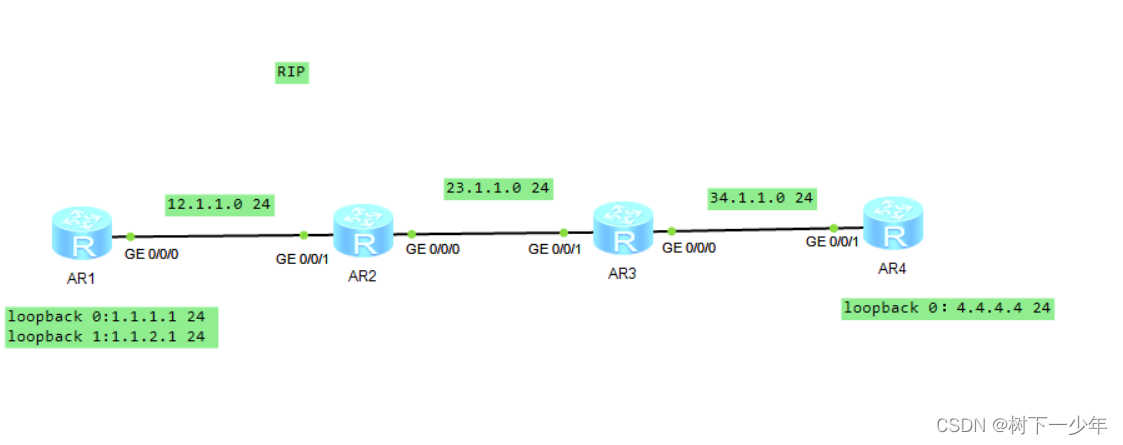
创建acl,设置acl规则,调用acl
[r4]acl 2000
#INTEGER<2000-2999>基础acl
#INTEGER<3000-3999>增强acl
[r4-acl-basic-2000]rule deny source 1.1.1.0 0.0.0.255 #指明源IP
源IP后缀参数是通配符,0代表固定位,1代表可变位,permit允许,deny拒绝
[r4]interface GigabitEthernet 0/0/1
[r4-GigabitEthernet0/0/1]traffic-filter inbound acl 2000 #调用ACL
#inbound为in方向,outbound为out方向查看测试
[r4]display acl 2000
Basic ACL 2000, 1 rule
Acl's step is 5
rule 5 deny source 1.1.1.0 0.0.0.255 (3 matches)
[r1]ping -a 1.1.1.1 4.4.4.4
PING 4.4.4.4: 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
--- 4.4.4.4 ping statistics ---
3 packet(s) transmitted
0 packet(s) received
100.00% packet loss
[r1]ping -a 1.1.2.1 4.4.4.4
PING 4.4.4.4: 56 data bytes, press CTRL_C to break
Reply from 4.4.4.4: bytes=56 Sequence=1 ttl=253 time=40 ms
Reply from 4.4.4.4: bytes=56 Sequence=2 ttl=253 time=40 ms
Reply from 4.4.4.4: bytes=56 Sequence=3 ttl=253 time=50 ms
Reply from 4.4.4.4: bytes=56 Sequence=4 ttl=253 time=40 ms
Reply from 4.4.4.4: bytes=56 Sequence=5 ttl=253 time=50 ms
--- 4.4.4.4 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 40/44/50 ms
[r1]ping 4.4.4.4
PING 4.4.4.4: 56 data bytes, press CTRL_C to break
Reply from 4.4.4.4: bytes=56 Sequence=1 ttl=253 time=50 ms
Reply from 4.4.4.4: bytes=56 Sequence=2 ttl=253 time=30 ms
Reply from 4.4.4.4: bytes=56 Sequence=3 ttl=253 time=30 ms
Reply from 4.4.4.4: bytes=56 Sequence=4 ttl=253 time=30 ms
Reply from 4.4.4.4: bytes=56 Sequence=5 ttl=253 time=40 ms
--- 4.4.4.4 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 30/36/50 ms(2)增强ACL:
实现AR1环回0ping不通AR4环回0但可以telnet,AR1环回1可以ping通AR4环回0但不可以telnet
AR4配置开启telnet
[r4]user-interface vty 0 4
[r4-ui-vty0-4]set authentication password cipher hw
[r4-ui-vty0-4]qAR2配置扩展ACL(靠近源但不能位于源上),acl调用
[r2]acl 3000
[r2-acl-adv-3000]rule deny icmp source 1.1.1.0 0.0.0.255 destination 4.4.4.4 0.0.0.0 icmp-type echo
[r2-acl-adv-3000]rule deny tcp source 1.1.2.0 0.0.0.255 destination 4.4.4.4 0.0.0.0 destination-port eq 23
[r2-acl-adv-3000]q
[r2]display acl 3000
Advanced ACL 3000, 2 rules
Acl's step is 5
rule 5 deny icmp source 1.1.1.0 0.0.0.255 destination 4.4.4.4 0 icmp-type echo
rule 10 deny tcp source 1.1.2.0 0.0.0.255 destination 4.4.4.4 0 destination-port eq telnet
[r2]interface GigabitEthernet 0/0/1
[r2-GigabitEthernet0/0/1]traffic-filter inbound acl 3000测试
[r1]ping -a 1.1.1.1 4.4.4.4
PING 4.4.4.4: 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
Request time out
Request time out
--- 4.4.4.4 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss
[r1]ping -a 1.1.2.1 4.4.4.4
PING 4.4.4.4: 56 data bytes, press CTRL_C to break
Reply from 4.4.4.4: bytes=56 Sequence=1 ttl=253 time=40 ms
Reply from 4.4.4.4: bytes=56 Sequence=2 ttl=253 time=40 ms
Reply from 4.4.4.4: bytes=56 Sequence=3 ttl=253 time=40 ms
Reply from 4.4.4.4: bytes=56 Sequence=4 ttl=253 time=30 ms
Reply from 4.4.4.4: bytes=56 Sequence=5 ttl=253 time=30 ms
--- 4.4.4.4 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 30/36/40 ms
[r1]q
<r1>telne
<r1>telnet -a 1.1.1.1 4.4.4.4
Press CTRL_] to quit telnet mode
Trying 4.4.4.4 ...
Connected to 4.4.4.4 ...
Login authentication
Password:
<r4>q
Configuration console exit, please retry to log on
The connection was closed by the remote host
<r1>telnet -a 1.1.2.1 4.4.4.
Press CTRL_] to quit telnet mode
Trying 4.4.4.4 ...
Error: Can't connect to the remote host二.NAT地址转换
1.类型介绍
所有NAT配置均在边界路由器上配置,在边界路由器上进行公有IP和私有IP间的相互转换,从内网(私网) 访问外部 (公网) 时,修改源地址,从外部进入内部时,修改目标地址。
(1)一对一
将一个私有地址转化为一个公有地址
(2)一对多
又称PAT端口地址转换,将多个私有ip地址转换为同一个公有 ip地址,多个私有IP地址同时转换为公有IP地址,其源IP和源MAC地址均相同时,只能基于不同的源MAC地址来进行识别
(3)多对多
一个IP对多有65535个端口号,在一个节点时间内最多转发65535个数据包,大型网络中,将使用等多个公有IP来实现通信效率
2.功能
(1)将大量的私有地址转换为公有地址(节约IP地址)
(2)将一个IP地址转换为另一个IP地址(增加内部网络设备的安全性)
3.缺陷:
(1)很消耗网络设备资源
(2)破坏数据端到端传输,安全策略实施受限
4.简单案例配置
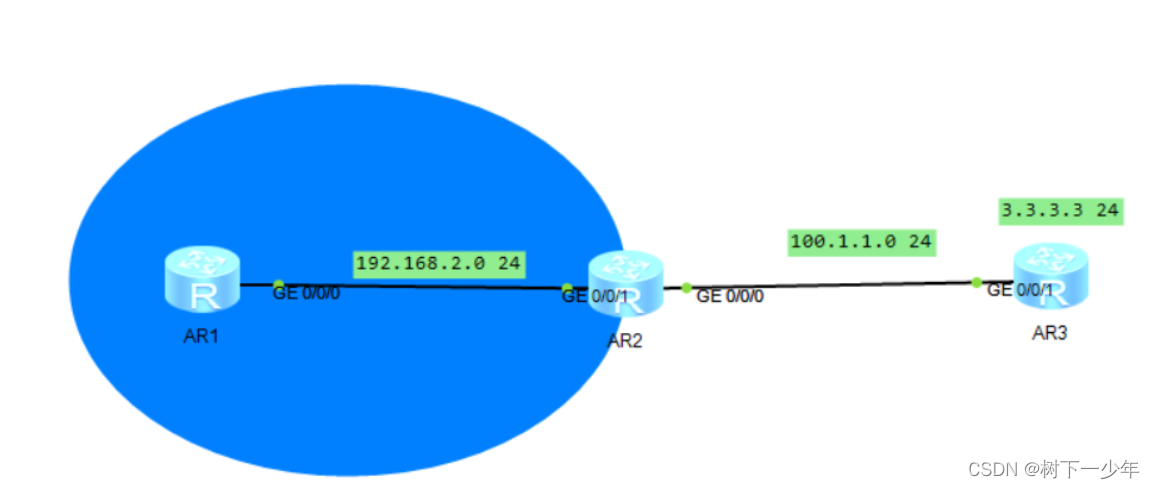
(1)静态模式(一对一转换)
手动指定公网IP,192.168.2.1通信3.3.3.3 ,需要自己指定网段内公有地址
全局
[r2]nat static global 100.1.1.6 inside 192.168.2.1 #转换地址
[r2]interface GigabitEthernet 0/0/0
[r2-GigabitEthernet0/0/0]nat static enable #开启静态nat
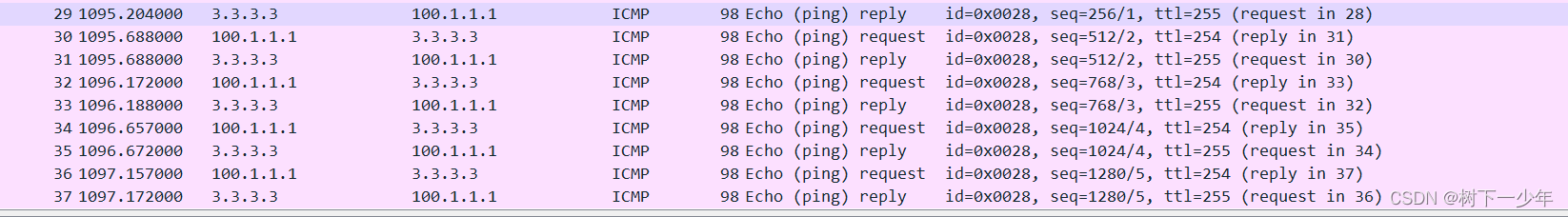
[r1]ping 3.3.3.3
PING 3.3.3.3: 56 data bytes, press CTRL_C to break
Reply from 3.3.3.3: bytes=56 Sequence=1 ttl=254 time=20 ms
Reply from 3.3.3.3: bytes=56 Sequence=2 ttl=254 time=30 ms
Reply from 3.3.3.3: bytes=56 Sequence=3 ttl=254 time=20 ms
Reply from 3.3.3.3: bytes=56 Sequence=4 ttl=254 time=30 ms
Reply from 3.3.3.3: bytes=56 Sequence=5 ttl=254 time=30 ms
--- 3.3.3.3 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 20/26/30 ms接口
[r2]interface GigabitEthernet 0/0/0
[r2-GigabitEthernet0/0/0]nat static global 200.1.1.6 inside 192.168.2.1 netmask 255.255.255.255地址映射为指定的100.1.1.6
(2)动态模式(多对多转换)
192.168.2.1通信3.3.3.3 ,使用ACL定义私有IP地址池和公有IP地址池进行映射
删去上文静态
[r2]undo nat static global 100.1.1.6 inside 192.168.2.1
[r2]interface GigabitEthernet 0/0/0
[r2-GigabitEthernet0/0/0]undo nat static enable 定义地址范围并使用
[r2]acl 2000
[r2-acl-basic-2000]rule permit source 192.168.2.0 0.0.0.255 #定于允许访问的源IP范围(私有)
[r2]nat address-group 1 100.1.1.20 100.1.1.30 #定于允许访问的公有IP范围
[r2]interface GigabitEthernet 0/0/0
[r2-GigabitEthernet0/0/0]nat outbound 2000 address-group 1 #调用acl和地址组
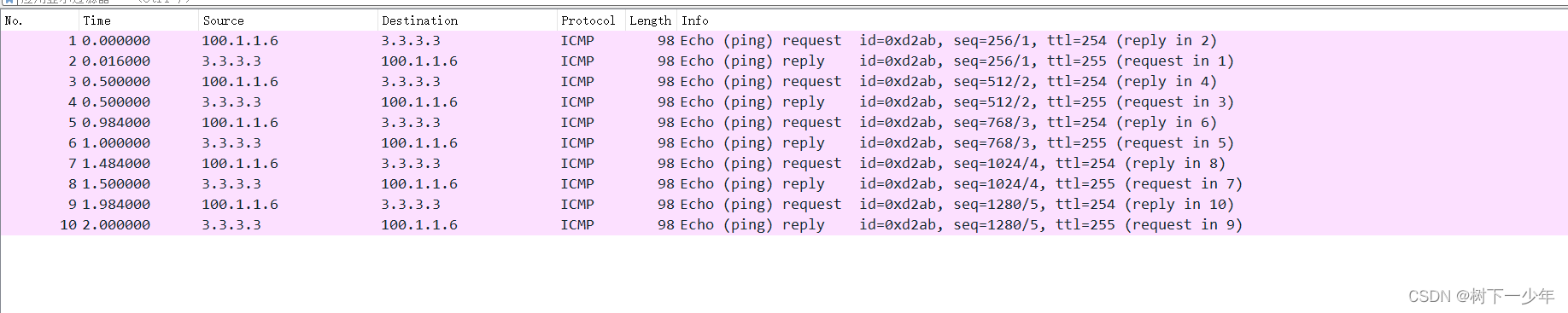
[r1]ping 3.3.3.3
PING 3.3.3.3: 56 data bytes, press CTRL_C to break
Reply from 3.3.3.3: bytes=56 Sequence=1 ttl=254 time=40 ms
Reply from 3.3.3.3: bytes=56 Sequence=2 ttl=254 time=20 ms
Reply from 3.3.3.3: bytes=56 Sequence=3 ttl=254 time=30 ms
Reply from 3.3.3.3: bytes=56 Sequence=4 ttl=254 time=20 ms
Reply from 3.3.3.3: bytes=56 Sequence=5 ttl=254 time=20 ms
--- 3.3.3.3 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 20/26/40 ms 20/26/40 ms地址映射为100.1.1.20到100.1.1.30之间

(3)NAPT(多对一转换)
将私有范围内的地址都转化为这个边界路由器的出接口的公有IP
删去上文动态
[r2-GigabitEthernet0/0/0]undo nat outbound 2000 address-group 1
[r2-GigabitEthernet0/0/0]q
[r2]undo nat address-group 1调用ACL定义范围
[r2]interface GigabitEthernet 0/0/0
[r2-GigabitEthernet0/0/0]nat outbound 2000
[r1]ping 3.3.3.3
PING 3.3.3.3: 56 data bytes, press CTRL_C to break
Reply from 3.3.3.3: bytes=56 Sequence=1 ttl=254 time=20 ms
Reply from 3.3.3.3: bytes=56 Sequence=2 ttl=254 time=20 ms
Reply from 3.3.3.3: bytes=56 Sequence=3 ttl=254 time=40 ms
Reply from 3.3.3.3: bytes=56 Sequence=4 ttl=254 time=20 ms
Reply from 3.3.3.3: bytes=56 Sequence=5 ttl=254 time=20 ms
--- 3.3.3.3 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 20/24/40 ms地址映射为100.1.1.1,为边界路由器出接口地址
(4)NAT服务配置
[r2]user-interface v
[r2]user-interface vty 0 4
[r2-ui-vty0-4]set
[r2-ui-vty0-4]set auth
[r2-ui-vty0-4]set authentication p
[r2-ui-vty0-4]set authentication password ci
[r2-ui-vty0-4]set authentication password cipher hw
[r2-ui-vty0-4]q
[r2-GigabitEthernet0/0/0]nat server protocol tcp global 100.1.1.16 23 inside 192.168.2.1 23
<r1>telnet 100.1.1.1
Press CTRL_] to quit telnet mode
Trying 100.1.1.1 ...
Connected to 100.1.1.1 ...
Login authentication
Password:
<r2>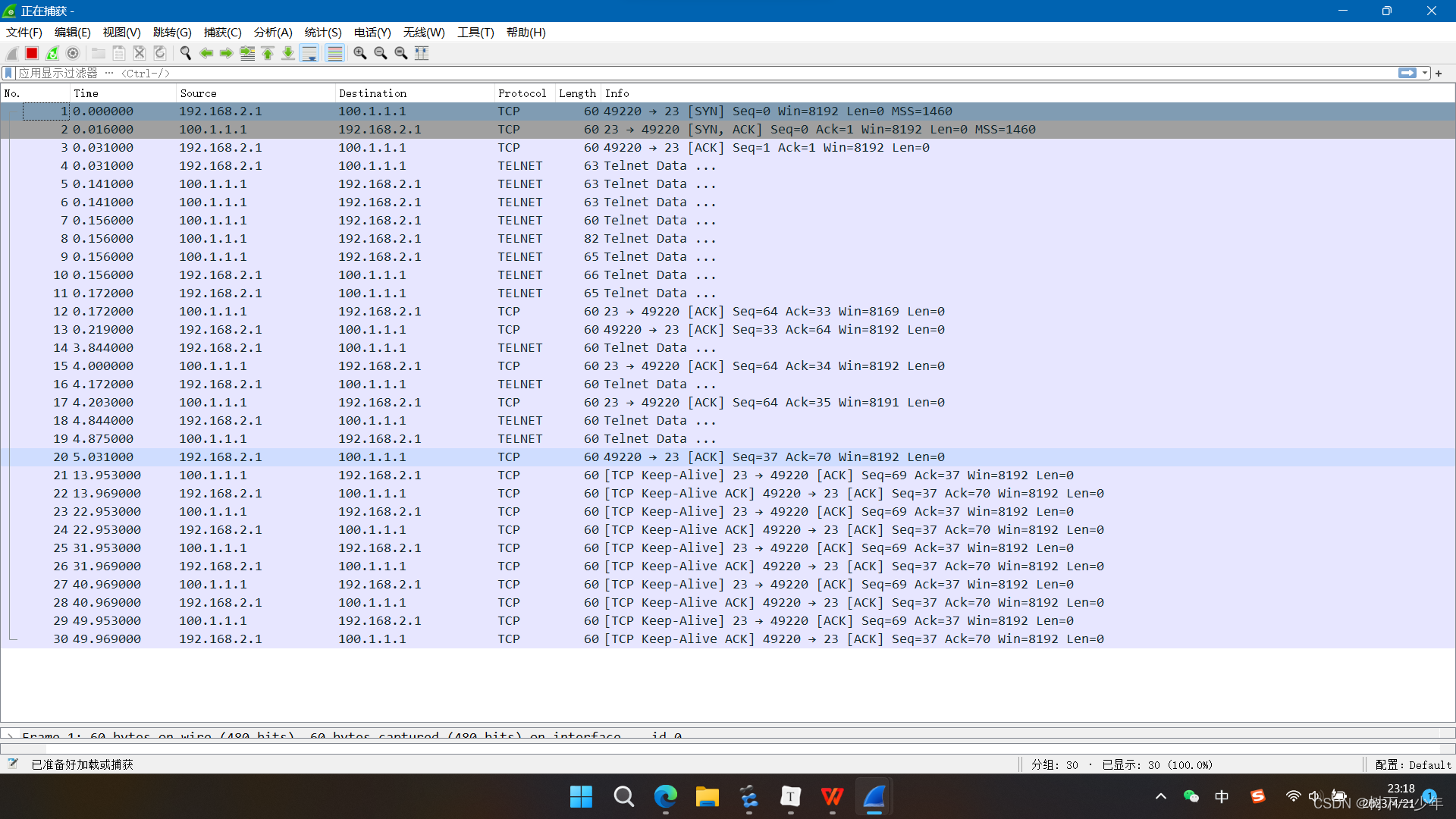
























 2144
2144











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










