HCIP security 综合实验测试
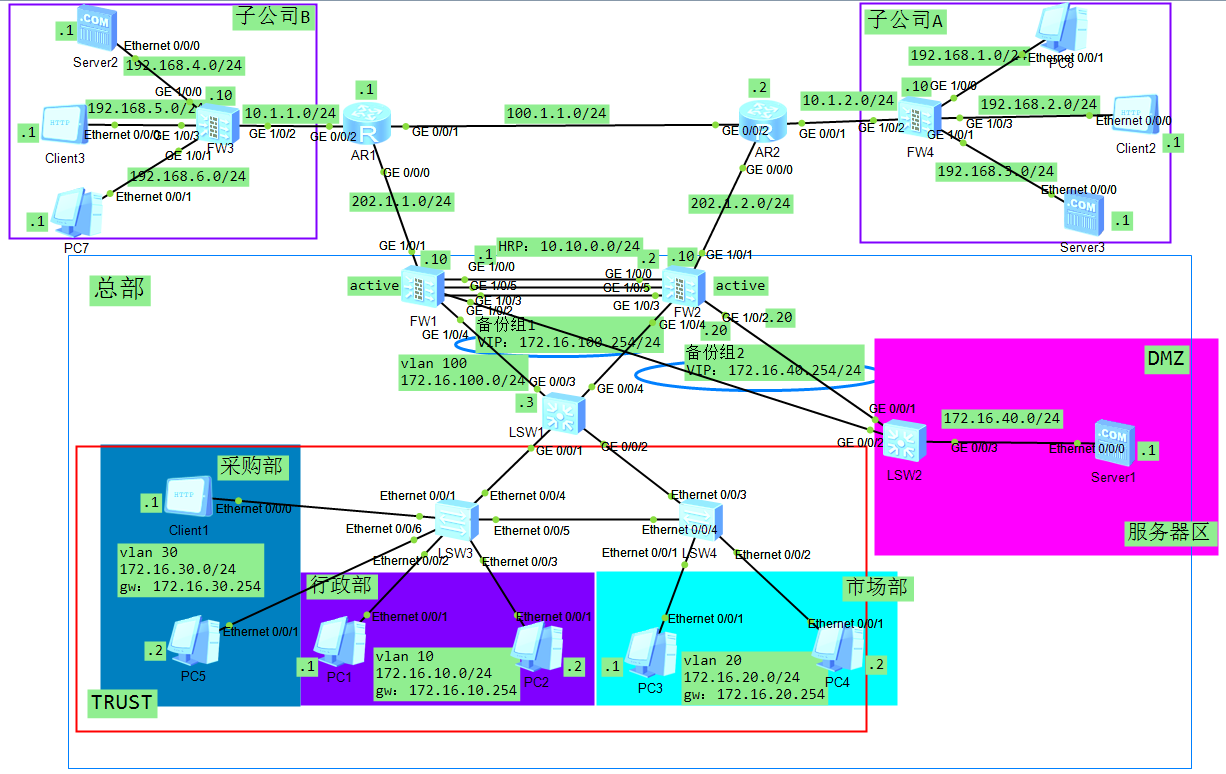
拓扑图
实验要求
1.总部在出口处部署双机热备负载分担模式,心跳线采用ETH-TRUNK链路聚合方式
2.内部网络访问总部服务器走内网网络,直接访问服务器真实内网地址;子公司访问总部HTTP/FTP服务器使用公网地址访问,
总部公司申请了200.1.1.100/24的公网地址供外网用户访问
3.子公司A与子公司B之间的通信使用加密通道进行通信
4.内网区域的各个部门访问子公司的服务器使用出接口方式访问
LSW1
//接口配置
#
vlan batch 10 20 30 100
#
#
interface Vlanif10
ip address 172.16.10.254 255.255.255.0
#
interface Vlanif20
ip address 172.16.20.254 255.255.255.0
#
interface Vlanif30
ip address 172.16.30.254 255.255.255.0
#
interface Vlanif100
ip address 172.16.100.3 255.255.255.0
#
#
interface GigabitEthernet0/0/1
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 10 20 30
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 10 20 30
#
interface GigabitEthernet0/0/3
port link-type access
port default vlan 100
#
interface GigabitEthernet0/0/4
port link-type access
port default vlan 100
#
//路由配置
#
ip route-static 0.0.0.0 0.0.0.0 172.16.100.254
#
LSW2
此交换机仅做转发,不做任何配置
LSW3
//接口配置
#
vlan batch 10 20 30
#
#
interface Ethernet0/0/1
port link-type access
port default vlan 30
#
interface Ethernet0/0/2
port link-type access
port default vlan 10
#
interface Ethernet0/0/3
port link-type access
port default vlan 10
#
interface Ethernet0/0/4
port link-type trunk
port trunk allow-pass vlan 10 20 30
#
interface Ethernet0/0/5
port link-type trunk
port trunk allow-pass vlan 10 20 30
#
interface Ethernet0/0/6
port link-type access
port default vlan 30
#
LSW4
//接口配置
#
vlan batch 10 20 30
#
#
interface Ethernet0/0/1
port link-type access
port default vlan 20
#
interface Ethernet0/0/2
port link-type access
port default vlan 20
#
interface Ethernet0/0/3
port link-type trunk
port trunk allow-pass vlan 10 20 30
#
interface Ethernet0/0/4
port link-type trunk
port trunk allow-pass vlan 10 20 30
#
AR1
//接口配置
#
interface GigabitEthernet0/0/0
ip address 202.1.1.1 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 100.1.1.1 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 10.1.1.1 255.255.255.0
#
//路由配置
#
ip route-static 10.1.2.0 255.255.255.0 100.1.1.2
ip route-static 192.168.0.0 255.255.248.0 10.1.1.10
ip route-static 192.168.0.0 255.255.252.0 100.1.1.2
ip route-static 200.1.1.0 255.255.255.0 202.1.1.10
ip route-static 200.1.1.0 255.255.255.0 100.1.1.2
ip route-static 202.1.2.0 255.255.255.0 100.1.1.2
#
AR2
//接口配置
#
interface GigabitEthernet0/0/0
ip address 202.1.2.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 10.1.2.2 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 100.1.1.2 255.255.255.0
#
//路由配置
#
ip route-static 10.1.1.0 255.255.255.0 100.1.1.1
ip route-static 192.168.0.0 255.255.248.0 100.1.1.1
ip route-static 192.168.0.0 255.255.252.0 10.1.2.10
ip route-static 200.1.1.0 255.255.255.0 202.1.2.10
ip route-static 202.1.1.0 255.255.255.0 100.1.1.1
#
FW1
//接口配置
#
interface Eth-Trunk1 //聚合链路,g1/0/0 1/0/5 1/0/3
ip address 10.10.0.1 255.255.255.0
#
#
interface GigabitEthernet1/0/0
undo shutdown
eth-trunk 1
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 202.1.1.10 255.255.255.0
service-manage ping permit
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 172.16.40.10 255.255.255.0
vrrp vrid 2 virtual-ip 172.16.40.254 active
service-manage ping permit
#
interface GigabitEthernet1/0/3
undo shutdown
eth-trunk 1
#
interface GigabitEthernet1/0/4
undo shutdown
ip address 172.16.100.10 255.255.255.0
vrrp vrid 1 virtual-ip 172.16.100.254 active
service-manage ping permit
#
//心跳线采用ETH-TRUNK链路聚合方式
//大致命令如下:
[FW2]int Eth-Trunk 1
[FW2-Eth-Trunk1]ip address 10.10.0.2 24
[FW2-Eth-Trunk1]trunkport GigabitEthernet 1/0/0 1/0/3 1/0/5
[FW2]dis eth-trunk
[FW2]hrp mirror session enable
[FW2]hrp interface Eth-Trunk 1 remote 10.10.0.1
[FW2]hrp enable
HRP_S[FW2]dis hrp state verbose
//安全区域及安全策略
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/4
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
#
firewall zone dmz
set priority 50
add interface Eth-Trunk1
add interface GigabitEthernet1/0/2
#
#
security-policy
rule name 1
source-zone trust
destination-zone dmz
action permit
rule name 2
source-zone untrust
destination-zone dmz
action permit
#
//总部内网不访问外网,服务器被动接受外网访问
//心跳配置,双机热备配置
#
hrp enable
hrp interface Eth-Trunk1 remote 10.10.0.2
hrp mirror session enable
hrp track interface Eth-Trunk1
hrp track interface GigabitEthernet1/0/1
hrp track interface GigabitEthernet1/0/2
hrp track interface GigabitEthernet1/0/4
#
//路由配置
#
ip route-static 0.0.0.0 0.0.0.0 202.1.1.1
ip route-static 172.16.0.0 255.255.224.0 172.16.100.3
#
//nat策略及nat server配置
#
nat server server1 protocol tcp global 200.1.1.100 www inside 172.16.40.1 www no-reverse
#
#
nat-policy
rule name nat1
source-zone trust
destination-zone untrust
action source-nat easy-ip
#
FW2
//接口配置
#
interface Eth-Trunk1
ip address 10.10.0.2 255.255.255.0
#
#
interface GigabitEthernet1/0/0
undo shutdown
eth-trunk 1
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 202.1.2.10 255.255.255.0
service-manage ping permit
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 172.16.40.20 255.255.255.0
vrrp vrid 2 virtual-ip 172.16.40.254 active
service-manage ping permit
#
interface GigabitEthernet1/0/3
undo shutdown
eth-trunk 1
#
interface GigabitEthernet1/0/4
undo shutdown
ip address 172.16.100.20 255.255.255.0
vrrp vrid 1 virtual-ip 172.16.100.254 active
service-manage ping permit
#
interface GigabitEthernet1/0/5
undo shutdown
eth-trunk 1
#
//安全区域及安全策略
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/4
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
#
firewall zone dmz
set priority 50
add interface Eth-Trunk1
add interface GigabitEthernet1/0/2
#
#
security-policy
rule name 1
source-zone trust
destination-zone dmz
action permit
rule name 2
source-zone untrust
destination-zone dmz
action permit
#
//心跳配置,双机热备配置
#
hrp enable
hrp interface Eth-Trunk1 remote 10.10.0.1
hrp mirror session enable
hrp track interface Eth-Trunk1
hrp track interface GigabitEthernet1/0/1
hrp track interface GigabitEthernet1/0/2
hrp track interface GigabitEthernet1/0/4
#
//路由配置
#
ip route-static 0.0.0.0 0.0.0.0 202.1.2.2
ip route-static 172.16.0.0 255.255.224.0 172.16.100.3
#
//nat策略及nat server配置
#
nat server server1 protocol tcp global 200.1.1.100 www inside 172.16.40.1 www no-reverse
#
#
nat-policy
rule name nat1
source-zone trust
destination-zone untrust
action source-nat easy-ip
#
FW3
//接口配置
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 192.168.4.10 255.255.255.0
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 192.168.6.10 255.255.255.0
service-manage ping permit
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 10.1.1.10 255.255.255.0
service-manage ping permit
ipsec policy map
#
interface GigabitEthernet1/0/3
undo shutdown
ip address 192.168.5.10 255.255.255.0
#
//acl数据流.......
#
acl number 3000
rule 5 permit ip source 192.168.6.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule 10 permit ip source 192.168.5.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
rule 15 permit ip source 192.168.4.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
#
#
ipsec proposal tran
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike proposal 10
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
ike peer fw4
pre-shared-key %^%#AYPHHt]k60aALrO>PsaP0(4*<UA".4ytkj,L4_LE%^%# //Test!123
ike-proposal 10
remote-address 10.1.2.10
#
ipsec policy map 10 isakmp
security acl 3000
ike-peer fw4
proposal tran
#
//安全区域及安全策略
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
add interface GigabitEthernet1/0/1
add interface GigabitEthernet1/0/3
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/2
#
firewall zone dmz
set priority 50
#
#
security-policy
rule name 1
source-zone trust
source-zone untrust
destination-zone trust
destination-zone untrust
action permit
rule name 2
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
action permit
#
//路由配置
#
ip route-static 0.0.0.0 0.0.0.0 10.1.1.1
#
FW4
//接口配置
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 192.168.1.10 255.255.255.0
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 192.168.3.10 255.255.255.0
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 10.1.2.10 255.255.255.0
ipsec policy map
#
interface GigabitEthernet1/0/3
undo shutdown
ip address 192.168.2.10 255.255.255.0
#
//acl数据流.......
#
acl number 3000
rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.6.0 0.0.0.255
rule 10 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.4.0 0.0.0.25
5
rule 15 permit ip source 192.168.3.0 0.0.0.255 destination 192.168.5.0 0.0.0.25
5
#
#
ipsec proposal tran
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike proposal 10
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
ike peer fw3
pre-shared-key %^%#8o,..LFy+2&.z8Ma<jqQ_G!Q#}{0(*Ty^T8U2,RS%^%#
ike-proposal 10
remote-address 10.1.1.10
#
ipsec policy map 10 isakmp
security acl 3000
ike-peer fw3
proposal tran
#
//安全区域及安全策略
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
add interface GigabitEthernet1/0/1
add interface GigabitEthernet1/0/3
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/2
#
firewall zone dmz
set priority 50
#
#
security-policy
rule name 1
source-zone trust
source-zone untrust
destination-zone trust
destination-zone untrust
action permit
rule name 2
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
action permit
#
//路由配置
#
ip route-static 0.0.0.0 0.0.0.0 10.1.2.2
#
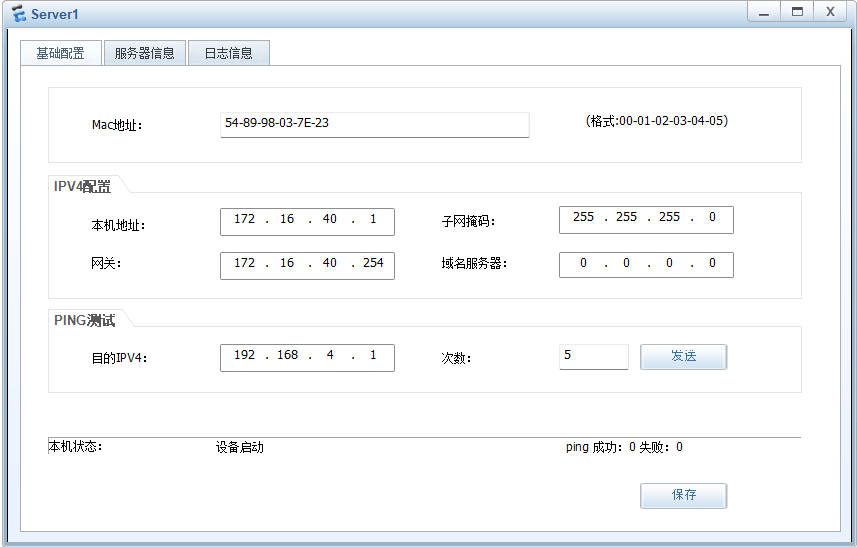
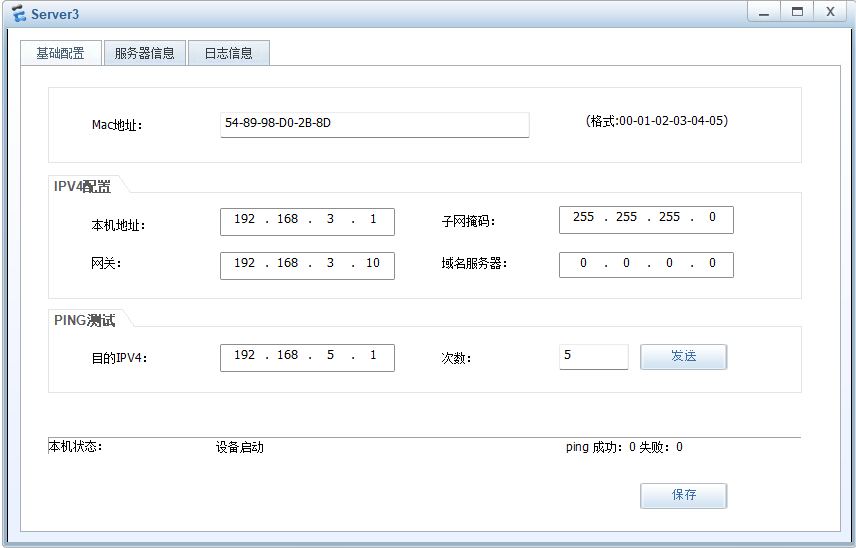
PC and 客户端

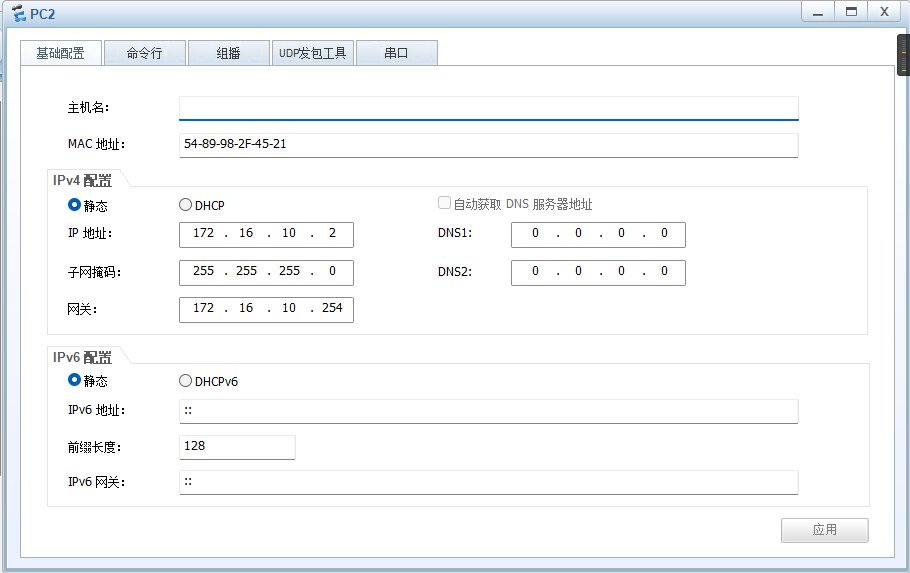
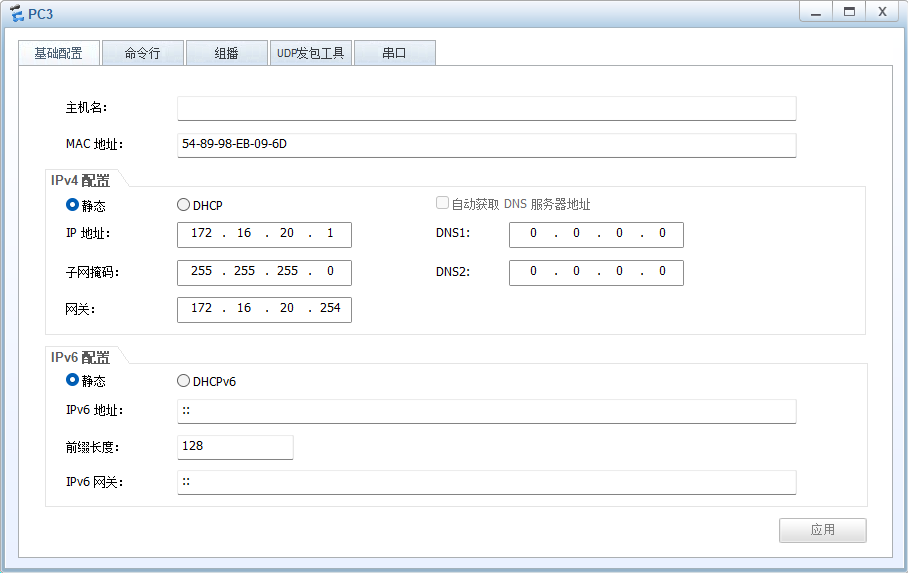
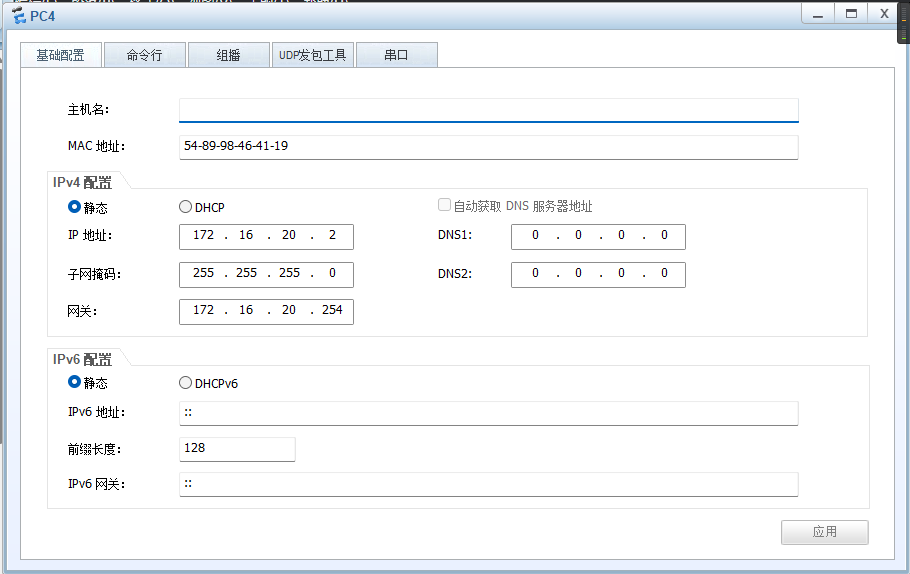
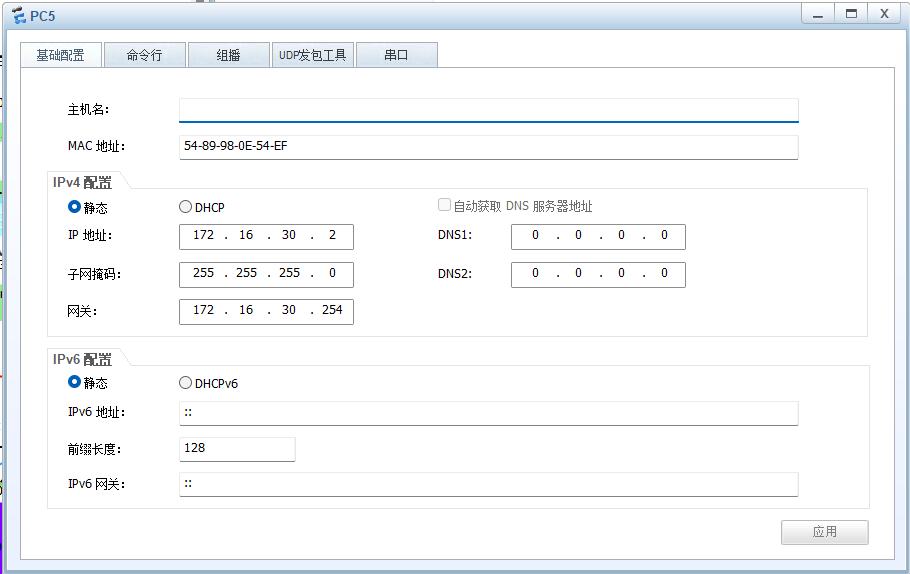
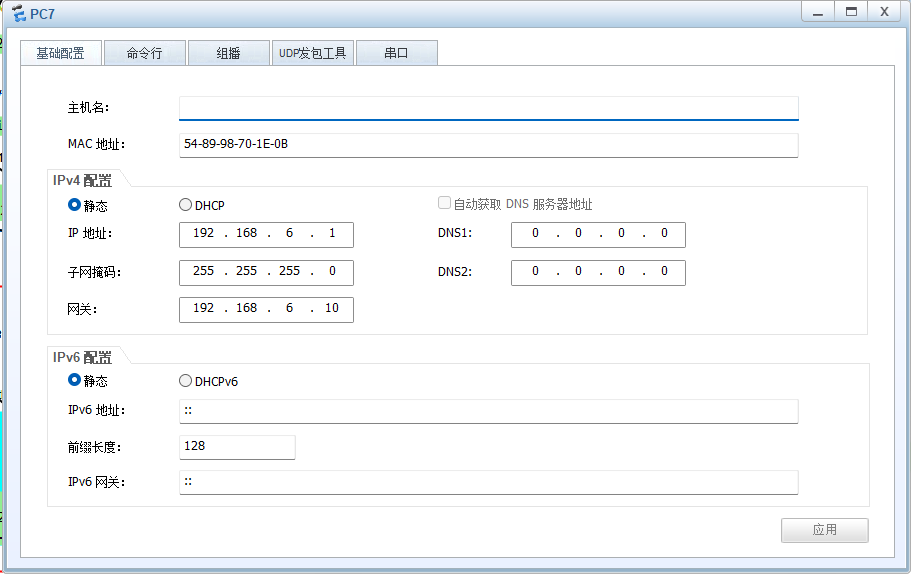
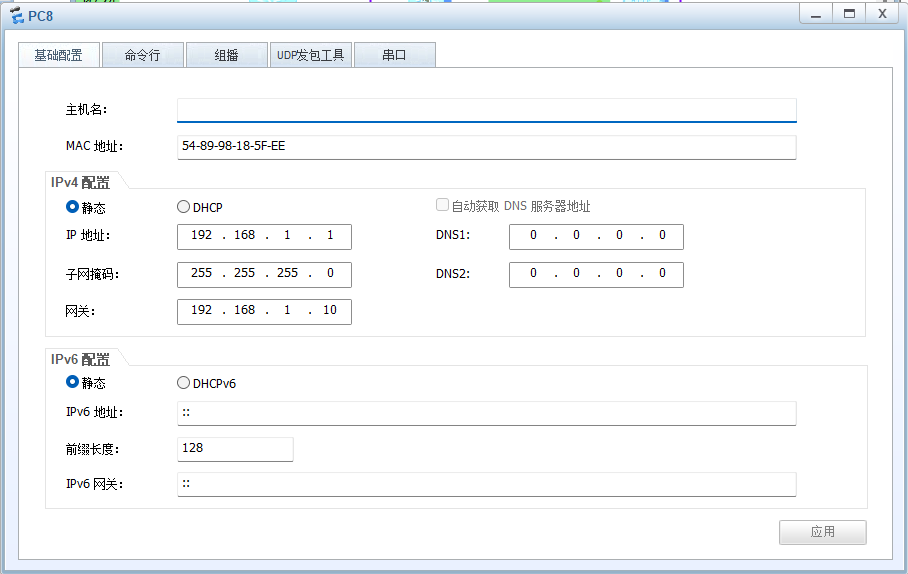
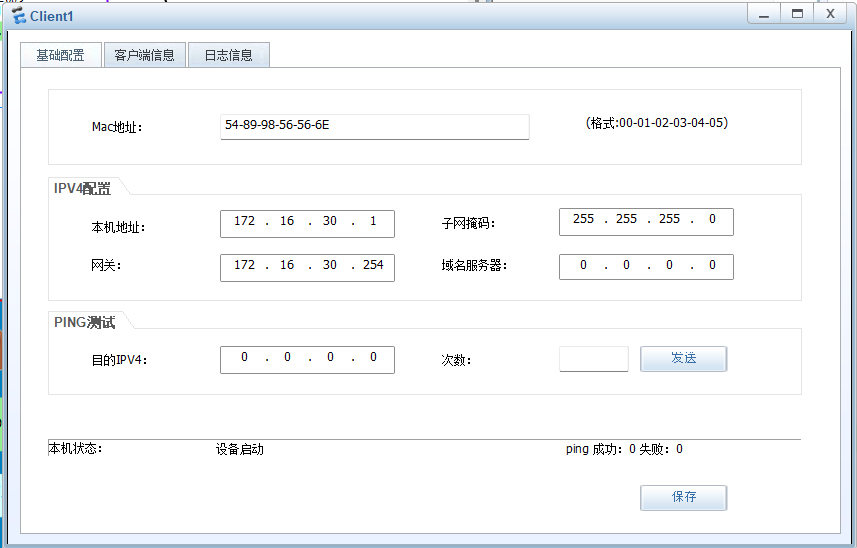
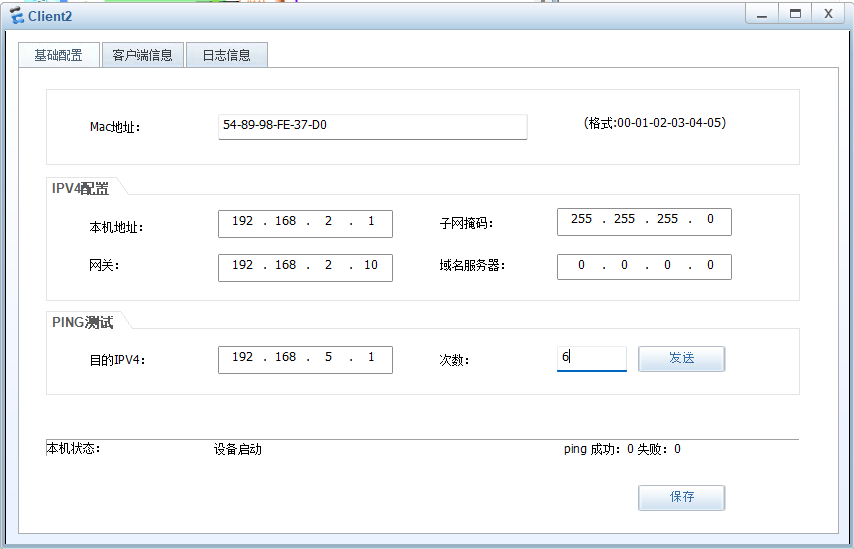
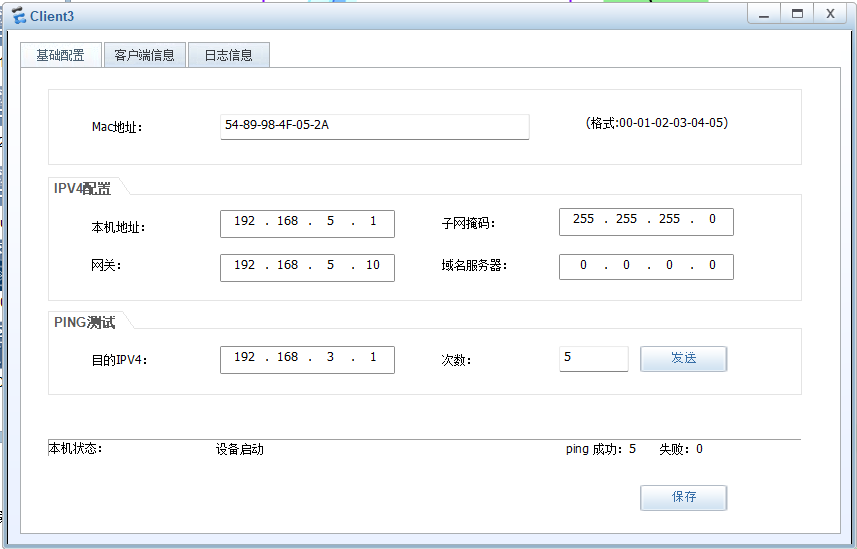
服务器

测试
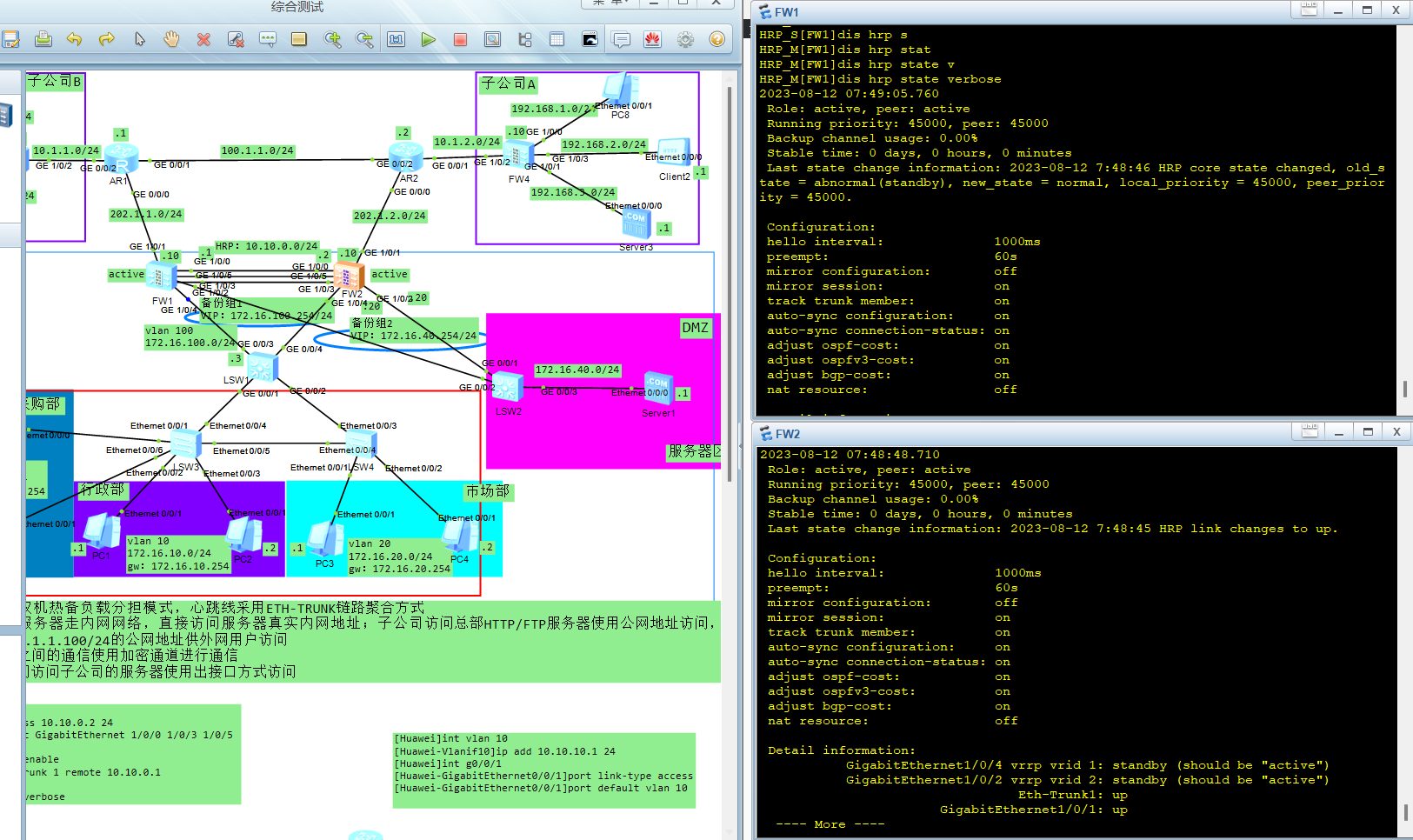
双机热备故障及回切,当LSW1G0/0/3出现故障时,查看抓包情况
故障前
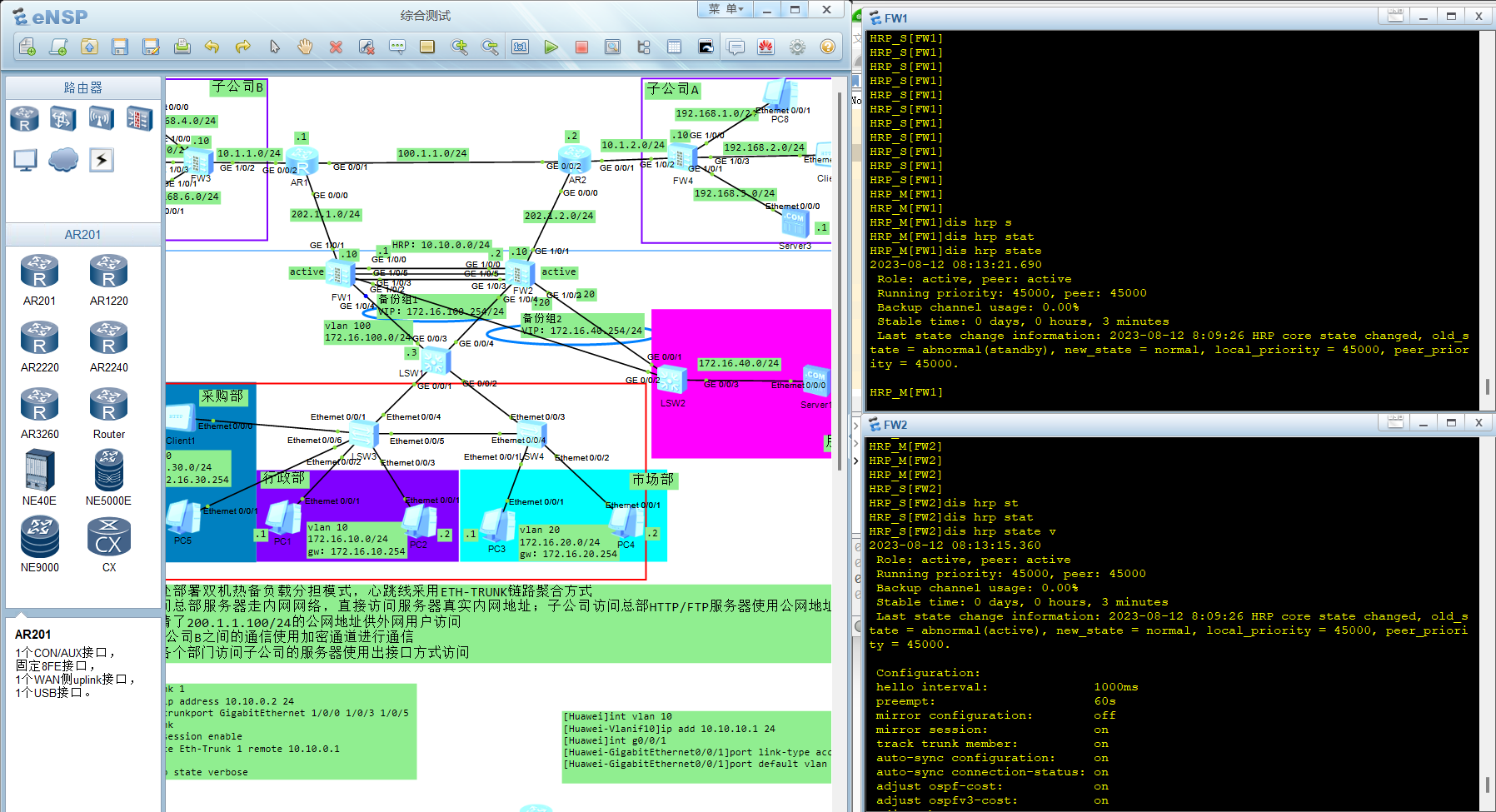
查看双机热备负载分担状态
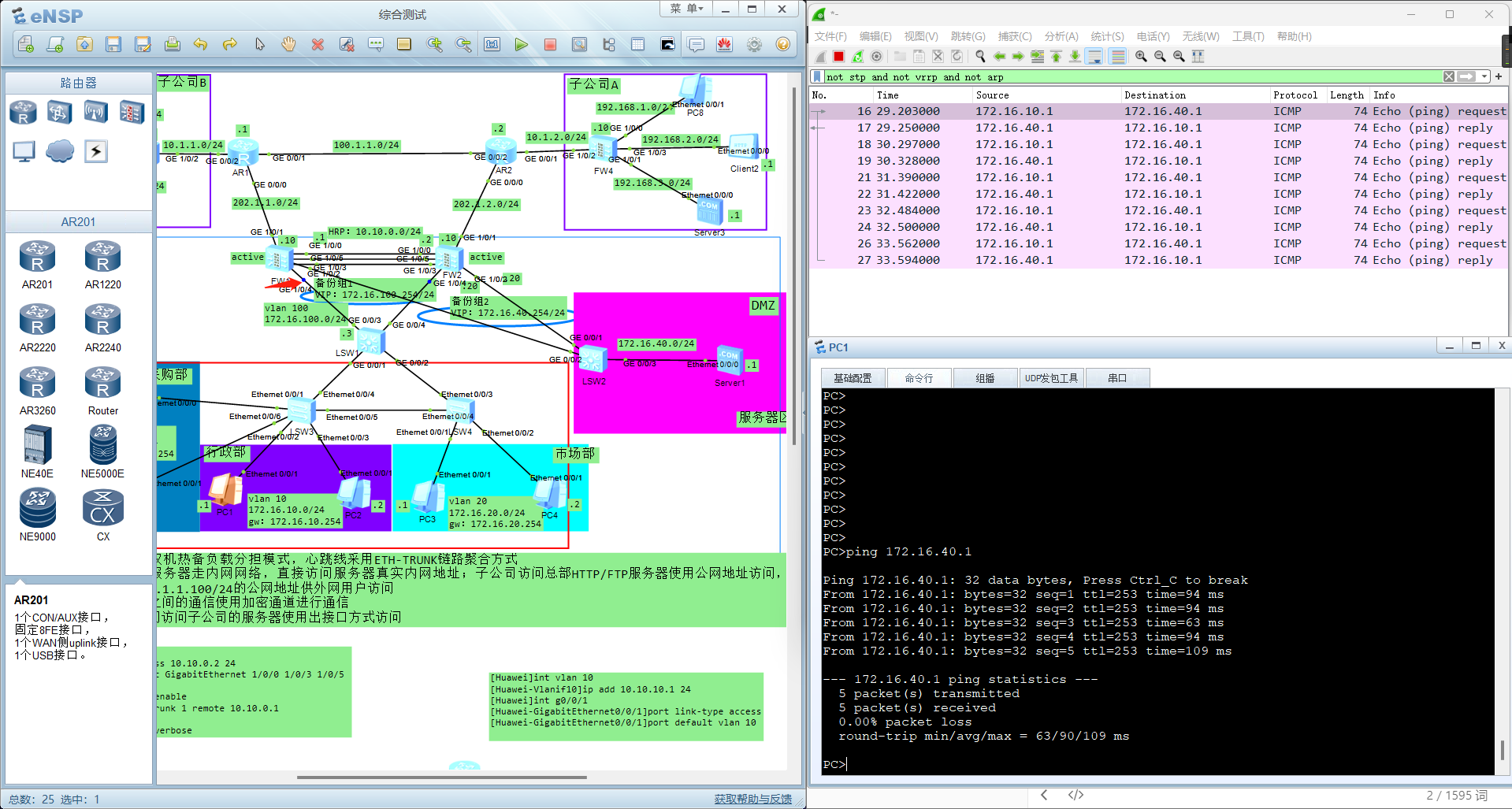
抓包查看
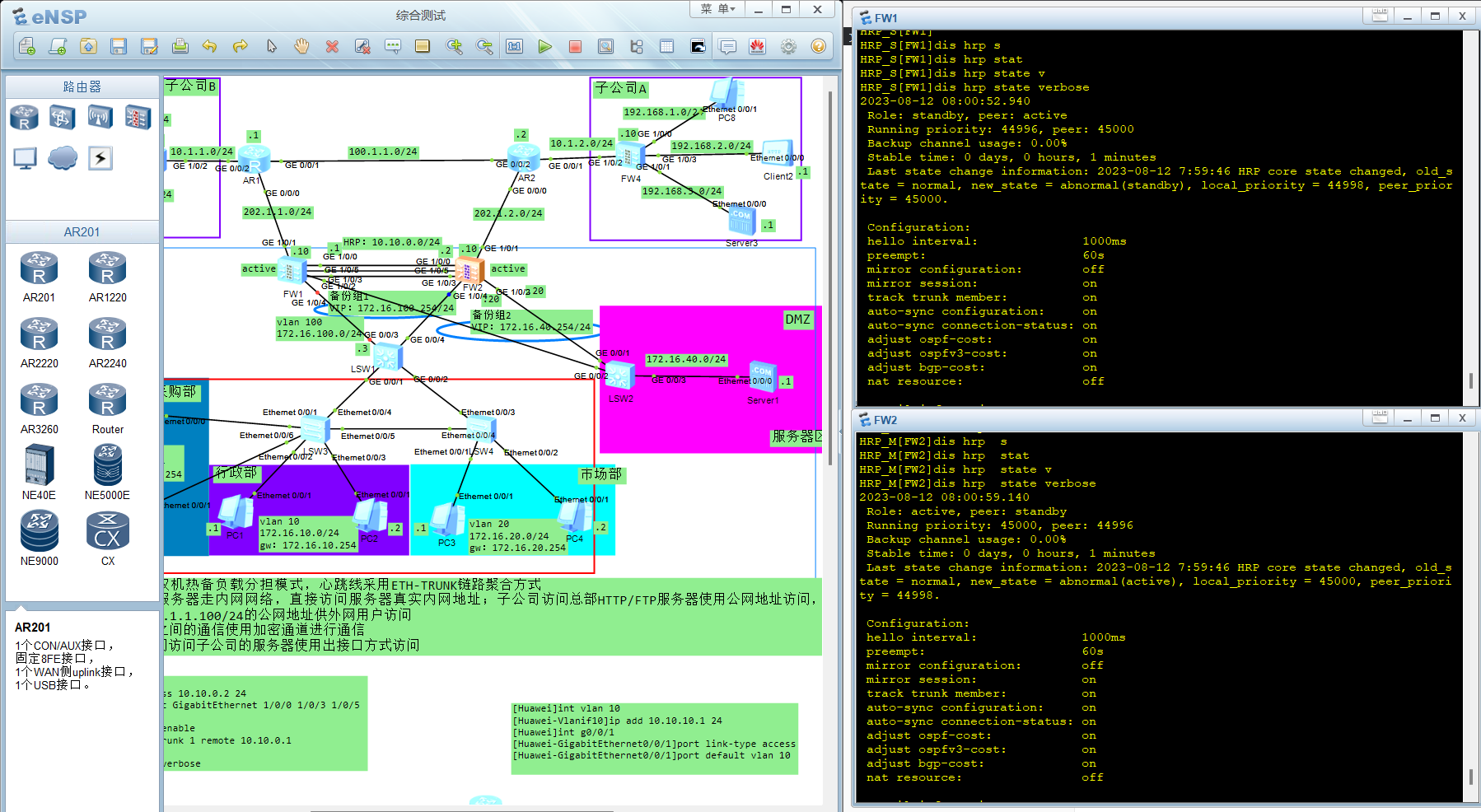
故障后
查看双机热备状态
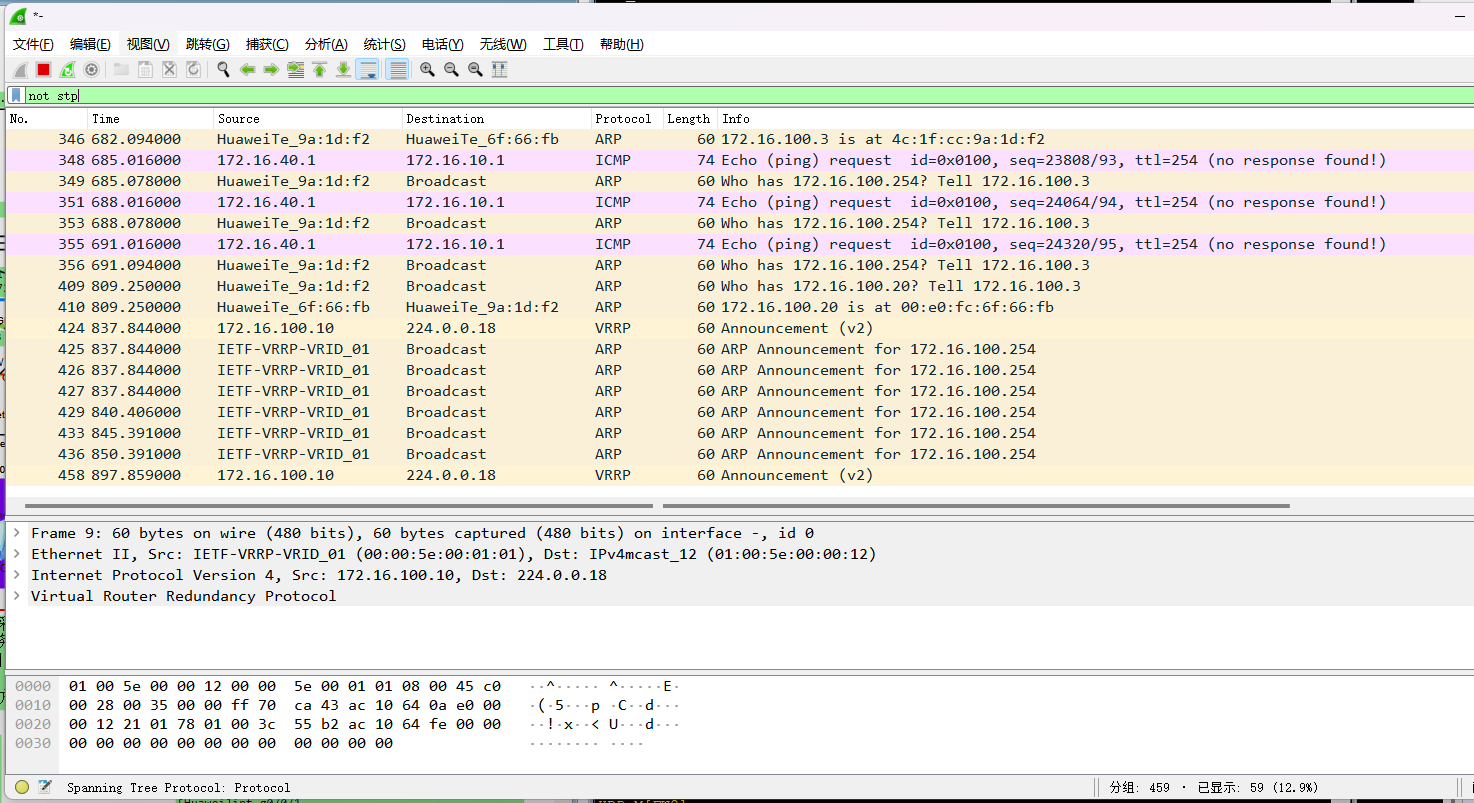
故障恢复后,故障回切
两个接口的回切动作抓包

查看双机热备负载分担状态
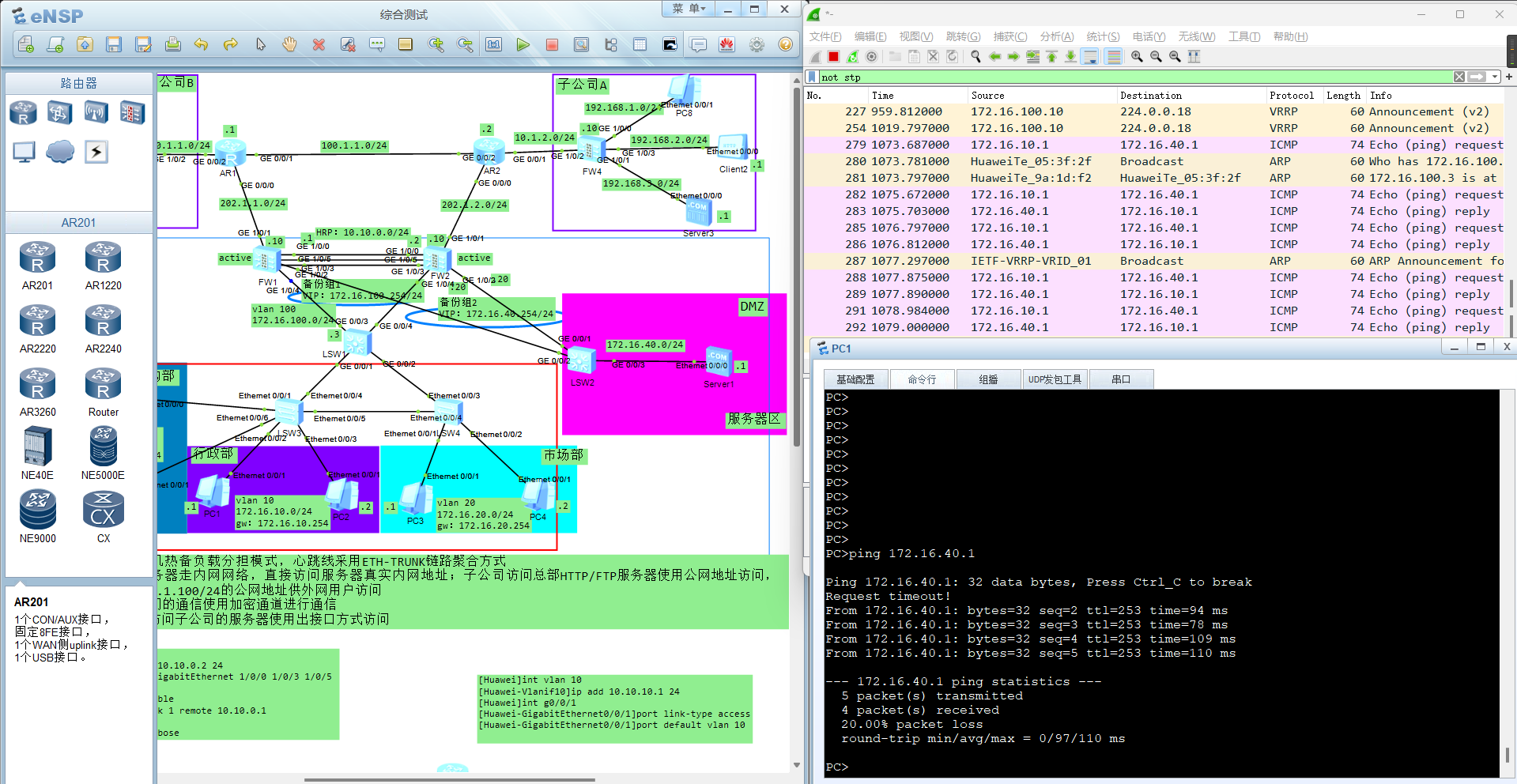
总部内部网络访问总部服务器时,使用内网真实地址
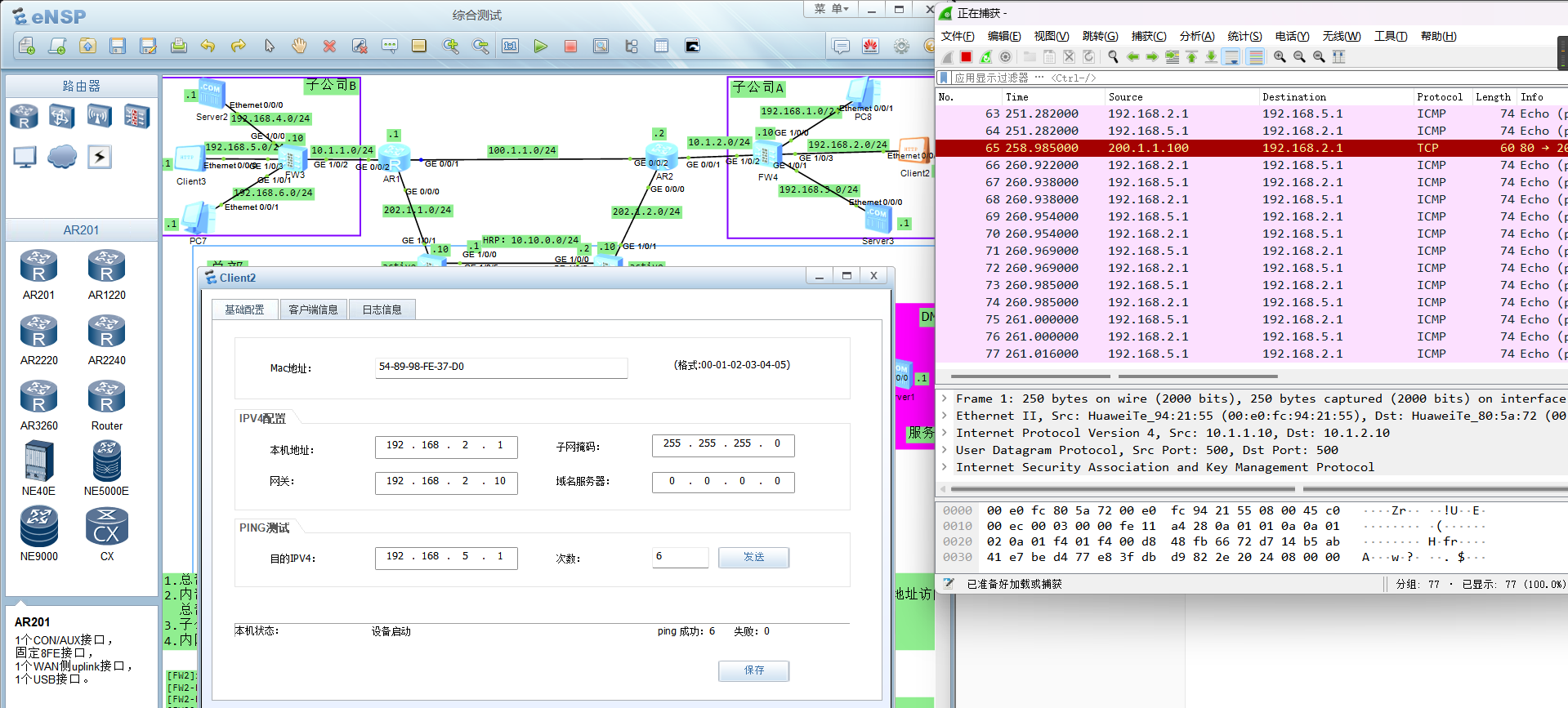
子公司通过公网地址去访问服务器

内网访问子公司使用地址转换出接口方式,保护内网真实地址

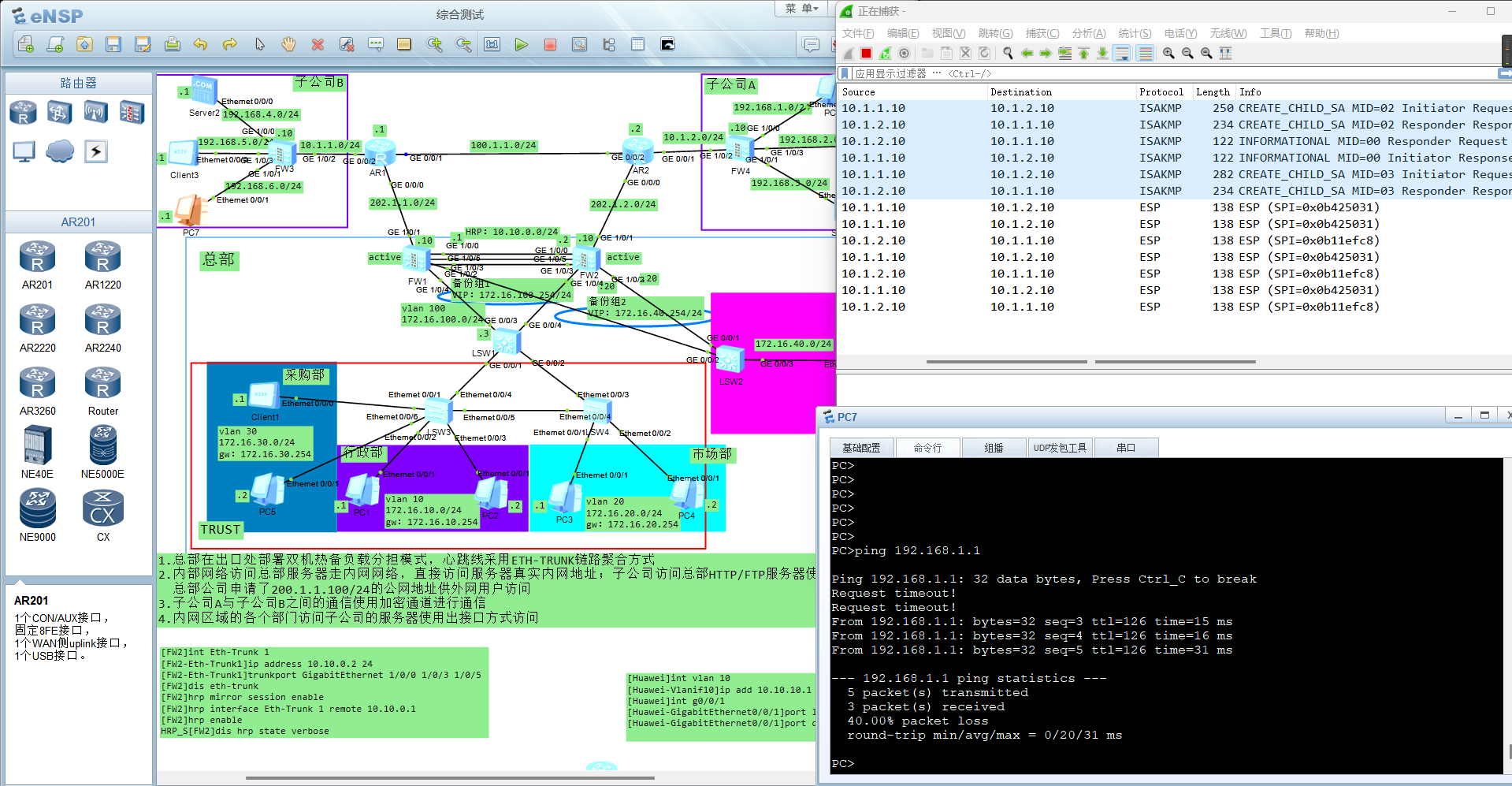
子公司之间的通信使用加密隧道进行通信
PC7→PC8
子公司 客户端之间访问 不走隧道
子公司之间 客户端访问服务器 走隧道
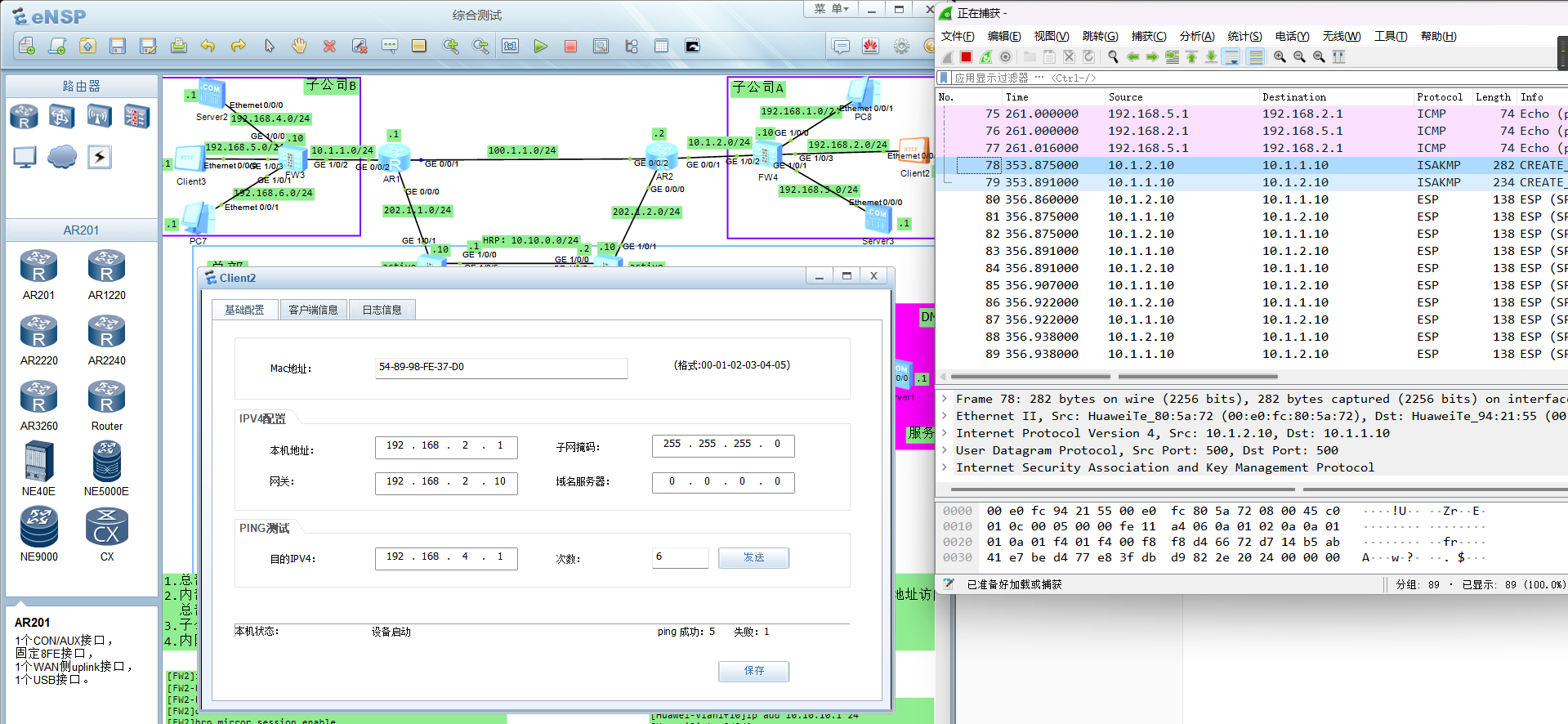
回顾总结:
1、本次实验应用知识点包括,IPSec VPN 技术、防火墙双机热备的负载分担模式,跨vlan通信技术,三层交换技术,心跳线ETH-TRUNK链路聚合技术,NAT转换–源地址转换–出接口的easy-ip模式(只做端口转换),nat策略及nat server配置
2、本次实验出现的主要问题,nat server配置及原理不熟悉,各设备的静态路由配置不够得心应手,数通部分知识有待加强
























 1467
1467











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








