网址请见:https://www.openssl.org/docs/HOWTO/keys.txt
1. Introduction
Keys are the basis of public key algorithms and PKI. Keys usually
come in pairs, with one half being the public key and the other half
being the private key. With OpenSSL, the private key contains the
public key information as well, so a public key doesn’t need to be
generated separately.
Public keys come in several flavors, using different cryptographic
algorithms. The most popular ones associated with certificates are
RSA and DSA, and this HOWTO will show how to generate each of them.
密钥是PKI的基础,密钥成对出现,一个公钥,一个私钥。私钥中都含有公钥信息,所以不用从新生成公钥。
算法不同,密钥不同。根据证书来说,最常用的是RSA和DSA。
2. To generate a RSA key
A RSA key can be used both for encryption and for signing.
Generating a key for the RSA algorithm is quite easy, all you have to do is the following:
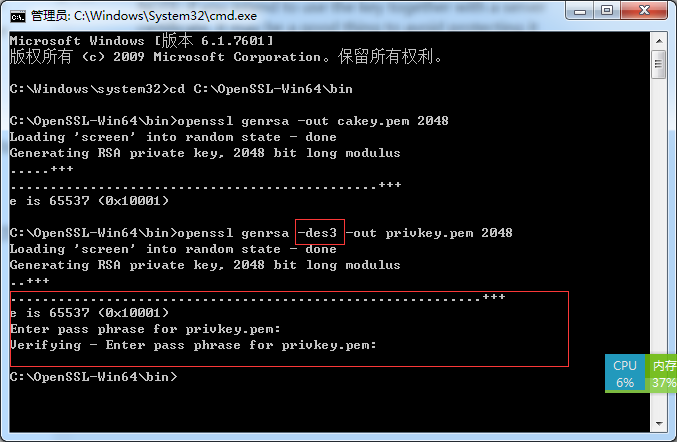
openssl genrsa -des3 -out privkey.pem 2048
生成RSA密钥很简单,只需要如上一行代码
With this variant, you will be prompted for a protecting password. If you don’t want your key to be protected by a password, remove the flag ‘-des3’ from the command line above.
NOTE: if you intend to use the key together with a server
certificate, it may be a good thing to avoid protecting it
with a password, since that would mean someone would have to
type in the password every time the server needs to access
如果不想让生成私钥用3des加密的话,去掉-des3
注意:如果你想把私钥和证书一起用的话,不用加密保护更好,否则每次使用密钥的时候都要输入密码
是否加入-des3的区别如图
The number 2048 is the size of the key, in bits. Today, 2048 or
higher is recommended for RSA keys, as fewer amount of bits is
consider insecure or to be insecure pretty soon.
2048是密钥的位数,推荐使用2048及以上的位数。
- To generate a DSA key
A DSA key can be used for signing only. This is important to keep
in mind to know what kind of purposes a certificate request with a
DSA key can really be used for.
DSA算法只用作签名,这对于调用证书DSA密钥的目的很重要
Generating a key for the DSA algorithm is a two-step process. First,you have to generate parameters from which to generate the key:
openssl dsaparam -out dsaparam.pem 2048
生成DSA密钥需要两步,首先生成参数dsaparam.pem
The number 2048 is the size of the key, in bits. Today, 2048 or
higher is recommended for DSA keys, as fewer amount of bits is
consider insecure or to be insecure pretty soon.
2048是密钥的位数,如今推荐2048或更高保障安全。
When that is done, you can generate a key using the parameters in
question (actually, several keys can be generated from the same
parameters):
输入如下命令生成DSA密钥,从命令可以看出来DSA是通过刚刚生成的私钥和参数生成的。
openssl gendsa -des3 -out privkey.pem dsaparam.pem
With this variant, you will be prompted for a protecting password. If you don’t want your key to be protected by a password, remove the flag’-des3’ from the command line above.
NOTE: if you intend to use the key together with a server
certificate, it may be a good thing to avoid protecting it
with a password, since that would mean someone would have to
type in the password every time the server needs to access
the key.








 本文档介绍了如何使用OpenSSL生成RSA和DSA密钥对。RSA密钥可用于加密和签名,生成过程简单,可通过移除'-des3'标志来选择是否设置密码保护。DSA密钥仅用于签名,其生成分为两步,先创建参数文件,再生成密钥,同样可选择是否加密码保护。
本文档介绍了如何使用OpenSSL生成RSA和DSA密钥对。RSA密钥可用于加密和签名,生成过程简单,可通过移除'-des3'标志来选择是否设置密码保护。DSA密钥仅用于签名,其生成分为两步,先创建参数文件,再生成密钥,同样可选择是否加密码保护。














 2万+
2万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








