strace ./sysmagic
用来跟踪sysmagic运行时的系统函数调用情况
iqiqiya@521:~/Desktop/gdb$ strace ./sysmagic
execve("./sysmagic", ["./sysmagic"], [/* 61 vars */]) = 0
[ Process PID=5667 runs in 32 bit mode. ]
brk(0) = 0x9261000
access("/etc/ld.so.nohwcap", F_OK) = -1 ENOENT (No such file or directory)
mmap2(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0xfffffffff7799000
access("/etc/ld.so.preload", R_OK) = -1 ENOENT (No such file or directory)
open("/etc/ld.so.cache", O_RDONLY|O_CLOEXEC) = 3
fstat64(3, {st_mode=S_IFREG|0644, st_size=98371, ...}) = 0
mmap2(NULL, 98371, PROT_READ, MAP_PRIVATE, 3, 0) = 0xfffffffff7780000
close(3) = 0
access("/etc/ld.so.nohwcap", F_OK) = -1 ENOENT (No such file or directory)
open("/lib32/libc.so.6", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\1\1\1\0\0\0\0\0\0\0\0\0\3\0\3\0\1\0\0\0000\234\1\0004\0\0\0"..., 512) = 512
fstat64(3, {st_mode=S_IFREG|0755, st_size=1750780, ...}) = 0
mmap2(NULL, 1759868, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0xfffffffff75d2000
mmap2(0xf777a000, 12288, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x1a7000) = 0xfffffffff777a000
mmap2(0xf777d000, 10876, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0xfffffffff777d000
close(3) = 0
mmap2(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0xfffffffff75d1000
set_thread_area(0xffb7f2b0) = 0
mprotect(0xf777a000, 8192, PROT_READ) = 0
mprotect(0x8049000, 4096, PROT_READ) = 0
mprotect(0xf77be000, 4096, PROT_READ) = 0
munmap(0xf7780000, 98371) = 0
open("/dev/urandom", O_RDONLY) = 3
read(3, "\275\201N\214", 4) = 4
write(1, "Give me maigc :", 15Give me maigc :) = 15
fstat64(0, {st_mode=S_IFCHR|0620, st_rdev=makedev(136, 0), ...}) = 0
mmap2(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0xfffffffff7798000
read(0, 11111111111
"11111111111\n", 1024) = 12
exit_group(0) = ?
+++ exited with 0 +++
ltrace ./sysmagic
用来跟踪sysmagic运行时的所有库调用情况
可以看到下面有scanf与printf函数
iqiqiya@521:~/Desktop/gdb$ ltrace ./sysmagic
__libc_start_main(0x8048774, 1, 0xff991024, 0x80487b0 <unfinished ...>
setvbuf(0xf76c2ac0, 0, 2, 0) = 0
open("/dev/urandom", 0, 036734054470) = 3
read(3, "\242\347u\275", 4) = 4
printf("Give me maigc :"Give me maigc :) = 15
__isoc99_scanf(0x804884d, 0xff990eec, 4, 111111111111
) = 1
+++ exited (status 0) +++
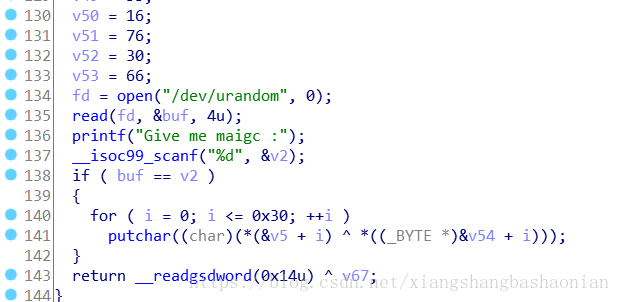
而这个elf文件用IDA反编译之后是这样的
























 212
212











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








