限流用于控制发送到上游服务的请求速率。 它可用于防止 DoS 攻击、限制网络抓取和其他形式的过度使用。 如果没有速率限制,客户可以无限制地访问您的上游服务,这可能会对可用性产生负面影响。
一、全局范围内的限流
1、启用限流
[root@min ~]# curl -i -X POST http://localhost:8001/plugins \
> --data name=rate-limiting \
> --data config.second=5 \
> --data config.policy=local
HTTP/1.1 201 Created
Date: Tue, 30 May 2023 15:08:12 GMT
Content-Type: application/json; charset=utf-8
Connection: keep-alive
Access-Control-Allow-Origin: http://localhost:8002
X-Kong-Admin-Request-ID: OA4KbAYVZzjlJliahJnwao89qZ3piJKj
vary: Origin
Access-Control-Allow-Credentials: true
Content-Length: 719
X-Kong-Admin-Latency: 9
Server: kong/3.3.0.0-enterprise-edition
{"created_at":1685459292,"consumer":null,"protocols":["grpc","grpcs","http","https"],"updated_at":1685459292,"ordering":null,"enabled":true,"instance_name":null,"id":"8503da12-0bd2-41fd-9db3-05e43d6dc74a","service":null,"name":"rate-limiting","tags":null,"config":{"redis_port":6379,"redis_username":null,"redis_password":null,"limit_by":"consumer","error_message":"API rate limit exceeded","policy":"local","redis_server_name":null,"path":null,"day":null,"redis_timeout":2000,"year":null,"header_name":null,"hide_client_headers":false,"redis_ssl_verify":false,"second":5,"redis_database":0,"fault_tolerant":true,"month":null,"error_code":429,"redis_ssl":false,"minute":null,"hour":null,"redis_host":null},"route":null}
2、测试限流
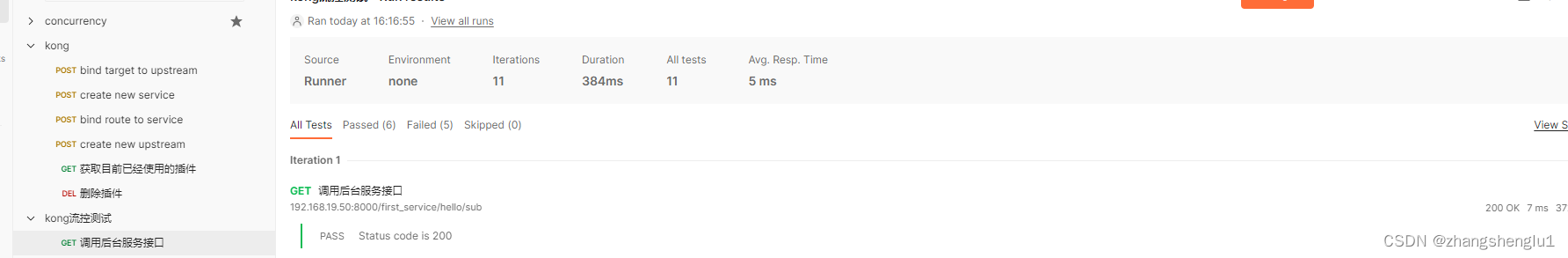
这里使用postman在1秒钟内发送10此请求,预期应该有五个请求通过。
2.1 、为请求的接口添加上只有当响应的状态码为200时候,测试通过
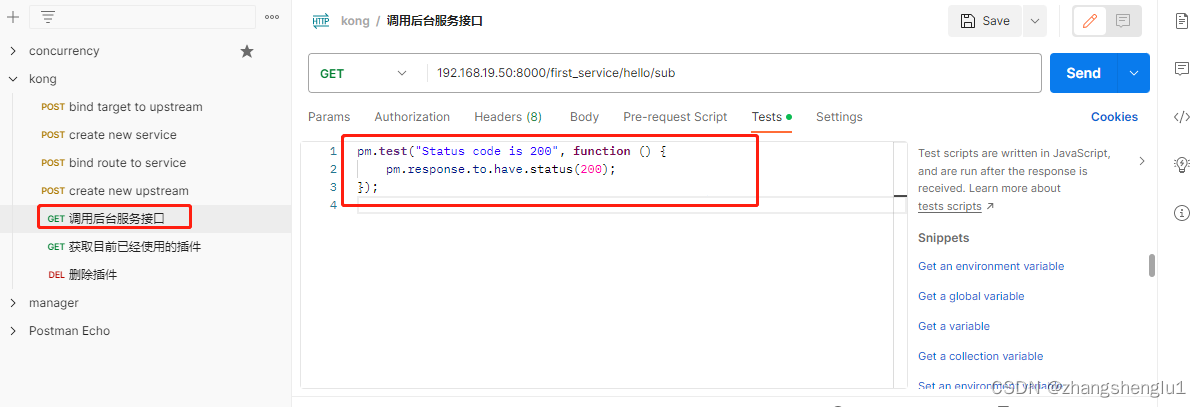
2.2、启动批量测试
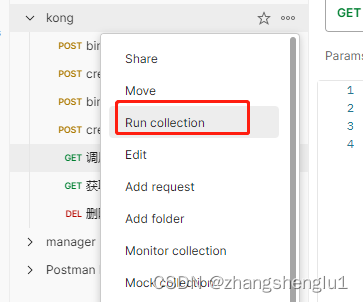
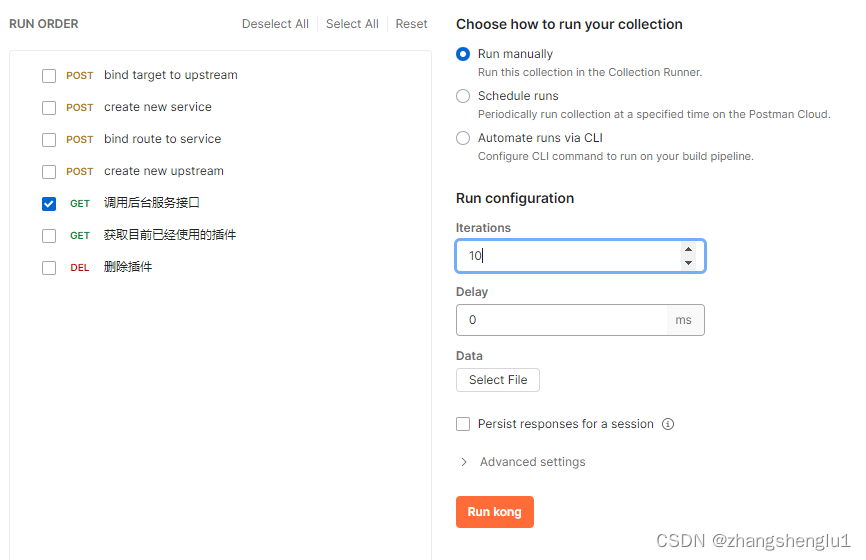
点击run kong
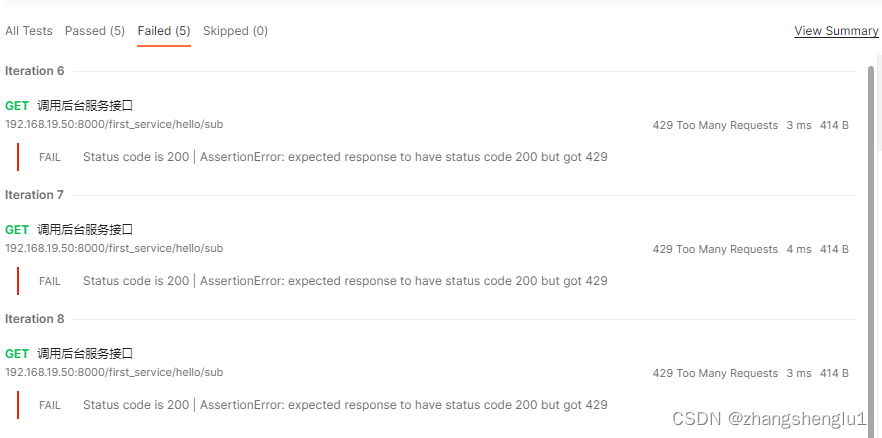
由此可以确定限流插件已经起作用了
二、 服务层级的限流
[root@min ~]# curl -X POST http://localhost:8001/services/first_service/plugins \
> --data "name=rate-limiting" \
> --data config.second=10 \
> --data config.policy=local
{"created_at":1685460463,"consumer":null,"protocols":["grpc","grpcs","http","https"],"updated_at":1685460463,"ordering":null,"enabled":true,"instance_name":null,"id":"d8f25f95-f61d-4666-b931-1a47c6158fde","service":{"id":"3aa00d3a-1f82-489a-bbe5-412c5e83c7c8"},"name":"rate-limiting","tags":null,"config":{"redis_port":6379,"redis_username":null,"redis_password":null,"limit_by":"consumer","error_message":"API rate limit exceeded","policy":"local","redis_server_name":null,"path":null,"day":null,"redis_timeout":2000,"year":null,"header_name":null,"hide_client_headers":false,"redis_ssl_verify":false,"second":10,"redis_database":0,"fault_tolerant":true,"month":null,"error_code":429,"redis_ssl":false,"minute":null,"hour":null,"redis_host":null},"route":null}
目前我们有两个限流配置,一个全局的每秒5个请求,服务层级的每秒10个请求。
服务级别会优先于全局级别的流控,即同时存在的时候以服务级别的限流为准
三、 route级别的流控限制
[root@min ~]# curl -X POST http://localhost:8001/routes/first_route/plugins \
> --data "name=rate-limiting" \
> --data config.second=6 \
> --data config.policy=local
{"created_at":1685461056,"consumer":null,"protocols":["grpc","grpcs","http","https"],"updated_at":1685461056,"ordering":null,"enabled":true,"instance_name":null,"id":"140831ea-a15f-431a-9aad-f3ea5ad16532","service":null,"name":"rate-limiting","tags":null,"config":{"redis_port":6379,"redis_username":null,"redis_password":null,"limit_by":"consumer","error_message":"API rate limit exceeded","policy":"local","redis_server_name":null,"path":null,"day":null,"redis_timeout":2000,"year":null,"header_name":null,"hide_client_headers":false,"redis_ssl_verify":false,"second":6,"redis_database":0,"fault_tolerant":true,"month":null,"error_code":429,"redis_ssl":false,"minute":null,"hour":null,"redis_host":null},"route":{"id":"3ef2a679-ba90-482d-96ff-2ca92dbce8f4"}}
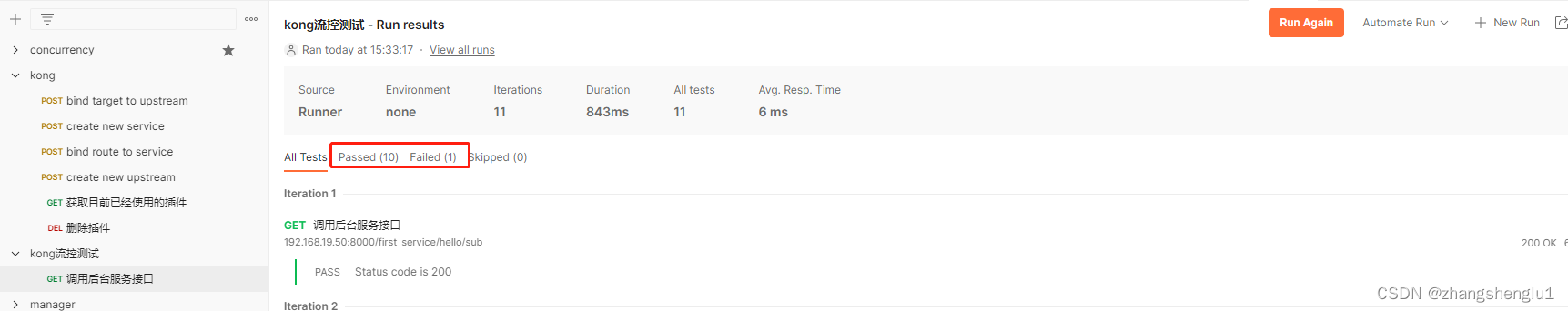
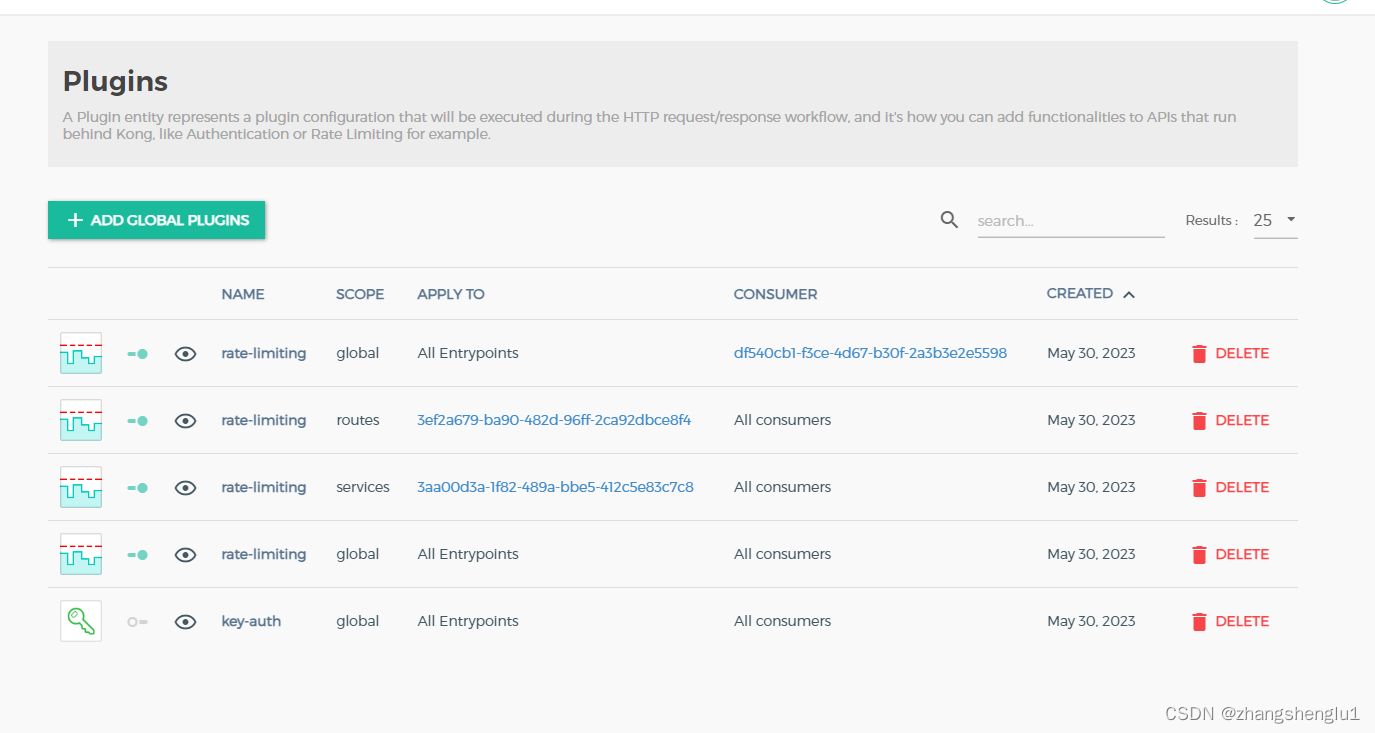
此时我们kong上面拥有三个流控配置,分配是全局5个/s,服务级别: 10个/s ,route级别 : 6个/s.在一秒内发起11个请求,响应的结果如下:
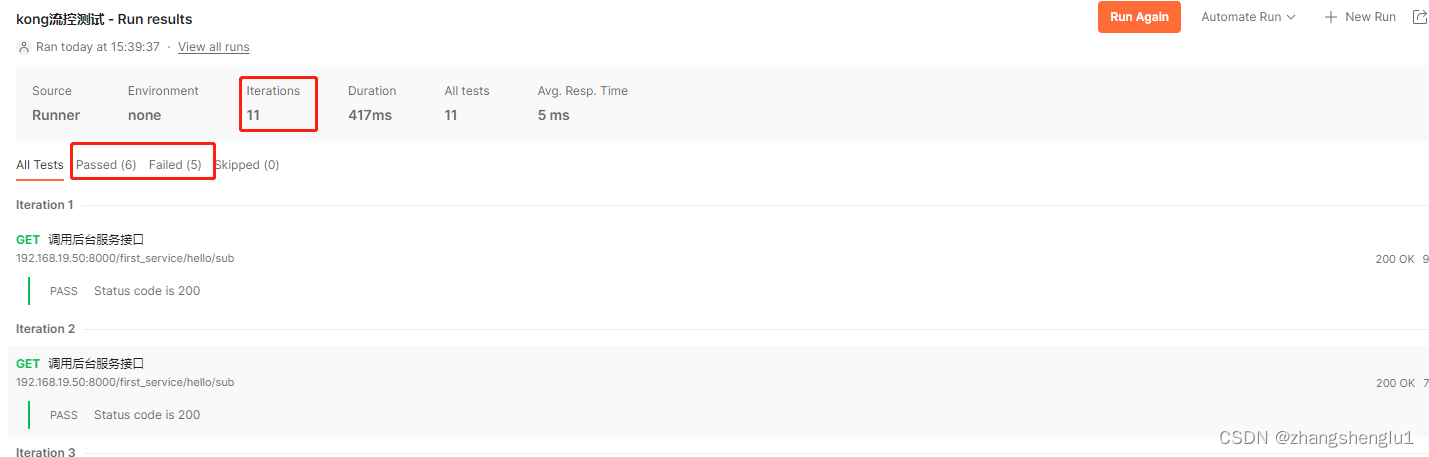
从这里我们可以看出当上面三种配置都存在的时候,将会以route路由配置的为准
四、用户级别的流控限制
4.1、创建一个新用户
[root@min ~]# curl -X POST http://localhost:8001/consumers/ \
> --data username=jsmith
{"created_at":1685461425,"custom_id":null,"username":"jsmith","tags":null,"type":0,"id":"df540cb1-f3ce-4d67-b30f-2a3b3e2e5598","username_lower":"jsmith","updated_at":1685461425}
4.2、为用户jsmith分配一个key
[root@min ~]# curl -i -X POST http://localhost:8001/consumers/jsmith/key-auth
HTTP/1.1 201 Created
Date: Tue, 30 May 2023 15:45:20 GMT
Content-Type: application/json; charset=utf-8
Connection: keep-alive
Access-Control-Allow-Origin: http://localhost:8002
X-Kong-Admin-Request-ID: HrG3mXhgQ0J4bXW4MnsfLLCn3KcHkWJt
vary: Origin
Access-Control-Allow-Credentials: true
Content-Length: 190
X-Kong-Admin-Latency: 9
Server: kong/3.3.0.0-enterprise-edition
{"created_at":1685461520,"id":"bcde542a-799c-4c1b-ac03-e3ad87cfe436","ttl":null,"tags":null,"key":"ErjixFQiI2cRLifn4ZhRkXP7AHVyAlaE","consumer":{"id":"df540cb1-f3ce-4d67-b30f-2a3b3e2e5598"}}
4.3、添加用户限流
[root@min ~]# curl -X POST http://localhost:8001/plugins \
> --data "name=rate-limiting" \
> --data "consumer.username=jsmith" \
> --data "config.second=7"
{"created_at":1685461850,"consumer":{"id":"df540cb1-f3ce-4d67-b30f-2a3b3e2e5598"},"protocols":["grpc","grpcs","http","https"],"updated_at":1685461850,"ordering":null,"enabled":true,"instance_name":null,"id":"ccc8284e-a511-4a7a-a37b-9c9930d1fb6c","service":null,"name":"rate-limiting","tags":null,"config":{"redis_port":6379,"redis_username":null,"redis_password":null,"limit_by":"consumer","error_message":"API rate limit exceeded","policy":"local","redis_server_name":null,"path":null,"day":null,"redis_timeout":2000,"year":null,"header_name":null,"hide_client_headers":false,"redis_ssl_verify":false,"second":7,"redis_database":0,"fault_tolerant":true,"month":null,"error_code":429,"redis_ssl":false,"minute":null,"hour":null,"redis_host":null},"route":null}
目前这里有四个限流方面的配置,global、service、route、客户级别,优先依次升高,但是这里需要注意的时候,启用用户级别的限流时候一定要要启用一个auth插件,以便能够知道当前调用的是哪个用户。不然无法生效
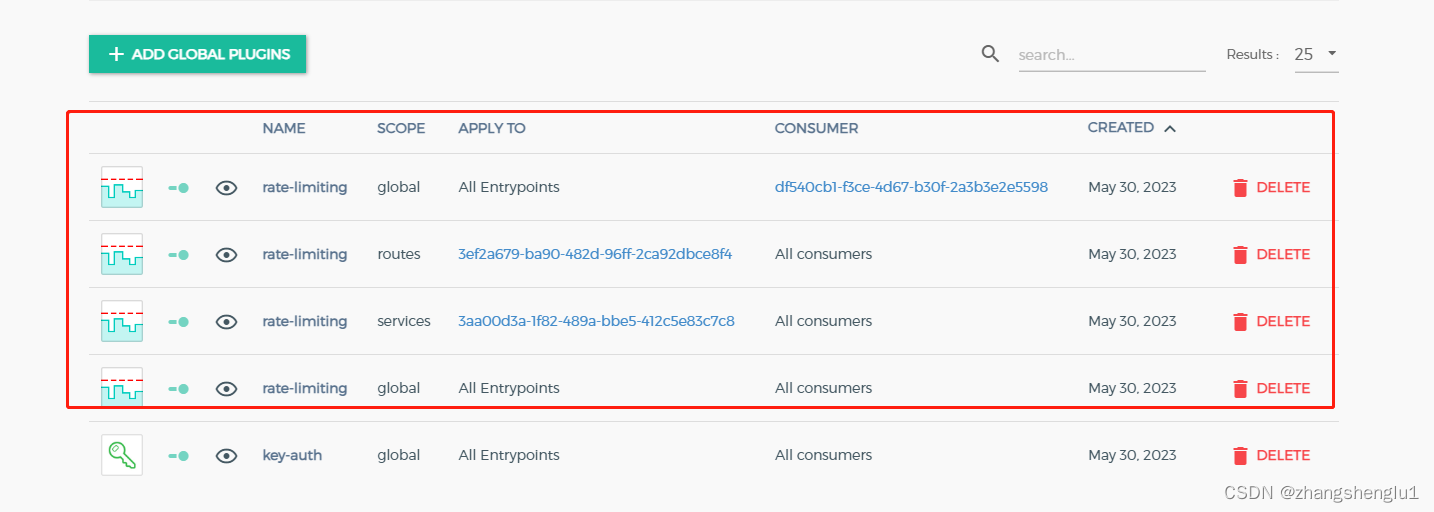
此时我们kong上面拥有四个流控配置,分配是全局5个/s,服务级别: 10个/s ,route级别 : 6个/s,客户级别:7个/s
在一秒内发起11个请求,响应的结果如下:
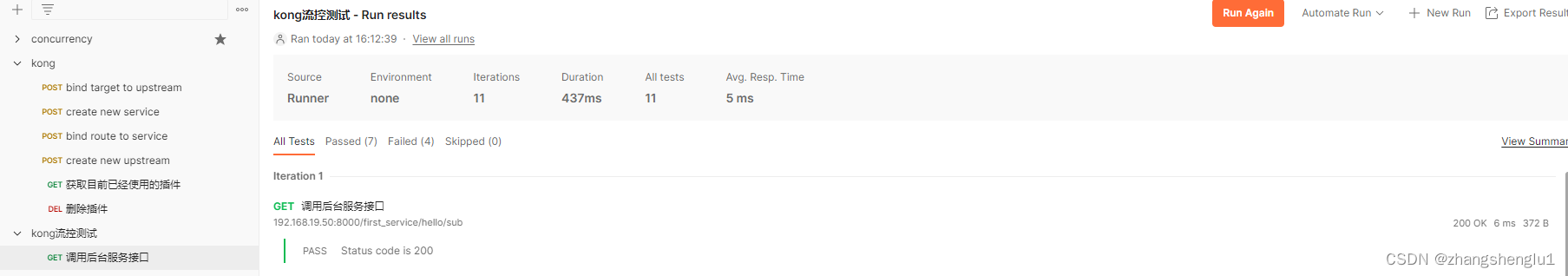
如果我们关闭key-auth插件,那么就会发现客户级别的限流不再其作用了。
再次使用11个请求进行测试,发现目前生效的限流配置是route级别的了!




















 1695
1695











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








