Endpoint Threat Detection and Response

Endpoint security refers to the protection of an organization's network when accessed via remote devices such as laptops or other wireless and mobile devices. Endpoint threat detection and response (ETDR) focuses on the endpoint as opposed to the network, threats as opposed to only malware, and officially declares incidents. It contains a collection of tools used for both detection and incident response. A mobile endpoint may use multiple methods and protocols to connect to cloud services and applications, while a fixed endpoint commonly uses one method and protocol to connect to cloud services and applications.
Figure 1 shows ETDRs being queued by a threat intelligence system.
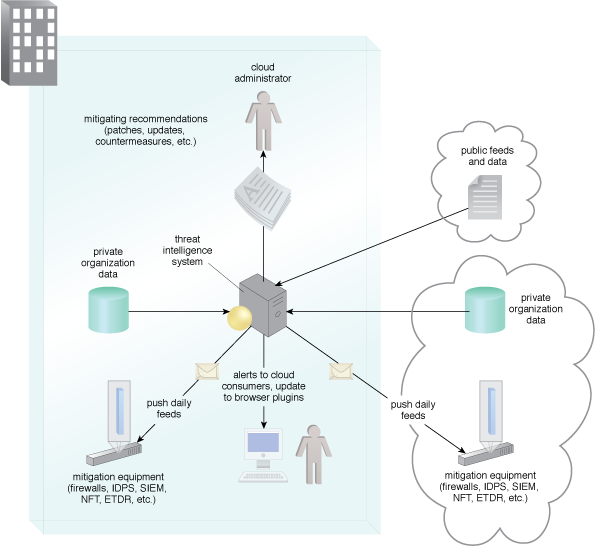 Figure 1 - ETDR in the context of a threat intelligence system.
Figure 1 - ETDR in the context of a threat intelligence system.
Advanced threats and zero-day attacks require organizations to detect and respond based on realtime monitoring and a continuous recorded history to reduce the attack surface with multiple forms of prevention. The ETDR strategy is to deploy sensors that cross network and endpoint boundaries. The architecture requires that the endpoint platforms' security, secure boot processes, and encryption key protections are in place.






















 908
908

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








