遍历json键名
:param http_request_body:
:param param_name:
:return:
'''
for name in http_request_body:
#print(name)
if param_name != '':
self.list_data.append((param_name + '.' + name,self.type_param(http_request_body[name]),http_request_body[name]))
else:
self.list_data.append((name,self.type_param(http_request_body[name]),http_request_body[name]))
if isinstance(http_request_body[name], dict):
if param_name != '':
self.process_json(http_request_body[name], param_name + '.' + name)
else:
self.process_json(http_request_body[name], name)
def callback_set_json(self,http_request,data):
http_request["param_name"] = data["param_name"]
http_request["param_value"] = data["param_value"]
http_request["param_type"] = data["param_type"]
return http_request
def callback_json_http_request(self,http_request_body, param_name_list, payload='', payload_num=0):
'''
Json格式http body返回
:param http_request_body:
:param param_name_list:json键名
:param payload:
:param num:
:return:
'''
param_name_list = param_name_list.split('.')
num_param = len(param_name_list)
num=0
task_name = 'http_request_body[param_name_list[%s]]' % num
for i in range(num_param):
if num ==num_param-1:
param_type = self.type_param(eval(task_name))
param_value=eval(task_name)
item=eval('task_name')+" = self.process_payload("+eval('task_name')+", payload_num, payload)"
exec(item)
num = num + 1
task_name =task_name+'[param_name_list[%s]]'%num
return {"param_name": '.'.join(param_name_list), "param_value": param_value, "param_type": param_type,
"data": http_request_body}
def callback_param_http_request(self, http_request_body, param, payload='', payload_num=0):
'''
a=str&b=str&c=1 返回
:param http_request_body:
:param param: 参数名
:param payload:
:param num:
:return:
'''
try:
list_data=[]
task_list=list(set(http_request_body.split('&')))
if '' in task_list:
task_list.remove('')
#print(task_list)
for tmp in task_list:
#print(tmp.split('=')[0])
#print(param)
tmp=copy.deepcopy(tmp)
if '=' in tmp and str(tmp.split('=')[0])==param:
param_name=tmp.split('=')[0]
param_value=tmp.split('=')[1]
param_type=self.type_param(tmp.split('=')[1])
list_data.append(tmp.split('=')[0]+'='+self.process_payload(tmp.split('=')[1],payload_num,payload))
else:
#print(tmp.split('='))
if len(tmp.split('='))==2:
list_data.append(tmp.split('=')[0] + '=' + tmp.split('=')[1])
else:
param_value='Null'
param_type='Null'
list_data.append(tmp.split('=')[0] + '=' + param_value)
#print(list_data)
return {"param_name":param_name, "param_value": param_value, "param_type": param_type,"param_data":'&'.join(list_data)}
except:return {}
def process_param(self, http_request_body, param_name=''):
'''
遍历参数名 a=str&b=str&c=1 这类参数处理
:param http_request:
:param param_name:
:return:
'''
try:
callback_param = []
for tmp in http_request_body.split('&'):
if len(tmp.split('='))==2:
callback_param.append((tmp.split('=')[0],self.type_param(tmp.split('=')[1]),tmp.split('=')[1]))
else:callback_param.append((tmp.split('=')[0],'Null','Null'))
return callback_param
except Exception as e:
print(e)
return []
def callback_param_list(self,http_request):
'''
:param http_request:
:return: (参数名 , 参数值类型)
[('method', 'String'), ('name', 'String'), ('age', 'Int'), ('data', 'Json'), ('data.name', 'String'), ('sada', 'Int')]
'''
param_list=[]
query = parse.urlparse(http_request['url']).query
if http_request['method'] == 'GET' and query!='':
param_list.extend(self.process_param(query))
elif http_request['method'] == 'POST' and http_request['body']!='':
if query!='':param_list.extend(self.process_param(query))
if self.type_param(http_request['body'])=='Json':
if type(http_request['body'])==type({}):
self.process_json(http_request['body'])
else:
self.process_json(json.loads(http_request['body']))
param_list.extend(self.list_data)
else:
param_list.extend(self.process_param(http_request['body']))
self.list_data=[]
return param_list
def callback_http_request(self,http_request,param,payload='',payload_num=0):
'''
返回设置payload后的http请求包
:param http_request:
:param param:
:param payload:
:param payload_num:
:return:
'''
http_request=copy.deepcopy(http_request)
if self.type_param(http_request['body'])=='Json':
http_request['body']=json.loads(http_request['body'])
url_process = parse.urlparse(http_request['url'])
http_get_data = self.callback_param_http_request(copy.deepcopy(url_process.query), param, payload, payload_num)
if http_request['method'] == 'GET' and url_process.query!='' and http_get_data!= {}:
http_request['url'] = url_process.scheme + '://' + url_process.netloc + url_process.path + '?' + http_get_data[
'param_data']
http_request=self.callback_set_json(http_request,http_get_data)
return http_request
elif http_request['method'] == 'POST' and http_request['body'] != 'Null':
if url_process.query != '' and http_get_data!= {}:
http_request['url']=url_process.scheme+'://'+url_process.netloc+url_process.path+'?'+http_get_data['param_data']
http_request=self.callback_set_json(http_request,http_get_data)
return http_request
if self.type_param(http_request['body'] )=='Json':
json_data=self.callback_json_http_request(http_request['body'],param,payload,payload_num)
http_request = self.callback_set_json(http_request, json_data)
http_request["body"] = json_data["data"]
return http_request
elif http_request['body']!='Null' :
post_data = self.callback_param_http_request(copy.deepcopy(http_request["body"]), param, payload,payload_num)
if post_data!={}:
http_request = self.callback_set_json(http_request, post_data)
http_request["body"] = post_data["param_data"]
return http_request
return http_request
if name == ‘main’:
test_json={“headers”: {“Origin”: “http://192.168.220.130”, “Cookie”: “PHPSESSID=1db5thrprbsm1nms5fer3fdj7c”, “Accept”: “/”, “User-Agent”: “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4505.0 Safari/537.36”, “Referer”: “http://192.168.220.130/web_vul_test/test_sql.html”, “Connection”: “close”, “Accept-Encoding”: “gzip, deflate”, “Content-type”: “application/json”, “Accept-Language”: “zh-CN,zh;q=0.9”, “Content-Length”: “58”}, “method”: “POST”, “body”: “{“name”:“lisi”,“age”:50,“data”:{“name”:“acccca”},“sada”:1}”, “url”: “http://192.168.220.130:80/web_vul_test/php_api/json_sql.php?method=sql_inj_json_insert_method&dsadas=aa1111111”}
#test_json = {“headers”: {“Cookie”: “PHPSESSID=1db5thrprbsm1nms5fer3fdj7c”, “Accept”: “/”, “User-Agent”: “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4505.0 Safari/537.36”, “Referer”: “http://192.168.220.130/web_vul_test/test_sql.html”, “Connection”: “close”, “Accept-Encoding”: “gzip, deflate”, “Accept-Language”: “zh-CN,zh;q=0.9”}, “method”: “GET”, “body”: “null”, “url”: “http://192.168.220.130:80/web_vul_test/php_api/json_sql.php?as&fds=111”}
#test_json={“headers”: {“Origin”: “http://192.168.220.130”, “Cookie”: “PHPSESSID=1db5thrprbsm1nms5fer3fdj7c”, “Accept”: “/”, “User-Agent”: “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4505.0 Safari/537.36”, “Referer”: “http://192.168.220.130/web_vul_test/test_sql.html”, “Connection”: “close”, “Accept-Encoding”: “gzip, deflate”, “Content-type”: “application/x-www-form-urlencoded”, “Accept-Language”: “zh-CN,zh;q=0.9”, “Content-Length”: “36”}, “method”: “POST”, “body”: “fname=Bill&lname=Gates&id=2&dasdsa=1”, “url”: “http://192.168.220.130:80/web_vul_test/php_api/json_sql.php?method=sql_inj_post_method&sa1=sada&aaa1=a1”}
task=process_http_request()
for item in task.callback_param_list(test_json):
if item[1] != ‘Json’:
print(item)
print(task.callback_http_request(test_json, item[0], ‘payload’, 0))
加V:mashibin98,领取价值11980安全资料包
以上为要用到的代码
#### 案例解释1:
用burp抓包得到的GET请求:
GET /web_vul_test/php_api/json_sql.php?method=sql_inj_get_method&id=1dasdsadsa&ida=13243234&id=1 HTTP/1.1
Host: 192.168.220.130
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4505.0 Safari/537.36
Accept: /
Referer: http://192.168.220.130/web_vul_test/test_sql.html
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
加V:mashibin97,领取价值11980安全资料包
通过我的burp插件(这个之后写)处理后为:
{
“headers”:
{
“Accept”: “/”,
“User-Agent”: “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML,like Gecko) Chrome/92.0.4505.0 Safari/537.36”,
“Referer”: “http://192.168.220.130/web_vul_test/test_sql.html”,
“Connection”: “close”,
“Accept-Encoding”: “gzip,deflate”,
“Accept-Language”: “zh-CN,zh;q=0.9”
},
“method”: “GET”,
“body”: “null”,
“url”: “http://192.168.220.130:80/web_vul_test/php_api/json_sql.php?method=sql_inj_get_method&id=1dasdsadsa&ida=13243234&id=1”
}
加V:mashibin98,领取价值11980安全资料包
这个时候从漏洞检测的角度讲,我完全可以通过修改`User-Agent/Referer/Cookie,`之类的`header`参数值,进行些黑盒漏洞测试,当然我们要讲的不在这里,是在`URL:http://192.168.220.130:80/web_vul_test/php_api/json_sql.php?method=sql_inj_get_method&id=1dasdsadsa&ida=13243234&id=1` 的参数段,
`method=sql_inj_get_method&id=1dasdsadsa&ida=13243234&id=1`,web漏洞不考虑0/N-day的情况下,大部分漏洞都在这个地方, 我们以上的代码`process_http_request.py`也就是为了处理这个地方。
[](https://docs.qq.com/doc/DSnZnQWVHY3ZreHFL)
如图所示,结果为
method=sql_inj_get_method&id=1dasdsadsa&ida=13243234&id=1
(参数名,参数值类型,参数值)
(‘method’, ‘String’, ‘sql_inj_get_method’)
(‘id’, ‘String’, ‘1dasdsadsa’)
(‘ida’, ‘Int’, ‘13243234’)
(‘id’, ‘Int’, ‘1’)
加V:mashibin98,领取价值11980安全资料包
那么我们取消掉图上注释执行结果:
[](https://docs.qq.com/doc/DSnZnQWVHY3ZreHFL)
(‘method’, ‘String’, ‘sql_inj_get_method’)
{‘headers’: {‘Accept’: ‘/’, ‘User-Agent’: ‘Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4505.0 Safari/537.36’, ‘Referer’: ‘http://192.168.220.130/web_vul_test/test_sql.html’, ‘Connection’: ‘close’, ‘Accept-Encoding’: ‘gzip, deflate’, ‘Accept-Language’: ‘zh-CN,zh;q=0.9’}, ‘method’: ‘GET’, ‘body’: ‘null’, ‘url’: ‘http://192.168.220.130:80/web_vul_test/php_api/json_sql.php?id=1dasdsadsa&ida=13243234&id=1&method=sql_inj_get_methodpayload’, ‘param_name’: ‘method’, ‘param_value’: ‘sql_inj_get_method’, ‘param_type’: ‘String’}
(‘id’, ‘String’, ‘1dasdsadsa’)
{‘headers’: {‘Accept’: ‘/’, ‘User-Agent’: ‘Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4505.0 Safari/537.36’, ‘Referer’: ‘http://192.168.220.130/web_vul_test/test_sql.html’, ‘Connection’: ‘close’, ‘Accept-Encoding’: ‘gzip, deflate’, ‘Accept-Language’: ‘zh-CN,zh;q=0.9’}, ‘method’: ‘GET’, ‘body’: ‘null’, ‘url’: ‘http://192.168.220.130:80/web_vul_test/php_api/json_sql.php?id=1dasdsadsapayload&ida=13243234&id=1payload&method=sql_inj_get_method’, ‘param_name’: ‘id’, ‘param_value’: ‘1’, ‘param_type’: ‘Int’}
(‘ida’, ‘Int’, ‘13243234’)
{‘headers’: {‘Accept’: ‘/’, ‘User-Agent’: ‘Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4505.0 Safari/537.36’, ‘Referer’: ‘http://192.168.220.130/web_vul_test/test_sql.html’, ‘Connection’: ‘close’, ‘Accept-Encoding’: ‘gzip, deflate’, ‘Accept-Language’: ‘zh-CN,zh;q=0.9’}, ‘method’: ‘GET’, ‘body’: ‘null’, ‘url’: ‘http://192.168.220.130:80/web_vul_test/php_api/json_sql.php?id=1dasdsadsa&ida=13243234payload&id=1&method=sql_inj_get_method’, ‘param_name’: ‘ida’, ‘param_value’: ‘13243234’, ‘param_type’: ‘Int’}
(‘id’, ‘Int’, ‘1’)
{‘headers’: {‘Accept’: ‘/’, ‘User-Agent’: ‘Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4505.0 Safari/537.36’, ‘Referer’: ‘http://192.168.220.130/web_vul_test/test_sql.html’, ‘Connection’: ‘close’, ‘Accept-Encoding’: ‘gzip, deflate’, ‘Accept-Language’: ‘zh-CN,zh;q=0.9’}, ‘method’: ‘GET’, ‘body’: ‘null’, ‘url’: ‘http://192.168.220.130:80/web_vul_test/php_api/json_sql.php?id=1dasdsadsapayload&ida=13243234&id=1payload&method=sql_inj_get_method’, ‘param_name’: ‘id’, ‘param_value’: ‘1’, ‘param_type’: ‘Int’}
加V:mashibin98,领取价值11980安全资料包
请自行发现规律和理解下…
**该代码主要用这两个方法:**
callback_param_list 方法为,遍历http的请求参数 并遍历返回 (参数名,参数值类型,参数值)
callback_http_request 方法为:
callback_http_request(burp转好的http request,要设置的参数名,payload,payload_num)
payload_num 0为值后追加 1为替换 2为值前追加
然后返回设置好`payload`的`http request`。
#### 案例解释2:
**POST方式 JSON数据格式传参的http请求**
{
“headers”:
{
“Origin”: “http://192.168.220.130”,
“Accept”: “/”,
“User-Agent”: “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML,
like Gecko) Chrome/92.0.4505.0 Safari/537.36”,
“Referer”: “http://192.168.220.130/web_vul_test/test_sql.html”,
“Connection”: “close”,
“Accept-Encoding”: “gzip,deflate”,
“Content-type”: “application/json”,
“Accept-Language”: “zh-CN,zh;q=0.9”,
“Content-Length”: “58”
},
“method”: “POST”,
“body”: "
{
“name”:“lisi”,
“age”:50,
“data”:
{
“name”:“acccca”,
“data”:
{
“url”:“http://www.qq.com”
}
},
“sada”:1
}
",
“url”: “http://192.168.220.130:80/web_vul_test/php_api/json_sql.php?method=sql_inj_json_insert_method”
}
加V:mashibin98,领取价值11980安全资料包
[](https://docs.qq.com/doc/DSnZnQWVHY3ZreHFL)
其实了和案例1 没有什么区别,就是GET和POST参数处理,支持处理 `GET POST`, `a=1&b=c&asda=dsadsa` 和JSON方式传参,并且遍历json N层json嵌套都可以。
### 漏洞检测案例
#### 案例1 ssrf检测
关于案例而的实战应用,假设url参数名是一个ssrf漏洞, 实际黑盒漏洞挖掘中,我们需要手工换掉`http://www.qq.com`为`http://www.ssrf.com`
**在本代码中**
[](https://docs.qq.com/doc/DSnZnQWVHY3ZreHFL)
执行结果:
{‘headers’: {‘Origin’: ‘http://192.168.220.130’, ‘Accept’: ‘/’, ‘User-Agent’: ‘Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4505.0 Safari/537.36’, ‘Referer’: ‘http://192.168.220.130/web_vul_test/test_sql.html’, ‘Connection’: ‘close’, ‘Accept-Encoding’: ‘gzip, deflate’, ‘Content-type’: ‘application/json’, ‘Accept-Language’: ‘zh-CN,zh;q=0.9’, ‘Content-Length’: ‘58’}, ‘method’: ‘POST’, ‘body’: {‘name’: ‘lisi’, ‘age’: 50, ‘data’: {‘name’: ‘acccca’, ‘data’: {‘url’: ‘http://www.ssrf.com’}}, ‘sada’: 1}, ‘url’: ‘http://192.168.220.130:80/web_vul_test/php_api/json_sql.php?method=sql_inj_json_insert_method’, ‘param_name’: ‘data.data.url’, ‘param_value’: ‘http://www.qq.com’, ‘param_type’: ‘Url’}
然后我们二次重放这个`http request`,就是在进行`SSRF`漏洞检测了。
### 案例2 反射XSS检测
还有兄弟不知道网络安全面试可以提前刷题吗?费时一周整理的160+网络安全面试题,金九银十,做网络安全面试里的显眼包!
王岚嵚工程师面试题(附答案),只能帮兄弟们到这儿了!如果你能答对70%,找一个安全工作,问题不大。
对于有1-3年工作经验,想要跳槽的朋友来说,也是很好的温习资料!
【完整版领取方式在文末!!】
***93道网络安全面试题***

内容实在太多,不一一截图了
### 黑客学习资源推荐
最后给大家分享一份全套的网络安全学习资料,给那些想学习 网络安全的小伙伴们一点帮助!
对于从来没有接触过网络安全的同学,我们帮你准备了详细的学习成长路线图。可以说是最科学最系统的学习路线,大家跟着这个大的方向学习准没问题。
😝朋友们如果有需要的话,可以联系领取~
#### 1️⃣零基础入门
##### ① 学习路线
对于从来没有接触过网络安全的同学,我们帮你准备了详细的**学习成长路线图**。可以说是**最科学最系统的学习路线**,大家跟着这个大的方向学习准没问题。
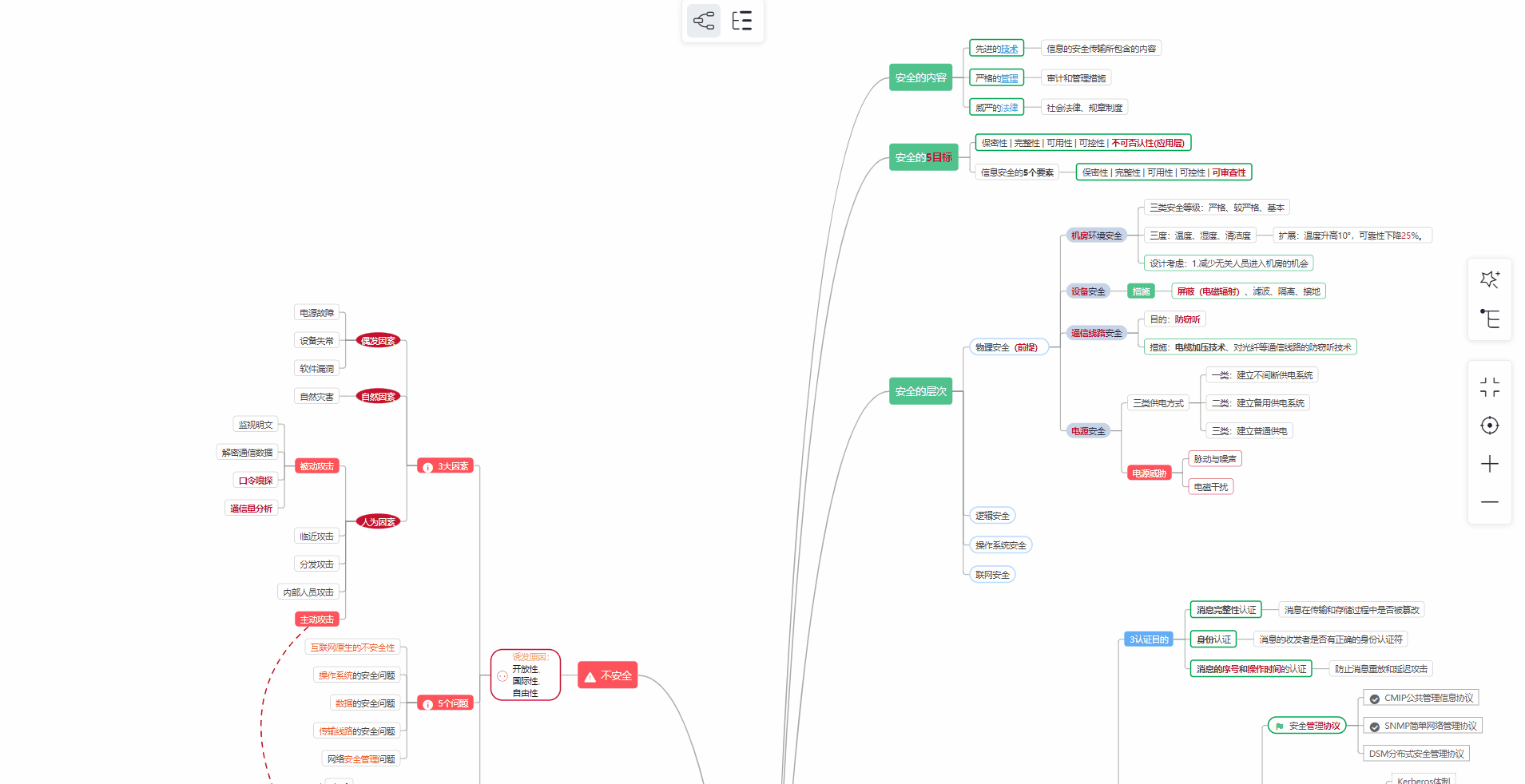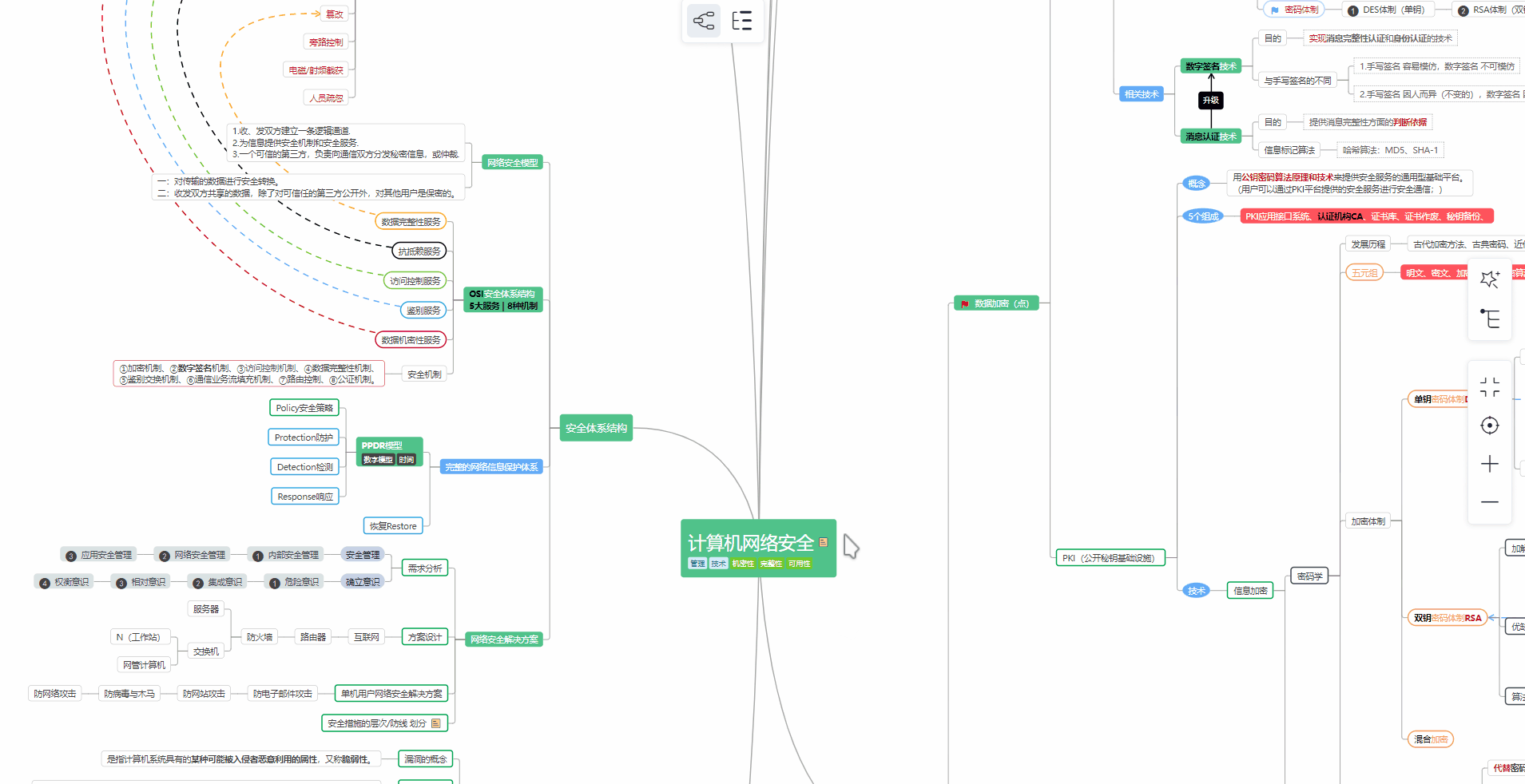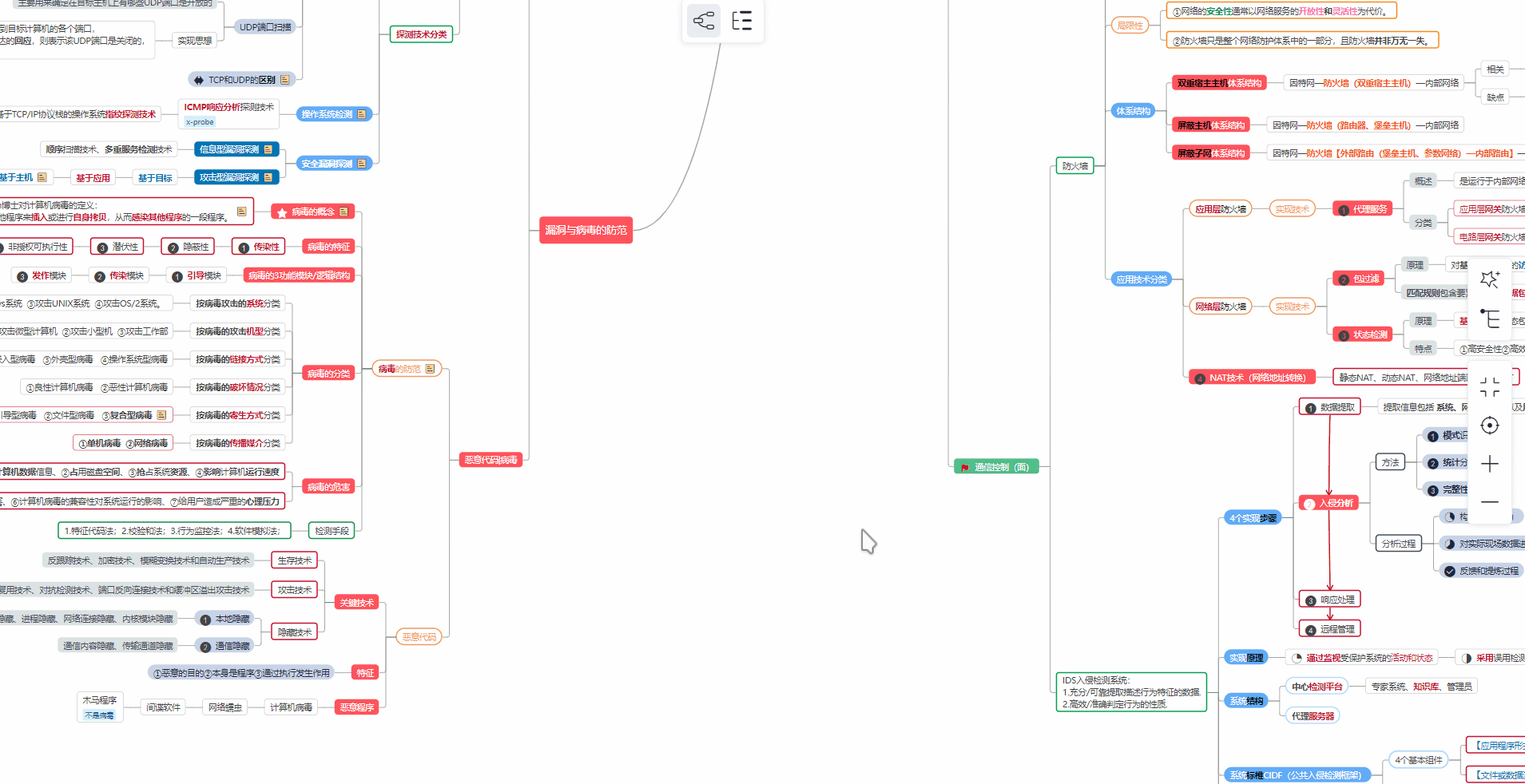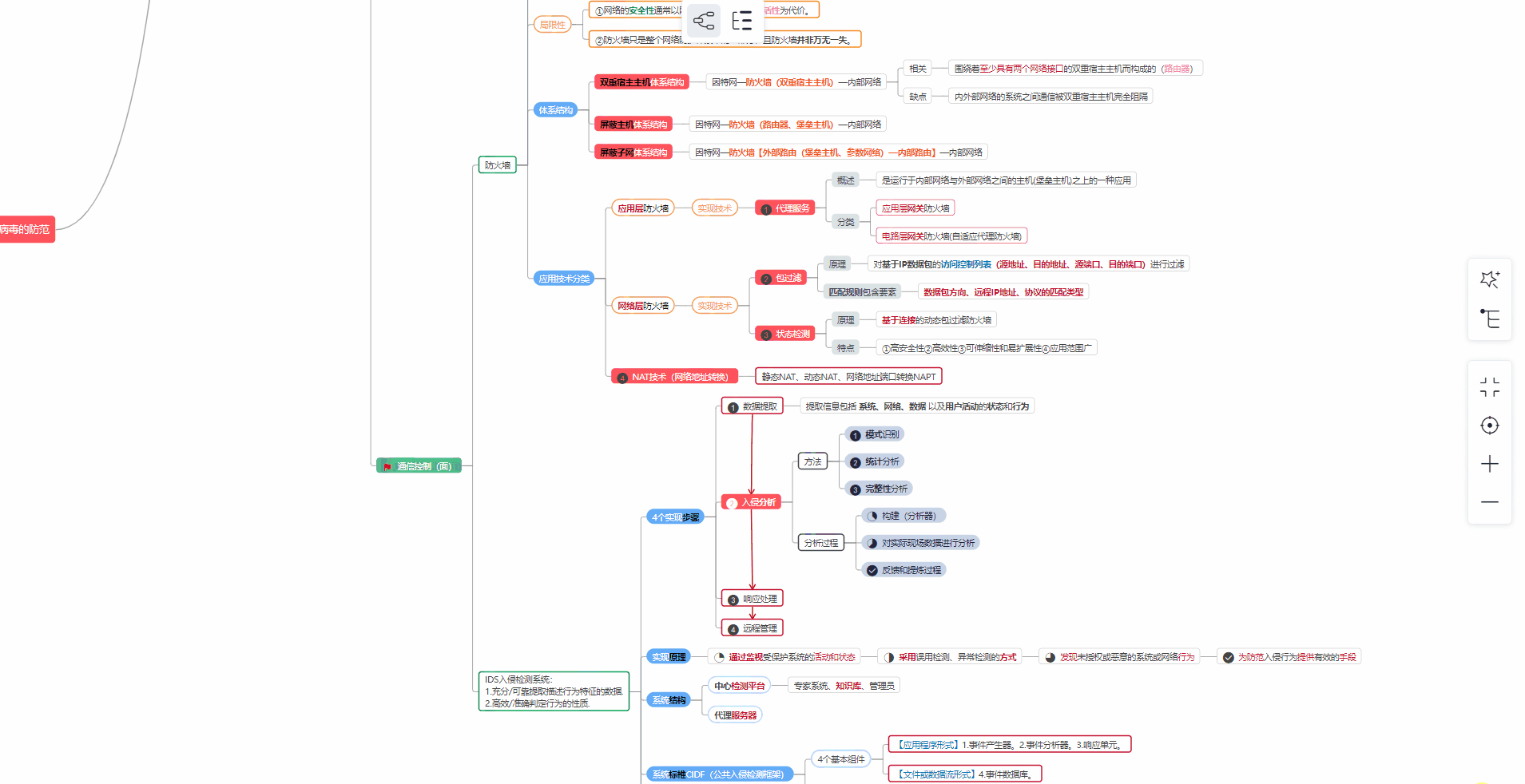
##### ② 路线对应学习视频
同时每个成长路线对应的板块都有配套的视频提供:
#### 2️⃣视频配套工具&国内外网安书籍、文档
##### ① 工具

##### ② 视频
##### ③ 书籍
资源较为敏感,未展示全面,需要的最下面获取
##### ② 简历模板
**因篇幅有限,资料较为敏感仅展示部分资料,添加上方即可获取👆**
**网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。**
**[需要这份系统化资料的朋友,可以点击这里获取](https://bbs.csdn.net/topics/618540462)**
**一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!**




















 4万+
4万+











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








