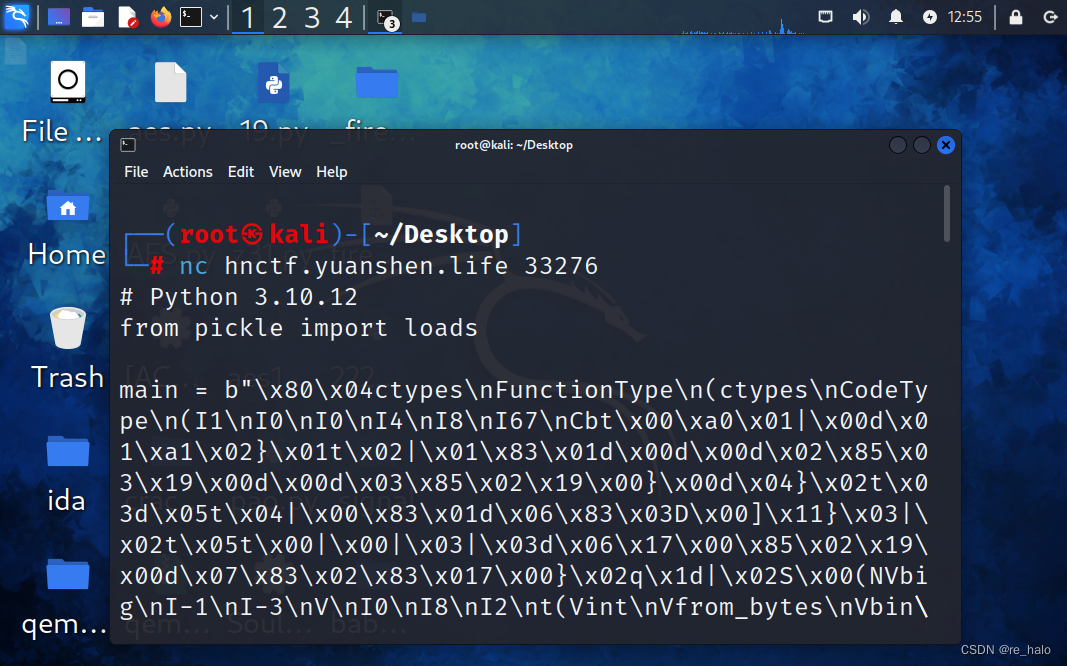
baby_python

hnctf.yuanshen.life:33276
网页打不开,只能 nc 连接远程服务器。
运行没有回显
利用pickletools库进行反编译为字节码(不知道为什么)
# Python 3.10.12
from pickle import loads
import pickletools
main = b"\x80\x04ctypes\nFunctionType\n(ctypes\nCodeType\n(I1\nI0\nI0\nI4\nI8\nI67\nCbt\x00\xa0\x01|\x00d\x01\xa1\x02}\x01t\x02|\x01\x83\x01d\x00d\x00d\x02\x85\x03\x19\x00d\x00d\x03\x85\x02\x19\x00}\x00d\x04}\x02t\x03d\x05t\x04|\x00\x83\x01d\x06\x83\x03D\x00]\x11}\x03|\x02t\x05t\x00|\x00|\x03|\x03d\x06\x17\x00\x85\x02\x19\x00d\x07\x83\x02\x83\x017\x00}\x02q\x1d|\x02S\x00(NVbig\nI-1\nI-3\nV\nI0\nI8\nI2\nt(Vint\nVfrom_bytes\nVbin\nVrange\nVlen\nVchr\nt(\x8c\x04\xf0\x9f\x94\xa5\x8c\x04\xf0\x9f\xa4\xab\x8c\x04\xf0\x9f\xa7\x8f\x8c\x04\xf0\x9f\x8e\xb5tVH&NCTF\n\x8c\x04\xf0\x9f\x93\xaeI0\nC\x0c\x00\x01\x0c\x01\x1a\x01\x04\x01\x14\x01 \x01))t\x81cbuiltins\nglobals\n)R\x8c\x04\xf0\x9f\x93\xaet\x81\x940g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x05\x01.\xce\x966\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x0b\x01\xa6&\xf6\xc6v\xa6tN.\xce\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x06\x01.v\x96N\x0e\x85R\x93VDo you know what's the flag??? \n\x85R0g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x06\x01.\xae\x0ev\x96\x85R\x93V> \n\x85R\x85R\x85R\x940g0\nC\x07\x01\xb6\xf6&v\x86N\x85Rg0\nC\x05\x01&\xa6\xa6\xce\x85R\x93Vwelcome to H&NCTF\n\x85R0g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x05\x01.\xce\x966\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x0b\x01\xa6&\xf6\xc6v\xa6tN.\xce\x85R\x93VH&NCTF\n\x85R\x85R\x940g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x05\x01.\xce\x966\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x04\x01\x0e\x86\xb6\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x0c\x01\xfa\xfaN\xf6\x1e\xfa\xfat.v\x96\x85R\x93g0\nC\n\x01\xce6\xf6\xf6.N\xa6.\x96\x85Rg0\nC\x06\x01\xa66\xc6\x9e\xc6\x85R\x93g2\n\x85Rg1\n\x87R\x85R\x940]\x94I2024\nag0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x05\x01.\xce\x966\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x04\x01\x0e\x86\xb6\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x0c\x01\xfa\xfa&&\x86\xfa\xfat.v\x96\x85R\x93g0\nC\n\x01\xce6\xf6\xf6.N\xa6.\x96\x85Rg0\nC\x06\x01\xa66\xc6\x9e\xc6\x85R\x93g4\n\x85Rg3\n\x87R\x85R\x940g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x04\x01\x9ev\x86\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x04\x01\x0e\x86\xb6\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x0c\x01\xfa\xfaN\xf6\x1e\xfa\xfat.v\x96\x85R\x93(I2024\nI2024\nI2024\nI2024\nI2024\nI2024\nI2075\nI2099\nI2071\nI2082\nI2078\nI2059\nI2047\nI2119\nI2057\nI2078\nI2035\nI2064\nI2069\nI2091\nI2066\nI2052\nI2077\nI2049\nI2067\nI2098\nI2057\nI2072\nI2073\nI2076\nI2047\nI2091\nI2078\nI2058\nI2081\nI2071\nI2062\nI2095\nI2082\nI2066\nI2083\nI2064\nI2077\nlg5\n\x87R\x85R\x940g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x0b\x01\xfa\xfaN\xf6\xfa\xfat.v\x96\x85R\x93g6\ng0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x0b\x01\xfa\xfa\xa6\xe6\xfa\xfat.v\x96\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x04\x01v\xa66\x85R\x93g5\n\x85RI50\n\x86R\x86R\x940g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x11\x01\xfa\xfa\xb6\xa6.\x96.\xa6\xe6\xfa\xfat.\xce\x966\x85R\x93(VOkay,maybe you need a closer examination!\nV \nlg7\n\x86R.g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x05\x01.\xce\x966\x85R\x93g0\nC\x07\x01\xb6\xf6&v\x86N\x85Rg0\nC\n\x01\xce\xa6.\x9eF&v\x86N\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x04\x01v\xa66\x85R\x93g1\n\x85R\x85R\x85R\x940g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x05\x01.\xce\x966\x85R\x93g0\nC\x07\x01\xb6\xf6&v\x86N\x85Rg0\nC\n\x01\xce\xa6.\x9eF&v\x86N\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x04\x01v\xa66\x85R\x93g2\n\x85R\x85R\x85R\x940g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x05\x01.\xce\x966\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x04\x01\x0e\x86\xb6\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x0c\x01\xfa\xfaN\xf6\x1e\xfa\xfat.v\x96\x85R\x93g0\nC\n\x01\xce6\xf6\xf6.N\xa6.\x96\x85Rg0\nC\x06\x01\xa66\xc6\x9e\xc6\x85R\x93g9\n\x85Rg1\n\x87R\x85R\x940g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x05\x01.\xce\x966\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x04\x01\x0e\x86\xb6\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x0c\x01\xfa\xfaN\xf6\x1e\xfa\xfat.v\x96\x85R\x93g0\nC\n\x01\xce6\xf6\xf6.N\xa6.\x96\x85Rg0\nC\x06\x01\xa66\xc6\x9e\xc6\x85R\x93g2\n\x85Rg8\n\x87R\x85R\x940g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x05\x01.\xce\x966\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x04\x01\x0e\x86\xb6\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x0c\x01\xfa\xfaN\xf6\x1e\xfa\xfat.v\x96\x85R\x93g10\ng11\n\x87R\x85R\x940g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x04\x01\x9ev\x86\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x04\x01\x0e\x86\xb6\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x0c\x01\xfa\xfaN\xf6\x1e\xfa\xfat.v\x96\x85R\x93(I72\nI24\nI7\nI107\nI142\nI150\nI112\nI158\nI174\nI172\nI155\nI126\nI69\nI235\nI64\nI229\nI102\nI158\nI118\nI61\nI36\nI12\nI234\nI194\nI71\nI51\nI47\nI82\nI41\nI122\nI121\nI221\nI7\nI119\nI96\nI104\nI246\nI3\nI103\nI153\nI232\nI210\nI7\nI188\nlg12\n\x87R\x85R\x940g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x0c\x01\xfa\xfaN\xf6\x1e\xfa\xfat.v\x96\x85R\x93g13\ng0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x0b\x01\xfa\xfa\xa6\xe6\xfa\xfat.v\x96\x85R\x93g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x04\x01v\xa66\x85R\x93g12\n\x85RI50\n\x86R\x86R\x940g0\nC\t\x01\xcev\x96.6\x96\xaeF\x85Rg0\nC\x11\x01\xfa\xfa\xb6\xa6.\x96.\xa6\xe6\xfa\xfat.\xce\x966\x85R\x93(VOkay,you get the flag!\nVOh no,maybe you should try again~\nlg14\n\x86R."
# print(loads(main))
print(pickletools.dis(main))
0: \x80 PROTO 4
2: c GLOBAL 'types FunctionType'
22: ( MARK
23: c GLOBAL 'types CodeType'
39: ( MARK
40: I INT 1
43: I INT 0
46: I INT 0
49: I INT 4
52: I INT 8
55: I INT 67
59: C SHORT_BINBYTES b't\x00\xa0\x01|\x00d\x01\xa1\x02}\x01t\x02|\x01\x83\x01d\x00d\x00d\x02\x85\x03\x19\x00d\x00d\x03\x85\x02\x19\x00}\x00d\x04}\x02t\x03d\x05t\x04|\x00\x83\x01d\x06\x83\x03D\x00]\x11}\x03|\x02t\x05t\x00|\x00|\x03|\x03d\x06\x17\x00\x85\x02\x19\x00d\x07\x83\x02\x83\x017\x00}\x02q\x1d|\x02S\x00'
159: ( MARK
160: N NONE
161: V UNICODE 'big'
166: I INT -1
170: I INT -3
174: V UNICODE ''
176: I INT 0
179: I INT 8
182: I INT 2
185: t TUPLE (MARK at 159)
186: ( MARK
187: V UNICODE 'int'
192: V UNICODE 'from_bytes'
204: V UNICODE 'bin'
209: V UNICODE 'range'
216: V UNICODE 'len'
221: V UNICODE 'chr'
226: t TUPLE (MARK at 186)
227: ( MARK
228: \x8c SHORT_BINUNICODE '🔥'
234: \x8c SHORT_BINUNICODE '🤫'
240: \x8c SHORT_BINUNICODE '🧏'
246: \x8c SHORT_BINUNICODE '🎵'
252: t TUPLE (MARK at 227)
253: V UNICODE 'H&NCTF'
261: \x8c SHORT_BINUNICODE '📮'
267: I INT 0
270: C SHORT_BINBYTES b'\x00\x01\x0c\x01\x1a\x01\x04\x01\x14\x01 \x01'
284: ) EMPTY_TUPLE
285: ) EMPTY_TUPLE
286: t TUPLE (MARK at 39)
287: \x81 NEWOBJ
288: c GLOBAL 'builtins globals'
306: ) EMPTY_TUPLE
307: R REDUCE
308: \x8c SHORT_BINUNICODE '📮'
314: t TUPLE (MARK at 22)
315: \x81 NEWOBJ
316: \x94 MEMOIZE (as 0)
317: 0 POP
318: g GET 0
321: C SHORT_BINBYTES b'\x01\xcev\x96.6\x96\xaeF'
332: \x85 TUPLE1
333: R REDUCE
334: g GET 0
337: C SHORT_BINBYTES b'\x01.\xce\x966'
344: \x85 TUPLE1
345: R REDUCE
346: \x93 STACK_GLOBAL
347: g GET 0
350: C SHORT_BINBYTES b'\x01\xcev\x96.6\x96\xaeF'
361: \x85 TUPLE1
362: R REDUCE
363: g GET 0
366: C SHORT_BINBYTES b'\x01\xa6&\xf6\xc6v\xa6tN.\xce'
379: \x85 TUPLE1
380: R REDUCE
381: \x93 STACK_GLOBAL
382: g GET 0
385: C SHORT_BINBYTES b'\x01\xcev\x96.6\x96\xaeF'
396: \x85 TUPLE1
397: R REDUCE
398: g GET 0
401: C SHORT_BINBYTES b'\x01.v\x96N\x0e'
409: \x85 TUPLE1
410: R REDUCE
411: \x93 STACK_GLOBAL
412: V UNICODE "Do you know what's the flag??? "
445: \x85 TUPLE1
446: R REDUCE
447: 0 POP
448: g GET 0
451: C SHORT_BINBYTES b'\x01\xcev\x96.6\x96\xaeF'
462: \x85 TUPLE1
463: R REDUCE
464: g GET 0
467: C SHORT_BINBYTES b'\x01.\xae\x0ev\x96'
475: \x85 TUPLE1
476: R REDUCE
477: \x93 STACK_GLOBAL
478: V UNICODE '> '
482: \x85 TUPLE1
483: R REDUCE
484: \x85 TUPLE1
485: R REDUCE
486: \x85 TUPLE1
487: R REDUCE
488: \x94 MEMOIZE (as 1)
489: 0 POP
490: g GET 0
493: C SHORT_BINBYTES b'\x01\xb6\xf6&v\x86N'
502: \x85 TUPLE1
503: R REDUCE
504: g GET 0
507: C SHORT_BINBYTES b'\x01&\xa6\xa6\xce'
514: \x85 TUPLE1
515: R REDUCE
516: \x93 STACK_GLOBAL
517: V UNICODE 'welcome to H&NCTF'
536: \x85 TUPLE1
537: R REDUCE
538: 0 POP
539: g GET 0
542: C SHORT_BINBYTES b'\x01\xcev\x96.6\x96\xaeF'
553: \x85 TUPLE1
554: R REDUCE
555: g GET 0
558: C SHORT_BINBYTES b'\x01.\xce\x966'
565: \x85 TUPLE1
566: R REDUCE
567: \x93 STACK_GLOBAL
568: g GET 0
571: C SHORT_BINBYTES b'\x01\xcev\x96.6\x96\xaeF'
582: \x85 TUPLE1
583: R REDUCE
584: g GET 0
587: C SHORT_BINBYTES b'\x01\xa6&\xf6\xc6v\xa6tN.\xce'
600: \x85 TUPLE1
601: R REDUCE
602: \x93 STACK_GLOBAL
603: V UNICODE 'H&NCTF'
611: \x85 TUPLE1
612: R REDUCE
613: \x85 TUPLE1
614: R REDUCE
615: \x94 MEMOIZE (as 2)
616: 0 POP
617: g GET 0
620: C SHORT_BINBYTES b'\x01\xcev\x96.6\x96\xaeF'
631: \x85 TUPLE1
632: R REDUCE
633: g GET 0
636: C SHORT_BINBYTES b'\x01.\xce\x966'
643: \x85 TUPLE1
644: R REDUCE
645: \x93 STACK_GLOBAL
646: g GET 0
649: C SHORT_BINBYTES b'\x01\xcev\x96.6\x96\xaeF'
660: \x85 TUPLE1
661: R REDUCE
662: g GET 0
665: C SHORT_BINBYTES b'\x01\x0e\x86\xb6'
671: \x85 TUPLE1
672: R REDUCE
673: \x93 STACK_GLOBAL
674: g GET 0
677: C SHORT_BINBYTES b'\x01\xcev\x96.6\x96\xaeF'
688: \x85 TUPLE1
689: R REDUCE
690: g GET 0
693: C SHORT_BINBYTES b'\x01\xfa\xfaN\xf6\x1e\xfa\xfat.v\x96'
707: \x85 TUPLE1
708: R REDUCE
709: \x93 STACK_GLOBAL
710: g GET 0
713: C SHORT_BINBYTES b'\x01\xce6\xf6\xf6.N\xa6.\x96'
725: \x85 TUPLE1
726: R REDUCE
727: g GET 0
730: C SHORT_BINBYTES b'\x01\xa66\xc6\x9e\xc6'
738: \x85 TUPLE1
739: R REDUCE
740: \x93 STACK_GLOBAL
741: g GET 2
744: \x85 TUPLE1
745: R REDUCE
746: g GET 1
749: \x87 TUPLE3
750: R REDUCE
751: \x85 TUPLE1
752: R REDUCE
753: \x94 MEMOIZE (as 3)
754: 0 POP
755: ] EMPTY_LIST
756: \x94 MEMOIZE (as 4)
757: I INT 2024
763: a APPEND
764: g GET 0
767: C SHORT_BINBYTES b'\x01\xcev\x96.6\x96\xaeF'
778: \x85 TUPLE1
779: R REDUCE
780: g GET 0
783: C SHORT_BINBYTES b'\x01.\xce\x966'
790: \x85 TUPLE1
791: R REDUCE
792: \x93 STACK_GLOBAL
793: g GET 0
796: C SHORT_BINBYTES b'\x01\xcev\x96.6\x96\xaeF'
807: \x85 TUPLE1
808: R REDUCE
809: g GET 0
812: C SHORT_BINBYTES b'\x01\x0e\x86\xb6'
818: \x85 TUPLE1
819: R REDUCE
820: \x93 STACK_GLOBAL
821: g GET 0
824: C SHORT_BINBYTES b'\x01\xcev\x96.6\x96\xaeF'
835: \x85 TUPLE1
836: R REDUCE
837: g GET 0
840: C SHORT_BINBYTES b'\x01\xfa\xfa&&\x86\xfa\xfat.v\x96'
854: \x85 TUPLE1
855: R REDUCE
856: \x93 STACK_GLOBAL
857: g GET 0
860: C SHORT_BINBYTES b'\x01\xce6\xf6\xf6.N\xa6.\x96'
872: \x85 TUPLE1
873: R REDUCE
874: g GET 0
877: C SHORT_BINBYTES b'\x01\xa66\xc6\x9e\xc6'
885: \x85 TUPLE1
886: R REDUCE
887: \x93 STACK_GLOBAL
888: g GET 4
891: \x85 TUPLE1
892: R REDUCE
893: g GET 3
896: \x87 TUPLE3
897: R REDUCE
898: \x85 TUPLE1
899: R REDUCE
900: \x94 MEMOIZE (as 5)
901: 0 POP
902: g GET 0
905: C SHORT_BINBYTES b'\x01\xcev\x96.6\x96\xaeF'
916: \x85 TUPLE1
917: R REDUCE
918: g GET 0
921: C SHORT_BINBYTES b'\x01\x9ev\x86'
927: \x85 TUPLE1
928: R REDUCE
929: \x93 STACK_GLOBAL
930: g GET 0
933: C SHORT_BINBYTES b'\x01\xcev\x96.6\x96\xaeF'
944: \x85 TUPLE1
945: R REDUCE
946: g GET 0
949: C SHORT_BINBYTES b'\x01\x0e\x86\xb6'
955: \x85 TUPLE1
956: R REDUCE
957: \x93 STACK_GLOBAL
958: g GET 0
961: C SHORT_BINBYTES b'\x01\xcev\x96.6\x96\xaeF'
972: \x85 TUPLE1
973: R REDUCE
974: g GET 0
977: C SHORT_BINBYTES b'\x01\xfa\xfaN\xf6\x1e\xfa\xfat.v\x96'
991: \x85 TUPLE1
992: R REDUCE
993: \x93 STACK_GLOBAL
994: ( MARK
995: I INT 2024
1001: I INT 2024
1007: I INT 2024
1013: I INT 2024
1019: I INT 2024
1025: I INT 2024
1031: I INT 2075
1037: I INT 2099
1043: I INT 2071
1049: I INT 2082
1055: I INT 2078
1061: I INT 2059
1067: I INT 2047
1073: I INT 2119
1079: I INT 2057
1085: I INT 2078
1091: I INT 2035
1097: I INT 2064
1103: I INT 2069
1109: I INT 2091
1115: I INT 2066
1121: I INT 2052
1127: I INT 2077
1133: I INT 2049
1139: I INT 2067
1145: I INT 2098
1151: I INT 2057
1157: I INT 2072
1163: I INT 2073
1169: I INT 2076
1175: I INT 2047
1181: I INT 2091
1187: I INT 2078
1193: I INT 2058
1199: I INT 2081
1205: I INT 2071
1211: I INT 2062
1217: I INT 2095
1223: I INT 2082
1229: I INT 2066
1235: I INT 2083
1241: I INT 2064
1247: I INT 2077
1253: l LIST (MARK at 994)
1254: g GET 5
1257: \x87 TUPLE3
1258: R REDUCE
1259: \x85 TUPLE1
1260: R REDUCE
1261: \x94 MEMOIZE (as 6)
1262: 0 POP
1263: g GET 0
1266: C SHORT_BINBYTES b'\x01\xcev\x96.6\x96\xaeF'
1277: \x85 TUPLE1
1278: R REDUCE
1279: g GET 0
1282: C SHORT_BINBYTES b'\x01\xfa\xfaN\xf6\xfa\xfat.v\x96'
1295: \x85 TUPLE1
1296: R REDUCE
1297: \x93 STACK_GLOBAL
1298: g GET 6
1301: g GET 0
1304: C SHORT_BINBYTES b'\x01\xcev\x96.6\x96\xaeF'
1315: \x85 TUPLE1
1316: R REDUCE
1317: g GET 0
1320: C SHORT_BINBYTES b'\x01\xfa\xfa\xa6\xe6\xfa\xfat.v\x96'
1333: \x85 TUPLE1
1334: R REDUCE
1335: \x93 STACK_GLOBAL
1336: g GET 0
1339: C SHORT_BINBYTES b'\x01\xcev\x96.6\x96\xaeF'
1350: \x85 TUPLE1
1351: R REDUCE
1352: g GET 0
1355: C SHORT_BINBYTES b'\x01v\xa66'
1361: \x85 TUPLE1
1362: R REDUCE
1363: \x93 STACK_GLOBAL
1364: g GET 5
1367: \x85 TUPLE1
1368: R REDUCE
1369: I INT 50
1373: \x86 TUPLE2
1374: R REDUCE
1375: \x86 TUPLE2
1376: R REDUCE
1377: \x94 MEMOIZE (as 7)
1378: 0 POP
1379: g GET 0
1382: C SHORT_BINBYTES b'\x01\xcev\x96.6\x96\xaeF'
1393: \x85 TUPLE1
1394: R REDUCE
1395: g GET 0
1398: C SHORT_BINBYTES b'\x01\xfa\xfa\xb6\xa6.\x96.\xa6\xe6\xfa\xfat.\xce\x966'
1417: \x85 TUPLE1
1418: R REDUCE
1419: \x93 STACK_GLOBAL
1420: ( MARK
1421: V UNICODE 'Okay,maybe you need a closer examination!'
1464: V UNICODE ' '
1467: l LIST (MARK at 1420)
1468: g GET 7
1471: \x86 TUPLE2
1472: R REDUCE
1473: . STOP
highest protocol among opcodes = 4没有技巧,全靠手撕,对着opcode文档直接开撕
整理一下就可以得到
之前NSS上也是有一道给python字节码的题目,只能手撕了。
[原创]死磕python字节码-手工还原python源码-软件逆向-看雪-安全社区|安全招聘|kanxue.com
Python的pyc字节码反编译反汇编相关知识_pycdc-CSDN博客
官方文档:
dis --- Python 字节码反汇编器 — Python 3.12.3 文档
是个大工程,先贴一下别人的复原
import random
random.seed('welcome to H&NCTF')
print("Do you know what's the flag???")
flag = input('> ')
flag = list(flag.encode())
print(flag)
a = [] #加密字符
b = [2024, 2024, 2024, 2024, 2024, 2024, 2075, 2099, 2071,
2082, 2078, 2059, 2047, 2119, 2057, 2078, 2035, 2064,
2069, 2091, 2066, 2052, 2077, 2049, 2067, 2098, 2057,
2072, 2073, 2076, 2047, 2091, 2078, 2058, 2081, 2071,
2062, 2095, 2082, 2066, 2083, 2064, 2077]
list1 = list(random.randbytes(len(flag)))
key1 = 'H&NCTF'
key1 = list(str.encode(key1))
key2 = list(random.randbytes(len(key1)))
enc_flag = []
for i in range(len(flag)):
enc_flag.append((flag[i] ^ key1[i % len(key1)]) + 2024)
if enc_flag == b:
print('Okay,maybe you need a closer examination!')
else:
print('')
enc_flag = []
for i in range(len(flag)):
enc_flag.append((flag[i] ^ key2[i % len(key2)]) ^ (list1[i] ^ key1[i % len(key1)]))
if enc_flag == a:
print('Okay,you get the flag!')
else:
print('Oh no,maybe you should try again~')
pickle的调试器
GitHub - Legoclones/pickledbg: A GDB+GEF-style debugger for unloading Python pickles
import random
# 给定的加密过程中的列表 'b'
b = [2024, 2024, 2024, 2024, 2024, 2024, 2075, 2099, 2071,
2082, 2078, 2059, 2047, 2119, 2057, 2078, 2035, 2064,
2069, 2091, 2066, 2052, 2077, 2049, 2067, 2098, 2057,
2072, 2073, 2076, 2047, 2091, 2078, 2058, 2081, 2071,
2062, 2095, 2082, 2066, 2083, 2064, 2077]
# 加密过程中使用的密钥
key1 = b'H&NCTF'
# 解密过程
flag = []
for i in range(len(b)):
decrypted_byte = (b[i] - 2024) ^ key1[i % len(key1)]
flag.append(decrypted_byte)
# 将字节列表转换回字符串
flag_str = bytes(flag).decode()
print("解密后的 flag:", flag_str)
flag = list(flag.encode())
# 作用是将输入的 flag 字符串转换成一个字节值的列表
'example'-->b'example'-->[101, 120, 97, 109, 112, 108, 101]
flag_str = bytes(flag).decode()
#逆操作




















 303
303

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








