还有兄弟不知道网络安全面试可以提前刷题吗?费时一周整理的160+网络安全面试题,金九银十,做网络安全面试里的显眼包!
王岚嵚工程师面试题(附答案),只能帮兄弟们到这儿了!如果你能答对70%,找一个安全工作,问题不大。
对于有1-3年工作经验,想要跳槽的朋友来说,也是很好的温习资料!
【完整版领取方式在文末!!】
93道网络安全面试题
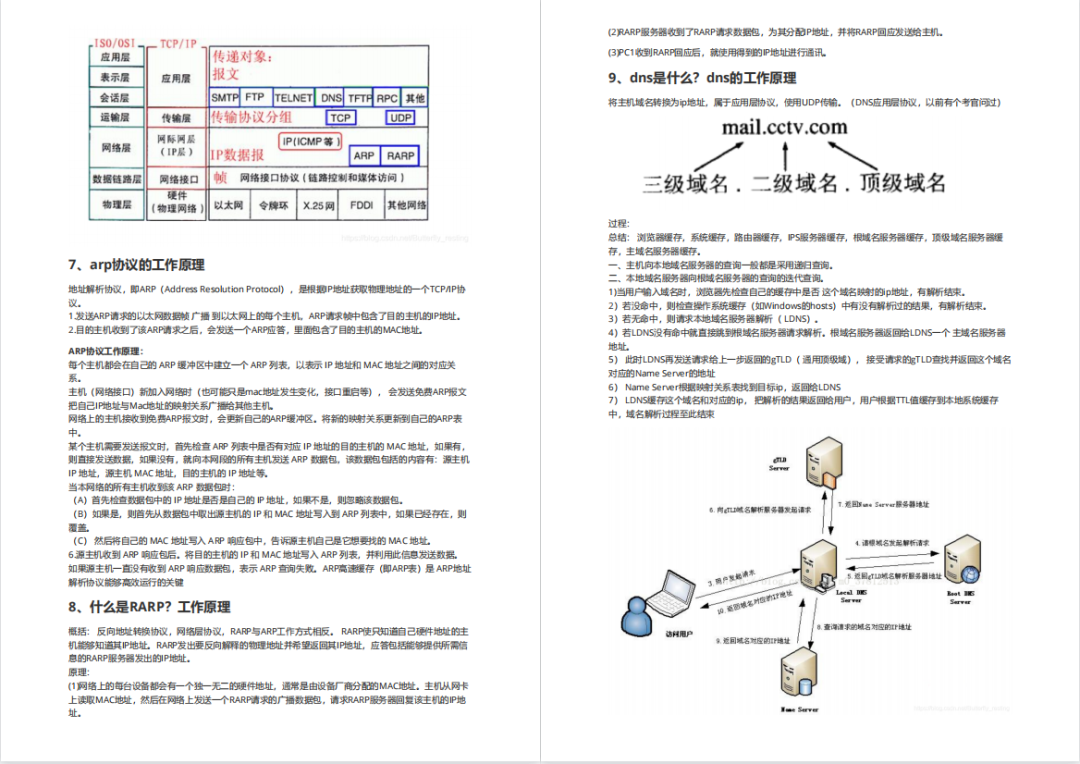
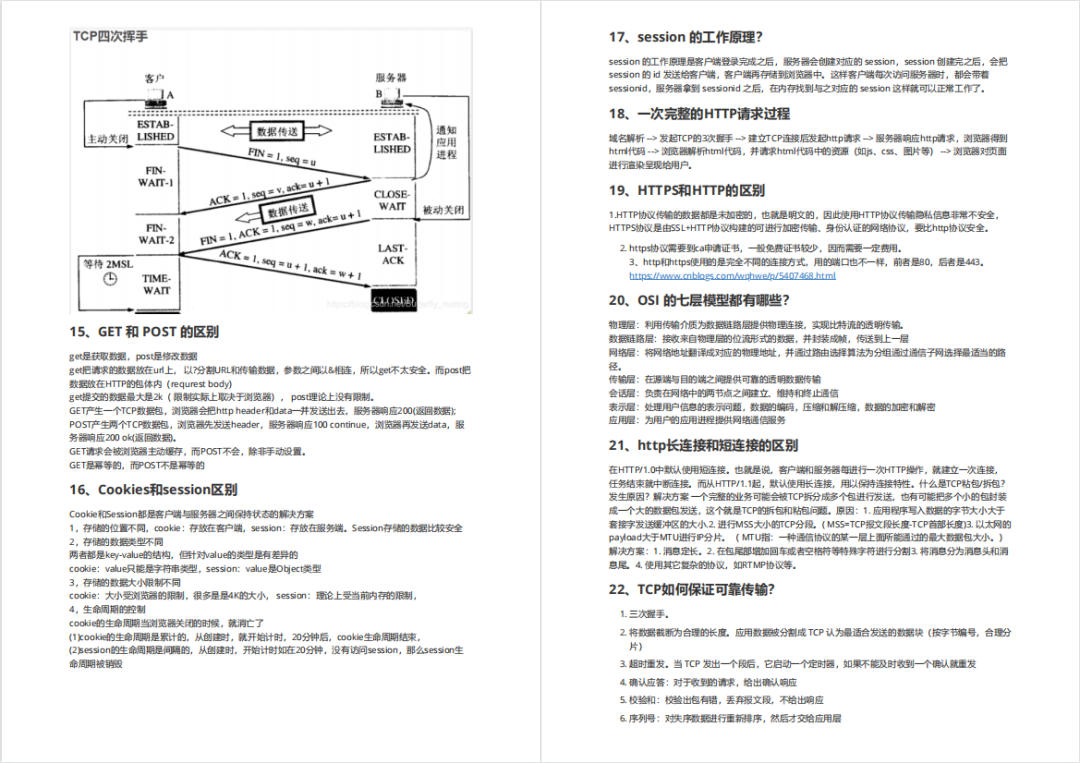

内容实在太多,不一一截图了
黑客学习资源推荐
最后给大家分享一份全套的网络安全学习资料,给那些想学习 网络安全的小伙伴们一点帮助!
对于从来没有接触过网络安全的同学,我们帮你准备了详细的学习成长路线图。可以说是最科学最系统的学习路线,大家跟着这个大的方向学习准没问题。
1️⃣零基础入门
① 学习路线
对于从来没有接触过网络安全的同学,我们帮你准备了详细的学习成长路线图。可以说是最科学最系统的学习路线,大家跟着这个大的方向学习准没问题。
② 路线对应学习视频
同时每个成长路线对应的板块都有配套的视频提供:
网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。
一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!
trs = soup.find_all('tr')
for i in range(1, len(trs)):
tr = trs[i]
tds = tr.find_all("td")
ip_item = tds[5].text.lower() + "://" + tds[1].text + ":" + tds[2].text
if ip_item[:5] == "https":
self.ip_https_list_tmp.add(ip_item)
elif ip_item[:4] == "http":
self.ip_http_list_tmp.add(ip_item)
def _check(self):
# 用百度验证https代理
while len(self.ip_https_list_tmp) > 0:
ip_for_test = self.ip_https_list_tmp.pop()
proxies = {
'https': ip_for_test
}
try:
response = requests.get('https://www.baidu.com', headers=headers, proxies=proxies, timeout=3)
if response.status_code == 200:
self.ip_https_list.add(ip_for_test)
except:
continue
# 验证http代理
while len(self.ip_http_list_tmp) > 0:
ip_for_test = self.ip_http_list_tmp.pop()
proxies = {
'http': ip_for_test
}
try:
response = requests.get('http://httpbin.org/ip', headers=headers, proxies=proxies, timeout=3)
if response.status_code == 200:
self.ip_http_list.add(ip_for_test)
except:
continue
if name == “main”:
Proxy = GetProxy()
Proxy.get()
print(“https代理:”)
print(Proxy.ip_https_list)
print(“http代理:”)
print(Proxy.ip_http_list)

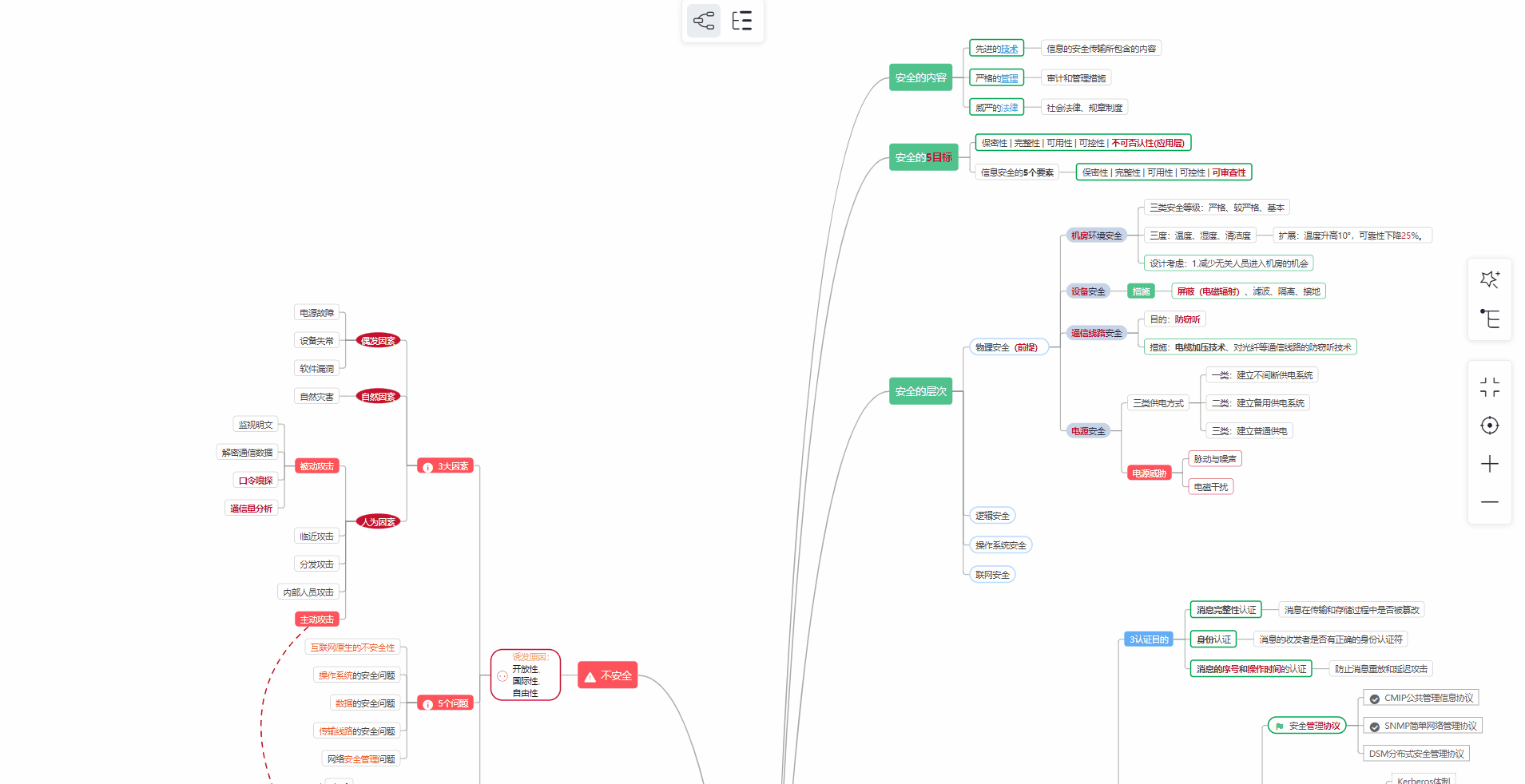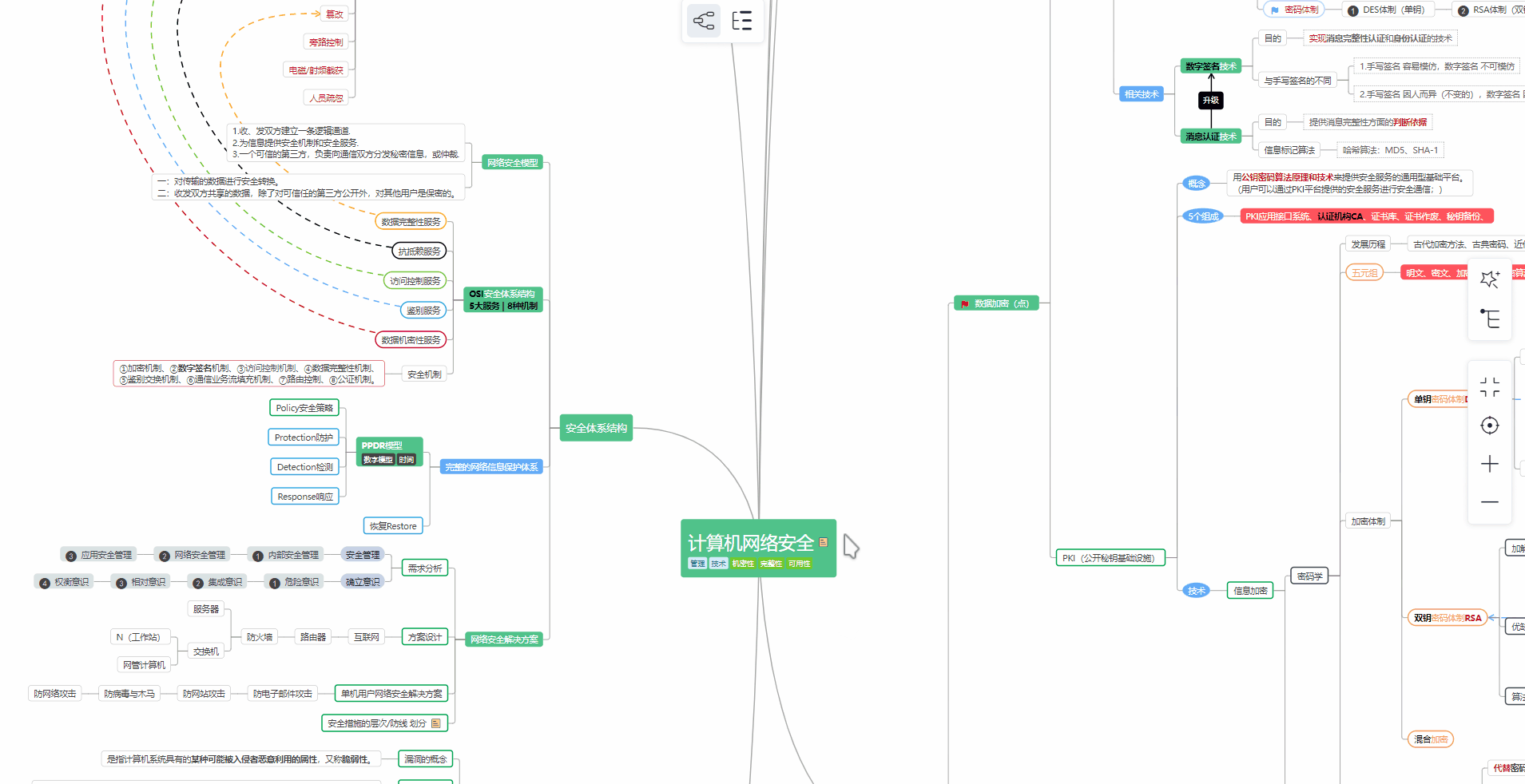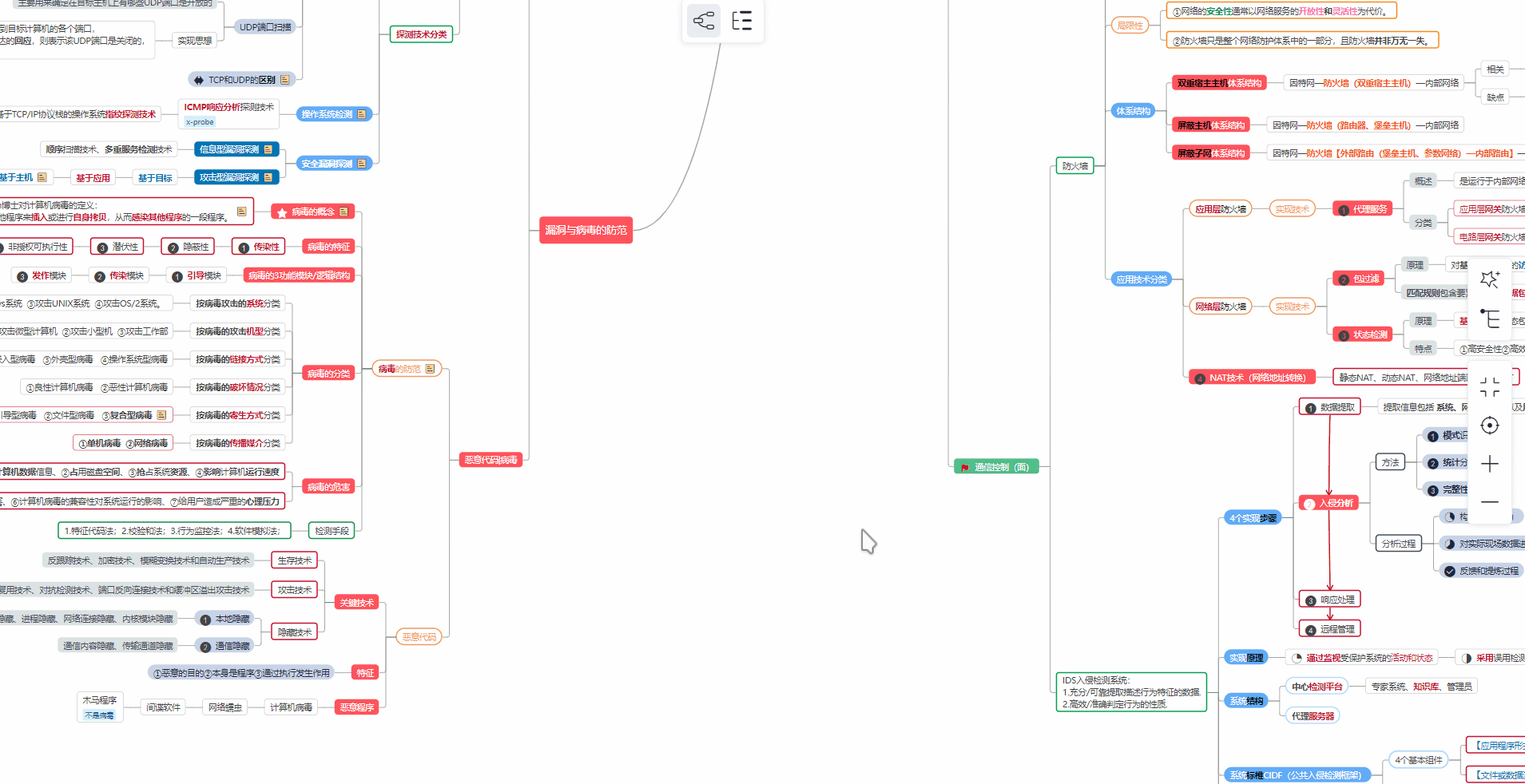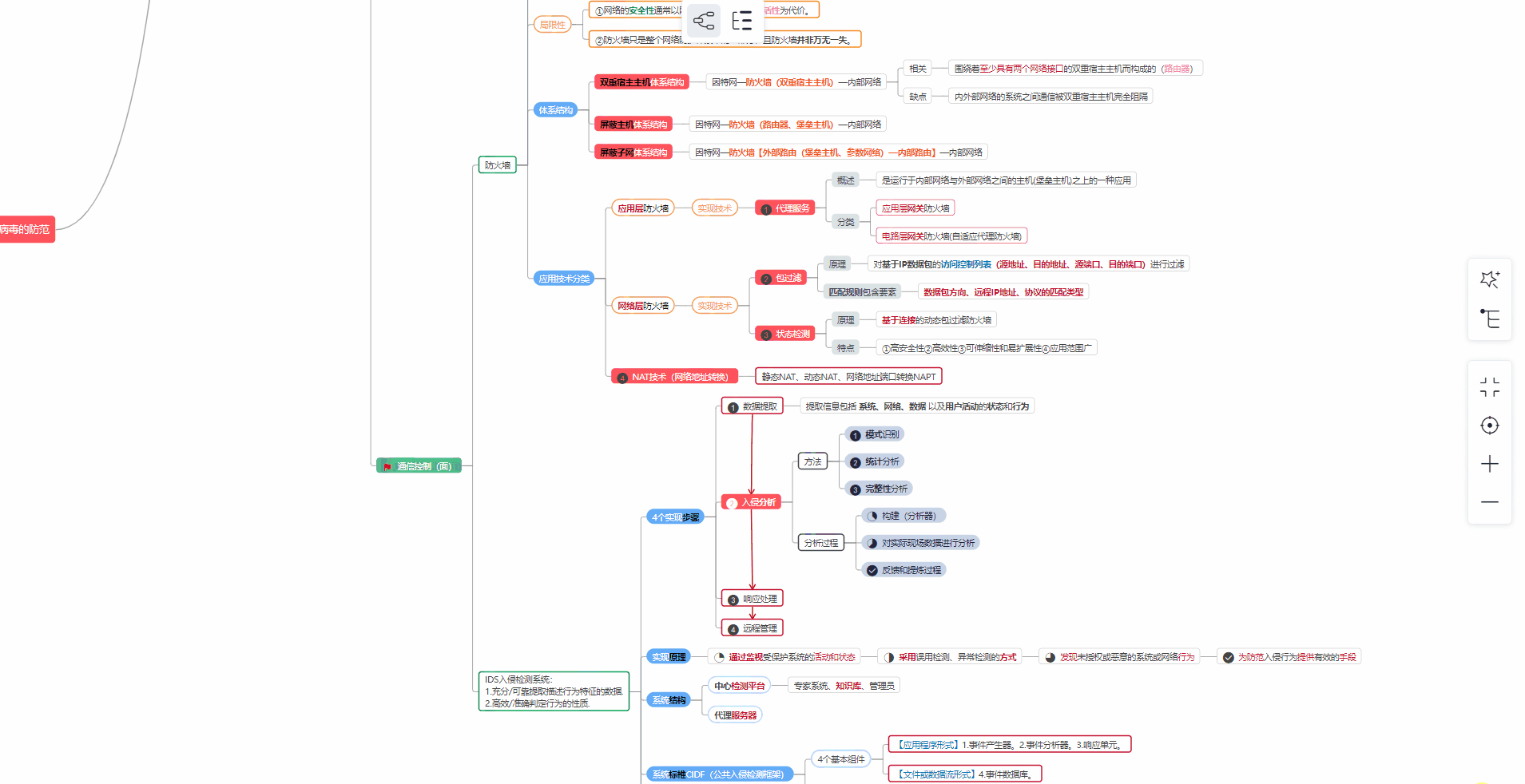
代理发现结果
## 地址段IP发现
import ipaddress
import multiprocessing
import random
from scapy.layers.inet import IP, ICMP
from scapy.sendrecv import sr1
DIP = “121.17.123.1/24”
BNUM = 20
TNUM = 64
def getBytes(num):
res = ‘’.join(random.sample(‘abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ01234567’, num))
return bytes(res, encoding=‘utf-8’)
def ping(ip):
pkt = IP(dst=ip) / ICMP() / getBytes(BNUM)
res = sr1(pkt, timeout=5, verbose=False)
if res:
return True, ip
else:
return False, ip
def getIpList(ip):
temp = ipaddress.ip_network(ip, False).hosts()
ipList = []
for i in temp:
ipList.append(str(i))
return ipList
def ipScan(ip, num):
ipList = getIpList(ip)
pool = multiprocessing.Pool(processes=int(TNUM))
result = pool.map(ping, ipList)
pool.close()
pool.join()
for res, ip in result:
if res:
print(ip)
if name == “main”:
ipScan(DIP, TNUM)
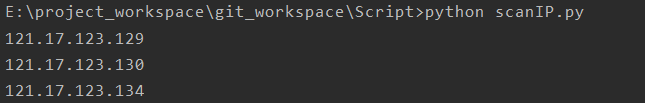
IP发现
这个脚本自己写的,还不会写参数,只好弄全局变量了,地址是我随便敲的,各位看官不要一直ping人家,换一个地址段试试。
## Ping命令
“”"
–coding:utf-8–
@File: Ping.py
@Author:frank yu
@DateTime: 2020.12.13 10:35
@Contact: frankyu112058@gmail.com
@Description:Implement of Ping
“”"
import random
import socket
import struct
import time
def checksum(msg):
“”"
:param msg:icmp message(bytes)
:return:checksum(bytes)
“”"
check_sum = 0
n = len(msg)
def carry_around_add(a, b):
c = a + b
return (c & 0xffff) + (c >> 16)
for i in range(0, n, 2):
w = msg[i] + (msg[i + 1] << 8)
check_sum = carry_around_add(check_sum, w)
res = ~check_sum & 0xffff
res = res >> 8 | (res << 8 & 0xff00)
return res
def icmp_packet(sequence_number):
“”"
:param sequence_number:
:return: binary of icmp packet
“”"
icmp_type = 8 # ICMP Echo Request
icmp_code = 0 # zero
icmp_checksum = 0 # set to zero first
icmp_Identifier = 1 # Identifier
icmp_Sequence_number = sequence_number
icmp_Data = b’abcdefghijklmnopqrstuvwabcdefghi’ # data
icmp_message = struct.pack(‘>2B3H32s’, icmp_type, icmp_code, icmp_checksum, icmp_Identifier, icmp_Sequence_number,
icmp_Data)
icmp_checksum = checksum(icmp_message)
icmp_message = struct.pack(‘>2B3H32s’, icmp_type, icmp_code, icmp_checksum, icmp_Identifier, icmp_Sequence_number,
icmp_Data)
return icmp_message
def icmp_request(dst_addr, pkt, timeout=2):
“”"
send icmp packet and return socket for listening
:param timeout: timeout
:param dst_addr: ip of destination address
:param pkt: packet of icmp
:return: socket of icmp,time
“”"
icmp_socket = socket.socket(socket.AF_INET, socket.SOCK_RAW, socket.IPPROTO_ICMP)
icmp_socket.settimeout(timeout)
icmp_socket.sendto(pkt, (dst_addr, 80))
send_time = time.time()
return icmp_socket, send_time
def icmp_reply(icmp_socket, send_time, sequence_num):
“”"
monitor the icmp socket and return how much time spent if receives reply msg
:param icmp_socket:socket which sent icmp msg before
:param send_time: time when send icmp request
:param sequence_num:sequence num
:return:time and TTL/-1,-1
“”"
try:
recv_pkt, addr = icmp_socket.recvfrom(1024)
# print(recv_pkt)
recv_time = time.time()
icmpHeader = recv_pkt[20:28]
type, _, _, _, sequence = struct.unpack(“>2B3H”, icmpHeader)
if type == 0 and sequence == sequence_num:
return recv_time - send_time, recv_pkt[8]
except socket.timeout:
return -1, -1
def ping(host):
“”"
:param host:domain name or ip addr
:return: None
“”"
Sequence_number = random.randint(0, 10 ** 4)
# 若为ip,不变;若为域名,转为ip
try:
dst_addr = socket.gethostbyname(host)
except socket.gaierror:
print(f’something wrong, please check your input.‘)
exit(0)
miss, short, long, alltime = 0, 10 ** 9, 0, []
print(f"正在 Ping {host} [{dst_addr}] 具有 32 字节的数据:“)
for i in range(0, 4):
# 构造icmp数据包
icmp_pkt = icmp_packet(Sequence_number + i)
# print(icmp_pkt)
# 发送并记录时间
icmp_socket, send_time = icmp_request(dst_addr, icmp_pkt)
# 接收并计算时间差
times, TTL = icmp_reply(icmp_socket, send_time, Sequence_number + i)
if times >= 0:
print(f"来自 {dst_addr} 的回复: 字节=32 时间={int(times * 1000)}ms TTL={TTL}”)
if short > times:
short = times
if long < times:
long = times
alltime.append(times * 1000)
time.sleep(1)
else:
print(“请求超时。”)
miss += 1
print()
print(f’{dst_addr} 的 Ping 统计信息:\n’
f’ 数据包: 已发送 = 4,已接收 = {4 - miss},丢失 = {miss} ({int(miss / 4 * 100)}% 丢失),‘)
if miss < 4:
print(‘往返行程的估计时间(以毫秒为单位):\n’
f’ 最短 = {int(short * 1000)}ms,最长 = {int(long * 1000)}ms,平均 = {int(sum(alltime) / (4 - miss))}ms’)
return None
if name == ‘main’:
host = input(‘please input domain name or ip addr:’)
ping(host)
学习了[ICMP协议](https://bbs.csdn.net/topics/618540462)之后,写的上面这个脚本。 可以实现简单的Ping命令。

## 端口扫描
/usr/bin/env python3
* coding:utf-8 *
auther: saucerman
project: https://github.com/saucer-man/penetration-script
“”"
基于python-nmap的端口扫描器
pip install python-nmap
“”"
import sys
import time
from colorama import init, Fore, Back, Style
import getopt
颜色定义
init(autoreset=True)
class Colored(object):
def red(self, s):
return Fore.RED + s + Fore.RESET
def blue(self, s):
return Fore.BLUE + s + Fore.RESET
def yellow(self, s):
return Fore.YELLOW + s + Fore.RESET
color = Colored()
try:
import nmap
except:
print(“FATAL: Module nmap missing (python-nmap)”)
sys.exit(1)
使用说明
def usage():
print(color.blue(‘Usage: port scanner’))
print(color.blue(‘\t-h/–host:\tpoint the target to scan’))
print(color.blue(‘\t-p/–port:\tpoint the port to scan(not nessesary)’))
print(color.blue(‘Examples:’))
print(color.blue(‘\tpython port_scanner.py -h 10.10.10.1’))
print(color.blue(‘\tpython port_scanner.py -h 10.10.10.1 -p 80,443,8080’))
print(color.blue(‘\tpython port_scanner.py -h 10.10.10.1 -p 1-1024’))
print(color.blue(‘\nSEE THE MAN PAGE (https://github.com/saucer-man/saucer-frame) FOR MORE OPTIONS AND EXAMPLES’))
sys.exit(0)
扫描
def scanner(host, ports):
nm = nmap.PortScanner()
try:
print(‘Scanner report for %s\n’ % host)
if len(ports) == 0:
result = nm.scan(host)
else:
result = nm.scan(host, ports)
if result[‘nmap’][‘scanstats’][‘uphosts’] == ‘0’:
print(color.red(‘Host seems down’))
else:
print(‘Host is up’)
print(“{:<7}\t{:<7}\t{:<7}\t{:<7}”.format(‘PORT’, ‘STATE’, ‘SERVICE’, ‘VERSION’))
for k, v in result[‘scan’][host][‘tcp’].items():
if v[‘state’] == ‘open’:
print(color.yellow(“{:<7}\t{:<7}\t{:<7}\t{:<7}”.format(str(k), v[‘state’], v[‘name’],
v[‘product’] + v[‘version’])))
学习路线:
这个方向初期比较容易入门一些,掌握一些基本技术,拿起各种现成的工具就可以开黑了。不过,要想从脚本小子变成黑客大神,这个方向越往后,需要学习和掌握的东西就会越来越多以下是网络渗透需要学习的内容:
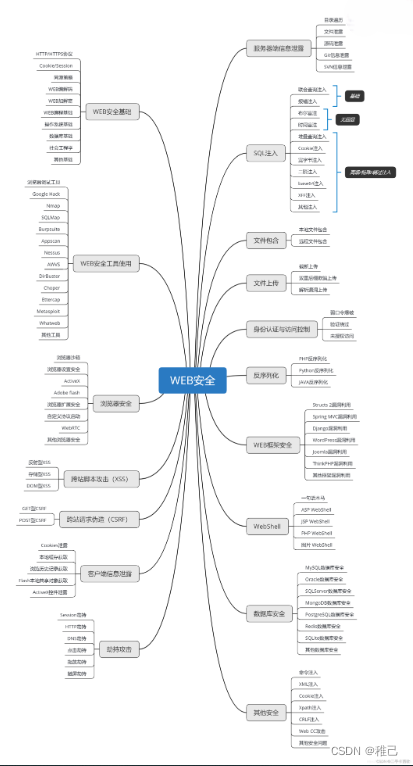
网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。
一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!






















 853
853

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








