先自我介绍一下,小编浙江大学毕业,去过华为、字节跳动等大厂,目前阿里P7
深知大多数程序员,想要提升技能,往往是自己摸索成长,但自己不成体系的自学效果低效又漫长,而且极易碰到天花板技术停滞不前!
因此收集整理了一份《2024年最新软件测试全套学习资料》,初衷也很简单,就是希望能够帮助到想自学提升又不知道该从何学起的朋友。
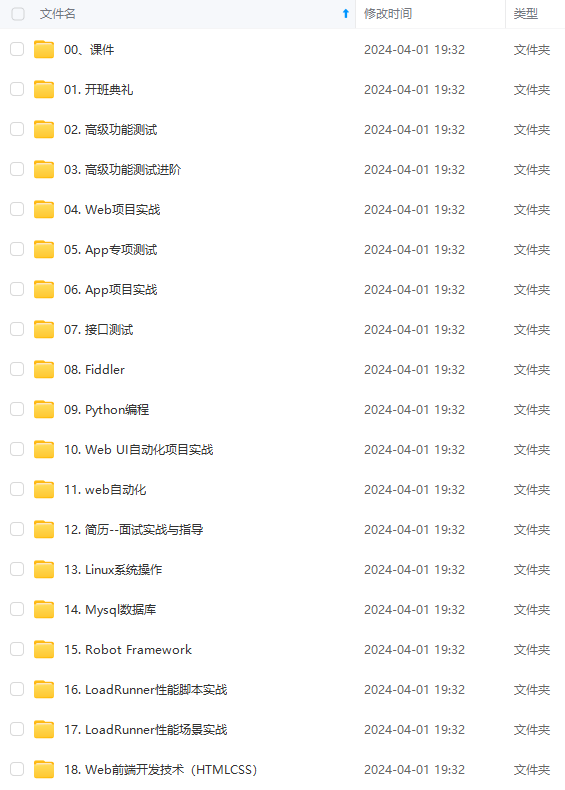
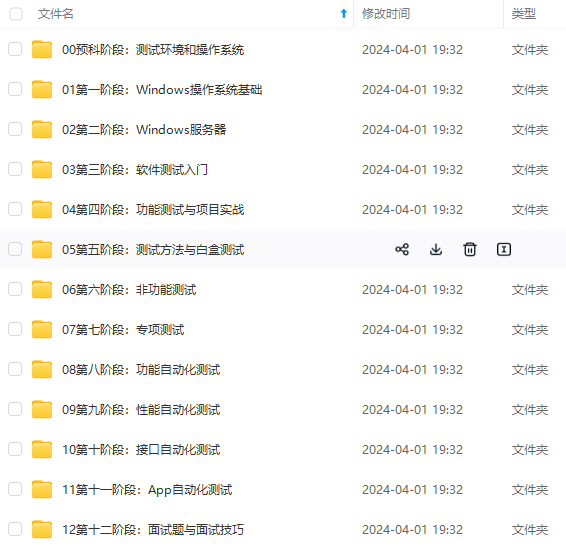
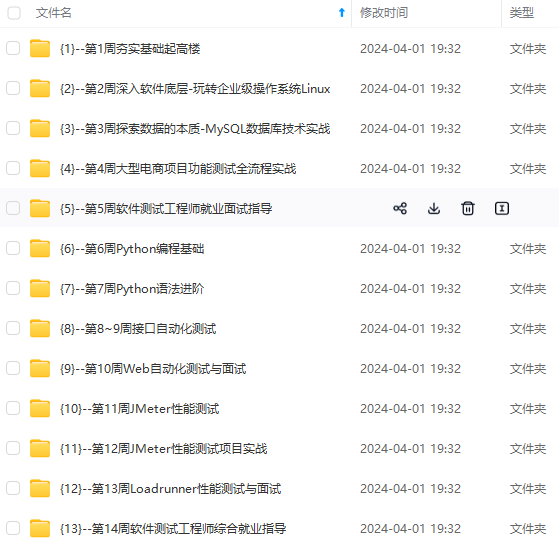
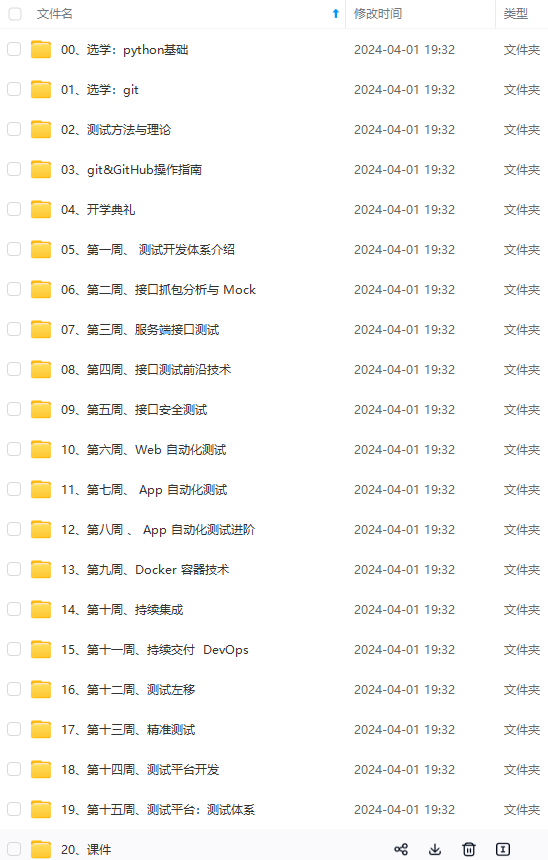
既有适合小白学习的零基础资料,也有适合3年以上经验的小伙伴深入学习提升的进阶课程,涵盖了95%以上软件测试知识点,真正体系化!
由于文件比较多,这里只是将部分目录截图出来,全套包含大厂面经、学习笔记、源码讲义、实战项目、大纲路线、讲解视频,并且后续会持续更新
如果你需要这些资料,可以添加V获取:vip1024b (备注软件测试)

正文
tcp6 0 0 :::389 ::😗 LISTEN 11394/slapd
注: 软件默认安装路径为/etc/ldap,mdb数据库文件存放路径为/var/lib/ldap/4. 测试LDAP的接口
ldapwhoami -H ldap:// -x
anonymous
anonymous是匿名用户的查询结果,因为我们运行ldapwhoami而不登录到LDAP服务器.这意味着服务器正在运行并应答查询. 5. 启动停止
systemctl stop slapd.service
systemctl start slapd.service
至此,LDAP的初步基本配置已经完成.官方文档解释在2.3之后的版本使用动态的配置文件的方式,使用ldapadd, ldapdelete or ldapmodify修改更新配置信息以及数据库信息,不建议使用slapd.conf配置文件方式进行管理.
二. 查看初始化信息
ldapsearch -Q -LLL -Y EXTERNAL -H ldapi:/// -b cn=config dn
dn: cn=config
dn: cn=module{0},cn=config
dn: cn=schema,cn=config
dn: cn={0}core,cn=schema,cn=config
dn: cn={1}cosine,cn=schema,cn=config
dn: cn={2}nis,cn=schema,cn=config
dn: cn={3}inetorgperson,cn=schema,cn=config
dn: olcBackend={0}mdb,cn=config
dn: olcDatabase={-1}frontend,cn=config
dn: olcDatabase={0}config,cn=config
dn: olcDatabase={1}mdb,cn=config
ldapsearch -x -LLL -H ldap:/// -b dc=wecash,dc=net dn
dn: dc=wecash,dc=net
dn: cn=admin,dc=wecash,dc=net
三. TLS
1、安装gnutls-bin和ssl-cert软件包
apt install gnutls-bin ssl-cert
2、为证书颁发机构创建私钥
sh -c “certtool --generate-privkey > /etc/ssl/private/cakey.pem”
3、创建模板文件/etc/ssl/ca.info来定义CA
cn = Wecash Company
ca
cert_signing_key
4、创建自签名CA证书
certtool --generate-self-signed --load-privkey /etc/ssl/private/cakey.pem --template /etc/ssl/ca.info --outfile /etc/ssl/certs/cacert.pem
5、为服务器创建私钥
certtool --generate-privkey --sec-param Medium --outfile /etc/ssl/private/tldap.wecash.net-key.pem
6、创建/etc/ssl/tldap.wecash.net.info信息文件,其中包含
organization = Wecash Company
cn = tldap.wecash.net
tls_www_server
encryption_key
signing_key
expiration_days = 3650
7、创建服务器的证书
certtool --generate-certificate --load-privkey /etc/ssl/private/tldap.wecash.net-key.pem --load-ca-certificate /etc/ssl/certs/cacert.pem --load-ca-privkey /etc/ssl/private/cakey.pem --template /etc/ssl/tldap.wecash.net.info --outfile /etc/ssl/certs/tldap.wecash.net.pem
8、调整权限和所有权
mkdir /etc/ldap/certs
cp /etc/ssl/private/tldap.wecash.net-key.pem /etc/ldap/certs/
cp /etc/ssl/certs/cacert.pem /etc/ldap/certs/
cp /etc/ssl/certs/tldap.wecash.net.pem /etc/ldap/certs/
chown -R openldap.openldap /etc/ldap/certs/
chmod 0640 /etc/ssl/private/tldap.wecash.net-key.pem
gpasswd -a openldap ssl-cert
9、创建文件certinfo.ldif
cat certinfo.ldif
create new
dn: cn=config
changetype: modify
add: olcTLSCACertificateFile
olcTLSCACertificateFile: /etc/ldap/certs/cacert.pem
replace: olcTLSCertificateFile
olcTLSCertificateFile: /etc/ldap/certs/tldap.wecash.net.pem
replace: olcTLSCertificateKeyFile
olcTLSCertificateKeyFile: /etc/ldap/certs/tldap.wecash.net-key.pem
10、使用ldapmodify命令通过slapd-config数据库告诉slapd我们的TLS工作
ldapmodify -Y EXTERNAL -H ldapi:/// -f certinfo.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry “cn=config”
11.需要在/etc/default/slapd中添加ldaps:///才能使用加密。
vim /etc/default/slapd
SLAPD_SERVICES=“ldap:/// ldapi:/// ldaps:///”
12、修改请求域名
cat slapd.ldif
log
dn: cn=config
changetype: modify
replace: olcLogLevel
olcLogLevel: stats
add: olcIdleTimeout
olcIdleTimeout: 30
add: olcReferral
olcReferral: ldaps://tldap.wecash.net
add: olcLogFile
olcLogFile: /var/log/sladp.log
ldapmodify -Q -Y EXTERNAL -H ldapi:/// -f slapd.ldif
modifying entry “cn=config”
ldapsearch -Y external -H ldapi:/// -b cn=config “(objectClass=olcGlobal)” olcReferral
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
extended LDIF
LDAPv3
base <cn=config> with scope subtree
filter: (objectClass=olcGlobal)
requesting: olcReferral
config
dn: cn=config
olcReferral: ldaps://tldap.wecash.net
search result
search: 2
result: 0 Success
numResponses: 2
numEntries: 1
13、重启slapd服务
systemctl restart slapd.service
netstat -ntlp | grep slapd
tcp 0 0 0.0.0.0:389 0.0.0.0:* LISTEN 13728/slapd
tcp 0 0 0.0.0.0:636 0.0.0.0:* LISTEN 13728/slapd
tcp6 0 0 :::389 ::😗 LISTEN 13728/slapd
tcp6 0 0 :::636 ::😗 LISTEN 13728/slapd
四. 验证数据
1、初始化一些数据
cat add_content.ldif
dn: ou=People,dc=example,dc=com
objectClass: organizationalUnit
ou: People
dn: ou=Groups,dc=example,dc=com
objectClass: organizationalUnit
ou: Groups
dn: cn=miners,ou=Groups,dc=example,dc=com
objectClass: posixGroup
cn: miners
gidNumber: 5000
dn: uid=john,ou=People,dc=example,dc=com
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: shadowAccount
uid: john
sn: Doe
givenName: John
cn: John Doe
displayName: John Doe
uidNumber: 10000
gidNumber: 5000
userPassword: johnldap
gecos: John Doe
loginShell: /bin/bash
homeDirectory: /home/john
ldapadd -x -W -D “cn=admin,dc=wecash,dc=net” -f add_content.ldif
Enter LDAP Password: ********
adding new entry “ou=People,dc=example,dc=com”
adding new entry “ou=Groups,dc=example,dc=com”
adding new entry “cn=miners,ou=Groups,dc=example,dc=com”
adding new entry “uid=john,ou=People,dc=example,dc=com”
此时,使用客户端工具phpLDAPadmin或者LDAP Admin Tool访问LDAP server端即可以查看到数据. 2. 查询目录结构树
ldapsearch -x -LLL -H ldap:/// -b dc=wecash,dc=net dn
dn: dc=wecash,dc=net
dn: cn=admin,dc=wecash,dc=net
dn: ou=Hosts,dc=wecash,dc=net
dn: ou=Devops,dc=wecash,dc=net
dn: ou=Groups,dc=wecash,dc=net
dn: ou=People,dc=wecash,dc=net
dn: ou=Marketing,dc=wecash,dc=net
dn: ou=department,dc=wecash,dc=net
dn: cn=iris+ipHostNumber=192.168.1.51,ou=Hosts,dc=wecash,dc=net
dn: cn=gojira+ipHostNumber=192.168.1.1,ou=Hosts,dc=wecash,dc=net
dn: cn=zedan+ipHostNumber=192.168.1.52,ou=Hosts,dc=wecash,dc=net
dn: cn=gamera+ipHostNumber=192.168.1.50,ou=Hosts,dc=wecash,dc=net
dn: cn=git-wecash01cn-p001.pek3.wecash.net,ou=Hosts,dc=wecash,dc=net
dn: uid=shuke,ou=Devops,dc=wecash,dc=net
dn: cn=dba,ou=Groups,dc=wecash,dc=net
dn: cn=devops,ou=Groups,dc=wecash,dc=net
dn: cn=tester,ou=Groups,dc=wecash,dc=net
dn: cn=manager,ou=Groups,dc=wecash,dc=net
dn: cn=developer,ou=Groups,dc=wecash,dc=net
dn: cn=Pete Minsky,ou=Marketing,dc=wecash,dc=net
账号登录认证
ldapwhoami -H ldapi:/// -x -D cn=admin,dc=wecash,dc=net -W
Enter LDAP Password:
dn:cn=admin,dc=wecash,dc=net
五. Logging设置
1、使用以下内容创建文件logging.ldif
cat logging.ldif
dn: cn=config
changetype: modify
replace: olcLogLevel
olcLogLevel: stats
2、更新数据
ldapmodify -Q -Y EXTERNAL -H ldapi:/// -f logging.ldif
3、在/etc/rsyslog.conf增加内容
Disable rate limiting
(default is 200 messages in 5 seconds; below we make the 5 become 0)
$SystemLogRateLimitInterval 0
4、重启rsyslog服务
systemctl restart syslog.service
此时,tail -f /var/log/syslog查看日志文件内容,可以查看到LDAP相关log
六. LDAP命令介绍
ldapmodrdn 命令用于对 OpenLDAP 目录树中 RDN 条目的修改,可以从标准的条目信息输入或者使用 -f 指定 LDIF 文件的格式输入。
ldapmodrdn -x -D cn=admin,dc=wecash,dc=net -w weopenldap -H ldapi:/// “cn=dba,ou=Groups,dc=wecash,dc=net” cn=wedba
ldappasswd 命令用于修改密码
ldappasswd -x -D cn=admin,dc=wecash,dc=net -w weopenldap -H ldapi:/// “cn=wedba,ou=Groups,dc=wecash,dc=net” -S
ldapdelete 命令用于从目录树中删除指定条目,并根据 DN 条目删除一个或多个条目,但必须提供所要删除指定条目的权限所绑定的 DN(整个目录树的唯一标识名称)。
ldapdelete -x -w weopenldap -D cn=admin,dc=wecash,dc=net “cn=tester,ou=Groups,dc=wecash,dc=net”
要检测配置文件的可用性,可设置输出级别:
slaptest -F /etc/ldap/slapd.d
config file testing succeeded
slaptest -d 3 -F /etc/ldap/slapd.d
slapcat 命令用于将数据条目转换为 OpenLDAP 的 LDIF 文件,可用于 OpenLDAP 条目的备份以及结合 slapdadd 指定用于恢复条目。
下面通过slapcat 备份 OpenLDAP 所有目录树条目:
slapcat -v -l openldap.ldif
通过 ldapsearch 查看 shuke 用户及 sre 组相关信息,命令如下:
ldapsearch -x -LLL uid=shuke
dn: uid=shuke,ou=stuff,dc=shuke,dc=com
givenName: shu
sn: ke
userPassword:: e01ENX00UXJjT1VtNldhdStWdUJYOGcrSVBnPT0=
gidNumber: 5000
homeDirectory: /home/shuke
loginShell: /bin/bash
cn: shuke
uid: shuke
uidNumber: 1100
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
objectClass: person
objectClass: ldapPublicKey
sshPublicKey: ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDRMPwi6Q/Zcb1N6sWnFf5/EwTv
mpfEZyRI0XUnCtZKWEPPCbgjPfQ2ZKYPCsmfvqA6uaVolBzLM04BZEbbeHmC1mB3kpvOXmZtH7iAt
22khCyS5A/jzaE9lwgyGzO/mhJQ83EIBt4MtO/UgGyk1EAyQH0gAGgfqQ2Htyp44wxul0plpbcmTE
lQQUZiLMNUspKS4i3BDGSWwu+Y2q7h3jTfgMpyLweqnt4vuUwhaGouP1P6q7M7HCRMKbXL5MH3K0s
z5G1WpiqsXxtHbFgQZiniOwO/EaUvca9MQRwY5zeMxkUJ38HlpvRjp16HevpuLqvUqy2Uw2migJNW
52ZubtGlOzc8mJh/qSLUTV1238Z6dgR6nELa260RnsPNp3Utb7HkhY6WZSRYxNxjvsGWDIKMczPHb
fhHf0iuuxGt96dPhpM6V8UH0zbPUEL/6+VRTMThflewLA+2/9J5VzG+Ugqm3vU3jVZxgMqqFlJmI9
nfw0/H+1H+6AEU556fNTqBFQAEQDNKltv4hv/YLmpcYh7lSJU9TjHaHCXpbLDaAQPLcNBFzA1lL3K
U+rx1xwww4Tbn77qU/JmSACLP/oczrLvb+kLjO2dyi0WfEjqgeIn83OPPv4CtTMlpHZj2kP2L7Sw8
RZHXurL1wLqBnVrCGzHcC2huB9jn3QUedWjVqdA6Sw== shuke@shukes-mbp
[root@tldap ldap]# ldapsearch -x -LLL cn=sre
dn: cn=sre,ou=groups,dc=shuke,dc=com
cn: sre
objectClass: posixGroup
objectClass: top
gidNumber: 5000
description: sre group
memberUid: uid=wangwu,ou=stuff,dc=shuke,dc=com
memberUid: uid=guoliman,ou=stuff,dc=shuke,dc=com
memberUid: uid=fengfengzhao,ou=stuff,dc=shuke,dc=com
memberUid: uid=shuke,ou=stuff,dc=shuke,dc=com
memberUid: uid=mazengsui,ou=stuff,dc=shuke,dc=com
LDAP客户端机器验证:
getent passwd shuke
shuke:*:12514:10202:shuke:/home/shuke:/bin/bash
OpenLDAP 命令介绍-OpenLDAP
七. 卸载LDAP
1、命令卸载
apt-get purge --auto-remove slapd ldap-utils
2、删除目录
rm -rf /etc/ldap && rm -rf /var/lib/ldap
八. Backup and Restore
1、下载脚本文件
wget --no-check-certificate https://raw.githubusercontent.com/alexanderjackson/ldap-backup-and-restore/master/ldap-backup -O /usr/local/sbin/ldap-backup
wget --no-check-certificate https://raw.githubusercontent.com/alexanderjackson/ldap-backup-and-restore/master/ldap-restore -O /usr/local/sbin/ldap-restore
chown root.root /usr/local/sbin/ldap-backup /usr/local/sbin/ldap-restore
chmod 500 /usr/local/sbin/ldap-backup /usr/local/sbin/ldap-restore
备份脚本
2、备份脚本
grep -v ‘^#’ /usr/local/sbin/ldap-backup
TIMESTAMP=
(
d
a
t
e
+
B
A
C
K
U
P
P
A
T
H
=
/
d
a
t
a
/
b
a
c
k
u
p
s
/
l
d
a
p
/
(date +%Y%m%d-%H%M%S) BACKUP_PATH=/data/backups/ldap/
(date+BACKUPPATH=/data/backups/ldap/{TIMESTAMP}
echo " Creating backup at ${BACKUP_PATH}"
mkdir -p ${BACKUP_PATH}
/usr/bin/nice /usr/sbin/slapcat -n 0 > ${BACKUP_PATH}/config.ldif
/usr/bin/nice /usr/sbin/slapcat -n 1 > ${BACKUP_PATH}/domain.ldif
/usr/bin/nice /usr/sbin/slapcat -n 2 > ${BACKUP_PATH}/access.ldif
chmod 640 ${BACKUP_PATH}/*.ldif
tar cpzf ${BACKUP_PATH}/etc_ldap.tgz /etc/ldap >/dev/null 2>&1
tar cpzf ${BACKUP_PATH}/var_lib_ldap.tgz /var/lib/ldap >/dev/null 2>&1
ls -ahl ${BACKUP_PATH}
echo “Run ldap-restore to restore previous backups…”
3、计划任务
cat /etc/cron.d/ldap-backup
MAILTO=yunwei@wecash.net
0 0 * * * root /usr/local/sbin/ldap-backup
4、恢复LDAP数据
sudo systemctl stop slapd.service
sudo mkdir /var/lib/ldap/accesslog
sudo slapadd -F /etc/ldap/slapd.d -n 0 -l /data/backups/ldap/
T
I
M
E
S
T
A
M
P
/
c
o
n
f
i
g
.
l
d
i
f
s
u
d
o
s
l
a
p
a
d
d
−
F
/
e
t
c
/
l
d
a
p
/
s
l
a
p
d
.
d
−
n
1
−
l
/
d
a
t
a
/
b
a
c
k
u
p
s
/
l
d
a
p
/
{TIMESTAMP}/config.ldif sudo slapadd -F /etc/ldap/slapd.d -n 1 -l /data/backups/ldap/
TIMESTAMP/config.ldifsudoslapadd−F/etc/ldap/slapd.d−n1−l/data/backups/ldap/{TIMESTAMP}/domain.com.ldif
sudo slapadd -F /etc/ldap/slapd.d -n 2 -l /data/backups/ldap/${TIMESTAMP}/access.ldif
sudo chown -R openldap:openldap /etc/ldap/slapd.d/
sudo chown -R openldap:openldap /var/lib/ldap/
sudo systemctl start slapd.service
参考脚本文件:GitHub - alexanderjackson/ldap-backup-and-restoreHow To Backup and Restore OpenLDAP - Tyler’s Guides
ldap3 client example
ldap3-client-example
ldapPublicKey
1、配置文件
cat openssh-lpk.ldif
LDAP SSH Public Key schema
Source: https://serverfault.com/questions/653792/ssh-key-authentication-using-ldap
Homepage: https://github.com/AndriiGrytsenko/openssh-ldap-publickey
dn: cn=openssh-lpk,cn=schema,cn=config
objectClass: olcSchemaConfig
cn: openssh-lpk
olcAttributeTypes: ( 1.3.6.1.4.1.24552.500.1.1.1.13 NAME ‘sshPublicKey’
DESC ‘MANDATORY: OpenSSH Public key’
EQUALITY octetStringMatch
SYNTAX 1.3.6.1.4.1.1466.115.121.1.40 )
olcObjectClasses: ( 1.3.6.1.4.1.24552.500.1.1.2.0 NAME ‘ldapPublicKey’
DESC ‘MANDATORY: OpenSSH LPK objectclass’
SUP top AUXILIARY
MAY ( sshPublicKey $ uid )
)
2、导入配置信息
ldapadd -Y EXTERNAL -H ldapi:/// -f openssh-lpk.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry “cn=openssh-lpk,cn=schema,cn=config”
此时,可以使用sshPublicKey属性进行user登录验证.
LDAP server端配置sudo
cat exports.ldif
dn: dc=shuke,dc=com
objectClass: top
objectClass: domain
dc: shuke
dn: ou=stuff,dc=shuke,dc=com
description:: 5ZGY5bel
ou: stuff
objectClass: top
objectClass: organizationalUnit
objectClass: labeledURIObject
dn: ou=groups,dc=shuke,dc=com
description:: 57uE
ou: groups
objectClass: top
objectClass: organizationalUnit
dn: ou=department,dc=shuke,dc=com
description:: 6YOo6Zeo
ou: department
objectClass: organizationalUnit
objectClass: top
dn: cn=sre,ou=groups,dc=shuke,dc=com
description: sre group
cn: sre
objectClass: posixGroup
objectClass: top
gidNumber: 5000
memberUid: uid=wangwu,ou=stuff,dc=shuke,dc=com
memberUid: uid=guoliman,ou=stuff,dc=shuke,dc=com
memberUid: uid=fengfengzhao,ou=stuff,dc=shuke,dc=com
memberUid: uid=shuke,ou=stuff,dc=shuke,dc=com
memberUid: uid=mazengsui,ou=stuff,dc=shuke,dc=com
dn: uid=fengfengzhao,ou=stuff,dc=shuke,dc=com
uid: fzhao
uid: fengfengzhao
sshPublicKey: ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDRMPwi6Q/Zcb1N6sWnFf5/Ew
TvmpfEZyRI0XUnCtZKWEPPCbgjPfQ2ZKYPCsmfvqA6uaVolBzLM04BZEbbeHmC1mB3kpvOXmZtH
7iAt22khCyS5A/jzaE9lwgyGzO/mhJQ83EIBt4MtO/UgGyk1EAyQH0gAGgfqQ2Htyp44wxul0pl
pbcmTElQQUZiLMNUspKS4i3BDGSWwu+Y2q7h3jTfgMpyLweqnt4vuUwhaGouP1P6q7M7HCRMKbX
L5MH3K0sz5G1WpiqsXxtHbFgQZiniOwO/EaUvca9MQRwY5zeMxkUJ38HlpvRjp16HevpuLqvUqy
2Uw2migJNW52ZubtGlOzc8mJh/qSLUTV1238Z6dgR6nELa260RnsPNp3Utb7HkhY6WZSRYxNxjv
sGWDIKMczPHbfhHf0iuuxGt96dPhpM6V8UH0zbPUEL/6+VRTMThflewLA+2/9J5VzG+Ugqm3vU3
jVZxgMqqFlJmI9nfw0/H+1H+6AEU556fNTqBFQAEQDNKltv4hv/YLmpcYh7lSJU9TjHaHCXpbLD
aAQPLcNBFzA1lL3KU+rx1xwww4Tbn77qU/JmSACLP/oczrLvb+kLjO2dyi0WfEjqgeIn83OPPv4
CtTMlpHZj2kP2L7Sw8RZHXurL1wLqBnVrCGzHcC2huB9jn3QUedWjVqdA6Sw== shuke@shukes
-mbp
loginShell: /bin/bash
homeDirectory: /home/fzhao
sn: zhao
uidNumber: 1110
cn: fengfengzhao
cn: uid
givenName: fengfeng
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: top
objectClass: ldapPublicKey
objectClass: shadowAccount
userPassword: {SSHA}zcDVAK2aCjni6gjm1YIX8KfmgCYoUgmY
gidNumber: 5000
dn: uid=shuke,ou=stuff,dc=shuke,dc=com
uid: shuke
sshPublicKey: ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDRMPwi6Q/Zcb1N6sWnFf5/Ew
TvmpfEZyRI0XUnCtZKWEPPCbgjPfQ2ZKYPCsmfvqA6uaVolBzLM04BZEbbeHmC1mB3kpvOXmZtH
7iAt22khCyS5A/jzaE9lwgyGzO/mhJQ83EIBt4MtO/UgGyk1EAyQH0gAGgfqQ2Htyp44wxul0pl
pbcmTElQQUZiLMNUspKS4i3BDGSWwu+Y2q7h3jTfgMpyLweqnt4vuUwhaGouP1P6q7M7HCRMKbX
L5MH3K0sz5G1WpiqsXxtHbFgQZiniOwO/EaUvca9MQRwY5zeMxkUJ38HlpvRjp16HevpuLqvUqy
2Uw2migJNW52ZubtGlOzc8mJh/qSLUTV1238Z6dgR6nELa260RnsPNp3Utb7HkhY6WZSRYxNxjv
sGWDIKMczPHbfhHf0iuuxGt96dPhpM6V8UH0zbPUEL/6+VRTMThflewLA+2/9J5VzG+Ugqm3vU3
jVZxgMqqFlJmI9nfw0/H+1H+6AEU556fNTqBFQAEQDNKltv4hv/YLmpcYh7lSJU9TjHaHCXpbLD
aAQPLcNBFzA1lL3KU+rx1xwww4Tbn77qU/JmSACLP/oczrLvb+kLjO2dyi0WfEjqgeIn83OPPv4
CtTMlpHZj2kP2L7Sw8RZHXurL1wLqBnVrCGzHcC2huB9jn3QUedWjVqdA6Sw== shuke@shukes
-mbp
loginShell: /bin/bash
homeDirectory: /home/shuke
sn: ke
cn: shuke
uidNumber: 1100
givenName: shu
userPassword: {MD5}4QrcOUm6Wau+VuBX8g+IPg==
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
objectClass: person
objectClass: ldapPublicKey
gidNumber: 5000
dn: uid=zhangsan,ou=stuff,dc=shuke,dc=com
displayName: zhangchao
shadowMax: 99999
shadowWarning: 7
cn: zhangchao
userPassword: {SSHA}8Bh8j9CCMOAk/73q700DYSnO02WAkMEveP8CeA==
gidNumber: 5000
uid: orange1
uid: zhangsan
sshPublicKey: ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQD0lrkO0xCQnkheasZ1oLtkNR
2oMhpUM/51V7ULfm6YvUMUyFdv04zZMfF/eCFYVTtHSu95MJIZ5HYS23Vn0J9qsjWMh3KvPqNM0
dTFbmj0Uq45ndaq8pRxwU/C7hGyAIR7mFyfkflNNNAa/MwGP7iI8hpdW1r4+mF2+lV6QXJFQxJT
iqZhDu0lxwx2D/oXQsv8P1S/2WOOtoNeLSx0onaPhi/+Veq9d+XZtkMaP6sXg1vNS3+oCxLosKG
8at8JBTGnHRBqPF3yoFAZwhpDcR/ti5/cE6sKwIcIka4eVxb/QSQRol1WLNdrOs5KRXrrPgfF1e
aoIB0vg14DGJB4kuth shuke@MacBooKPro
loginShell: /bin/bash
mail: zhangchao@pyg168.com
description: zhangchao’s Home
homeDirectory: /home/zhangchao
shadowMin: 0
sn: zhangchao
uidNumber: 1102
givenName: zhangchao
objectClass: top
objectClass: shadowAccount
objectClass: posixAccount
objectClass: inetOrgPerson
objectClass: ldapPublicKey
mobile: 136868866688
dn: uid=mazengsui,ou=stuff,dc=shuke,dc=com
displayName: mazengsui
shadowMax: 99999
shadowWarning: 7
cn: uid
userPassword: {SSHA}CLbC3r65e+W5aNBu8P1c+Nlx1yoSRGLw
gidNumber: 5000
uid: mazengsui
sshPublicKey: ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDRMPwi6Q/Zcb1N6sWnFf5/Ew
TvmpfEZyRI0XUnCtZKWEPPCbgjPfQ2ZKYPCsmfvqA6uaVolBzLM04BZEbbeHmC1mB3kpvOXmZtH
7iAt22khCyS5A/jzaE9lwgyGzO/mhJQ83EIBt4MtO/UgGyk1EAyQH0gAGgfqQ2Htyp44wxul0pl
pbcmTElQQUZiLMNUspKS4i3BDGSWwu+Y2q7h3jTfgMpyLweqnt4vuUwhaGouP1P6q7M7HCRMKbX
L5MH3K0sz5G1WpiqsXxtHbFgQZiniOwO/EaUvca9MQRwY5zeMxkUJ38HlpvRjp16HevpuLqvUqy
2Uw2migJNW52ZubtGlOzc8mJh/qSLUTV1238Z6dgR6nELa260RnsPNp3Utb7HkhY6WZSRYxNxjv
sGWDIKMczPHbfhHf0iuuxGt96dPhpM6V8UH0zbPUEL/6+VRTMThflewLA+2/9J5VzG+Ugqm3vU3
jVZxgMqqFlJmI9nfw0/H+1H+6AEU556fNTqBFQAEQDNKltv4hv/YLmpcYh7lSJU9TjHaHCXpbLD
aAQPLcNBFzA1lL3KU+rx1xwww4Tbn77qU/JmSACLP/oczrLvb+kLjO2dyi0WfEjqgeIn83OPPv4
CtTMlpHZj2kP2L7Sw8RZHXurL1wLqBnVrCGzHcC2huB9jn3QUedWjVqdA6Sw== shuke@shukes
-mbp
loginShell: /bin/bash
mail: mazengsui@pyg168.com
description: mazengsui’s Home
homeDirectory: /home/mazengsui
shadowMin: 0
sn: mazengsui
uidNumber: 1104
givenName: mazengsui
objectClass: top
objectClass: shadowAccount
objectClass: posixAccount
objectClass: inetOrgPerson
objectClass: ldapPublicKey
mobile: 136868866688
dn: uid=guoliman,ou=stuff,dc=shuke,dc=com
displayName: guoliman
shadowMax: 99999
shadowWarning: 7
cn: uid
userPassword: {SSHA}IKP3AfbrX0acBejnXL00AlafrRCFDU9I8z6erg==
gidNumber: 5000
uid: guoliman
sshPublicKey: ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDRMPwi6Q/Zcb1N6sWnFf5/Ew
TvmpfEZyRI0XUnCtZKWEPPCbgjPfQ2ZKYPCsmfvqA6uaVolBzLM04BZEbbeHmC1mB3kpvOXmZtH
7iAt22khCyS5A/jzaE9lwgyGzO/mhJQ83EIBt4MtO/UgGyk1EAyQH0gAGgfqQ2Htyp44wxul0pl
pbcmTElQQUZiLMNUspKS4i3BDGSWwu+Y2q7h3jTfgMpyLweqnt4vuUwhaGouP1P6q7M7HCRMKbX
L5MH3K0sz5G1WpiqsXxtHbFgQZiniOwO/EaUvca9MQRwY5zeMxkUJ38HlpvRjp16HevpuLqvUqy
2Uw2migJNW52ZubtGlOzc8mJh/qSLUTV1238Z6dgR6nELa260RnsPNp3Utb7HkhY6WZSRYxNxjv
sGWDIKMczPHbfhHf0iuuxGt96dPhpM6V8UH0zbPUEL/6+VRTMThflewLA+2/9J5VzG+Ugqm3vU3
jVZxgMqqFlJmI9nfw0/H+1H+6AEU556fNTqBFQAEQDNKltv4hv/YLmpcYh7lSJU9TjHaHCXpbLD
aAQPLcNBFzA1lL3KU+rx1xwww4Tbn77qU/JmSACLP/oczrLvb+kLjO2dyi0WfEjqgeIn83OPPv4
CtTMlpHZj2kP2L7Sw8RZHXurL1wLqBnVrCGzHcC2huB9jn3QUedWjVqdA6Sw== shuke@shukes
-mbp
loginShell: /bin/bash
mail: guoliman@pyg168.com
description: guoliman’s Home
homeDirectory: /home/guoliman
shadowMin: 0
sn: guoliman
uidNumber: 1106
givenName: guoliman
objectClass: top
objectClass: shadowAccount
objectClass: posixAccount
objectClass: inetOrgPerson
objectClass: ldapPublicKey
mobile: 136868866688
dn: uid=chenghuikai,ou=stuff,dc=shuke,dc=com
displayName: chenghuikai
shadowMax: 99999
shadowWarning: 7
网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。
需要这份系统化的资料的朋友,可以添加V获取:vip1024b (备注软件测试)

一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!
CLP/oczrLvb+kLjO2dyi0WfEjqgeIn83OPPv4
CtTMlpHZj2kP2L7Sw8RZHXurL1wLqBnVrCGzHcC2huB9jn3QUedWjVqdA6Sw== shuke@shukes
-mbp
loginShell: /bin/bash
mail: guoliman@pyg168.com
description: guoliman’s Home
homeDirectory: /home/guoliman
shadowMin: 0
sn: guoliman
uidNumber: 1106
givenName: guoliman
objectClass: top
objectClass: shadowAccount
objectClass: posixAccount
objectClass: inetOrgPerson
objectClass: ldapPublicKey
mobile: 136868866688
dn: uid=chenghuikai,ou=stuff,dc=shuke,dc=com
displayName: chenghuikai
shadowMax: 99999
shadowWarning: 7
网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。
需要这份系统化的资料的朋友,可以添加V获取:vip1024b (备注软件测试)
[外链图片转存中…(img-F9kxy6Z7-1713420181656)]
一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!






















 6118
6118

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








