目录
概要
基于路由的VPN是一种配置,在两个端点之间创建IPsec VPN隧道并配置隧道路由,通过目标IP地址确定哪些流量通过隧道转发。
应用场景
- 两个LAN之间存在重叠的子网或IP地址
- 网络中使用的是中心辐射型VPN拓扑,需要辐射式流量
- 需要主VPN和备用VPN
- VPN中运行的是动态路由协议
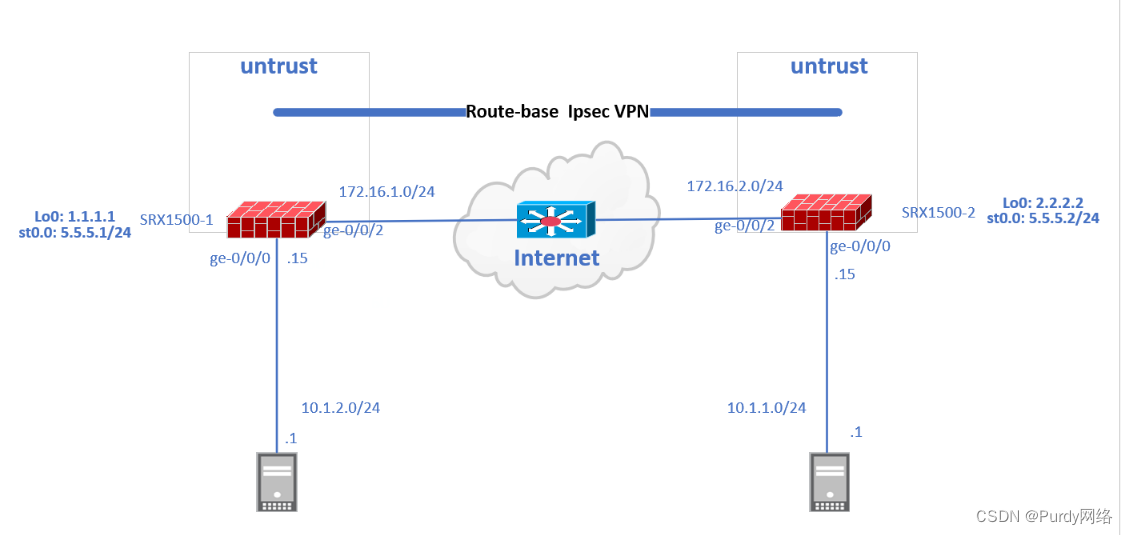
网络拓扑
配置
- SRX1500-1
set system host-name SRX1500-1
set system time-zone Asia/Shanghai
set security ike proposal Ike_Phase1_Proposal authentication-method pre-shared-keys
set security ike policy Ike_Phase1_Policy mode main
set security ike policy Ike_Phase1_Policy proposals Ike_Phase1_Proposal
set security ike policy Ike_Phase1_Policy pre-shared-key ascii-text "$9$/pPM9pBIRSleWB17-ws4o"
set security ike gateway Ike_Gateway ike-policy Ike_Phase1_Policy
set security ike gateway Ike_Gateway address 172.16.2.1
set security ike gateway Ike_Gateway external-interface ge-0/0/2
set security ipsec proposal Ipsec_Phase2_Proposal
set security ipsec policy Ipsec_Phase_Policy proposals Ipsec_Phase2_Proposal
set security ipsec vpn Ipsec_VPN bind-interface st0.0
set security ipsec vpn Ipsec_VPN ike gateway Ike_Gateway
set security ipsec vpn Ipsec_VPN ike ipsec-policy Ipsec_Phase_Policy
set security ipsec vpn Ipsec_VPN establish-tunnels immediately
set security address-book Host1 address 10.1.2.0/24 10.1.2.0/24
set security address-book Host1 attach zone trust
set security address-book VPN_Address address 10.1.1.0/24 10.1.1.0/24
set security address-book VPN_Address attach zone VPN
set security flow tcp-mss ipsec-vpn mss 1350
set security policies from-zone trust to-zone VPN policy VPN-OUT match source-address 10.1.2.0/24
set security policies from-zone trust to-zone VPN policy VPN-OUT match destination-address 10.1.1.0/24
set security policies from-zone trust to-zone VPN policy VPN-OUT match application any
set security policies from-zone trust to-zone VPN policy VPN-OUT then permit
set security policies from-zone VPN to-zone trust policy VPN_IN match source-address 10.1.1.0/24
set security policies from-zone VPN to-zone trust policy VPN_IN match destination-address 10.1.2.0/24
set security policies from-zone VPN to-zone trust policy VPN_IN match application any
set security policies from-zone VPN to-zone trust policy VPN_IN then permit
set security zones security-zone trust host-inbound-traffic system-services ping
set security zones security-zone trust interfaces ge-0/0/0.0
set security zones security-zone untrust host-inbound-traffic system-services ike
set security zones security-zone untrust host-inbound-traffic system-services ping
set security zones security-zone untrust interfaces ge-0/0/2.0
set security zones security-zone VPN host-inbound-traffic system-services ping
set security zones security-zone VPN interfaces st0.0
set interfaces ge-0/0/0 unit 0 family inet address 10.1.2.15/24
set interfaces ge-0/0/2 unit 0 family inet address 172.16.1.1/24
set interfaces lo0 unit 0 family inet address 1.1.1.1/32
set interfaces st0 unit 0 family inet address 5.5.5.1/24
set routing-options static route 0.0.0.0/0 next-hop 172.16.1.2
set routing-options static route 10.1.1.0/24 next-hop st0.0
- SRX1500-2
set system host-name SRX1500-2
set security ike proposal Ike_Phase1_Proposal authentication-method pre-shared-keys
set security ike policy Ike_Phase1_Policy mode main
set security ike policy Ike_Phase1_Policy proposals Ike_Phase1_Proposal
set security ike policy Ike_Phase1_Policy pre-shared-key ascii-text "$9$2qgJDiHm5T3DjCtOBEh"
set security ike gateway Ike_Gateway ike-policy Ike_Phase1_Policy
set security ike gateway Ike_Gateway address 172.16.1.1
set security ike gateway Ike_Gateway external-interface ge-0/0/2
set security ipsec proposal Ipsec_Phase2_Proposal
set security ipsec policy Ipsec_Phase2_Policy proposals Ipsec_Phase2_Proposal
set security ipsec vpn Ipsec_VPN bind-interface st0.0
set security ipsec vpn Ipsec_VPN ike gateway Ike_Gateway
set security ipsec vpn Ipsec_VPN ike ipsec-policy Ipsec_Phase2_Policy
set security ipsec vpn Ipsec_VPN establish-tunnels immediately
set security address-book Host2 address 10.1.1.0/24 10.1.1.0/24
set security address-book Host2 attach zone trust
set security address-book VPN_Address address 10.1.2.0/24 10.1.2.0/24
set security address-book VPN_Address attach zone VPN
set security flow tcp-mss ipsec-vpn mss 1350
set security policies from-zone trust to-zone VPN policy VPN-OUT match source-address 10.1.1.0/24
set security policies from-zone trust to-zone VPN policy VPN-OUT match destination-address 10.1.2.0/24
set security policies from-zone trust to-zone VPN policy VPN-OUT match application any
set security policies from-zone trust to-zone VPN policy VPN-OUT then permit
set security policies from-zone VPN to-zone trust policy VPN-IN match source-address 10.1.2.0/24
set security policies from-zone VPN to-zone trust policy VPN-IN match destination-address 10.1.1.0/24
set security policies from-zone VPN to-zone trust policy VPN-IN match application any
set security policies from-zone VPN to-zone trust policy VPN-IN then permit
set security zones security-zone trust host-inbound-traffic system-services all
set security zones security-zone trust interfaces ge-0/0/0.0
set security zones security-zone untrust host-inbound-traffic system-services ping
set security zones security-zone untrust host-inbound-traffic system-services ike
set security zones security-zone untrust interfaces ge-0/0/2.0
set security zones security-zone VPN host-inbound-traffic system-services ping
set security zones security-zone VPN interfaces st0.0
set interfaces ge-0/0/0 unit 0 family inet address 10.1.1.15/24
set interfaces ge-0/0/2 unit 0 family inet address 172.16.2.1/24
set interfaces lo0 unit 0 family inet address 2.2.2.2/32
set interfaces st0 unit 0 family inet address 5.5.5.2/24
set routing-options static route 0.0.0.0/0 next-hop 172.16.2.2
set routing-options static route 10.1.2.0/24 next-hop st0.0
- Internet
set system host-name Internet
set chassis alarm management-ethernet link-down ignore
set interfaces ge-0/0/0 unit 0 family inet address 172.16.1.2/24
set interfaces ge-0/0/46 unit 0 family inet address 172.16.2.2/24
小结
- 与基于策略的VPN不同,对于基于路由的VPN,策略是指目标地址,而非VPN隧道。
- 基于路由的VPN允许在多个远程站点之间的分支之间进行路由,易于配置、监控和故障排除。
- TCP-MSS作为TCP三次握手的一部分协商,并限制TCP分段的最大大小,以便更好地适应网络上的MTU限制。
























 597
597

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








