BeginCTF-Re-xor
z3模拟运算代码
from z3 import *
flag = [BitVec('u%d'%i,8) for i in range(0,32)]
table1 = "63290794207715587679621386735000"
byte1 = "6329079420771558"
byte2 = "7679621386735000"
table = "41803873625901363092606632787947"
byte11 = "4180387362590136"
byte22 = "3092606632787947"
enc = "`agh{^bvuwTooahlYocPtmyiijj|ek\'p"
enc1 = [0x60, 0x61, 0x67, 0x68, 0x7B, 0x5E, 0x62, 0x76, 0x75, 0x77, 0x54, 0x6F, 0x6F, 0x61, 0x68, 0x6C, 0x59, 0x6F, 0x63, 0x50, 0x74, 0x6D, 0x79, 0x69, 0x69, 0x6A, 0x6A, 0x7C, 0x65, 0x6B, 0x27, 0x70]
print(enc)
tmp1 = [0]*16
tmp2 = [0]*16
tmp11 = [0]*16
tmp22 = [0]*32
tmp22_0 = [0]*16
tmp22_1 = [0]*16
byte_14001D7C0 = [0]*32
'''
赋值
'''
for i in range(16):
tmp1[i] = flag[i]
for j in range(16):
tmp2[j] = flag[j+16]
'''
xor
'''
for i in range(16):
tmp1[i]^= ord(byte2[i])
tmp1[i] = tmp1[i] & 0xff
for i in range(16):
tmp2[i]^= ord(byte1[i])
tmp2[i] = tmp2[i]&0xff
for i in range(16):
tmp1[i]^= ord(byte1[i])
tmp1[i] = tmp1[i] & 0xff
for i in range(16):
tmp2[i]^= ord(byte2[i])
'''
xor_re
'''
for i in range(1,16):
tmp1[i]^=ord(byte2[16-i])
for i in range(1,16):
tmp2[i]^=ord(byte1[16-i])
for i in range(1,16):
tmp1[i]^=ord(byte1[16-i])
for i in range(1,16):
tmp2[i]^=ord(byte2[16-i])
'''
fuzhi2
'''
for i in range(16):
tmp22[i] = tmp2[i]
for i in range(16):
tmp22[i+16] = tmp1[i]
'''
'''
for i in range(16):
tmp22_0[i] = tmp22[i]
for i in range(16):
tmp22_1[i] = tmp22[i+16]
'''
xor
'''
for i in range(16):
tmp22_0[i] ^= byte22[i]
for i in range(16):
tmp22_1[i] ^= byte11[i]
'''
'''
for i in range(16):
tmp22_0[i] ^= byte11[i]
for i in range(16):
tmp22_1[i] ^= byte22[i]
for i in range(1,16):
tmp22_0[i] ^= byte22[16 - i]
for i in range(1,16):
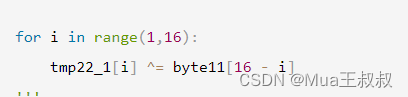
tmp22_1[i] ^= byte11[16 - i]
'''
'''
for i in range(1,16):
tmp22_0[i] ^= byte11[16 - i]
for i in range(1,16):
tmp22_1[i] ^= byte22[16 - i]
for i in range(16):
byte_14001D7C0[i] = tmp22_1[i]
for i in range(16):
byte_14001D7C0[i + 16] = tmp22_0[i]
s = Solver()
for i in range(32):
s.add(byte_14001D7C0[i]==enc1[i])
print(s.check())
result = s.model()
print(result)
flag1 = ''
for i in range(0,32):
flag1 += chr(result[flag[i]].as_long().real)
print(flag1)
注意下面基础的下标,与伪代码要稍加改动。这地方卡了好久(菜鸡崩溃)。




















 721
721











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








