概括:
内容包括:NDS各配置文件解析、正解区域配置及测试、反向区域配置及测试 、使用通配符做泛域名解析、配置为客户机Windows的dns服务器提供解析功能
一、安装bind及相关配置文件解析
(1)、安装bind
[root@field named]# yum install -y bind
查看bind安装情况
[root@fieldnamed]# rpm -ql bind| less
[root@field ~]# cd /var/named
(2)、最上层.(root)数据库文件:
该配置文件会时时更新,可以到专门的ftp站点下载,在这里我选择保持默认,也就是直接使用本系统提供的name.ca文件,可以通过编辑“/var/named/chroot/var/named/named.ca”文件查看相关配置内容;
[root@field named]# ls
data dynamic named.ca named.empty named.localhost named.loopback slaves
#name.ca文件,可以通过编辑包含了Internet的根服务器名字和地址,DNS接到客户端主机的查询请求时,如果在Cache中找不到相应的数据,就会通过根服务器进行逐级查询
[root@field named]# cat named.ca
; This file holds the information on rootname servers needed to
……;
. 3600000 NS M.ROOT-SERVERS.NET.
M.ROOT-SERVERS.NET. 3600000 A 202.12.27.33
M.ROOT-SERVERS.NET. 3600000 AAAA 2001:dc3::35
; End of file
(3)、默认配置/var/named/named.localhost
[root@field named]# cat named.loopback
$TTL 1D
@ IN SOA @ rname.invalid. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS @
A 127.0.0.1
AAAA ::1
PTR localhost.
(4)、默认配置/var/named/named.localhost
[root@field named]# cat named.localhost
$TTL 1D
@ IN SOA @ rname.invalid. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS @
A 127.0.0.1
AAAA ::1
(5)、启动named服务器并查看监听端口
[root@field ~]# service namedstart
Generating /etc/rndc.key:[确定]
启动 named:[确定]
[root@field ~]# ss -tnlup | grep :53
tcp 0 3 ::1:53 :::* users:(("named",13467,21))
tcp 0 3 127.0.0.1:53 *:* users:(("named",13467,20))
(6)、主配置文件:
全局配置:options{}
日志子系统配置:logging{}
区域定义:本机能够为哪些zone进行解析,就要定义哪些zone;
zone"ZONE_NAME" IN {}
缓存名称服务器的配置:监听外部地址即可
dnssec:建议测试时关闭dnssec
[root@field ~]# vim/etc/named.conf
// named.conf
// Provided by Red Hat bindpackage to configure the ISC BIND named(8) DNS
// server as a caching onlynameserver (as a localhost DNS resolver only).
//
// See/usr/share/doc/bind*/sample/ for example named configuration files.
//
options {
listen-on port 53 { 127.0.0.1;}; //ipv4监听端口
listen-on-v6 port 53 {::1; }; //ipv6监听端口
directory "/var/named"; //制定装载zone区域文件的目录
dump-file "/var/named/data/cache_dump.db"; //cache缓存数据目录
statistics-file"/var/named/data/named_stats.txt";
memstatistics-file"/var/named/data/named_mem_stats.txt";
allow-query { localhost; }; //允许访问列表
recursion yes;
dnssec-enable yes; //是否启用DNSSEC支持
dnssec-validationyes; //是否进行DNSSEC确认开关,默认为no
/* Path to ISC DLV key */
bindkeys-file"/etc/named.iscdlv.key";
managed-keys-directory"/var/named/dynamic";
};
logging {
channel default_debug {
file"data/named.run";
severity dynamic;
};
};
zone "." IN { // "."代表根区域,所有解析
type hint; //根区域的类型就为hint
file"named.ca"; //指定zone文件,默认已经生成
};
include "/etc/named.rfc1912.zones";
include"/etc/named.root.key";
注意:任何服务程序如果期望其能够通过网络被其他主机访问,至少应该监听在一个能与外部主机通信的IP地址上:
[root@field ~]# service namedstart
Generating /etc/rndc.key:[确定]
启动 named:[确定]
[root@field ~]# ss -tnlup | grep :53
tcp 0 3 ::1:53 :::* users:(("named",13467,21))
tcp 0 3 127.0.0.1:53 *:* users:(("named",13467,20))
(7)、主DNS名称服务器:
1)、在主配置文件中定义区域
zone "ZONE_NAME" IN {
type {master|slave|hint|forward};
file "ZONE_NAME.zone";
}
}
2)、定义正解区域解析库文件
出现的内容:
宏定义
资源记录
示例:
$TTL 86400
$ORIGIN field.com
@ IN SOA ns1.field.com.admin.field.com (
2017111701
1H
5M
7D
1D )
IN NS ns1
IN NS ns2
IN MX 10 mx1
IN MX 20 mx2
ns1 IN A 192.168.88.131
ns2 IN A 192.168.88.130
mx1 IN A 192.168.88.132
mx2 IN A 192.168.88.133
www IN A 192.168.88.131
ftp IN CNAME www
3)、定义反解区域:
区域名称:网络地址反写 .in-addr.arpa.
192.168.88.--> 88.168.192.in-addr.arpa.
定义区域
zone "ZONE_NAME" IN {
type {master|slave|forward};
file "网络地址.zone";
};
定义反解区域解析库文件
注意:不需要MX和A,以及AAAA记录;以PTR记录为主
示例:
$TTL 86400
$ORIGIN 88.168.192.in-addr.arpa.
@ IN SOA ns1.field.com. admin.field.com. (
2017111701
1H
5M
7D
1D )
IN NS ns1.field.com.
IN NS ns2.field.com.
131 IN PTR ns1.field.com.
131 IN PTR www.field.com.
131 IN PTR mx1.field.com.
130 IN PTR mx2.field.com.
(8)、测试命令:dig的使用
dig [-t type] name [@SERVER] [query options]
dig用于测试dns系统,因此,不会查询host文件进行解析
查询选项:
+[no]trace:跟踪解析过程
+[no]recurse:进行递归解析
测试反向解析:
dig -x IP @SERVER
模拟区域传送:
dig -t axfr ZONE_NAME @SERVER
例如: dig -t axfr field.com @192.168.88.131
dig -t axfr88.168.192.in-addr.arpa @192.168.88.131
host命令:
host [-t type] name [SERVER]
nslookup命令:
nslookup [-option] [name | -] [server]
交互式模式;
nslookup>
server IP:指明使用哪个DNS server进行查询;
set q=RR_TYPE:指明查询的资源记录类型;
NAME:要查询的名称
二、正解区域配置及测试
(1)、全局配置:options{}
日志子系统配置:logging{}
区域定义:本机能够为哪些zone进行解析,就要定义哪些zone;
zone "ZONE_NAME" IN {}
注意:任何服务程序如果期望其能够通过网络被其他主机访问,
至少应该监听在一个能与外部主机通信的IP地址上
[root@field ~]# service namedstart
Generating /etc/rndc.key:[确定]
启动 named:[确定]
[root@field ~]# ss -tnlup | grep :53
tcp 0 3 ::1:53 :::* users:(("named",13467,21))
tcp 0 3 127.0.0.1:53 *:* users:(("named",13467,20))
[root@field etc]# vim/etc/named.conf
// named.conf
// Provided by Red Hat bindpackage to configure the ISC BIND named(8) DNS
// server as a caching onlynameserver (as a localhost DNS resolver only).
// See/usr/share/doc/bind*/sample/ for example named configuration files.
options {
listen-on port 53 { 192.168.88.131;127.0.0.1; }; //ipv4监听地址
// listen-on-v6 port 53 {::1; }; 关闭ipv6 监听端口
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file"/var/named/data/named_stats.txt";
memstatistics-file"/var/named/data/named_mem_stats.txt";
allow-query { localhost; };
recursion yes;
// dnssec-enable yes;建议测试时关闭dnssec
// dnssec-validation yes;
/* Path to ISC DLV key*/
// bindkeys-file"/etc/named.iscdlv.key";
// managed-keys-directory"/var/named/dynamic";
};
logging {
channel default_debug {
file"data/named.run";
severity dynamic;
};
};
zone "." IN {
type hint;
file "named.ca"; //最上层 .(root)数据库文件
};
include"/etc/named.rfc1912.zones";
include"/etc/named.root.key";
(2)、在主配置文件中定义区域
zone "ZONE_NAME" IN {
type {master|slave|hint|forward};
file "ZONE_NAME.zone";
}
}
[root@field etc]# vim /etc/named.rfc1912.zones
// named.rfc1912.zones:
// Provided by Red Hatcaching-nameserver package
// ISC BIND named zoneconfiguration for zones recommended by
// RFC 1912 section 4.1 :localhost TLDs and address zones
// and http://www.ietf.org/internet-drafts/draft-ietf-dnsop-default-local-zones-02.txt
// (c)2007 R W Franks
//
// See/usr/share/doc/bind*/sample/ for example named configuration files.
//
file "field.com.zone";
zone"localhost.localdomain" IN {
type master;
file "named.localhost";
allow-update { none; };
};
zone "localhost" IN{
type master;
file "named.localhost";
allow-update { none; };
};
zone "1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.ip6.arpa"IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone"1.0.0.127.in-addr.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone"0.in-addr.arpa" IN {
type master;
file "named.empty";
allow-update { none; };
};
zone "field.com" IN { //新建的zone名称
type master; //类型为主dns
file"field.com.zone"; //zone file的文件
};
~
"named.rfc1912.zones"47L, 1009C 已写入
[root@www named]# named-checkconf
//查看主配置文件是否有语法错误
(3)、定义区域解析库文件
[root@field etc]# cd/var/named
[root@field named]# vimfield.com.zone
$TTL 86400
$ORIGIN field.com.
@ IN SOA ns1.field.com. admin.field.com (
2017111701
1H
5M
7D
1D )
IN NS ns1
IN NS ns2
IN MX 10 mx1
IN MX 20 mx2
ns1 IN A 192.168.88.131
ns2 IN A 192.168.88.130
mx1 IN A 192.168.88.132
mx2 IN A 192.168.88.133
www IN A 192.168.88.131
ftp IN CNAME www
~
"field.com.zone"18L, 361C 已写入
[root@field named]# named-checkzone "field.com"/var/named/field.com.zone
zone field.com/IN: loadedserial 2017111701
OK
//查看定义的区域解析库文件语法是否有错
[root@field named]# ps aux |grep named
named 16254 0.0 1.2 180052 11136 ? Ssl 15:48 0:00 /usr/sbin/named -unamed
root 17234 0.0 0.0 103268 864 pts/0 S+ 16:44 0:00 grep named
[root@field named]# ll/etc/named.conf -l
-rw-r-----. 1 root named 101011月 17 15:48 /etc/named.conf
(4)、基于安全性考虑,修改区域解析库文件访问权限为640并将named加入属组。
[root@field named]# ll
总用量 32
drwxrwx---. 2 named named4096 11月 17 13:26 data
drwxrwx---. 2 named named4096 11月 17 13:27 dynamic
-rw-r--r--. 1 root root 361 11月 17 16:42 field.com.zone
-rw-r-----. 1 root named 3289 4月 11 2017 named.ca
-rw-r-----. 1 root named 152 12月 15 2009 named.empty
-rw-r-----. 1 root named 152 6月 21 2007 named.localhost
-rw-r-----. 1 root named 168 12月 15 2009 named.loopback
drwxrwx---. 2 named named4096 7月 5 17:55 slaves
[root@field named]# id named
uid=25(named) gid=25(named) 组=25(named)
[root@field named]# chmod 640 field.com.zone
[root@field named]# ll
总用量 32
drwxrwx---. 2 named named4096 11月 17 13:26 data
drwxrwx---. 2 named named4096 11月 17 13:27 dynamic
-rw-r-----. 1root root 361 11月 17 16:42field.com.zone
-rw-r-----. 1 root named 3289 4月 11 2017 named.ca
-rw-r-----. 1 root named 152 12月 15 2009 named.empty
-rw-r-----. 1 root named 152 6月 21 2007 named.localhost
-rw-r-----. 1 root named 168 12月 15 2009 named.loopback
drwxrwx---. 2 named named4096 7月 5 17:55 slaves
[root@field named]# chown :named field.com.zone
[root@field named]# ll
总用量 32
drwxrwx---. 2 named named4096 11月 17 13:26 data
drwxrwx---. 2 named named4096 11月 17 13:27 dynamic
-rw-r-----. 1root named 361 11月 17 16:42field.com.zone
-rw-r-----. 1 root named 3289 4月 11 2017 named.ca
-rw-r-----. 1 root named 152 12月 15 2009 named.empty
-rw-r-----. 1 root named 152 6月 21 2007 named.localhost
-rw-r-----. 1 root named 168 12月 15 2009 named.loopback
drwxrwx---. 2 named named4096 7月 5 17:55 slaves
[root@field named]# servicenamed restart
停止 named:.[确定]
启动 named:[确定]
//查看bind运行状态
[root@field named]# rndc status
version: 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.4
CPUs found: 3
worker threads: 3
number of zones: 20
debug level: 0
xfers running: 0
xfers deferred: 0
soa queries in progress: 0
query logging is OFF
recursive clients: 0/0/1000
tcp clients: 0/100
server is up and running
(5)、正解测试及常用测试命令使用
dig的命令:
dig [-t type] name [@SERVER] [query options]
dig用于测试dns系统,因此,不会查询host文件进行解析
查询选项:
+[no]trace:跟踪解析过程
+[no]recurse:进行递归解析
host命令:
host [-t type] name [SERVER]
nslookup命令:
nslookup [-option] [name | -] [server]
交互式模式;
nslookup>
server IP:指明使用哪个DNS server进行查询;
set q=RR_TYPE:指明查询的资源记录类型;
NAME:要查询的名称;
[root@www ~]# rndc reload
server reload successful
测试示例:
1)、检测本机的A标志
[root@www ~]# dig -t A www.field.com @192.168.88.131
; <<>> DiG9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.4 <<>> -t A www.field.com@192.168.88.131
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<-opcode: QUERY, status: NOERROR, id: 17461
;; flags: qr aa rd ra; QUERY:1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 2
;; QUESTION SECTION:
;www.field.com. IN A
;; ANSWER SECTION:
www.field.com. 86400 IN A 192.168.88.131
;; AUTHORITY SECTION:
field.com. 86400 IN NS ns1.field.com.
field.com. 86400 IN NS ns2.field.com.
;; ADDITIONAL SECTION:
ns1.field.com. 86400 IN A 192.168.88.131
ns2.field.com. 86400 IN A 192.168.88.130
;; Query time: 1 msec
;; SERVER:192.168.88.131#53(192.168.88.131)
;; WHEN: Fri Nov 17 19:20:352017
;; MSG SIZE rcvd: 115
2)、检测本机ftp.field.com的A标志
[root@www ~]# dig -t A ftp.field.com @192.168.88.131
; <<>> DiG9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.4 <<>> -t A ftp.field.com@192.168.88.131
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<-opcode: QUERY, status: NOERROR, id: 23208
;; flags: qr aa rd ra; QUERY:1, ANSWER: 2, AUTHORITY: 2, ADDITIONAL: 2
;; QUESTION SECTION:
;ftp.field.com. IN A
;; ANSWER SECTION:
ftp.field.com. 86400 IN CNAME www.field.com.
www.field.com. 86400 IN A 192.168.88.131
;; AUTHORITY SECTION:
field.com. 86400 IN NS ns1.field.com.
field.com. 86400 IN NS ns2.field.com.
;; ADDITIONAL SECTION:
ns1.field.com. 86400 IN A 192.168.88.131
ns2.field.com. 86400 IN A 192.168.88.130
;; Query time: 1 msec
;; SERVER:192.168.88.131#53(192.168.88.131)
;; WHEN: Fri Nov 17 19:21:162017
;; MSG SIZE rcvd: 133
3)、递归解析百度A记录
[root@www ~]# dig -t A WWW.BAIDU.COM +recurse
; <<>> DiG9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.4 <<>> -t A WWW.BAIDU.COM+recurse
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<-opcode: QUERY, status: NOERROR, id: 26624
;; flags: qr rd ra; QUERY: 1,ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;WWW.BAIDU.COM. IN A
;; ANSWER SECTION:
WWW.BAIDU.COM. 5 IN A 163.177.151.109
WWW.BAIDU.COM. 5 IN A 163.177.151.110
;; Query time: 17 msec
;; SERVER:192.168.88.2#53(192.168.88.2)
;; WHEN: Fri Nov 17 22:05:072017
;; MSG SIZE rcvd: 63
4)、host命令查看本机A记录
# [root@www named]# host -t A www.field.com 192.168.88.131
Using domain server:
Name: 192.168.88.131
Address: 192.168.88.131#53
Aliases:
www.field.com has address192.168.88.131
5)、host命令查看本机MX记录
[root@www named]# host -t MX field.com 192.168.88.131
Using domain server:
Name: 192.168.88.131
Address: 192.168.88.131#53
Aliases:
field.com mail is handled by20 mx2.field.com.
field.com mail is handled by10 mx1.field.com.
6)、host命令查看本机NS记录
[root@www named]# host -t NS field.com 192.168.88.131
Using domain server:
Name: 192.168.88.131
Address: 192.168.88.131#53
Aliases:
field.com name serverns2.field.com.
field.com name serverns1.field.com.
7)、nslookup交互式模式查询示例:
server IP:指明使用哪个DNSserver进行查询;
set q=RR_TYPE:指明查询的资源记录类型;
NAME:要查询的名称;
[root@www named]# nslookup
> server 192.168.88.131 //指明使用(192.168.88.131)DNSserver进行查询
Default server:192.168.88.131
Address: 192.168.88.131#53
> set q=A //指明查询的资源记录类型为A记录
> www.field.com //指明要查询的名称
Server: 192.168.88.131
Address: 192.168.88.131#53
Name: www.field.com
Address: 192.168.88.131
> set q=NS
> field.com
Server: 192.168.88.131
Address: 192.168.88.131#53
field.com nameserver = ns2.field.com.
field.com nameserver = ns1.field.com.
> set q=MX
> field.com
Server: 192.168.88.131
Address: 192.168.88.131#53
field.com mail exchanger = 10 mx1.field.com.
field.com mail exchanger = 20 mx2.field.com.
> exit //退出交互式模式
三、反向区域配置及测试
反向区域:
区域名称:网络地址反写 .in-addr.arpa.
192.168.88.--> 88.168.192.in-addr.arpa.
1)、定义区域
zone "ZONE_NAME" IN {
type {master|slave|forward};
file "网络地址.zone";
};
2)、定义区域解析库文件
注意:不需要MX和A,以及AAAA记录;以PTR记录为主
示例:
$TTL 86400
$ORIGIN 88.168.192.in-addr.arpa.
@ IN SOA ns1.field.com. admin.field.com. (
2017111701
1H
5M
7D
1D )
IN NS ns1.field.com.
IN NS ns2.field.com.
131 IN PTR ns1.field.com.
131 IN PTR www.field.com.
131 IN PTR mx1.field.com.
130 IN PTR mx2.field.com.
(1)、在主配置文件中定义区域
zone "ZONE_NAME" IN {
type {master|slave|forward};
file "网络地址.zone";
};
[root@www named]# vim /etc/named.rfc1912.zones
zone"localhost.localdomain" IN {
type master;
file "named.localhost";
allow-update { none; };
};
zone "localhost" IN{
type master;
file "named.localhost";
allow-update { none; };
};
zone"1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.ip6.arpa"IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone"1.0.0.127.in-addr.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone"0.in-addr.arpa" IN {
type master;
file "named.empty";
allow-update { none; };
};
zone "field.com" IN{
type master;
file "field.com.zone";
};
zone "88.168.192.in-addr.arpa" IN {
type master;
file"192.168.88.zone";
};
"/etc/named.rfc1912.zones"52L, 1102C 已写入
[root@www named]# named-checkconf
//查看配置文件是否有语法错误
(2)、定义区域解析库文件
注意:不需要MX和A,以及AAAA记录;以PTR记录为主
[root@www named]# vim 192.168.88.zone
$TTL 86400
$ORIGIN 88.168.192.in-addr.arpa.
@ IN SOA ns1.field.com. admin.field.com. (
2017111701
1H
5M
7D
1D )
IN NS ns1.field.com.
IN NS ns2.field.com.
131 IN PTR ns1.field.com.
131 IN PTR www.field.com.
131 IN PTR mx1.field.com.
130 IN PTR mx2.field.com.
~
"192.168.88.zone"14L, 302C 已写入
[root@www named]# named-checkzone "88.168.192.in-addr.arpa"192.168.88.zone
zone88.168.192.in-addr.arpa/IN: loaded serial 2017111701
OK
//查看区域解析库文件是否有语法错误
(3)、基于安全性考虑,修改区域解析库文件访问权限为640并将named加入属组。
[root@field named]# chmod 640 192.168.88.zone
[root@field named]# chown :named 192.168.88.zone
[root@www named]# ll
总用量 40
-rw-r-----. 1root named 302 11月 18 00:08192.168.88.zone
drwxr-x---. 7 root named 4096 11月 17 18:39 chroot
drwxrwx---. 2 named named4096 11月 17 13:26 data
drwxrwx---. 2 named named4096 11月 17 13:27 dynamic
-rw-r-----. 1 root named 361 11月 17 23:49 field.com.zone
-rw-r-----. 1 root named 3289 4月 11 2017 named.ca
-rw-r-----. 1 root named 152 12月 15 2009 named.empty
-rw-r-----. 1 root named 152 6月 21 2007 named.localhost
-rw-r-----. 1 root named 168 12月 15 2009 named.loopback
drwxrwx---. 2 named named4096 7月 5 17:55 slaves
[root@www named]#
[root@www named]# named-checkzone "88.168.192.in-addr.arpa"192.168.88.zone
zone88.168.192.in-addr.arpa/IN: loaded serial 2017111701
OK
[root@www named]# service named reload
重新载入named: [确定]
[root@www named]# rndc status
version: 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.4
CPUs found: 3
worker threads: 3
number of zones: 20
debug level: 0
xfers running: 0
xfers deferred: 0
soa queries in progress: 0
query logging is OFF
recursive clients: 0/0/1000
tcp clients: 0/100
server is up and running
[root@www named]#
[root@www named]#named-checkconf
[root@www named]# servicenamed reload
重新载入named: [确定]
[root@www named]# clear
[root@www named]# tail /var/log/messages
Nov 18 00:15:56 wwwnamed[4255]: loading configuration from '/etc/named.conf'
Nov 18 00:15:56 wwwnamed[4255]: using default UDP/IPv4 port range: [1024, 65535]
Nov 18 00:15:56 wwwnamed[4255]: using default UDP/IPv6 port range: [1024, 65535]
Nov 18 00:15:56 wwwnamed[4255]: sizing zone task pool based on 7 zones
Nov 18 00:15:57 wwwnamed[4255]: Warning: 'empty-zones-enable/disable-empty-zone' not set:disabling RFC 1918 empty zones
Nov 18 00:15:59 wwwnamed[4255]: reloading configuration succeeded
Nov 18 00:15:59 wwwnamed[4255]: reloading zones succeeded
Nov 18 00:16:00 wwwnamed[4255]: zone field.com/IN: zone serial (2017111701) unchanged. zone mayfail to transfer to slaves.
Nov 18 00:16:00 wwwnamed[4255]: zone field.com/IN: loaded serial 2017111701
Nov 18 00:16:00 wwwnamed[4255]: zone field.com/IN: sending notifies (serial 2017111701)
(4)、测试反向解析:
dig -x IP @SERVER
模拟区域传送:
dig -t axfr ZONE_NAME @SERVER
例如: dig -t axfr field.com @192.168.88.131
dig -t axfr88.168.192.in-addr.arpa @192.168.88.131
host命令:
host [-t type] name [SERVER]
nslookup命令:
nslookup [-option] [name | -] [server]
交互式模式;
nslookup>
server IP:指明使用哪个DNS server进行查询;
set q=RR_TYPE:指明查询的资源记录类型;
NAME:要查询的名称;
测试示例:
1)、查看PTR记录
[root@www named]# host -t PTR 192.168.88.131 192.168.88.131
Using domain server:
Name: 192.168.88.131
Address: 192.168.88.131#53
Aliases:
131.88.168.192.in-addr.arpadomain name pointer www.field.com.
131.88.168.192.in-addr.arpadomain name pointer mx1.field.com.
131.88.168.192.in-addr.arpadomain name pointer ns1.field.com.
[root@www named]# dig -x 192.168.88.131 @192.168.88.131
; <<>> DiG9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.4 <<>> -x 192.168.88.131@192.168.88.131
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<-opcode: QUERY, status: NOERROR, id: 4893
;; flags: qr aa rd ra; QUERY:1, ANSWER: 3, AUTHORITY: 2, ADDITIONAL: 2
;; QUESTION SECTION:
;131.88.168.192.in-addr.arpa. IN PTR
;; ANSWER SECTION:
131.88.168.192.in-addr.arpa.86400 IN PTR mx1.field.com.
131.88.168.192.in-addr.arpa.86400 IN PTR ns1.field.com.
131.88.168.192.in-addr.arpa.86400 IN PTR www.field.com.
;; AUTHORITY SECTION:
88.168.192.in-addr.arpa.86400 IN NS ns2.field.com.
88.168.192.in-addr.arpa.86400 IN NS ns1.field.com.
;; ADDITIONAL SECTION:
ns1.field.com. 86400 IN A 192.168.88.131
ns2.field.com. 86400 IN A 192.168.88.131
;; Query time: 1 msec
;; SERVER:192.168.88.131#53(192.168.88.131)
;; WHEN: Sat Nov 18 00:24:312017
;; MSG SIZE rcvd: 172
2)、模拟区域传送:
dig -t axfr ZONE_NAME @SERVER
[root@www named]# dig -t axfr field.com @192.168.88.131
; <<>> DiG9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.4 <<>> -t axfr field.com@192.168.88.131
;; global options: +cmd
field.com. 86400 IN SOA ns1.field.com. admin.field.com.field.com.2017111701 3600 300 604800 86400
field.com. 86400 IN NS ns1.field.com.
field.com. 86400 IN NS ns2.field.com.
field.com. 86400 IN MX 10 mx1.field.com.
field.com. 86400 IN MX 20 mx2.field.com.
ftp.field.com. 86400 IN CNAME www.field.com.
mx1.field.com. 86400 IN A 192.168.88.131
mx2.field.com. 86400 IN A 192.168.88.130
ns1.field.com. 86400 IN A 192.168.88.131
ns2.field.com. 86400 IN A 192.168.88.131
www.field.com. 86400 IN A 192.168.88.131
field.com. 86400 IN SOA ns1.field.com. admin.field.com.field.com.2017111701 3600 300 604800 86400
;; Query time: 38 msec
;; SERVER:192.168.88.131#53(192.168.88.131)
;; WHEN: Sat Nov 18 00:27:152017
;; XFR size: 12 records(messages 1, bytes 293)
[root@www named]# dig -t axfr 88.168.192.in-addr.arpa @192.168.88.131
; <<>> DiG9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.4 <<>> -t axfr88.168.192.in-addr.arpa @192.168.88.131
;; global options: +cmd
88.168.192.in-addr.arpa.86400 IN SOA ns1.field.com. admin.field.com. 2017111701 3600 300 604800 86400
88.168.192.in-addr.arpa.86400 IN NS ns1.field.com.
88.168.192.in-addr.arpa.86400 IN NS ns2.field.com.
130.88.168.192.in-addr.arpa.86400 IN PTR mx2.field.com.
131.88.168.192.in-addr.arpa.86400 IN PTR ns1.field.com.
131.88.168.192.in-addr.arpa.86400 IN PTR www.field.com.
131.88.168.192.in-addr.arpa.86400 IN PTR mx1.field.com.
88.168.192.in-addr.arpa.86400 IN SOA ns1.field.com. admin.field.com. 2017111701 3600 300 604800 86400
;; Query time: 18 msec
;; SERVER:192.168.88.131#53(192.168.88.131)
;; WHEN: Sat Nov 18 00:27:512017
;; XFR size: 8 records(messages 1, bytes 240)
四、泛域名解析:(使用通配符)
//无论使用什么名字都不会出错
随便测试一个不存在的名称,无法解析
[root@www named]# dig -t A pop3.field.com @192.168.88.131
; <<>> DiG9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.4 <<>> -t A pop3.field.com@192.168.88.131
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<-opcode: QUERY, status: NXDOMAIN, id: 60214
;; flags: qr aa rd ra; QUERY:1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 0
;; QUESTION SECTION:
;pop3.field.com. IN A
;; AUTHORITY SECTION:
field.com. 86400 IN SOA ns1.field.com.admin.field.com.field.com. 2017111701 3600 300 604800 86400
;; Query time: 1 msec
;; SERVER: 192.168.88.131#53(192.168.88.131)
;; WHEN: Sat Nov 18 00:33:452017
;; MSG SIZE rcvd: 88
[root@www named]#
[root@www named]# vimfield.com.zone
$TTL 86400
$ORIGIN field.com.
@ IN SOA ns1.field.com.admin.field.com (
2017111701
1H
5M
7D
1D )
IN NS ns1
IN NS ns2
IN MX 10 mx1
IN MX 20 mx2
ns1 IN A 192.168.88.131
ns2 IN A 192.168.88.131
mx1 IN A 192.168.88.131
mx2 IN A 192.168.88.130
www IN A 192.168.88.131
ftp IN CNAME www
* IN A 192.168.88.131
~
"field.com.zone"19L, 383C 已写入
[root@www named]# rndc reload
server reload successful
[root@www named]# dig -t A pop3.field.com @192.168.88.131
; <<>> DiG9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.4 <<>> -t A pop3.field.com@192.168.88.131
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<-opcode: QUERY, status: NOERROR, id: 41432
;; flags: qr aa rd ra; QUERY:1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 2
;; QUESTION SECTION:
;pop3.field.com. IN A
;; ANSWER SECTION:
pop3.field.com. 86400 IN A 192.168.88.131
;; AUTHORITY SECTION:
field.com. 86400 IN NS ns2.field.com.
field.com. 86400 IN NS ns1.field.com.
;; ADDITIONAL SECTION:
ns1.field.com. 86400 IN A 192.168.88.131
ns2.field.com. 86400 IN A 192.168.88.131
;; Query time: 1 msec
;; SERVER:192.168.88.131#53(192.168.88.131)
;; WHEN: Sat Nov 18 00:38:412017
;; MSG SIZE rcvd: 116
[root@www named]# vimfield.com.zone
$TTL 86400
$ORIGIN field.com.
@ IN SOA ns1.field.com.admin.field.com (
2017111701
1H
5M
7D
1D )
IN NS ns1
IN NS ns2
IN MX 10 mx1
IN MX 20 mx2
ns1 IN A 192.168.88.131
ns2 IN A 192.168.88.131
mx1 IN A 192.168.88.131
mx2 IN A 192.168.88.130
www IN A 192.168.88.131
ftp IN CNAME www
field.com. IN A 192.168.88.131
~
[root@www named]# rndc reload
server reload successful
[root@www named]#
[root@www named]# dig -t A field.com @192.168.88.131
; <<>> DiG9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.4 <<>> -t A field.com@192.168.88.131
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<-opcode: QUERY, status: NOERROR, id: 65503
;; flags: qr aa rd ra; QUERY:1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 2
;; QUESTION SECTION:
;field.com. IN A
;; ANSWER SECTION:
field.com. 86400 IN A 192.168.88.131
;; AUTHORITY SECTION:
field.com. 86400 IN NS ns1.field.com.
field.com. 86400 IN NS ns2.field.com.
;; ADDITIONAL SECTION:
ns1.field.com. 86400 IN A 192.168.88.131
ns2.field.com. 86400 IN A 192.168.88.131
;; Query time: 1 msec
;; SERVER:192.168.88.131#53(192.168.88.131)
;; WHEN: Sat Nov 18 00:51:272017
;; MSG SIZE rcvd: 111
[root@www named]# vim field.com.zone
$TTL 86400
$ORIGIN field.com.
@ IN SOA ns1.field.com.admin.field.com (
2017111701
1H
5M
7D
1D )
IN NS ns1
IN NS ns2
IN MX 10 mx1
IN MX 20 mx2
ns1 IN A 192.168.88.131
ns2 IN A 192.168.88.131
mx1 IN A 192.168.88.131
mx2 IN A 192.168.88.130
www IN A 192.168.88.131
ftp IN CNAME www
field.com. IN A 192.168.88.131
* IN A 192.168.88.131
~
[root@www named]# rndc reload
server reload successful
[root@www named]# dig -t A pop3.field.com @192.168.88.131
; <<>> DiG9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.4 <<>> -t A pop3.field.com@192.168.88.131
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<-opcode: QUERY, status: NOERROR, id: 47811
;; flags: qr aa rd ra; QUERY:1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 2
;; QUESTION SECTION:
;pop3.field.com. IN A
;; ANSWER SECTION:
pop3.field.com. 86400 IN A 192.168.88.131
;; AUTHORITY SECTION:
field.com. 86400 IN NS ns2.field.com.
field.com. 86400 IN NS ns1.field.com.
;; ADDITIONAL SECTION:
ns1.field.com. 86400 IN A 192.168.88.131
ns2.field.com. 86400 IN A 192.168.88.131
;; Query time: 1 msec
;; SERVER:192.168.88.131#53(192.168.88.131)
;; WHEN: Sat Nov 18 00:52:422017
;; MSG SIZE rcvd: 116
[root@www named]# dig -t A field.com @192.168.88.131
; <<>> DiG9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.4 <<>> -t A field.com@192.168.88.131
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<-opcode: QUERY, status: NOERROR, id: 41284
;; flags: qr aa rd ra; QUERY:1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 2
;; QUESTION SECTION:
;field.com. IN A
;; ANSWER SECTION:
field.com. 86400 IN A 192.168.88.131
;; AUTHORITY SECTION:
field.com. 86400 IN NS ns2.field.com.
field.com. 86400 IN NS ns1.field.com.
;; ADDITIONAL SECTION:
ns1.field.com. 86400 IN A 192.168.88.131
ns2.field.com. 86400 IN A 192.168.88.131
;; Query time: 1 msec
;; SERVER:192.168.88.131#53(192.168.88.131)
;; WHEN: Sat Nov 18 00:52:472017
;; MSG SIZE rcvd: 111
五、配置为dns服务器提供解析功能:
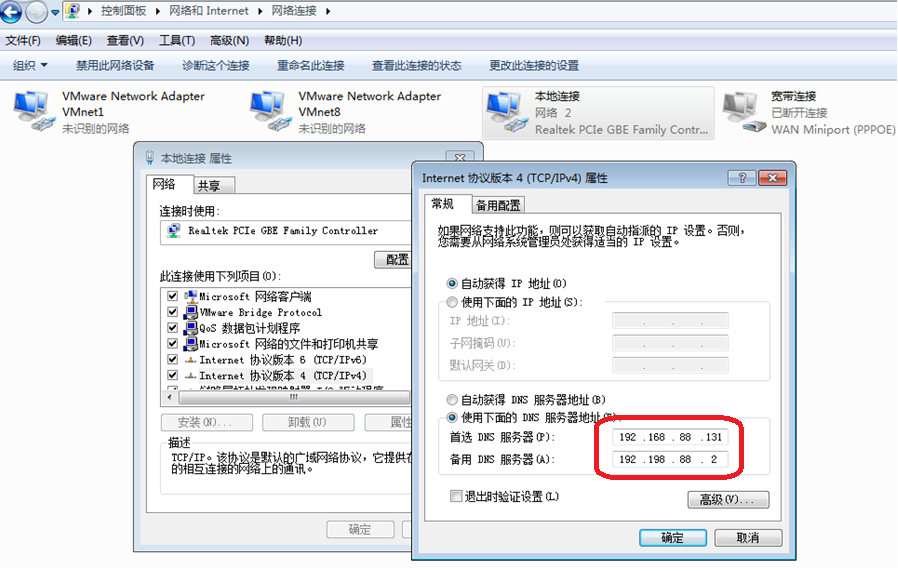
(1)、设置为客户机Windows的dns服务器,为其提供解析功能:
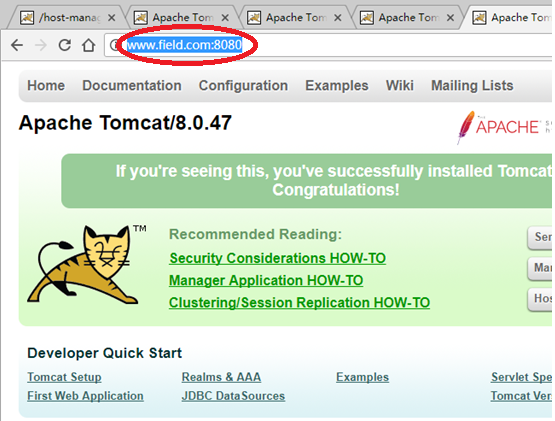
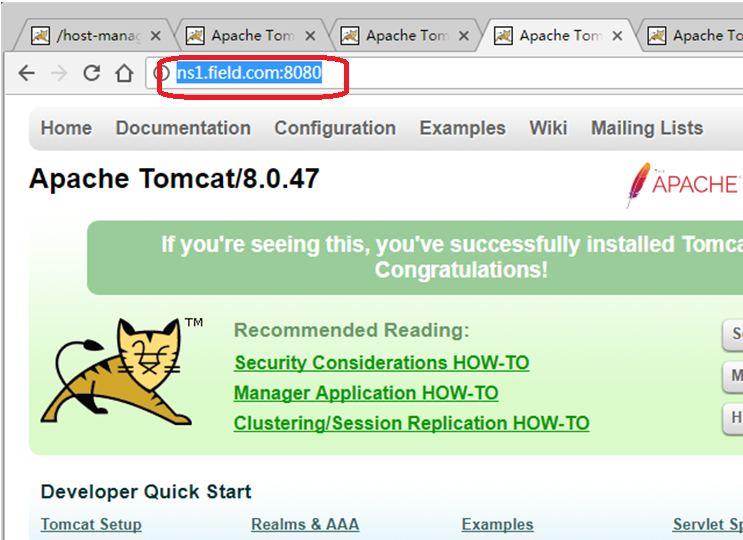
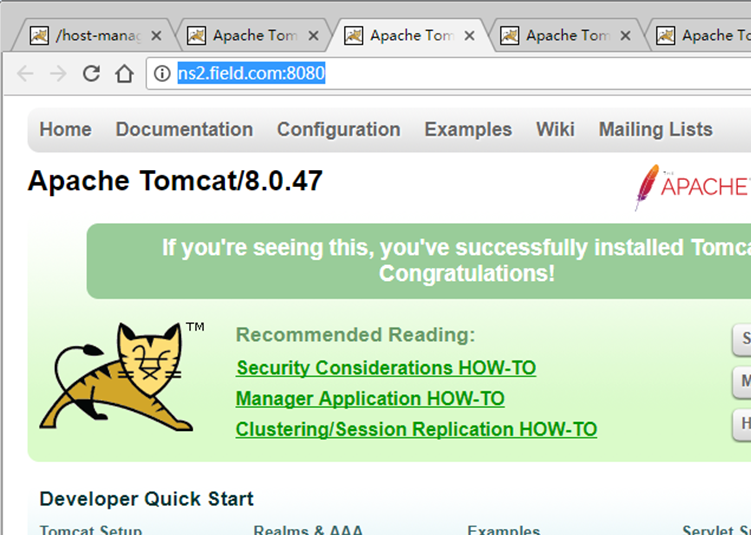
(2)、在Windows7上访问DNS主从服务器上的tomcat主页面:
分别通过访问主服务器上192.168.88.131的www.field.com:8080和 ns1.field.com:8080
以及从服务器上192.168.88.130的test.field.com:8080和ns2.field.com:8080
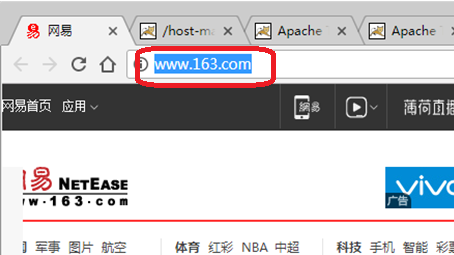
(3)、在Windows7上访问网易主页面(www.163.com),测试是否能解析:























 1563
1563

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








