Please refer to Security Guides
Base on the esp-idf/examples/wifi/getting_started/station example for testing.
Partition Table setting:
# Name, Type, SubType, Offset, Size, Flags
# Note: if you have increased the bootloader size, make sure to update the offsets to avoid overlap
nvs, data, nvs, , 0x4000,
otadata, data, ota, , 0x2000,
phy_init, data, phy, , 0x1000,
factory, app, factory, , 1M,
ota_0, app, ota_0, , 1M,
ota_1, app, ota_1, , 1M,
With flash encryption enabled, the following types of data are encrypted by default:
- Second Stage Bootloader
- Partition Table
- NVS Key Partition
- Otadata
- All
apptype partitions
Other types of data can be encrypted conditionally:
- Any partition marked with the encrypted flag in the partition table. For details, see Encrypted Partition Flag.
1、 Generate Flash Encryption Key
The ESP32-S3 Flash Encryption function support used the AES-128 (256-bit key) or AES-256 (512-bit key)

- Generate AES-128 (256-bit key) Flash Encryption Key:
espsecure.py generate_flash_encryption_key flash_encryption_key.bin

- Generate AES-256 (512-bit key) Flash Encryption Key:
espsecure.py generate_flash_encryption_key --keylen 512 flash_encryption_key.bin
2、Software setting:
→ Flash Size setting
- The value of Flash Size must not be larger than the hardware Flash Size and must not be smaller than the total partition size set in the partition table.

→ Partition Table setting
- Enabling flash encryption will increase the size of bootloader, which might require updating partition table offset. See Bootloader Size.

→ Security features
- Enable Flash Encryption Release mode

→ Security features → UART ROM download mode
- Disable the download mode

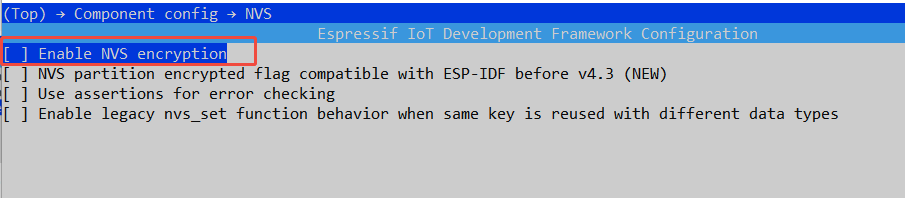
→ Component config → NVS
- If you don’t encryption the NVS partitions ,please disable NVS Encryption
3、Build the project and Get the firmware
- From the project building log ,we can get the Partition table offset address informations,as follows:
Partition table binary generated. Contents:
*******************************************************************************
# ESP-IDF Partition Table
# Name, Type, SubType, Offset, Size, Flags
nvs,data,nvs,0xe000,16K,
otadata,data,ota,0x12000,8K,
phy_init,data,phy,0x14000,4K,
factory,app,factory,0x20000,1M,
ota_0,app,ota_0,0x120000,1M,
ota_1,app,ota_1,0x220000,1M,
*******************************************************************************
- From the project building log ,we can get the binary generated informations ,as follows:

4、Use Flash Encryption Key to encrypt all the firmware
Please node: The address is your firmware download address
The command for encrypting the firmware of all partitions using the Flash encryption Key are the same.
espsecure.py encrypt_flash_data --aes_xts --keyfile flash_encryption_key.bin --output bootloader-encrypted.bin --address 0x0 build\bootloader\bootloader.bin
espsecure.py encrypt_flash_data --aes_xts --keyfile flash_encryption_key.bin --output partition-encrypted.bin --address 0xd000 build\partition_table\partition-table.bin
espsecure.py encrypt_flash_data --aes_xts --keyfile flash_encryption_key.bin --output ota-data-encrypted.bin --address 0x12000 build\ota_data_initial.bin
espsecure.py encrypt_flash_data --aes_xts --keyfile flash_encryption_key.bin --output encrypted-wifi-station.bin --address 0x20000 build\wifi_station.bin

5、Download all encrypt firmware
esptool.py -p COM68 write_flash 0x0 bootloader-encrypted.bin 0xd000 partition-encrypted.bin 0x12000 ota-data-encrypted.bin 0x20000 encrypted-wifi-station.bin

6、Write Flash encryption key to eFuse BLOCK
- For Flash Encryption, Write flash_encryption_key.bin to efuse
BLOCK_KEY0
espefuse.py -p COM68 burn_key BLOCK_KEY0 flash_encryption_key.bin XTS_AES_128_KEY

7、Write various efuse control bits for Flash Encryption
espefuse.py -p COM68 burn_efuse --do-not-confirm DIS_USB_JTAG 0x1 DIS_PAD_JTAG 0x1 SOFT_DIS_JTAG 0x7 DIS_USB_OTG_DOWNLOAD_MODE 0x1 DIS_DIRECT_BOOT 0x1 DIS_DOWNLOAD_ICACHE 0x1 DIS_DOWNLOAD_DCACHE 0x1 DIS_DOWNLOAD_MANUAL_ENCRYPT 0x1 SPI_BOOT_CRYPT_CNT 0x7

8、Last, reset your device to Flash boot mode:
ESP-ROM:esp32s3-20210327
Build:Mar 27 2021
rst:0x1 (POWERON),boot:0x8 (SPI_FAST_FLASH_BOOT)
SPIWP:0xee
mode:DIO, clock div:1
load:0x3fce2980,len:0x277c
load:0x403c8700,len:0x4
load:0x403c8704,len:0xd20
load:0x403cb700,len:0x45d0
entry 0x403c8928
I (36) boot: ESP-IDF v5.4-dev-3602-ga97a7b0962-dirty 2nd stage bootloader
I (36) boot: compile time Apr 14 2025 18:43:01
I (36) boot: Multicore bootloader
I (39) boot: chip revision: v0.1
I (42) boot: efuse block revision: v1.2
I (45) boot.esp32s3: Boot SPI Speed : 80MHz
I (49) boot.esp32s3: SPI Mode : DIO
I (53) boot.esp32s3: SPI Flash Size : 4MB
I (57) boot: Enabling RNG early entropy source...
I (61) boot: Partition Table:
I (64) boot: ## Label Usage Type ST Offset Length
I (70) boot: 0 nvs WiFi data 01 02 0000e000 00004000
I (76) boot: 1 otadata OTA data 01 00 00012000 00002000
I (83) boot: 2 phy_init RF data 01 01 00014000 00001000
I (89) boot: 3 factory factory app 00 00 00020000 00100000
I (96) boot: 4 ota_0 OTA app 00 10 00120000 00100000
I (103) boot: 5 ota_1 OTA app 00 11 00220000 00100000
I (109) boot: End of partition table
I (112) boot: Defaulting to factory image
I (116) esp_image: segment 0: paddr=00020020 vaddr=3c080020 size=1fbc8h (129992) map
I (149) esp_image: segment 1: paddr=0003fbf0 vaddr=3fc99900 size=00428h ( 1064) load
I (150) esp_image: segment 2: paddr=00040020 vaddr=42000020 size=786a4h (493220) map
I (250) esp_image: segment 3: paddr=000b86cc vaddr=3fc99d28 size=04550h ( 17744) load
I (254) esp_image: segment 4: paddr=000bcc24 vaddr=40374000 size=158e8h ( 88296) load
I (275) esp_image: segment 5: paddr=000d2514 vaddr=600fe100 size=00018h ( 24) load
I (284) boot: Loaded app from partition at offset 0x20000
I (284) boot: Checking flash encryption...
I (284) flash_encrypt: flash encryption is enabled (0 plaintext flashes left)
I (288) boot: Disabling RNG early entropy source...
I (305) cpu_start: Multicore app
I (314) cpu_start: Pro cpu start user code
I (314) cpu_start: cpu freq: 160000000 Hz
I (314) app_init: Application information:
I (314) app_init: Project name: wifi_station
I (318) app_init: App version: v5.4-dev-3602-ga97a7b0962-dirty
I (324) app_init: Compile time: Apr 14 2025 18:41:38
I (329) app_init: ELF file SHA256: 89eb98773...
I (334) app_init: ESP-IDF: v5.4-dev-3602-ga97a7b0962-dirty
I (340) efuse_init: Min chip rev: v0.0
I (344) efuse_init: Max chip rev: v0.99
I (348) efuse_init: Chip rev: v0.1
I (351) heap_init: Initializing. RAM available for dynamic allocation:
I (358) heap_init: At 3FCA1F98 len 00047778 (285 KiB): RAM
I (363) heap_init: At 3FCE9710 len 00005724 (21 KiB): RAM
I (368) heap_init: At 3FCF0000 len 00008000 (32 KiB): DRAM
I (373) heap_init: At 600FE118 len 00001ED0 (7 KiB): RTCRAM
I (380) spi_flash: detected chip: generic
I (382) spi_flash: flash io: dio
W (385) spi_flash: Detected size(8192k) larger than the size in the binary image header(4096k). Using the size in the binary image header.
I (397) flash_encrypt: Flash encryption mode is RELEASE
I (429) efuse: BURN BLOCK0
I (431) efuse: BURN BLOCK0 - OK (all write block bits are set)
I (432) sleep_gpio: Configure to isolate all GPIO pins in sleep state
I (432) sleep_gpio: Enable automatic switching of GPIO sleep configuration
I (439) main_task: Started on CPU0
I (449) main_task: Calling app_main()
I (449) wifi station: ESP_WIFI_MODE_STA
I (459) pp: pp rom version: e7ae62f
I (459) net80211: net80211 rom version: e7ae62f
I (479) wifi:wifi driver task: 3fcac14c, prio:23, stack:6656, core=0
I (479) wifi:wifi firmware version: 0a80d45
I (479) wifi:wifi certification version: v7.0
I (479) wifi:config NVS flash: enabled
I (479) wifi:config nano formatting: disabled
I (489) wifi:Init data frame dynamic rx buffer num: 32
I (489) wifi:Init static rx mgmt buffer num: 5
I (499) wifi:Init management short buffer num: 32
I (499) wifi:Init dynamic tx buffer num: 32
I (499) wifi:Init static tx FG buffer num: 2
I (509) wifi:Init static rx buffer size: 1600
I (509) wifi:Init static rx buffer num: 10
I (519) wifi:Init dynamic rx buffer num: 32
I (519) wifi_init: rx ba win: 6
I (519) wifi_init: accept mbox: 6
I (529) wifi_init: tcpip mbox: 32
I (529) wifi_init: udp mbox: 6
I (529) wifi_init: tcp mbox: 6
I (529) wifi_init: tcp tx win: 5760
I (539) wifi_init: tcp rx win: 5760
I (539) wifi_init: tcp mss: 1440
I (539) wifi_init: WiFi IRAM OP enabled
I (549) wifi_init: WiFi RX IRAM OP enabled
I (569) phy_init: phy_version 680,a6008b2,Jun 4 2024,16:41:10
W (569) phy_init: failed to load RF calibration data (0x1102), falling back to full calibration
W (609) phy_init: saving new calibration data because of checksum failure, mode(2)
I (619) wifi:mode : sta (68:b6:b3:50:1c:d4)
I (619) wifi:enable tsf
I (619) wifi station: wifi_init_sta finished.
I (1099) wifi:new:<1,1>, old:<1,0>, ap:<255,255>, sta:<1,1>, prof:1, snd_ch_cfg:0x0
I (1099) wifi:state: init -> auth (0xb0)
I (1109) wifi:state: auth -> assoc (0x0)
I (1119) wifi:state: assoc -> run (0x10)
I (1369) wifi:connected with cc2.4, aid = 1, channel 1, 40U, bssid = 7c:b5:9b:6b:d6:c2
I (1369) wifi:security: WPA2-PSK, phy: bgn, rssi: -33
I (1379) wifi:pm start, type: 1
I (1379) wifi:dp: 1, bi: 102400, li: 3, scale listen interval from 307200 us to 307200 us
I (1379) wifi:set rx beacon pti, rx_bcn_pti: 0, bcn_timeout: 25000, mt_pti: 0, mt_time: 10000
I (1439) wifi:AP's beacon interval = 102400 us, DTIM period = 1
I (2119) wifi:<ba-add>idx:0 (ifx:0, 7c:b5:9b:6b:d6:c2), tid:0, ssn:2, winSize:64
I (3699) esp_netif_handlers: sta ip: 192.168.1.100, mask: 255.255.255.0, gw: 192.168.1.1
I (3699) wifi station: got ip:192.168.1.100
I (3699) wifi station: connected to ap SSID:cc2.4 password:12345678
I (3699) main_task: Returned from app_main()

























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








