背景:
我是在"10.0.132.111", “10.0.134.144”, “10.0.128.191” 这三台虚拟机上安装etcd集群,每台一个etcd服务。
一. 安装cfssl
wget https://pkg.cfssl.org/R1.2/cfssl_linux-amd64
wget https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64
chmod +x cfssl_linux-amd64 cfssljson_linux-amd64
mv cfssl_linux-amd64 /usr/bin/cfssl
mv cfssljson_linux-amd64 /usr/bin/cfssljson
二. 创建CA证书,客户端,服务端,节点之间的证书
2.1 证书配置 ca-config.json
{
"signing": {
"default": {
"expiry": "43800h"
},
"profiles": {
"server": {
"expiry": "43800h",
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
]
},
"client": {
"expiry": "43800h",
"usages": [
"signing",
"key encipherment",
"client auth"
]
},
"peer": {
"expiry": "43800h",
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
]
}
}
}
}
2.2 证书签名请求配置 ca-csr.json
{
"CN": "etcd",
"hosts": [
"10.0.132.111",
"10.0.134.144",
"10.0.128.191",
"127.0.0.1"
],
"key": {
"algo": "ecdsa",
"size": 256
},
"names": [
{
"C": "CN",
"ST": "SH",
"L": "SH"
}
]
}
2.3 生成CA证书和私钥
cfssl gencert -initca ca-csr.json | cfssljson -bare ca
2.4 客户端证书配置 client.json
{
"CN": "client",
"hosts": [""],
"key": {
"algo": "ecdsa",
"size": 256
}
}
2.5 生成客户端 client 证书
cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=client client.json | cfssljson -bare client -
2.6 server 端证书配置 etcd.json
{
"CN": "etcd",
"hosts": [
"10.0.132.111",
"10.0.134.144",
"10.0.128.191",
"127.0.0.1"
],
"key": {
"algo": "ecdsa",
"size": 256
},
"names": [
{
"C": "CN",
"L": "SH",
"ST": "SH"
}
]
}
2.7 生成 server 证书
cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=server etcd.json | cfssljson -bare server
2.8 生成 peer 证书
cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=peer etcd.json | cfssljson -bare peer
注意证书配置中hosts, 127.0.0.1 必须添加,否则影响用户认证开启状态下,root用户的默认创建。
证书生成结果展示:
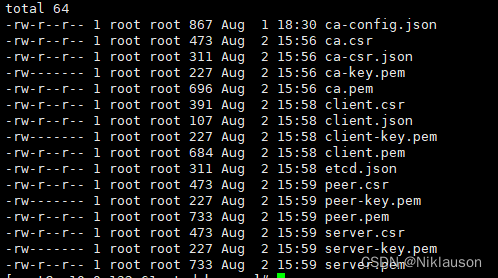
以下是三台虚拟机上 etcd 服务的 docker-compose.yaml , 开启用户认证和 tls 认证,证书的引用方式在其中已展示,证书路径为当前 docker-compose.yaml 文件同级目录ssl 下,etcd版本为3.5.7,仅供参考:
节点:10.0.132.111
version: '3'
services:
etcd01:
image: bitnami/etcd:latest
container_name: etcd01
environment:
- ETCD_NAME=etcd01
- ETCD_ROOT_PASSWORD=hillstone
- ETCD_CLIENT_CERT_AUTH=true
- ETCD_PEER_CLIENT_CERT_AUTH=true
- ETCD_ADVERTISE_CLIENT_URLS=https://10.0.132.111:12379
- ETCD_INITIAL_ADVERTISE_PEER_URLS=https://10.0.132.111:12380
- ETCD_LISTEN_CLIENT_URLS=https://0.0.0.0:2379
- ETCD_LISTEN_PEER_URLS=https://0.0.0.0:2380
- ETCD_INITIAL_CLUSTER_TOKEN=config_etcd_cluster
- ETCD_INITIAL_CLUSTER=etcd01=https://10.0.132.111:12380,etcd02=https://10.0.134.144:12380,etcd03=https://10.0.128.191:12380
- ETCD_INITIAL_CLUSTER_STATE=new
#- ETCD_LOG_LEVEL=debug
- ETCD_TRUSTED_CA_FILE=/opt/bitnami/etcd/ssl/ca.pem
- ETCD_KEY_FILE=/opt/bitnami/etcd/ssl/server-key.pem
- ETCD_CERT_FILE=/opt/bitnami/etcd/ssl/server.pem
- ETCD_PEER_TRUSTED_CA_FILE=/opt/bitnami/etcd/ssl/ca.pem
- ETCD_PEER_KEY_FILE=/opt/bitnami/etcd/ssl/peer-key.pem
- ETCD_PEER_CERT_FILE=/opt/bitnami/etcd/ssl/peer.pem
volumes:
- /etc/localtime:/etc/localtime
- ./data:/bitnami/etcd/data
- ./ssl/ca.pem:/opt/bitnami/etcd/ssl/ca.pem
- ./ssl/peer.pem:/opt/bitnami/etcd/ssl/peer.pem
- ./ssl/peer-key.pem:/opt/bitnami/etcd/ssl/peer-key.pem
- ./ssl/server.pem:/opt/bitnami/etcd/ssl/server.pem
- ./ssl/server-key.pem:/opt/bitnami/etcd/ssl/server-key.pem
- ./ssl/client-key.pem:/opt/bitnami/etcd/ssl/client-key.pem
- ./ssl/client.pem:/opt/bitnami/etcd/ssl/client.pem
ports:
- 12379:2379
- 12380:2380
节点:10.0.134.144
version: '3'
services:
etcd02:
image: bitnami/etcd:latest
container_name: etcd02
environment:
- ETCD_NAME=etcd02
- ETCD_ROOT_PASSWORD=hillstone
- ETCD_CLIENT_CERT_AUTH=true
- ETCD_PEER_CLIENT_CERT_AUTH=true
- ETCD_ADVERTISE_CLIENT_URLS=https://10.0.134.144:12379
- ETCD_INITIAL_ADVERTISE_PEER_URLS=https://10.0.134.144:12380
- ETCD_LISTEN_CLIENT_URLS=https://0.0.0.0:2379
- ETCD_LISTEN_PEER_URLS=https://0.0.0.0:2380
- ETCD_INITIAL_CLUSTER_TOKEN=etcd_cluster
- ETCD_INITIAL_CLUSTER=etcd01=https://10.0.132.111:12380,etcd02=https://10.0.134.144:12380,etcd03=https://10.0.128.191:12380
- ETCD_INITIAL_CLUSTER_STATE=new
#- ETCD_LOG_LEVEL=debug
- ETCD_TRUSTED_CA_FILE=/opt/bitnami/etcd/ssl/ca.pem
- ETCD_KEY_FILE=/opt/bitnami/etcd/ssl/server-key.pem
- ETCD_CERT_FILE=/opt/bitnami/etcd/ssl/server.pem
- ETCD_PEER_TRUSTED_CA_FILE=/opt/bitnami/etcd/ssl/ca.pem
- ETCD_PEER_KEY_FILE=/opt/bitnami/etcd/ssl/peer-key.pem
- ETCD_PEER_CERT_FILE=/opt/bitnami/etcd/ssl/peer.pem
volumes:
- /etc/localtime:/etc/localtime
- ./data:/bitnami/etcd/data
- ./ssl/ca.pem:/opt/bitnami/etcd/ssl/ca.pem
- ./ssl/peer.pem:/opt/bitnami/etcd/ssl/peer.pem
- ./ssl/peer-key.pem:/opt/bitnami/etcd/ssl/peer-key.pem
- ./ssl/server.pem:/opt/bitnami/etcd/ssl/server.pem
- ./ssl/server-key.pem:/opt/bitnami/etcd/ssl/server-key.pem
- ./ssl/client-key.pem:/opt/bitnami/etcd/ssl/client-key.pem
- ./ssl/client.pem:/opt/bitnami/etcd/ssl/client.pem
ports:
- 12379:2379
- 12380:2380
节点:10.0.128.191
version: '3'
services:
etcd03:
image: bitnami/etcd:latest
container_name: etcd03
environment:
- ETCD_NAME=etcd03
- ETCD_ROOT_PASSWORD=hillstone
- ETCD_CLIENT_CERT_AUTH=true
- ETCD_PEER_CLIENT_CERT_AUTH=true
- ETCD_ADVERTISE_CLIENT_URLS=https://10.0.128.191:12379
- ETCD_INITIAL_ADVERTISE_PEER_URLS=https://10.0.128.191:12380
- ETCD_LISTEN_CLIENT_URLS=https://0.0.0.0:2379
- ETCD_LISTEN_PEER_URLS=https://0.0.0.0:2380
- ETCD_INITIAL_CLUSTER_TOKEN=etcd_cluster
- ETCD_INITIAL_CLUSTER=etcd01=https://10.0.132.111:12380,etcd02=https://10.0.134.144:12380,etcd03=https://10.0.128.191:12380
- ETCD_INITIAL_CLUSTER_STATE=new
#- ETCD_LOG_LEVEL=debug
- ETCD_TRUSTED_CA_FILE=/opt/bitnami/etcd/ssl/ca.pem
- ETCD_KEY_FILE=/opt/bitnami/etcd/ssl/server-key.pem
- ETCD_CERT_FILE=/opt/bitnami/etcd/ssl/server.pem
- ETCD_PEER_TRUSTED_CA_FILE=/opt/bitnami/etcd/ssl/ca.pem
- ETCD_PEER_KEY_FILE=/opt/bitnami/etcd/ssl/peer-key.pem
- ETCD_PEER_CERT_FILE=/opt/bitnami/etcd/ssl/peer.pem
volumes:
- /etc/localtime:/etc/localtime
- ./data:/bitnami/etcd/data
- ./ssl/ca.pem:/opt/bitnami/etcd/ssl/ca.pem
- ./ssl/peer.pem:/opt/bitnami/etcd/ssl/peer.pem
- ./ssl/peer-key.pem:/opt/bitnami/etcd/ssl/peer-key.pem
- ./ssl/server.pem:/opt/bitnami/etcd/ssl/server.pem
- ./ssl/server-key.pem:/opt/bitnami/etcd/ssl/server-key.pem
- ./ssl/client-key.pem:/opt/bitnami/etcd/ssl/client-key.pem
- ./ssl/client.pem:/opt/bitnami/etcd/ssl/client.pem
ports:
- 12379:2379
- 12380:2380
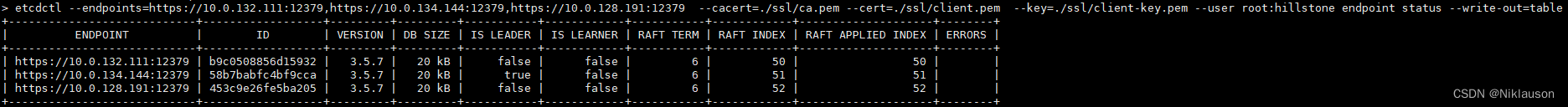
etctctl 命令查询集群状态(因为开启了证书认证和用户认证,所以需要添加相关的参数):
etcdctl --endpoints=https://10.0.132.111:12379,https://10.0.134.144:12379,https://10.0.128.191:12379 --cacert=./ssl/ca.pem --cert=./ssl/client.pem --key=./ssl/client-key.pem --user root:hillstone endpoint status --write-out=table





















 941
941











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








