volatility2很好装,插件mimikatz你只需要下载好mimikatz.py放到对应的plugins目录下就可以
教程很多 也是正确的 但有些细节问题 容易踩坑
装插件mimikatz真是装的我头痛
主要的问题出在:
1. 有些github上的mimikatz.py有点问题 没办法使用
我找到的靠谱的:
hotoloti/volatility/mimikatz.py at master · RealityNet/hotoloti (github.com)
2.可能出现这样的错误提示
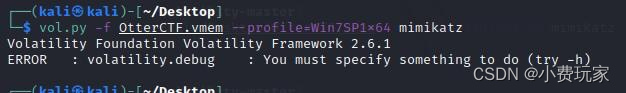
在-f 前增加--plugin,后面接你的volatility里plugins存放的目录 例如我这里是
--plugin=/home/kali/volatility/volatility/plugins┌──(kali㉿kali)-[~/volatility/volatility/plugins]
└─$ vol.py --plugin=./ -f /home/kali/Desktop/OtterCTF.vmem --profile=Win7SP1x64 mimikatz 3.construct版本问题
如果你也出现了下面这条错误信息
**Failed to import volatility.plugins.mimikatz (AttributeError: 'module' object has no attribute 'Int32ul')我在网上搜索到了全都是将construct换成2.5.5 但我就是换成2.5.5之后会出现了上面这个问题
解决办法:
直接 sudo pip install construct 下载的2.10.54的版本 并不会出问题(注意这里的pip是python2的)
┌──(kali㉿kali)-[~/volatility/volatility/plugins]
└─$ sudo pip install construct
DEPRECATION: Python 2.7 reached the end of its life on January 1st, 2020. Please upgrade your Python as Python 2.7 is no longer maintained. pip 21.0 will drop support for Python 2.7 in January 2021. More details about Python 2 support in pip can be found at https://pip.pypa.io/en/latest/development/release-process/#python-2-support pip 21.0 will remove support for this functionality.
Processing /root/.cache/pip/wheels/af/8e/c5/686cebf634111570b5dde5b340fcff57968f6c57e9d1024a0f/construct-2.10.54-py2-none-any.whl
Installing collected packages: construct
Successfully installed construct-2.10.54


























 5324
5324

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








