听说你想学习破译密码(crypto)?这可是CTF中最冷门的鸭,你可真是个奇怪的人。还不如学习WEB安全,快去渗透它吧,给个好评哟~如果你坚持要搞crypto,那就来挑战12道新手密码题吧。相信我,你会转去做WEB安全的。如果你硬着皮头,搞到底,你会发现你是没朋友滴,嘿嘿,渗透大法好~
攻防世界XCFT刷题信息汇总如下:攻防世界XCTF黑客笔记刷题记录 ,收藏一下哈~
第一题:考察Base64编码
解题报告:
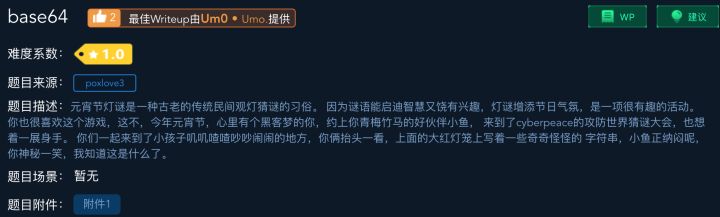
打开附件,里面是一串Base64的字符串,解码就行咯
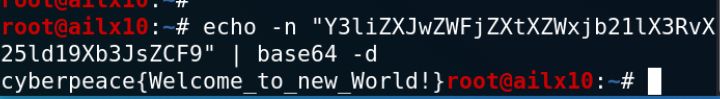
echo -n "Y3liZXJwZWFjZXtXZWxjb21lX3RvX25ld19Xb3JsZCF9" | base64 -d
第二题:考察凯撒密码
解题报告:
写一个python小脚本就是咯,这种脚本是必备的,萌新默默记在小本子里吧~
str1 = "oknqdbqmoq{kag_tmhq_xqmdzqp_omqemd_qzodkbfuaz}"
num = 26
def caesar(str="123",num=1):
l = list(str)
i = 0
while i < len(l):
if l[i]>='0' and l[i]<='9':
i = i+1
elif l[i]>='a' and l[i] <='z':
l[i]=chr(ord('a')+(ord(l[i])+num-ord('a'))%26)
i =i+1
elif l[i]>='A' and l[i] <='Z':
l[i]=chr(ord('A')+(ord(l[i])+num-ord('A'))%26)
i=i+1
else:
i =i+1
ans = "".join(l)
return ans
for i in range(num):
caesar_str = caesar(str1,i)
print(caesar_str)
第三题:考察莫斯密码
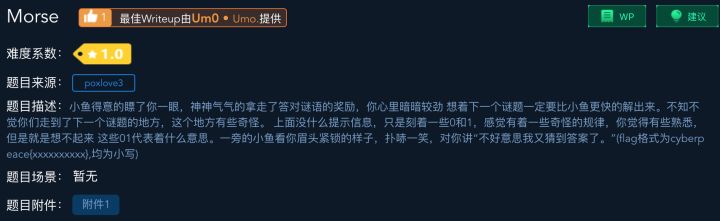
解题报告:
写一个小脚本,莫斯密码就可以不求人啦
dict1 = {'0': '.',
'1': '-',
' ': '/'
};
dict2 = {'.-': 'a',
'-...': 'b',
'-.-.': 'c',
'-..':'d',
'.':'e',
'..-.':'f',
'--.': 'g',
'....': 'h',
'..': 'i',
'.---':'j',
'-.-': 'k',
'.-..': 'l',
'--': 'm',
'-.': 'n',
'---': 'o',
'.--.': 'p',
'--.-': 'q',
'.-.': 'r',
'...': 's',
'-': 't',
'..-': 'u',
'...-': 'v',
'.--': 'w',
'-..-': 'x',
'-.--': 'y',
'--..': 'z',
'.----': '1',
'..---': '2',
'...--': '3',
'....-': '4',
'.....': '5',
'-....': '6',
'--...': '7',
'---..': '8',
'----.': '9',
'-----': '0',
'/': ' '
};
enc_str0="11 111 010 000 0 1010 111 100 0 00 000 000 111 00 10 1 0 010 0 000 1 00 10 110"
enc_str1=""
dec_str=""
for i in enc_str0:
enc_str1+=dict1[i]
enc_str1=enc_str1.split("/")
for i in enc_str1:
dec_str += dict2[i]
print(dec_str)
如果遇到这种外国版的甲骨文(图片代表字符),只能上机器学习了。

第四题:考察base64和ASCII编码
解题报告:
第一步:base64解码
输入:
echo -n "JiM3NjsmIzEyMjsmIzY5OyYjMTIwOyYjNzk7JiM4MzsmIzU2OyYjMTIwOyYjNzc7JiM2ODsmIzY5OyYjMTE4OyYjNzc7JiM4NDsmIzY1OyYjNTI7JiM3NjsmIzEyMjsmIzEwNzsmIzUzOyYjNzY7JiMxMjI7JiM2OTsmIzEyMDsmIzc3OyYjODM7JiM1NjsmIzEyMDsmIzc3OyYjNjg7JiMxMDc7JiMxMTg7JiM3NzsmIzg0OyYjNjU7JiMxMjA7JiM3NjsmIzEyMjsmIzY5OyYjMTIwOyYjNzg7JiMxMDU7JiM1NjsmIzEyMDsmIzc3OyYjODQ7JiM2OTsmIzExODsmIzc5OyYjODQ7JiM5OTsmIzExODsmIzc3OyYjODQ7JiM2OTsmIzUwOyYjNzY7JiMxMjI7JiM2OTsmIzEyMDsmIzc4OyYjMTA1OyYjNTY7JiM1MzsmIzc4OyYjMTIxOyYjNTY7JiM1MzsmIzc5OyYjODM7JiM1NjsmIzEyMDsmIzc3OyYjNjg7JiM5OTsmIzExODsmIzc5OyYjODQ7JiM5OTsmIzExODsmIzc3OyYjODQ7JiM2OTsmIzExOTsmIzc2OyYjMTIyOyYjNjk7JiMxMTk7JiM3NzsmIzY3OyYjNTY7JiMxMjA7JiM3NzsmIzY4OyYjNjU7JiMxMTg7JiM3NzsmIzg0OyYjNjU7JiMxMjA7JiM3NjsmIzEyMjsmIzY5OyYjMTE5OyYjNzc7JiMxMDU7JiM1NjsmIzEyMDsmIzc3OyYjNjg7JiM2OTsmIzExODsmIzc3OyYjODQ7JiM2OTsmIzExOTsmIzc2OyYjMTIyOyYjMTA3OyYjNTM7JiM3NjsmIzEyMjsmIzY5OyYjMTE5OyYjNzc7JiM4MzsmIzU2OyYjMTIwOyYjNzc7JiM4NDsmIzEwNzsmIzExODsmIzc3OyYjODQ7JiM2OTsmIzEyMDsmIzc2OyYjMTIyOyYjNjk7JiMxMjA7JiM3ODsmIzY3OyYjNTY7JiMxMjA7JiM3NzsmIzY4OyYjMTAzOyYjMTE4OyYjNzc7JiM4NDsmIzY1OyYjMTE5Ow==" | base64 -d
输出:
LzExOS8xMDEvMTA4Lzk5LzExMS8xMDkvMTAxLzExNi8xMTEvOTcvMTE2LzExNi85Ny85OS8xMDcvOTcvMTEwLzEwMC8xMDAvMTAxLzEwMi8xMDEvMTEwLzk5LzEwMS8xMTkvMTExLzExNC8xMDgvMTAw
第二步:转化为ASCII对应的字符
LzExOS8xMDEvMTA4Lzk5LzExMS8xMDkvMTAxLzExNi8xMTEvOTcvMTE2LzExNi85Ny85OS8xMDcvOTcvMTEwLzEwMC8xMDAvMTAxLzEwMi8xMDEvMTEwLzk5LzEwMS8xMTkvMTExLzExNC8xMDgvMTAw
第三步:再次base64解码
/119/101/108/99/111/109/101/116/111/97/116/116/97/99/107/97/110/100/100/101/102/101/110/99/101/119/111/114/108/100
第四步:再次转化为ASCII对应的字符串
welcometoattackanddefenceworld
一口气脚本:
import base64
str1 = "JiM3NjsmIzEyMjsmIzY5OyYjMTIwOyYjNzk7JiM4MzsmIzU2OyYjMTIwOyYjNzc7JiM2ODsmIzY5OyYjMTE4OyYjNzc7JiM4NDsmIzY1OyYjNTI7JiM3NjsmIzEyMjsmIzEwNzsmIzUzOyYjNzY7JiMxMjI7JiM2OTsmIzEyMDsmIzc3OyYjODM7JiM1NjsmIzEyMDsmIzc3OyYjNjg7JiMxMDc7JiMxMTg7JiM3NzsmIzg0OyYjNjU7JiMxMjA7JiM3NjsmIzEyMjsmIzY5OyYjMTIwOyYjNzg7JiMxMDU7JiM1NjsmIzEyMDsmIzc3OyYjODQ7JiM2OTsmIzExODsmIzc5OyYjODQ7JiM5OTsmIzExODsmIzc3OyYjODQ7JiM2OTsmIzUwOyYjNzY7JiMxMjI7JiM2OTsmIzEyMDsmIzc4OyYjMTA1OyYjNTY7JiM1MzsmIzc4OyYjMTIxOyYjNTY7JiM1MzsmIzc5OyYjODM7JiM1NjsmIzEyMDsmIzc3OyYjNjg7JiM5OTsmIzExODsmIzc5OyYjODQ7JiM5OTsmIzExODsmIzc3OyYjODQ7JiM2OTsmIzExOTsmIzc2OyYjMTIyOyYjNjk7JiMxMTk7JiM3NzsmIzY3OyYjNTY7JiMxMjA7JiM3NzsmIzY4OyYjNjU7JiMxMTg7JiM3NzsmIzg0OyYjNjU7JiMxMjA7JiM3NjsmIzEyMjsmIzY5OyYjMTE5OyYjNzc7JiMxMDU7JiM1NjsmIzEyMDsmIzc3OyYjNjg7JiM2OTsmIzExODsmIzc3OyYjODQ7JiM2OTsmIzExOTsmIzc2OyYjMTIyOyYjMTA3OyYjNTM7JiM3NjsmIzEyMjsmIzY5OyYjMTE5OyYjNzc7JiM4MzsmIzU2OyYjMTIwOyYjNzc7JiM4NDsmIzEwNzsmIzExODsmIzc3OyYjODQ7JiM2OTsmIzEyMDsmIzc2OyYjMTIyOyYjNjk7JiMxMjA7JiM3ODsmIzY3OyYjNTY7JiMxMjA7JiM3NzsmIzY4OyYjMTAzOyYjMTE4OyYjNzc7JiM4NDsmIzY1OyYjMTE5Ow=="
def dec_base64(str1):
str = base64.b64decode(str1)
return str
def dec_ascii(str1):
str = ""
str1 = str1.split(";")
for i in str1:
try:
str2 = i.split("&#")[1]
ch = chr(int(str2))
str += ch
except:
pass
return str
def dec_ascii2(str1):
str = ""
str1 = str1.split("/")
for i in str1:
try:
ch = chr(int(i))
str += ch
except:
pass
return str
if __name__ == "__main__":
str = dec_base64(str1)
str = dec_ascii(str)
str = dec_base64(str)
str = dec_ascii2(str)
print(str)
第五题:考察栏栅密码
解题报告:
关于栏栅密码的解释[1],在线破解它不香吗?
但是我不推荐大家搜在线破解,这样还不如直接搜索通关答案,是学不到知识滴~
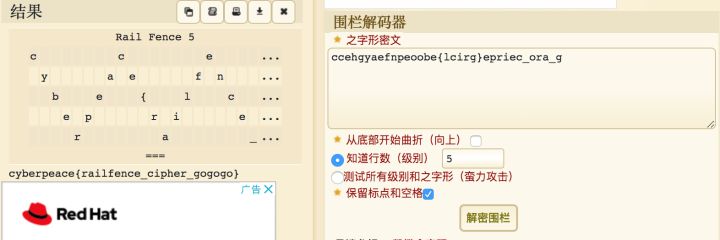
一口气脚本,不求人:
def fence(lst, numrails):
fence = [[None] * len(lst) for n in range(numrails)]
rails = range(numrails - 1) + range(numrails - 1, 0, -1)
for n, x in enumerate(lst):
fence[rails[n % len(rails)]][n] = x
return [c for rail in fence for c in rail if c is not None]
def encode(text, n):
return ''.join(fence(text, n))
def decode(text, n):
rng = range(len(text))
pos = fence(rng, n)
return ''.join(text[pos.index(n)] for n in rng)
z = "ccehgyaefnpeoobe{lcirg}epriec_ora_g"
for i in range(2,10):
y = decode(z,i)
print y
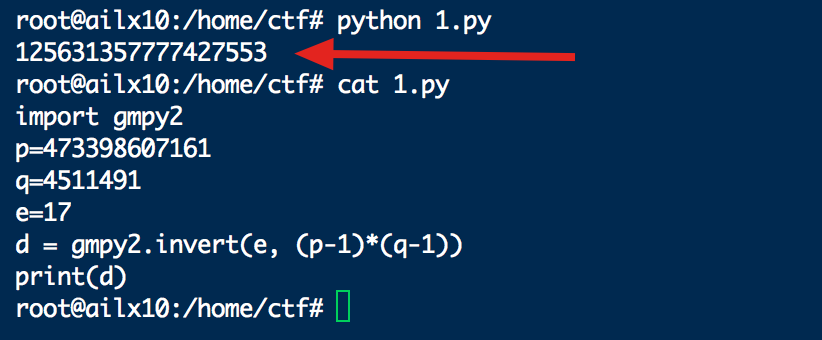
第六题:考察RSA加密
在一次RSA密钥对生成中,假设p=473398607161,q=4511491,e=17
求解出d
解题报告:
在ubuntu下安装的gmpy2,可以直接求d,不求人:
import gmpy2
p=473398607161
q=4511491
e=17
d = gmpy2.invert(e, (p-1)*(q-1))
print(d)
第七题:考察莫斯密码和培根密码
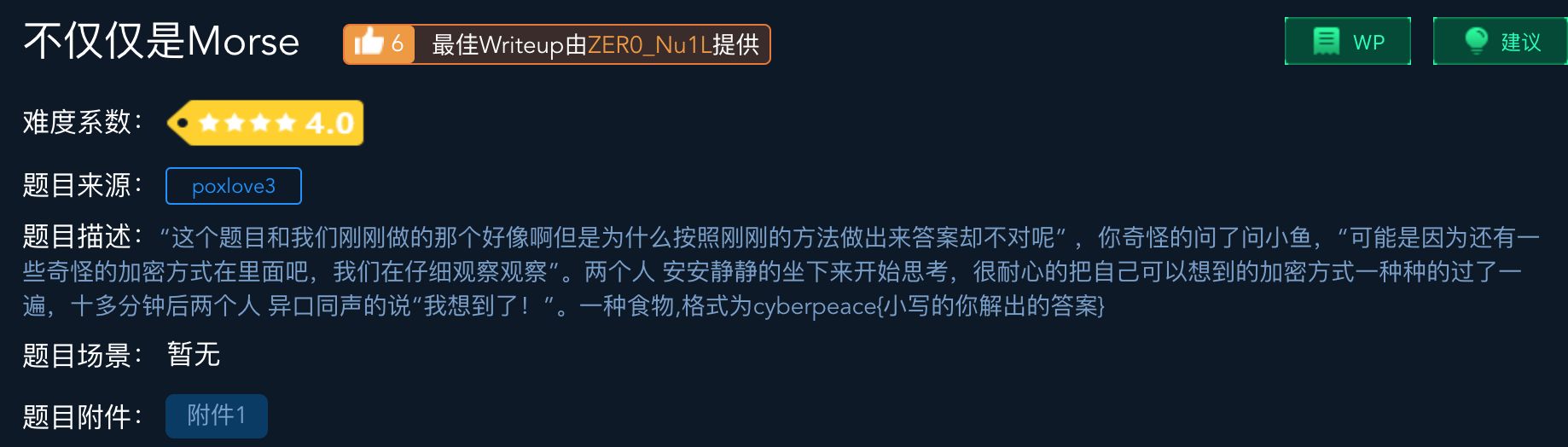
解题报告:
一口气脚本,不求人:
dict1 = {'aaaaa':'a',
'aaaab':'b',
'aaaba':'c',
'aaabb':'d',
'aabaa':'e',
'aabab':'f',
'aabba':'g',
'aabbb':'h',
'abaaa':'i',
'abaab':'j',
'ababa':'k',
'ababb':'l',
'abbaa':'m',
'abbab':'n',
'abbba':'o',
'abbbb':'p',
'baaaa':'q',
'baaab':'r',
'baaba':'s',
'baabb':'t',
'babaa':'u',
'babab':'v',
'babba':'w',
'babbb':'x',
'bbaaa':'y',
'bbaab':'z'
};
dict2 = {'.-': 'a',
'-...': 'b',
'-.-.': 'c',
'-..':'d',
'.':'e',
'..-.':'f',
'--.': 'g',
'....': 'h',
'..': 'i',
'.---':'j',
'-.-': 'k',
'.-..': 'l',
'--': 'm',
'-.': 'n',
'---': 'o',
'.--.': 'p',
'--.-': 'q',
'.-.': 'r',
'...': 's',
'-': 't',
'..-': 'u',
'...-': 'v',
'.--': 'w',
'-..-': 'x',
'-.--': 'y',
'--..': 'z',
'.----': '1',
'..---': '2',
'...--': '3',
'....-': '4',
'.....': '5',
'-....': '6',
'--...': '7',
'---..': '8',
'----.': '9',
'-----': '0',
'/': ' '
};
enc_str0="--/.-/-.--/..--.-/-..././..--.-/..../.-/...-/./..--.-/.-/-./---/-/...././.-./..--.-/-.././-.-./---/-.././..../..../..../..../.-/.-/.-/.-/.-/-.../.-/.-/-.../-.../-.../.-/.-/-.../-.../.-/.-/.-/.-/.-/.-/.-/.-/-.../.-/.-/-.../.-/-.../.-/.-/.-/.-/.-/.-/.-/-.../-.../.-/-.../.-/.-/.-/-.../-.../.-/.-/.-/-.../-.../.-/.-/-.../.-/.-/.-/.-/-.../.-/-.../.-/.-/-.../.-/.-/.-/-.../-.../.-/-.../.-/.-/.-/-.../.-/.-/.-/-.../.-/.-/-.../.-/-.../-.../.-/.-/-.../-.../-.../.-/-.../.-/.-/.-/-.../.-/-.../.-/-.../-.../.-/.-/.-/-.../-.../.-/-.../.-/.-/.-/-.../.-/.-/-.../.-/.-/-.../.-/.-/.-/.-/-.../-.../.-/-.../-.../.-/.-/-.../-.../.-/.-/-.../.-/.-/-.../.-/.-/.-/-.../.-/.-/-.../.-/.-/-.../.-/.-/-.../.-/-.../.-/.-/-.../-.../.-/-.../.-/.-/.-/.-/-.../-.../.-/-.../.-/.-/-.../-.../.-"
dec_str=""
enc_str2=""
enc_str1=enc_str0.split("/")
for i in enc_str1:
try:
enc_str2 += dict2[i]
except:
pass
enc_str2=enc_str2.split("hhhh")[1]
for i in range(len(enc_str2)/5):
dec_str += dict1[enc_str2[:5]]
enc_str2=enc_str2[5:]
print(dec_str)
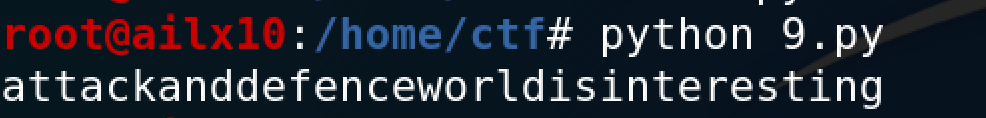
第八题:考察逆运算
解题报告:
python反编译,得到源代码:
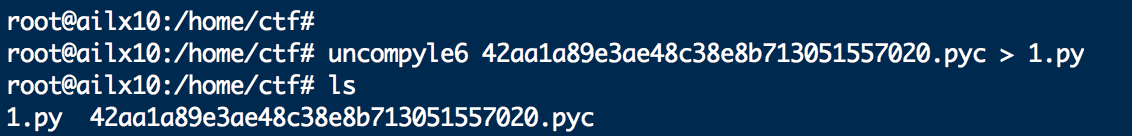
# uncompyle6 version 3.6.2
# Python bytecode 2.7 (62211)
# Decompiled from: Python 2.7.15+ (default, Oct 7 2019, 17:39:04)
# [GCC 7.4.0]
# Embedded file name: ans.py
# Compiled at: 2018-08-09 11:29:44
import base64
def encode1(ans):
s = ''
for i in ans:
x = ord(i) ^ 36
x = x + 25
s += chr(x)
return s
def encode2(ans):
s = ''
for i in ans:
x = ord(i) + 36
x = x ^ 36
s += chr(x)
return s
def encode3(ans):
return base64.b32encode(ans)
flag = ' '
print 'Please Input your flag:'
flag = raw_input()
final = 'UC7KOWVXWVNKNIC2XCXKHKK2W5NLBKNOUOSK3LNNVWW3E==='
if encode3(encode2(encode1(flag))) == final:
print 'correct'
else:
print 'wrong'
# okay decompiling 42aa1a89e3ae48c38e8b713051557020.pyc
逆着它的计算过程,写一个破解代码,不求人:
import base64
str="UC7KOWVXWVNKNIC2XCXKHKK2W5NLBKNOUOSK3LNNVWW3E==="
def decode1(str1):
return base64.b32decode(str1)
def decode2(str1):
s = ''
for i in str1:
x = ord(i)^36
x -= 36
s +=chr(x)
return s
def decode3(str1):
s = ''
for i in str1:
x = ord(i) -25
x ^= 36
s += chr(x)
return s
print(decode3(decode2(decode1(str))))
第九题:考察云影密码
8842101220480224404014224202480122
解题报告:
0是分隔符,1248可以加法得到0-9,再用数字表示A-Z,所以就很简单啦~
一口气脚本,不求人:
enc_str = "8842101220480224404014224202480122"
dec_str = ""
enc = enc_str.split("0")
for i in enc:
sum = 0
for k in i:
sum +=int(k)
ch = chr(sum + ord('A')-1)
dec_str += ch
print(dec_str)
第十题:考察轮转机加密
1: < ZWAXJGDLUBVIQHKYPNTCRMOSFE <
2: < KPBELNACZDTRXMJQOYHGVSFUWI <
3: < BDMAIZVRNSJUWFHTEQGYXPLOCK <
4: < RPLNDVHGFCUKTEBSXQYIZMJWAO <
5: < IHFRLABEUOTSGJVDKCPMNZQWXY <
6: < AMKGHIWPNYCJBFZDRUSLOQXVET <
7: < GWTHSPYBXIZULVKMRAFDCEONJQ <
8: < NOZUTWDCVRJLXKISEFAPMYGHBQ <
9: < XPLTDSRFHENYVUBMCQWAOIKZGJ <
10: < UDNAJFBOWTGVRSCZQKELMXYIHP <
11: < MNBVCXZQWERTPOIUYALSKDJFHG <
12: < LVNCMXZPQOWEIURYTASBKJDFHG <
13: < JZQAWSXCDERFVBGTYHNUMKILOP <
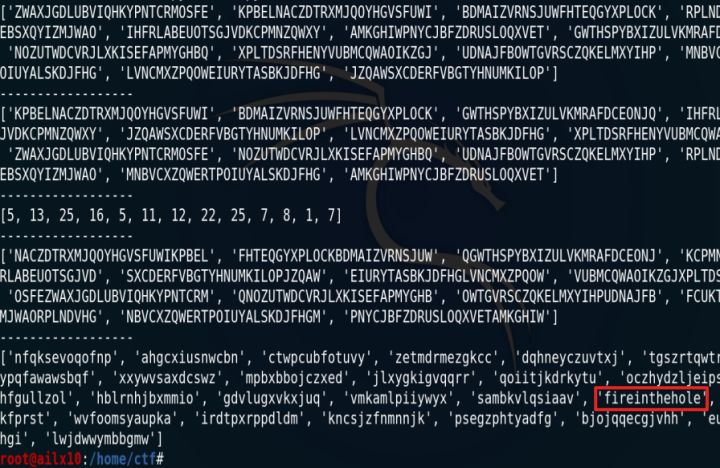
密钥为:2,3,7,5,13,12,9,1,8,10,4,11,6
密文为:NFQKSEVOQOFNP
解题报告:
说实话,要搞懂这题还是挺坑的,首先尝试了一个失败的方法,大家可以分析分析这个解题思路,看看哪里出问题了。我感觉主要还是对这个密钥不理解,错误使用导致的。欢迎高手兄,评论区指点迷经~
第一步:使用密钥,调整轮盘
- 把第1行移动到第2行,2
- 把第2行移动到第3行,3
- 把第3行移动到第7行,7
- 把第4行移动到第5行,5
- 以此类推得到下面这个结果:
1:['NOZUTWDCVRJLXKISEFAPMYGHBQ',
2:'ZWAXJGDLUBVIQHKYPNTCRMOSFE',
3:'KPBELNACZDTRXMJQOYHGVSFUWI',
4:'MNBVCXZQWERTPOIUYALSKDJFHG',
5:'RPLNDVHGFCUKTEBSXQYIZMJWAO',
6:'JZQAWSXCDERFVBGTYHNUMKILOP',
7:'BDMAIZVRNSJUWFHTEQGYXPLOCK',
8:'XPLTDSRFHENYVUBMCQWAOIKZGJ',
9:'GWTHSPYBXIZULVKMRAFDCEONJQ',
10:'UDNAJFBOWTGVRSCZQKELMXYIHP',
11:'LVNCMXZPQOWEIURYTASBKJDFHG',
12:'AMKGHIWPNYCJBFZDRUSLOQXVET',
13:'IHFRLABEUOTSGJVDKCPMNZQWXY']
第二步:左移,对齐密文
1:['NOZUTWDCVRJLXKISEFAPMYGHBQ',
2:'FEZWAXJGDLUBVIQHKYPNTCRMOS',
3:'QOYHGVSFUWIKPBELNACZDTRXMJ',
4:'KDJFHGMNBVCXZQWERTPOIUYALS',
5:'SXQYIZMJWAORPLNDVHGFCUKTEB',
6:'ERFVBGTYHNUMKILOPJZQAWSXCD',
7:'VRNSJUWFHTEQGYXPLOCKBDMAIZ',
8:'OIKZGJXPLTDSRFHENYVUBMCQWA',
9:'QGWTHSPYBXIZULVKMRAFDCEONJ',
10:'OWTGVRSCZQKELMXYIHPUDNAJFB',
11:'FHGLVNCMXZPQOWEIURYTASBKJD',
12:'NYCJBFZDRUSLOQXVETAMKGHIWP',
13:'PMNZQWXYIHFRLABEUOTSGJVDKC']
第三步:从26列中挑一个像密码的,结果失败鸟~
经过了苦思冥想,参考网上的writeUP,依然没搞懂这个咋破解。
感谢评论区的大佬:@忘芥 ,问题出在第一步,要反着调整轮盘,一口气脚本,不求人:
import re
sss='''1: < ZWAXJGDLUBVIQHKYPNTCRMOSFE < 2: < KPBELNACZDTRXMJQOYHGVSFUWI < 3: < BDMAIZVRNSJUWFHTEQGYXPLOCK < 4: < RPLNDVHGFCUKTEBSXQYIZMJWAO < 5: < IHFRLABEUOTSGJVDKCPMNZQWXY < 6: < AMKGHIWPNYCJBFZDRUSLOQXVET < 7: < GWTHSPYBXIZULVKMRAFDCEONJQ < 8: < NOZUTWDCVRJLXKISEFAPMYGHBQ < 9: < XPLTDSRFHENYVUBMCQWAOIKZGJ < 10: < UDNAJFBOWTGVRSCZQKELMXYIHP < 11 < MNBVCXZQWERTPOIUYALSKDJFHG < 12 < LVNCMXZPQOWEIURYTASBKJDFHG < 13 < JZQAWSXCDERFVBGTYHNUMKILOP <
'''
m="NFQKSEVOQOFNP"
content=re.findall(r'< (.*?) <',sss,re.S)
iv=[2,3,7,5,13,12,9,1,8,10,4,11,6]
print(content)
print("------------------")
c2=[None for k in range(13)]
for i,j in enumerate(iv):
c2[i]=content[j-1]
print(c2)
print("------------------")
v=[]
for i in range(13):
index=c2[i].index(m[i])
v.append(index)
print(v)
print("------------------")
c3=[None for k in range(13)]
for i,s in enumerate(c2):
c3[i]=s[v[i]:]+s[:v[i]]
print(c3)
print("------------------")
c5=[]
for i in range(26):
c4=""
for j in range(13):
c4+=c3[j][i]
c5.append(c4.lower())
print(c5)
第十一题:考察RSA加密
解题报告:
拿到了一个公钥和一个密文,求解明文。
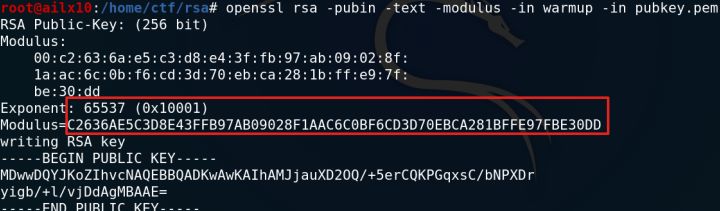
第一步:分析公钥
openssl rsa -pubin -text -modulus -in warmup -in pubkey.pem
第二步:大数进制转换
python的Long类型是不限长度的,所以就:
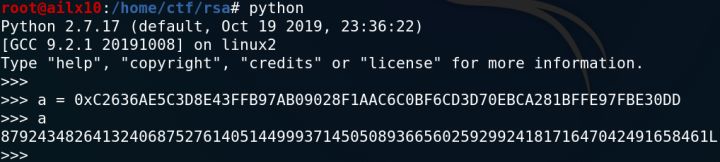
第三步:大数分解
大数因数分解可是个难题,这个还是在线分解[2]来的舒服:
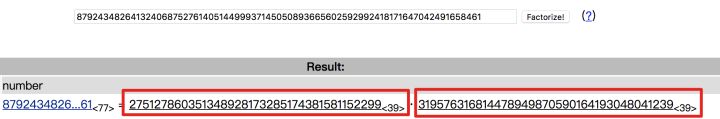
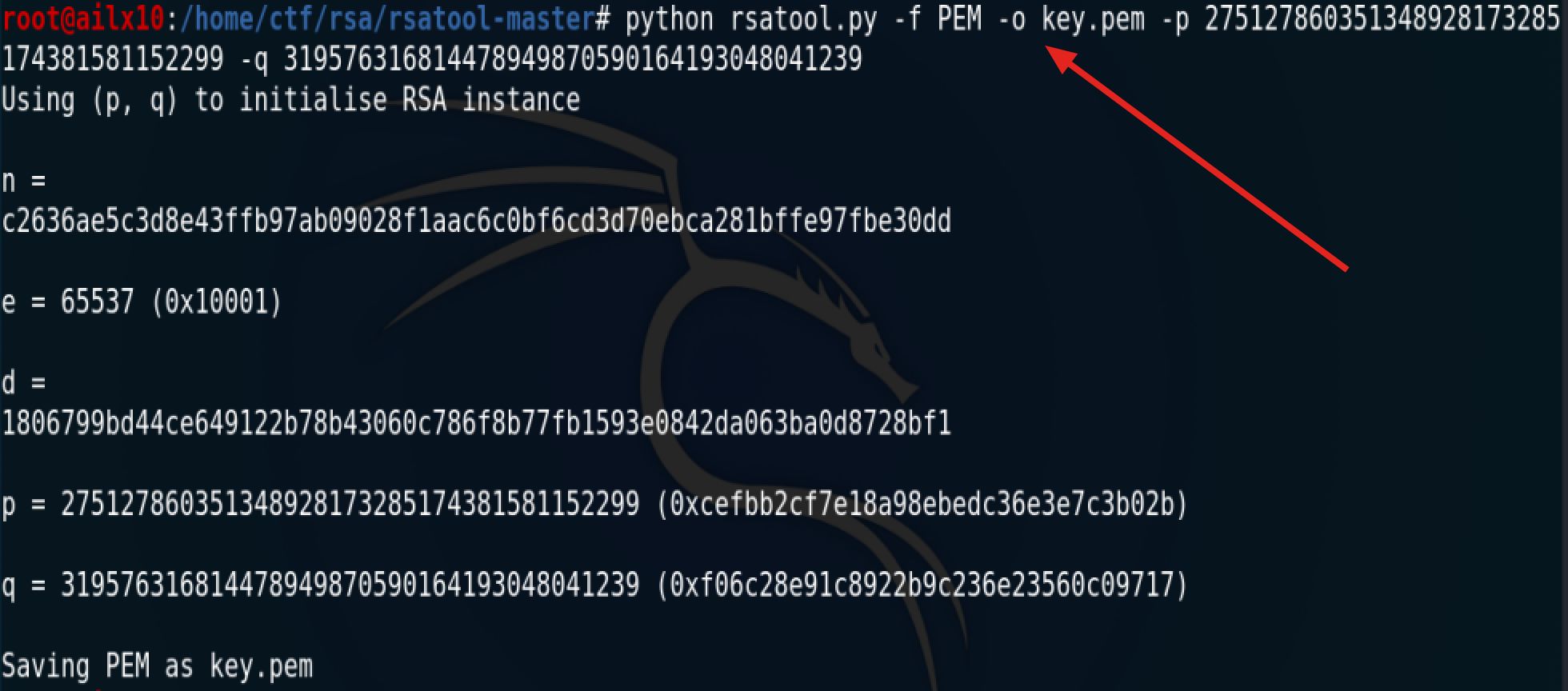
第四步:生成私钥[3]
现在我们有了p、q,就可以轻松拿到私钥
python rsatool.py -f PEM -o key.pem -p 275127860351348928173285174381581152299 -q 319576316814478949870590164193048041239
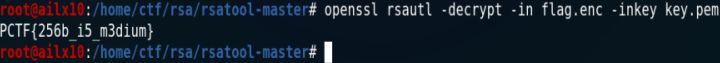
第五步:用私钥解密
openssl rsautl -decrypt -in flag.enc -inkey key.pem
PCTF{256b_i5_m3dium}
第十二题:考察椭圆曲线加密
已知椭圆曲线加密Ep(a,b)参数为
p = 15424654874903
a = 16546484
b = 4548674875
G(6478678675,5636379357093)
私钥为
k = 546768
求公钥K(x,y)
解题报告:

一句话脚本,要求人[4]:
# encoding=utf-8
p = 15424654874903
a = 16546484
b = 4548674875
def add(A, B):
if A == (0, 0): return B
if B == (0, 0): return A
x1, y1 = A
x2, y2 = B
if A != B:
r = (y2 - y1) * pow((x2 - x1), p-2, p)
else:
r = (x1*x1*3 + a) * pow(2*y1, p-2, p)
x3 = r * r - x1 - x2
y3 = r * (x1 - x3) - y1
return (x3 % p, y3 % p)
G = (6478678675,5636379357093)
k = 546768
C = (0, 0)
for i in range(k):
C = add(C, G)
print(C)
print("cyberpeace{%d}"%(C[0]+C[1]))
# cyberpeace{19477226185390}
完结撒花,解题不易,求三连,怕怕怕~






















 437
437











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










